Safety Dashboard

Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V
The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V can be your best option for delivering a presentation. Represent everything in detail using Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments.

Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V
The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices. Want to ace your presentation in front of a live audience Our Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices.

Corporate Security And Risk Management Table Of Contents Corporate Security Summary PDF
This is a corporate security and risk management table of contents corporate security summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring financial assets security, leveraging workforce, budget assessment, dashboard, impact assessment . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
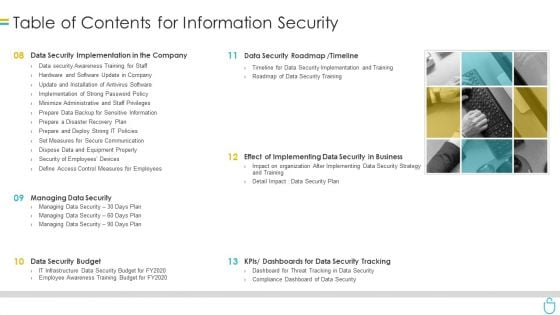
Table Of Contents For Information Security Ppt Styles Outline PDF
Presenting table of contents for information security ppt styles outline pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data security implementation, data security roadmap, data security budget, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
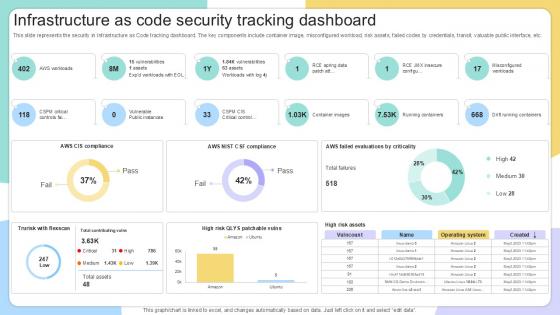
Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide
This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide. This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc.
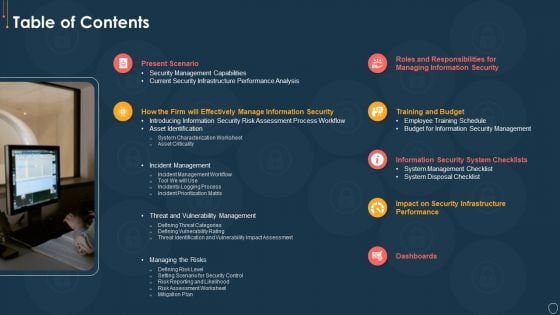
Cyber Security Risk Management Plan Table Of Contents Pictures PDF
Presenting cyber security risk management plan table of contents pictures pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like present scenario, roles and responsibilities, training and budget, dashboards, security infrastructure performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
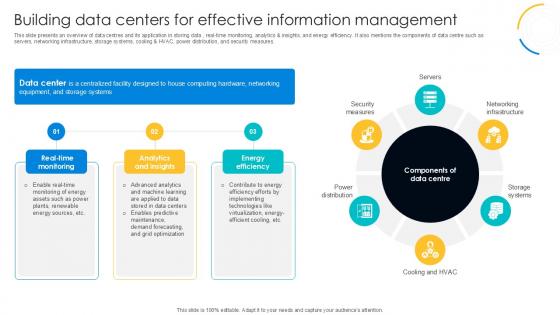
Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V
This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures. If you are looking for a format to display your unique thoughts, then the professionally designed Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures.
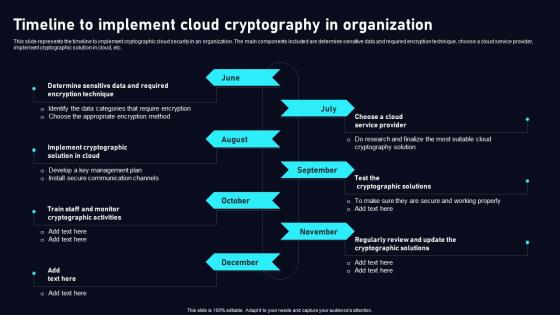
Timeline To Implement Cloud Data Security Using Cryptography Download Pdf
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Timeline To Implement Cloud Data Security Using Cryptography Download Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.

Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
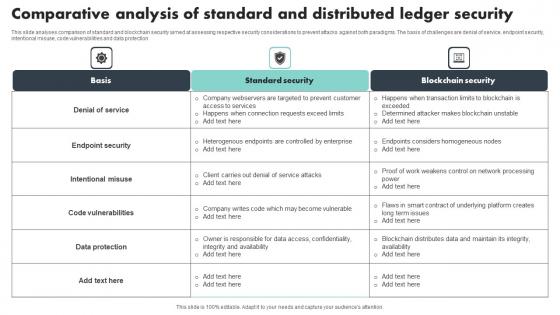
Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf
This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection Pitch your topic with ease and precision using this Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf This layout presents information on Denial Of Service, Endpoint Security, Code Vulnerabilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection

Key Resources Security Service Provider Business Model BMC SS V
This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources. Slidegeeks is here to make your presentations a breeze with Key Resources Security Service Provider Business Model BMC SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources.
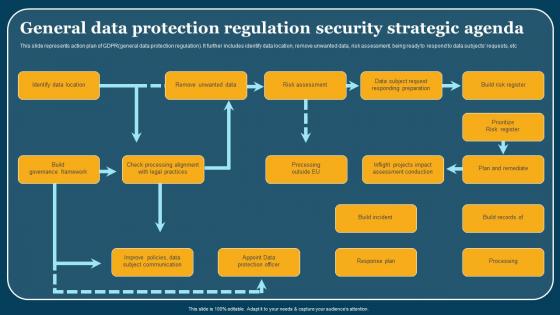
General Data Protection Regulation Security Strategic Agenda Formats Pdf
This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc. Pitch your topic with ease and precision using this General Data Protection Regulation Security Strategic Agenda Formats Pdf. This layout presents information on Identify Data Location, Build Governance Framework, Build Incident. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc.

Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Do you know about Slidesgeeks Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls.
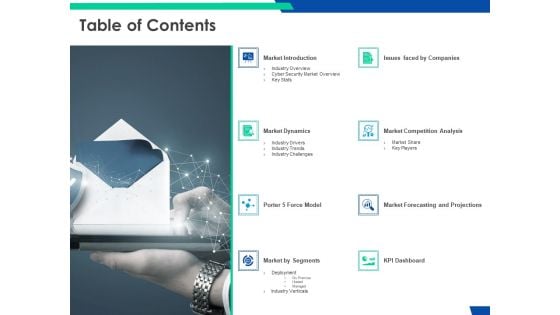
Cloud Based Email Security Market Report Table Of Contents Ppt Inspiration Vector PDF
Presenting cloud based email security market report table of contents ppt inspiration vector pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like market introduction, market dynamics, issues faced by companies, kpi dashboard, market by segments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Risk Management Model For Data Security Diagrams PDF
This is a Table Of Contents For Risk Management Model For Data Security Diagrams PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Present Scenario, Incident Management, Managing Risks, Dashboards, Training And Budget. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
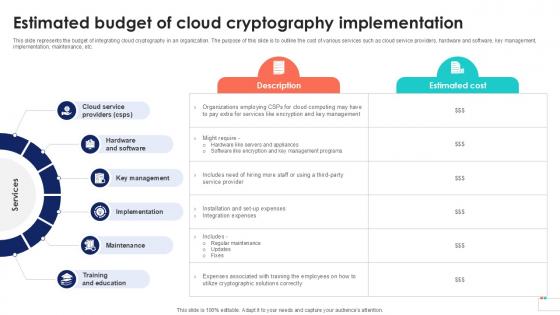
Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide from Slidegeeks and deliver a wonderful presentation. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
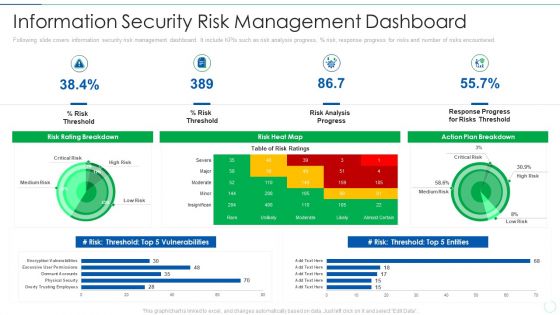
Effective IT Risk Management Process Information Security Risk Management Brochure PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percentage risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative effective it risk management process information security risk management brochure pdf bundle. Topics like analysis, plan, risk, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Security And Performance Digital Marketing Playbook Rules PDF
Presenting Table Of Contents For Security And Performance Digital Marketing Playbook Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Automation Throughout, Automated Sequences, Reporting Dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Functioning Centre Table Of Contents Ppt Professional Graphic Tips PDF
Presenting security functioning centre table of contents ppt professional graphic tips pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like dashboard, impact analysis, incident management, security operations centre, technologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Datacenter Services Network Security Ppt Sample
This is a datacenter services network security ppt sample. This is a five stage process. The stages in this process are arrow, business, marketing.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Table Of Contents Ppt Inspiration Professional PDF
Presenting this set of slides with name strategies to mitigate cyber security risks table of contents ppt inspiration professional pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role personnel, cost associated to firm, impact analysis dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Implementation Framework Table Of Contents Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting this set of slides with name cyber security implementation framework table of contents ppt powerpoint presentation icon portfolio pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role of personnel, cost associated to firm, impact analysis, dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
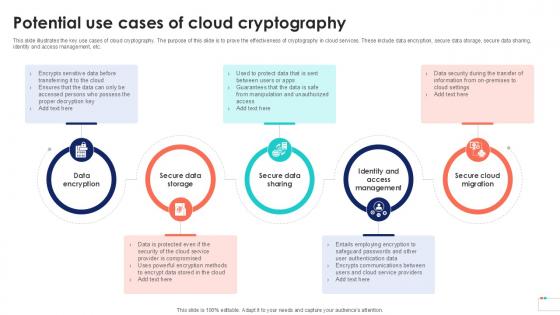
Potential Use Cases Of Cloud Data Security In Cloud Computing Ppt Sample
This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Potential Use Cases Of Cloud Data Security In Cloud Computing Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc.
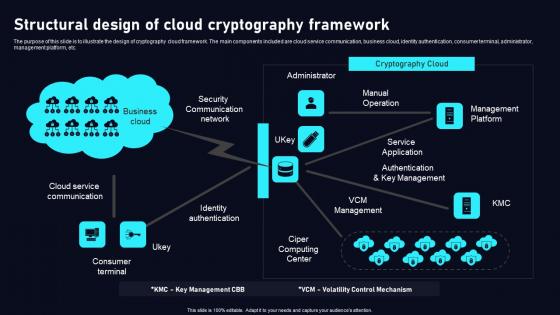
Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.
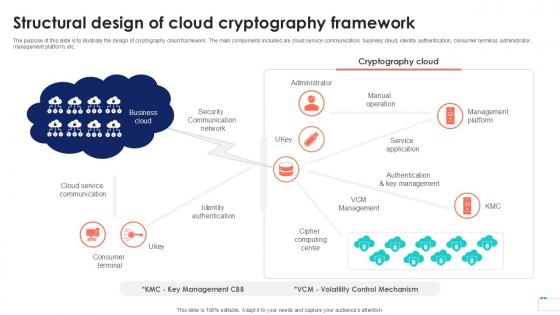
Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.

Use Case Of Splunk Big Data For Security Intelligence Elements Pdf
Following slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc. Showcasing this set of slides titled Use Case Of Splunk Big Data For Security Intelligence Elements Pdf The topics addressed in these templates are Security Monitoring, Compliance, Threat Intelligence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc.
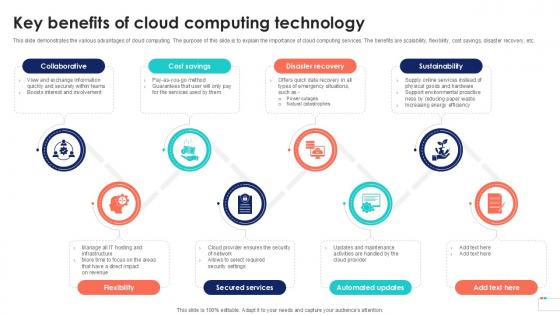
Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example. This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc.

Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API.
Icons Slide For Cloud Security Firewall Proposal
Elevate your presentations with our intuitive Icons Slide For Cloud Security Firewall Proposal template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression. Our Icons Slide For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cybersecurity Key Performance Indicators With Applications Summary Pdf
Pitch your topic with ease and precision using this Cybersecurity Key Performance Indicators With Applications Summary Pdf This layout presents information on Identify Weaknesses, Review Improvement, Security Policies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc.

Statistical Analysis Challenges Data Analytics For Informed Decision Ppt Example
The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints. Slidegeeks has constructed Statistical Analysis Challenges Data Analytics For Informed Decision Ppt Example after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints.

Azure Powerpoint Ppt Template Bundles
Increase your chances of writing a winning business proposal and grabbing your prospects attention with this well-crafted, innovative Azure Powerpoint Ppt Template Bundles. This DevOps, Pricing model, SaaS architecture, Certifications, Big data-slide presentation template comes with in-built content to help you outline a presentation that can serve as an industry benchmark. The complete deck also makes use of an impressive color scheme to create a visual impact and hook the audience. Use this PPT to plan how your business can be the Numero uno in its segment within no time at all. Download now to showcase your brand USP and offerings to engage your client. Azure is a cloud computing platform that offers a comprehensive suite of services, including computing power, storage solutions, networking capabilities, analytics, and artificial intelligence tools. The purpose is to deliver a secure, upgradable, and flexible cloud computing platform that empowers businesses, developers, and organizations to efficiently build, deploy, and manage applications and services. This template includes Azure DeVops services, architecture, pricing models, emerging trends, Artificial intelligence, certifications and Big data.
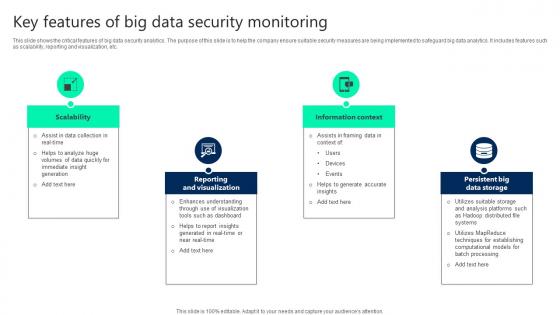
Key Features Of Big Data Security Monitoring Ideas pdf
This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc. Pitch your topic with ease and precision using this Key Features Of Big Data Security Monitoring Ideas pdf. This layout presents information on Scalability, Reporting And Visualization, Information Context. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc.
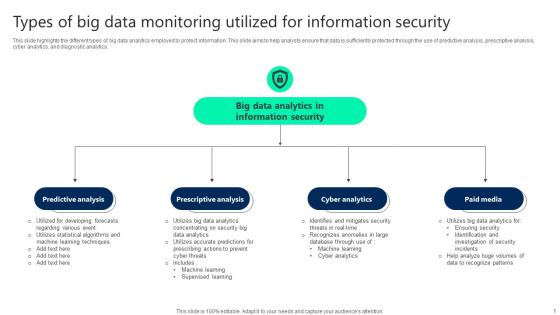
Types Of Big Data Monitoring Utilized For Information Security Elements pdf
This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics. Pitch your topic with ease and precision using this Types Of Big Data Monitoring Utilized For Information Security Elements pdf. This layout presents information on Predictive Analysis, Prescriptive Analysis, Cyber Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics.
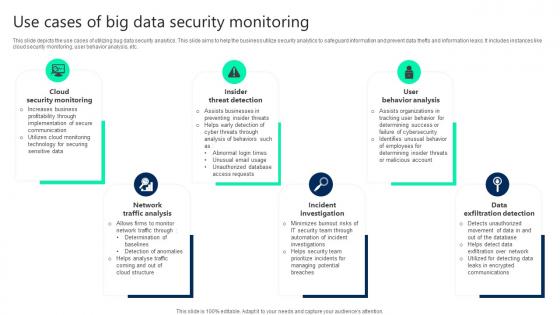
Use Cases Of Big Data Security Monitoring Clipart pdf
This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc. Pitch your topic with ease and precision using this Use Cases Of Big Data Security Monitoring Clipart pdf. This layout presents information on Cloud Security Monitoring, Insider Threat Detection, User Behavior Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc.
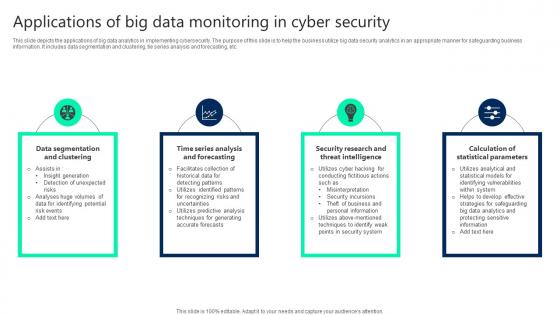
Applications Of Big Data Monitoring In Cyber Security Themes pdf
This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Pitch your topic with ease and precision using this Applications Of Big Data Monitoring In Cyber Security Themes pdf. This layout presents information on Data Segmentation, Security Research, Threat Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc.

IT And Cloud Facilities Management Content Ppt PowerPoint Presentation Infographics Layouts PDF
Presenting it and cloud facilities management content ppt powerpoint presentation infographics layouts pdf to provide visual cues and insights. Share and navigate important information on eleven stages that need your due attention. This template can be used to pitch topics like optimization and decision making, performance and cost functions, capital budgeting, kpi metrics and dashboard, contract and workflow management, interdependence, resiliency and security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
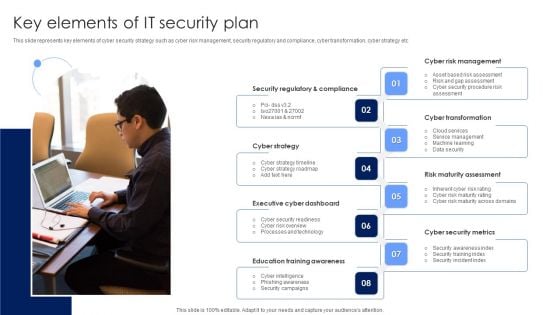
Key Elements Of IT Security Plan Background PDF
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
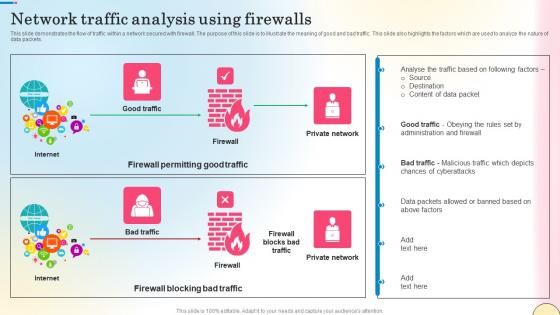
Network Traffic Analysis Using Firewalls Network Security Themes Pdf
This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc. Take your projects to the next level with our ultimate collection of Network Traffic Analysis Using Firewalls Network Security Themes Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc.

Table Of Contents Risk Management For Organization Essential Assets Priorities Infographics PDF
This is a table of contents risk management for organization essential assets priorities infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like leveraging workforce, dashboard, impact assessment, budget assessment, ensuring financial assets security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Table Of Contents For Cybersecurity Business Ppt Outline Guidelines PDF
Presenting cybersecurity table of contents for cybersecurity business ppt outline guidelines pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like information security, implementing, dashboards, organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
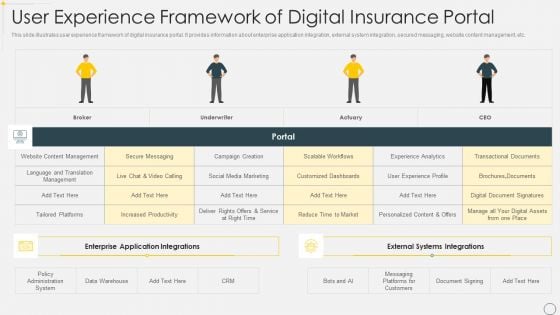
User Experience Framework Of Digital Insurance Portal Brochure PDF
This slide illustrates user experience framework of digital insurance portal. It provides information about enterprise application integration, external system integration, secured messaging, website content management, etc. Showcasing this set of slides titled User Experience Framework Of Digital Insurance Portal Brochure PDF. The topics addressed in these templates are Management, Customized Dashboards, Policy Administration System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Security Challenges And Solutions In Banking Industry Download Pdf
This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.Showcasing this set of slides titled Internet Security Challenges And Solutions In Banking Industry Download Pdf The topics addressed in these templates are Installing Intergraded, Introducing Firewall, Learning Algorisms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.
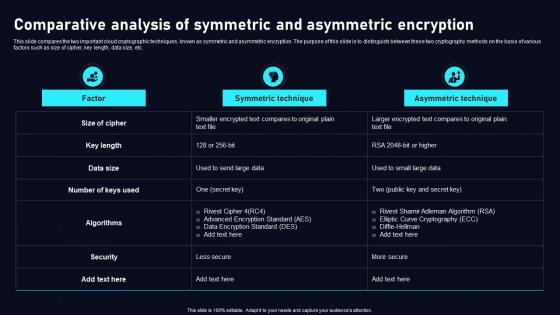
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
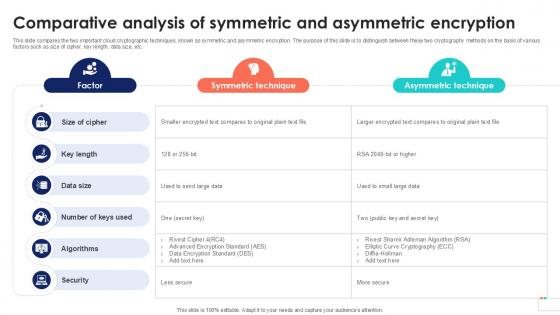
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
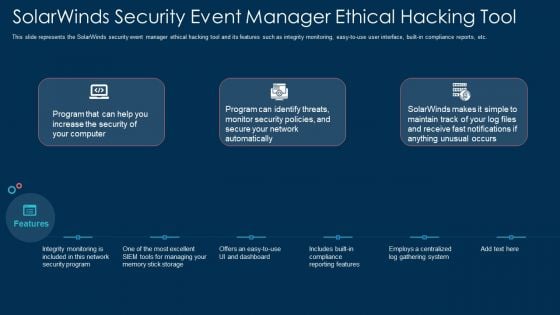
Solarwinds Security Event Manager Ethical Hacking Tool Ppt Show Clipart Images PDF
This slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy to use user interface, built-in compliance reports, etc. Presenting solarwinds security event manager ethical hacking tool ppt show clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network, security program, dashboard, system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
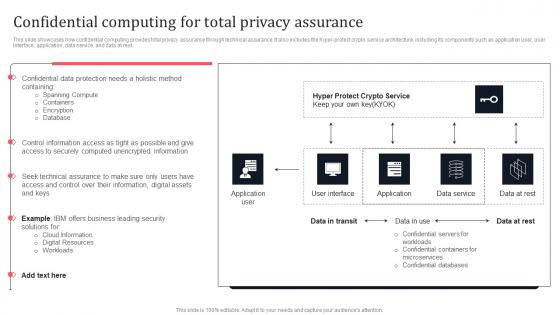
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
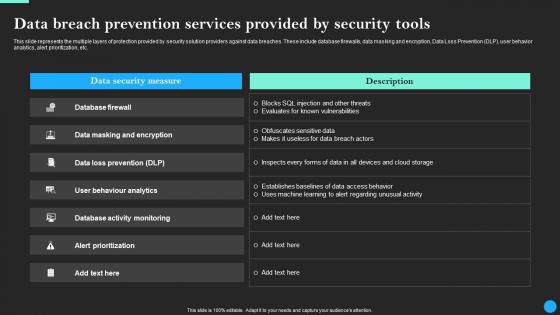
Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdf
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdfand observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc.
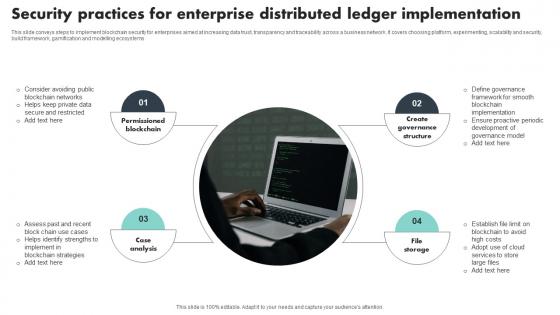
Security Practices For Enterprise Distributed Ledger Implementation Template Pdf
This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems Showcasing this set of slides titled Security Practices For Enterprise Distributed Ledger Implementation Template Pdf The topics addressed in these templates are Permissioned Blockchain, Case Analysis, Create Governance Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems
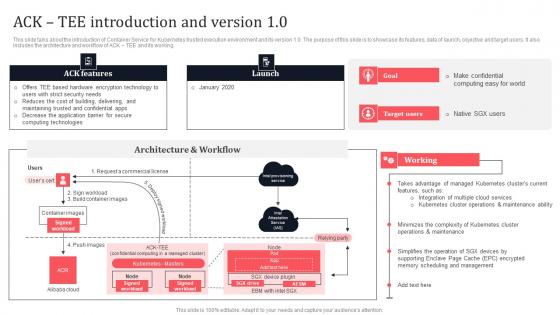
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.

Career Key Isolated PowerPoint Templates And PowerPoint Themes 1012
Career Key Isolated PowerPoint Templates And PowerPoint Themes 1012-Use this template showing the golden key signifying the building of the career. This template portrays the concepts of security, business, services, abstract, lock, unlock, key, data, documents, information, curriculum and old key, abstract, background, career, corporate, employment, yellow, brown, black, security, services, business and abstract.-Career Key Isolated PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Career gold key, security, success, business, future, finance Oversee plans with our Career Key Isolated PowerPoint Templates And PowerPoint Themes 1012. Download without worries with our money back guaranteee.

About Us For Our Firewall Solutions Company Cloud Security Firewall Proposal
This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry-leading organizations, and history.Elevate your presentations with our intuitive About Us For Our Firewall Solutions Company Cloud Security Firewall Proposal template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression. This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry-leading organizations, and history.
Key Solutions For Building A Successful Startup Ppt PowerPoint Presentation Infographics
This is a key solutions for building a successful startup ppt powerpoint presentation infographics. This is a six stage process. The stages in this process are key, arrows, security, business, marketing.

Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
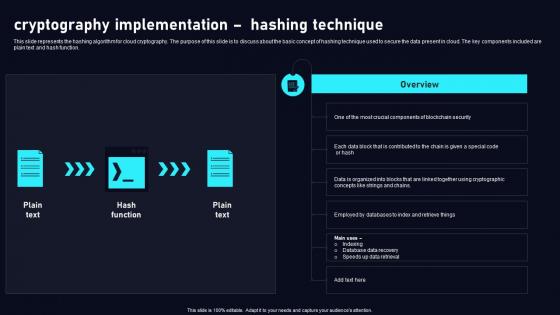
Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. Are you searching for a Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf from Slidegeeks today. This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
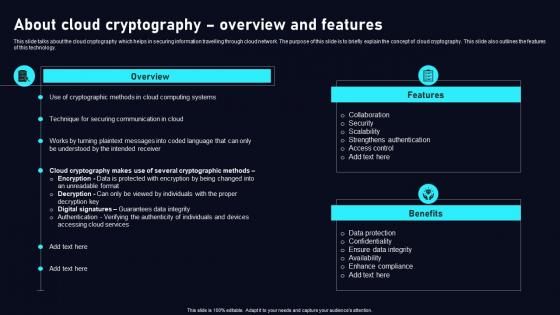
About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Present like a pro with About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
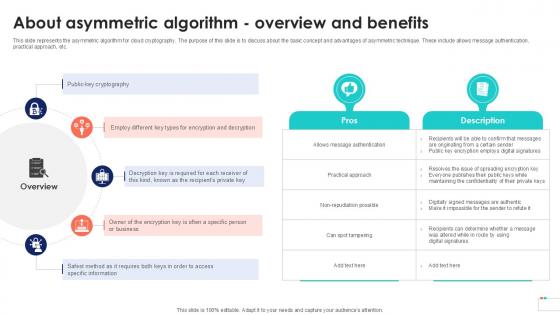
About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Boost your pitch with our creative About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.


 Continue with Email
Continue with Email

 Home
Home


































