Safety Improvement Plan
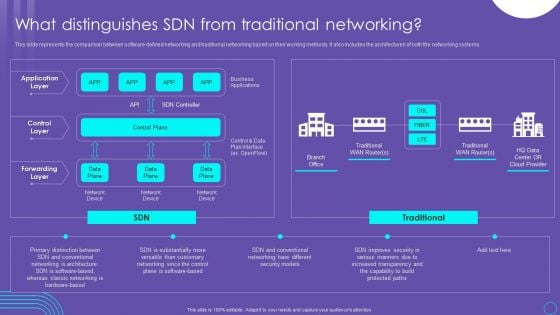
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
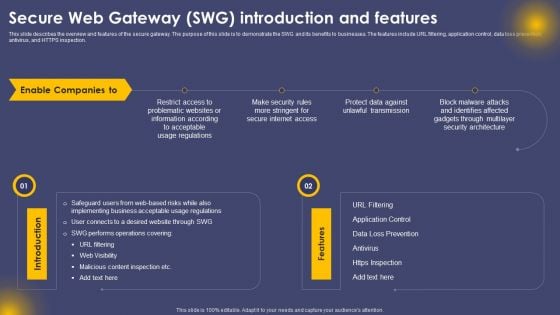
Secure Web Gateway SWG Introduction And Features Ppt Portfolio Master Slide PDF
This slide describes the overview and features of the secure gateway. The purpose of this slide is to demonstrate the SWG and its benefits to businesses. The features include URL filtering, application control, data loss prevention, antivirus, and HTTPS inspection. Present like a pro with Secure Web Gateway SWG Introduction And Features Ppt Portfolio Master Slide PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Explore a selection of the finest Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
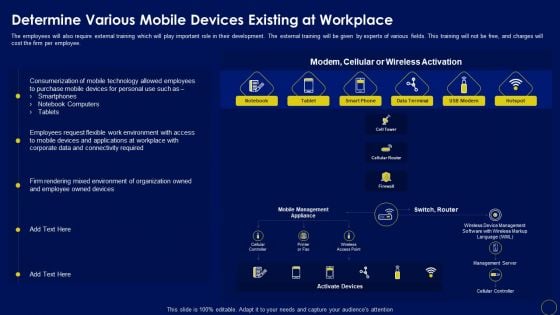
Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Do you know about Slidesgeeks Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
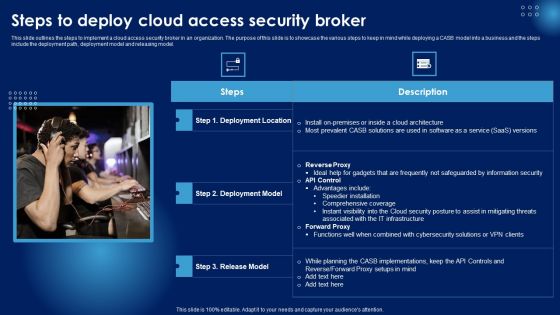
Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cognitive Visualizations Computing Strategy How Cognitive Technology Affects Functional Business Areas Slides PDF
This slide provides information regarding how cognitive technology affect core functional business areas such as front office, middle office and back office. Deliver an awe inspiring pitch with this creative Cognitive Visualizations Computing Strategy How Cognitive Technology Affects Functional Business Areas Slides PDF bundle. Topics like Customer Service, Product Development, Information Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
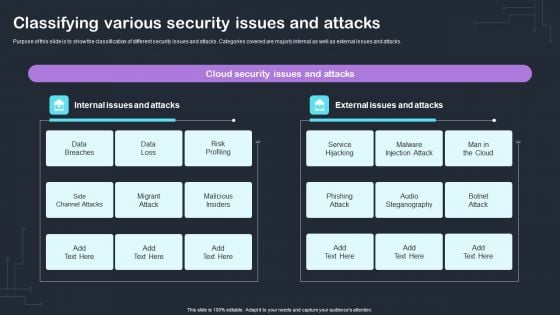
Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
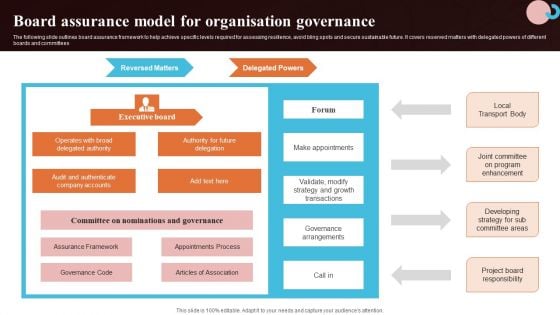
Board Assurance Model For Organisation Governance Diagrams PDF
The following slide outlines board assurance framework to help achieve specific levels required for assessing resilience, avoid bling spots and secure sustainable future. It covers reserved matters with delegated powers of different boards and committees. Showcasing this set of slides titled Board Assurance Model For Organisation Governance Diagrams PDF. The topics addressed in these templates are Assurance Framework, Appointments Process, Articles Of Association. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
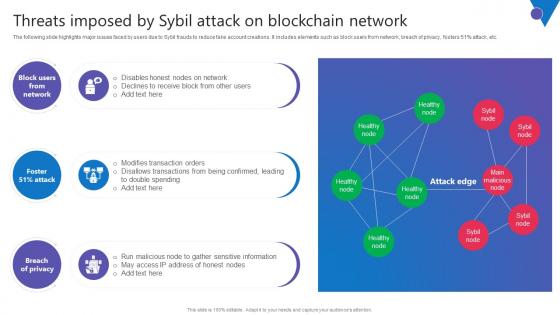
Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc.
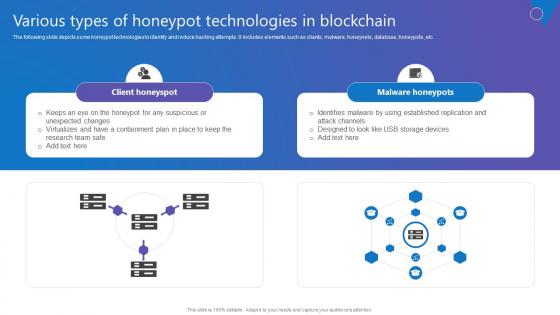
Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc.
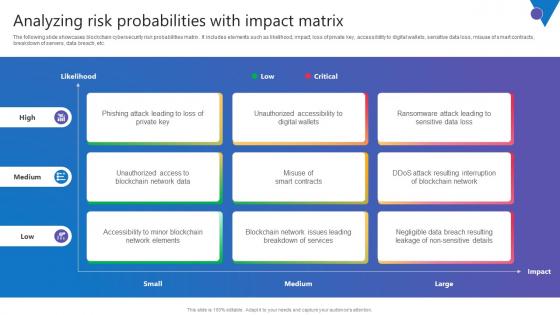
Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Presenting this PowerPoint presentation, titled Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc.

Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF
The following slide will assist an IT company to show the investors or audience a complete view of its competitive landscape based on elements like leaders by category, company, their market capitalization and revenue. There are so many reasons you need a Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Key Issues Faced By Hospitality Sector Ppt PowerPoint Presentation Icon Example PDF
Showcasing this set of slides titled key issues faced by hospitality sector ppt powerpoint presentation icon example pdf. The topics addressed in these templates are management, data security, growth. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Best Practices To Create Winning Digital Account Opening Experience Mockup PDF
This slide covers top techniques to enhance customer experience in opening digital bank account. The purpose of this template is to provide an overview of action steps that should be taken to improve user experience. It includes techniques such as streamlining KYC checks, adopting a mobile first account opening, emphazing regulatory and security, etc along with action steps and impact of these techniques. Find a pre designed and impeccable Best Practices To Create Winning Digital Account Opening Experience Mockup PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
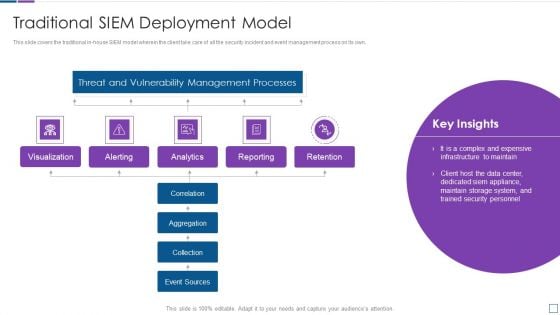
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
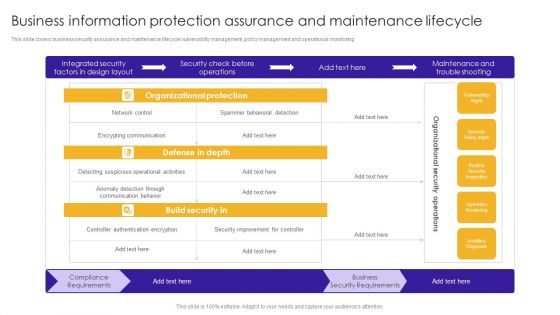
Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
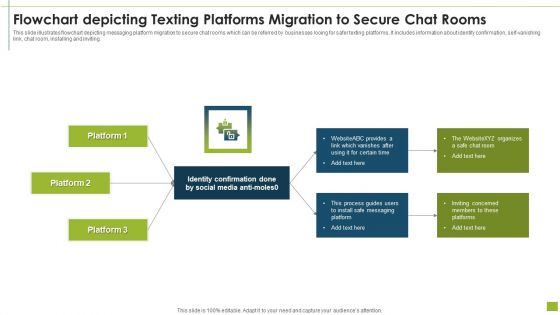
Flowchart Depicting Texting Platforms Migration To Secure Chat Rooms Inspiration PDF
This slide illustrates flowchart depicting messaging platform migration to secure chat rooms which can be referred by businesses looing for safer texting platforms. It includes information about identity confirmation, self-vanishing link, chat room, installing and inviting.Pitch your topic with ease and precision using this flowchart depicting texting platforms migration to secure chat rooms inspiration pdf This layout presents information on identity confirmation, process guides, install safe messaging It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
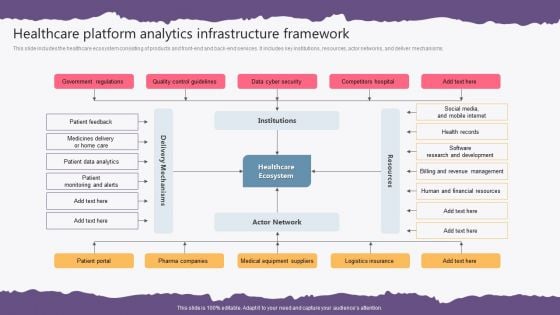
Healthcare Platform Analytics Infrastructure Framework Background PDF
This slide includes the healthcare ecosystem consisting of products and front-end and back-end services. It includes key institutions, resources, actor networks, and deliver mechanisms. Pitch your topic with ease and precision using this Healthcare Platform Analytics Infrastructure Framework Background PDF. This layout presents information on Government Regulations, Quality Control Guidelines, Data Cyber Security, Competitors Hospital. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Quantum Computing For Everyone IT How Will Quantum Computing Help Enterprises Download PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Deliver and pitch your topic in the best possible manner with this quantum computing for everyone it how will quantum computing help enterprises download pdf. Use them to share invaluable insights on development, optimization, accelerate autonomous, transform cybersecurity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
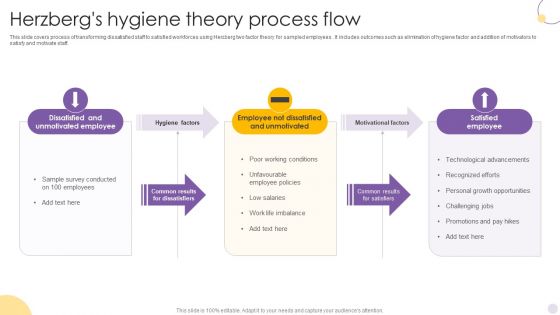
Herzbergs Hygiene Theory Process Flow Introduction PDF
This slide covers conditional hygiene and motivating factors to match motivation with job requirements. It includes extrinsic and intrinsic factors such as salary and pay hikes, secure working conditions , grow and career opportunities, recognition of efforts, etc. Showcasing this set of slides titled Herzbergs Hygiene Theory Process Flow Introduction PDF. The topics addressed in these templates are Hygiene Factors, Motivational Factors, Satisfied Employee. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
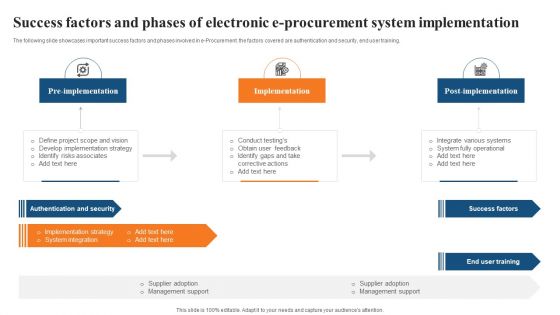
Success Factors And Phases Of Electronic E Procurement System Implementation Formats PDF
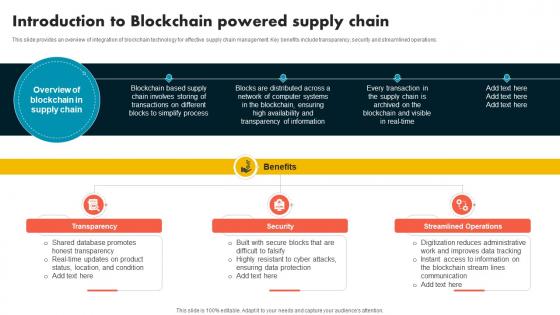
Introduction To Blockchain Powered Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V
This slide provides an overview of integration of blockchain technology for effective supply chain management. Key benefits include transparency, security and streamlined operations. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Introduction To Blockchain Powered Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Introduction To Blockchain Powered Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V today and make your presentation stand out from the rest This slide provides an overview of integration of blockchain technology for effective supply chain management. Key benefits include transparency, security and streamlined operations.
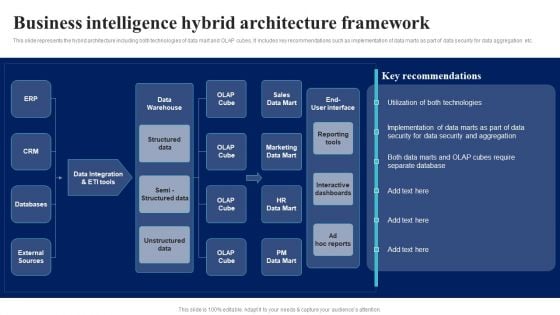
BI Implementation To Enhance Hiring Process Business Intelligence Hybrid Architecture Framework Structure PDF
This slide represents the hybrid architecture including both technologies of data mart and OLAP cubes. It includes key recommendations such as implementation of data marts as part of data security for data aggregation etc.Slidegeeks is here to make your presentations a breeze with BI Implementation To Enhance Hiring Process Business Intelligence Hybrid Architecture Framework Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Roadmap To Identify And Launch Devops Initiatives Ppt Professional Slide Download PDF
This template covers DevOps implementation roadmaps starting from organizing devOps initiative, then building, containerizing, integrating, test automation and monitoring etc. Deliver and pitch your topic in the best possible manner with this roadmap to identify and launch devops initiatives ppt professional slide download pdf. Use them to share invaluable insights on process, security, strategy, opportunities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
RUP Methodology Management And Control Change Software Icons PDF
This slide represents how management and control change software is easy in the rational unified process methodology RUP also determines work and security domains.Deliver an awe inspiring pitch with this creative RUP Methodology Management And Control Change Software Icons PDF bundle. Topics like Unforeseen Effects On Applications, Management Is Critical, Domains Assuring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
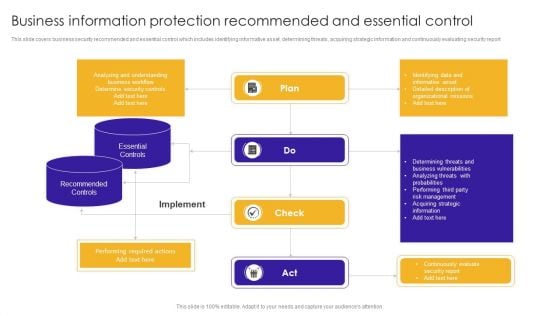
Business Information Protection Recommended And Essential Control Background PDF
This slide covers business security recommended and essential control which includes identifying informative asset, determining threats, acquiring strategic information and continuously evaluating security report. Showcasing this set of slides titled Business Information Protection Recommended And Essential Control Background PDF. The topics addressed in these templates are Determining Threats, Business Vulnerabilities, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
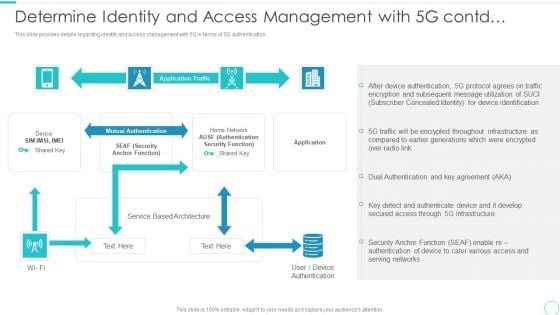
5G Evolution Architectural Technology Determine Identity And Access Management With 5G Contd Microsoft PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Determine Identity And Access Management With 5G Contd Microsoft PDF Use them to share invaluable insights on Uthentication, Security Function, Based Architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
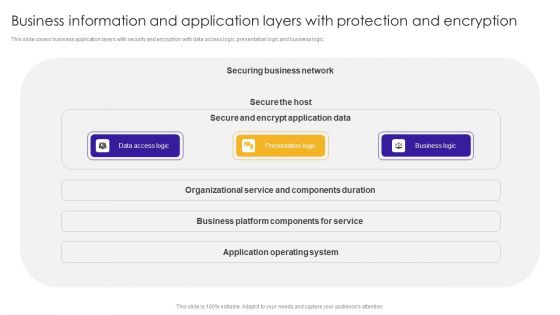
Business Information And Application Layers With Protection And Encryption Brochure PDF
This slide covers business application layers with security and encryption with data access logic, presentation logic and business logic.Pitch your topic with ease and precision using this Business Information And Application Layers With Protection And Encryption Brochure PDF. This layout presents information on Organizational Service, Components Duration, Operating System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
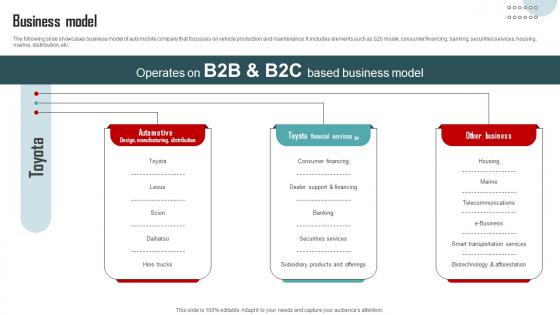
Business Model Vehicle Company Capital Funding Pitch Deck
The following slide showcases business model of automobile company that focusses on vehicle production and maintenance. It includes elements such as b2b model, consumer financing, banking, securities services, housing, marine, distribution, etc. Boost your pitch with our creative Business Model Vehicle Company Capital Funding Pitch Deck. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The following slide showcases business model of automobile company that focusses on vehicle production and maintenance. It includes elements such as b2b model, consumer financing, banking, securities services, housing, marine, distribution, etc.
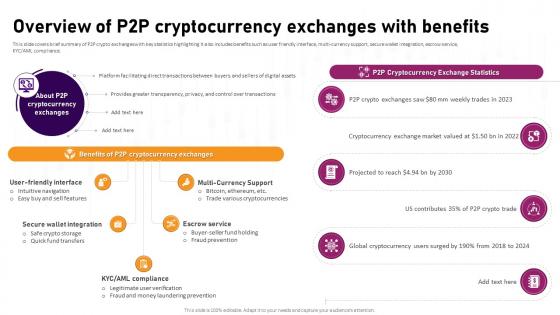
Overview Of P2P Cryptocurrency Exchanges With Complete Roadmap To Blockchain BCT SS V
This slide covers brief summary of P2P crypto exchanges with key statistics highlighting It also includes benefits such as user friendly interface, multi-currency support, secure wallet integration, escrow service, KYC AML compliance. Slidegeeks is here to make your presentations a breeze with Overview Of P2P Cryptocurrency Exchanges With Complete Roadmap To Blockchain BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers brief summary of P2P crypto exchanges with key statistics highlighting It also includes benefits such as user friendly interface, multi-currency support, secure wallet integration, escrow service, KYC AML compliance.
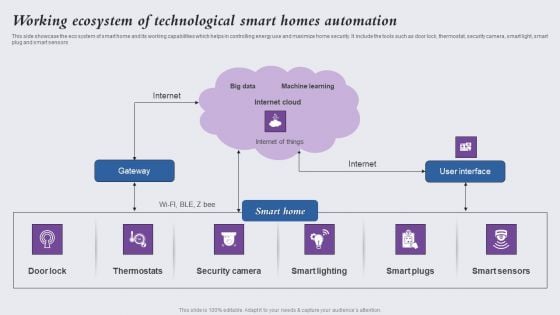
Working Ecosystem Of Technological Smart Homes Automation Elements PDF
This side showcase the eco system of smart home and its working capabilities which helps in controlling energy use and maximize home security. It include the tools such as door lock, thermostat, security camera, smart light, smart plug and smart sensors. Showcasing this set of slides titled Working Ecosystem Of Technological Smart Homes Automation Elements PDF. The topics addressed in these templates are Internet, Gateway, Thermostats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
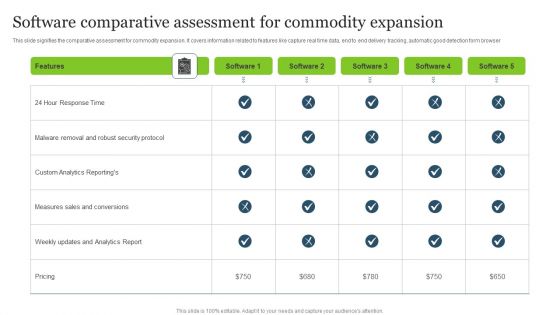
Software Comparative Assessment For Commodity Expansion Microsoft PDF
This slide signifies the comparative assessment for commodity expansion. It covers information related to features like capture real time data, end to end delivery tracking, automatic good detection form browser.Pitch your topic with ease and precision using this Software Comparative Assessment For Commodity Expansion Microsoft PDF. This layout presents information on Malware Removal, Security Protocol, Custom Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Employee Upskilling Training Program Ppt Outline Layout Ideas PDF
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables. Deliver and pitch your topic in the best possible manner with this employee upskilling training program ppt outline layout ideas pdf. Use them to share invaluable insights on security target, performance, risk, analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Online Gaming Funding Pitch Deck Rendering Unified Solutions To Handle Concerns Faced By Prospect Download PDF
This slide caters details about unified solutions to address concerns faced by clients in terms of game engine, security enhancement, revolutionary gameplay, absolute control. Deliver an awe inspiring pitch with this creative online gaming funding pitch deck rendering unified solutions to handle concerns faced by prospect download pdf bundle. Topics like game engine, revolutionary gameplay, security enhancement, absolute control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
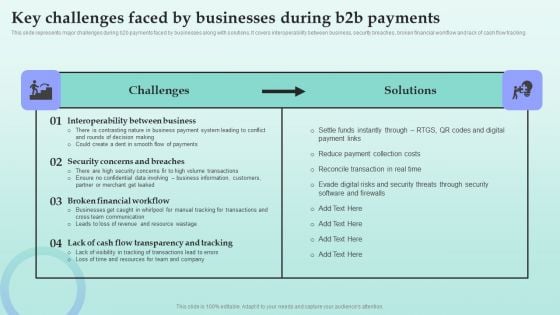
Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
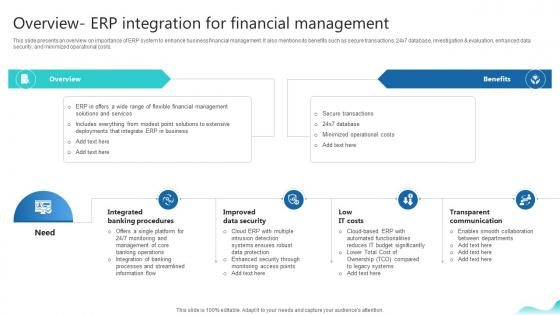
Overview Erp Integration For Financial Management Erp And Digital Transformation For Maximizing DT SS V
This slide presents an overview on importance of ERP system to enhance business financial management. It also mentions its benefits such as secure transactions, 24x7 database, investigation and evaluation, enhanced data security, and minimized operational costs.The Overview Erp Integration For Financial Management Erp And Digital Transformation For Maximizing DT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide presents an overview on importance of ERP system to enhance business financial management. It also mentions its benefits such as secure transactions, 24x7 database, investigation and evaluation, enhanced data security, and minimized operational costs.
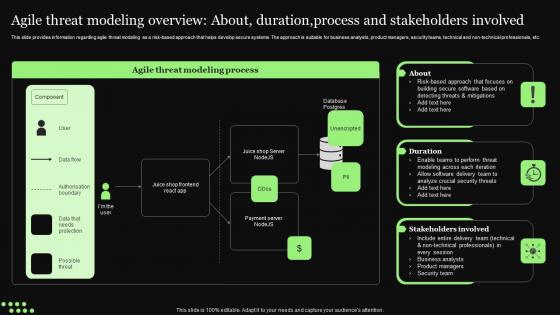
Ethical Technology Utilization Agile Threat Modeling Overview Duration process Formats Pdf
This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Create an editable Ethical Technology Utilization Agile Threat Modeling Overview Duration process Formats Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Ethical Technology Utilization Agile Threat Modeling Overview Duration process Formats Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc.
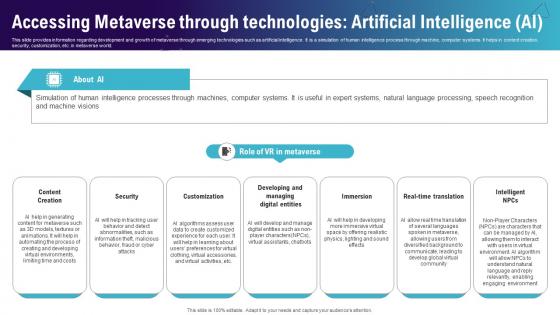
Accessing Metaverse Through Technologies Artificial Continuum Of Technology Revamping Business AI SS V
This slide provides information regarding development and growth of metaverse through emerging technologies such as artificial intelligence. It is a simulation of human intelligence process through machine, computer systems. It helps in content creation, security, customization, etc. in metaverse world. Create an editable Accessing Metaverse Through Technologies Artificial Continuum Of Technology Revamping Business AI SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Accessing Metaverse Through Technologies Artificial Continuum Of Technology Revamping Business AI SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding development and growth of metaverse through emerging technologies such as artificial intelligence. It is a simulation of human intelligence process through machine, computer systems. It helps in content creation, security, customization, etc. in metaverse world.
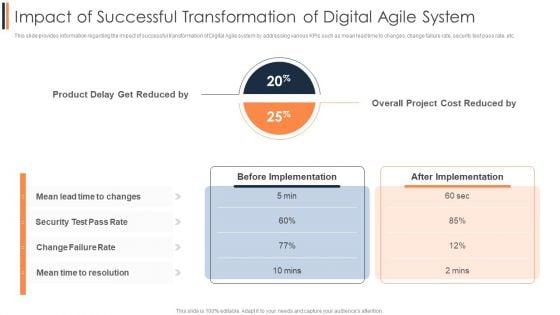
Agile Approach To Digital Transformation IT Impact Of Successful Transformation Of Digital Agile System Professional PDF
This slide provides information regarding the impact of successful transformation of Digital Agile system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. Deliver an awe inspiring pitch with this creative Agile Approach To Digital Transformation IT Impact Of Successful Transformation Of Digital Agile System Professional PDF bundle. Topics like Overall Project, Cost Reduced, Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
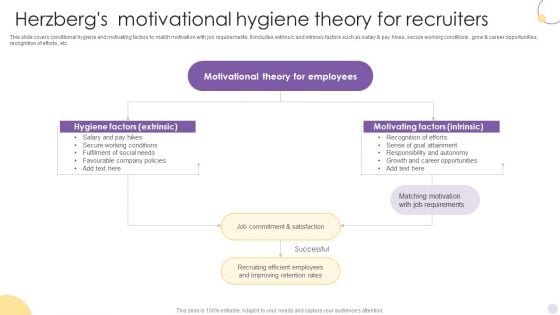
Herzbergs Motivational Hygiene Theory For Recruiters Structure PDF
This slide covers conditional hygiene and motivating factors to match motivation with job requirements. It includes extrinsic and intrinsic factors such as salary and pay hikes, secure working conditions, grow and career opportunities, recognition of efforts, etc. Showcasing this set of slides titled Herzbergs Motivational Hygiene Theory For Recruiters Structure PDF. The topics addressed in these templates are Hygiene Factors, Motivating Factors, Motivational Theory. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Step 3 Assess The Environment Elements PDF
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Step 3 Assess The Environment Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Step 3 Assess The Environment Elements PDF today and make your presentation stand out from the rest
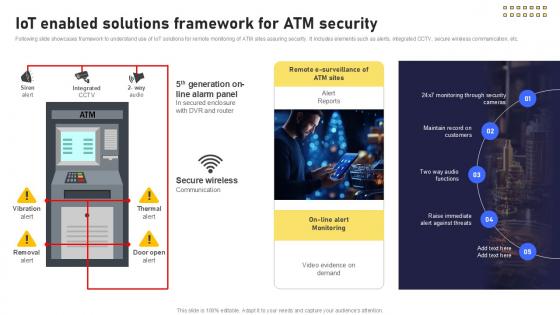
IoT Enabled Solutions Framework Banking Future With IoT Ppt Sample IoT SS V
Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc. Find highly impressive IoT Enabled Solutions Framework Banking Future With IoT Ppt Sample IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IoT Enabled Solutions Framework Banking Future With IoT Ppt Sample IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc.
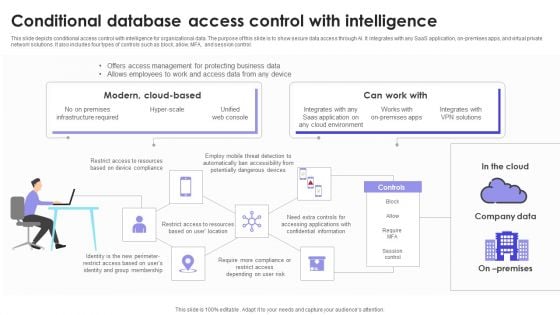
Conditional Database Access Control With Intelligence Download PDF
This slide depicts conditional access control with intelligence for organizational data. The purpose of this slide is to show secure data access through AI. It integrates with any SaaS application, on-premises apps, and virtual private network solutions. It also includes four types of controls such as block, allow, MFA, and session control. Pitch your topic with ease and precision using this Conditional Database Access Control With Intelligence Download PDF. This layout presents information on Company Data, Modern, Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
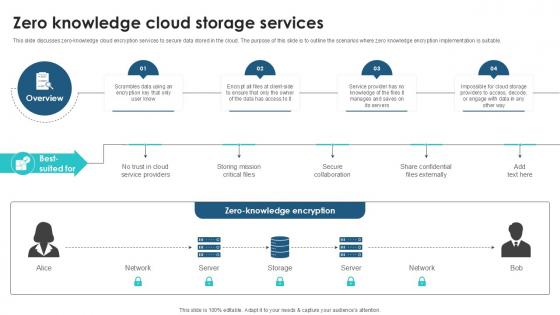
Zero Knowledge Cloud Storage Client Side Encryption PPT Template
This slide discusses zero-knowledge cloud encryption services to secure data stored in the cloud. The purpose of this slide is to outline the scenarios where zero knowledge encryption implementation is suitable. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Knowledge Cloud Storage Client Side Encryption PPT Template to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Knowledge Cloud Storage Client Side Encryption PPT Template. This slide discusses zero-knowledge cloud encryption services to secure data stored in the cloud. The purpose of this slide is to outline the scenarios where zero knowledge encryption implementation is suitable.

Cryptocurrencies Available On Kraken Complete Roadmap To Blockchain BCT SS V
This slide covers types of coins available for trading on Kraken crypto exchange platforms. It includes coins such as bitcoins, Ethereum, XRP, Cardano, Solana, Dogecoin, Polkadot, Polygon, TRON, etc along with ratings for Kraken based on trading, advanced trading features, security and storage, crypto wallets, staking, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Cryptocurrencies Available On Kraken Complete Roadmap To Blockchain BCT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cryptocurrencies Available On Kraken Complete Roadmap To Blockchain BCT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers types of coins available for trading on Kraken crypto exchange platforms. It includes coins such as bitcoins, Ethereum, XRP, Cardano, Solana, Dogecoin, Polkadot, Polygon, TRON, etc along with ratings for Kraken based on trading, advanced trading features, security and storage, crypto wallets, staking, etc.
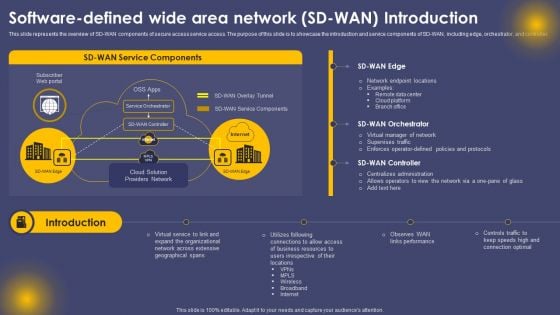
Software Defined Wide Area Network SD WAN Introduction Ppt Slides Objects PDF
This slide represents the overview of SD-WAN components of secure access service access. The purpose of this slide is to showcase the introduction and service components of SD-WAN, including edge, orchestrator, and controller. Present like a pro with Software Defined Wide Area Network SD WAN Introduction Ppt Slides Objects PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
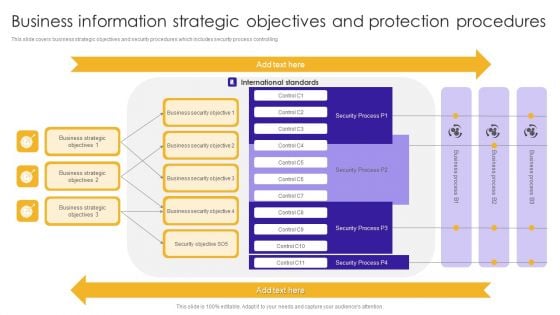
Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
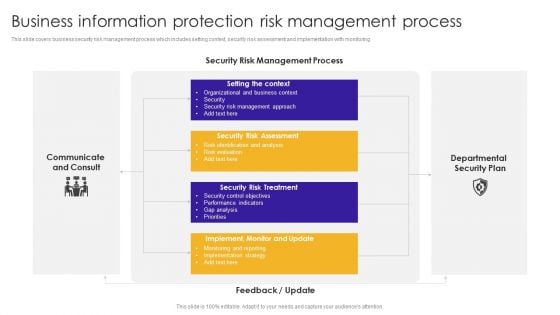
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
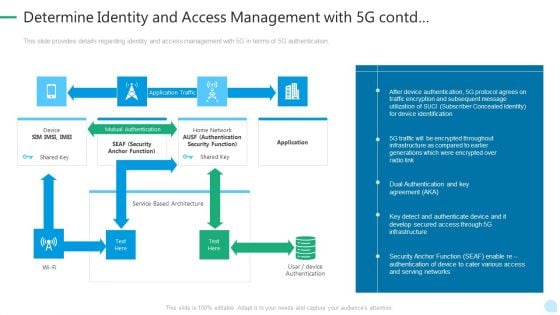
5G Network Technology Determine Identity And Access Management With 5G Contd Ppt Outline Background PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver an awe inspiring pitch with this creative 5g network technology determine identity and access management with 5g contd ppt outline background pdf bundle. Topics like security, develop, infrastructure, protocol can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
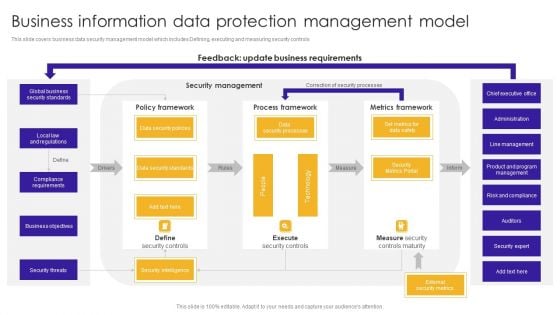
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computerized Game Pitch Deck Rendering Unified Solutions To Handle Concerns Faced By Prospect Download PDF
This slide caters details about unified solutions to address concerns faced by clients in terms of game engine, security enhancement, revolutionary gameplay, absolute control. Deliver and pitch your topic in the best possible manner with this computerized game pitch deck rendering unified solutions to handle concerns faced by prospect download pdf. Use them to share invaluable insights on game engine, absolute control, security enhancement, revolutionary gameplay and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
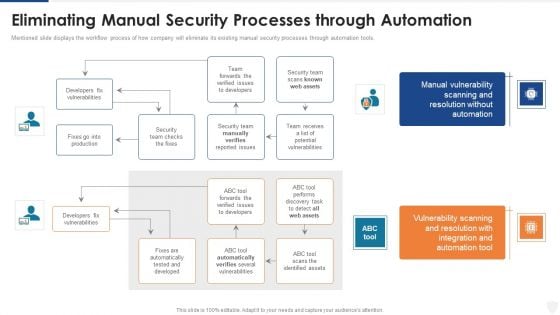
Defining Risk Events Based On Impact Size And Likelihood Of Occurrence Ppt Pictures Background PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this eliminating manual security processes through automation ppt styles images pdf. Use them to share invaluable insights on security, team, production, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
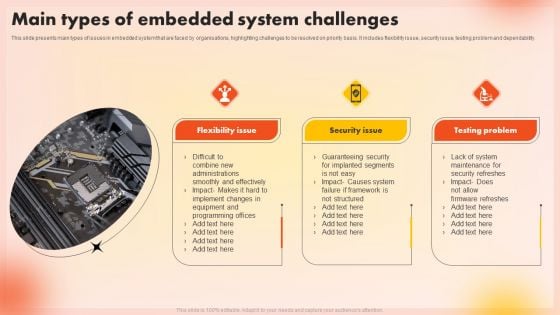
Main Types Of Embedded System Challenges Download PDF
This slide presents main types of issues in embedded system that are faced by organisations, highlighting challenges to be resolved on priority basis. It includes flexibility issue, security issue, testing problem and dependability. Showcasing this set of slides titled Main Types Of Embedded System Challenges Download PDF. The topics addressed in these templates are Flexibility Issue, Security Issue, Testing Problem. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
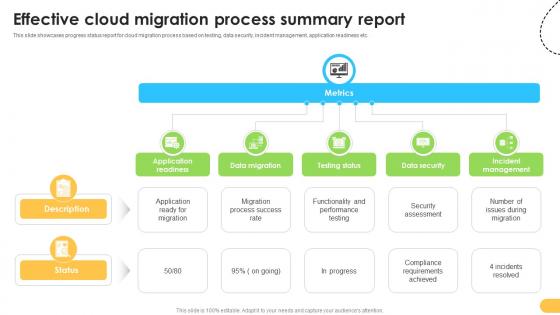
Effective Cloud Migration Process Summary Report Data Migration From On Premises
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Cloud Migration Process Summary Report Data Migration From On Premises and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc.
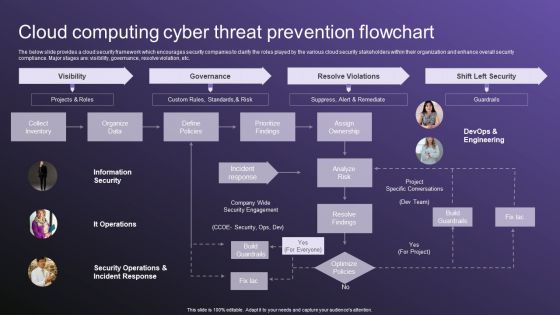
Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
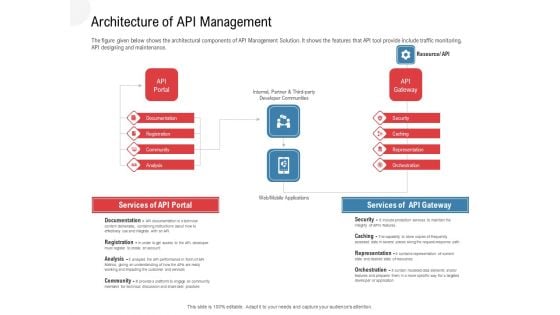
API Outline Architecture Of API Management Ppt Summary Format PDF
The figure given below shows the architectural components of API Management Solution. It shows the features that API tool provide include traffic monitoring, API designing and maintenance. Deliver an awe-inspiring pitch with this creative api outline architecture of api management ppt summary format pdf bundle. Topics like documentation, registration, analysis, community, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
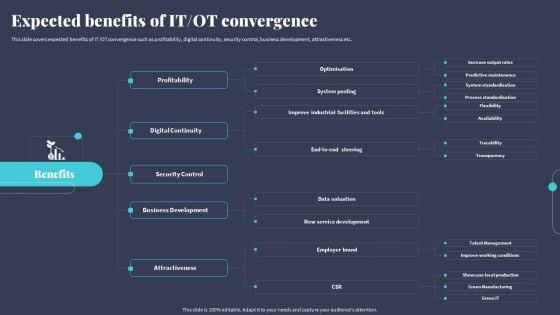
Tactics For Incorporating OT And IT With The Latest PI System Expected Benefits Of IT OT Convergence Inspiration PDF
This slide covers expected benefits of IT OT convergence such as profitability, digital continuity, security control, business development, attractiveness etc. Present like a pro with Tactics For Incorporating OT And IT With The Latest PI System Expected Benefits Of IT OT Convergence Inspiration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
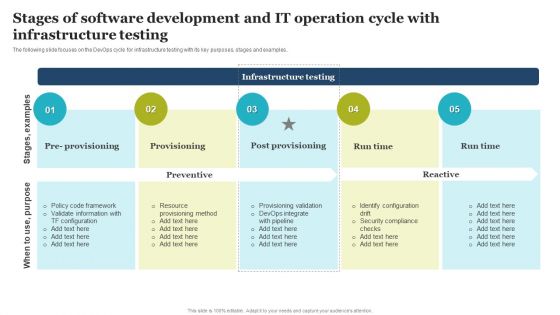
Stages Of Software Development And IT Operation Cycle With Infrastructure Testing Clipart PDF
The following slide focuses on the DevOps cycle for infrastructure testing with its key purposes, stages and examples. Pitch your topic with ease and precision using this Stages Of Software Development And IT Operation Cycle With Infrastructure Testing Clipart PDF. This layout presents information on Information, Security Compliance, Devops Integrate. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
E Business And Cyber Risk Management Table Of Contents Elements PDF
Deliver and pitch your topic in the best possible manner with this e business and cyber risk management table of contents elements pdf. Use them to share invaluable insights on global market, requirements, security, technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































