Safety Improvement Plan

Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide
This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc. Find highly impressive Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc.

Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Slidegeeks is here to make your presentations a breeze with Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
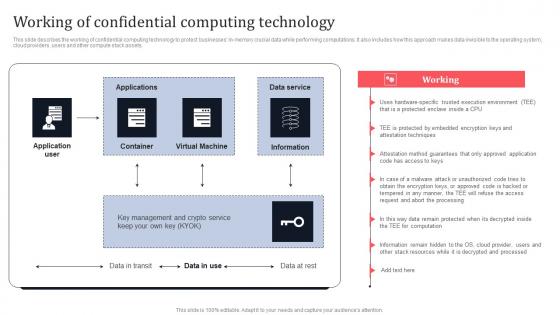
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
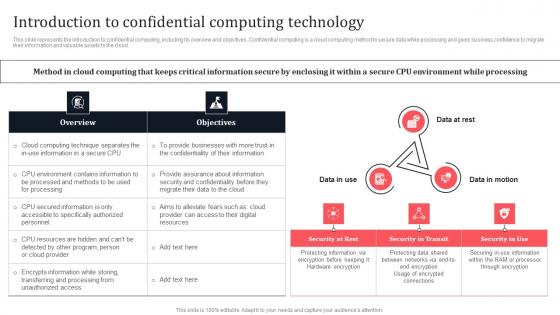
Introduction To Confidential Computing Technology Secure Multi Party Download Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Do you know about Slidesgeeks Introduction To Confidential Computing Technology Secure Multi Party Download Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
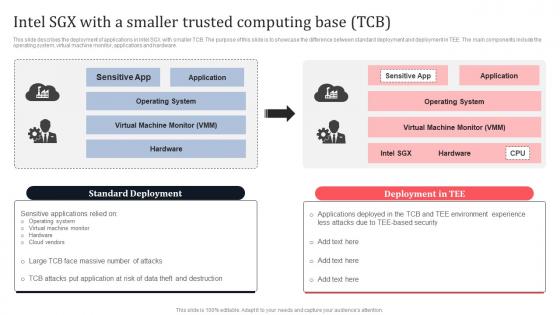
Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Take your projects to the next level with our ultimate collection of Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
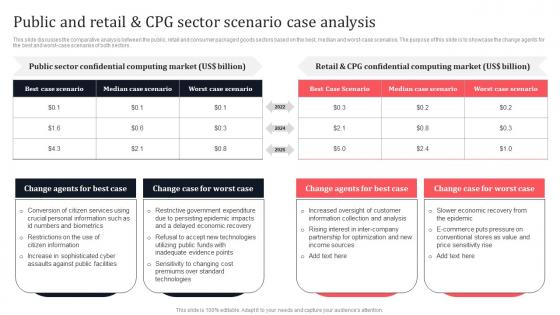
Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Slidegeeks is here to make your presentations a breeze with Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.

SIEM Services Benefits Of Choosing Our Company For SIEM Services Ppt Layouts Slide Download PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a siem services benefits of choosing our company for siem services ppt layouts slide download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, reduction, prevention of potential security, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Management Process Control Ppt Slides
This is a information management process control ppt slide. This is a four stage process. The stages in this process are process improvement, facilities and safety, customer service, documents and records.
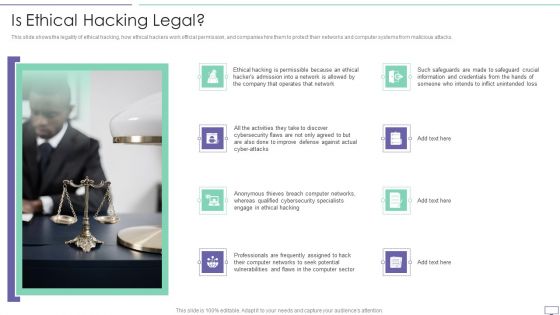
IT Security Hacker Is Ethical Hacking Legal Rules PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.Presenting IT Security Hacker Is Ethical Hacking Legal Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Improve Defense, Anonymous Thieves, Qualified Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
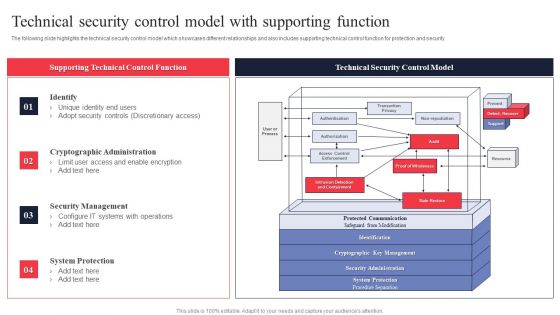
IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
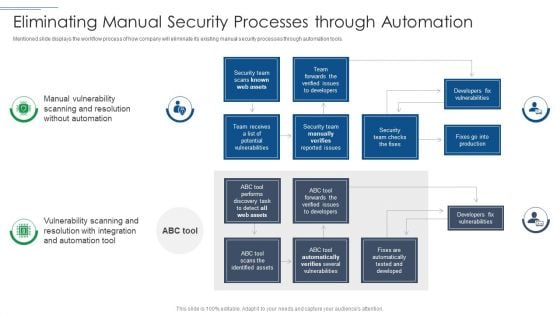
IT Security Risk Management Approach Introduction Eliminating Manual Security Processes Through Automation Guidelines PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Eliminating Manual Security Processes Through Automation Guidelines PDF bundle. Topics like Security Team, Developers Fix Vulnerabilities, Security Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
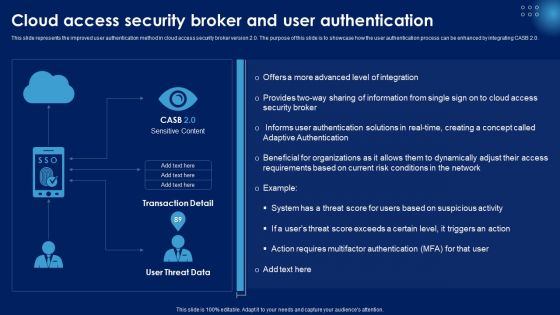
Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Motivators And Hygiene Factors For Human Capital Optimization Icons PDF
Pitch your topic with ease and precision using this motivators and hygiene factors for human capital optimization icons pdf. This layout presents information on growth, security, remuneration. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
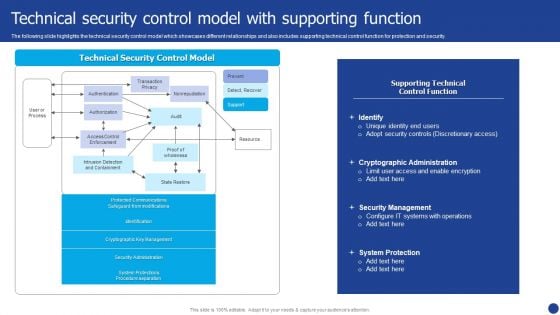
Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
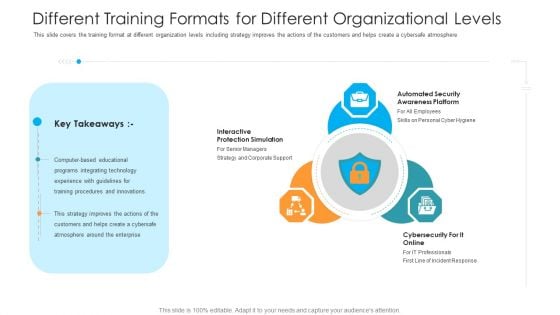
Different Training Formats For Different Organizational Levels Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. This is a different training formats for different organizational levels hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interactive protection simulation, automated security awareness platform, cybersecurity for it online. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
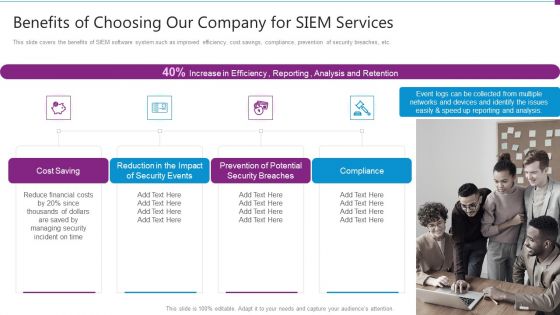
Security Information And Event Management Strategies For Financial Audit And Compliance Benefits Of Choosing Our Company Topics PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a security information and event management strategies for financial audit and compliance benefits of choosing our company topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, security breaches, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Quality Assurance Templates Set 3 Demonstration PDF
Presenting table of contents for quality assurance templates set 3 demonstration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like reliability, risk management, safety, stakeholders, software quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
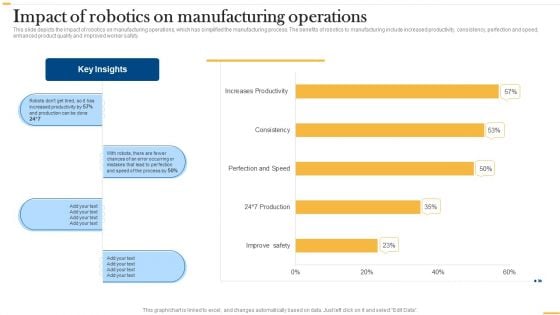
Deploying AI To Enhance Impact Of Robotics On Manufacturing Operations Sample PDF
This slide depicts the impact of robotics on manufacturing operations, which has simplified the manufacturing process. The benefits of robotics to manufacturing include increased productivity, consistency, perfection and speed, enhanced product quality and improved worker safety. Are you searching for a Deploying AI To Enhance Impact Of Robotics On Manufacturing Operations Sample PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying AI To Enhance Impact Of Robotics On Manufacturing Operations Sample PDF from Slidegeeks today.

Web App Firewall Services IT Features Of WAF Centralized Management System Designs PDF
This slide depicts the centralized management system feature of WAF and how it allows organizations to manage different web appliances from a single platform. Deliver an awe inspiring pitch with this creative web app firewall services it features of waf centralized management system designs pdf bundle. Topics like security, organization, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Desktop Security Management What Is Computer Security And How Does It Work Template PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Deliver an awe inspiring pitch with this creative desktop security management what is computer security and how does it work template pdf bundle. Topics like networks, systems, protect data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
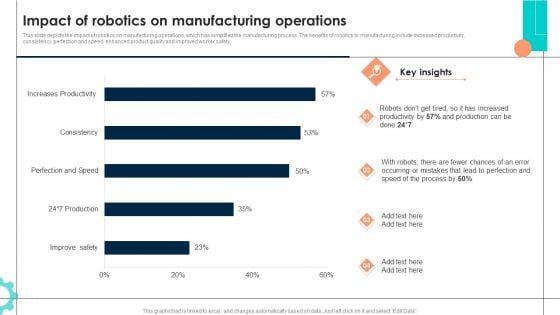
Intelligent Manufacturing Impact Of Robotics On Manufacturing Operations Topics PDF
This slide depicts the impact of robotics on manufacturing operations, which has simplified the manufacturing process. The benefits of robotics to manufacturing include increased productivity, consistency, perfection and speed, enhanced product quality and improved worker safety. Are you searching for a Intelligent Manufacturing Impact Of Robotics On Manufacturing Operations Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Intelligent Manufacturing Impact Of Robotics On Manufacturing Operations Topics PDF from Slidegeeks today.
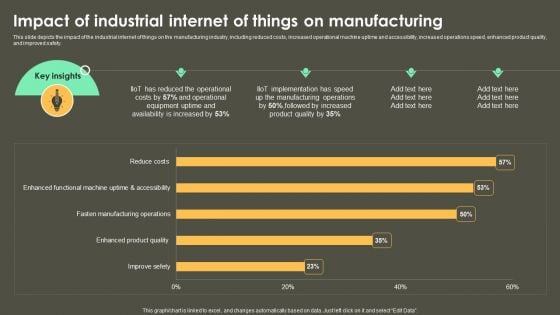
Iot Integration In Manufacturing Impact Of Industrial Internet Of Things On Manufacturing Structure PDF
This slide depicts the impact of the industrial internet of things on the manufacturing industry, including reduced costs, increased operational machine uptime and accessibility, increased operations speed, enhanced product quality, and improved safety. Are you searching for a Iot Integration In Manufacturing Impact Of Industrial Internet Of Things On Manufacturing Structure PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Iot Integration In Manufacturing Impact Of Industrial Internet Of Things On Manufacturing Structure PDF from Slidegeeks today.
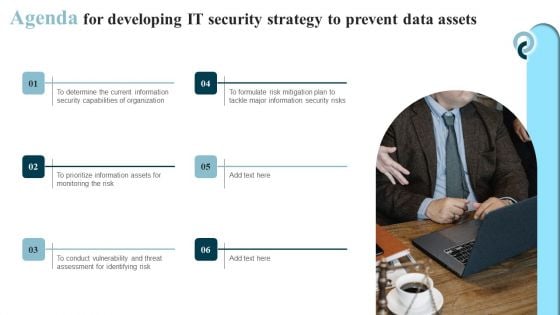
Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Icons Slide Development And Integration Of Cyber Security Incident Administration Slides PDF
Introducing our well designed Icons Slide Development And Integration Of Cyber Security Incident Administration Slides PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
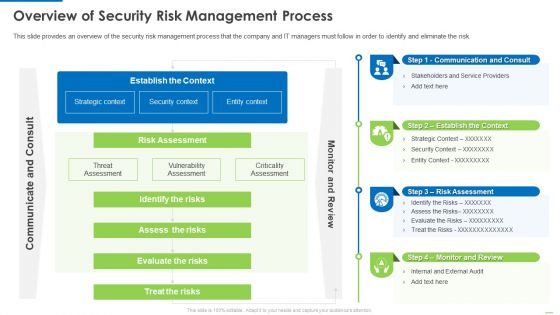
Overview Of Security Risk Management Process Demonstration PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver and pitch your topic in the best possible manner with this Overview of security risk management process demonstration pdf. Use them to share invaluable insights on identify the risks, assess the risks, evaluate the risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Portfolio Evaluation Template 1 Ppt PowerPoint Presentation Backgrounds
This is a portfolio evaluation template 1 ppt powerpoint presentation backgrounds. This is a five stage process. The stages in this process are annualized gross return, annualized standard deviation, portfolio, equity, dollar corporate debt securities, corporate debt securities.
Icons Slide For CYBER Security Breache Response Strategy Pictures PDF
Introducing our well designed Icons Slide For CYBER Security Breache Response Strategy Pictures PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide Security Software Company Investor Funding Elevator Pitch Deck Elements PDF
Presenting our innovatively structured Icons Slide Security Software Company Investor Funding Elevator Pitch Deck Elements PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
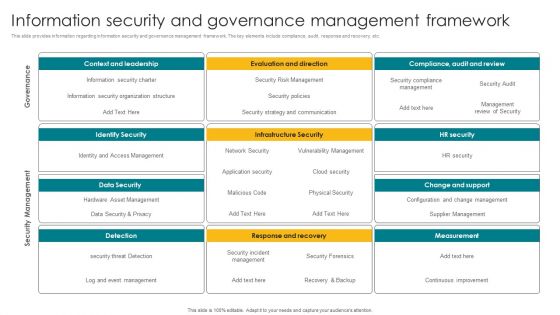
Information Security And Governance Management Framework Summary PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Security And Governance Management Framework Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Security And Governance Management Framework Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
icons slide for cyber security administration in organization summary pdf
Presenting our innovatively structured icons slide for cyber security administration in organization summary pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
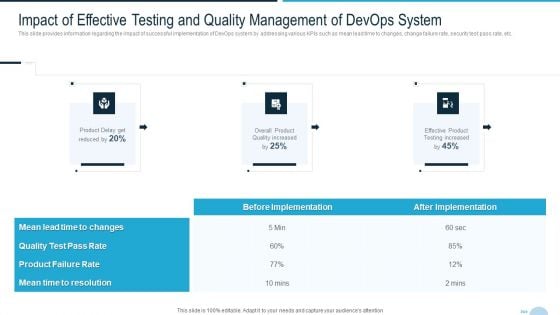
Development And Operations Quality Assurance And Validation IT Impact Of Effective Testing And Quality Template PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. Deliver and pitch your topic in the best possible manner with this development and operations quality assurance and validation it impact of effective testing and quality template pdf Use them to share invaluable insights on product failure, quality test pass, mean time to resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
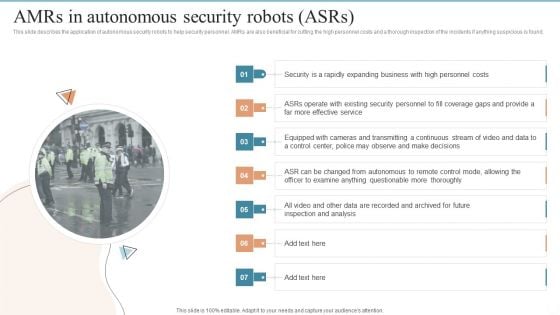
Amrs In Autonomous Security Robots Asrs Ppt PowerPoint Presentation File Outline PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Amrs In Autonomous Security Robots Asrs Ppt PowerPoint Presentation File Outline PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
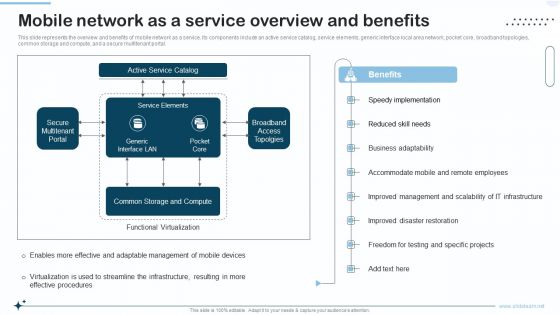
Naas Integrated Solution IT Mobile Network As A Service Overview And Benefits Formats PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. Deliver and pitch your topic in the best possible manner with this Naas Integrated Solution IT Mobile Network As A Service Overview And Benefits Formats PDF. Use them to share invaluable insights on Management, Employees, Implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
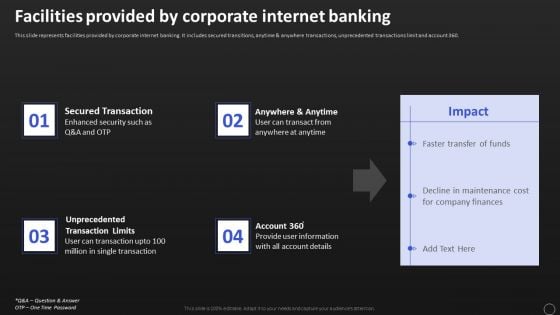
Net Banking Channel And Service Management Facilities Provided By Corporate Internet Banking Diagrams PDF
This slide represents facilities provided by corporate internet banking. It includes secured transitions, anytime and anywhere transactions, unprecedented transactions limit and account 360. Find a pre designed and impeccable Net Banking Channel And Service Management Facilities Provided By Corporate Internet Banking Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for. Download the template from Slidegeeks today and give a unique touch to your presentation.
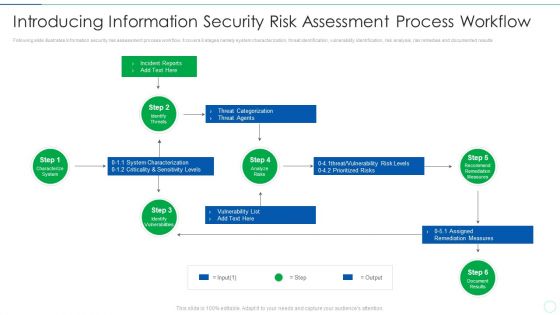
Effective IT Risk Management Process Introducing Information Security Risk Designs PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an awe inspiring pitch with this creative effective it risk management process information security risk assessment formats pdf bundle. Topics like system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
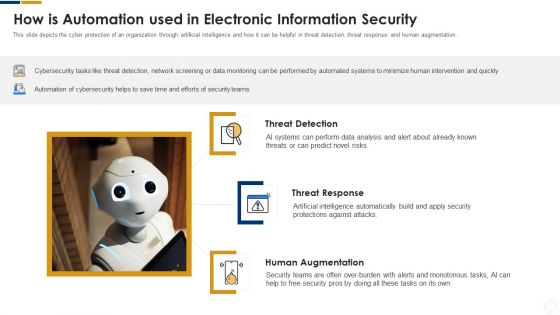
Cybersecurity How Is Automation Used In Electronic Information Security Ppt Ideas Elements PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Deliver an awe inspiring pitch with this creative cybersecurity how is automation used in electronic information security ppt ideas elements pdf bundle. Topics like threat detection, threat response, human augmentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of IoT And Smart Technology Impact Of IoT Technology On Education IoT SS V
Following slide showcases positive impact of IoT based devices deployment on education sector. It includes pointers such as enhance accessibility, campus security, cost efficient, energy and resource management. Welcome to our selection of the Impact Of IoT And Smart Technology Impact Of IoT Technology On Education IoT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. Following slide showcases positive impact of IoT based devices deployment on education sector. It includes pointers such as enhance accessibility, campus security, cost efficient, energy and resource management.
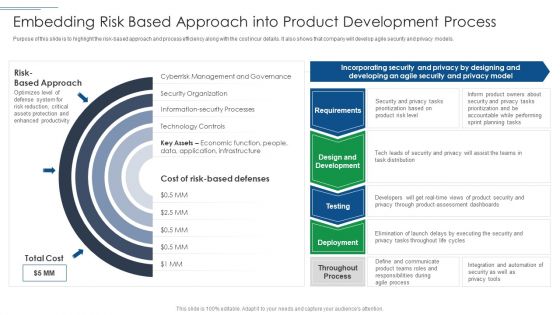
IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF bundle. Topics like Technology Controls, Information Security Processes, Security Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
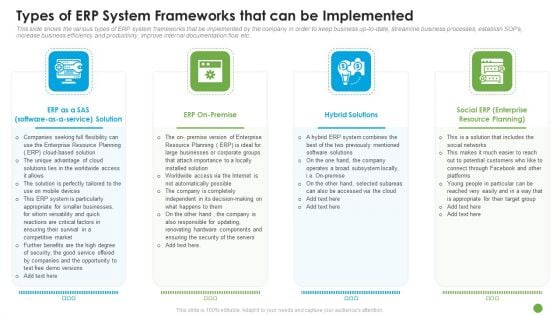
Types Of ERP System Frameworks That Can Be Implemented Ppt Slides Example PDF
This slide shows the various types of ERP system frameworks that be implemented by the company in order to keep business up to date, streamline business processes, establish SOPs, increase business efficiency and productivity, improve internal documentation flow etc. This is a types of erp system frameworks that can be implemented ppt slides example pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like competitive market, opportunity, resource planning, enterprise, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For Techniques And Strategies To Reduce Security Management Risks Designs PDF
Introducing our well designed icons slide for techniques and strategies to reduce security management risks designs pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
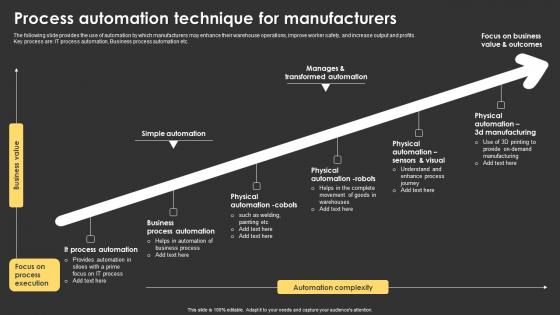
Process Automation Technique For Manufacturers Diagrams Pdf
The following slide provides the use of automation by which manufacturers may enhance their warehouse operations, improve worker safety, and increase output and profits. Key process are IT process automation, Business process automation etc. Pitch your topic with ease and precision using this Process Automation Technique For Manufacturers Diagrams Pdf. This layout presents information on Process Automation, Business Process Automation, Physical Automation Robots. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide provides the use of automation by which manufacturers may enhance their warehouse operations, improve worker safety, and increase output and profits. Key process are IT process automation, Business process automation etc.
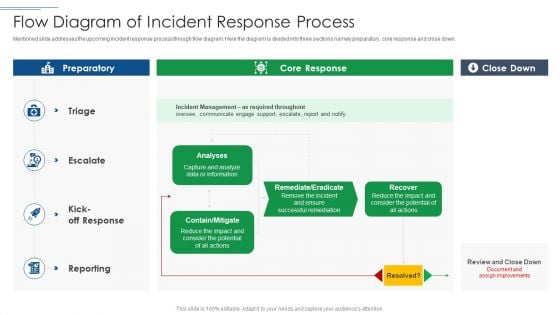
IT Security Risk Management Approach Introduction Flow Diagram Of Incident Response Process Demonstration PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Flow Diagram Of Incident Response Process Demonstration PDF bundle. Topics like Incident Management, Potential can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
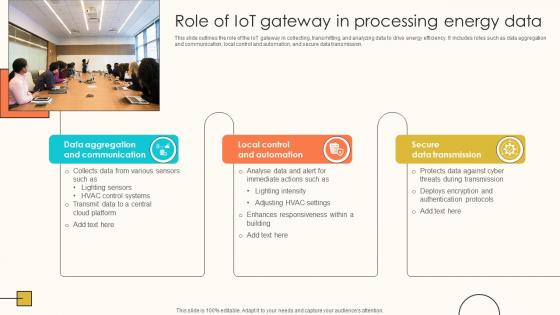
Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V
This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission. Do you know about Slidesgeeks Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission.

Business Reasons For Executing Identify And Access Management Technique Mockup PDF
This slide shows major reasons to execute IAM strategy in organization to ease complexity of management and reducing IT costs. It include reasons such as improved security system, simplifies information sharing and usability sue , etc. Persuade your audience using this Business Reasons For Executing Identify And Access Management Technique Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security System, Information Sharing, Usability Ease. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Securing Memcached On Centos And Fedora Servers Ppt Infographics Show PDF
Deliver an awe inspiring pitch with this creative securing memcached on centos and fedora servers ppt infographics show pdf bundle. Topics like system, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For Securing Market Leadership Through Competitive Excellence Designs PDF
Help your business to create an attention-grabbing presentation using our Icons Slide For Securing Market Leadership Through Competitive Excellence Designs PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide For Securing Market Leadership Through Competitive Excellence Designs PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
Project Risk Management Tracking Complete Guide On How To Mitigate Professional Pdf
This slide provides an overview of project management software used to monitor and track risks. It includes reviews, trials, pricing and features which are automatic risk alerts,a secure database, details reporting and customizable parameters. Welcome to our selection of the Project Risk Management Tracking Complete Guide On How To Mitigate Professional Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today. This slide provides an overview of project management software used to monitor and track risks. It includes reviews, trials, pricing and features which are automatic risk alerts,a secure database, details reporting and customizable parameters.
Icons Slide For SDN Security Architecture Ppt PowerPoint Presentation File Model PDF
Introducing our well designed Icons Slide For SDN Security Architecture Ppt PowerPoint Presentation File Model PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Mobile Banking For Convenient And Secure Online Payments Ppt Styles Format Ideas PDF
Presenting our innovatively structured Icons Slide For Mobile Banking For Convenient And Secure Online Payments Ppt Styles Format Ideas PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
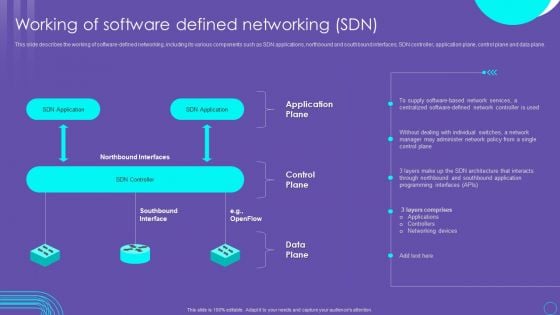
SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF
This slide describes the working of software defined networking, including its various components such as SDN applications, northbound and southbound interfaces, SDN controller, application plane, control plane and data plane. Slidegeeks is here to make your presentations a breeze with SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
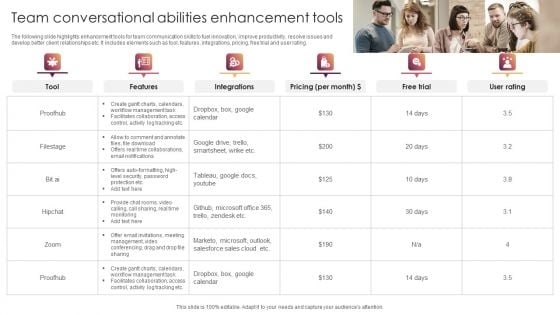
Team Conversational Abilities Enhancement Tools Demonstration PDF
The following slide highlights enhancement tools for team communication skills to fuel innovation, improve productivity, resolve issues and develop better client relationships etc. It includes elements such as tool, features, integrations, pricing, free trial and user rating. Presenting Team Conversational Abilities Enhancement Tools Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security, Password, Management, Salesforce Sales. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
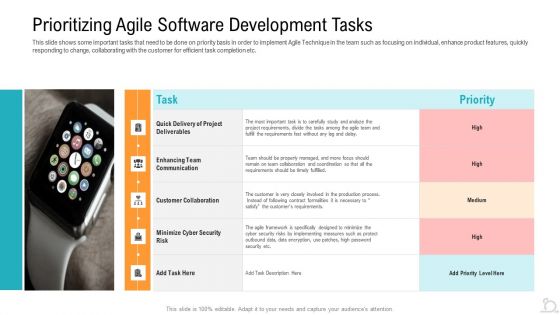
Prioritizing Agile Software Development Tasks Clipart PDF
This slide shows some important tasks that need to be done on priority basis in order to implement Agile Technique in the team such as focusing on individual, enhance product features, quickly responding to change, collaborating with the customer for efficient task completion etc.Deliver an awe inspiring pitch with this creative prioritizing agile software development tasks clipart pdf bundle. Topics like enhancing team communication, customer collaboration, minimize cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Construction Project Playbook Contd Ppt Outline Aids PDF
This is a table of contents for construction project playbook contd ppt outline aids pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring workforce safety, construction team, cost management, dashboard. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Tracking Risk Tracker Matrix Themes PDF
The following slide depicts the risk assessment matrix of project tracking to manage uncertain activities and improve decision making. It includes activities such as assessment, configuration, advancement, security check and dispose etc. Persuade your audience using this Project Tracking Risk Tracker Matrix Themes PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Project Tracking Risk, Tracker Matrix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Advantages Of Integrating IoT Banking Future With IoT Ppt Powerpoint IoT SS V
Following slide showcases various benefits of utilizing IoT devices to assure effective and smart banking services increasing customer satisfaction. It covers elements such as security, real time monitoring, better analytics and others. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Key Advantages Of Integrating IoT Banking Future With IoT Ppt Powerpoint IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Key Advantages Of Integrating IoT Banking Future With IoT Ppt Powerpoint IoT SS V Following slide showcases various benefits of utilizing IoT devices to assure effective and smart banking services increasing customer satisfaction. It covers elements such as security, real time monitoring, better analytics and others.
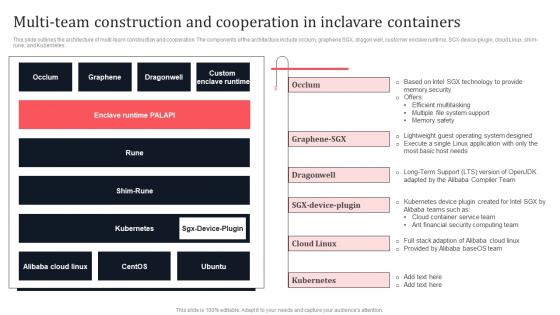
Multi Team Construction And Cooperation In Inclavare Containers Secure Multi Party Pictures Pdf
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Boost your pitch with our creative Multi Team Construction And Cooperation In Inclavare Containers Secure Multi Party Pictures Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.

Impact Of Automated Issue Escalation Process Graphics PDF
The following slide formulates the results of automated incident escalation process. It includes improved cross functional communication, reduced threat for security teams, limit the disclosure of fake alerts, increased response efficiency etc. Persuade your audience using this Impact Of Automated Issue Escalation Process Graphics PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Of Automated, Issue Escalation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
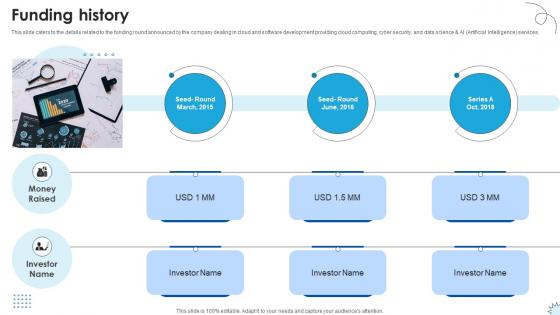
Funding History Technology Solutions Provider Investor Funding Elevator Pitch Deck
This slide caters to the details related to the funding round announced by the company dealing in cloud and software development providing cloud computing, cyber security, and data science and AI Artificial Intelligence services. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Funding History Technology Solutions Provider Investor Funding Elevator Pitch Deck. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Funding History Technology Solutions Provider Investor Funding Elevator Pitch Deck today and make your presentation stand out from the rest This slide caters to the details related to the funding round announced by the company dealing in cloud and software development providing cloud computing, cyber security, and data science and AI Artificial Intelligence services.
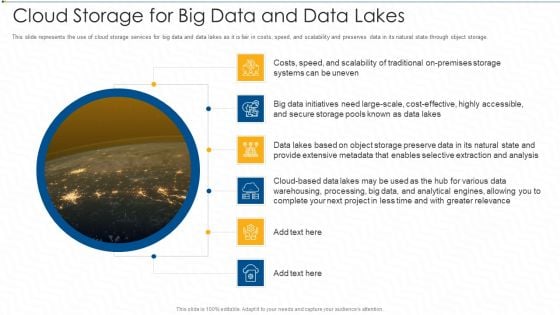
Cloud Storage For Big Data And Data Lakes Ppt Model Outfit PDF
This slide represents the use of cloud storage services for big data and data lakes as it is fair in costs, speed, and scalability and preserves data in its natural state through object storage. Deliver an awe inspiring pitch with this creative cloud storage for big data and data lakes ppt model outfit pdf bundle. Topics like analysis, systems, secure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































