Safety Improvement Plan
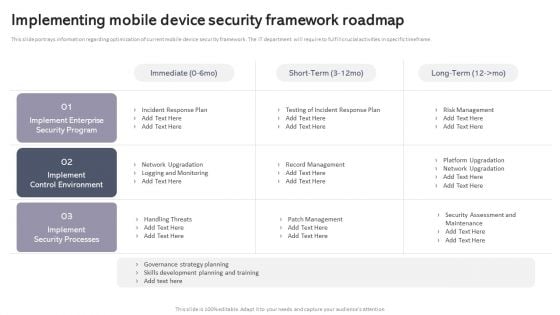
Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Explore a selection of the finest Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

CIO Role In Digital Evolution Basic IT Professional Skills Required For Digital Transformation Microsoft PDF
This slide shows the major skills that are possessed by an IT professional such as Machine Learning, Data Analysis, DevOps, Mobility Management, Digital Marketing, Data and Digital Security, Digital Literacy etc. Presenting CIO Role In Digital Evolution Basic IT Professional Skills Required For Digital Transformation Microsoft PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Digital Literacy, Data Analysis, Machine Learning. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
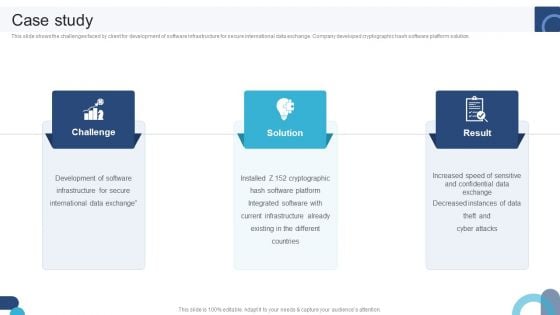
Digital Application Software Development Business Profile Case Study Ideas PDF
This slide shows the challenges faced by client for development of software infrastructure for secure international data exchange. Company developed cryptographic hash software platform solution. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Digital Application Software Development Business Profile Case Study Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Business Strategy Marketing PowerPoint Templates And PowerPoint Themes 1112
We present our Business Strategy Marketing PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, Discuss each one and slowly but surely move up the pyramid narrowing down to the best and most success oriented project. Use our Success PowerPoint Templates because, Profit fairly earned is what you believe in. Use our Business PowerPoint Templates because,Marketing Strategy Business Template:- Maximising sales of your product is the intended destination. Use our Finance PowerPoint Templates because, Sales Template:- Generation of sales is the core of any business. Use our Marketing PowerPoint Templates because,There are so many different pieces to the puzzle.Use these PowerPoint slides for presentations relating to Strategy gold key, security, success, business, finance, marketing. The prominent colors used in the PowerPoint template are Orange, Yellow, Black Represent yourself with our Business Strategy Marketing PowerPoint Templates And PowerPoint Themes 1112. Download without worries with our money back guaranteee.

Agenda Of Risk Management For Organization Essential Assets Elements PDF
This is a agenda of risk management for organization essential assets elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital assets, people, financial assets, physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
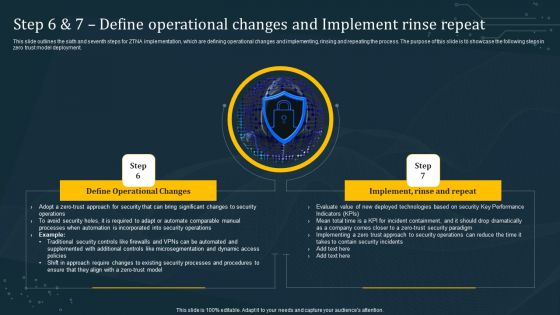
Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Find highly impressive Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
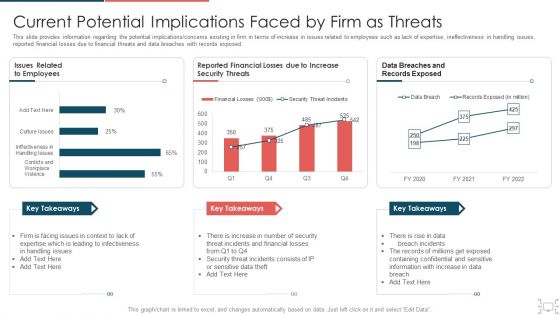
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
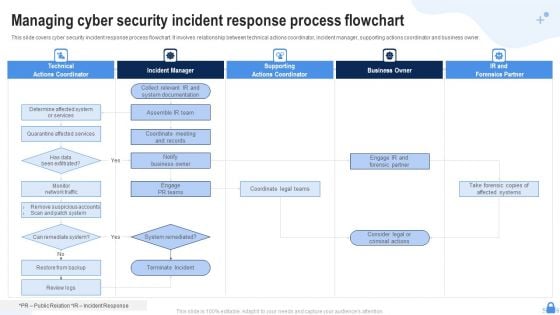
Managing Cyber Security Incident Response Process Flowchart Ppt Templates PDF
This slide covers cyber security incident response process flowchart. It involves relationship between technical actions coordinator, incident manager, supporting actions coordinator and business owner. Presenting Managing Cyber Security Incident Response Process Flowchart Ppt Templates PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Technical Actions Coordinator, Incident Manager, Supporting Actions Coordinator. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
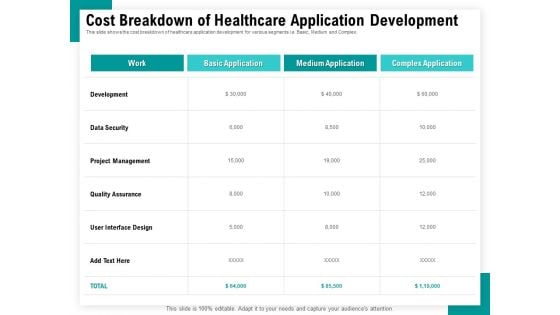
Android Framework For Apps Development And Deployment Cost Breakdown Of Healthcare Application Development Ideas PDF
Presenting this set of slides with name android framework for apps development and deployment cost breakdown of healthcare application development ideas pdf. The topics discussed in these slides are development, data security, project management, quality assurance, work, basic application, medium application, complex application. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF
Explore a selection of the finest Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
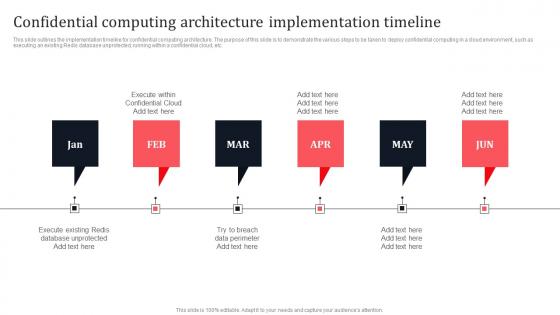
Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Find highly impressive Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
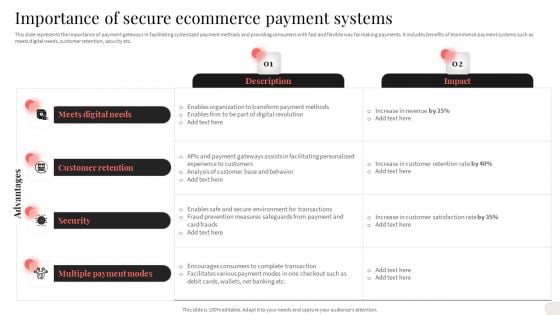
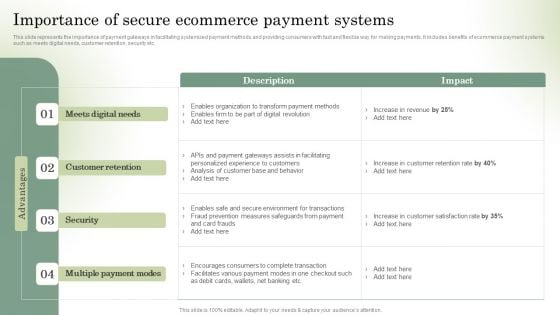
Analyzing And Implementing Effective CMS Importance Of Secure Ecommerce Payment Systems Portrait PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. This Analyzing And Implementing Effective CMS Importance Of Secure Ecommerce Payment Systems Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Analyzing And Implementing Effective CMS Importance Of Secure Ecommerce Payment Systems Portrait PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
Optimizing Online Stores Importance Of Secure Ecommerce Payment Systems Clipart PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. This Optimizing Online Stores Importance Of Secure Ecommerce Payment Systems Clipart PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Optimizing Online Stores Importance Of Secure Ecommerce Payment Systems Clipart PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
Business Security Management 4 Step Workflow Icons PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Persuade your audience using this Business Security Management 4 Step Workflow Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Treat, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
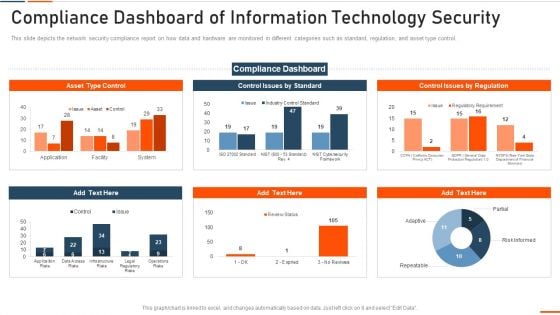
Compliance Dashboard Of Information Technology Security Ppt Inspiration Microsoft PDF
This slide depicts the network security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative compliance dashboard of information technology security ppt inspiration microsoft pdf bundle. Topics like compliance dashboard of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
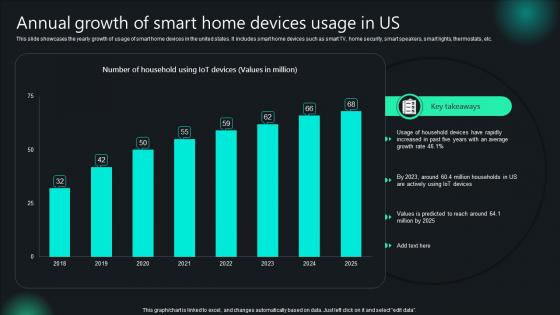
Unlocking Potential IoTs Application Annual Growth Of Smart Home Devices Usage In Us IoT SS V
This slide showcases the yearly growth of usage of smart home devices in the united states. It includes smart home devices such as smart TV, home security, smart speakers, smart lights, thermostats, etc. Slidegeeks is here to make your presentations a breeze with Unlocking Potential IoTs Application Annual Growth Of Smart Home Devices Usage In Us IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the yearly growth of usage of smart home devices in the united states. It includes smart home devices such as smart TV, home security, smart speakers, smart lights, thermostats, etc.

4 Best Practices Of Data Management Ethics In Organizations Ppt Infographics Grid PDF
This slide shows the various data practices that organizations can use in data collection. It includes having clear policies, get employees buy-in, secure IT systems and be transparent. Persuade your audience using this 4 Best Practices Of Data Management Ethics In Organizations Ppt Infographics Grid PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Clear Policies, Get Employees, Buy In, Secure IT Systems, Be Transparent. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
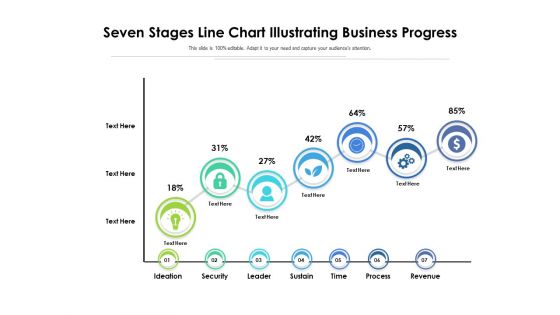
Seven Stages Line Chart Illustrating Business Progress Ppt PowerPoint Presentation Styles Professional PDF
Persuade your audience using this seven stages line chart illustrating business progress ppt powerpoint presentation styles professional pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including ideation, security, leader, sustain, time, process, revenue. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
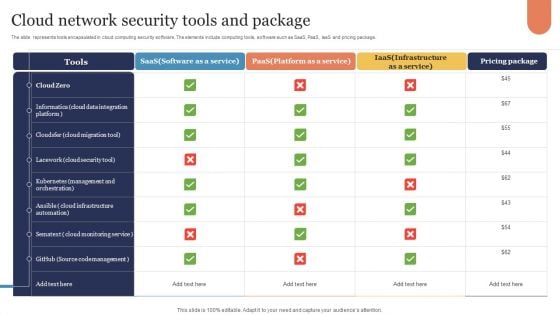
Cloud Network Security Tools And Package Graphics PDF
The slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Showcasing this set of slides titled Cloud Network Security Tools And Package Graphics PDF. The topics addressed in these templates are Saas, Paas, Iaas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
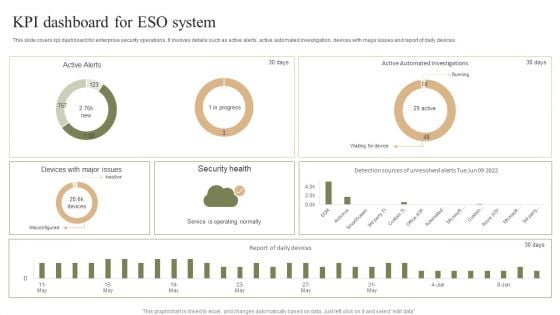
KPI Dashboard For ESO System Ppt PowerPoint Presentation File Template PDF
This slide covers kpi dashboard for enterprise security operations. It involves details such as active alerts, active automated investigation, devices with major issues and report of daily devices. Pitch your topic with ease and precision using this KPI Dashboard For ESO System Ppt PowerPoint Presentation File Template PDF. This layout presents information on Security Health, Misconfigured, Service Operating Normally. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
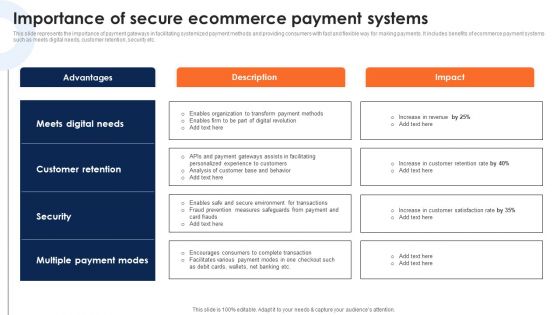
Importance Of Secure Ecommerce Payment Systems Deploying Ecommerce Order Management Software Rules PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc.This modern and well-arranged Importance Of Secure Ecommerce Payment Systems Deploying Ecommerce Order Management Software Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
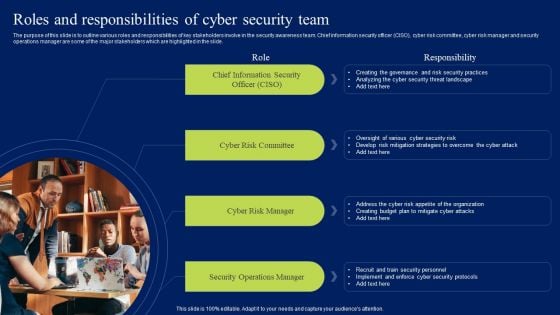
Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
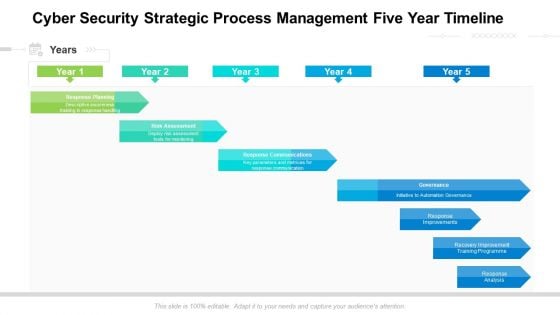
Cyber Security Strategic Process Management Five Year Timeline Inspiration
Presenting our jaw dropping cyber security strategic process management five year timeline inspiration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
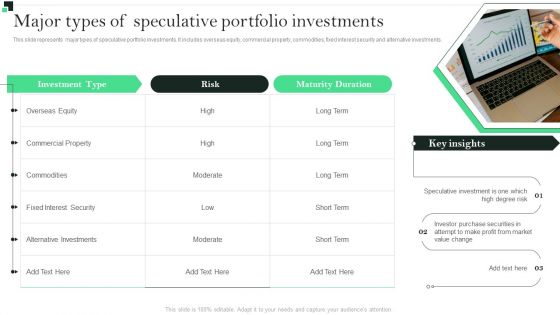
Major Types Of Speculative Portfolio Investments Strategies To Enhance Portfolio Management Portrait PDF
This slide represents major types of speculative portfolio investments. It includes overseas equity, commercial property, commodities, fixed interest security and alternative investments.Create an editable Major Types Of Speculative Portfolio Investments Strategies To Enhance Portfolio Management Portrait PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Major Types Of Speculative Portfolio Investments Strategies To Enhance Portfolio Management Portrait PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
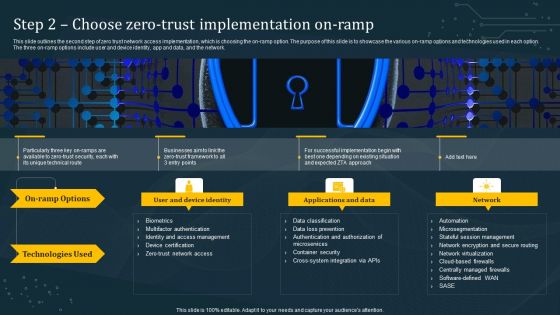
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
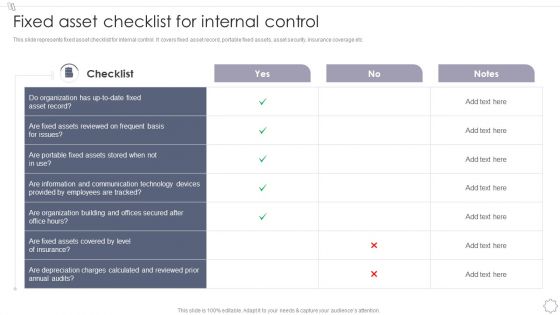
Maintaining And Managing Fixed Assets Fixed Asset Checklist For Internal Control Inspiration PDF
This slide represents fixed asset checklist for internal control. It covers fixed asset record, portable fixed assets, asset security, insurance coverage etc.Deliver and pitch your topic in the best possible manner with this Maintaining And Managing Fixed Assets Fixed Asset Checklist For Internal Control Inspiration PDF. Use them to share invaluable insights on Reviewed Frequent, Communication Technology, Organization Building and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Fixed Asset Checklist For Internal Control Implementing Fixed Asset Tracking Solution Download PDF
This slide represents fixed asset checklist for internal control. It covers fixed asset record, portable fixed assets, asset security, insurance coverage etc.Deliver and pitch your topic in the best possible manner with this Fixed Asset Checklist For Internal Control Implementing Fixed Asset Tracking Solution Download PDF. Use them to share invaluable insights on Information Communication, Organization Building, Calculated Reviewed and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Insurance Agent Protection Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Deliver a dose of enlightenment with our Insurance Agent Protection Security PowerPoint Presentation Slides C. Light up the bulbs in the minds of your audience.

Insurance Agent Protection Security PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Our Insurance Agent Protection Security PowerPoint Presentation Slides Cc can be very enticing. Their blend of colors will captivate anyone.

Insurance Agent Protection Security PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Exert influence with your thoughts. Let our Insurance Agent Protection Security PowerPoint Presentation Slides F be the conduit.

Insurance Agent Protection Security PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Attain victory with our Insurance Agent Protection Security PowerPoint Presentation Slides R. You will come out on top.

Insurance Agent Protection Security PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Stimulate peoples brain with our Insurance Agent Protection Security PowerPoint Presentation Slides S. Just download, type and present.

IT And Cloud Facilities Management Infrastructure Optimization Ppt Inspiration Shapes PDF
Presenting it and cloud facilities management infrastructure optimization ppt inspiration shapes pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like it infrastructure optimization, services, applications, servers and desktops, networks, security, process, business goals. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides
This presentation deck enables you to communicate the message, idea, and proposal to your audience in a clear and effective manner. The slides of this PowerPoint Bundle are professional and visually appealing, engaging your audience and gaining their heartful interest in your content. In addition to its spectacular design, this PPT deck is easy to use and altered to fit the specific needs of the user. All fifty one slides in this set are compatible with multiple data handling and presentation platforms like Google Slides, MS Excel, Tableau, etc., so you can present your information hassle free. Begin your journey to tremendous success using our Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides in many settings, including meetings, pitches, and conference presentations In fact, customer testimonials.
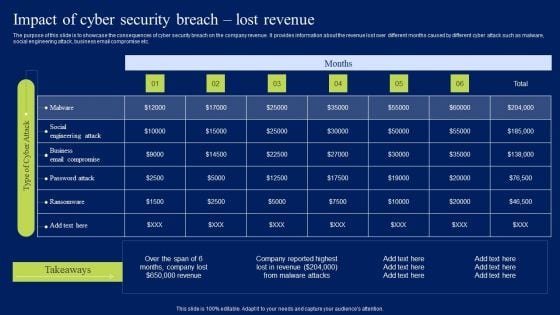
Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. If you are looking for a format to display your unique thoughts, then the professionally designed Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
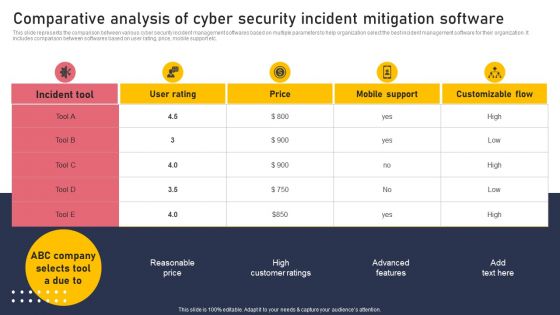
Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Project Management Outline For Schedule Performance Index Using Optimized Tools For Continuous Monitoring Pictures PDF
This slide provides the glimpse about the tools which can be used by the company for regular monitoring and optimization within the company. Deliver and pitch your topic in the best possible manner with this project management outline for schedule performance index using optimized tools for continuous monitoring pictures pdf. Use them to share invaluable insights on monitoring, management, it security, cost, database and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF
This slide showcases assessing impact on major operations and workflows. It provides information about customer understanding, knowledge, data management, financial risk management, customer relationship management, client onboarding, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF.
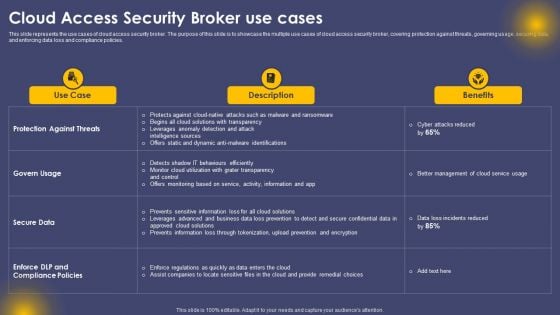
Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Find highly impressive Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
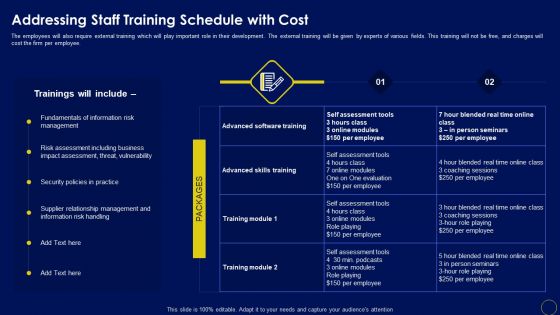
Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
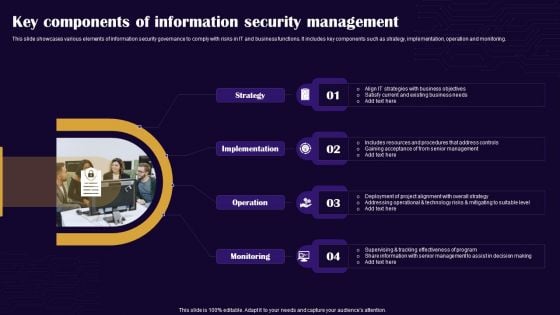
Key Components Of Information Security Management Graphics PDF
This slide showcases various elements of information security governance to comply with risks in IT and business functions. It includes key components such as strategy, implementation, operation and monitoring. Persuade your audience using this Key Components Of Information Security Management Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Implementation, Operation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Stages To Develop Security Analysis Approach Documentation Ppt PowerPoint Presentation File Graphics PDF
Showcasing this set of slides titled stages to develop security analysis approach documentation ppt powerpoint presentation file graphics pdf. The topics addressed in these templates are relevant frameworks, stages to develop security, analysis approach documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
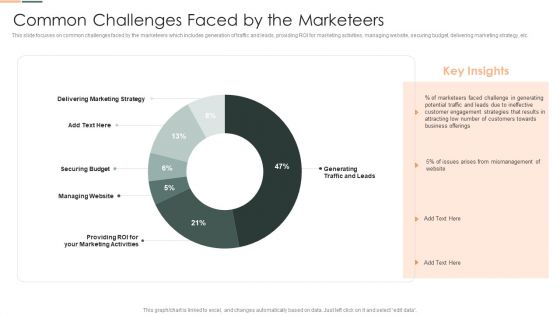
Developing Client Engagement Techniques Common Challenges Faced By The Marketeers Clipart PDF
This slide focuses on common challenges faced by the marketeers which includes generation of traffic and leads, providing ROI for marketing activities, managing website, securing budget, delivering marketing strategy, etc. Deliver an awe inspiring pitch with this creative Developing Client Engagement Techniques Common Challenges Faced By The Marketeers Clipart PDF bundle. Topics like Securing Budget, Managing Website, Delivering Marketing Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
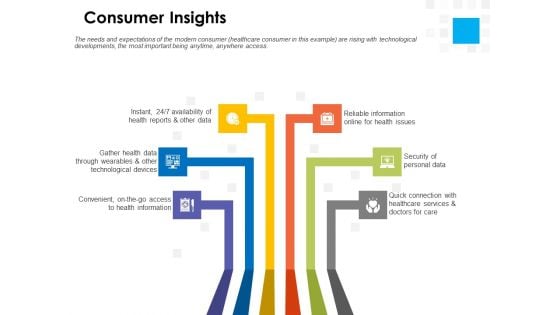
Digital Transformation Strategy Roadmap Consumer Insights Ppt PowerPoint Presentation Layouts Design Inspiration PDF
Presenting this set of slides with name digital transformation strategy roadmap consumer insights ppt powerpoint presentation layouts design inspiration pdf. This is a six stage process. The stages in this process are convenient access, health information, quick connection, healthcare services, security personal data, reliable information online health issues, health reports, gather health data through wearables, technological devices. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Activity Schedule For Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Activity Schedule For Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Activity Schedule For Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.

Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V
This slide provides an overview of the blockchain technology used for remote monotiling. It also includes the benefits that are it allows device communication, enhance security and provides authorization access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V today and make your presentation stand out from the rest This slide provides an overview of the blockchain technology used for remote monotiling. It also includes the benefits that are it allows device communication, enhance security and provides authorization access.
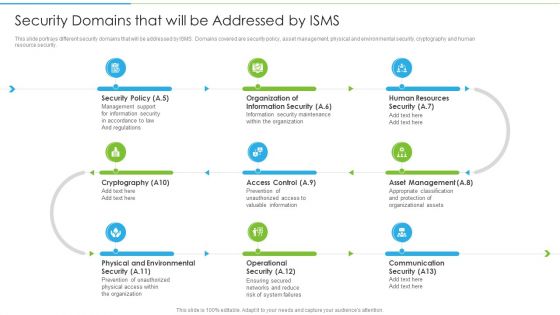
Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policy, Organization Information, Human Resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
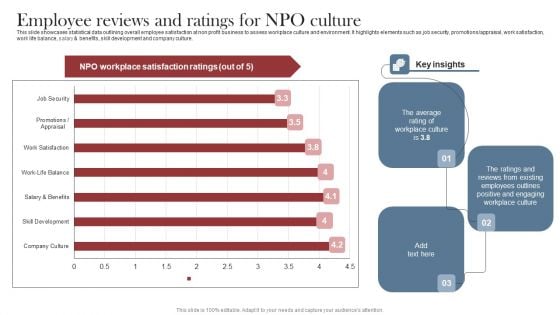
Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF
This slide showcases statistical data outlining overall employee satisfaction at non profit business to assess workplace culture and environment. It highlights elements such as job security, promotions appraisal, work satisfaction, work life balance, salary and benefits, skill development and company culture. This Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
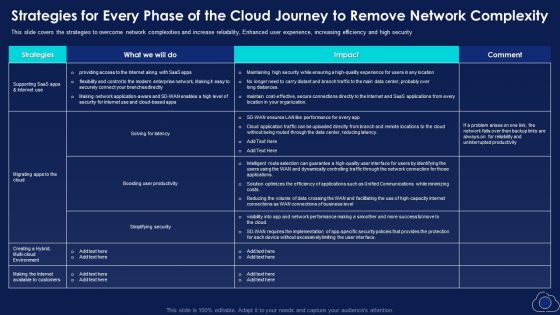
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security. Deliver an awe inspiring pitch with this creative Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF bundle. Topics like Productivity, Simplifying Security, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
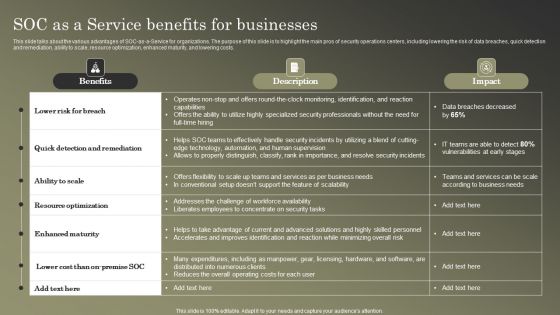
Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF
This slide talks about the various advantages of SOC-as-a-Service for organizations. The purpose of this slide is to highlight the main pros of security operations centers, including lowering the risk of data breaches, quick detection and remediation, ability to scale, resource optimization, enhanced maturity, and lowering costs. Find highly impressive Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Online PR Techniques To Boost Brands Online Visibility Budget Securing Tips For Public Relations Introduction PDF
This slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Make sure to capture your audiences attention in your business displays with our gratis customizable Online PR Techniques To Boost Brands Online Visibility Budget Securing Tips For Public Relations Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
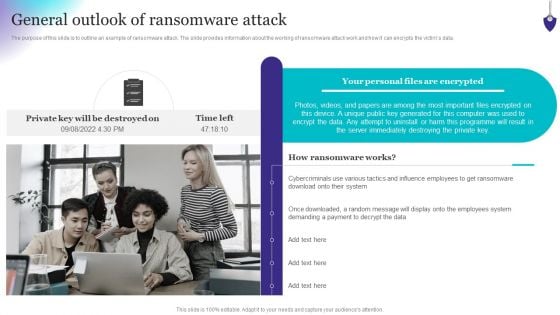
Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
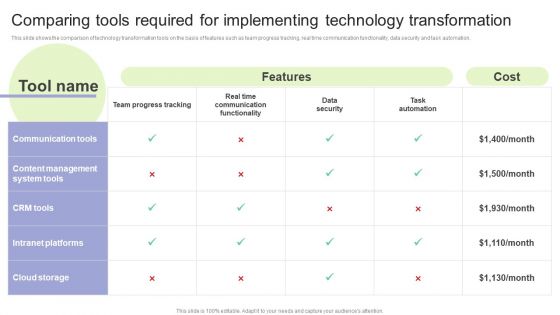
Implementing Change Management Strategy To Transform Business Processes Comparing Tools Required Elements PDF
This slide shows the comparison of technology transformation tools on the basis of features such as team progress tracking, real time communication functionality, data security and task automation. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Change Management Strategy To Transform Business Processes Comparing Tools Required Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Techniques To Monitor Transactions Key Members Of Financial Security Department Themes PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Techniques To Monitor Transactions Key Members Of Financial Security Department Themes PDF from Slidegeeks and deliver a wonderful presentation.
Key Approaches For Successful Implementation Of Smart Production Ppt Icon Portrait PDF
This slide signifies the key strategies for successfully executing smart production. It covers information about approaches like cybersecurity, augmented reality, big data, stimulation, system integration and cloud computing. Presenting Key Approaches For Successful Implementation Of Smart Production Ppt Icon Portrait PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Cyber Security, Augmented Reality, Big Data, Autonomous Robots. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
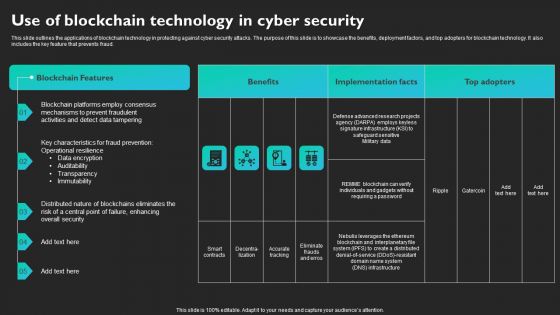
Use Of Blockchain Technology In Cyber Security Slides PDF
This slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Find a pre-designed and impeccable Use Of Blockchain Technology In Cyber Security Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Multi Stages System For Contractor Security Management With Key Tasks Ppt PowerPoint Presentation Styles Tips PDF
Presenting this set of slides with name multi stages system for contractor security management with key tasks ppt powerpoint presentation styles tips pdf. This is a five stage process. The stages in this process are contract definition and award, pre commencement, contract execution and control, hand over and acceptance, close out and review. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
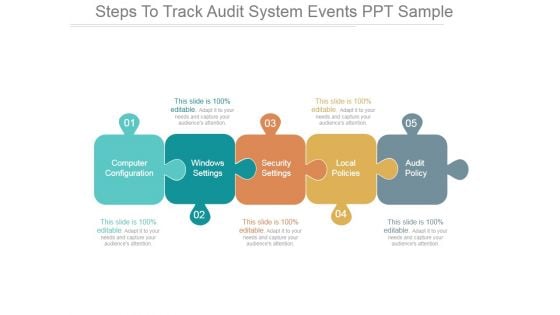
Steps To Track Audit System Events Ppt PowerPoint Presentation Summary
This is a steps to track audit system events ppt powerpoint presentation summary. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.

Investment Service Provider Capital Raising Elevator Details About Emerging Fintech Firm Topics PDF
This slide caters details about emerging fintech firm including details about vision statement, features of FinTech platform with rise in transactional value in FinTech addressing its growth potential. Deliver and pitch your topic in the best possible manner with this investment service provider capital raising elevator details about emerging fintech firm topics pdf. Use them to share invaluable insights on payment gateways, digital banking, asset management, secure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
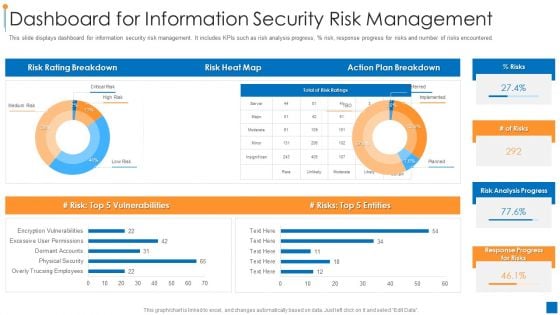
International Organization Standardization 270001 Dashboard For Information Security Risk Management Pictures PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, parcent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative international organization standardization 270001 dashboard for information security risk management pictures pdf bundle. Topics like dashboard for information security risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































