Safety Improvement Plan

Cognitive Visualizations Computing Strategy Current Challenges Faced By Firm While Implementing Rules PDF
This slide provides information regarding the current challenges faced by firm while implementing cognitive computing in terms of budget, lack in pool of talent and expertise and tools.This is a Cognitive Visualizations Computing Strategy Current Challenges Faced By Firm While Implementing Rules PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Talent Expertise, Absence Advanced, Efficient Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF
This slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF
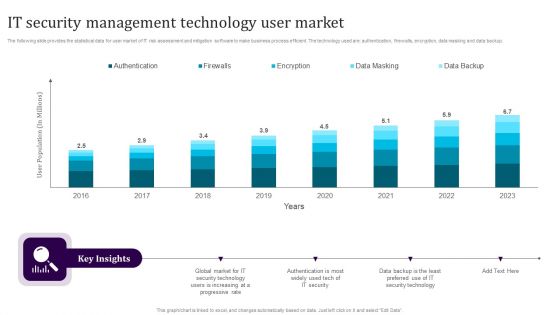
IT Security Management Technology User Market Guidelines PDF
The following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Showcasing this set of slides titled IT Security Management Technology User Market Guidelines PDF. The topics addressed in these templates are Authentication, Firewalls, Encryption, Data Masking, Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
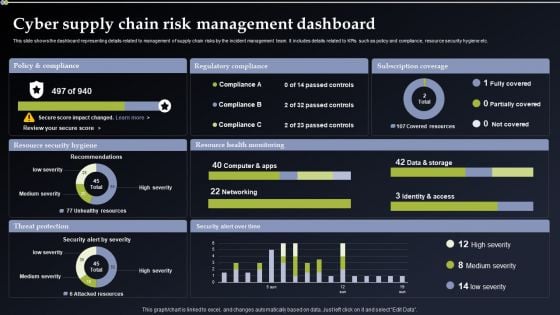
Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF today and make your presentation stand out from the rest.
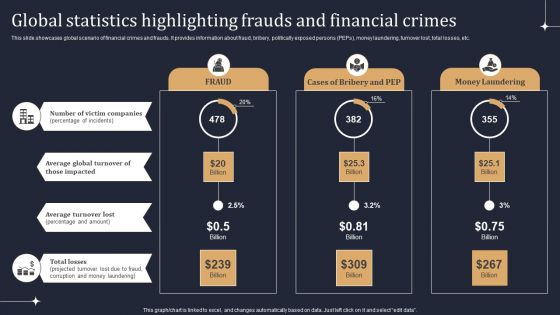
KYC Transaction Monitoring System Business Security Global Statistics Highlighting Frauds Diagrams PDF
This slide showcases global scenario of financial crimes and frauds. It provides information about fraud, bribery, politically exposed persons PEPs, money laundering, turnover lost, total losses, etc. Take your projects to the next level with our ultimate collection of KYC Transaction Monitoring System Business Security Global Statistics Highlighting Frauds Diagrams PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
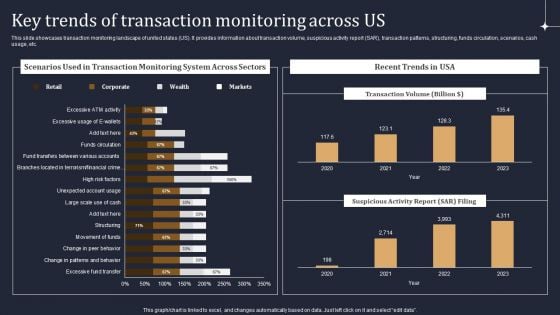
KYC Transaction Monitoring System Business Security Key Trends Of Transaction Monitoring Across Us Diagrams PDF
This slide showcases transaction monitoring landscape of united states US. It provides information about transaction volume, suspicious activity report SAR, transaction patterns, structuring, funds circulation, scenarios, cash usage, etc. There are so many reasons you need a KYC Transaction Monitoring System Business Security Key Trends Of Transaction Monitoring Across Us Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
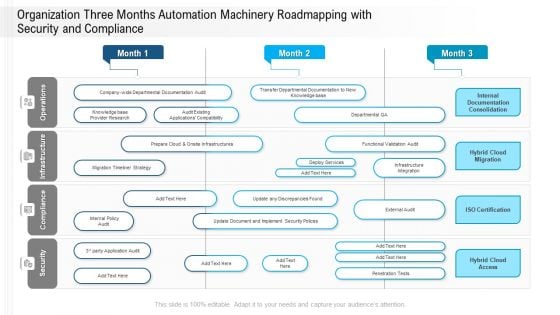
Organization Three Months Automation Machinery Roadmapping With Security And Compliance Rules
Introducing our organization three months automation machinery roadmapping with security and compliance rules. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Risk Based Procedures To IT Security Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Risk Based Procedures To IT Security Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
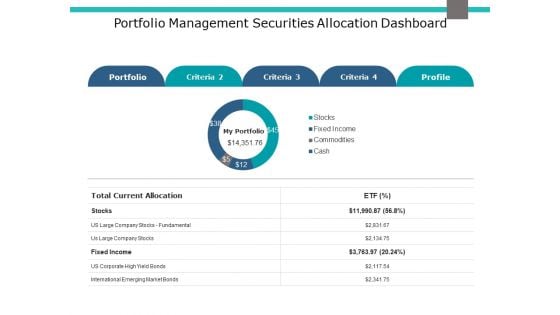
Portfolio Management Securities Allocation Dashboard Ppt PowerPoint Presentation Pictures Objects
This is a portfolio management securities allocation dashboard ppt powerpoint presentation pictures objects. This is a five stage process. The stages in this process are finance, marketing, management, investment.
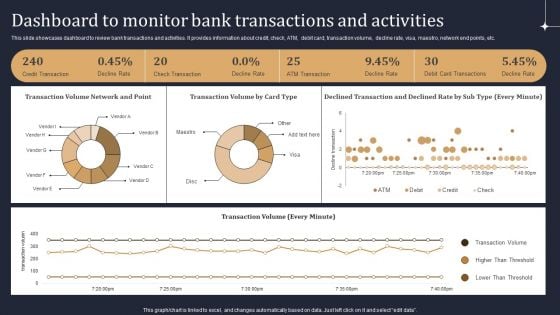
KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF
This slide showcases dashboard to review bank transactions and activities. It provides information about credit, check, ATM, debit card, transaction volume, decline rate, visa, maestro, network end points, etc. This KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
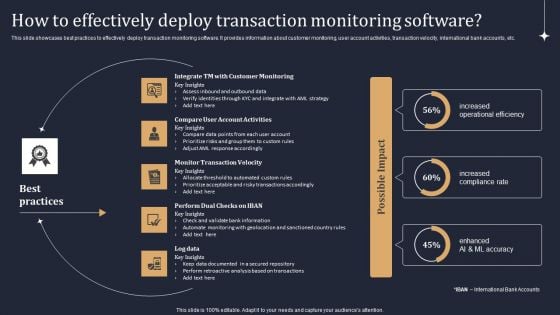
KYC Transaction Monitoring System Business Security How To Effectively Deploy Transaction Brochure PDF
This slide showcases best practices to effectively deploy transaction monitoring software. It provides information about customer monitoring, user account activities, transaction velocity, international bank accounts, etc. Do you know about Slidesgeeks KYC Transaction Monitoring System Business Security How To Effectively Deploy Transaction Brochure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
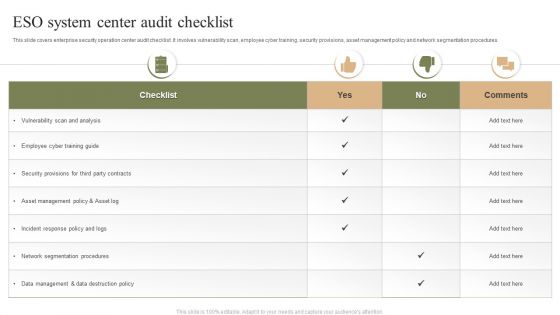
ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Showcasing this set of slides titled ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF. The topics addressed in these templates are Checklist, Employee Cyber, Training Guide. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Implementation Framework Cybersecurity Risk Management Worksheet Ppt Ideas Format PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity risk management worksheet ppt ideas format pdf. The topics discussed in these slides are risk priority, identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
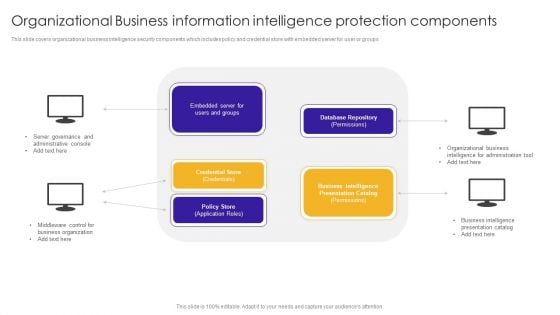
Organizational Business Information Intelligence Protection Components Background PDF
This slide covers organizational business intelligence security components which includes policy and credential store with embedded server for user or groups. Presenting Organizational Business Information Intelligence Protection Components Background PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Administrative Console, Server Governance, Middleware Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
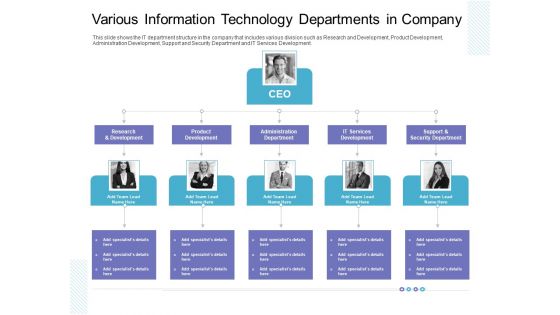
Various Information Technology Departments In Company Slides PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development. This is a various information technology departments in company slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like product development, administration department, research and development, support and security department. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
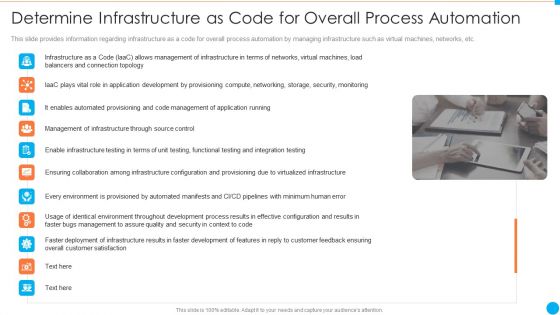
Determine Infrastructure As Code For Overall Process Automation IT Infrastructure By Executing Devops Approach Professional PDF
This slide provides information regarding infrastructure as a code for overall process automation by managing infrastructure such as virtual machines, networks, etc. This is a determine infrastructure as code for overall process automation it infrastructure by executing devops approach professional pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collaboration, infrastructure, management, security, monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Goal Security Analysis And Assessment Ppt PowerPoint Presentation Topics
Presenting this set of slides with name business goal security analysis and assessment ppt powerpoint presentation topics. This is a three stage process. The stages in this process are general outcomes framework, practical level platform, implementation level toolkit and prototypes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc.
Deployment Of Omnichannel Banking Solutions Why Omnichannel Strategy Is Important In Banking Sector Icons PDF
This slide covers top benefits of deploying omnichannel strategies in banking sector to enhance both financial and operational efficiencies. It includes points of importance such as digital operations, new revenue streams, personalized services and enhanced security. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Deployment Of Omnichannel Banking Solutions Why Omnichannel Strategy Is Important In Banking Sector Icons PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf
The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc.
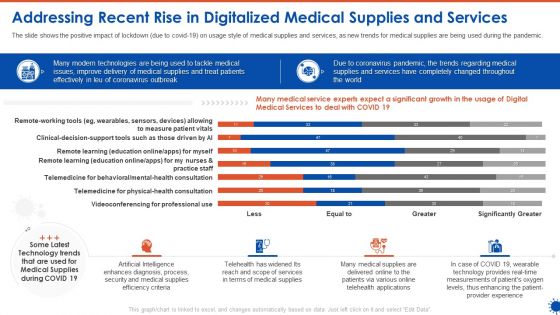
Addressing Recent Rise In Digitalized Medical Supplies And Services Ppt File Mockup PDF
The slide shows the positive impact of lockdown due to covid 19 on usage style of medical supplies and services, as new trends for medical supplies are being used during the pandemic. Deliver an awe inspiring pitch with this creative addressing recent rise in digitalized medical supplies and services ppt file mockup pdf bundle. Topics like process, security, efficiency, measurements, technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Governance Risk And Compliance Implementation Process To Manage Security Risks Pictures PDF
Mentioned slide outlines 3 step process of governance, risk and compliance GRC. Information covered in this slide is related to governance, risk management and compliance which will assist organization to successfully mitigate IT and security risks. Presenting Governance Risk And Compliance Implementation Process To Manage Security Risks Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Governance, Risk Management, Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
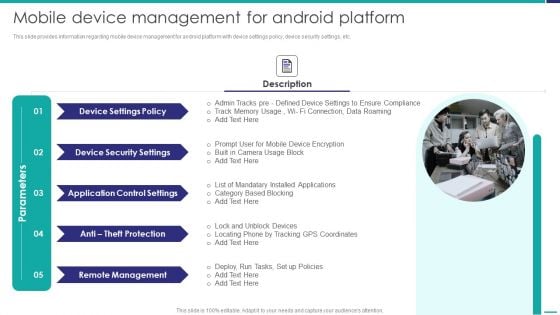
Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Presenting Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Device Security, Application Control, Remote Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
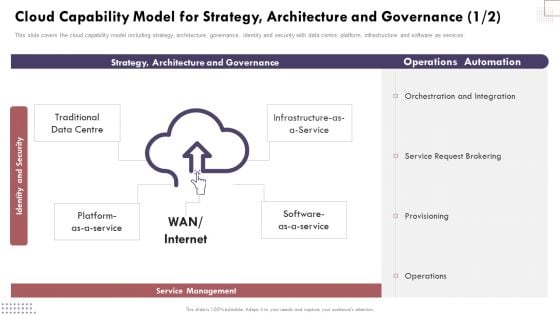
Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. Explore a selection of the finest Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
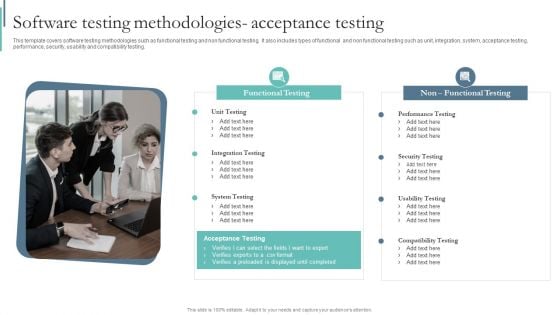
Agile Playbook For Program Designers Software Testing Methodologies Acceptance Testing Ppt Slides Mockup PDF
This template covers software testing methodologies such as functional testing and non functional testing. It also includes types of functional and non functional testing such as unit, integration, system, acceptance testing, performance, security, usability and compatibility testing. This Agile Playbook For Program Designers Software Testing Methodologies Acceptance Testing Ppt Slides Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Agile Playbook For Program Designers Software Testing Methodologies Acceptance Testing Ppt Slides Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Slidegeeks has constructed Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Data Science Learning Benefits In Financial Institution Ppt Icon Slide PDF
This slide contains the benefits that a finance company get from using AI, ML and DL to outsmart the competition and achieve desired business growth. It includes investment predictions, process automation, secure transactions, etc. Presenting Data Science Learning Benefits In Financial Institution Ppt Icon Slide PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Investment Predictions, Process Automation, Secure Transactions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
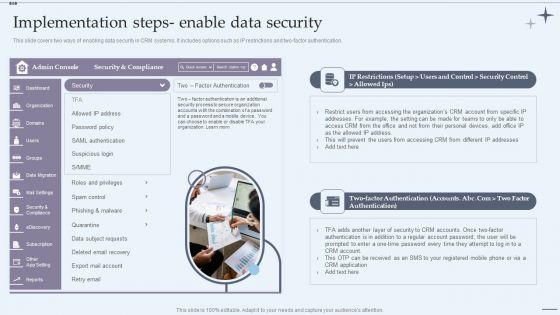
CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Presenting CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Marketing Executive, Marketing Intern, Sales Executive. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112
We present our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because,You too have got the framework of your companys growth in place. Use our Success PowerPoint Templates because, You can Transmit this concern to your staff using our helpful slides. Use our Puzzles or jigsaws PowerPoint Templates because,We all know that alphabetical order is a time honoured concept. Use our Shapes PowerPoint Templates because,you can put it up there for all to see. Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Key chain tied with puzzle piece, business, success, puzzles or jigsaws, shapes, marketing. The prominent colors used in the PowerPoint template are Yellow, Black, Red Engineer growth with our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112. Download without worries with our money back guaranteee.

Risk Procedure Security Threads Ppt PowerPoint Presentation Complete Deck With Slides
This risk procedure security threads ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing eleven slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this risk procedure security threads ppt powerpoint presentation complete deck with slides PPT slideshow.
In Business PowerPoint Templates Download Process Circular Flow Diagram Slides
We present our in business powerpoint templates download process Circular Flow Diagram Slides.Present our Arrows PowerPoint Templates because this template contains the material to highlight the key issues of your presentation. Download and present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download and present our Signs PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Use our Shapes PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Spheres PowerPoint Templates because this diagram has the unique ability to drive home your ideas and show how they mesh to guarantee success.Use these PowerPoint slides for presentations relating to Arrows, Business, Chart, Circular, Commerce, Concept, Contribution, Cycle, Development, Diagram, Global, Idea, Informative, Internet, Join, Making, Manage, Management, Market, Marketing, Partner, Paying, Performance, Plans, Process, Productive, Productivity, Profit, Profitable, Project. The prominent colors used in the PowerPoint template are Green, Black, Gray. Professionals tell us our in business powerpoint templates download process Circular Flow Diagram Slides are designed by professionals You can be sure our Chart PowerPoint templates and PPT Slides are Adorable. Customers tell us our in business powerpoint templates download process Circular Flow Diagram Slides are Classic. Professionals tell us our Contribution PowerPoint templates and PPT Slides are Dazzling. People tell us our in business powerpoint templates download process Circular Flow Diagram Slides are Excellent. People tell us our Cycle PowerPoint templates and PPT Slides are Appealing. Economise on the time you have. Equip yourself with our In Business PowerPoint Templates Download Process Circular Flow Diagram Slides.
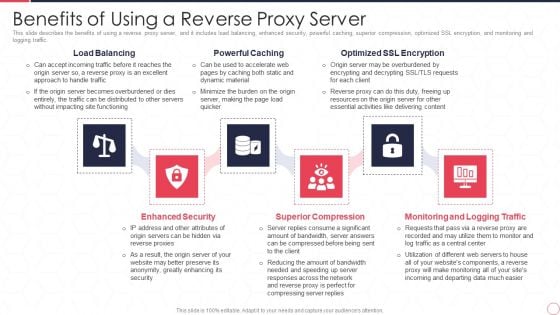
Reverse Proxy Server IT Benefits Of Using A Reverse Proxy Server Ppt Model Designs PDF
This slide describes the benefits of using a reverse proxy server, and it includes load balancing, enhanced security, powerful caching, superior compression, optimized SSL encryption, and monitoring and logging traffic. This is a reverse proxy server it benefits of using a reverse proxy server ppt model designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like load balancing, powerful caching, optimized ssl encryption, enhanced security, superior compression, monitoring and logging traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
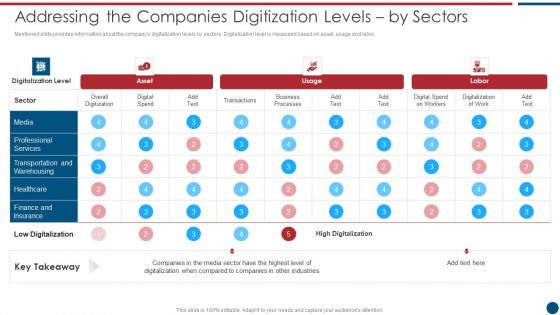
Risk Based Procedures To IT Security Addressing The Companies Digitization Levels By Sectors Infographics PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Addressing The Companies Digitization Levels By Sectors Infographics PDF bundle. Topics like Digital Spend, Digitalization Level, Business Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Software Development Company Profile Case Study Rules PDF
This slide shows the challenges faced by client for development of software infrastructure for secure international data exchange. Company developed cryptographic hash software platform solution. Presenting Business Software Development Company Profile Case Study Rules PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Challenge, Solution, Current Infrastructure, Integrated Software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
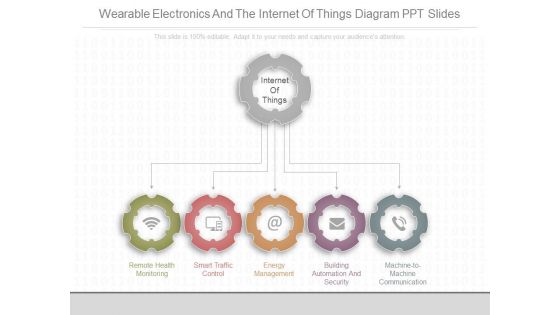
Wearable Electronics And The Internet Of Things Diagram Ppt Slides
This is a wearable electronics and the internet of things diagram ppt slides. This is a five stage process. The stages in this process are remote health monitoring, smart traffic control, energy management, building automation and security, machine to machine communication, internet of things.
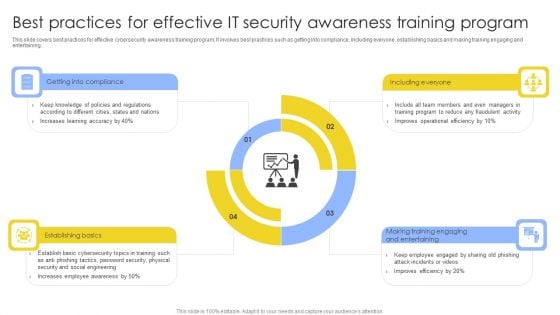
Best Practices For Effective IT Security Awareness Training Program Background PDF
This slide covers best practices for effective cybersecurity awareness training program. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Effective IT Security Awareness Training Program Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Including Everyone, Establishing Basics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Understanding The Kubernetes Components Through Diagram Table Of Contents Ppt Ideas Graphic Images
Presenting this set of slides with name understanding the kubernetes components through diagram table of contents ppt ideas graphic images. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Understanding The Kubernetes Concepts And Architecture Table Of Contents Ppt Summary Inspiration PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture table of contents ppt summary inspiration pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
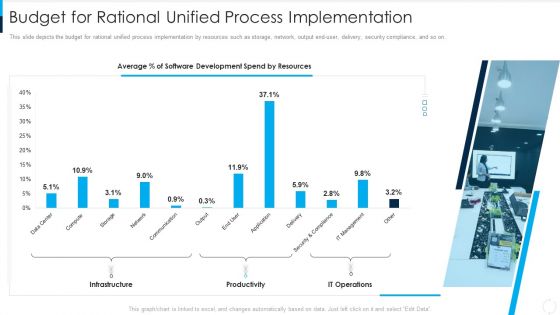
RUP Model Budget For Rational Unified Process Implementation Ppt Outline Layout PDF
This slide depicts the budget for rational unified process implementation by resources such as storage, network, output end-user, delivery, security compliance, and so on. Deliver an awe inspiring pitch with this creative rup model budget for rational unified process implementation ppt outline layout pdf bundle. Topics like infrastructure, productivity, it operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Project Security Administration IT Project Management Activities Tracking Dashboard Structure PDF
This slide provides information regarding the dashboard which will help team in managing different activities associated to projects and keep track on the time, cost spent. Deliver an awe inspiring pitch with this creativeproject security administration it project management activities tracking dashboard structure pdf bundle. Topics like time, cost, team cost breakdown, workload, spent time on projects, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
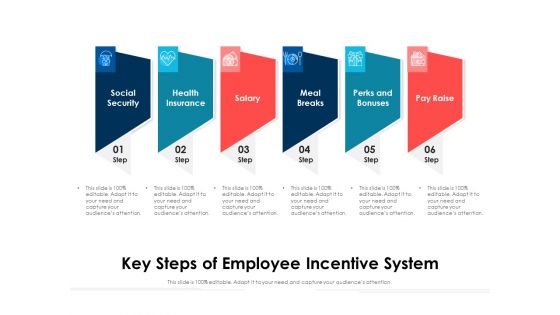
Key Steps Of Employee Incentive System Ppt PowerPoint Presentation Professional Objects PDF
Presenting key steps of employee incentive system ppt powerpoint presentation professional objects pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social security, health insurance, salary, meal breaks, perks and bonuses, pay raise. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
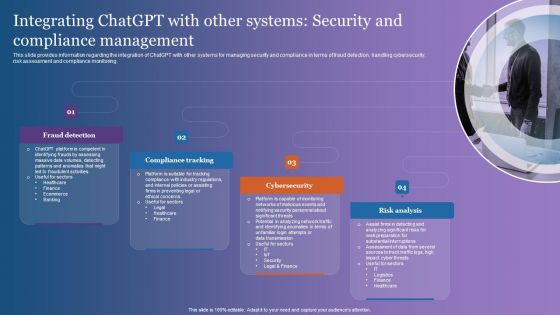
Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF
This slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
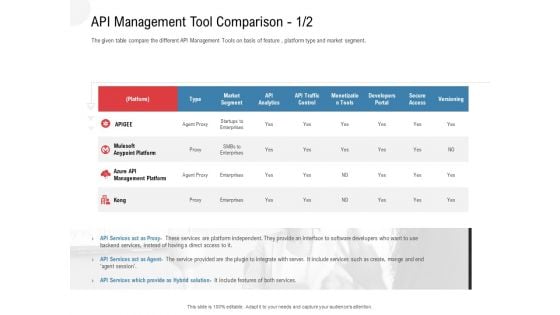
API Outline API Management Tool Comparison Ppt Samples PDF
The given table compare the different API Management Tools on basis of feature , platform type and market segment. Deliver an awe-inspiring pitch with this creative api outline api management tool comparison ppt samples pdf bundle. Topics like market segment, api analytics, developers portal, secure access, versioning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
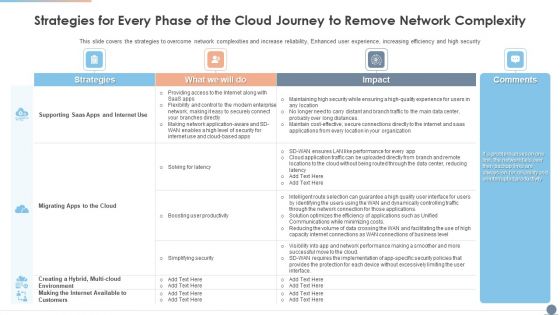
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Deliver and pitch your topic in the best possible manner with this Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF. Use them to share invaluable insights on Environment, Strategies, Productivity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
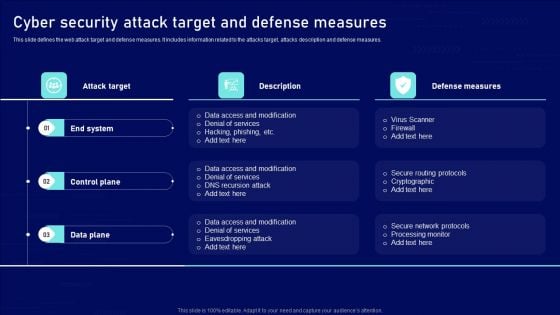
Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
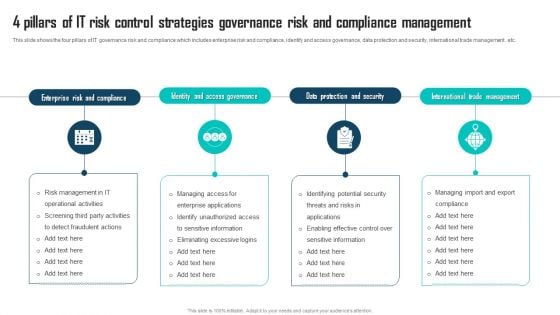
4 Pillars Of IT Risk Control Strategies Governance Risk And Compliance Management Sample PDF
This slide shows the four pillars of IT governance risk and compliance which includes enterprise risk and compliance, identify and access governance, data protection and security, international trade management , etc. Presenting 4 Pillars Of IT Risk Control Strategies Governance Risk And Compliance Management Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk And Compliance, Data Protection, International Trade Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
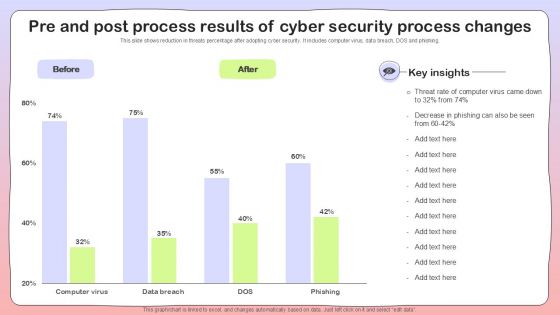
Pre And Post Process Results Of Cyber Security Process Changes Sample PDF
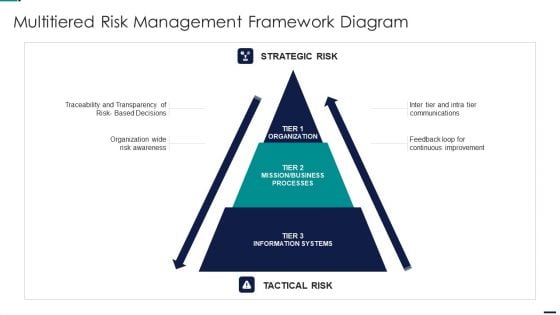
Risk Management Model For Data Security Multitiered Risk Management Framework Diagram Ideas PDF
This is a Risk Management Model For Data Security Multitiered Risk Management Framework Diagram Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategic Risk, Mission, Business Processes, Information Systems, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
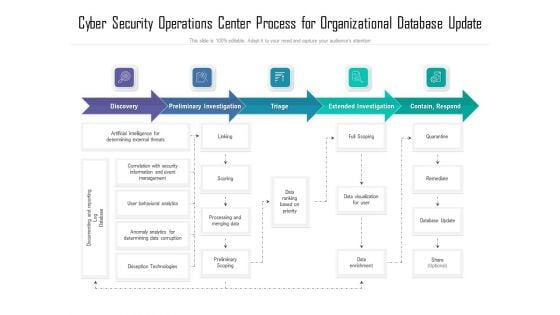
Cyber Security Operations Center Process For Organizational Database Update Ppt Show Deck PDF
Showcasing this set of slides titled cyber security operations center process for organizational database update ppt show deck pdf. The topics addressed in these templates are process, organizational, database. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
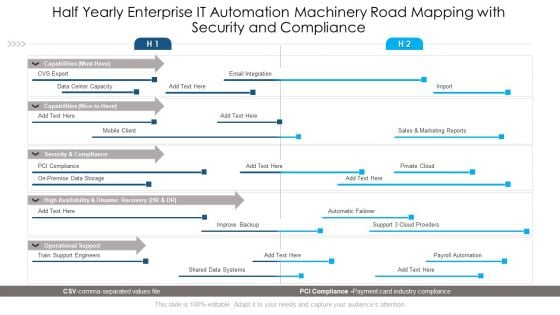
Half Yearly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Inspiration
Introducing our half yearly enterprise it automation machinery road mapping with security and compliance inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Cyber Security Implementation Framework Dashboard Incident Tracking Ppt Styles Topics PDF
Presenting this set of slides with name cyber security implementation framework dashboard incident tracking ppt styles topics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
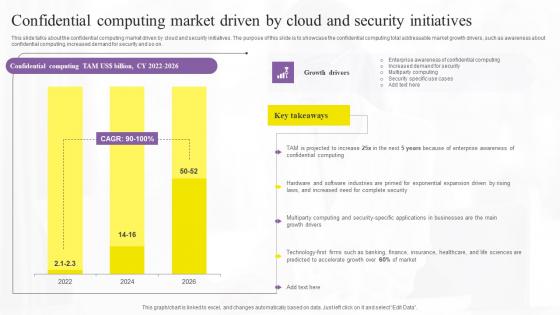
Confidential Computing Market Driven Confidential Computing Technologies Rules Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This modern and well-arranged Confidential Computing Market Driven Confidential Computing Technologies Rules Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
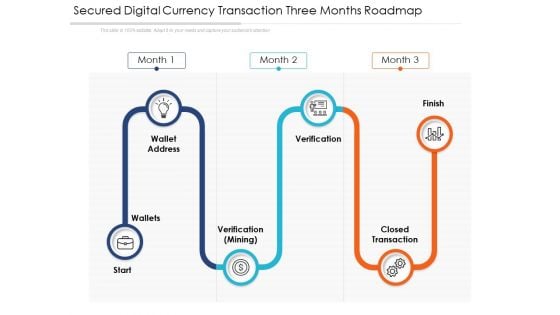
Secured Digital Currency Transaction Three Months Roadmap Graphics
Presenting our jaw dropping secured digital currency transaction three months roadmap graphics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
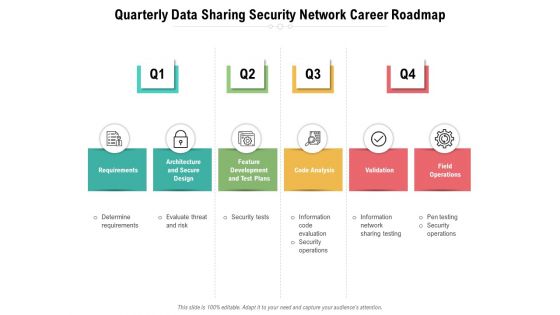
Quarterly Data Sharing Security Network Career Roadmap Guidelines
Presenting our jaw-dropping quarterly data sharing security network career roadmap guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
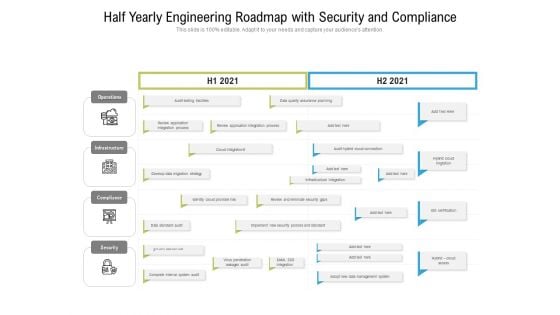
Half Yearly Engineering Roadmap With Security And Compliance Topics
Presenting our jaw-dropping half yearly engineering roadmap with security and compliance topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Effective Digital Security Three Months Strategic Timeline Download
Presenting our jaw dropping effective digital security three months strategic timeline download. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
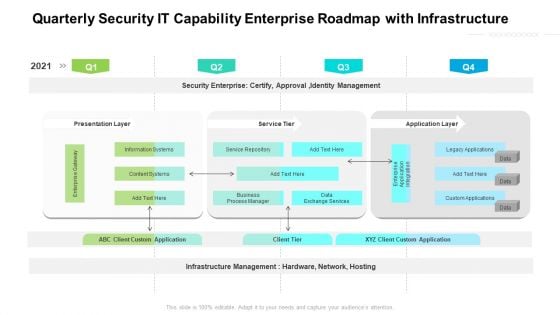
Quarterly Security IT Capability Enterprise Roadmap With Infrastructure Background
Presenting our jaw dropping quarterly security it capability enterprise roadmap with infrastructure background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
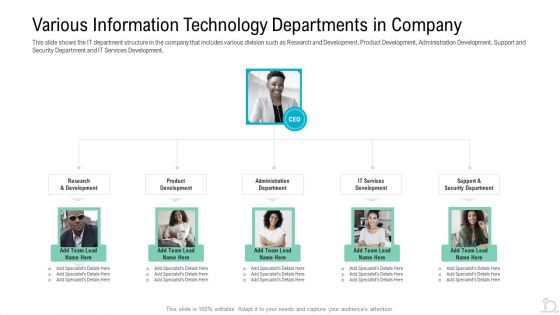
Various Information Technology Departments In Company Formats PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development. This is a various information technology departments in company formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like product development, research and development, support and security department. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































