Safety Inspection

Cyber Security Problems Management And Action Plan Microsoft PDF
The following slide illustrates the cyber security risk management plan to outline business security threats and draft proposed strategies. It also includes elements such as objectives, issues, breach response actions, employee training etc. Persuade your audience using this Cyber Security Problems Management And Action Plan Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Breach Response Actions, Employee Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
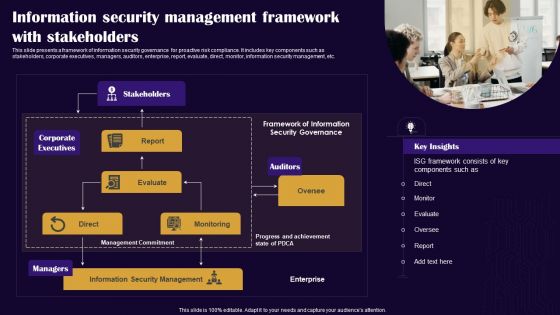
Information Security Management Framework With Stakeholders Diagrams PDF
This slide presents a framework of information security governance for proactive risk compliance. It includes key components such as stakeholders, corporate executives, managers, auditors, enterprise, report, evaluate, direct, monitor, information security management, etc. Persuade your audience using this Information Security Management Framework With Stakeholders Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Stakeholders, Auditors, Corporate Executives. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
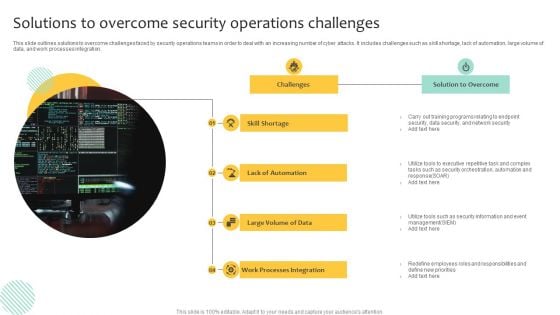
Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
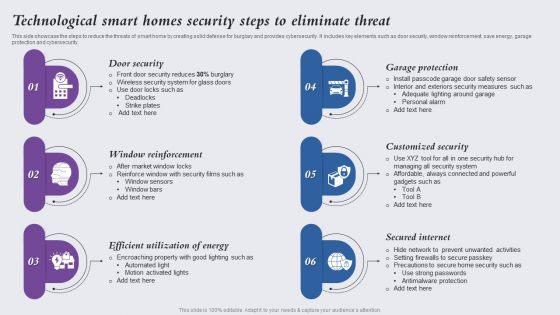
Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
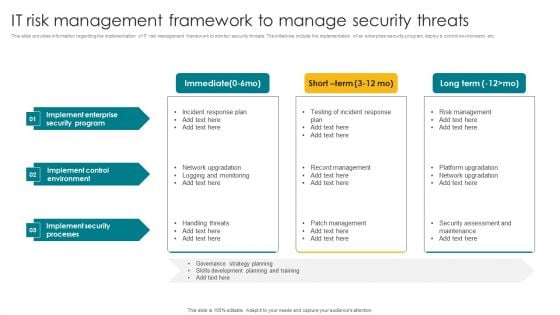
IT Risk Management Framework To Manage Security Threats Template PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. The IT Risk Management Framework To Manage Security Threats Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
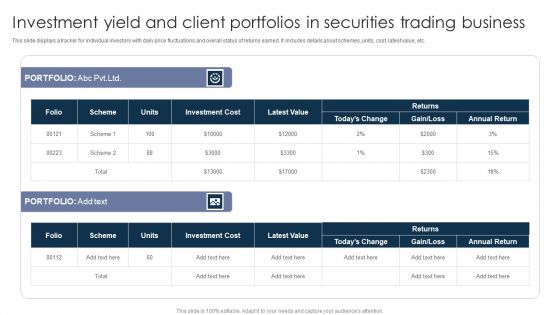
Investment Yield And Client Portfolios In Securities Trading Business Ppt PowerPoint Presentation Gallery Format Ideas PDF
This slide displays a tracker for individual investors with daily price fluctuations and overall status of returns earned. It includes details about schemes, units, cost, latest value, etc. Showcasing this set of slides titled Investment Yield And Client Portfolios In Securities Trading Business Ppt PowerPoint Presentation Gallery Format Ideas PDF. The topics addressed in these templates are Investment Cost, Latest Value, Annual Return. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
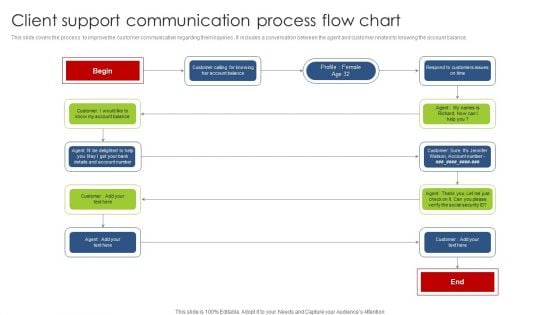
Client Support Communication Process Flow Chart Pictures PDF
This slide covers the process to improve the customer communication regarding their inquiries . It includes a conversation between the agent and customer related to knowing the account balance. Presenting Client Support Communication Process Flow Chart Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Customers Issues, Social Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Ensure Security And Access Controls Ppt PowerPoint Presentation Slides Information
This is a ensure security and access controls ppt powerpoint presentation slides information. This is a two stage process. The stages in this process are business, management, planning, strategy, marketing.
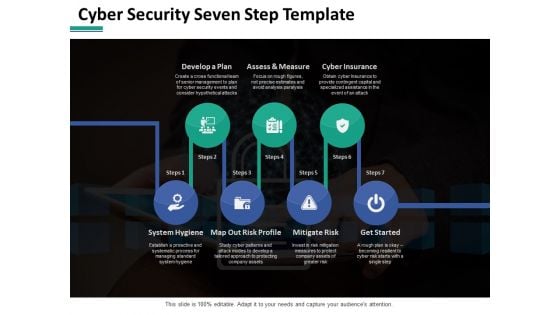
Cyber Security Seven Step Ppt PowerPoint Presentation Infographic Template Maker
This is a cyber security seven step ppt powerpoint presentation infographic template maker. This is a seven stage process. The stages in this process are business, management, planning, strategy, marketing.
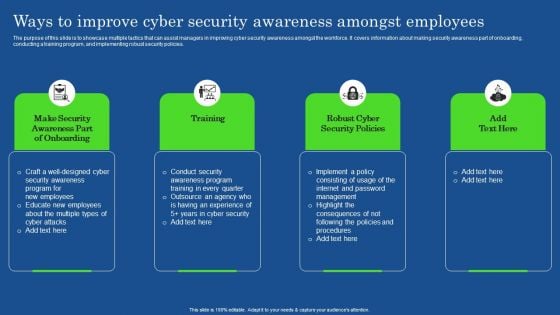
Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF
The purpose of this slide is to showcase multiple tactics that can assist managers in improving cyber security awareness amongst the workforce. It covers information about making security awareness part of onboarding, conducting a training program, and implementing robust security policies. The Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Query Slide Diagram For Secure Cash Endowment Rules PDF
Persuade your audience using this query slide diagram for secure cash endowment rules pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including query slide diagram for secure cash endowment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Project Security Administration IT Diagrams PDF
This is a agenda for project security administration it diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, management, implemented, security center, improvement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
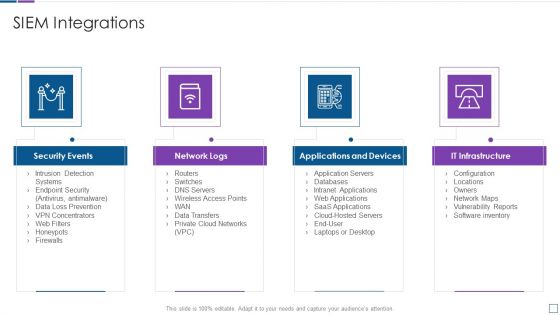
Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Standard Computing Vs Modern Information Security Icon Microsoft PDF
Persuade your audience using this Standard Computing Vs Modern Information Security Icon Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Standard Computing, Modern Information Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Awareness Training Program Icons Ppt Layouts Structure PDF
Persuade your audience using this IT Security Awareness Training Program Icons Ppt Layouts Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Awareness, Training Program, Icons. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
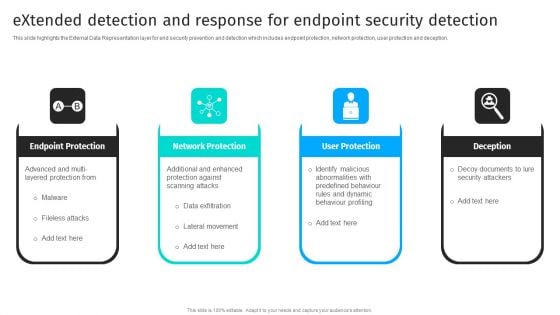
Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
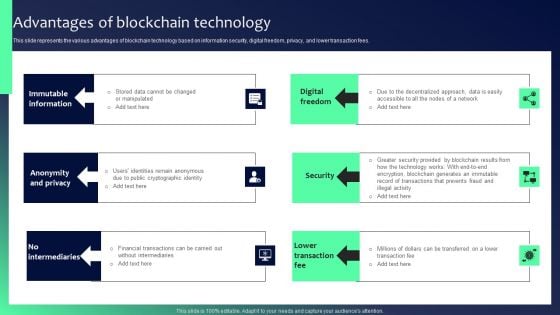
Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. Find a pre-designed and impeccable Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
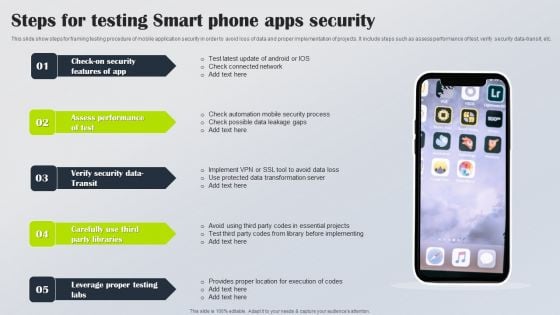
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
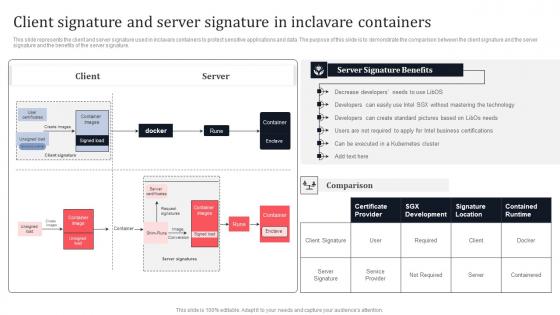
Client Signature And Server Signature In Inclavare Containers Secure Multi Party Mockup Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. Want to ace your presentation in front of a live audience Our Client Signature And Server Signature In Inclavare Containers Secure Multi Party Mockup Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
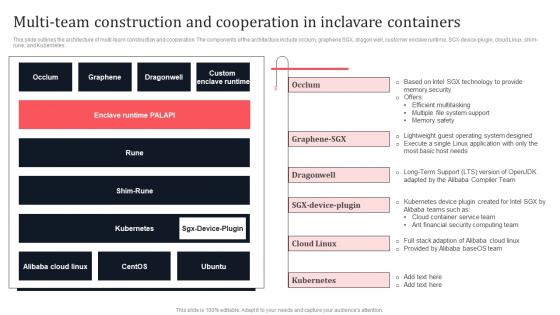
Multi Team Construction And Cooperation In Inclavare Containers Secure Multi Party Pictures Pdf
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Boost your pitch with our creative Multi Team Construction And Cooperation In Inclavare Containers Secure Multi Party Pictures Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.

Security In 5G Technology Architecture 5G Network Structure Pictures PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Retrieve professionally designed Security In 5G Technology Architecture 5G Network Structure Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF
This slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present like a pro with Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
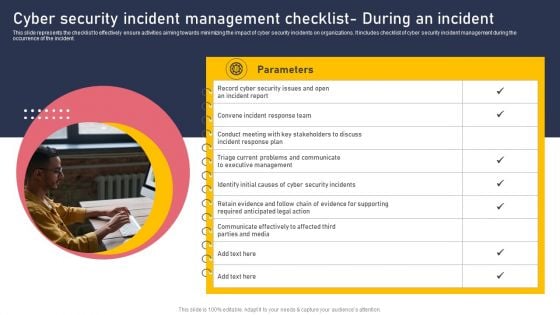
Cyber Security Incident Management Checklist During An Incident Inspiration PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. The Cyber Security Incident Management Checklist During An Incident Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
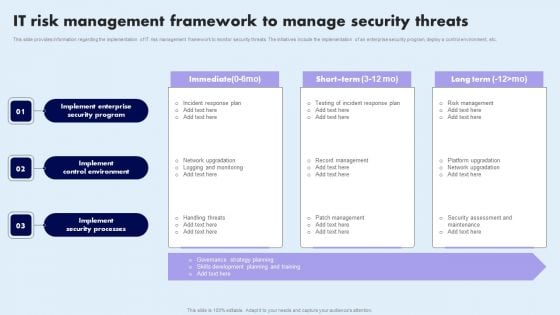
IT Risk Management Framework To Manage Security Threats Summary PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Retrieve professionally designed IT Risk Management Framework To Manage Security Threats Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
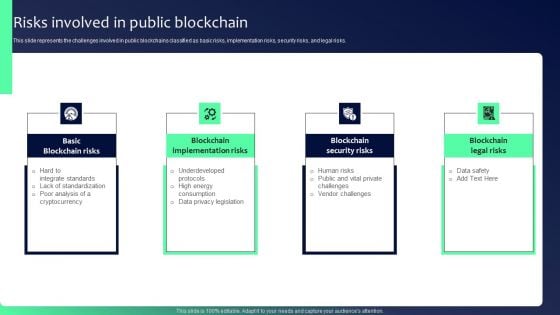
Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF
This slide represents the challenges involved in public blockchains classified as basic risks, implementation risks, security risks, and legal risks. Are you searching for a Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF from Slidegeeks today.

Objectives Of Corporate Governance Ppt Diagrams
This is a objectives of corporate governance ppt diagrams. This is a five stage process. The stages in this process are legal and financial discipline, delivering values, accountability, transparency, stakeholder analysis.

Organizational Security Solutions Prerequisites For Effective Secops Implementation Summary PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a organizational security solutions prerequisites for effective secops implementation summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
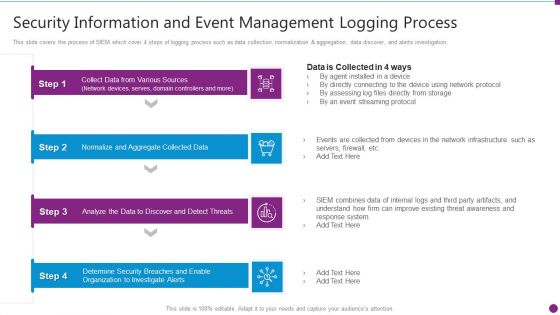
Security Information And Event Management Logging Process Structure PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
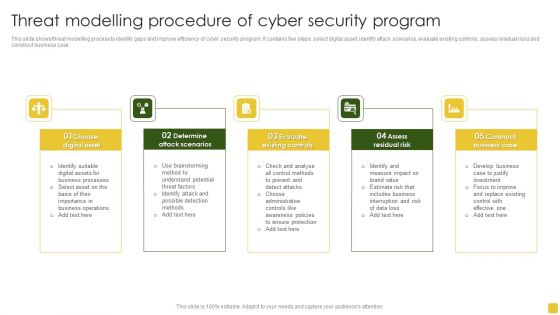
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
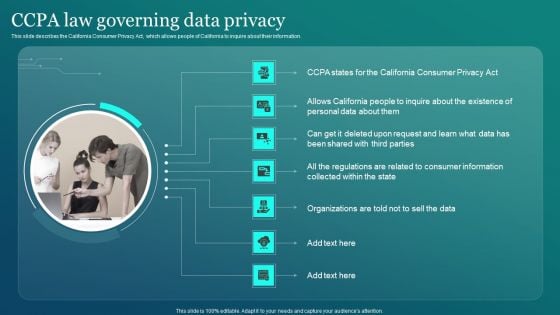
Information Security CCPA Law Governing Data Privacy Clipart PDF
This slide describes the California Consumer Privacy Act, which allows people of California to inquire about their information. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Security CCPA Law Governing Data Privacy Clipart PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Security CCPA Law Governing Data Privacy Clipart PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Information Security Data Privacy In Financial Institutions Mockup PDF
This slide represents the data privacy in financial institutions which decreases the possibility of fines and reputational damage as a result of unlawful disclosure. This Information Security Data Privacy In Financial Institutions Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security Data Privacy In Financial Institutions Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
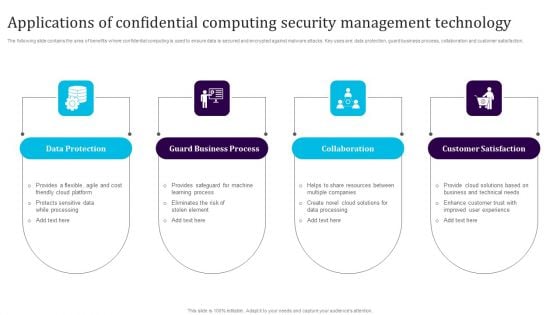
Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
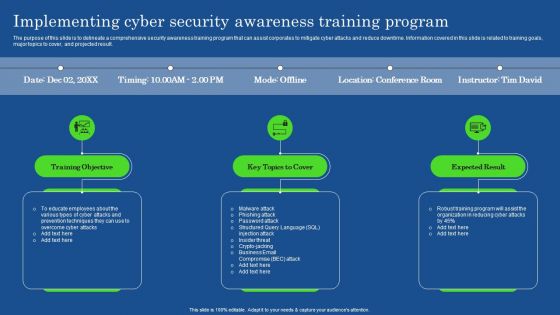
Implementing Cyber Security Awareness Training Program Professional PDF
The purpose of this slide is to delineate a comprehensive security awareness training program that can assist corporates to mitigate cyber attacks and reduce downtime. Information covered in this slide is related to training goals, major topics to cover, and projected result. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Awareness Training Program Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Table Of Contents Organizational Assets Security Management Strategy Information PDF
Find highly impressive Table Of Contents Organizational Assets Security Management Strategy Information PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Organizational Assets Security Management Strategy Information PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents For Workplace Security Management Program Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Workplace Security Management Program Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Workplace Security Management Program Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident Management Table Of Contents Clipart PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Management Table Of Contents Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Management Table Of Contents Clipart PDF today and make your presentation stand out from the rest.

3 Key Areas For Document Management Security Controls Ideas PDF
This slide presents the key areas of security control that enable companies to manage information access and permissions. It includes cryptography, best practice guidelines, compliance certifications and attestations. Persuade your audience using this 3 Key Areas For Document Management Security Controls Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cryptography, Practice Guidelines, Attestations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Workforce Security Realization Coaching Plan Comparison Ppt Outline Picture PDF
This is a workforce security realization coaching plan comparison ppt outline picture pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topic like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
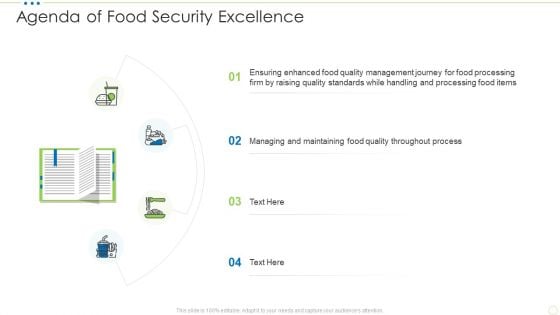
Agenda Of Food Security Excellence Ppt Model Visuals PDF
Presenting agenda of food security excellence ppt model visuals pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like maintaining, process, management, raising quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Agenda For Cyber Security Automation Framework Icons PDF
Find a pre designed and impeccable Agenda For Cyber Security Automation Framework Icons PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda IT Security Automation Systems Guide Sample PDF
Find a pre designed and impeccable Agenda IT Security Automation Systems Guide Sample PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
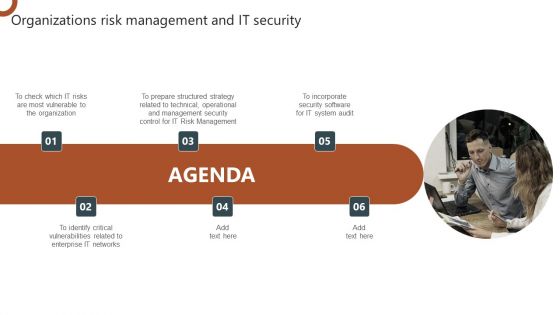
Agenda Organizations Risk Management And IT Security Portrait PDF
Find a pre designed and impeccable Agenda Organizations Risk Management And IT Security Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
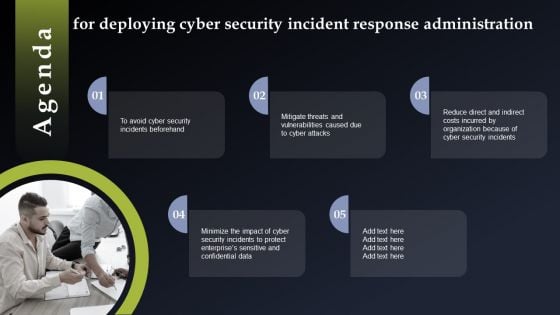
Agenda For Deploying Cyber Security Incident Response Administration Guidelines PDF
Find a pre designed and impeccable Agenda For Deploying Cyber Security Incident Response Administration Guidelines PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Information Security Ppt PowerPoint Presentation File Styles PDF
Find a pre designed and impeccable Agenda For Information Security Ppt PowerPoint Presentation File Styles PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda Securing Market Leadership Through Competitive Excellence Pictures PDF
Find a pre designed and impeccable Agenda Securing Market Leadership Through Competitive Excellence Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Cyber Security Breache Response Strategy Slides PDF
Find a pre designed and impeccable Agenda For Cyber Security Breache Response Strategy Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda Implementing Cyber Security Incident Management Template PDF
Find a pre designed and impeccable Agenda Implementing Cyber Security Incident Management Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
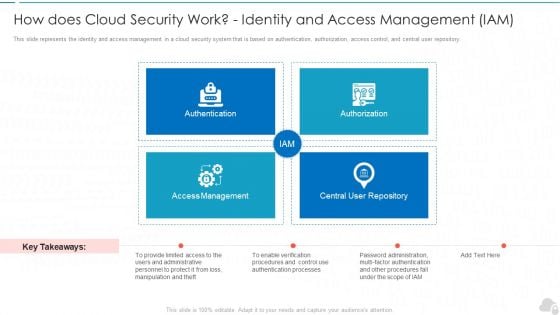
How Does Cloud Security Work Identity And Access Management Iam Cloud Computing Security IT Ppt Infographics Picture PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting how does cloud security work identity and access management iam cloud computing security it ppt infographics picture pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like authentication, authorization, access management, central user repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Adhere To Strict Compliance Requirements Diagrams PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Adhere To Strict Compliance Requirements Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Adhere To Strict Compliance Requirements Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
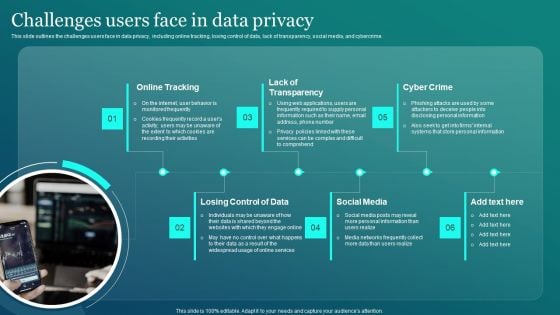
Information Security Challenges Users Face In Data Privacy Sample PDF
This slide outlines the challenges users face in data privacy, including online tracking, losing control of data, lack of transparency, social media, and cybercrime. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Security Challenges Users Face In Data Privacy Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Security Challenges Users Face In Data Privacy Sample PDF.

Information Security Storage Limitation Principle Of GDPR Law Designs PDF
This slide conveys the GDPR laws storage limitation principle, which prohibits you from holding personal data for longer than is required and requires you to justify your reasons for maintaining data. Get a simple yet stunning designed Information Security Storage Limitation Principle Of GDPR Law Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Security Storage Limitation Principle Of GDPR Law Designs PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
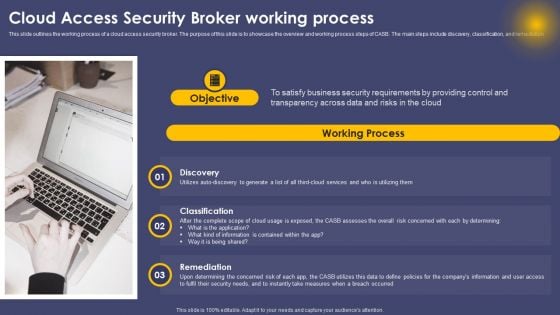
Cloud Access Security Broker Working Process Ppt Slides Portrait PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Boost your pitch with our creative Cloud Access Security Broker Working Process Ppt Slides Portrait PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
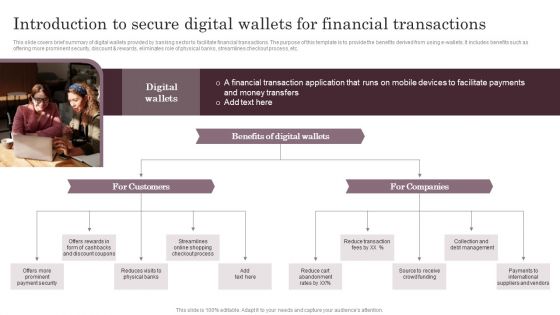
Introduction To Secure Digital Wallets For Financial Transactions Themes PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Digital Wallets For Financial Transactions Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
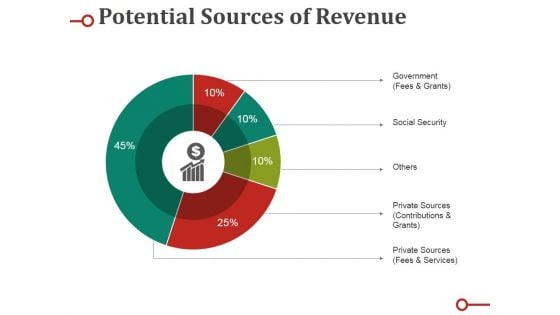
Potential Sources Of Revenue Ppt PowerPoint Presentation Templates
This is a potential sources of revenue ppt powerpoint presentation templates. This is a five stage process. The stages in this process are social security, others, private sources contributions and grants, private sources, fees and services, government, fees and grants.

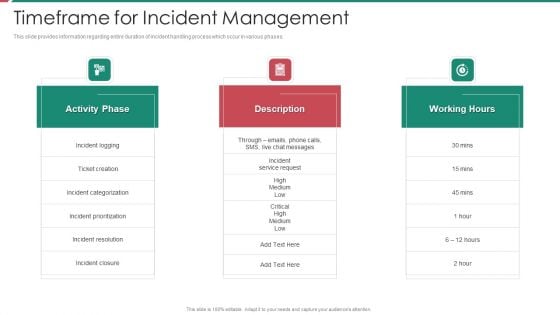
Organizational Security Solutions Timeframe For Incident Management Elements PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Presenting organizational security solutions timeframe for incident management elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like activity phase, description, working hours. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security And Process Integration Timeframe For Incident Management Sample PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Presenting security and process integration timeframe for incident management sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like activity phase, description, working hours. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
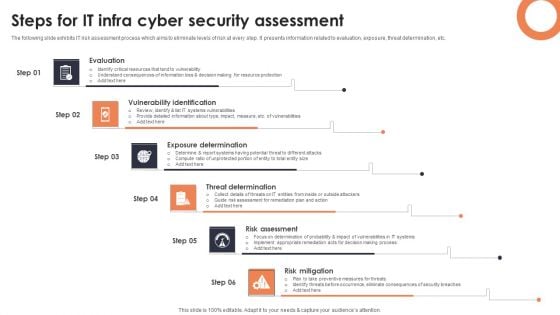
Steps For IT Infra Cyber Security Assessment Background PDF
The following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Presenting Steps For IT Infra Cyber Security Assessment Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Evaluation, Vulnerability Identification, Exposure Determination. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Breache Response Strategy Table Of Contents Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Breache Response Strategy Table Of Contents Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.


 Continue with Email
Continue with Email

 Home
Home


































