Safety Inspection

Security Incident Response Plan Template Ppt Design Templates
This is a security incident response plan template ppt design templates. This is a three stage process. The stages in this process are prepare, detection and analysis, post incident activity.
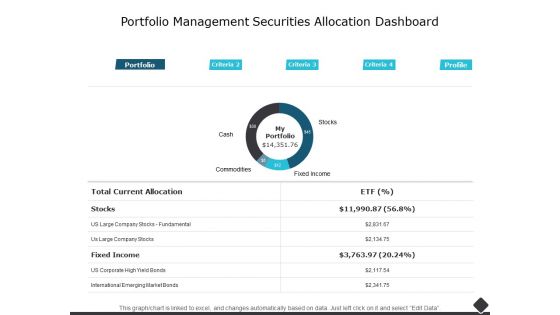
Portfolio Management Securities Allocation Dashboard Ppt PowerPoint Presentation Infographics Examples
This is a portfolio management securities allocation dashboard ppt powerpoint presentation infographics examples. The topics discussed in this diagram are finance, marketing, management, investment, analysis. This is a completely editable PowerPoint presentation, and is available for immediate download.

Vector Showing Technology Issues Of Information Security Ppt PowerPoint Presentation File Sample PDF
Showcasing this set of slides titled vector showing technology issues of information security ppt powerpoint presentation file sample pdf. The topics addressed in these templates are vector showing technology issues of information security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Bank Vault To Secure Valuables And Money Ppt PowerPoint Presentation Gallery Infographic Template PDF
Showcasing this set of slides titled bank vault to secure valuables and money ppt powerpoint presentation gallery infographic template pdf. The topics addressed in these templates are bank vault to secure valuables and money. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Blockchain In Financial Sector For Security Ppt PowerPoint Presentation File Slide Portrait PDF
Showcasing this set of slides titled blockchain in financial sector for security ppt powerpoint presentation file slide portrait pdf. The topics addressed in these templates are security, digital transactions, authentication of users. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Vector Showing IT Security Under Threat Ppt PowerPoint Presentation Gallery Deck PDF
Showcasing this set of slides titled vector showing it security under threat ppt powerpoint presentation gallery deck pdf. The topics addressed in these templates are vector showing it security under threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Drone Flying Over Beach For Security Purpose Ppt PowerPoint Presentation File Inspiration PDF
Showcasing this set of slides titled drone flying over beach for security purpose ppt powerpoint presentation file inspiration pdf. The topics addressed in these templates are drone flying over beach for security purpose. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Company Data Security And Management Vector Icon Ppt PowerPoint Presentation Gallery Template PDF
Showcasing this set of slides titled company data security and management vector icon ppt powerpoint presentation gallery template pdf. The topics addressed in these templates are company data security and management vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Corporate Data Management For Network Security Vector Icon Ppt PowerPoint Presentation Icon Portfolio PDF
Pitch your topic with ease and precision using this corporate data management for network security vector icon ppt powerpoint presentation icon portfolio pdf. This layout presents information on corporate data management for network security vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Business Warehouse Security Vector Icon Ppt PowerPoint Presentation Gallery Vector PDF
Showcasing this set of slides titled business warehouse security vector icon ppt powerpoint presentation gallery vector pdf. The topics addressed in these templates are business warehouse security vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
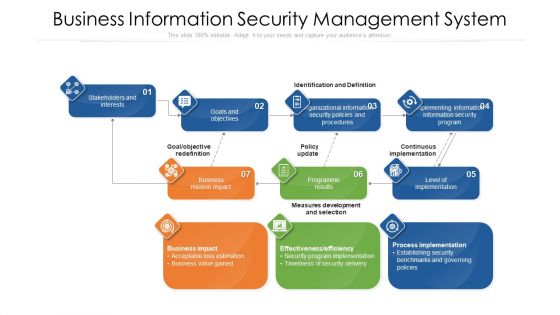
Business Information Security Management System Ppt PowerPoint Presentation Gallery Background Image PDF
Showcasing this set of slides titled business information security management system ppt powerpoint presentation gallery background image pdf. The topics addressed in these templates are business information security management system. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
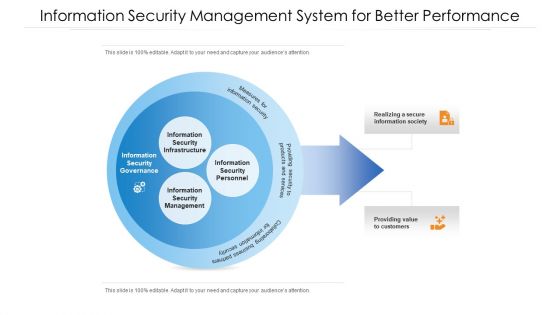
Information Security Management System For Better Performance Ppt PowerPoint Presentation File Example PDF
Showcasing this set of slides titled information security management system for better performance ppt powerpoint presentation file example pdf. The topics addressed in these templates are information security management system for better performance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information Security Management System With Monitoring And Tracking Ppt PowerPoint Presentation Gallery Sample PDF
Showcasing this set of slides titled information security management system with monitoring and tracking ppt powerpoint presentation gallery sample pdf. The topics addressed in these templates are analyze, auditors, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Management To Enhance Project Security Ppt Infographics Outline PDF
Deliver and pitch your topic in the best possible manner with this table of contents for management to enhance project security ppt infographics outline pdf. Use them to share invaluable insights on management, implementation, security, technological, program and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Query Slide Diagram For Designing A Secure Network Perimeter Diagrams PDF
Showcasing this set of slides titled query slide diagram for designing a secure network perimeter diagrams pdf. The topics addressed in these templates are query slide diagram for designing a secure network perimeter. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Developing Firm Security Strategy Plan Information PDF
Deliver an awe inspiring pitch with this creative table of contents for developing firm security strategy plan information pdf bundle. Topics like implementing, security, management, corporate, governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Desktop Security Management Cont Plan Designs PDF
Deliver and pitch your topic in the best possible manner with this table of contents for desktop security management cont plan designs pdf. Use them to share invaluable insights on requirement, security, organization, financial, planning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icon Of Information Security Strategic Action Plan To Prevent Threats Clipart PDF
Pitch your topic with ease and precision using this icon of information security strategic action plan to prevent threats clipart pdf. This layout presents information on icon of information security strategic action plan to prevent threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Secure Transaction During E Commerce Business Financial Operations Icon Guidelines PDF
Showcasing this set of slides titled secure transaction during e commerce business financial operations icon guidelines pdf The topics addressed in these templates are secure transaction during e commerce business financial operations icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
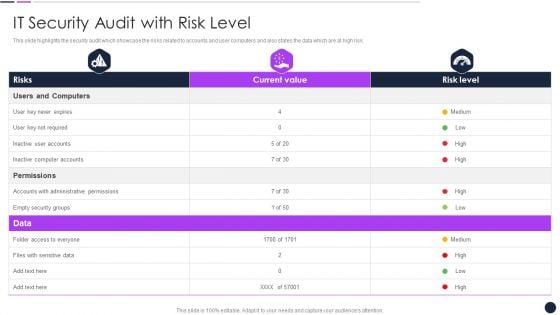
Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF
Deliver an awe inspiring pitch with this creative Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF bundle. Topics like Inactive Computer, Administrative Permissions, Security Groups can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security For Cloud Based Systems Icon For Data Protection Themes PDF
Showcasing this set of slides titled Security For Cloud Based Systems Icon For Data Protection Themes PDF. The topics addressed in these templates are Security For Cloud, Based Systems Icon, For Data Protection . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF
Pitch your topic with ease and precision using this Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF. This layout presents information on Pathway Change Framework, Food Security Sustainable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icon Showcasing Application Of Computer Vision Technologyin Digital Security Sample PDF
Pitch your topic with ease and precision using this Icon Showcasing Application Of Computer Vision Technologyin Digital Security Sample PDF. This layout presents information on Showcasing Application, Computer Vision, Technologyin Digital Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
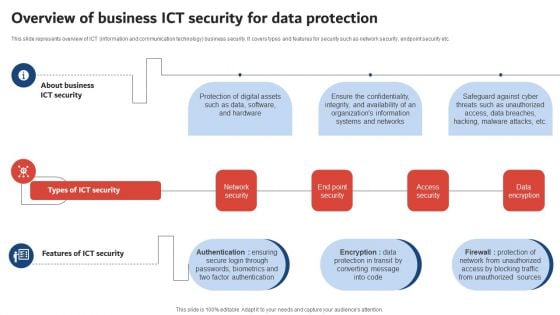
Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF
This slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Welcome to our selection of the Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
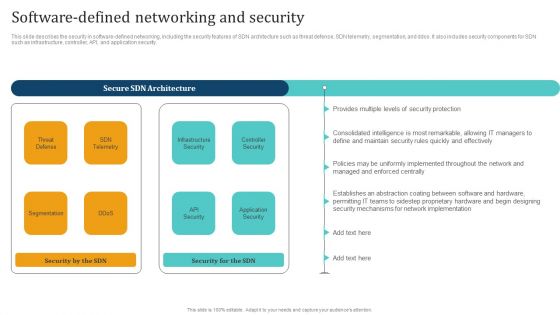
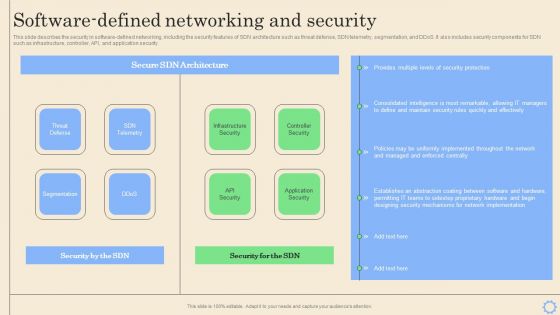
Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Want to ace your presentation in front of a live audience Our Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT Ss V
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.

Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF
This slide shows solutions to various challenges faced by organizations to provide cloud security. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Showcasing this set of slides titled Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF. The topics addressed in these templates are Solutions To Overcome, Various Security For Cloud, Based Systems Challenges . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF
This slide showcases blockchain technology for anti money laundering AML and transaction monitoring. It provides information about transaction subsets, input data, monitoring, analysis, alerts, record, red flags, Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF.
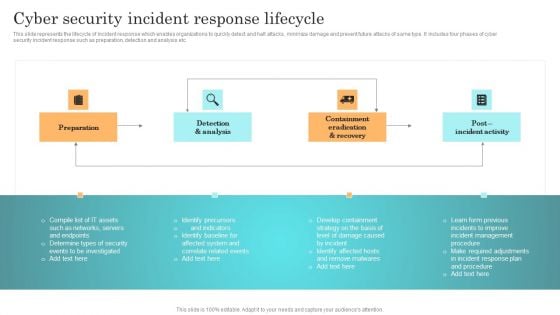
Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
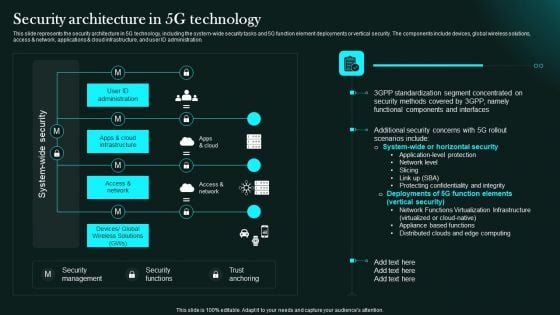
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
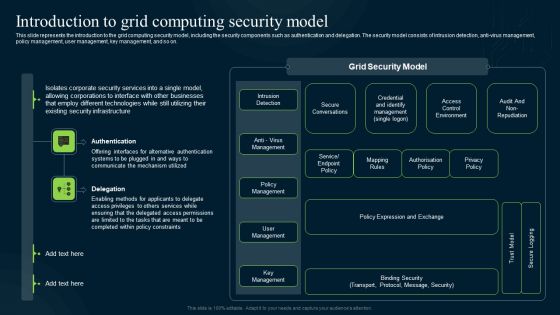
Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. This modern and well-arranged Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
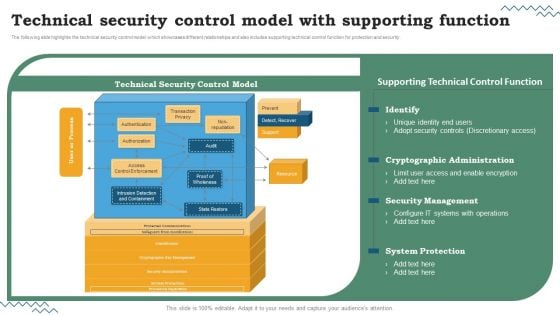
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.

Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
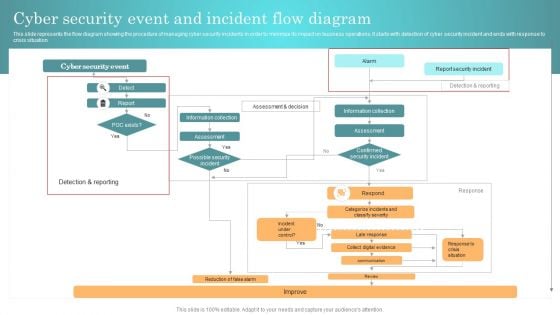
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Flying Security Camera With Smart Phone On Wooden Table Ppt PowerPoint Presentation File Topics PDF
Pitch your topic with ease and precision using this flying security camera with smart phone on wooden table ppt powerpoint presentation file topics pdf. This layout presents information on flying security camera with smart phone on wooden table. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Environments Best Suited For Efficient And Secure Supply Chains Template PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains template pdf bundle. Topics like inventory investment, strategy, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
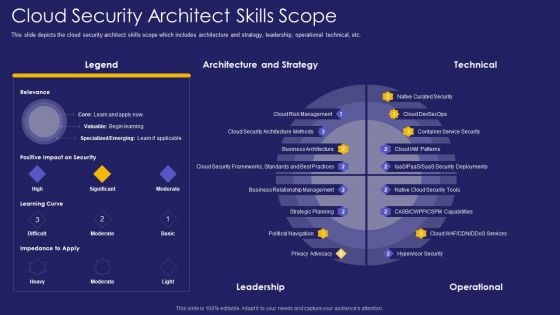
Role IT Team Digital Transformation Cloud Security Architect Skills Scope Rules PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative role it team digital transformation cloud security architect skills scope rules pdf bundle. Topics like architecture, strategy, leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Shift Capital Fundraising Pitch Deck Details About Shifts Secure Storage Facility Formats PDF
This slide provides information about the storage facility at Shift and some details regarding the hub. Deliver an awe inspiring pitch with this creative shift capital fundraising pitch deck details about shifts secure storage facility formats pdf bundle. Topics like our secure storage facility, the hub can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
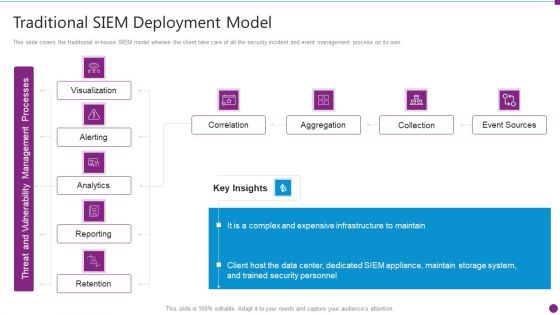
Security Information And Event Management Strategies For Financial Audit And Compliance Traditional SIEM Deployment Guidelines PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance traditional siem deployment guidelines pdf bundle. Topics like correlation, aggregation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc.Deliver an awe inspiring pitch with this creative Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF bundle. Topics like Architecture And Strategy, Technical, Leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
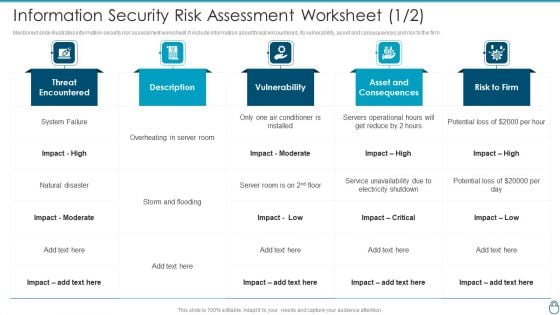
Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
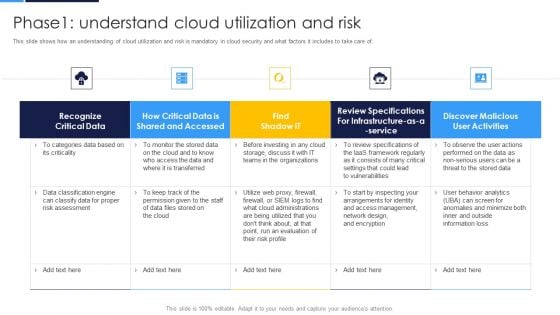
Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF bundle. Topics like Shared And Accessed, Risk Assessment, Review Specifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
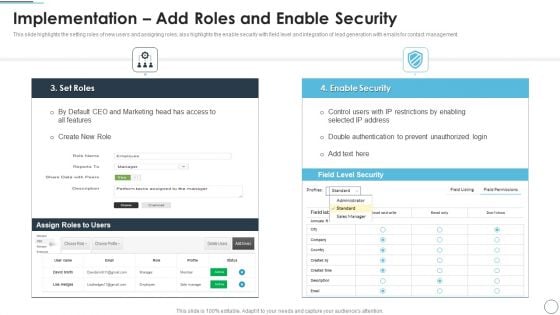
CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF bundle. Topics like Restrictions By Enabling, Prevent Unauthorized, Double Authentication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
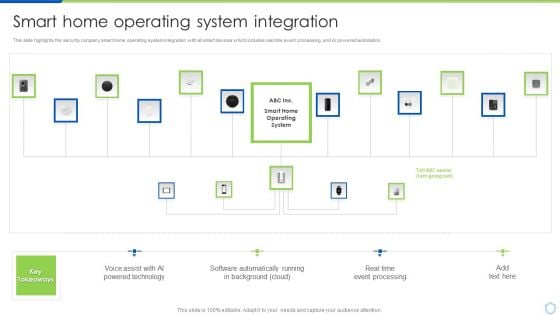
Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
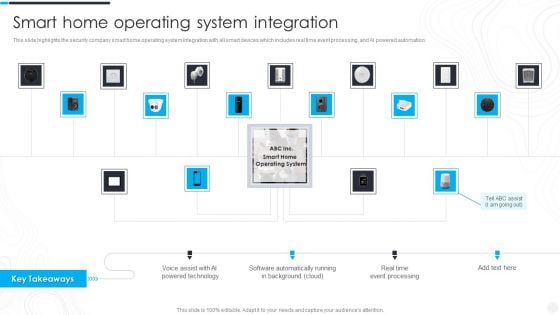
Security Camera System Company Profile Smart Home Operating System Integration Background PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Smart Home Operating System Integration Background PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF. Use them to share invaluable insights on Assessing Information, Occurrence Identification, Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
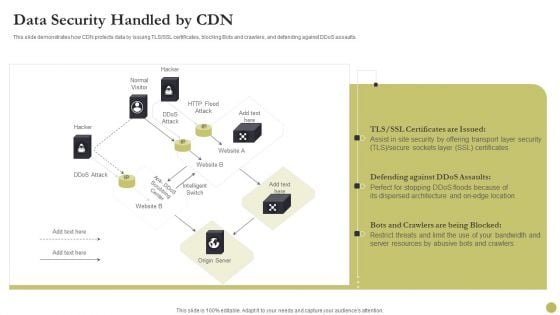
Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
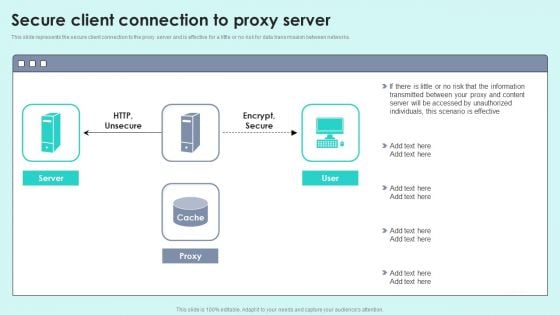
Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks.Deliver an awe inspiring pitch with this creative Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF bundle. Topics like Transmitted Between, Accessed Unauthorized, Scenario Effective can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Government And Private Sector Clients Sample PDF
This slide highlights the security company clients from government and private sector which includes offices with location and industries with company name. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Government And Private Sector Clients Sample PDF bundle. Topics like Industry, Location, Treasure Office can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF
The following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy,disaster recovery, password encryption, tasks, reviews etc. There are so many reasons you need a Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
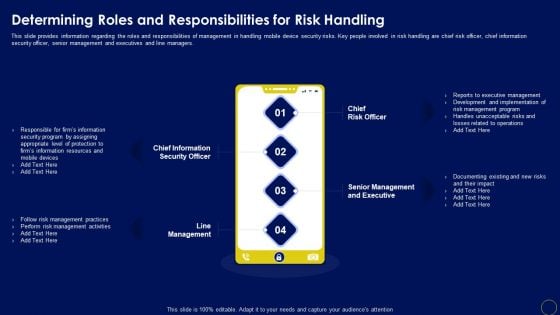
Determining Roles And Responsibilities For Risk Handling Business Mobile Device Security Management Graphics PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Boost your pitch with our creative Determining Roles And Responsibilities For Risk Handling Business Mobile Device Security Management Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.
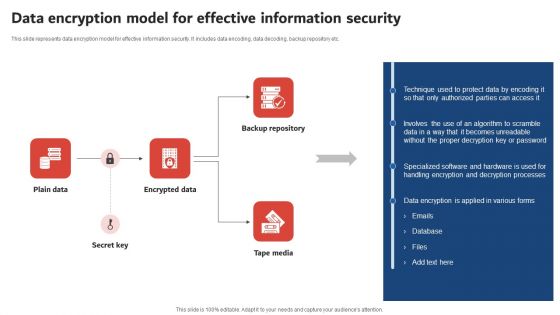
Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF
This slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
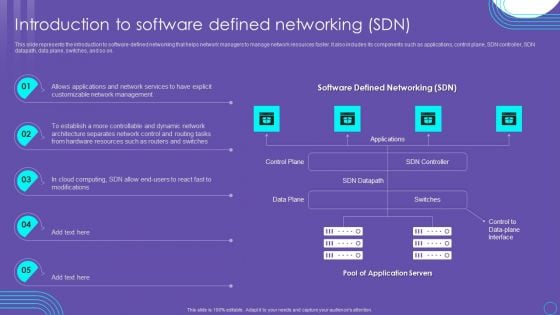
SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF
This slide represents the introduction to software defined networking that helps network managers to manage network resources faster. It also includes its components such as applications, control plane, SDN controller, SDN datapath, data plane, switches, and so on. Presenting this PowerPoint presentation, titled SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
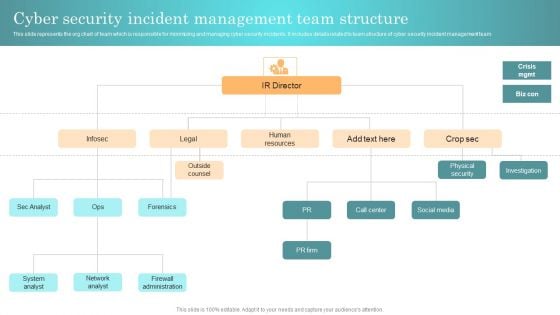
Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
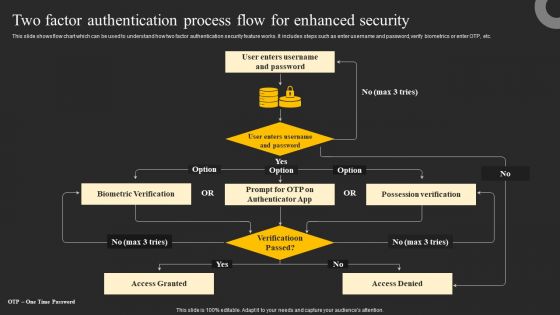
Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Explore a selection of the finest Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
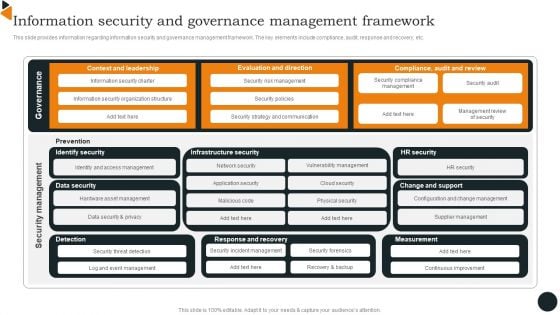
Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Explore a selection of the finest Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.


 Continue with Email
Continue with Email

 Home
Home


































