Safety Inspection

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.

Key Advantages Of Integrating IoT Banking Future With IoT Ppt Powerpoint IoT SS V
Following slide showcases various benefits of utilizing IoT devices to assure effective and smart banking services increasing customer satisfaction. It covers elements such as security, real time monitoring, better analytics and others. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Key Advantages Of Integrating IoT Banking Future With IoT Ppt Powerpoint IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Key Advantages Of Integrating IoT Banking Future With IoT Ppt Powerpoint IoT SS V Following slide showcases various benefits of utilizing IoT devices to assure effective and smart banking services increasing customer satisfaction. It covers elements such as security, real time monitoring, better analytics and others.
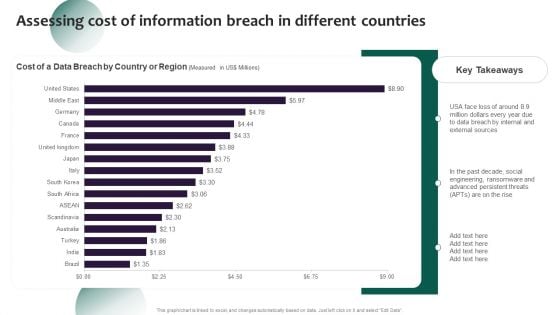
Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Key Takeaways, Countries, Region and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
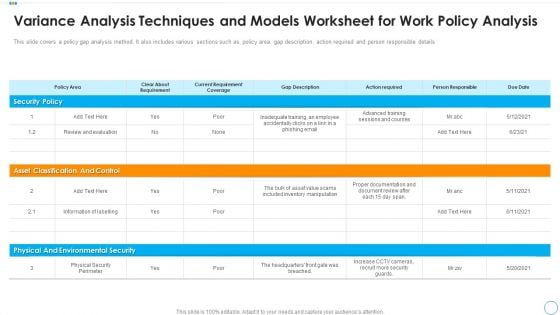
Variance Analysis Techniques And Models Worksheet For Work Policy Analysis Pictures PDF
This slide covers a policy gap analysis method. It also includes various sections such as, policy, gap desareacription, action required and person responsible details. Pitch your topic with ease and precision using this variance analysis techniques and models worksheet for work policy analysis pictures pdf. This layout presents information on security policy, asset classification and control, physical and environmental security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf today and make your presentation stand out from the rest The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc.
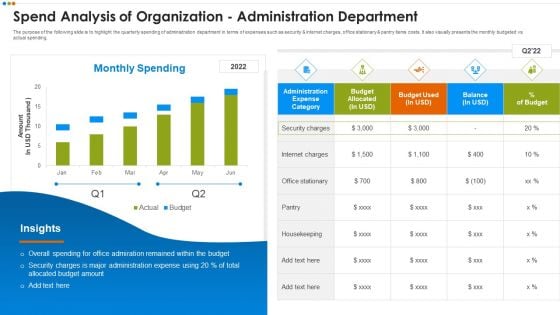
Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending.Deliver an awe inspiring pitch with this creative Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF bundle. Topics like Overall Spending, Admiration Remained, Security Administration Expense can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
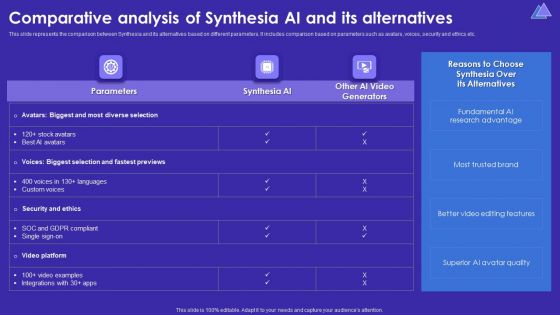
Comparative Analysis Of Synthesia AI And Its Alternatives Summary PDF
This slide represents the comparison between Synthesia and its alternatives based on different parameters. It includes comparison based on parameters such as avatars, voices, security and ethics etc. Slidegeeks is here to make your presentations a breeze with Comparative Analysis Of Synthesia AI And Its Alternatives Summary PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
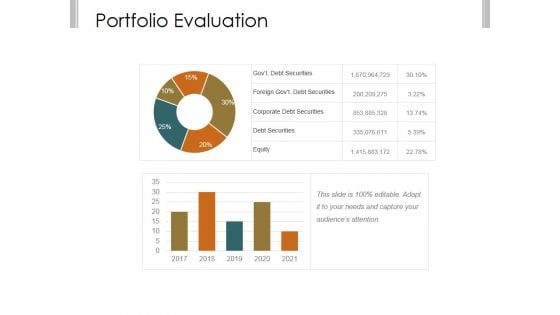
Portfolio Evaluation Ppt PowerPoint Presentation Topics
This is a portfolio evaluation ppt powerpoint presentation topics. This is a five stage process. The stages in this process are govt debt securities, foreign govt debt securities, corporate debt securities, corporate debt securities, equity.
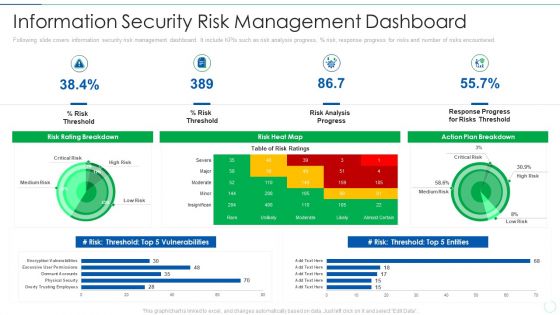
Effective IT Risk Management Process Information Security Risk Management Brochure PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percentage risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative effective it risk management process information security risk management brochure pdf bundle. Topics like analysis, plan, risk, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
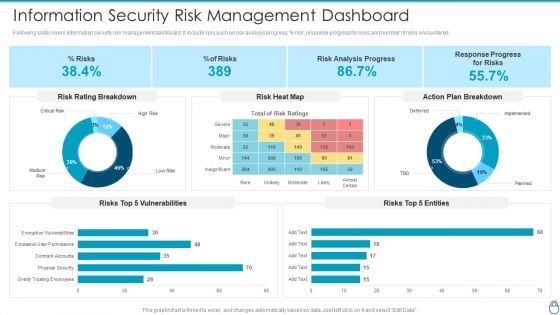
Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Unlocking Potential IoTs Application Overview Of IoT Based Smart Home Security IoT SS V
This slide briefly introduces IoT devices in smart home security with features. It also showcases the components of IoT security systems, such as hardware, software, and communication protocols. Slidegeeks is here to make your presentations a breeze with Unlocking Potential IoTs Application Overview Of IoT Based Smart Home Security IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide briefly introduces IoT devices in smart home security with features. It also showcases the components of IoT security systems, such as hardware, software, and communication protocols.
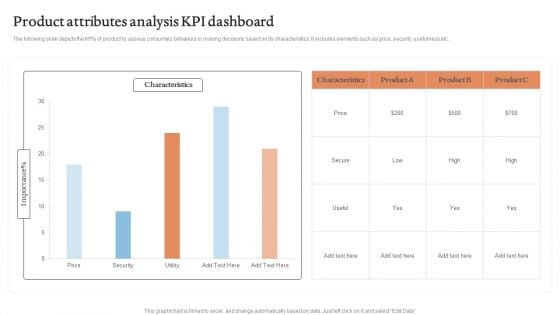
Product Attributes Analysis KPI Dashboard Graphics PDF
The following slide depicts the KPIs of product to assess consumers behaviour in making decisions based on its characteristics. It includes elements such as price, security, usefulness etc.Showcasing this set of slides titled Product Attributes Analysis KPI Dashboard Graphics PDF. The topics addressed in these templates are Characteristics, Product Attributes, Analysis KPI Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Legacy Application Modernization Requirement Analysis Ideas PDF
The purpose of this template is to define the legacy systems need for transition in an organization. It covers information about departments, systems, age, security, etc. Pitch your topic with ease and precision using this Legacy Application Modernization Requirement Analysis Ideas PDF. This layout presents information on Legacy Application, Modernization Requirement Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
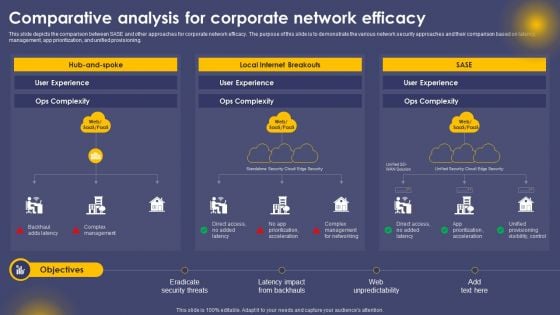
Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF
This slide depicts the comparison between SASE and other approaches for corporate network efficacy. The purpose of this slide is to demonstrate the various network security approaches and their comparison based on latency, management, app prioritization, and unified provisioning. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
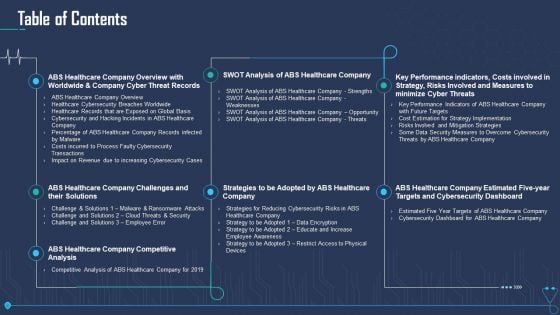
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Table Of Contents Guidelines PDF
Deliver an awe inspiring pitch with this creative case competition overpower the obstacle of cyber security in medicare table of contents guidelines pdf bundle. Topics like swot analysis of abs healthcare company, abs healthcare company competitive analysis, abs healthcare company challenges and their solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Corporate Security And Risk Management Financial Performance Tracking Dashboard Introduction PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an awe inspiring pitch with this creative corporate security and risk management financial performance tracking dashboard introduction pdf bundle. Topics like revenue and expense trends, receivables analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
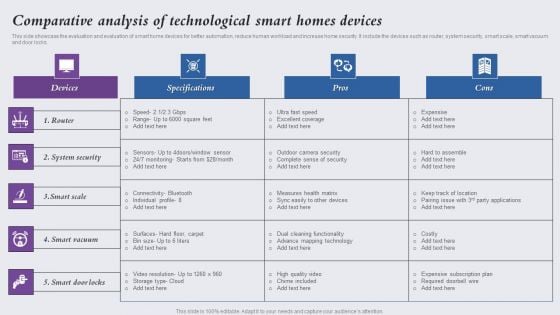
Comparative Analysis Of Technological Smart Homes Devices Information PDF
This side showcase the evaluation and evaluation of smart home devices for better automation, reduce human workload and increase home security. It include the devices such as router, system security, smart scale, smart vacuum and door locks. Showcasing this set of slides titled Comparative Analysis Of Technological Smart Homes Devices Information PDF. The topics addressed in these templates are Router, System Security, Smart Scale. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
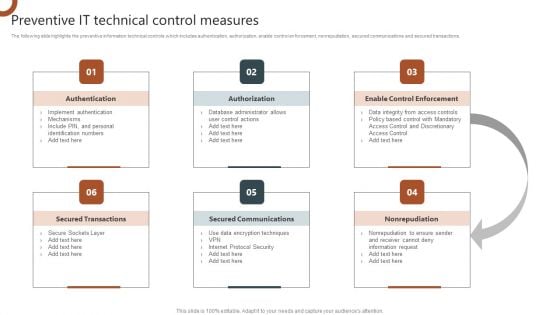
Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Slidegeeks is here to make your presentations a breeze with Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
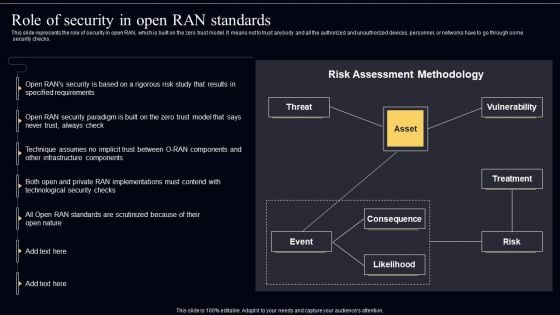
Open Radio Access Network IT Role Of Security In Open RAN Standards Inspiration PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Present like a pro with Open Radio Access Network IT Role Of Security In Open RAN Standards Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
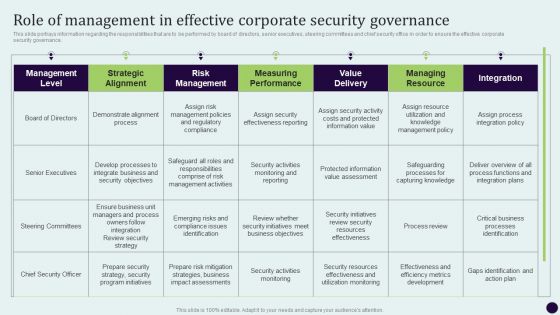
Critical Measures For Ensuring Role Of Management In Effective Corporate Security Themes PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Slidegeeks is here to make your presentations a breeze with Critical Measures For Ensuring Role Of Management In Effective Corporate Security Themes PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
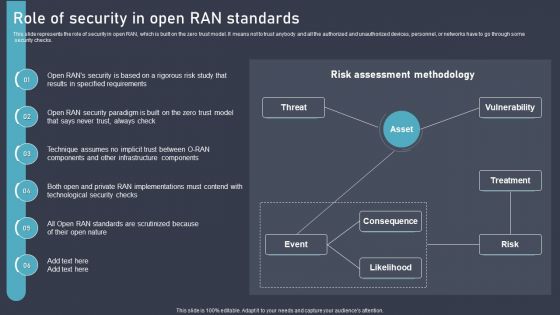
O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

New Website Launch Strategy Website Security Management Action Plan Portrait PDF
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Slidegeeks is here to make your presentations a breeze with New Website Launch Strategy Website Security Management Action Plan Portrait PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Slidegeeks is here to make your presentations a breeze with Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
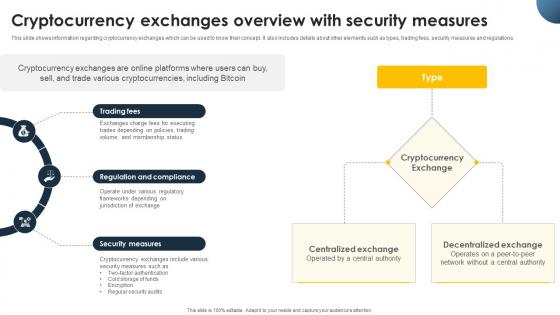
Complete Beginners Guide Cryptocurrency Exchanges Overview With Security Fin SS V
This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Complete Beginners Guide Cryptocurrency Exchanges Overview With Security Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations.
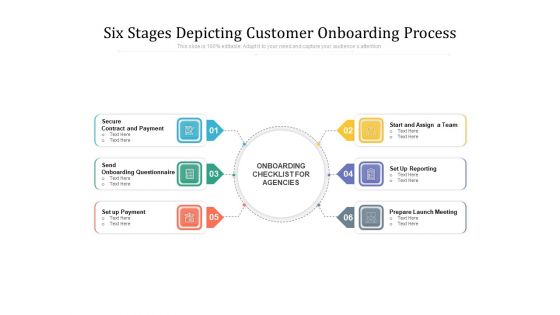
Six Stages Depicting Customer Onboarding Process Ppt PowerPoint Presentation Summary Layout PDF
Presenting six stages depicting customer onboarding process ppt powerpoint presentation summary layout pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including secure contract and payment, send onboarding questionnaire, set up payment, start and assign a team, set up reporting, prepare launch meeting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
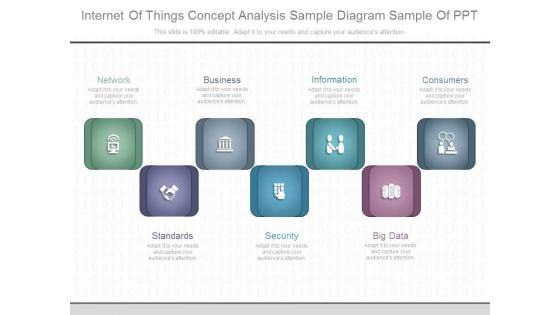
Internet Of Things Concept Analysis Sample Diagram Sample Of Ppt
This is a internet of things concept analysis sample diagram sample of ppt. This is a seven stage process. The stages in this process are network, business, information, consumers, standards, security, big data.
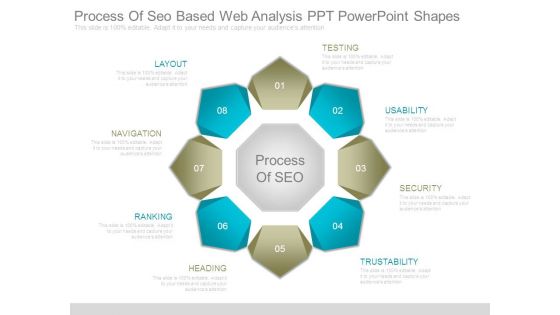
Process Of Seo Based Web Analysis Ppt Powerpoint Shapes
This is a process of seo based web analysis ppt powerpoint shapes. This is a eight stage process. The stages in this process are testing, usability, security, trustability, heading, ranking, navigation, layout, process of seo.
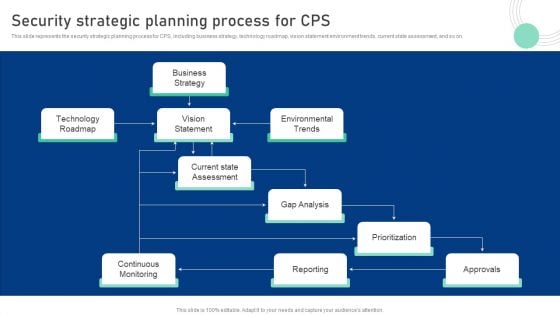
Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
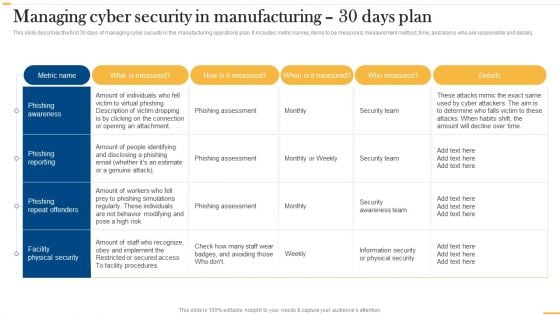
Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Slidegeeks is here to make your presentations a breeze with Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
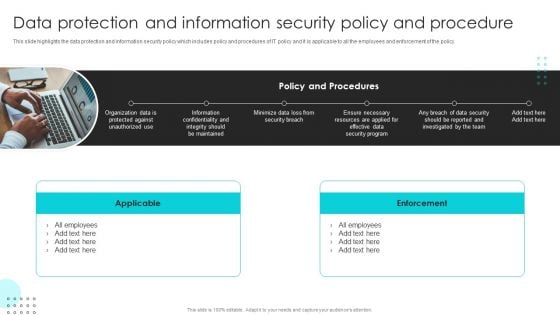
Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Slidegeeks is here to make your presentations a breeze with Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
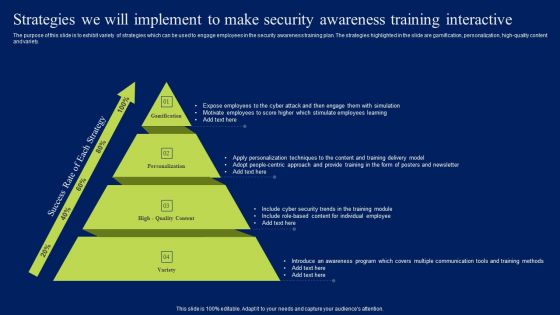
Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Slidegeeks is here to make your presentations a breeze with Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
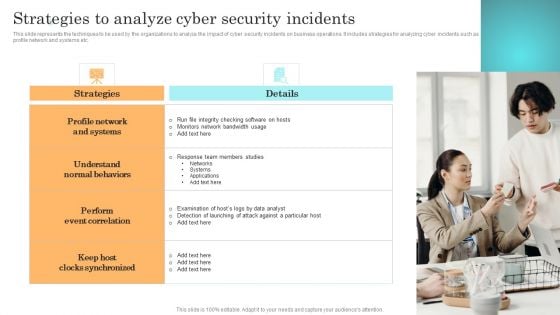
Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
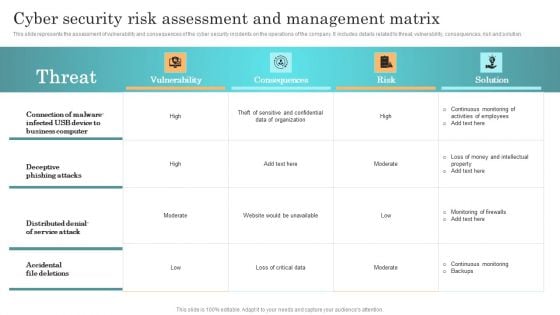
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF
The following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is here to make your presentations a breeze with Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Secure Web Gateways SWG Setup And Working Ppt Show Tips PDF
This slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Slidegeeks is here to make your presentations a breeze with Secure Web Gateways SWG Setup And Working Ppt Show Tips PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
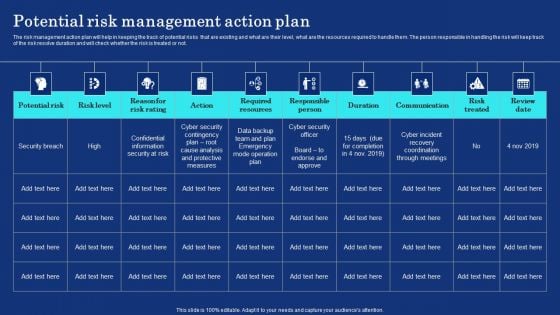
Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF can be your best option for delivering a presentation. Represent everything in detail using Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
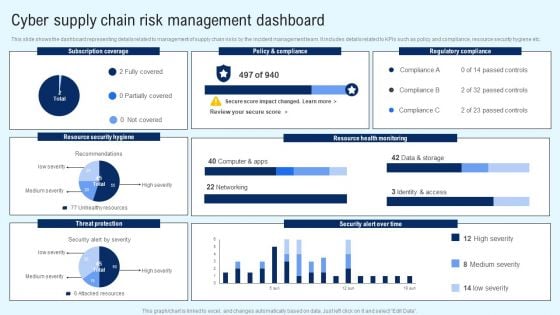
Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
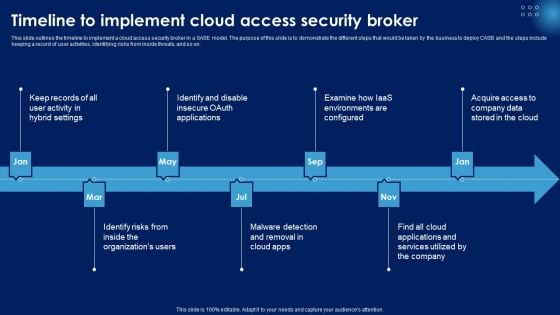
Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
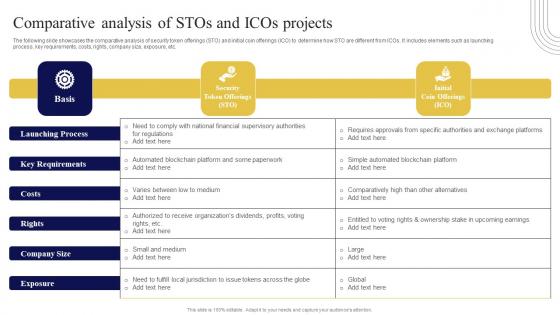
Comparative Analysis Of Stos And Icos Exploring Investment Opportunities Download Pdf
The following slide showcases the comparative analysis of security token offerings STO and initial coin offerings ICO to determine how STO are different from ICOs. It includes elements such as launching process, key requirements, costs, rights, company size, exposure, etc. Slidegeeks is here to make your presentations a breeze with Comparative Analysis Of Stos And Icos Exploring Investment Opportunities Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide showcases the comparative analysis of security token offerings STO and initial coin offerings ICO to determine how STO are different from ICOs. It includes elements such as launching process, key requirements, costs, rights, company size, exposure, etc.
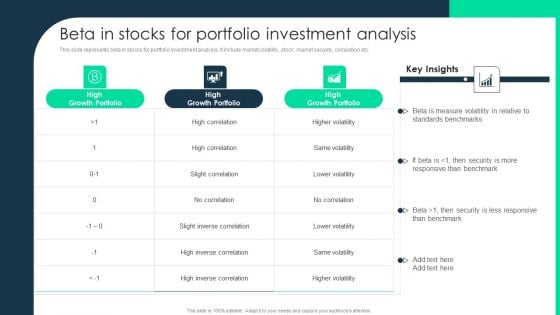
Beta In Stocks For Portfolio Investment Analysis Rules PDF
This slide represents beta in stocks for portfolio investment analysis. It include market volatility, stock, market security, correlation etc. Deliver an awe inspiring pitch with this creative Beta In Stocks For Portfolio Investment Analysis Rules PDF bundle. Topics like High Growth Portfolio, Security, Measure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
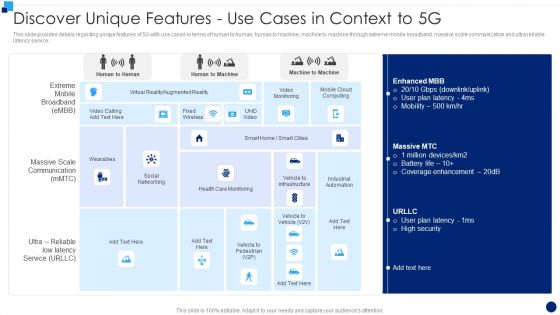
Developing 5G Wireless Cellular Network Discover Unique Features Use Cases In Context To 5G Pictures PDF
This slide provides details regarding unique features of 5G with use cases in terms of human to human, human to machine, machine to machine through extreme mobile broadband, massive scale communication and ultra reliable latency service. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Discover Unique Features Use Cases In Context To 5G Pictures PDF bundle. Topics like Plan, Security, Social Networking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
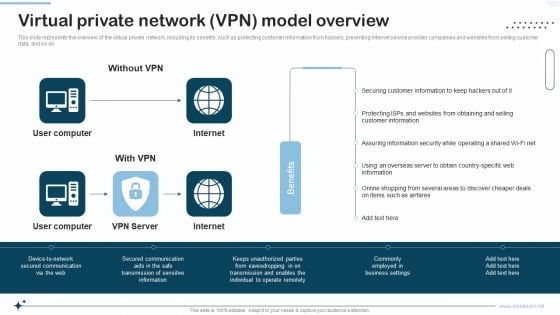
Naas Integrated Solution IT Virtual Private Network VPN Model Overview Designs PDF
This slide represents the overview of the virtual private network, including its benefits, such as protecting customer information from hackers, preventing internet service provider companies and websites from selling customer data, and so on. Deliver an awe inspiring pitch with this creative Naas Integrated Solution IT Virtual Private Network VPN Model Overview Designs PDF bundle. Topics like Secured Communication, Business, Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
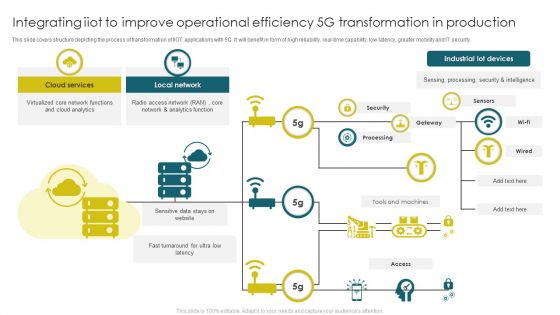
Integrating Iiot To Improve Operational Efficiency 5G Transformation In Production Clipart PDF
This slide covers structure depicting the process of transformation of IIOT applications with 5G. It will benefit in form of high reliability, real time capability, low latency, greater mobility and IT security. Showcasing this set of slides titled Integrating Iiot To Improve Operational Efficiency 5G Transformation In Production Clipart PDF. The topics addressed in these templates are Cloud Services, Local Network, Industrial Lot Devices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
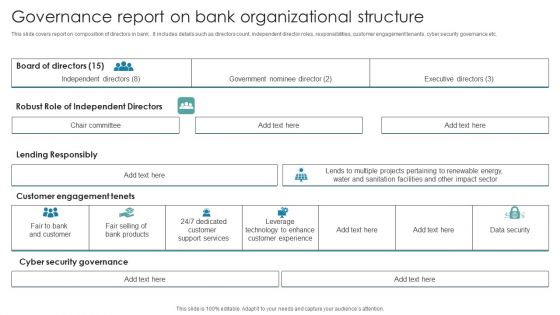
Governance Report On Bank Organizational Structure Slides PDF
This slide covers report on composition of directors in bank . It includes details such as directors count, independent director roles, responsibilities, customer engagement tenants, cyber security governance etc. Showcasing this set of slides titled Governance Report On Bank Organizational Structure Slides PDF. The topics addressed in these templates are Executive Directors, Leverage Technology, Customer Support Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
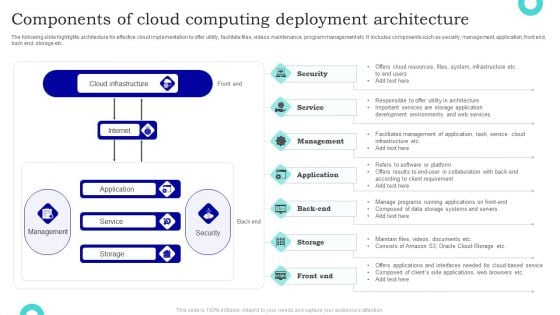
Components Of Cloud Computing Deployment Architecture Sample PDF
The following slide highlights architecture for effective cloud implementation to offer utility, facilitate files, videos maintenance, program management etc. It includes components such as security, management, application, front end, back end, storage etc. Pitch your topic with ease and precision using this Components Of Cloud Computing Deployment Architecture Sample PDF. This layout presents information on Cloud Infrastructure, Application, Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
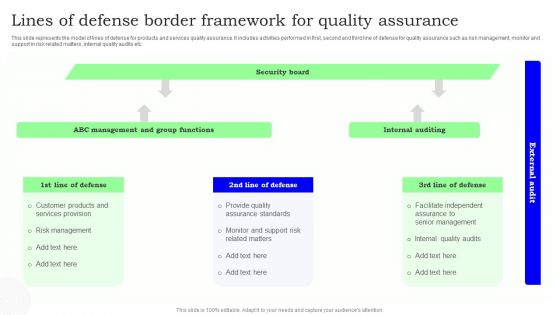
Lines Of Defense Border Framework For Quality Assurance Topics PDF
This slide represents the model of lines of defense for products and services quality assurance. It includes activities performed in first, second and third line of defense for quality assurance such as risk management, monitor and support in risk related matters, internal quality audits etc. Showcasing this set of slides titled Lines Of Defense Border Framework For Quality Assurance Topics PDF. The topics addressed in these templates are Security Board, Internal Auditing, Assurance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Devops Engineer Capabilities Software Security Skills Ppt Slides Graphics Template PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. This is a devops engineer capabilities software security skills ppt slides graphics template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vulnerability management, threat investigation, compliance monitoring, security training, code analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
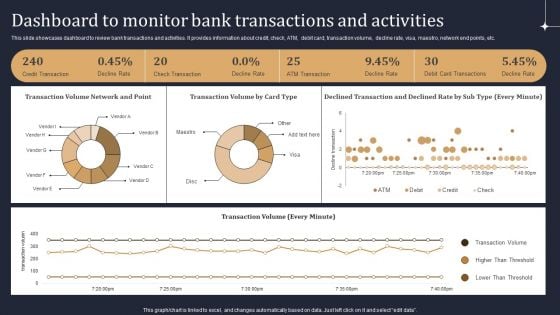
KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF
This slide showcases dashboard to review bank transactions and activities. It provides information about credit, check, ATM, debit card, transaction volume, decline rate, visa, maestro, network end points, etc. This KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Organizational Assets Security Management Strategy Evaluating Financial Practices In Firm Formats PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Slidegeeks is here to make your presentations a breeze with Organizational Assets Security Management Strategy Evaluating Financial Practices In Firm Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
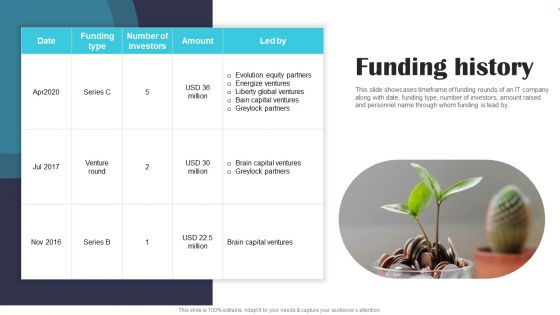
Security Software Company Investor Funding Pitch Deck Funding History Portrait PDF
This slide showcases timeframe of funding rounds of an IT company along with date, funding type, number of investors, amount raised and personnel name through whom funding is lead by. Slidegeeks is here to make your presentations a breeze with Security Software Company Investor Funding Pitch Deck Funding History Portrait PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf
The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Slidegeeks is here to make your presentations a breeze with Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc.

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.

Complete Beginners Guide Cold Wallets For Enhancing Bitcoin Security Fin SS V
This slide shows information regarding cold wallets which can be used by Bitcoin holders. It also includes types of cold crypto wallets which are hardware wallets and paper wallets. Slidegeeks is here to make your presentations a breeze with Complete Beginners Guide Cold Wallets For Enhancing Bitcoin Security Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows information regarding cold wallets which can be used by Bitcoin holders. It also includes types of cold crypto wallets which are hardware wallets and paper wallets.

Security Information And Event Management Strategies For Financial Audit And Compliance SIM Vs SEM Vs SIEM Sample PDF
Presenting security information and event management strategies for financial audit and compliance sim vs sem vs siem sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
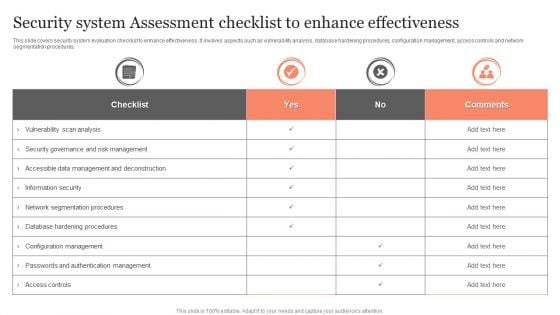
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
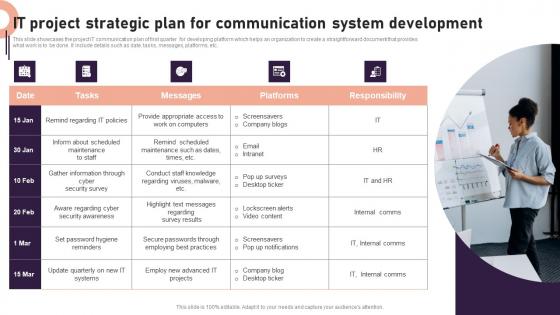
IT Project Strategic Plan For Communication System Development Structure Pdf
This slide showcases the project IT communication plan of first quarter for developing platform which helps an organization to create a straightforward document that provides what work is to be done. It include details such as date, tasks, messages, platforms, etc. Pitch your topic with ease and precision using this IT Project Strategic Plan For Communication System Development Structure Pdf. This layout presents information on Cyber Security Survey, IT Systems, Communication System Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the project IT communication plan of first quarter for developing platform which helps an organization to create a straightforward document that provides what work is to be done. It include details such as date, tasks, messages, platforms, etc.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































