Safety Inspection

Iot Integration In Manufacturing Digital Twin Technology Supply Chain Management Slides PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Iot Integration In Manufacturing Digital Twin Technology Supply Chain Management Slides PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
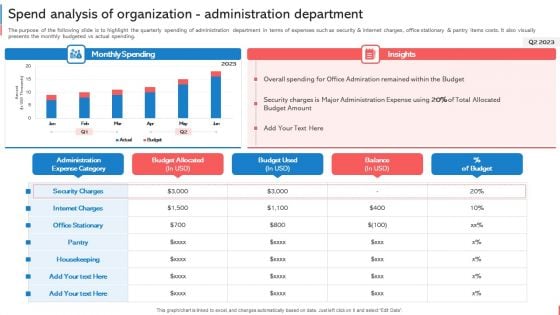
Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending. This Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF
This slide represents the official announcement from lotem finkelstein, head of threat intelligence at check point software, that anyone can join ukraine and russia cyber warfare. Slidegeeks is here to make your presentations a breeze with Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Optimization Of IoT Remote Monitoring Types Of Smart Home Automation System Devices IoT SS V
This slide provides an overview of smart home devices. Major devices covered are smart thermostats, locks, doorbells, security, motion smoke detection, water, alarm, lighting, speakers, displays, plugs, vacuum and HVAC systems. Slidegeeks is here to make your presentations a breeze with Optimization Of IoT Remote Monitoring Types Of Smart Home Automation System Devices IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides an overview of smart home devices. Major devices covered are smart thermostats, locks, doorbells, security, motion smoke detection, water, alarm, lighting, speakers, displays, plugs, vacuum and HVAC systems.

CASB 2 0 IT Reverse Proxy CASB Deployment Model
This slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit CASB 2 0 IT Reverse Proxy CASB Deployment Model and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers.
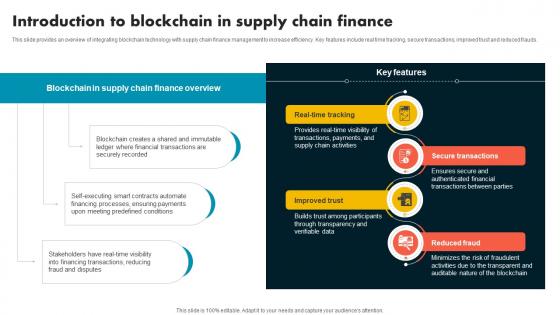
Introduction To Blockchain In Supply Chain Finance Supply Chain Evolution Harnessing The Power BCT SS V
This slide provides an overview of integrating blockchain technology with supply chain finance management to increase efficiency. Key features include real time tracking, secure transactions, improved trust and reduced frauds. Slidegeeks is here to make your presentations a breeze with Introduction To Blockchain In Supply Chain Finance Supply Chain Evolution Harnessing The Power BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides an overview of integrating blockchain technology with supply chain finance management to increase efficiency. Key features include real time tracking, secure transactions, improved trust and reduced frauds.
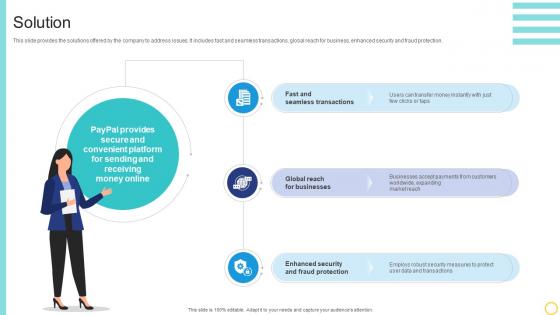
Solution Online Transaction Facilitator Business Model BMC SS V
This slide provides the solutions offered by the company to address issues. It includes fast and seamless transactions, global reach for business, enhanced security and fraud protection. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Online Transaction Facilitator Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides the solutions offered by the company to address issues. It includes fast and seamless transactions, global reach for business, enhanced security and fraud protection.
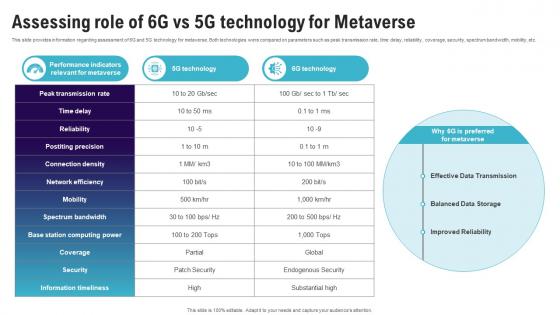
Assessing Role Of 6G Vs 5G Technology For Metaverse Continuum Of Technology Revamping Business AI SS V
This slide provides information regarding assessment of 6G and 5G technology for metaverse. Both technologies were compared on parameters such as peak transmission rate, time delay, reliability, coverage, security, spectrum bandwidth, mobility, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Assessing Role Of 6G Vs 5G Technology For Metaverse Continuum Of Technology Revamping Business AI SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides information regarding assessment of 6G and 5G technology for metaverse. Both technologies were compared on parameters such as peak transmission rate, time delay, reliability, coverage, security, spectrum bandwidth, mobility, etc.
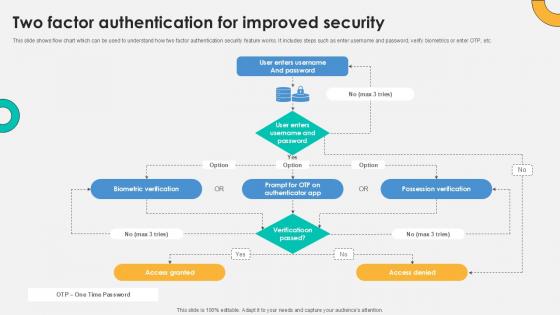
Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
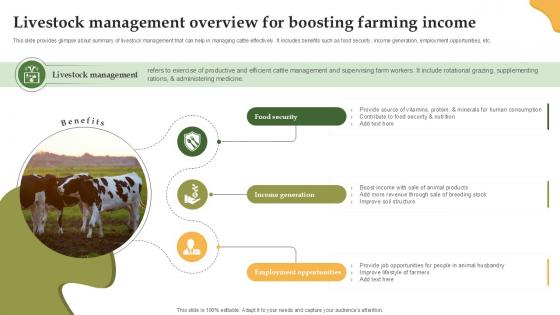
Livestock Management Overview Enhancing Productivity With Adoption PPT Slide
This slide provides glimpse about summary of livestock management that can help in managing cattle effectively. It includes benefits such as food security, income generation, employment opportunities, etc. Slidegeeks is here to make your presentations a breeze with Livestock Management Overview Enhancing Productivity With Adoption PPT Slide With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides glimpse about summary of livestock management that can help in managing cattle effectively. It includes benefits such as food security, income generation, employment opportunities, etc.

Airtable Capital Funding Pitch Deck Our Solution Microsoft PDF
This slide covers key solutions offered by cloud based software company. It involves solutions such as transform workflows with AI, build on flexible data model and offers data security and compliance. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Airtable Capital Funding Pitch Deck Our Solution Microsoft PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
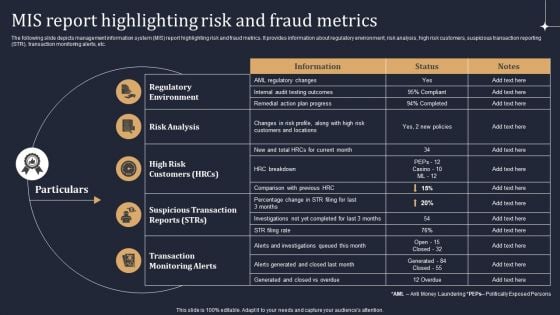
KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF
The following slide depicts management information system MIS report highlighting risk and fraud metrics. It provides information about regulatory environment, risk analysis, high risk customers, suspicious transaction reporting STR, transaction monitoring alerts, etc. Retrieve professionally designed KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Merchandising Industry Analysis Retail Price Management Goals Graphics PDF
Presenting merchandising industry analysis retail price management goals graphics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like enterprise wide price transparency, price monitoring and analysis, system wide security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
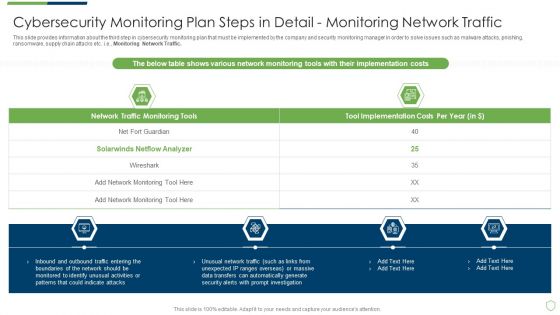
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
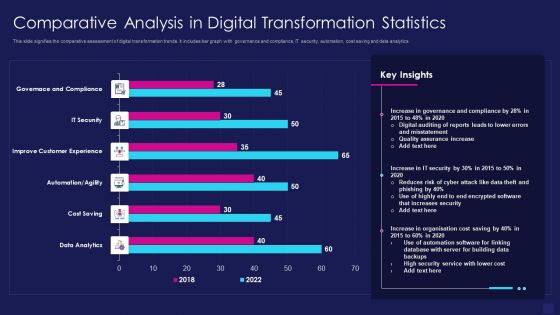
Comparative Analysis In Digital Transformation Statistics Graphics PDF
This slide signifies the comparative assessment of digital transformation trends. It includes bar graph with governance and compliance, IT security, automation, cost saving and data analytics. Showcasing this set of slides titled comparative analysis in digital transformation statistics graphics pdf. The topics addressed in these templates are data analytics, cost saving, improve customer experience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
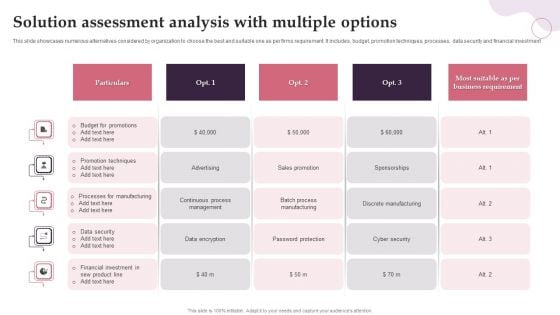
Solution Assessment Analysis With Multiple Options Sample PDF
This slide showcases numerous alternatives considered by organization to choose the best and suitable one as per firms requirement. It includes, budget, promotion techniques, processes, data security and financial investment. Showcasing this set of slides titled Solution Assessment Analysis With Multiple Options Sample PDF. The topics addressed in these templates are Budget, Manufacturing, Promotion Techniques. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
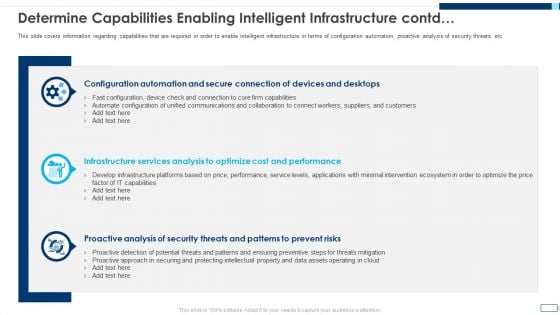
Evolving BI Infrastructure Determine Capabilities Enabling Intelligent Infrastructure Contd Template PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. This is a evolving bi infrastructure determine capabilities enabling intelligent infrastructure contd template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configuration automation, infrastructure services analysis, proactive analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Diversified Profitable Portfolio Beta In Stocks For Portfolio Investment Analysis Elements PDF
This slide represents beta in stocks for portfolio investment analysis. It include market volatility, stock, market security, correlation etc. Deliver and pitch your topic in the best possible manner with this Diversified Profitable Portfolio Beta In Stocks For Portfolio Investment Analysis Elements PDF. Use them to share invaluable insights on Measure Volatility, Security, Portfolio Investment Analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Seamless Integration The Power Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Seamless Integration The Power Comparative Analysis Of Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases.

Understanding Various Blockchain Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. Present like a pro with Understanding Various Blockchain Comparative Analysis Of Blockchain Interoperability BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases.
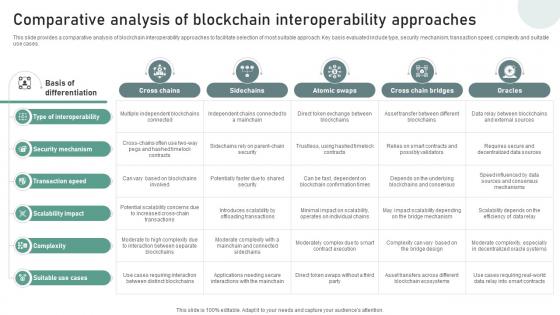
Bridging Blockchains A Deep Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Bridging Blockchains A Deep Comparative Analysis Of Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases.
Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics.

Comparative Analysis Health Healthcare Information Tech To Enhance Medical Facilities Diagrams Pdf
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Health Healthcare Information Tech To Enhance Medical Facilities Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Health Healthcare Information Tech To Enhance Medical Facilities Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics.
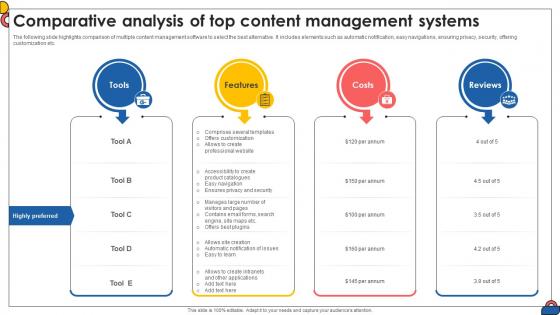
Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.

Risk Management For Organization Essential Assets Impact Analysis For Effective Threat Rules PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative risk management for organization essential assets impact analysis for effective threat rules pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
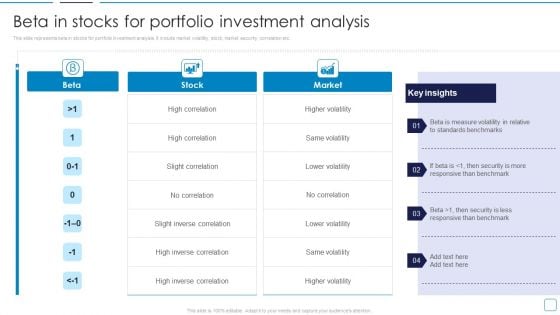
Portfolio Wealth Management Beta In Stocks For Portfolio Investment Analysis Elements PDF
This slide represents beta in stocks for portfolio investment analysis. It include market volatility, stock, market security, correlation etc. Deliver an awe inspiring pitch with this creative Portfolio Wealth Management Beta In Stocks For Portfolio Investment Analysis Elements PDF bundle. Topics like Standards Benchmarks, Security, Stock, Market can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
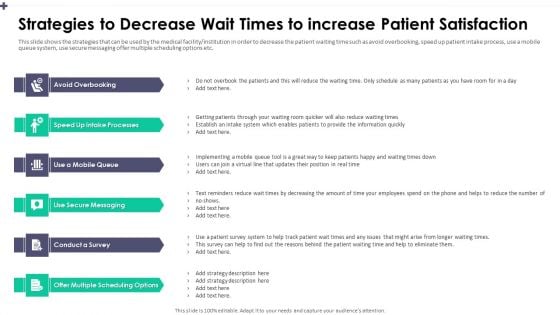
Strategies To Decrease Wait Times To Increase Patient Satisfaction Infographics PDF
This slide shows the strategies that can be used by the medical facility or institution in order to decrease the patient waiting time such as avoid overbooking, speed up patient intake process, use a mobile queue system, use secure messaging offer multiple scheduling options etc.This is a strategies to decrease wait times to increase patient satisfaction infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like avoid overbooking, speed up intake processes, conduct a survey. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. There are so many reasons you need a Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.
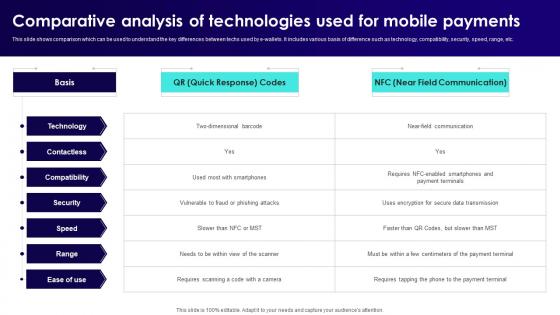
A8 Wireless Banking To Improve Comparative Analysis Of Technologies Used Fin SS V
This slide shows comparison which can be used to understand the key differences between techs used by e-wallets. It includes various basis of difference such as technology, compatibility, security, speed, range, etc. Find a pre-designed and impeccable A8 Wireless Banking To Improve Comparative Analysis Of Technologies Used Fin SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide shows comparison which can be used to understand the key differences between techs used by e-wallets. It includes various basis of difference such as technology, compatibility, security, speed, range, etc.
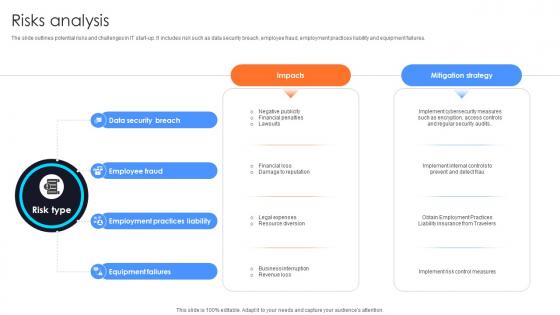
Risks Analysis Information Technology Startup Go To Market Strategy GTM SS V
The slide outlines potential risks and challenges in IT start-up. It includes risk such as data security breach, employee fraud, employment practices liability and equipment failures.This modern and well-arranged Risks Analysis Information Technology Startup Go To Market Strategy GTM SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide outlines potential risks and challenges in IT start-up. It includes risk such as data security breach, employee fraud, employment practices liability and equipment failures.
Big Data Architecture Processes Ppt Icon Examples PDF
This slide depicts the processes of big data architecture, and it covers connecting to data sources, data governance, system management, and protecting quality of service. Presenting big data architecture processes ppt icon examples pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like data, systems, networks, analysis, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
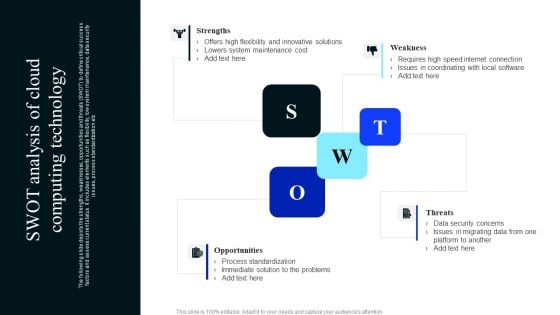
SWOT Analysis Of Cloud Computing Technology Download PDF
The following slide depicts the strengths, weaknesses, opportunities and threats SWOT to define critical success factors and assess current status. It includes elements such as flexibility, low system maintenance, data security issues, process standardization etc. Presenting SWOT Analysis Of Cloud Computing Technology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strengths, Weakness, Threats, Opportunities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Tools Corporate Vulnerability Analysis In The Organization Guidelines PDF
This slide showcases tools for enterprise vulnerability management helps businesses secure their networks by identifying and fixing issues. It also includes tools such as nessus professional,nexpose community edition, openvas, manageengine vulnerability manager plus, etc. Persuade your audience using this Tools Corporate Vulnerability Analysis In The Organization Guidelines PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Organizations Environment, Limitless Evaluation, Implement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
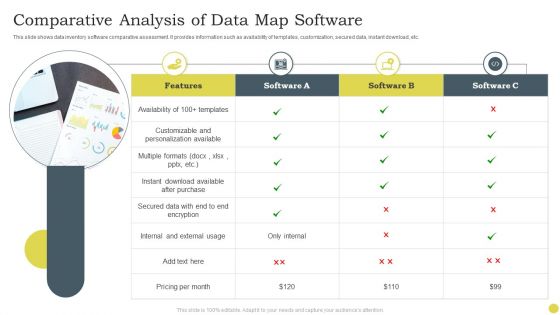
Comparative Analysis Of Data Map Software Ppt PowerPoint Presentation File Objects PDF
This slide shows data inventory software comparative assessment. It provides information such as availability of templates, customization, secured data, instant download, etc. Presenting Comparative Analysis Of Data Map Software Ppt PowerPoint Presentation File Objects PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Multiple Formats, Secured Data, External Usage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Resources And Training That Companies Man In The Middle Phishing IT
This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if youve already been breached, be aware of the various phishing attacks, invest in security education, etc. Find highly impressive Resources And Training That Companies Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Resources And Training That Companies Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if youve already been breached, be aware of the various phishing attacks, invest in security education, etc.

Benefits Of Acquiring Shares Through Investment Agency Template Pdf
The slide showcases major advantages associated with investing through an investment firm. It covers capital cost and allocation, protection against hidden risks, expertise, asset management and secure investment. Showcasing this set of slides titled Benefits Of Acquiring Shares Through Investment Agency Template Pdf. The topics addressed in these templates are Secure Investment, Asset Management, Investment Agency. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases major advantages associated with investing through an investment firm. It covers capital cost and allocation, protection against hidden risks, expertise, asset management and secure investment.
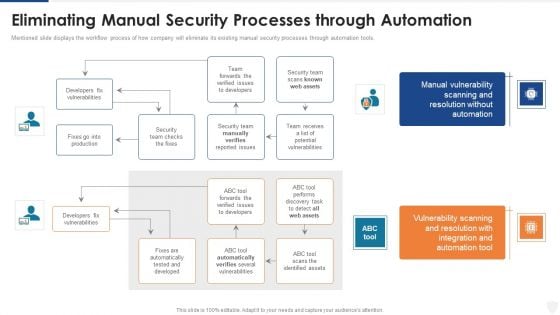
Defining Risk Events Based On Impact Size And Likelihood Of Occurrence Ppt Pictures Background PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this eliminating manual security processes through automation ppt styles images pdf. Use them to share invaluable insights on security, team, production, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF
This slide covers various courses for employees to aware about IT security threats. It includes identification of compliance stands, audit standards, incident trends, organisations security awareness, etc.Showcasing this set of slides titled Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF. The topics addressed in these templates are Compliance Standards, Identify Audit Standards, Security Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
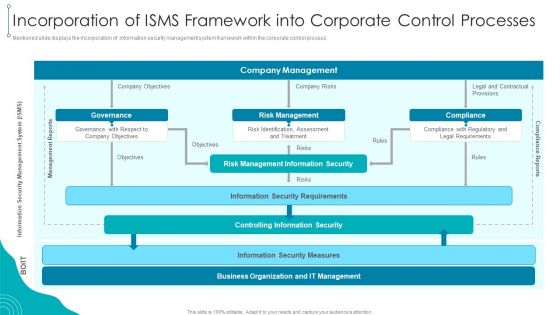
Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF. Use them to share invaluable insights on Management Information, Security Requirements, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
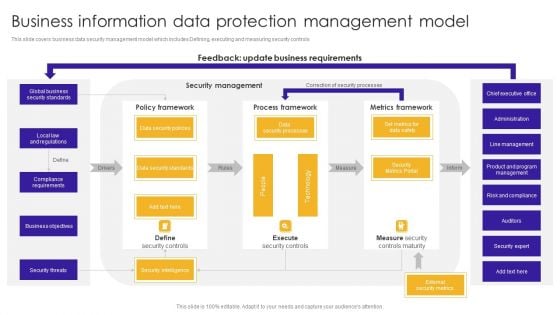
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
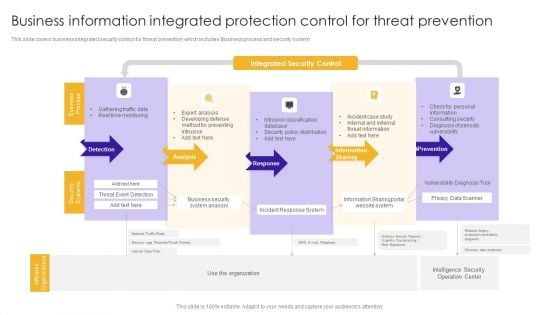
Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
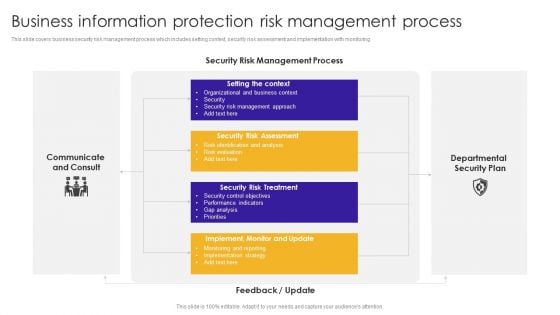
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
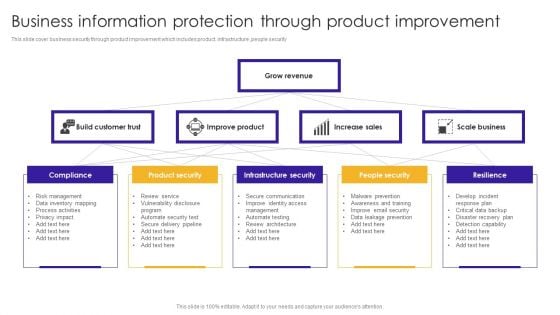
Business Information Protection Through Product Improvement Infographics PDF
This slide cover business security through product improvement which includes product, infrastructure ,people security. Pitch your topic with ease and precision using this Business Information Protection Through Product Improvement Infographics PDF. This layout presents information on Improve Product, Scale Business, Infrastructure Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
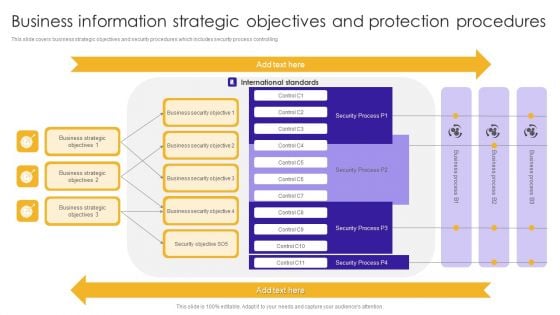
Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
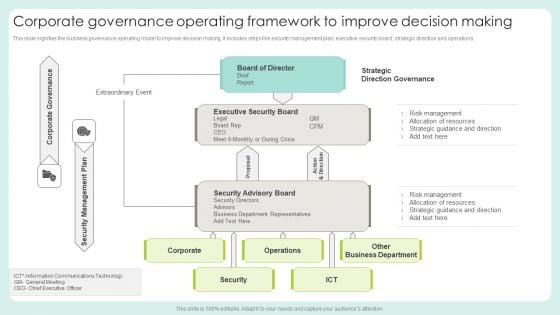
Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
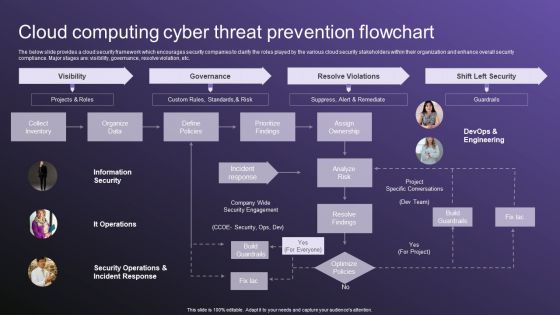
Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
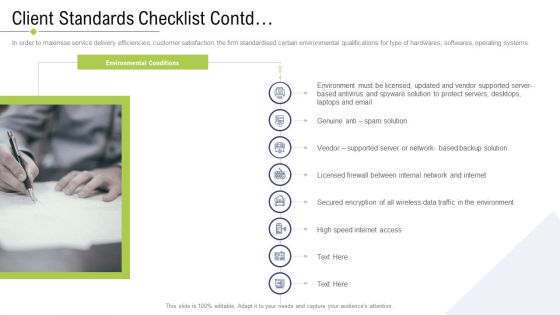
Technology Facility Maintenance And Provider Client Standards Checklist Contd Clipart PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a technology facility maintenance and provider client standards checklist contd clipart pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secured encryption, protect servers, internal network, high speed internet access . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
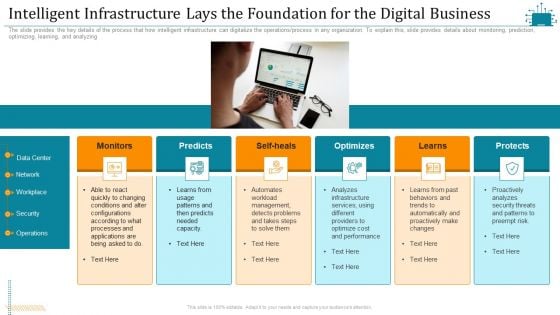
Cloud Intelligence Framework For Application Consumption Intelligent Infrastructure Lays The Foundation For The Digital Business Summary PDF
The slide provides the key details of the process that how intelligent infrastructure can digitalize the operations process in any organization. To explain this, slide provides details about monitoring, prediction, optimizing, learning, and analyzing. Presenting cloud intelligence framework for application consumption intelligent infrastructure lays the foundation for the digital business summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, operations, proactively analyzes, optimize cost and performance, analyzes infrastructure services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download

Developing 5G Wireless Cellular Network Determine Various Business Models For 5G Operators Structure PDF
This slide provides details regarding various business models for 5G operators such as subscription model, bundling model, usage based model and differentiated pricing model. This is a Developing 5G Wireless Cellular Network Determine Various Business Models For 5G Operators Structure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Revenue Stream, Security, Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
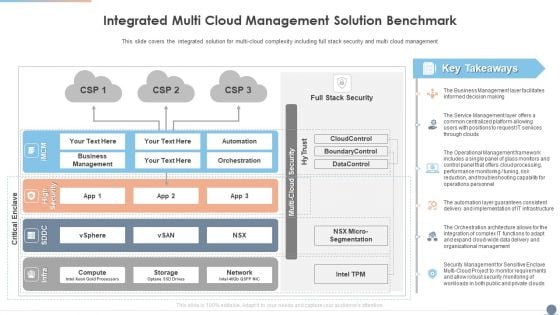
Multi Cloud Complexity Management Integrated Multi Cloud Management Solution Benchmark Elements PDF
This slide covers the integrated solution for multi cloud complexity including full stack security and multi cloud management. Presenting Multi Cloud Complexity Management Integrated Multi Cloud Management Solution Benchmark Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Business Management, Network, Service Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

RPA As A Integration Factors For Business Processes Portrait PDF
Following Slide Covers Various Factors Associated With Robotic Process Automation As Service. Purpose Of This Slide Is To Understand The Role Of Automation In Business Efficiency And Cost Reduction. It Includes Factors Such As Platforms, Security. Maintenance Etc. With Description And Impact Persuade your audience using this RPA As A Integration Factors For Business Processes Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Factors, Description, Impact. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Drivers For SASE Adoption Ppt Styles Visual Aids PDF
This slide outlines the critical drivers for secure access service edge adoption. This slide aims to demonstrate the key drivers that boost SASE adoption among different organizations, including cloud adoption, increased flexibility and agility, cost-effective network traffic management, etc. There are so many reasons you need a Key Drivers For SASE Adoption Ppt Styles Visual Aids PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
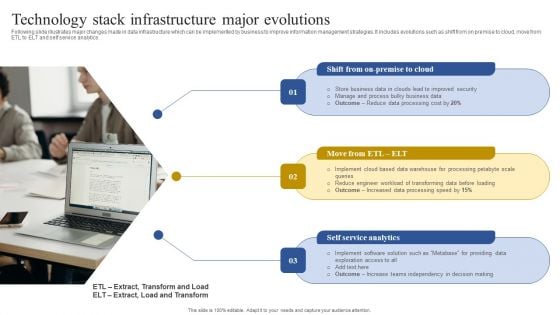
Technology Stack Infrastructure Major Evolutions Download PDF
Following slide illustrates major changes made in data infrastructure which can be implemented by business to improve information management strategies. It includes evolutions such as shift from on premise to cloud, move from ETL to ELT and self service analytics. Persuade your audience using this Technology Stack Infrastructure Major Evolutions Download PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Business Data, Improved Security, Processing Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
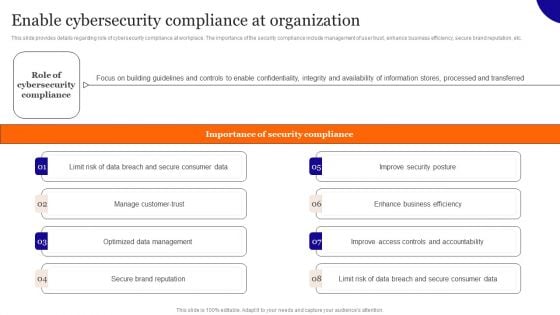
Enable Cybersecurity Compliance At Organization Mockup PDF
This slide provides details regarding role of cybersecurity compliance at workplace. The importance of the security compliance include management of user trust, enhance business efficiency, secure brand reputation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Enable Cybersecurity Compliance At Organization Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Why CASB Is Important For Businesses Ppt PowerPoint Presentation File Example File PDF
This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Why CASB Is Important For Businesses Ppt PowerPoint Presentation File Example File PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
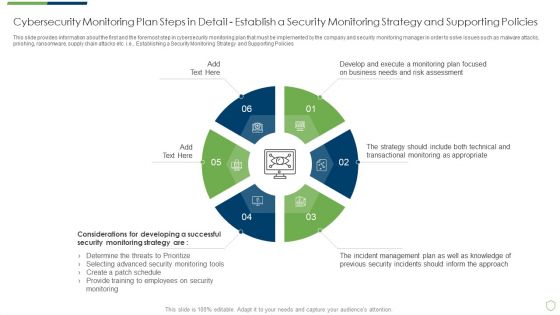
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
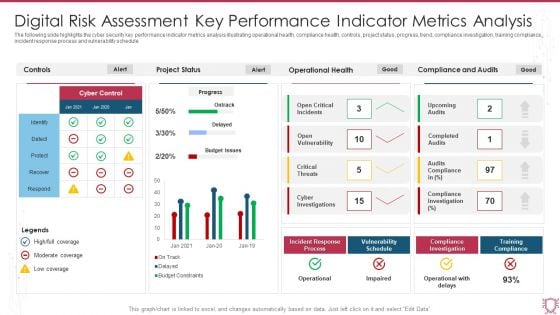
Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF
The following slide highlights the cyber security key performance indicator metrics analysis illustrating operational health, compliance health, controls, project status, progress, trend, compliance investigation, training compliance, incident response process and vulnerability schedule. Showcasing this set of slides titled Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF. The topics addressed in these templates are Project Status, Operational Health, Compliance And Audits. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
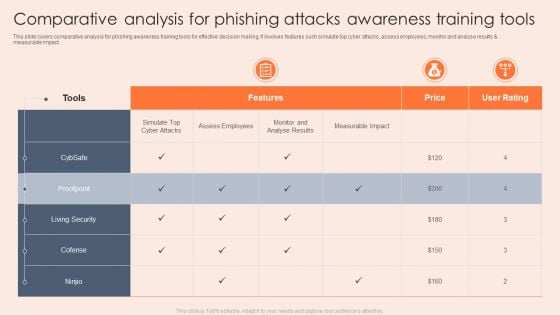
Comparative Analysis For Phishing Attacks Awareness Training Tools Rules PDF
This slide covers comparative analysis for phishing awareness training tools for effective decision making. It involves features such simulate top cyber attacks, assess employees, monitor and analyse results and measurable impact. Showcasing this set of slides titled Comparative Analysis For Phishing Attacks Awareness Training Tools Rules PDF. The topics addressed in these templates are Analyse Results, Measurable Impact, Living Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
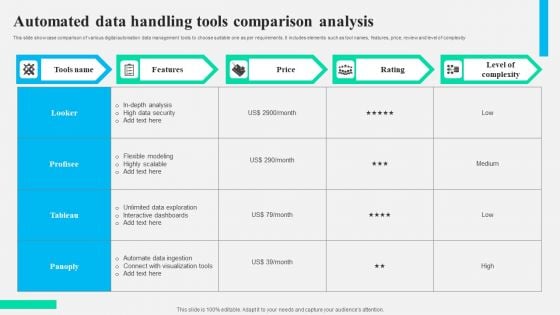
Automated Data Handling Tools Comparison Analysis Formats PDF
This slide showcase comparison of various digital automation data management tools to choose suitable one as per requirements. It includes elements such as tool names, features, price, review and level of complexity. Showcasing this set of slides titled Automated Data Handling Tools Comparison Analysis Formats PDF. The topics addressed in these templates are High Data Security, Analysis, Interactive Dashboards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
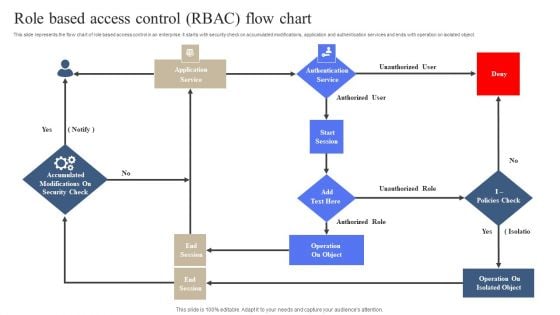
Role Based Access Control RBAC Flow Chart Slides PDF
This slide represents the flow chart of role based access control in an enterprise. It starts with security check on accumulated modifications, application and authentication services and ends with operation on isolated object. Persuade your audience using this Role Based Access Control RBAC Flow Chart Slides PDF. This PPT design covers One stage, thus making it a great tool to use. It also caters to a variety of topics including Operation On Object, Operation On Isolated Object. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































