Safety Management Strategy Ppt

Ways To Create Devsecops Culture In Organization Role Of Devsecops Ppt Powerpoint
This slide showcases the way to develop a DevSecOps culture in an organization. The purpose of this slide is to discuss the methods to create a DevSecOps culture these include the value of security, early detection of vulnerabilities, small iterations, inclusive collaboration, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Ways To Create Devsecops Culture In Organization Role Of Devsecops Ppt Powerpoint and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the way to develop a DevSecOps culture in an organization. The purpose of this slide is to discuss the methods to create a DevSecOps culture these include the value of security, early detection of vulnerabilities, small iterations, inclusive collaboration, etc.
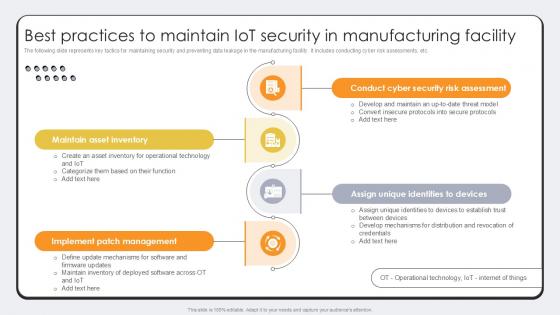
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
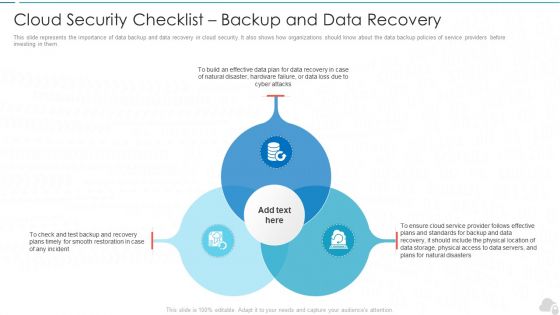
Cloud Security Checklist Backup And Data Recovery Cloud Computing Security IT Ppt Styles Rules PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting cloud security checklist backup and data recovery cloud computing security it ppt styles rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like effective, cloud service, natural disasters, data plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
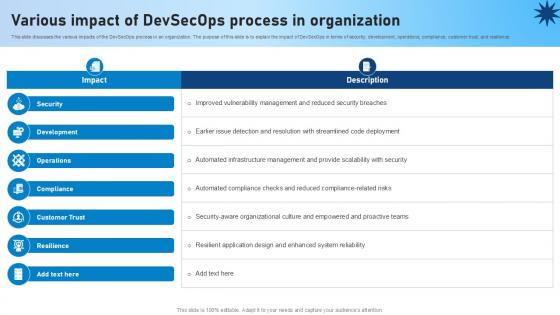
Various Impact Of Devsecops Process In Organization Role Of Devsecops Ppt Slide
This slide discusses the various impacts of the DevSecOps process in an organization. The purpose of this slide is to explain the impact of DevSecOps in terms of security, development, operations, compliance, customer trust, and resilience. If you are looking for a format to display your unique thoughts, then the professionally designed Various Impact Of Devsecops Process In Organization Role Of Devsecops Ppt Slide is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Various Impact Of Devsecops Process In Organization Role Of Devsecops Ppt Slide and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide discusses the various impacts of the DevSecOps process in an organization. The purpose of this slide is to explain the impact of DevSecOps in terms of security, development, operations, compliance, customer trust, and resilience.
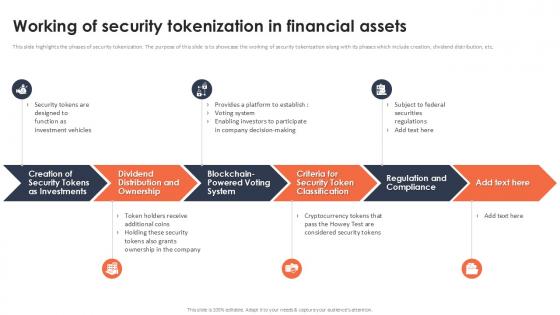
Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc.

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
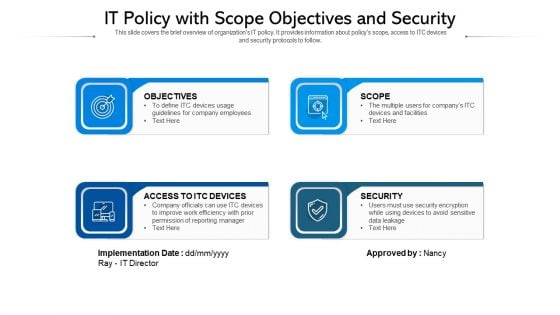
IT Policy With Scope Objectives And Security Ppt PowerPoint Presentation Infographics Show PDF
This slide covers the brief overview of organizations IT policy. It provides information about policys scope, access to ITC devices and security protocols to follow. Persuade your audience using this IT policy with scope objectives and security ppt powerpoint presentation infographics show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including objectives, access to itc devices, security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
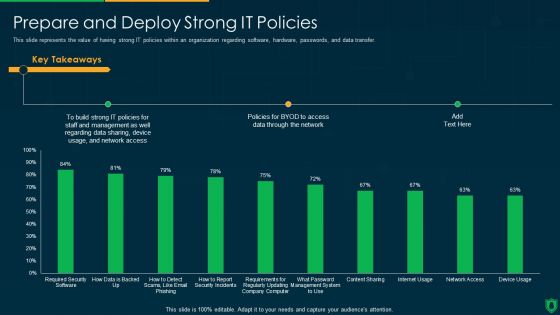
Info Security Prepare And Deploy Strong IT Policies Ppt PowerPoint Presentation File Model PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative info security prepare and deploy strong it policies ppt powerpoint presentation file model pdf bundle. Topics like build strong, it policies, data sharing, access data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
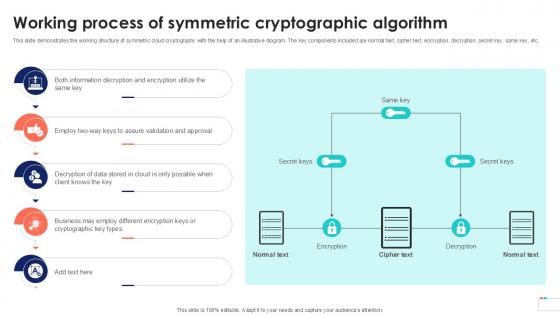
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.

Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. Slidegeeks is here to make your presentations a breeze with Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.
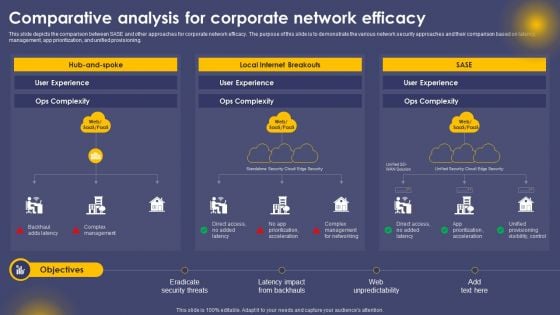
Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF
This slide depicts the comparison between SASE and other approaches for corporate network efficacy. The purpose of this slide is to demonstrate the various network security approaches and their comparison based on latency, management, app prioritization, and unified provisioning. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
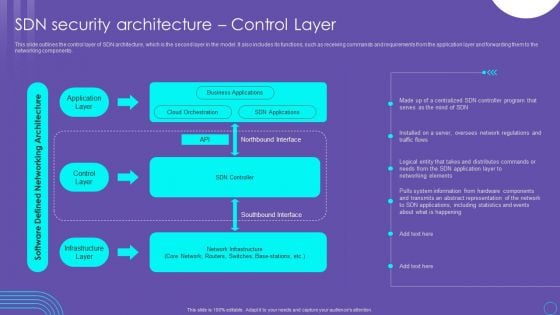
SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. If you are looking for a format to display your unique thoughts, then the professionally designed SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
10 Diverging Stages Planning Process Diagram Ppt Circular Flow Spoke Chart PowerPoint Slides
We present our 10 diverging stages planning process diagram ppt Circular Flow Spoke Chart PowerPoint Slides.Download and present our Arrows PowerPoint Templates because individual components well researched and understood in their place. Download and present our Flow charts PowerPoint Templates because the foundation stones of many a life. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Present our Process and Flows PowerPoint Templates because you can see In any endeavour people matter most. Download and present our Circle charts PowerPoint Templates because you can blaze a brilliant trail from point to point.Use these PowerPoint slides for presentations relating to Business, catalog, chart, circle, concept, conceptual, conference, connection, corporate, description, design, development, diagram, goal, graphic, idea, illustration, item, management, marketing, mind, mind map, model, navigation, organization, parts, plans, presentation, process, reports, solutions, strategy, success, target. The prominent colors used in the PowerPoint template are Yellow, Black, Gray. You can be sure our 10 diverging stages planning process diagram ppt Circular Flow Spoke Chart PowerPoint Slides are Versatile. Presenters tell us our corporate PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. We assure you our 10 diverging stages planning process diagram ppt Circular Flow Spoke Chart PowerPoint Slides are Chic. Customers tell us our connection PowerPoint templates and PPT Slides are Spiffy. Presenters tell us our 10 diverging stages planning process diagram ppt Circular Flow Spoke Chart PowerPoint Slides will impress their bosses and teams. You can be sure our conference PowerPoint templates and PPT Slides are Fun. Cross the chasm with our 10 Diverging Stages Planning Process Diagram Ppt Circular Flow Spoke Chart PowerPoint Slides. You will come out on top.
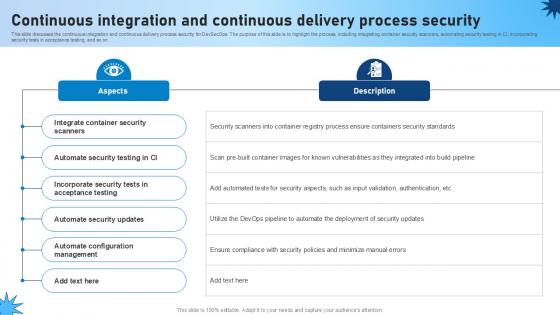
Continuous Integration And Continuous Delivery Process Security Role Of Devsecops Ppt Slide
This slide discusses the continuous integration and continuous delivery process security for DevSecOps. The purpose of this slide is to highlight the process, including integrating container security scanners, automating security testing in CI, incorporating security tests in acceptance testing, and so on. Present like a pro with Continuous Integration And Continuous Delivery Process Security Role Of Devsecops Ppt Slide Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide discusses the continuous integration and continuous delivery process security for DevSecOps. The purpose of this slide is to highlight the process, including integrating container security scanners, automating security testing in CI, incorporating security tests in acceptance testing, and so on.

Benefits Of Devsecops Model In Organization Role Of Devsecops Ppt Example
This slide explains the importance of the DevSecOps model in an organization. The purpose of this slide is to highlight the Benefits these are faster delivery, improved security posture, reduced cost, enhanced value of DevSecOps, improved security integration and peace, etc. Create an editable Benefits Of Devsecops Model In Organization Role Of Devsecops Ppt Example that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Benefits Of Devsecops Model In Organization Role Of Devsecops Ppt Example is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide explains the importance of the DevSecOps model in an organization. The purpose of this slide is to highlight the Benefits these are faster delivery, improved security posture, reduced cost, enhanced value of DevSecOps, improved security integration and peace, etc.

Development And Integration Of Cyber Security Incident Administration Ppt PowerPoint Presentation Complete Deck
Landing corporate business deals can be a huge achievement, both in terms of reputation and finance. This highlights the importance of drafting a comprehensive plan for this business segment that this Development And Integration Of Cyber Security Incident Administration Ppt PowerPoint Presentation Complete Deck does perfectly for you. Given below is a perfectly curated service proposal in Seventy slides that is sure to give your presentation the desired edge. It will display all the details enabling the company to analyze standout components and make an informed decision. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.

Integrating Naas Service Model Naas Shifts Focus From Architectures To Outcomes Ppt Portfolio Maker PDF
This slide represents how the network as a service sifts the focus of businesses from architectures to results. Organizations can cater to changing customer needs with migration to multi-cloud and IT teams can track the impact of changes made on the business. Presenting this PowerPoint presentation, titled Integrating Naas Service Model Naas Shifts Focus From Architectures To Outcomes Ppt Portfolio Maker PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Integrating Naas Service Model Naas Shifts Focus From Architectures To Outcomes Ppt Portfolio Maker PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Integrating Naas Service Model Naas Shifts Focus From Architectures To Outcomes Ppt Portfolio Maker PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Why CASB Is Important For Businesses Ppt PowerPoint Presentation File Example File PDF
This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Why CASB Is Important For Businesses Ppt PowerPoint Presentation File Example File PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
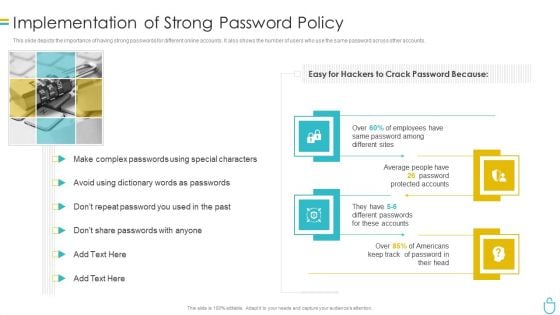
Information Security Implementation Of Strong Password Policy Ppt Styles Brochure PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. This is a information security implementation of strong password policy ppt styles brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation of strong password policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.

Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Presenting Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Implement Policies, Protect Data, Security Procedures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
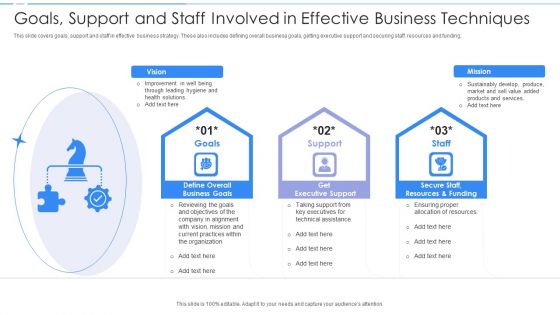
Goals Support And Staff Involved In Effective Business Techniques Ppt PowerPoint Presentation Outline Example PDF
This slide covers goals, support and staff in effective business strategy. These also includes defining overall business goals, getting executive support and securing staff, resources and funding.Showcasing this set of slides titled Goals Support And Staff Involved In Effective Business Techniques Ppt PowerPoint Presentation Outline Example PDF. The topics addressed in these templates are Leading Hygiene, Health Solutions, Improvement Well. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V
This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making. The Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making.
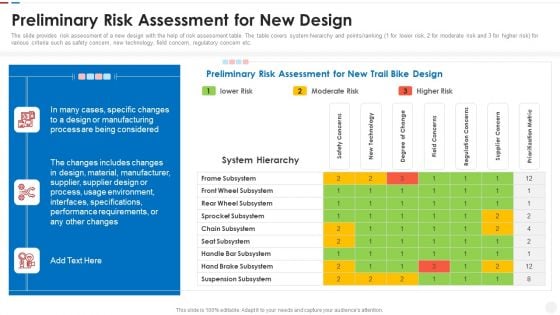
Failure Methods And Effects Assessments FMEA Preliminary Risk Assessment For New Design Ideas PDF
The slide provides risk assessment of a new design with the help of risk assessment table. The table covers system hierarchy and points or ranking 1 for lower risk, 2 for moderate risk and 3 for higher risk for various criteria such as safety concern, new technology, field concern, regulatory concern etc. Deliver an awe inspiring pitch with this creative failure methods and effects assessments fmea preliminary risk assessment for new design ideas pdf bundle. Topics like requirements, environment, performance, process, supplier can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Five Step Roadmap To Implement Application Security Testing Ppt Powerpoint Icons
This slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc. This Five Step Roadmap To Implement Application Security Testing Ppt Powerpoint Icons is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Five Step Roadmap To Implement Application Security Testing Ppt Powerpoint Icons features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc.
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information security define access control measures for employees ppt icon pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
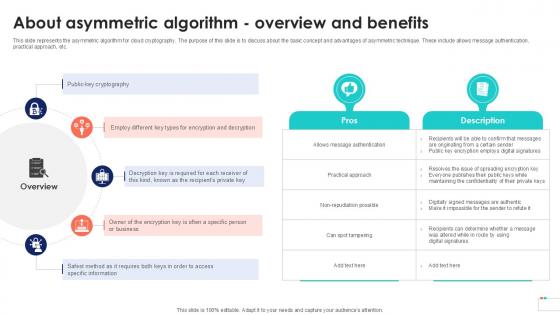
About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Boost your pitch with our creative About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.
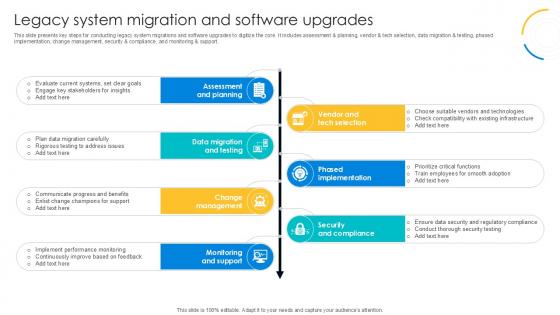
Legacy System Migration And Software Digital Transformation Journey PPT PowerPoint DT SS V
This slide presents key steps for conducting legacy system migrations and software upgrades to digitize the core. It includes assessment and planning, vendor and tech selection, data migration and testing, phased implementation, change management, security and compliance, and monitoring and support. Do you know about Slidesgeeks Vendor And Tech Selection, Phased Implementation, Security And Compliance These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide presents key steps for conducting legacy system migrations and software upgrades to digitize the core. It includes assessment and planning, vendor and tech selection, data migration and testing, phased implementation, change management, security and compliance, and monitoring and support.

Prepare Data Backup For Sensitive Information IT Security IT Ppt Infographics Clipart PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Deliver an awe inspiring pitch with this creative prepare data backup for sensitive information it security it ppt infographics clipart pdf bundle. Topics like manipulation, secure, disasters, cloud services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
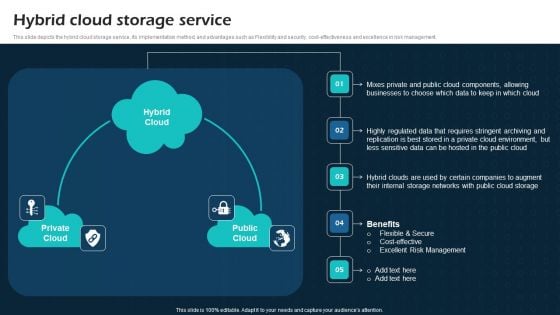
Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF
This slide depicts the hybrid cloud storage service, its implementation method, and advantages such as Flexibility and security, cost effectiveness and excellence in risk management. If you are looking for a format to display your unique thoughts, then the professionally designed Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Protect Your Savings Fom Market PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Protect Your Savings Fom Market PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Money PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Download our Finance PowerPoint Templates because You can Bask in the warmth of our PowerPoint Templates and Slides. Enjoy the heartfelt glowing response of your listeners. Download and present our Umbrellas PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let your ideas bloom. Create a bed of roses for your audience. Download and present our Services PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Financial piggy bank with umbrella protect, money, finance, umbrellas, security, services. The prominent colors used in the PowerPoint template are Red, Yellow, Blue. With our Protect Your Savings Fom Market PowerPoint Templates Ppt Backgrounds For Slides 0413 your plans will never fall apart. They assist in maintaining close control.

Cloud Security Threats Shared Vulnerabilities Cloud Computing Security IT Ppt Slides Picture PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Presenting cloud security threats shared vulnerabilities cloud computing security it ppt slides picture pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cloud service, responsibility, cloud data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation
This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Explore a selection of the finest Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts.
Stock Inventory Acquisition Plan For Purchasing Inventory From Suppliers Icons PDF
This slide showcases plan that can help organization to purchase inventory from suppliers. Its key elements are product, on hand, pending sales orders, lead time, safety stock, purchase price, quantity value and days of supply. Find a pre-designed and impeccable Stock Inventory Acquisition Plan For Purchasing Inventory From Suppliers Icons PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
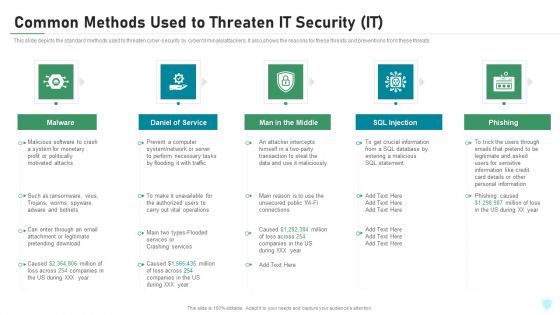
Common Methods Used To Threaten IT Security IT Ppt Inspiration Rules PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten it security it ppt inspiration rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Common Methods Used To Threaten Electronic Information Security Ppt Infographics Inspiration PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a cybersecurity common methods used to threaten electronic information security ppt infographics inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
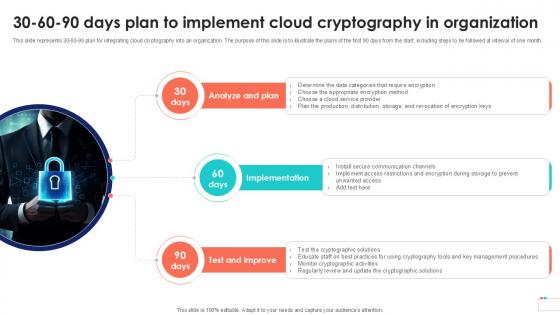
30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample
This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
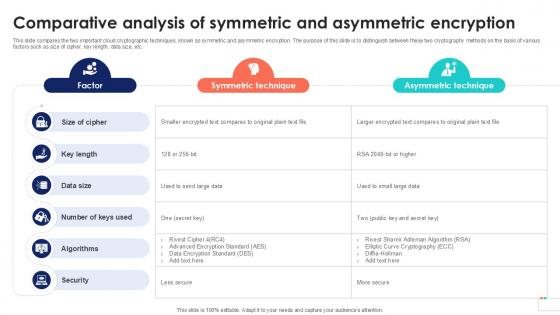
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.

Evolution Of Tokenization From Ancient Times To Modern Era Securing Your Data Ppt Powerpoint
This slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Evolution Of Tokenization From Ancient Times To Modern Era Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc.
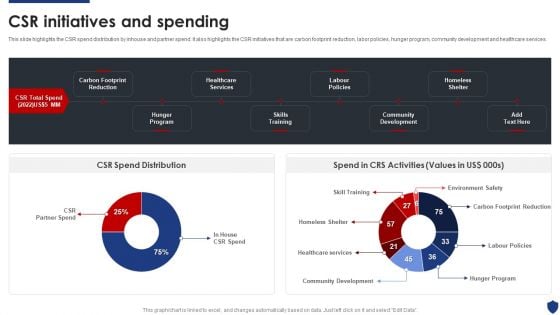
Security Officer Service Company Profile Csr Initiatives And Spending Ppt PowerPoint Presentation Gallery Shapes PDF
This slide highlights the CSR spend distribution by inhouse and partner spend. It also highlights the CSR initiatives that are carbon footprint reduction, labor policies, hunger program, community development and healthcare services. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Csr Initiatives And Spending Ppt PowerPoint Presentation Gallery Shapes PDF bundle. Topics like CSR Total Spend, Hunger Program, Skills Training, Community Development can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Construction Project Playbook Hybrid Or Semi Volumetric Construction Method Ppt Infographic Template File Formats PDF
This slide provides information regarding hybrid or semi volumetric construction method as modern method of construction along with benefits associated to it. Deliver an awe inspiring pitch with this creative construction project playbook hybrid or semi volumetric construction method ppt infographic template file formats pdf bundle. Topics like faster construction, benefits, improved site utilization, secured working environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

3d Golden Keys On Black Background Business PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our 3D Golden Keys On Black Background Business PowerPoint Templates PPT Backgrounds For Slides 1112.Download our Security PowerPoint Templates because you can Present your views on the methods using our self-explanatory templates. Use our Success PowerPoint Templates because the choices you make today will determine the future growth of your enterprise. Download and present our Business PowerPoint Templates because you are sure you have the right people for your plans. Use our Future PowerPoint Templates because you should explain the process by which you intend to right it. Download and present our Marketing PowerPoint Templates because customer satisfaction is a mantra of the marketplace. Building a loyal client base is an essential element of your business.Use these PowerPoint slides for presentations relating to Golden key on black background, security, success, business, future, marketing. The prominent colors used in the PowerPoint template are Yellow, Brown, Black. People tell us our 3D Golden Keys On Black Background Business PowerPoint Templates PPT Backgrounds For Slides 1112 are Tranquil. Presenters tell us our on PowerPoint templates and PPT Slides are Nifty. PowerPoint presentation experts tell us our 3D Golden Keys On Black Background Business PowerPoint Templates PPT Backgrounds For Slides 1112 are Perfect. Customers tell us our success PowerPoint templates and PPT Slides are Adorable. Customers tell us our 3D Golden Keys On Black Background Business PowerPoint Templates PPT Backgrounds For Slides 1112 are Lush. Customers tell us our black PowerPoint templates and PPT Slides are visually appealing. Give your thoughts an artistic backing. Add on the craftsmanship of our 3d Golden Keys On Black Background Business PowerPoint Templates Ppt Backgrounds For Slides 1112.
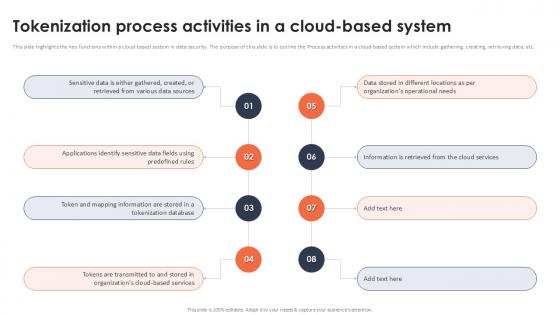
Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint
This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc.
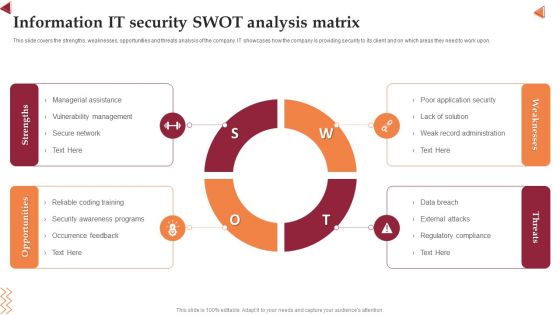
Information IT Security Swot Analysis Matrix Clipart PDF
This slide covers the strengths, weaknesses, opportunities and threats analysis of the company. IT showcases how the company is providing security to its client and on which areas they need to work upon. Persuade your audience using this Information IT Security Swot Analysis Matrix Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Opportunities, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Market Restraints Impacting The Global Security Industry PPT Template IR SS V
The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry. This modern and well-arranged Market Restraints Impacting The Global Security Industry PPT Template IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry.

House On Globe Siver Key Estate PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our House On Globe Siver Key Estate PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Globe PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Download our Real estate PowerPoint Templates because Our PowerPoint Templates and Slides will definately Enhance the stature of your presentation. Adorn the beauty of your thoughts with their colourful backgrounds. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Download and present our Services PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Download and present our Security PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level.Use these PowerPoint slides for presentations relating to Key to the world key and globe with estate, globe, real estate, business, services, security. The prominent colors used in the PowerPoint template are Red, Blue, Gray. Our House On Globe Siver Key Estate PowerPoint Templates Ppt Backgrounds For Slides 0213 team are exceedingly good. They have a clear assessment of what you need.

Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF
The following slide highlights key responsibilities of the digitization of security systems team with the position level and requirements. The various positions mentioned in the slide are security engineer, senior security engineer, distinguished security engineer and digitization of security systems manager. Showcasing this set of slides titled Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF. The topics addressed in these templates are Security Engineer, Senior Security Engineer, Security Automation Manager. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

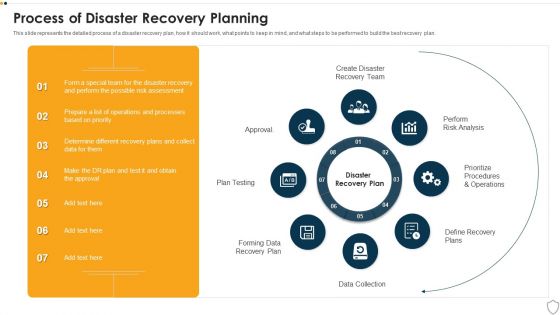
Process Of Disaster Recovery Planning IT Security IT Ppt Outline Example Introduction PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a process of disaster recovery planning it security it ppt outline example introduction pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data collection, plan testing, approval, perform risk analysis, prioritize procedures and operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
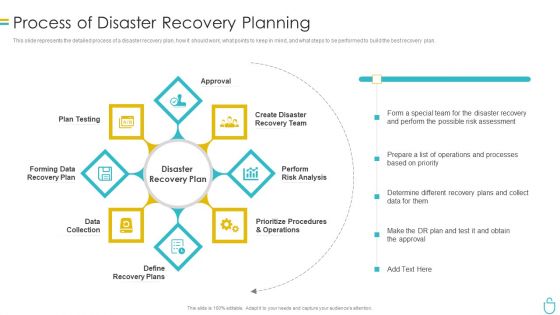
Information Security Process Of Disaster Recovery Planning Ppt Portfolio Backgrounds PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information security process of disaster recovery planning ppt portfolio backgrounds pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like recovery team, risk analysis, prioritize procedures, recovery plan, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Process Of Disaster Recovery Planning Ppt Portfolio Microsoft PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting it security process of disaster recovery planning ppt portfolio microsoft pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like plan testing, perform risk analysis, data collection, prioritize procedures and operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example
This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc. This modern and well-arranged Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc.
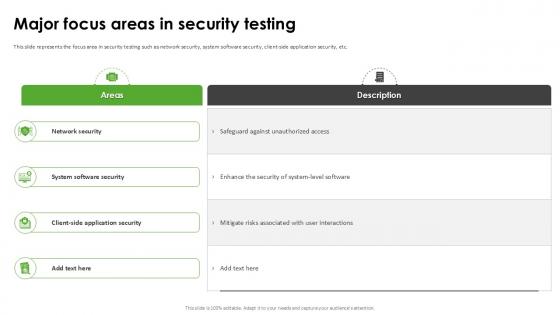
Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example
This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc.

Security Control Techniques For Real Estate Project Ppt PowerPoint Presentation Complete Deck With Slides
This Security Control Techniques For Real Estate Project Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This Fifty one slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence.
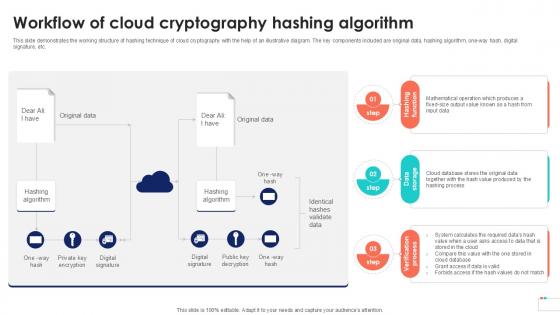
Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc.
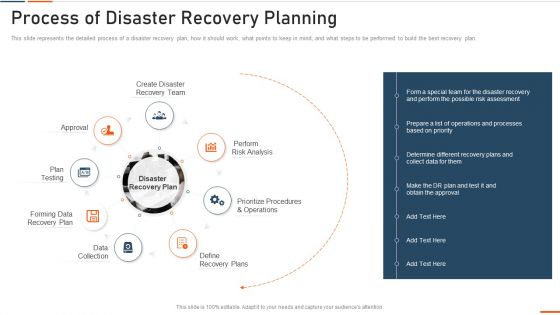
Information Technology Security Process Of Disaster Recovery Planning Ppt Portfolio Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information technology security process of disaster recovery planning ppt portfolio summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like approval, plan testing, recovery plan, data collection, perform . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
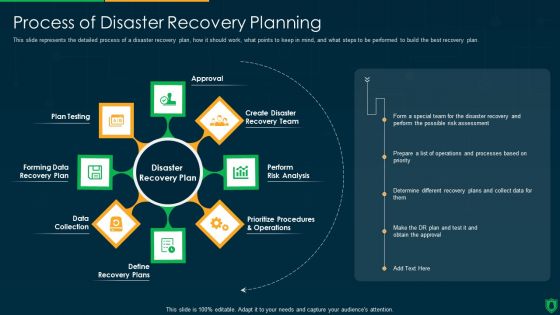
Info Security Process Of Disaster Recovery Planning Ppt PowerPoint Presentation File Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a info security process of disaster recovery planning ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like approval, perform risk analysis, define recovery plans, data collection, forming data recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
8 Cycle Representation Of Security Policy Ppt PowerPoint Presentation Gallery Grid PDF
Persuade your audience using this 8 cycle representation of security policy ppt powerpoint presentation gallery grid pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 cycle representation of security policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
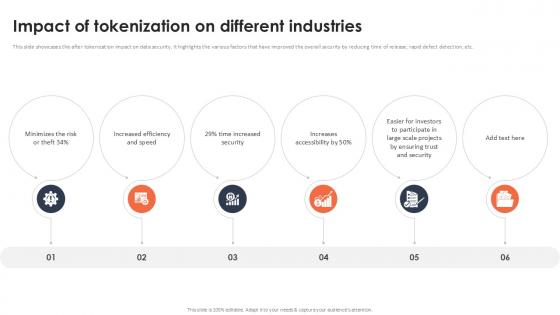
Impact Of Tokenization On Different Industries Securing Your Data Ppt Example
This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Welcome to our selection of the Impact Of Tokenization On Different Industries Securing Your Data Ppt Example These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc.

Leader Protecting The Team Good Values PowerPoint Templates Ppt Backgrounds For Slides 0713
Duct it through with our Leader Protecting The Team Good Values PowerPoint Templates PPT Backgrounds For Slides. Your ideas will reach into their minds intact. Recieve your due with our umbrellas PowerPoint Templates. Your audience will display their admiration for you. Our leadership PowerPoint Templates give your thoughts their due. They project them with full intensity. Formalize plans with our Leader Protecting The Team Good Values PowerPoint Templates Ppt Backgrounds For Slides 0713. Download without worries with our money back guaranteee.


 Continue with Email
Continue with Email

 Home
Home


































