Safety Management Strategy Ppt
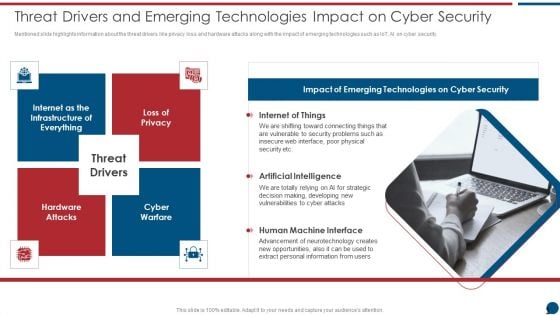
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
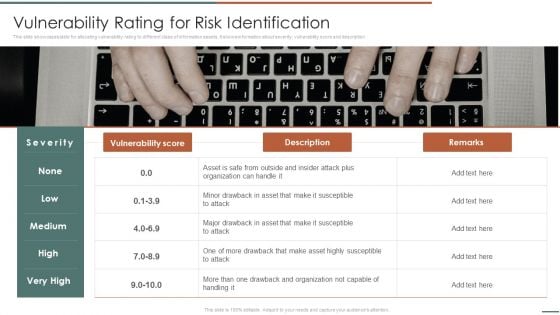
Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description.This is a Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drawback And Organization, Drawback Asset, Vulnerability Score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
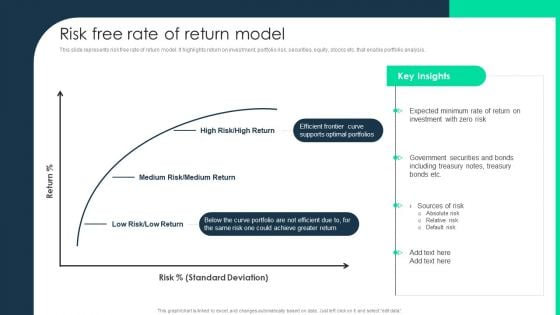
Monetary Investment Portfolio Growth And Administration Risk Free Rate Of Return Model Rules PDF
This slide represents risk free rate of return model. It highlights return on investment, portfolio risk, securities, equity, stocks etc. that enable portfolio analysis. Presenting Monetary Investment Portfolio Growth And Administration Risk Free Rate Of Return Model Rules PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Absolute Risk, Relative Risk, Default Risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Purpose Of IT Threats Response Playbook Professional PDF
This is a Purpose Of IT Threats Response Playbook Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Standardized Cybersecurity, Future Security, Appropriate Manner. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Conducting Monetary Inclusion Stakeholders Expectation From Our MFS Ecosystem Clipart PDF
This slide shows various stakeholders expectations from the mobile financial service ecosystem. Stakeholders covered in the table are consumer, employees, mobile network operators, micro finance institutions, agents and regulator. This is a Conducting Monetary Inclusion Stakeholders Expectation From Our MFS Ecosystem Clipart PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Transaction Security, Commission Transactions, Reduce Money. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Certified Information Systems Security Collection Of Information Technology Certifications Download PDF
This slide covers CISSP certification details such as what is the CISSP how to become certified, how to prepare for CISSP and why to get CISSP certifications. Presenting certified information systems security collection of information technology certifications download pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like information systems, network security, information network, organization, average. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
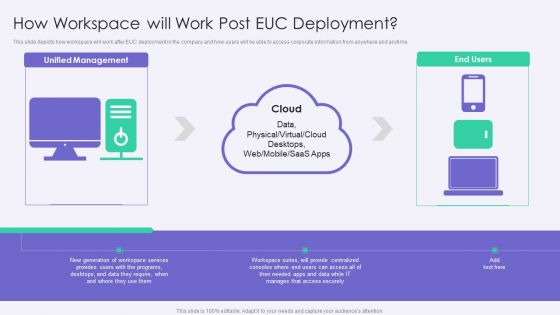
VID How Workspace Will Work Post EUC Deployment Template PDF
This slide depicts how workspace will work after EUC deployment in the company and how users will be able to access corporate information from anywhere and anytime.This is a VID How Workspace Will Work Post EUC Deployment Template PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Workspace Services, Access Securely, Provide Centralized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Investigations by HR, Phishing Detection And Prevention, Risk Mitigation of Left Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Functioning Centre Various Metrics To Measure Secops System Performance Icons PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. This is a security functioning centre various metrics to measure secops system performance icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security analysts productivity, escalation breakdown, average time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
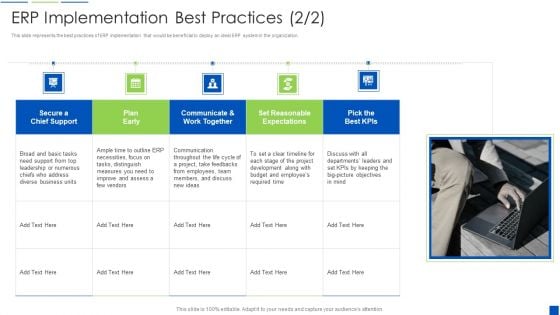
Corporate Resource Planning ERP Implementation Best Practices Slides PDF
This slide represents the best practices of ERP implementation that would be beneficial to deploy an ideal ERP system in the organization.This is a Corporate Resource Planning ERP Implementation Best Practices Slides PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Communicate And Work Together, Set Reasonable Expectations, Secure A Chief Support You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Company Vulnerability Administration Overview Structure PDF
This is a company vulnerability administration overview structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it is a security weakness or flaw of a component in the technology stack of an organization, vulnerabilities may exist on network devices, servers pcs mobile devices applications or any other elements connected to the network, a typical organizations network has many vulnerabilities per device or system therefore even a small organization may have tens of thousands of vulnerabilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Distributed Computing Challenges And Solutions Of Edge Computing Deployment Designs PDF
This slide represents the challenges and solutions of edge computing deployment in the organization, and it includes challenges such as scale, performance, control, and security.This is a Distributed Computing Challenges And Solutions Of Edge Computing Deployment Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Infrastructure Environment, Repository Performance, Monitoring Controlling You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying Quality Assurance QA Transformation Implement Code Quality Measurements Guidelines PDF
This slide shows the details about Code Quality Measurements Approach for Effective QA Transformation along with details on Software Quality Indicators and Test Metrics such as Reliability, Security, Testability, Rate of Delivery etc.This is a Deploying Quality Assurance QA Transformation Implement Code Quality Measurements Guidelines PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Performance Efficiency, Maintainability, Reliability You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Facilitating IT Intelligence Architecture Determine Capabilities Enabling Intelligent Infrastructure Graphics PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting Facilitating IT Intelligence Architecture Determine Capabilities Enabling Intelligent Infrastructure Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Configuration Automation, Connection Of Devices And Desktops, Infrastructure Services Analysis In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
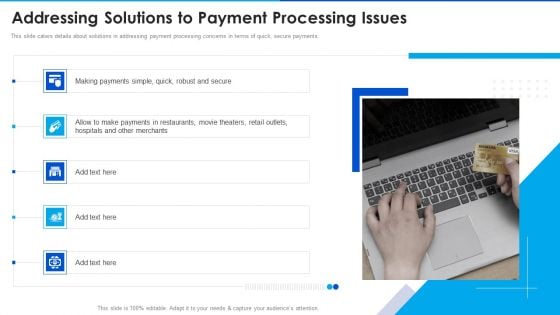
Digital Payment Solution Company Stakeholder Addressing Solutions To Payment Summary PDF
This slide caters details about solutions in addressing payment processing concerns in terms of quick, secure payments. Presenting digital payment solution company stakeholder addressing solutions to payment summary pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like making payments simple, hospitals and other merchants, payments in restaurants In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Software Development Company Profile Case Study Rules PDF
This slide shows the challenges faced by client for development of software infrastructure for secure international data exchange. Company developed cryptographic hash software platform solution. Presenting Business Software Development Company Profile Case Study Rules PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Challenge, Solution, Current Infrastructure, Integrated Software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
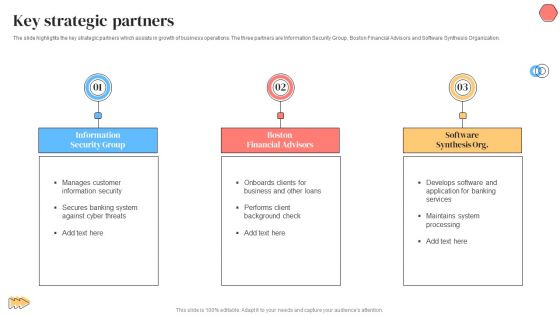
Banking Solutions Company Overview Key Strategic Partners Diagrams PDF
The slide highlights the key strategic partners which assists in growth of business operations. The three partners are Information Security Group, Boston Financial Advisors and Software Synthesis Organization. Presenting Banking Solutions Company Overview Key Strategic Partners Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Information Security Group, Boston Financial Advisors, Software Synthesis Org. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risks Associated To Gym Staff Themes PDF
This slide covers the key risks related to gym staff members during the Covid 19. Major risk includes risks related to job security, risk associated to work, risk of getting stresses etc.Presenting risks associated to gym staff themes pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like risk related to job security, risks associated to work, risk of getting stressed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Awareness Trends In 2022 Diagrams PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Presenting Cyber Security Awareness Trends In 2022 Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Malware Ransomware, Advanced Challenging, Malware Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Financial Solutions Company Profile Key Strategic Partners Graphics PDF
The slide highlights the key strategic partners which assists in growth of business operations. The three partners are Information Security Group, Boston Financial Advisors and Software Synthesis Organization.Presenting Financial Solutions Company Profile Key Strategic Partners Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Security Group, Financial Advisors, Software Synthesis In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Improving Technology Based Overview Of Recruitment Blockchain Technology Infographics PDF
This slide showcases introduction to blockchain technology that possesses qualities in making recruitment process faster and secure. It provides details about legitimacy, secure access, quick verification, applicant profiles, fraud elimination, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Improving Technology Based Overview Of Recruitment Blockchain Technology Infographics PDF from Slidegeeks and deliver a wonderful presentation.

Youtube Advertising Techniques Problems Related To Digital Marketing Download PDF
This slide highlights the problems that company is facing from Facebook and Twitter marketing which includes changing trends, wrong targeting, security risks and expensive Ads. This is a Youtube Advertising Techniques Problems Related To Digital Marketing Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Changing Trends, Wrong Targeting, Security Risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
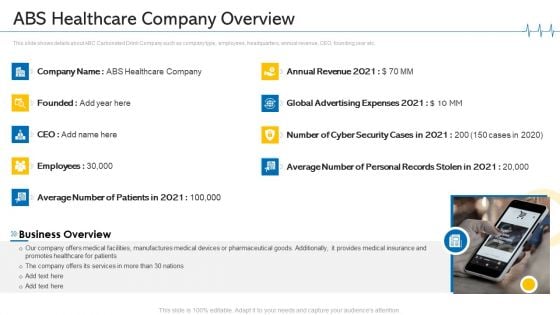
Minimize Cloud Risks Medical Care Business Case Competition ABS Healthcare Company Overview Introduction PDF
This slide shows details about ABC Carbonated Drink Company such as company type, employees, headquarters, annual revenue, CEO, founding year etc. This is a minimize cloud risks medical care business case competition ABS healthcare company overview introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business overview, annual revenue, cyber security cases, manufactures, global advertising expenses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
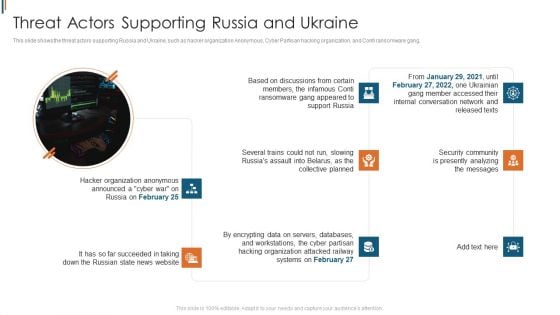
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
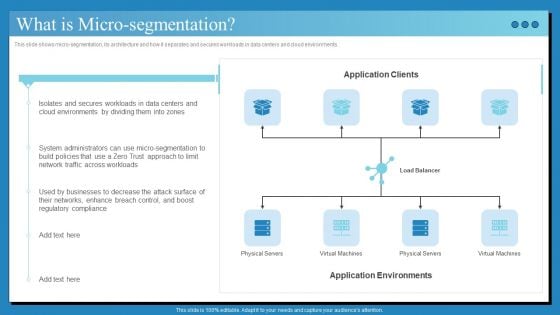
Data Center Infrastructure Technologies What Is Micro Segmentation Clipart PDF
This slide shows micro-segmentation, its architecture and how it separates and secures workloads in data centers and cloud environments. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Data Center Infrastructure Technologies What Is Micro Segmentation Clipart PDF from Slidegeeks and deliver a wonderful presentation.
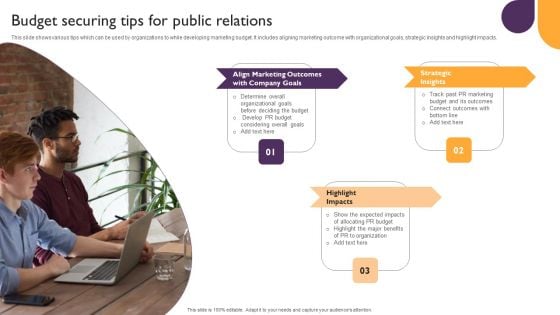
Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF
This slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Get a simple yet stunning designed Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
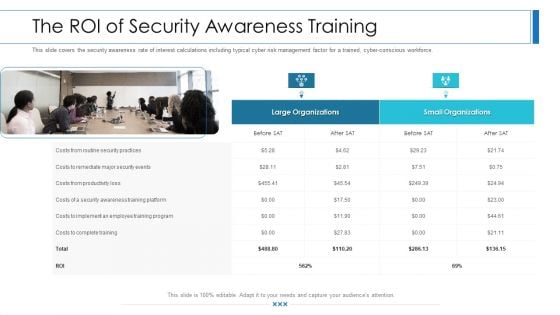
Workforce Security Realization Coaching Plan The ROI Of Security Awareness Training Pictures PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan the roi of security awareness training pictures pdf. Use them to share invaluable insights on security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
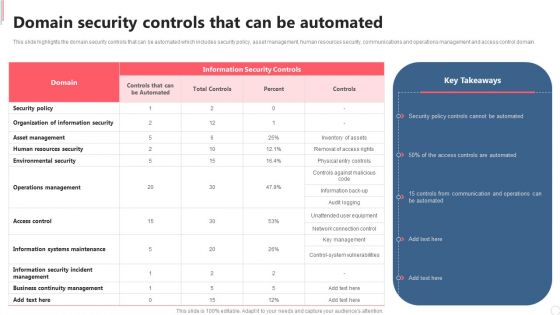
Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF.
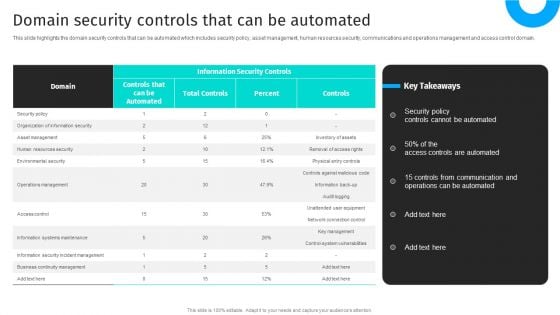
Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain.Find highly impressive Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
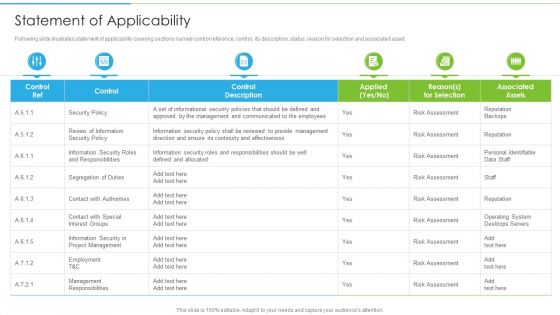
Ways To Accomplish ISO 27001 Accreditation Statement Of Applicability Demonstration PDF
Following slide illustrates statement of applicability covering sections namely control reference, control, its description, status, reason for selection and associated asset. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Statement Of Applicability Demonstration PDF. Use them to share invaluable insights on Security Policy, Contact Authorities, Project Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
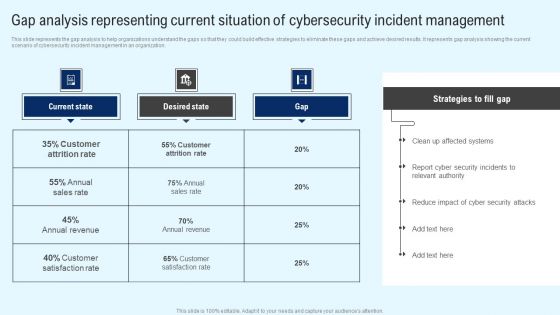
Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Retrieve professionally designed Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
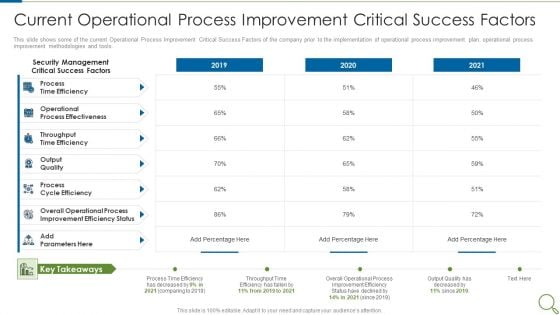
Current Operational Process Improvement Critical Success Factors Topics PDF
This slide shows some of the current Operational Process Improvement Critical Success Factors of the company prior to the implementation of operational process improvement plan, operational process improvement methodologies and tools. Deliver and pitch your topic in the best possible manner with this current operational process improvement critical success factors topics pdf. Use them to share invaluable insights on process, output quality, security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
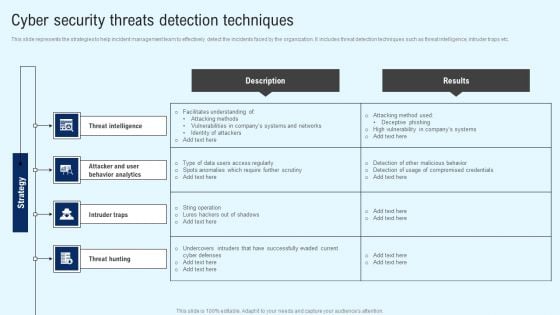
Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF from Slidegeeks today.

Cloud Intelligence Framework For Application Consumption Major Cybersecurity Challenges With Required Actions Mockup PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption major cybersecurity challenges with required actions mockup pdf. Use them to share invaluable insights on cybersecurity strategy, performing effective oversight, protecting cyber critical infrastructure, telecommunications, management challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
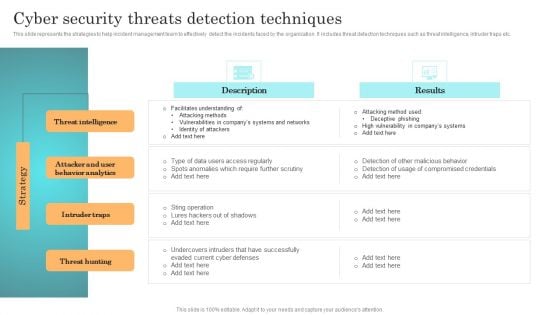
Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.
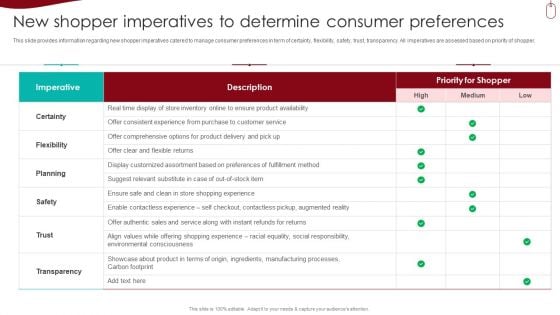
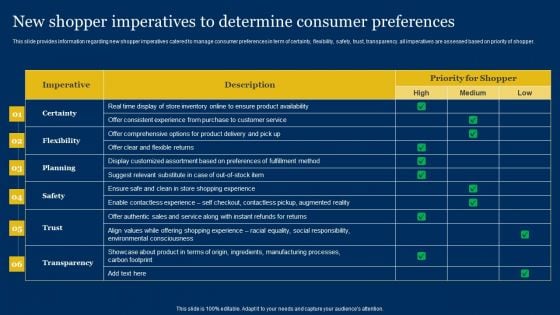
Retail Outlet Experience Optimization Playbook New Shopper Imperatives To Determine Consumer Preferences Brochure PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. All imperatives are assessed based on priority of shopper. Deliver an awe inspiring pitch with this creative Retail Outlet Experience Optimization Playbook New Shopper Imperatives To Determine Consumer Preferences Brochure PDF bundle. Topics like Planning, Customer Service, Manufacturing Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
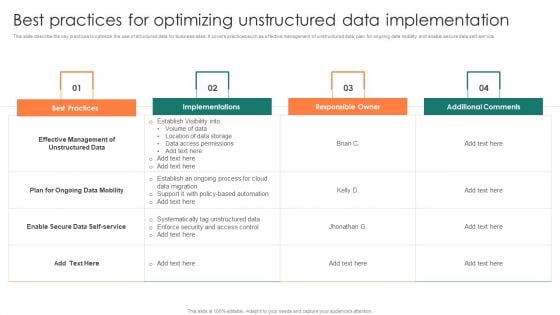
Best Practices For Optimizing Unstructured Data Implementation Ideas PDF
This slide describe the key practices to optimize the use of structured data for business sites. It covers practices such as effective management of unstructured data, plan for ongoing data mobility and enable secure data self-service. Showcasing this set of slides titled Best Practices For Optimizing Unstructured Data Implementation Ideas PDF. The topics addressed in these templates are Best Practices, Implementations, Responsible Owner, Additional Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
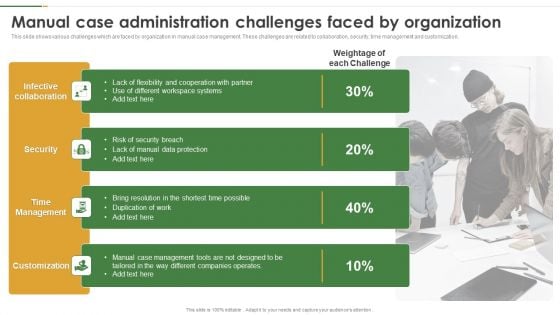
Manual Case Administration Challenges Faced By Organization Sample PDF
This slide shows various challenges which are faced by organization in manual case management. These challenges are related to collaboration, security, time management and customization. Presenting Manual Case Administration Challenges Faced By Organization Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Time Management, Customization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
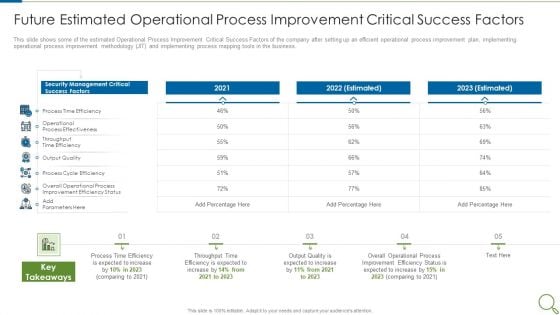
Future Estimated Operational Process Improvement Critical Success Factors Slides PDF
This slide shows some of the estimated Operational Process Improvement Critical Success Factors of the company after setting up an efficient operational process improvement plan, implementing operational process improvement methodology JIT and implementing process mapping tools in the business. Deliver an awe inspiring pitch with this creative future estimated operational process improvement critical success factors slides pdf bundle. Topics like process, output quality, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Focus Areas For Internal Audit And Review Teams In FY23 Icons PDF
This slide illustrates key areas of focus for internal auditors for risk management and lawful following of compliance laws. It includes proposed areas like health and safety, payroll, IT security etc.Presenting Focus Areas For Internal Audit And Review Teams In FY23 Icons PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Proposed Internal, Reputational Risk, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Retailer Instructions Playbook New Shopper Imperatives To Determine Consumer Preferences Inspiration PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. all imperatives are assessed based on priority of shopper. Deliver and pitch your topic in the best possible manner with this Retailer Instructions Playbook New Shopper Imperatives To Determine Consumer Preferences Inspiration PDF. Use them to share invaluable insights on Planning, Environmental Consciousness, Manufacturing Process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. If you are looking for a format to display your unique thoughts, then the professionally designed User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find highly impressive Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
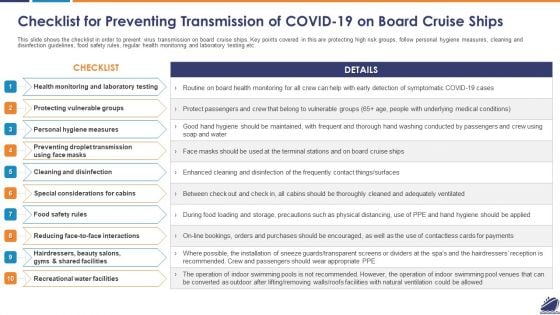
Checklist For Preventing Transmission Of COVID 19 On Board Cruise Ships Introduction PDF
This slide shows the checklist in order to prevent virus transmission on board cruise ships. Key points covered in this are protecting high risk groups, follow personal hygiene measures, cleaning and disinfection guidelines, food safety rules, regular health monitoring and laboratory testing etc. Presenting checklist for preventing transmission of covid 19 on board cruise ships introduction pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like protecting vulnerable groups, personal hygiene measures, cleaning and disinfection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing New Healthcare Policies And Procedures Pictures PDF

Guide To Healthcare Services Administration Developing New Healthcare Policies And Procedures Rules PDF

Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Critical Measures For Ensuring Business Security Formats PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Table Of Contents Critical Measures For Ensuring Business Security Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
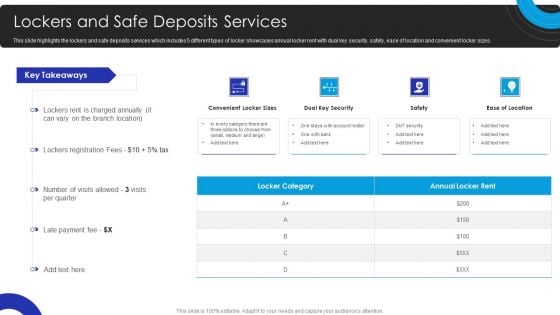
Operational Innovation In Banking Lockers And Safe Deposits Services Summary PDF
This slide highlights the lockers and safe deposits services which includes 5 different types of locker showcases annual locker rent with dual key security, safety, ease of location and convenient locker sizes. Make sure to capture your audiences attention in your business displays with our gratis customizable Operational Innovation In Banking Lockers And Safe Deposits Services Summary PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Types Of Robots For Industrial Operations Advantages Of Using Robots In Industrial Sector Template PDF
This slide illustrates the benefits of using robots in industries. The purpose of this slide is to explain how industrial sector is getting optimized from robotic automation. Their key pros included are high speed, increased load capacity, improved safety, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Robots For Industrial Operations Advantages Of Using Robots In Industrial Sector Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

5 Kpis To Monitor And Track Network Service Assessment Information PDF
Mentioned slide outlines various kpis which can be used by IT reps to monitor network performance. The kpis mentioned in the template are latency, network jitter, packet loss, throughput and mean opinion score. It also covers information about objective, strategies implemented and actual performance of each kpis. Showcasing this set of slides titled 5 Kpis To Monitor And Track Network Service Assessment Information PDF. The topics addressed in these templates are Strategies Implemented, Network Security, Quality. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Structure PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring structure pdf. Use them to share invaluable insights on cybersecurity monitoring tools to be implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
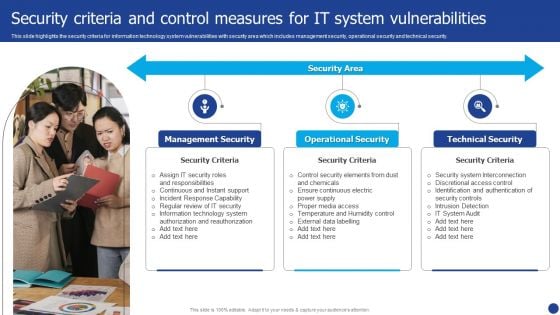
Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
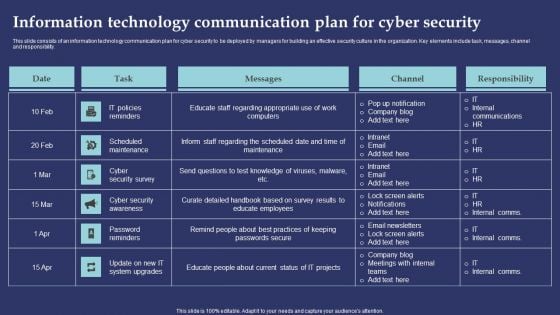
Information Technology Communication Plan For Cyber Security Information PDF
This slide consists of an information technology communication plan for cyber security to be deployed by managers for building an effective security culture in the organization. Key elements include task, messages, channel and responsibility. Showcasing this set of slides titled Information Technology Communication Plan For Cyber Security Information PDF. The topics addressed in these templates are IT Policies Reminders, Scheduled Maintenance, Cyber Security Survey. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































