Safety Performance Dashboard

Prevention Of Information Cyber Security Awareness Trends In 2023 Infographics PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. rom laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Prevention Of Information Cyber Security Awareness Trends In 2023 Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.
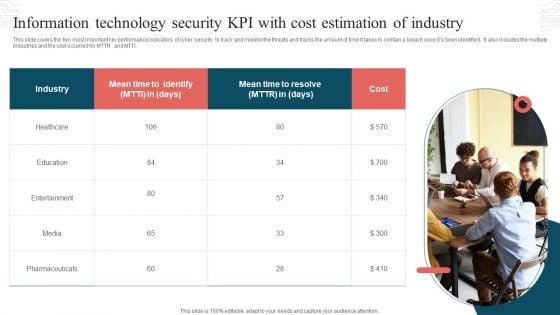
Information Technology Security KPI With Cost Estimation Of Industry Topics PDF
This slide covers the two most important key performance indicators of cyber security to track and monitor the threats and tracks the amount of time it takes to contain a breach once its been identified. It also includes the multiple industries and the cost occurred for MTTR and MTTI. Persuade your audience using this Information Technology Security KPI With Cost Estimation Of Industry Topics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Industry, Mean Time, Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF
This slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
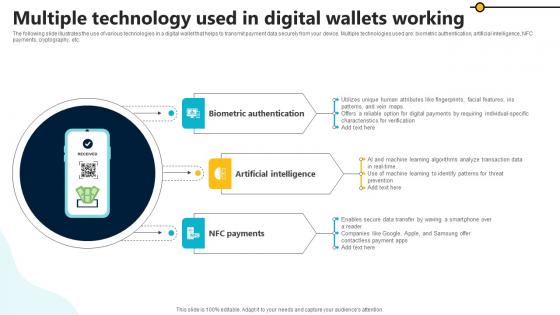
Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V
The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc.

Comprehensive Look At Blockchain Skills Required To Become Blockchain BCT SS V
This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comprehensive Look At Blockchain Skills Required To Become Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles.
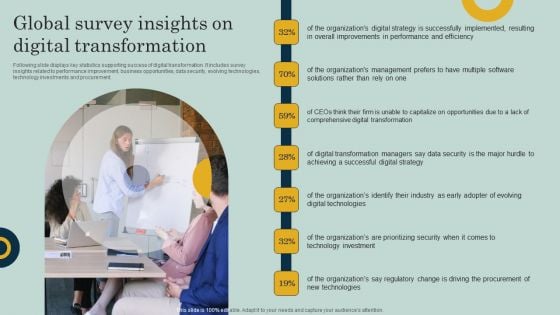
Global Survey Insights On Digital Transformation Ppt Visual Aids Files PDF
Following slide displays key statistics supporting success of digital transformation. It includes survey insights related to performance improvement, business opportunities, data security, evolving technologies, technology investments and procurement. This Global Survey Insights On Digital Transformation Ppt Visual Aids Files PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Global Survey Insights On Digital Transformation Ppt Visual Aids Files PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Clarify Roles And Responsibilities Of STO Exploring Investment Opportunities Infographics Pdf
The following slide illustrates major roles and responsibilities of security token offerings team to ensure successful launch. It includes elements such as technical officer, community manager, engineers, developers, founder, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Clarify Roles And Responsibilities Of STO Exploring Investment Opportunities Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide illustrates major roles and responsibilities of security token offerings team to ensure successful launch. It includes elements such as technical officer, community manager, engineers, developers, founder, etc.
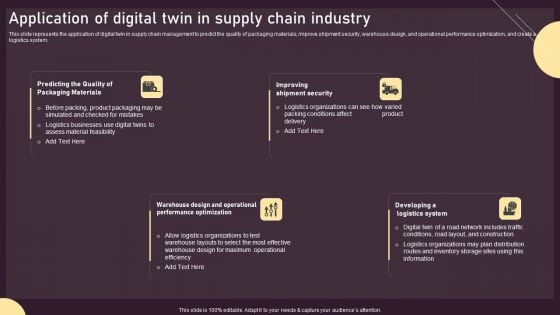
Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. This Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
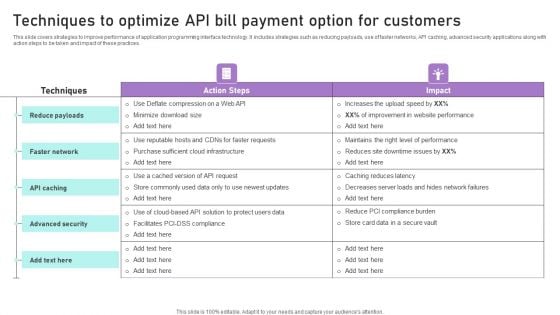
Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF.
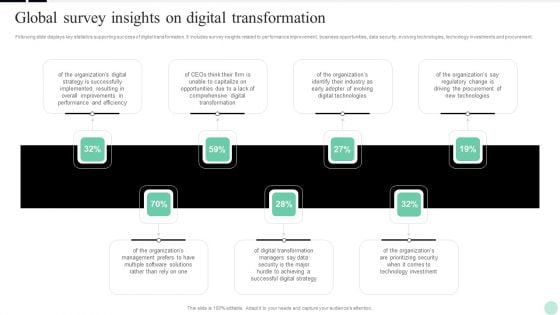
Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF
Following slide displays key statistics supporting success of digital transformation. It includes survey insights related to performance improvement, business opportunities, data security, evolving technologies, technology investments and procurement. This Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Major Types Of Distributed Ledger Security Methods Portrait Pdf
This slide highlights types of blockchain security methods aimed at efficiently storing data to execute transaction and perform functions in an open environment. It covers three types public blockchain, private blockchain and consortium blockchain Showcasing this set of slides titled Major Types Of Distributed Ledger Security Methods Portrait Pdf The topics addressed in these templates are Public Blockchain, Private Blockchain, Consortium Blockchain All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights types of blockchain security methods aimed at efficiently storing data to execute transaction and perform functions in an open environment. It covers three types public blockchain, private blockchain and consortium blockchain

Determinants Of Product Quality Ppt PowerPoint Presentation Infographic Template Files
This is a determinants of product quality ppt powerpoint presentation infographic template files. This is a seven stage process. The stages in this process are performance, reliability, durability, evaluation, safety.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.

Determinants Of Product Quality Ppt PowerPoint Presentation Infographics Graphic Tips
This is a determinants of product quality ppt powerpoint presentation infographics graphic tips. This is a seven stage process. The stages in this process are performance, reliability, durability, evaluation, safety.
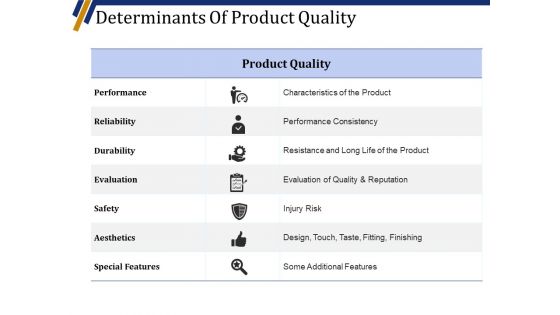
Determinants Of Product Quality Ppt PowerPoint Presentation Infographics Design Templates
This is a determinants of product quality ppt powerpoint presentation infographics design templates. This is a seven stage process. The stages in this process are performance, reliability, durability, evaluation, safety.
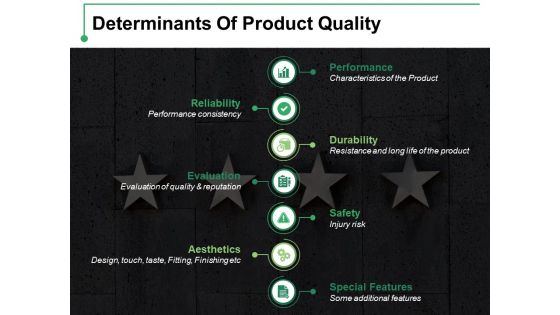
Determinants Of Product Quality Ppt PowerPoint Presentation Infographic Template Outline
This is a determinants of product quality ppt powerpoint presentation infographic template outline. This is a seven stage process. The stages in this process are performance, durability, safety, reliability, evaluation.
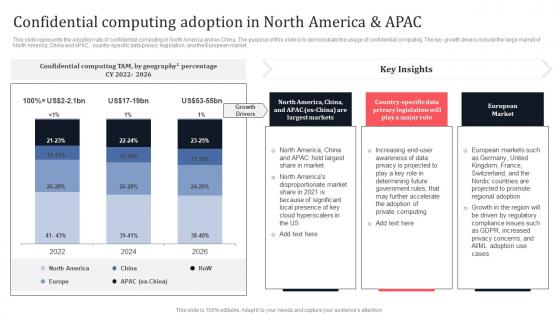
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
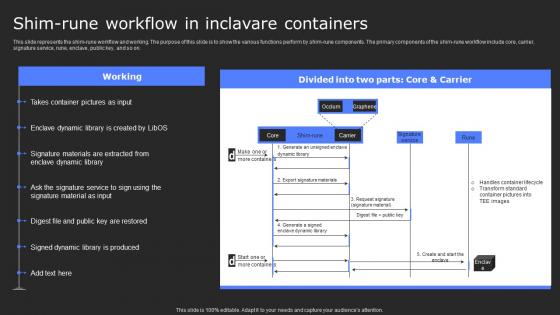
Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Create an editable Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.

Data Interpretation And Analysis Playbook Business Intelligence And Predictive Analytics Challenges Template PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Presenting data interpretation and analysis playbook business intelligence and predictive analytics challenges template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like security vulnerabilities, operationalizing, perform analysis, deployed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Visualizations Playbook Business Intelligence And Predictive Analytics Challenges Icons PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Presenting Information Visualizations Playbook Business Intelligence And Predictive Analytics Challenges Icons PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Raw Data Organized, Security Vulnerabilities, Perform Analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
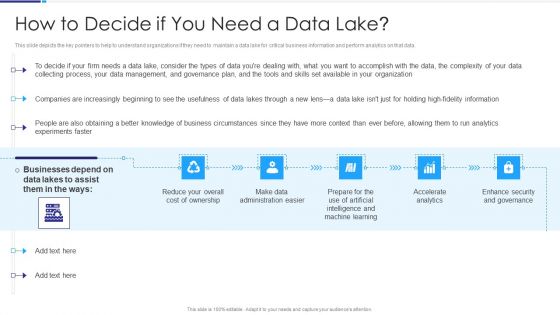
Data Lake Architecture How To Decide If You Need A Data Lake Information PDF
This slide depicts the key pointers to help to understand organizations if they need to maintain a data lake for critical business information and perform analytics on that data. Deliver an awe inspiring pitch with this creative Data Lake Architecture How To Decide If You Need A Data Lake Information PDF bundle. Topics like Make Data Administration Easier, Accelerate Analytics, Enhance Security And Governance, Businesses Depend can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Arrows PowerPoint Templates Business Data Mining Process Ppt Slides
Business Arrows PowerPoint Templates Business data mining process PPT Slides-Use this diagram to show Data Mining Process as a mechanism or group of parts performing one function or serving one purpose in a complex situation-Business Arrows PowerPoint Templates Business data mining process PPT Slides-This template can be used for presentations relating to Analysis, Anomaly, Artificial, Break, Clean, Computer, Cut, Data, Database, Decision, Detection, Discovery, Divide, Explore, Extract, Hammer, Helmet, Human, Index, Intelligence, Kdd, knowledge, Learning, Light, Mallet, Management, Mining, Model, Movement, Pattern, Predictive, Process, Records, Recycle, Repair, Safety, Science Crush doubts with our Business Arrows PowerPoint Templates Business Data Mining Process Ppt Slides. You will come out on top.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Continual Improvement Model Determinants Of Product Quality Ppt Model Infographics PDF
Presenting this set of slides with name continual improvement model determinants of product quality ppt model infographics pdf. This is a seven stage process. The stages in this process are performance, reliability, evaluation, safety, durability. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
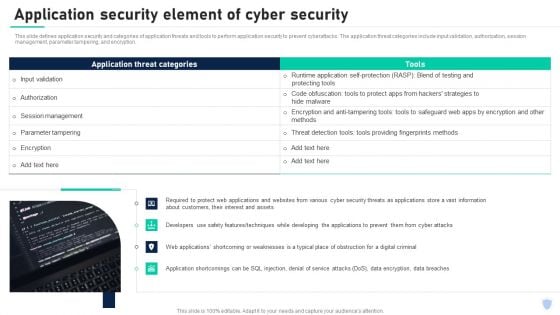
Cyber Security Components To Enhance Processes Application Security Element Of Cyber Security Infographics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Boost your pitch with our creative Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
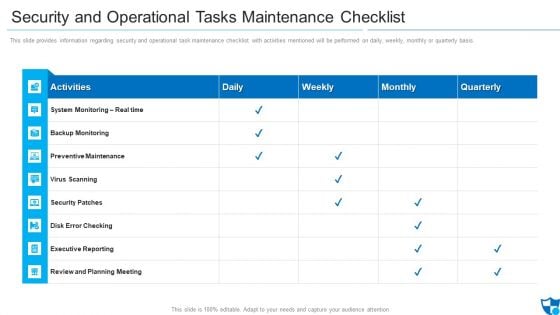
Security And Operational Tasks Maintenance Checklist Infographics PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis.Deliver an awe inspiring pitch with this creative security and operational tasks maintenance checklist infographics pdf bundle. Topics like preventive maintenance, security patches, review and planning meeting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
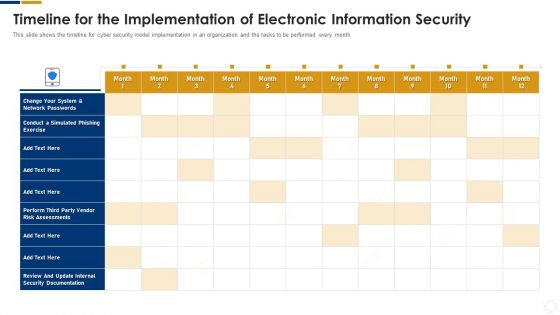
Cybersecurity Timeline For The Implementation Of Electronic Information Security Ppt Infographic Template Information PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative cybersecurity timeline for the implementation of electronic information security ppt infographic template information pdf bundle. Topics like security documentation, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
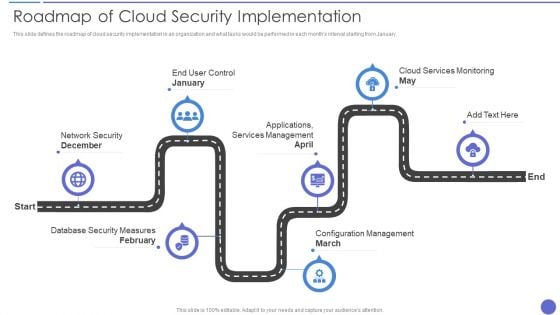
Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
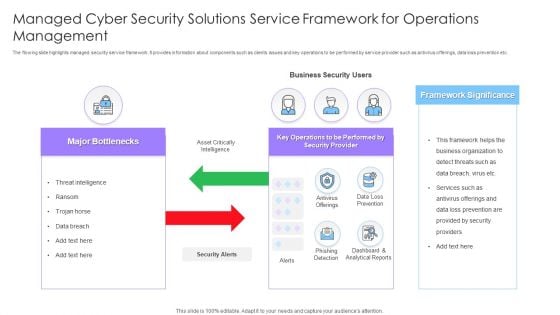
Managed Cyber Security Solutions Service Framework For Operations Management Ppt Styles Themes PDF
The flowing slide highlights managed security service framework. It provides information about components such as clients issues and key operations to be performed by service provider such as antivirus offerings, data loss prevention etc. Presenting Managed Cyber Security Solutions Service Framework For Operations Management Ppt Styles Themes PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Framework Significance, Business Security Users, Major Bottlenecks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
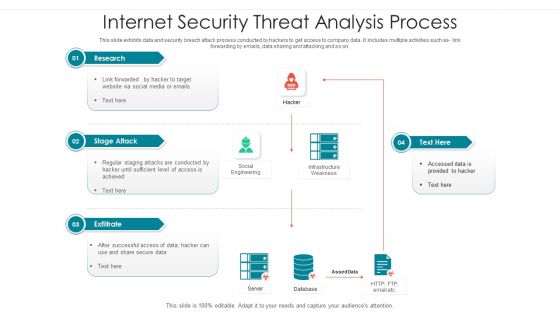
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
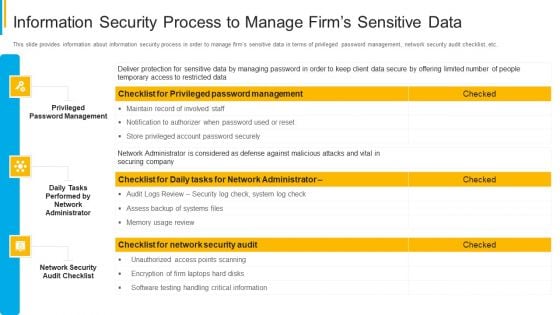
Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF
This slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Presenting Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Probe, Initial Attack, Expanded Attack, Data Lift. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
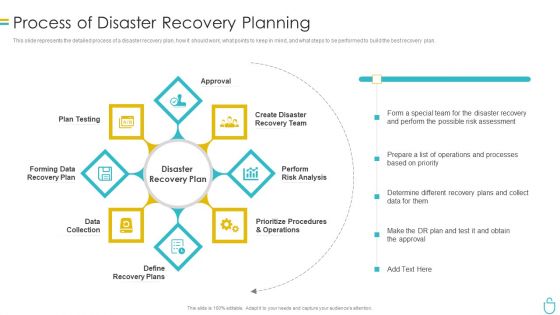
Information Security Process Of Disaster Recovery Planning Ppt Portfolio Backgrounds PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information security process of disaster recovery planning ppt portfolio backgrounds pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like recovery team, risk analysis, prioritize procedures, recovery plan, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
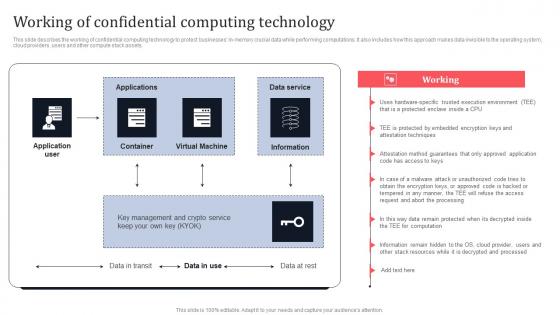
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.

Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
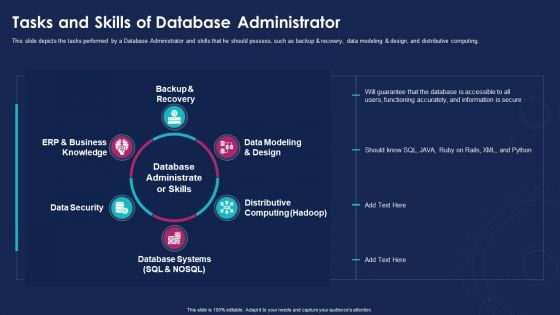
Data Analytics IT Tasks And Skills Of Database Administrator Ppt Summary Introduction PDF
This slide depicts the tasks performed by a Database Administrator and skills that he should possess, such as backup and recovery, data modeling and design, and distributive computing. Presenting data analytics it tasks and skills of database administrator ppt summary introduction pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like backup and recovery, data security, database systems, distributive computing, data modeling and design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Analytics Tasks And Skills Of Database Administrator Ppt Visual Aids PDF
This slide depicts the tasks performed by a Database Administrator and skills that he should possess, such as backup and recovery, data modeling and design, and distributive computing. Presenting data analytics tasks and skills of database administrator ppt visual aids pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data security, database systems, distributive computing, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
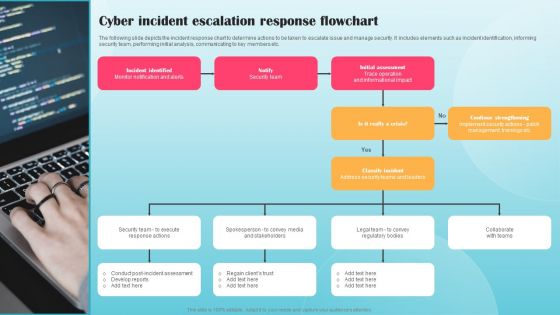
Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF
The following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
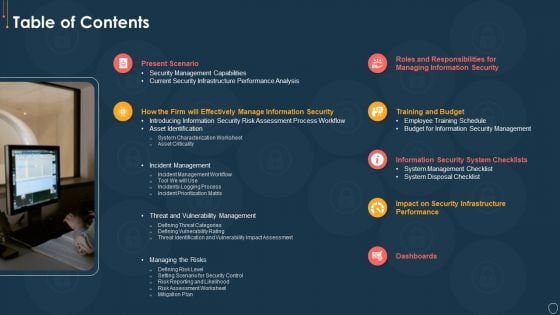
Cyber Security Risk Management Plan Table Of Contents Pictures PDF
Presenting cyber security risk management plan table of contents pictures pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like present scenario, roles and responsibilities, training and budget, dashboards, security infrastructure performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF
The following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
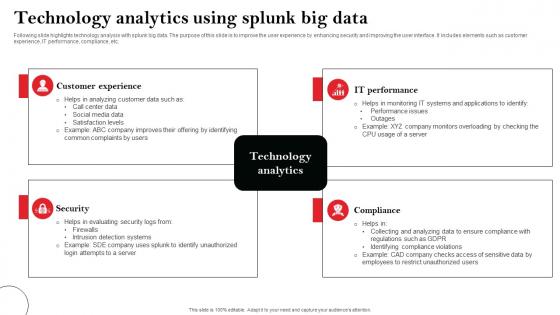
Technology Analytics Using Splunk Big Data Microsoft Pdf
Following slide highlights technology analysis with splunk big data. The purpose of this slide is to improve the user experience by enhancing security and improving the user interface. It includes elements such as customer experience, IT performance, compliance, etc. Pitch your topic with ease and precision using this Technology Analytics Using Splunk Big Data Microsoft Pdf This layout presents information on Customer Experience, Security, Compliance It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide highlights technology analysis with splunk big data. The purpose of this slide is to improve the user experience by enhancing security and improving the user interface. It includes elements such as customer experience, IT performance, compliance, etc.
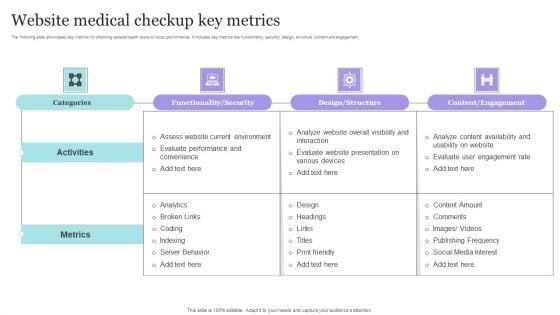
Website Medical Checkup Key Metrics Themes PDF
The following slide showcases key metrics for checking website health score to boost performance. It includes key metrics like functionality, security, design, structure, content and engagement. Pitch your topic with ease and precision using this Website Medical Checkup Key Metrics Themes PDF. This layout presents information on Evaluate Performance, Environment, Metrics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf
Pitch your topic with ease and precision using this Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf This layout presents information on Futuristic Approach, Data Driven Decisions, Exposed Assets It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the comparative analysis of cybersecurity KPIs for small businesses which helps an organization to carefully choose, select the best metric to track performance. It include details such as goal oriented, actionable, easy to understand, etc.
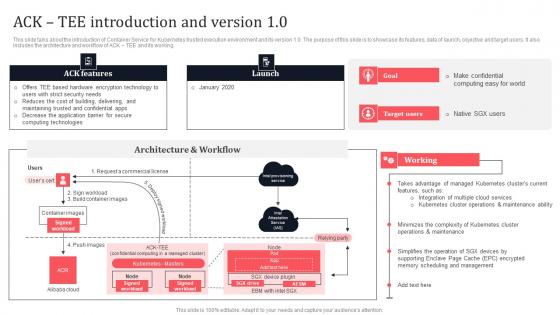
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
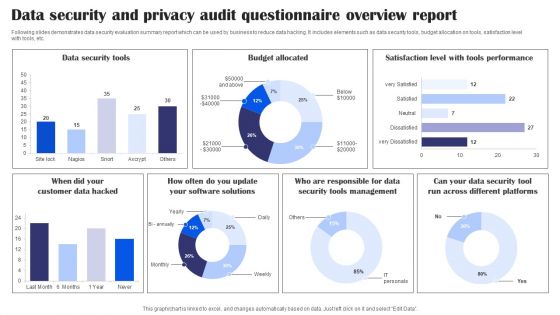
Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Transforming Big Data Analytics To Knowledge Tools For Analysing Big Data Ppt Professional Slides PDF
Presenting transforming big data analytics to knowledge tools for analysing big data ppt professional slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, performance, management, techniques, analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
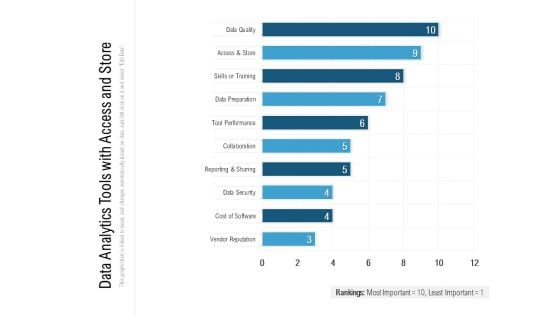
Data Analytics Tools With Access And Store Ppt PowerPoint Presentation Inspiration Aids PDF
Showcasing this set of slides titled data analytics tools with access and store ppt powerpoint presentation inspiration aids pdf. The topics addressed in these templates are cost of software, data security, collaboration, skills or training, tool performance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
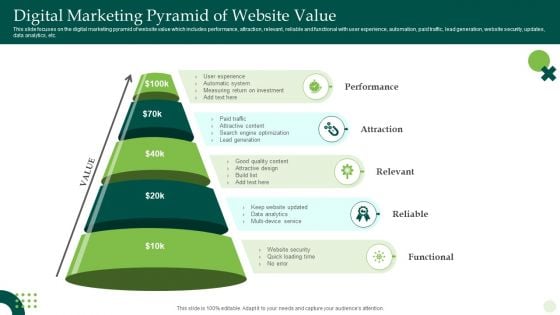
Digital Marketing Pyramid Of Website Value Ppt Inspiration Background Images PDF
This slide focuses on the digital marketing pyramid of website value which includes performance, attraction, relevant, reliable and functional with user experience, automation, paid traffic, lead generation, website security, updates, data analytics, etc. Presenting Digital Marketing Pyramid Of Website Value Ppt Inspiration Background Images PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Performance, Attraction, Relevant, Reliable, Functional. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
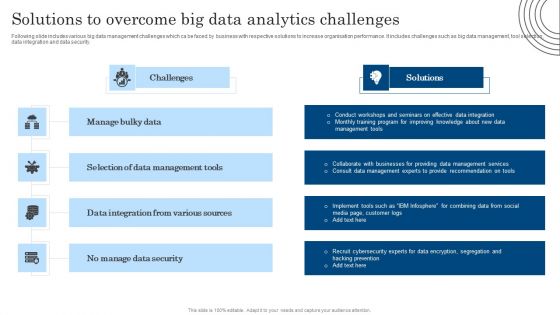
Solutions To Overcome Big Data Analytics Challenges Download PDF
Following slide includes various big data management challenges which ca be faced by business with respective solutions to increase organisation performance. It includes challenges such as big data management, tool selection, data integration and data security. Showcasing this set of slides titled Solutions To Overcome Big Data Analytics Challenges Download PDF. The topics addressed in these templates are Data Management Tools, Data Integration, Various Sources. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
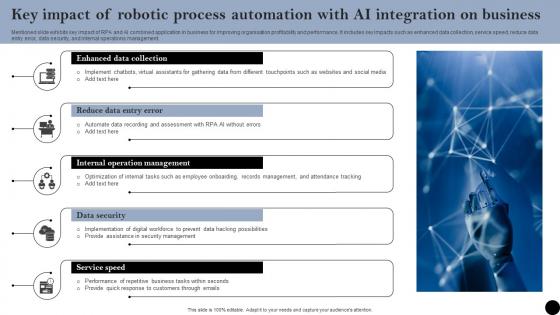
Key Impact Of Robotic Process Automation With AI Integration On Business Infographics Pdf
Mentioned slide exhibits key impact of RPA and AI combined application in business for improving organisation profitability and performance. It includes key impacts such as enhanced data collection, service speed, reduce data entry error, data security, and internal operations management. Showcasing this set of slides titled Key Impact Of Robotic Process Automation With AI Integration On Business Infographics Pdf. The topics addressed in these templates are Reduce Data Entry, Data Security, Internal Operations Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Mentioned slide exhibits key impact of RPA and AI combined application in business for improving organisation profitability and performance. It includes key impacts such as enhanced data collection, service speed, reduce data entry error, data security, and internal operations management.
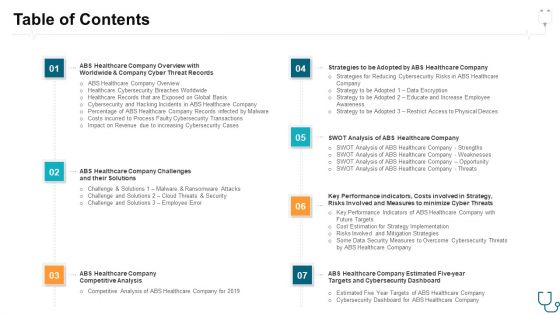
Table Of Contents Ppt Infographics Background Designs PDF
Deliver an awe-inspiring pitch with this creative table of contents ppt infographics background designs pdf. bundle. Topics like security, measures, performance, future targets, implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Statistics Of Cloud Data Security Client Side Encryption PPT Slide
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. This Statistics Of Cloud Data Security Client Side Encryption PPT Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc.

Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
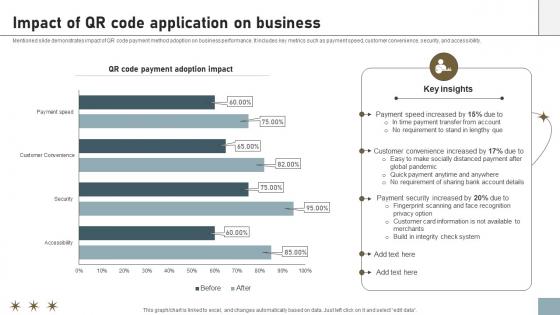
Online Payment Techniques Impact Of QR Code Application On Business
Mentioned slide demonstrates impact of QR code payment method adoption on business performance. It includes key metrics such as payment speed, customer convenience, security, and accessibility. Present like a pro with Online Payment Techniques Impact Of QR Code Application On Business. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide demonstrates impact of QR code payment method adoption on business performance. It includes key metrics such as payment speed, customer convenience, security, and accessibility.
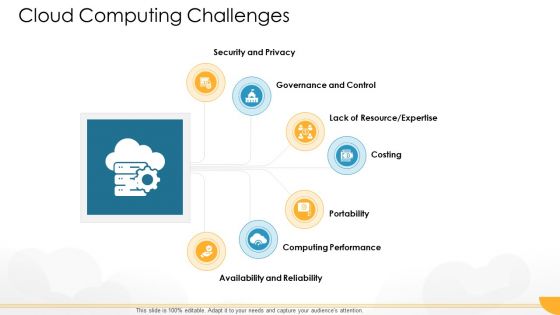
Technology Guide For Serverless Computing Cloud Computing Challenges Infographics PDF
Presenting technology guide for serverless computing cloud computing challenges infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like security and privacy, governance and control, portability, costing, computing performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
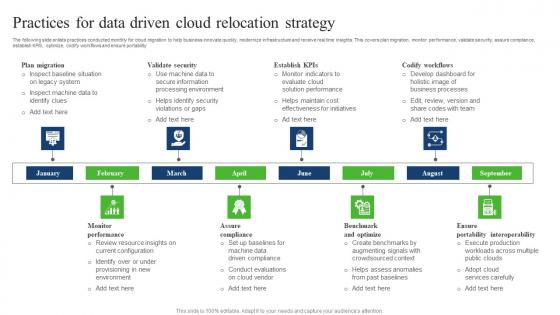
Practices For Data Driven Cloud Relocation Strategy Slides Pdf
The following slide enlists practices conducted monthly for cloud migration to help business innovate quickly, modernize infrastructure and receive real time insights. This covers plan migration, monitor performance, validate security, assure compliance, establish KPIS, optimize, codify workflows and ensure portability. Pitch your topic with ease and precision using this Practices For Data Driven Cloud Relocation Strategy Slides Pdf. This layout presents information on Validate Security, Codify Workflows, Benchmark And Optimize, Assure Compliance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide enlists practices conducted monthly for cloud migration to help business innovate quickly, modernize infrastructure and receive real time insights. This covers plan migration, monitor performance, validate security, assure compliance, establish KPIS, optimize, codify workflows and ensure portability.

Iot Logistics Comprehensive Training Program Ideas PDF
This slide showcases internet of things IoT comprehensive training program. It provides details such as modules, trainer, time, outcome, worker performance, productivity, IoT architecture, big data, analytics, warehouse IoT, testing, support, etc. Deliver and pitch your topic in the best possible manner with this Iot Logistics Comprehensive Training Program Ideas PDF. Use them to share invaluable insights on Transportation Management, Security, Data Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
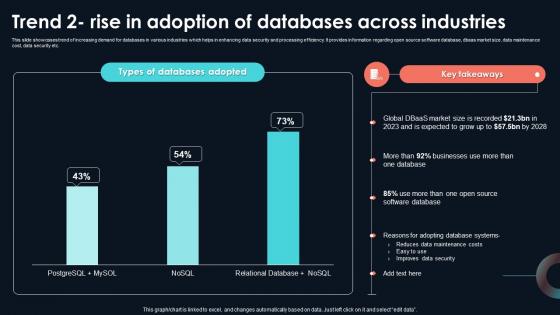
Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc. This Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc.

Issues Addressed By Dcaas Elements PDF
This slide brings forth various issues which are addressed by data service centers to provide users a solution in order to improve current business performance. The various issues addressed are data management, hyper converged infrastructure, data security and file storage. Presenting Issues Addressed By Dcaas Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Management, Data Security, Converged Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































