Safety Performance Dashboard
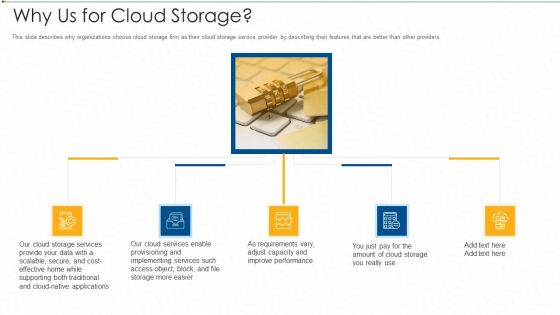
Why Us For Cloud Storage Ppt Infographic Template Graphics Pictures PDF
This slide describes why organizations choose cloud storage firm as their cloud storage service provider by describing their features that are better than other providers.This is a why us for cloud storage ppt infographic template graphics pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure, applications, implementing, services, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.
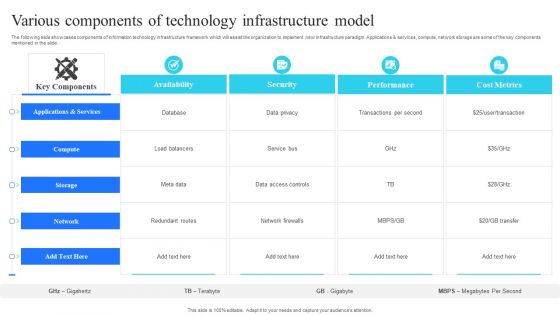
Various Components Of Technology Infrastructure Model Portrait PDF
The following slide showcases components of information technology infrastructure framework which will assist the organization to implement new infrastructure paradigm. Applications and services, compute, network storage are some of the key components mentioned in the slide. Showcasing this set of slides titled Various Components Of Technology Infrastructure Model Portrait PDF. The topics addressed in these templates are Availability, Security, Performance, Cost Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. The Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Secure Web Gateway Architecture And Working Web Threat Protection System
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. This Secure Web Gateway Architecture And Working Web Threat Protection System from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.

VID Managing End User Computing In The Company Infographics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting VID Managing End User Computing In The Company Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Implications, Application Performance, Endeavor And Metrics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Characteristics Of Modern ZTNA Solution Portrait PDF
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Are you searching for a Key Characteristics Of Modern ZTNA Solution Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Characteristics Of Modern ZTNA Solution Portrait PDF from Slidegeeks today.
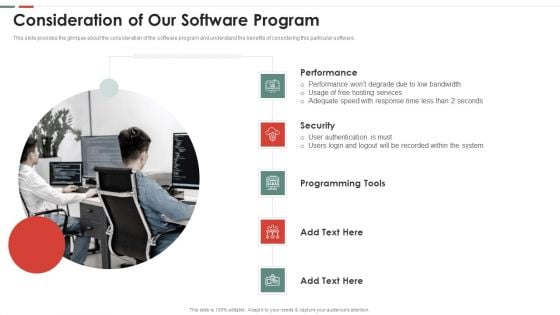
Feasibility Analysis Template Different Projects Consideration Of Our Software Program Infographics PDF
This slide provides the glimpse about the consideration of the software program and understand the benefits of considering this particular software. This is a feasibility analysis template different projects consideration of our software program infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performance, security, programming tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
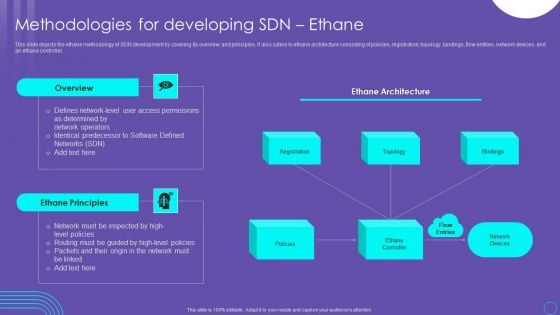
SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. This SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
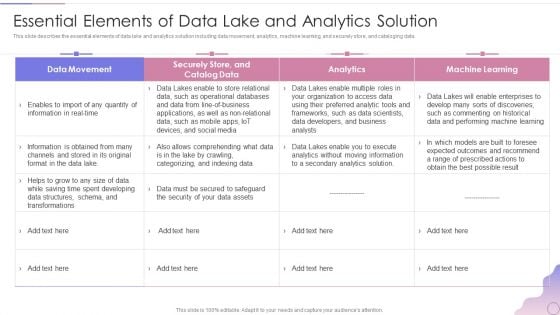
Data Lake Architecture Future Of Data Analysis Essential Elements Of Data Lake And Analytics Solution Topics PDF
This slide describes the essential elements of data lake and analytics solution including data movement, analytics, machine learning, and securely store, and cataloging data.Deliver an awe inspiring pitch with this creative Data Lake Architecture Future Of Data Analysis Essential Elements Of Data Lake And Analytics Solution Topics PDF bundle. Topics like Expected Outcomes, Data And Performing, Machine Learning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
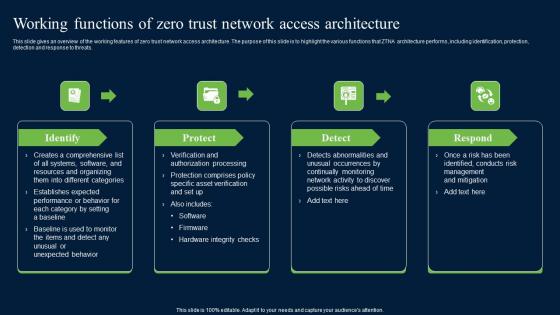
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
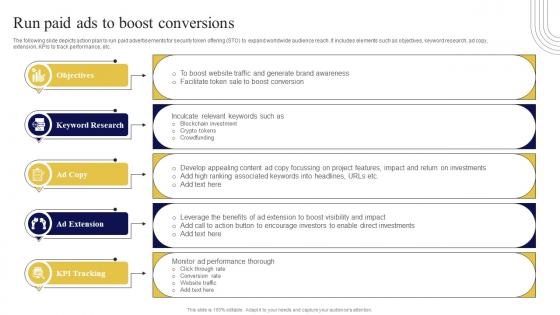
Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf
The following slide depicts action plan to run paid advertisements for security token offering STO to expand worldwide audience reach. It includes elements such as objectives, keyword research, ad copy, extension, KPIs to track performance, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts action plan to run paid advertisements for security token offering STO to expand worldwide audience reach. It includes elements such as objectives, keyword research, ad copy, extension, KPIs to track performance, etc.

Key Drivers For Encouraging Adoption Of Complete Roadmap To Blockchain BCT SS V
This slide covers critical factors that encourages widespread adoption of blockchain technology across various industries. It includes drivers such as efficiency and cost savings, security and data integrity, disintermediation and decentralization, etc. This Key Drivers For Encouraging Adoption Of Complete Roadmap To Blockchain BCT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide covers critical factors that encourages widespread adoption of blockchain technology across various industries. It includes drivers such as efficiency and cost savings, security and data integrity, disintermediation and decentralization, etc.

Major Cybersecurity Challenges With Required Actions Ppt Pictures Background Designs PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges This is a major cybersecurity challenges with required actions ppt pictures background designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, cybersecurity strategy, performing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
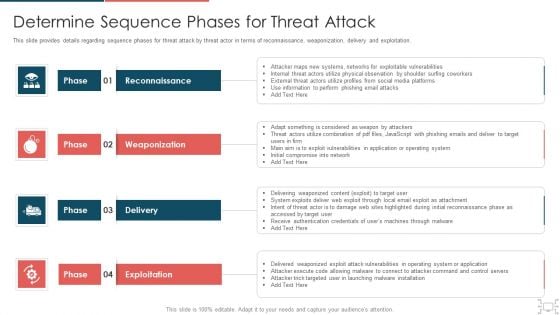
cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































