Safety Performance
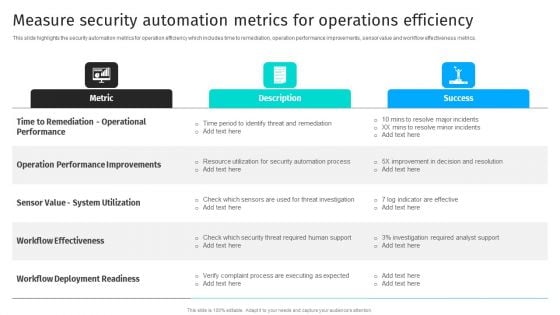
Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
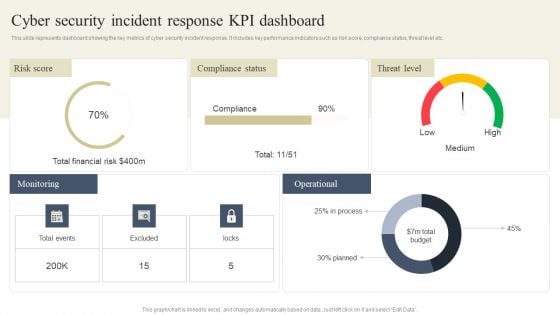
CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
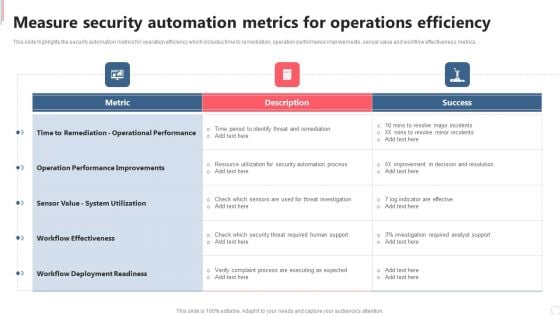
Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
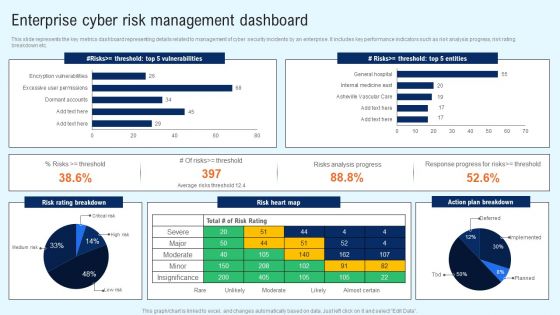
Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF today and make your presentation stand out from the rest.
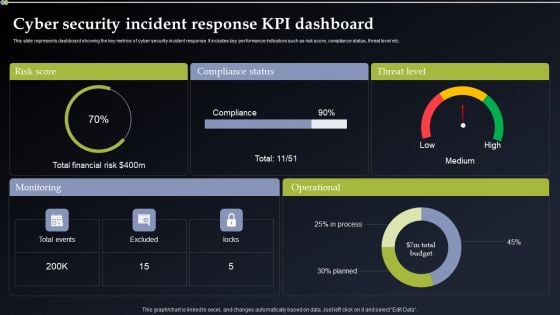
Cyber Security Incident Response KPI Dashboard Pictures PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Do you know about Slidesgeeks Cyber Security Incident Response KPI Dashboard Pictures PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
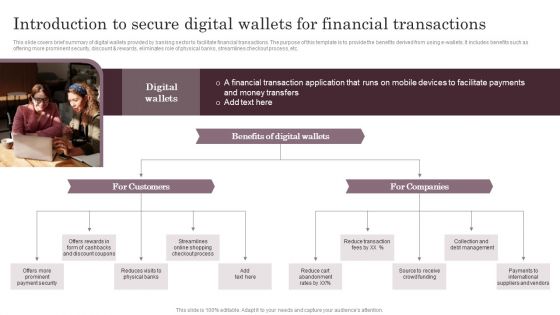
Introduction To Secure Digital Wallets For Financial Transactions Themes PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Digital Wallets For Financial Transactions Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
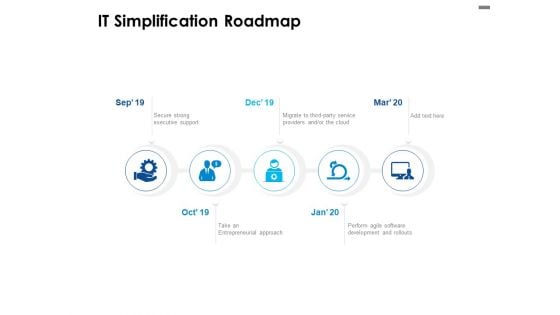
IT Simplification Roadmap Ppt PowerPoint Presentation Portfolio Picture
Presenting this set of slides with name it simplification roadmap ppt powerpoint presentation portfolio picture. This is a five stage process. The stages in this process are entrepreneurial approach, perform agile software development and rollouts, secure strong executive support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
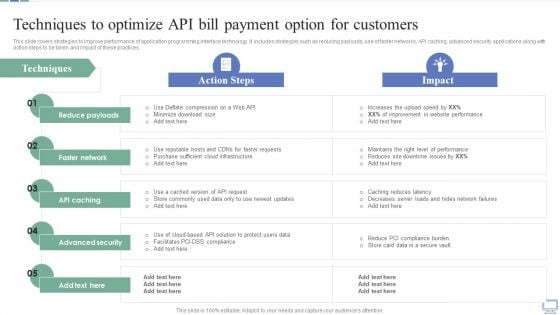
Omnichannel Banking Services Platform Techniques To Optimize API Bill Payment Option For Customers Demonstration PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. Present like a pro with Omnichannel Banking Services Platform Techniques To Optimize API Bill Payment Option For Customers Demonstration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
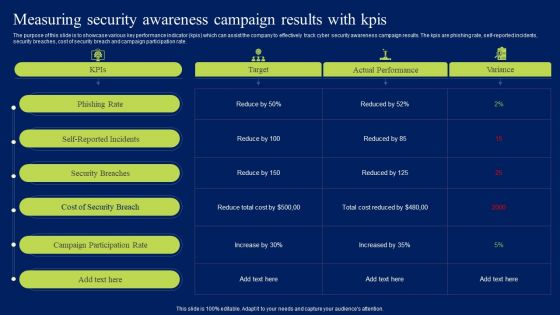
Measuring Security Awareness Campaign Results With Kpis Ppt Summary Sample PDF
The purpose of this slide is to showcase various key performance indicator kpis which can assist the company to effectively track cyber security awareness campaign results. The kpis are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. This modern and well-arranged Measuring Security Awareness Campaign Results With Kpis Ppt Summary Sample PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
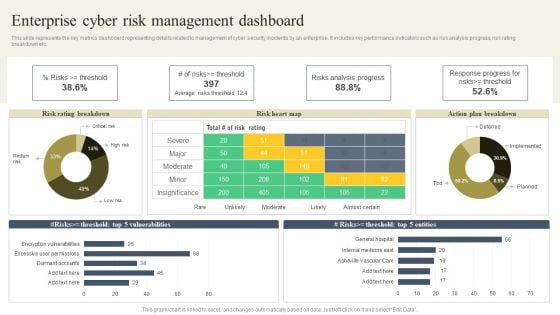
CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Are you searching for a CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF from Slidegeeks today.
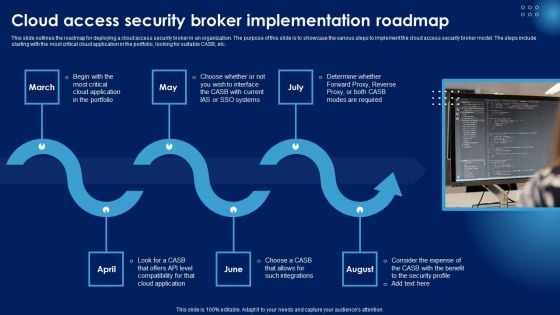
Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.

Web Access Control Solution 30 60 90 Days Plan To Integrate Secure Web Gateway Into Organizational
This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution 30 60 90 Days Plan To Integrate Secure Web Gateway Into Organizational will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management.. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. This Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
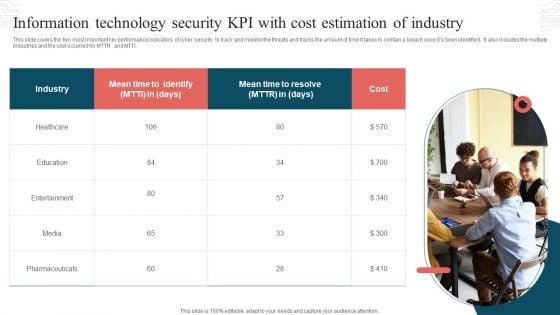
Information Technology Security KPI With Cost Estimation Of Industry Topics PDF
This slide covers the two most important key performance indicators of cyber security to track and monitor the threats and tracks the amount of time it takes to contain a breach once its been identified. It also includes the multiple industries and the cost occurred for MTTR and MTTI. Persuade your audience using this Information Technology Security KPI With Cost Estimation Of Industry Topics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Industry, Mean Time, Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Cyber Security Awareness Trends In 2023 Infographics PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. rom laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Prevention Of Information Cyber Security Awareness Trends In 2023 Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Cyber Security Awareness Trends Download PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. Increase malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cybersecurity Awareness Program To Prevent Attacks Cyber Security Awareness Trends Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
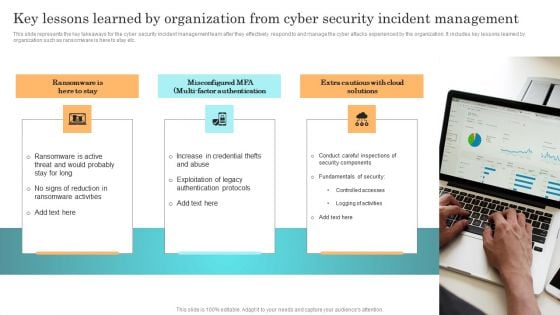
Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF
The following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Take your projects to the next level with our ultimate collection of Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
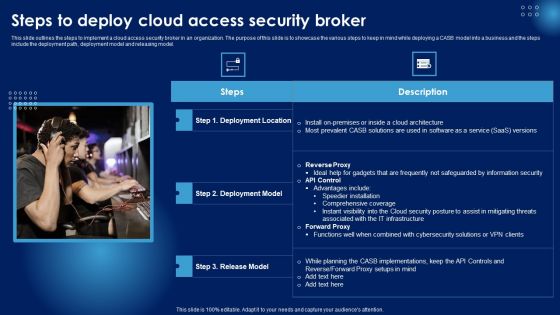
Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Organizational Assets Security Management Strategy Evaluating Financial Practices In Firm Formats PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Slidegeeks is here to make your presentations a breeze with Organizational Assets Security Management Strategy Evaluating Financial Practices In Firm Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
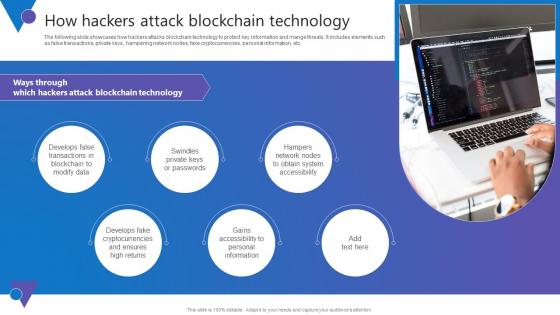
How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc.
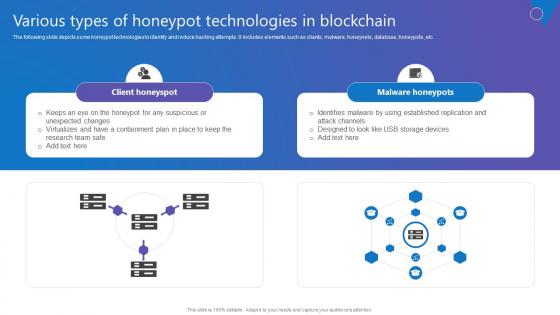
Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.

Pros And Cons Of Private Blockchain Different Architectures Of Blockchain Inspiration Pdf
This slide represents the Pros and Cons of the private blockchain framework based on factors such as speed, flexibility, trust building, and security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Pros And Cons Of Private Blockchain Different Architectures Of Blockchain Inspiration Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the Pros and Cons of the private blockchain framework based on factors such as speed, flexibility, trust building, and security.
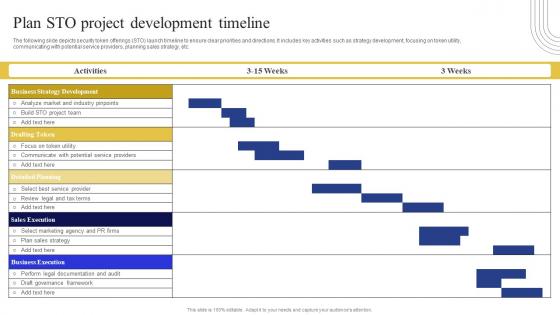
Plan Sto Project Development Timeline Exploring Investment Opportunities Themes Pdf
The following slide depicts security token offerings STO launch timeline to ensure clear priorities and directions. It includes key activities such as strategy development, focusing on token utility, communicating with potential service providers, planning sales strategy, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Plan Sto Project Development Timeline Exploring Investment Opportunities Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts security token offerings STO launch timeline to ensure clear priorities and directions. It includes key activities such as strategy development, focusing on token utility, communicating with potential service providers, planning sales strategy, etc.

Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF
This slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Zero Trust Model Case Study Intellectual Property Protection
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Case Study Intellectual Property Protection will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.

Content Protection Mechanisms In Mobile Application Areas Of Mobile Cloud Computing
The purpose of the mentioned slide is to showcase the content protection techniques to secure mobile cloud media streaming. It includes encryption, secure authentication and authorization, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Content Protection Mechanisms In Mobile Application Areas Of Mobile Cloud Computing will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of the mentioned slide is to showcase the content protection techniques to secure mobile cloud media streaming. It includes encryption, secure authentication and authorization, etc.
Bluetooth Low Energy Ble Maximizing Efficiency With Asset Tracking Solutions Formats Pdf
This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Bluetooth Low Energy Ble Maximizing Efficiency With Asset Tracking Solutions Formats Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications.
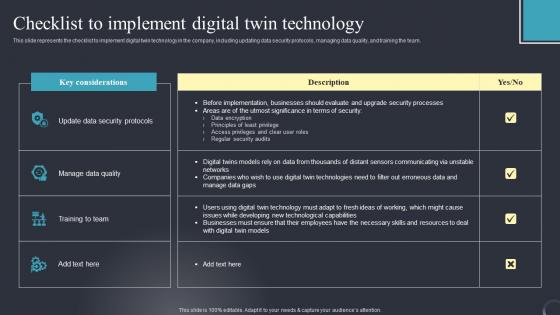
Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team.

Company Introduction Paubox Capital Funding Pitch Deck Mockup Pdf
This slide covers a company overview of email security enterprise. It includes information such as foundation date, company status, employee count, headquarters, website, and industry. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Company Introduction Paubox Capital Funding Pitch Deck Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers a company overview of email security enterprise. It includes information such as foundation date, company status, employee count, headquarters, website, and industry.
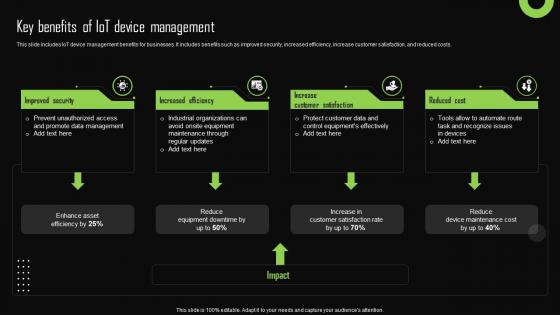
Key Benefits Of Iot Device Management Iot Device Management Designs Pdf
This slide includes IoT device management benefits for businesses. It includes benefits such as improved security, increased efficiency, increase customer satisfaction, and reduced costs. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Benefits Of Iot Device Management Iot Device Management Designs Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide includes IoT device management benefits for businesses. It includes benefits such as improved security, increased efficiency, increase customer satisfaction, and reduced costs.

Clarify Roles And Responsibilities Of STO Exploring Investment Opportunities Infographics Pdf
The following slide illustrates major roles and responsibilities of security token offerings team to ensure successful launch. It includes elements such as technical officer, community manager, engineers, developers, founder, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Clarify Roles And Responsibilities Of STO Exploring Investment Opportunities Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide illustrates major roles and responsibilities of security token offerings team to ensure successful launch. It includes elements such as technical officer, community manager, engineers, developers, founder, etc.
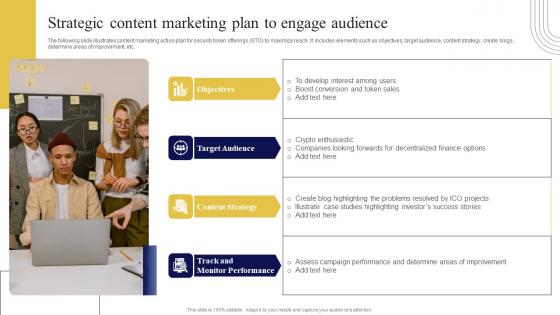
Strategic Content Marketing Plan To Engage Exploring Investment Opportunities Themes Pdf
The following slide illustrates content marketing action plan for security token offerings STO to maximize reach. It includes elements such as objectives, target audience, content strategy, create blogs, determine areas of improvement, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Strategic Content Marketing Plan To Engage Exploring Investment Opportunities Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide illustrates content marketing action plan for security token offerings STO to maximize reach. It includes elements such as objectives, target audience, content strategy, create blogs, determine areas of improvement, etc.
Bluetooth Low Energy Ble Asset Tracking Technique RFID Solutions For Asset Traceability Mockup Pdf
This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Bluetooth Low Energy Ble Asset Tracking Technique RFID Solutions For Asset Traceability Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications.
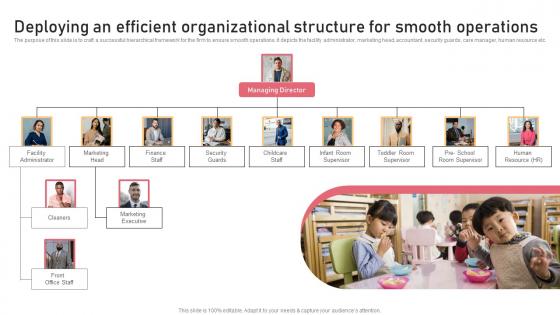
Deploying An Efficient Organizational Structure Childcare Business Plan Download Pdf
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Deploying An Efficient Organizational Structure Childcare Business Plan Download Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc.
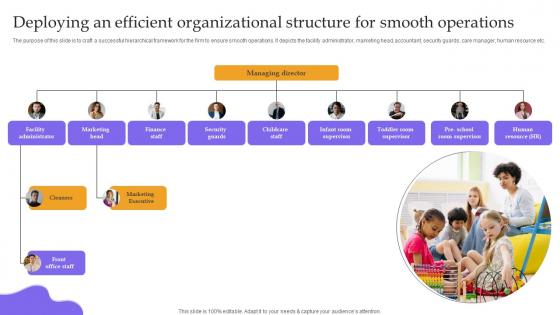
Deploying An Efficient Organizational Structure For Childcare Business Plan Structure Pdf
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Deploying An Efficient Organizational Structure For Childcare Business Plan Structure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc.

Budget Requirements For IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V
Following slide exhibits budget allocation for implementing IoT devices and technology based infrastructure in educational premises. It includes elements such as technology deployment, security, integration, support, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Budget Requirements For IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Following slide exhibits budget allocation for implementing IoT devices and technology based infrastructure in educational premises. It includes elements such as technology deployment, security, integration, support, etc.
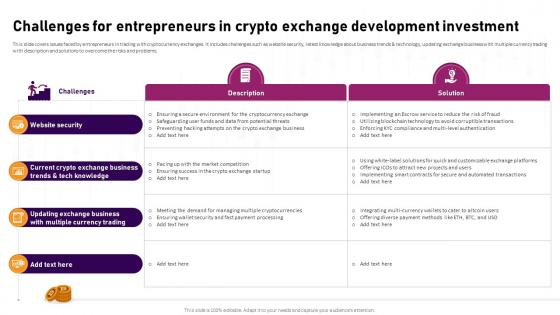
Challenges For Entrepreneurs In Crypto Exchange Complete Roadmap To Blockchain BCT SS V
This slide covers issues faced by entrepreneurs in trading with cryptocurrency exchanges. It includes challenges such as website security, latest knowledge about business trends and technology, updating exchange business with multiple currency trading with description and solutions to overcome the risks and problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Challenges For Entrepreneurs In Crypto Exchange Complete Roadmap To Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers issues faced by entrepreneurs in trading with cryptocurrency exchanges. It includes challenges such as website security, latest knowledge about business trends and technology, updating exchange business with multiple currency trading with description and solutions to overcome the risks and problems.

Overview Of Decentralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V
This slide covers brief summary of decentralized crypto exchanges with ways to operate by users. It also includes benefits such as faster and cheaper transactions, secure, integration with hardware wallets, users control funds, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Decentralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers brief summary of decentralized crypto exchanges with ways to operate by users. It also includes benefits such as faster and cheaper transactions, secure, integration with hardware wallets, users control funds, etc.
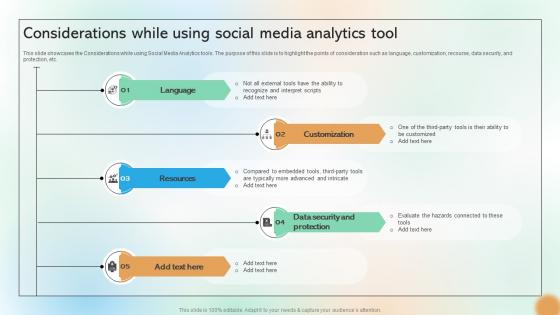
Considerations While Using Social Media Analytics Tool Cracking The Code Of Social Media
This slide showcases the Considerations while using Social Media Analytics tools. The purpose of this slide is to highlight the points of consideration such as language, customization, recourse, data security, and protection, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Considerations While Using Social Media Analytics Tool Cracking The Code Of Social Media will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the Considerations while using Social Media Analytics tools. The purpose of this slide is to highlight the points of consideration such as language, customization, recourse, data security, and protection, etc.
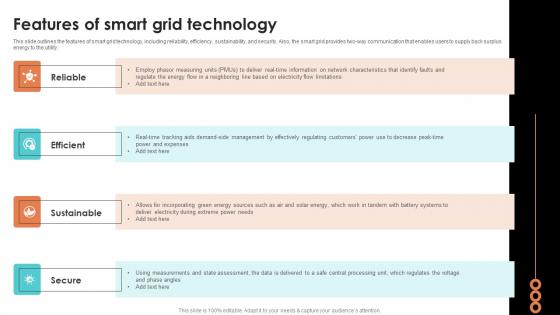
Features Of Smart Grid Technology Smart Grid Working
This slide outlines the features of smart grid technology, including reliability, efficiency, sustainability, and security. Also, the smart grid provides two way communication that enables users to supply back surplus energy to the utility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Features Of Smart Grid Technology Smart Grid Working will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the features of smart grid technology, including reliability, efficiency, sustainability, and security. Also, the smart grid provides two way communication that enables users to supply back surplus energy to the utility.
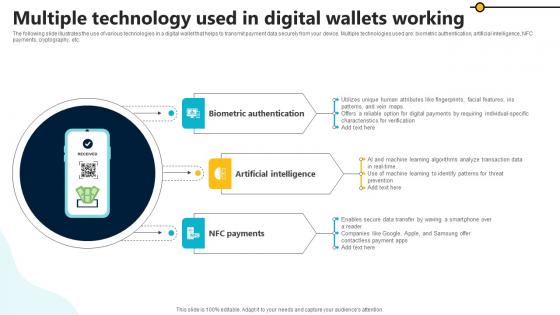
Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V
The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc.

Comprehensive Look At Blockchain Skills Required To Become Blockchain BCT SS V
This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comprehensive Look At Blockchain Skills Required To Become Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles.

Seamless Integration The Power Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Seamless Integration The Power Comparative Analysis Of Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases.

Unlocking The Potential Of Introduction To Nfts In Gaming Landscape BCT SS V
This slide provide overview of the concept of Non Fungible Tokens and their role in blockchain gaming at large. Key role highlighted includes ownership of virtual items, ownership of in game assets, buying or selling through marketplace and security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Unlocking The Potential Of Introduction To Nfts In Gaming Landscape BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provide overview of the concept of Non Fungible Tokens and their role in blockchain gaming at large. Key role highlighted includes ownership of virtual items, ownership of in game assets, buying or selling through marketplace and security.
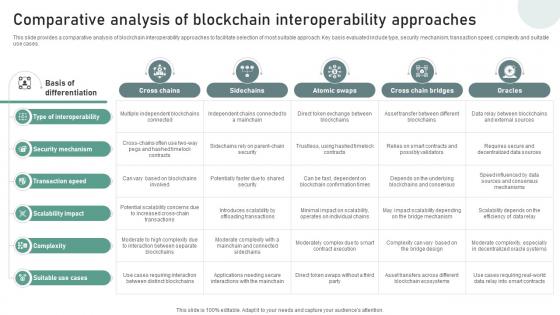
Bridging Blockchains A Deep Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Bridging Blockchains A Deep Comparative Analysis Of Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases.
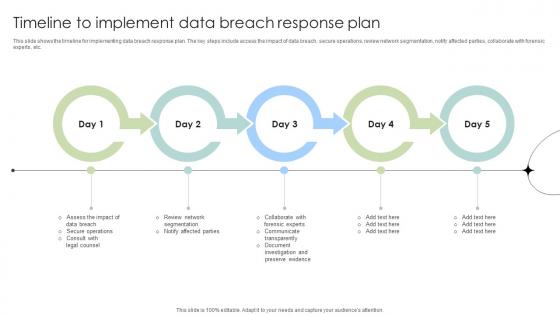
Timeline To Implement Data Breach Response Plan Data Fortification Strengthening Defenses
This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline To Implement Data Breach Response Plan Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc.
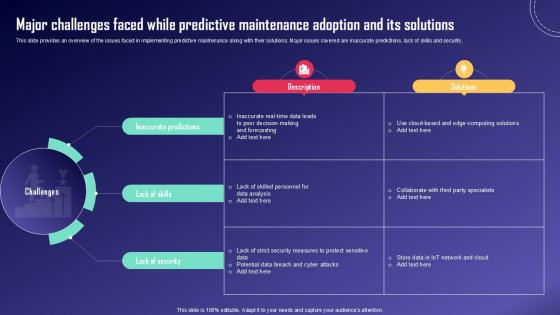
Major Challenges Faced While IoT Fleet Monitoring Ppt Template IoT SS V
This slide provides an overview of the issues faced in implementing predictive maintenance along with their solutions. Major issues covered are inaccurate predictions, lack of skills and security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Major Challenges Faced While IoT Fleet Monitoring Ppt Template IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides an overview of the issues faced in implementing predictive maintenance along with their solutions. Major issues covered are inaccurate predictions, lack of skills and security.
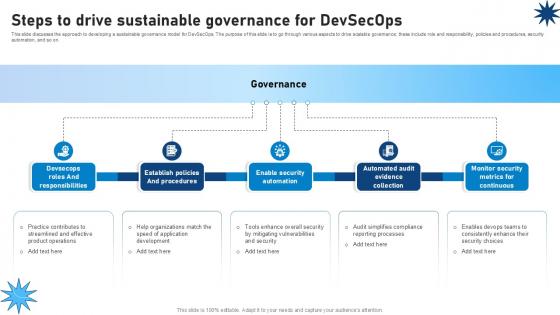
Steps To Drive Sustainable Governance For Devsecops Role Of Devsecops Ppt Sample
This slide discusses the approach to developing a sustainable governance model for DevSecOps. The purpose of this slide is to go through various aspects to drive scalable governance these include role and responsibility, policies and procedures, security automation, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Drive Sustainable Governance For Devsecops Role Of Devsecops Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses the approach to developing a sustainable governance model for DevSecOps. The purpose of this slide is to go through various aspects to drive scalable governance these include role and responsibility, policies and procedures, security automation, and so on.
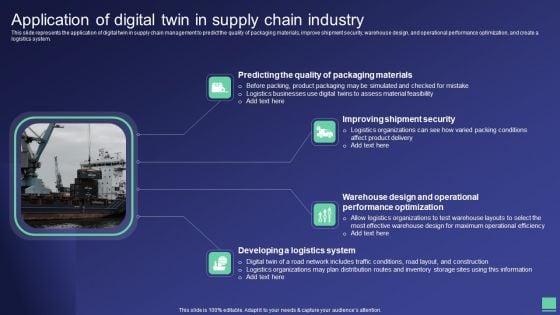
Digital Twin Tech IT Application Of Digital Twin In Supply Chain Industry Information PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Digital Twin Tech IT Application Of Digital Twin In Supply Chain Industry Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
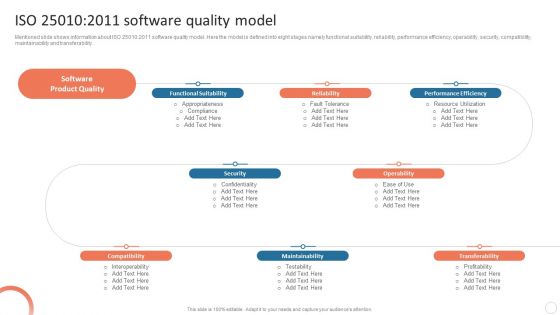
Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF
Mentioned slide shows information about ISO 25010 2011 software quality model. Here the model is defined into eight stages namely functional suitability, reliability, performance efficiency, operability, security, compatibility, maintainability and transferability. Find highly impressive Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Deploying AI To Enhance Digital Twin Technology Supply Chain Management Rules PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Find highly impressive Deploying AI To Enhance Digital Twin Technology Supply Chain Management Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Deploying AI To Enhance Digital Twin Technology Supply Chain Management Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
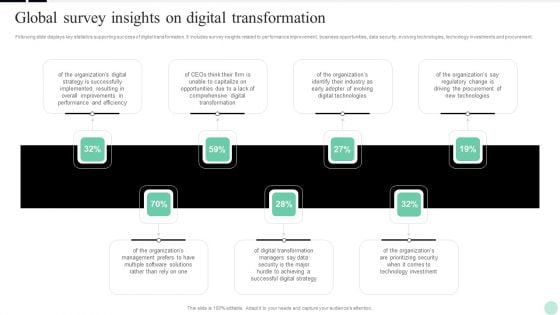
Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF
Following slide displays key statistics supporting success of digital transformation. It includes survey insights related to performance improvement, business opportunities, data security, evolving technologies, technology investments and procurement. This Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
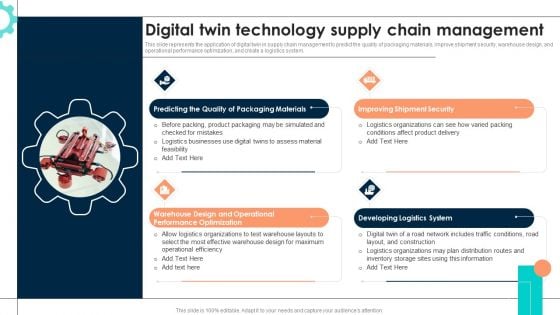
Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
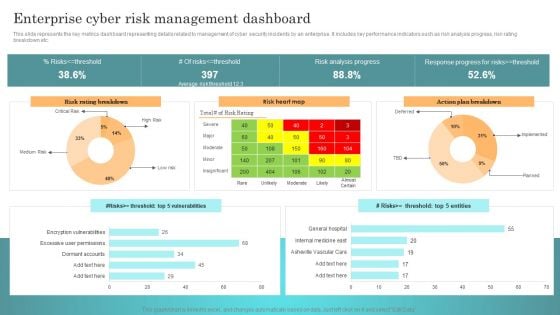
Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Find highly impressive Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
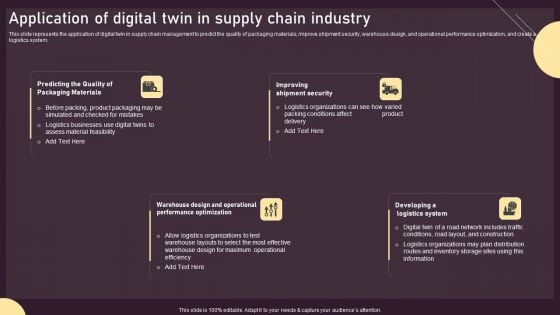
Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. This Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today


 Continue with Email
Continue with Email

 Home
Home


































