Safety Performance
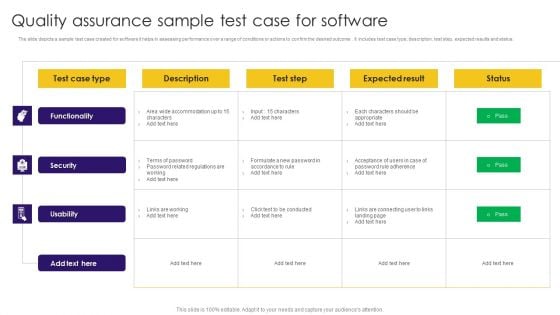
Quality Assurance Sample Test Case For Software Ppt Show Summary PDF
The slide depicts a sample test case created for software it helps in assessing performance over a range of conditions or actions to confirm the desired outcome. it includes test case type, description, test step, expected results and status. Pitch your topic with ease and precision using this Quality Assurance Sample Test Case For Software Ppt Show Summary PDF. This layout presents information on Functionality, Security, Usability, Test Case Type. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Optimizing Production Process Major Impact Of Smart Factory On Enterprises Template PDF
This slide represents major impacts of smart factory. It includes production process monitoring, asset visibility, data analysis and employee and asset security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Optimizing Production Process Major Impact Of Smart Factory On Enterprises Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Resolving Virtual Virtual Team Management Challenges Rules PDF
Following slide demonstrates ways to manage remote team challenges which organizations employ to eliminate potential threats and enhance productivity. This slide provides data regarding challenges, description, solutions and overall impact. Pitch your topic with ease and precision using this Resolving Virtual Virtual Team Management Challenges Rules PDF. This layout presents information on Communication, Project Collaborations, Performance Management, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
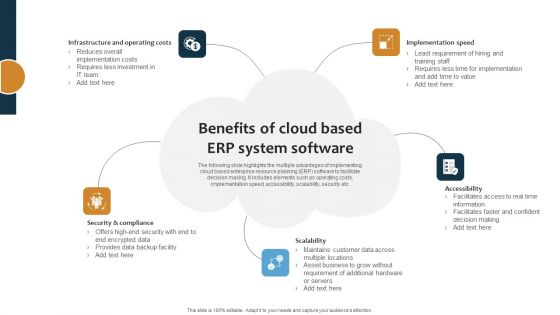
Improving Business Procedures Enterprise Resource Planning System Benefits Of Cloud Based Erp Inspiration PDF
The following slide highlights the multiple advantages of implementing cloud based enterprise resource planning ERP software to facilitate decision making. It includes elements such as operating costs, implementation speed, accessibility, scalability, security etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Improving Business Procedures Enterprise Resource Planning System Benefits Of Cloud Based Erp Inspiration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
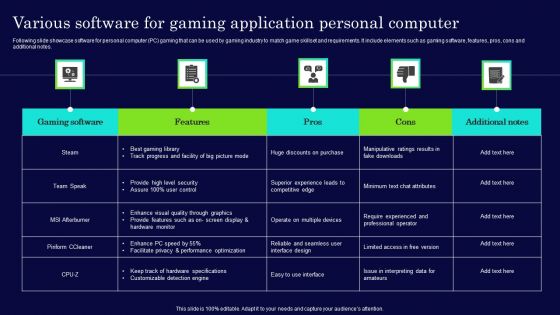
Various Software For Gaming Application Personal Computer Summary PDF
Following slide showcase software for personal computer PC gaming that can be used by gaming industry to match game skillset and requirements. It include elements such as gaming software, features, pros, cons and additional notes. Showcasing this set of slides titled Various Software For Gaming Application Personal Computer Summary PDF. The topics addressed in these templates are Team Speak, Performance Optimization, Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
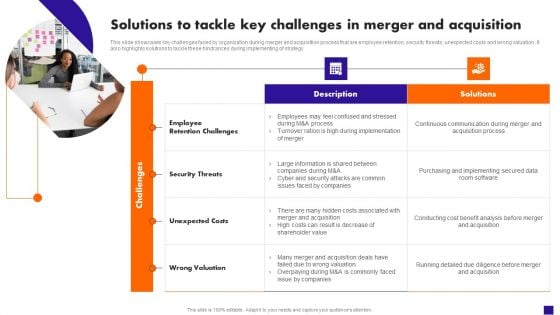
Solutions To Tackle Key Challenges In Merger And Acquisition Portrait PDF
This slide showcases key challenges faced by organization during merger and acquisition process that are employee retention, security threats, unexpected costs and wrong valuation. It also highlights solutions to tackle these hindrances during implementing of strategy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Solutions To Tackle Key Challenges In Merger And Acquisition Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Multi Level Marketing Company Outline Our Unique Selling Proposition USP Themes PDF
This slide highlights the Yashbiz company unique selling proposition which includes more than 80 products, secure shopping, 100 percent delivery and paid shipping. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Multi Level Marketing Company Outline Our Unique Selling Proposition USP Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Consumption Based Pricing Model Challenges In Recurring Business Model Slides PDF
The purpose of the following slide is to show multiple challenges that the company can face while implementing a recurring revenue model , these challenges can be customer management, payment security and invoicing. Make sure to capture your audiences attention in your business displays with our gratis customizable Consumption Based Pricing Model Business Performance Dashboard Demonstration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
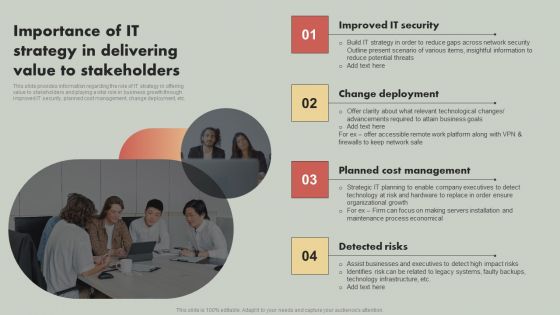
IT Reducing Costs And Management Tips Importance Of IT Strategy In Delivering Value To Stakeholders Pictures PDF
This slide provides information regarding the role of IT strategy in offering value to stakeholders and playing a vital role in business growth through improved IT security, planned cost management, change deployment, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. IT Reducing Costs And Management Tips Importance Of IT Strategy In Delivering Value To Stakeholders Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
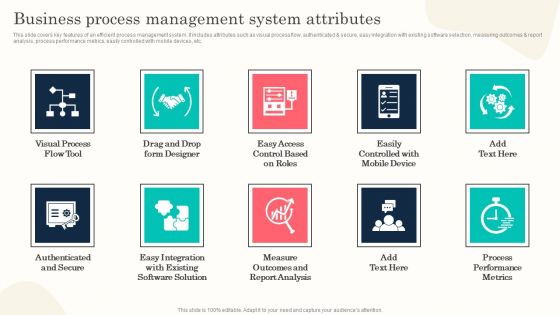
Business Process Management System Attributes Formats PDF
This slide covers key features of an efficient process management system. It includes attributes such as visual process flow, authenticated and secure, easy integration with existing software selection, measuring outcomes and report analysis, process performance metrics, easily controlled with mobile devices, etc. There are so many reasons you need a Business Process Management System Attributes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Essential Iot Value Drivers Ppt Inspiration Design Templates PDF
This slide provides information regarding essential implementing IoT value drivers such as simplified proximity triggers, automated product security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Essential Iot Value Drivers Ppt Inspiration Design Templates PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
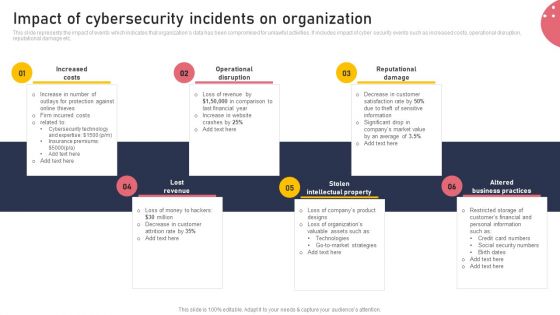
Impact Of Cybersecurity Incidents On Organization Microsoft PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Impact Of Cybersecurity Incidents On Organization Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Major Reasons For Not Automating Manual Tasksoptimizing Business Processes Through Automation Infographics PDF
The following slide outlines different reasons due to which the organization is not implementing process automation at workplace. The key reasons highlighted in the slide are higher cost, security concern and no formal training. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Major Reasons For Not Automating Manual Tasksoptimizing Business Processes Through Automation Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
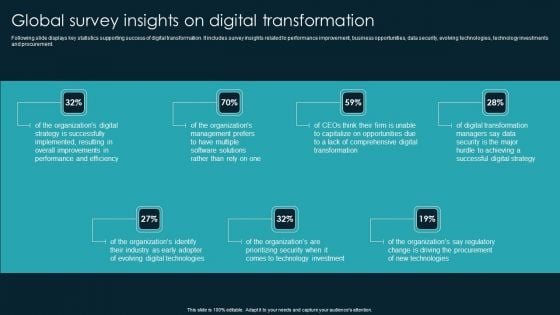
Global Survey Insights On Digital Transformation Icons PDF

Iot Integration In Manufacturing Digital Twin Technology Supply Chain Management Slides PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Iot Integration In Manufacturing Digital Twin Technology Supply Chain Management Slides PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Intelligent Process Automation IPA Machine Learning Applications In Different Areas Icons PDF
This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Intelligent Process Automation IPA Machine Learning Applications In Different Areas Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
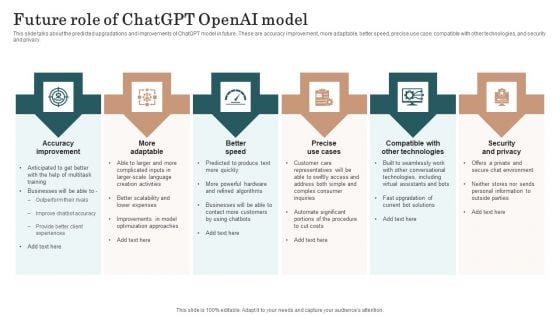
Chatgpt Incorporation Into Web Apps Future Role Of Chatgpt Openai Model Topics PDF
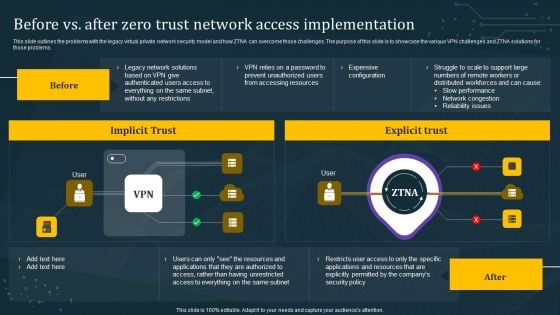
Before Vs After Zero Trust Network Access Implementation Background PDF
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Zero Trust Network Access Implementation Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Comparison Between CASB And Data Loss Prevention DLP Ppt PowerPoint Presentation File Portfolio PDF
This slide describes the difference between cloud access security broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Comparison Between CASB And Data Loss Prevention DLP Ppt PowerPoint Presentation File Portfolio PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
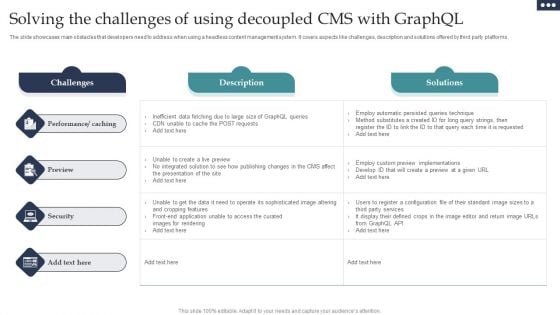
Solving The Challenges Of Using Decoupled CMS With Graphql Portrait PDF
The slide showcases main obstacles that developers need to address when using a headless content management system. It covers aspects like challenges, description and solutions offered by third party platforms. Showcasing this set of slides titled Solving The Challenges Of Using Decoupled CMS With Graphql Portrait PDF. The topics addressed in these templates are Performance Caching, Preview, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
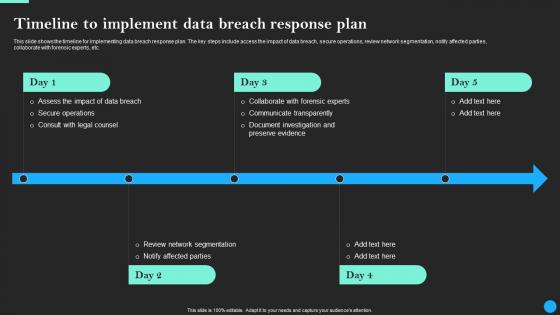
Timeline To Implement Data Breach Response Plan Data Breach Prevention Template Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline To Implement Data Breach Response Plan Data Breach Prevention Template Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc.
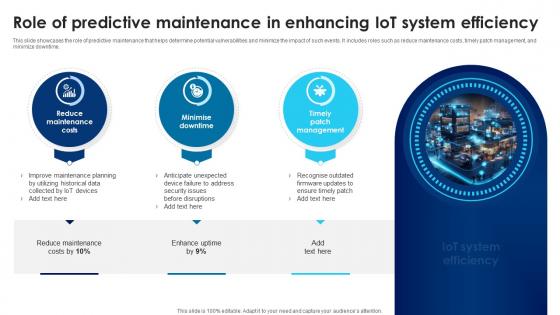
Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V
This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime.
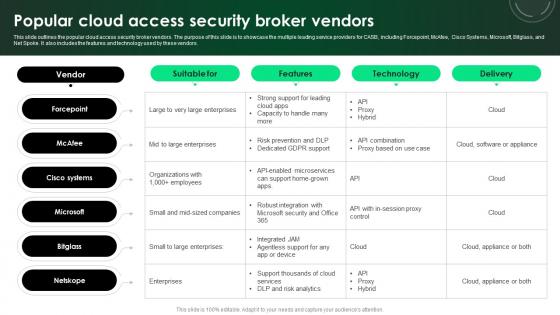
CASB 2 0 IT Popular Cloud Access Security Broker Vendors
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. CASB 2 0 IT Popular Cloud Access Security Broker Vendors will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors.
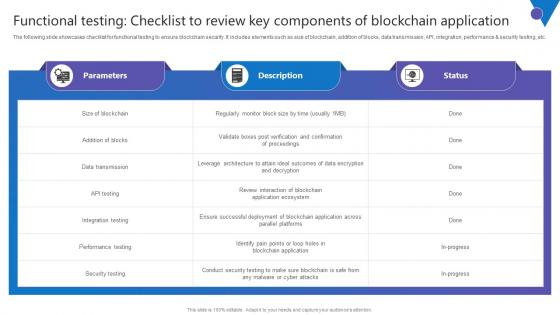
Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf
The following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc.

Digital Twin Technology Supply Chain Management Designs PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Digital Twin Technology Supply Chain Management Designs PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Digital Twin Technology Supply Chain Management Designs PDF. This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system.

IoT Device Management Fundamentals IoT Device Monitoring Dashboard To Analyse IoT Ss V
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. Slidegeeks is here to make your presentations a breeze with IoT Device Management Fundamentals IoT Device Monitoring Dashboard To Analyse IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc.
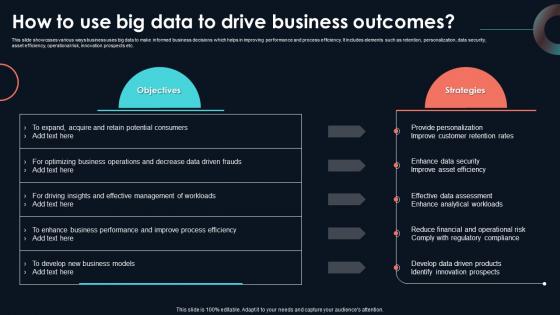
How To Use Big Data To Drive Business Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases various ways business uses big data to make informed business decisions which helps in improving performance and process efficiency. It includes elements such as retention, personalization, data security, asset efficiency, operational risk, innovation prospects etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download How To Use Big Data To Drive Business Developing Strategic Insights Using Big Data Analytics SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the How To Use Big Data To Drive Business Developing Strategic Insights Using Big Data Analytics SS V. This slide showcases various ways business uses big data to make informed business decisions which helps in improving performance and process efficiency. It includes elements such as retention, personalization, data security, asset efficiency, operational risk, innovation prospects etc.

Process Of Disaster Recovery Planning IT Security IT Ppt Outline Example Introduction PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a process of disaster recovery planning it security it ppt outline example introduction pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data collection, plan testing, approval, perform risk analysis, prioritize procedures and operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
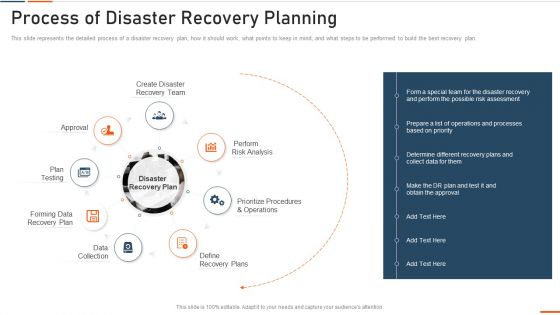
Information Technology Security Process Of Disaster Recovery Planning Ppt Portfolio Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information technology security process of disaster recovery planning ppt portfolio summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like approval, plan testing, recovery plan, data collection, perform . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
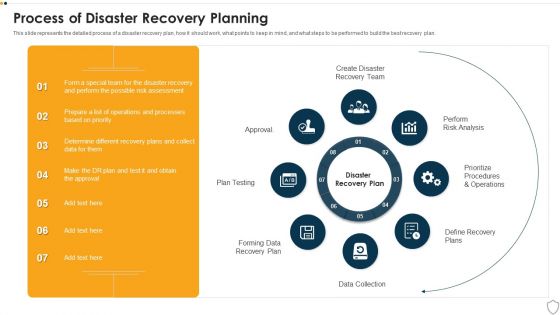
IT Security Process Of Disaster Recovery Planning Ppt Portfolio Microsoft PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting it security process of disaster recovery planning ppt portfolio microsoft pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like plan testing, perform risk analysis, data collection, prioritize procedures and operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
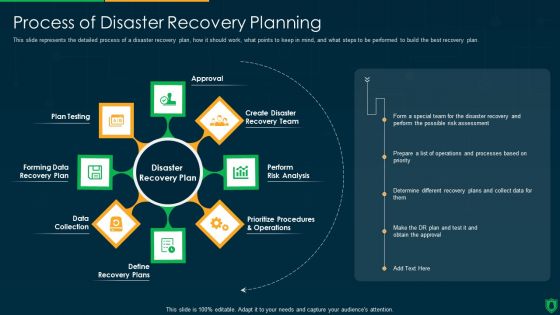
Info Security Process Of Disaster Recovery Planning Ppt PowerPoint Presentation File Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a info security process of disaster recovery planning ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like approval, perform risk analysis, define recovery plans, data collection, forming data recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.
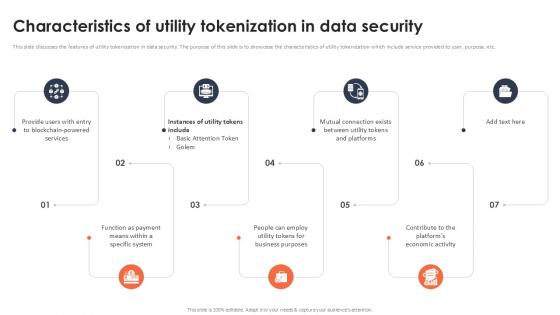
Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.
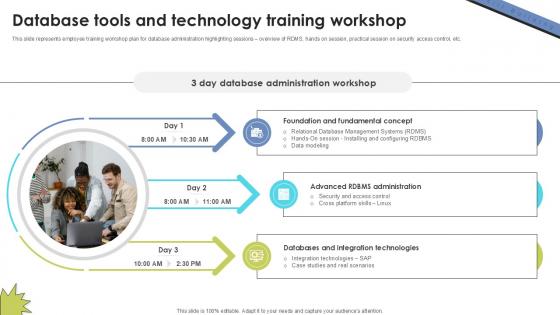
Database Tools And Technology Skill Building Plan For Application PPT Presentation DTE SS V
This slide represents employee training workshop plan for database administration highlighting sessions overview of RDMS, hands on session, practical session on security access control, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Database Tools And Technology Skill Building Plan For Application PPT Presentation DTE SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents employee training workshop plan for database administration highlighting sessions overview of RDMS, hands on session, practical session on security access control, etc.
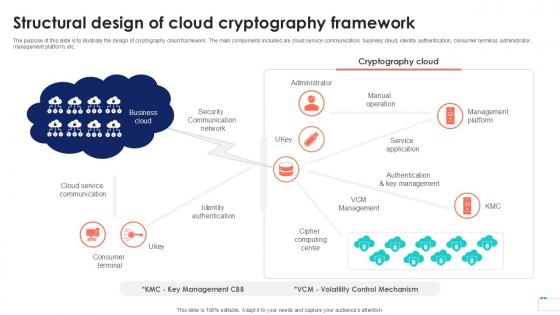
Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.

Malware Assessment Prevention Strategies From Infection Topics PDF
This slide demonstrates malware analysis approaches which assist businesses to protect and secure their system from attacks and threats. Up to date systems, being cautious of social engineering attacks, performing regular scans, etc. are few of the key approaches included in this slide. Presenting Malware Assessment Prevention Strategies From Infection Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Perform Regular Scans, Employ Best Security Practices, Create Backups. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
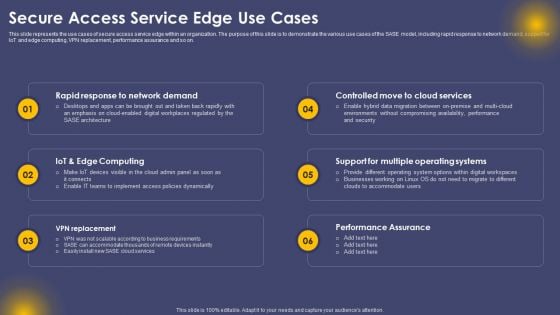
Secure Access Service Edge Use Cases Ppt Outline Images PDF
This slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Explore a selection of the finest Secure Access Service Edge Use Cases Ppt Outline Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Secure Access Service Edge Use Cases Ppt Outline Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Stop Signs PowerPoint Slides And Stop Road Signs Ppt Templates
Stop Signs PowerPoint Slides and Stop Road Signs PPT TemplatesThese high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Applaud the performance of your employees. Give them due credit through our Stop Signs PowerPoint Slides And Stop Road Signs Ppt Templates.

Existing It Security Infrastructure Constituents Corrective Regression Testing Ppt Slides
This slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Existing It Security Infrastructure Constituents Corrective Regression Testing Ppt Slides will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on.

Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc.

Tokenization Case Study Comforte Fashion Retailer Securing Your Data Ppt Example
This slide represents the tokenization case study at comforte fashion retailer. The purpose of this slide is to give an overview of the retailer, including the challenges they face and the solutions provided by tokenization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Tokenization Case Study Comforte Fashion Retailer Securing Your Data Ppt Example will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the tokenization case study at comforte fashion retailer. The purpose of this slide is to give an overview of the retailer, including the challenges they face and the solutions provided by tokenization.
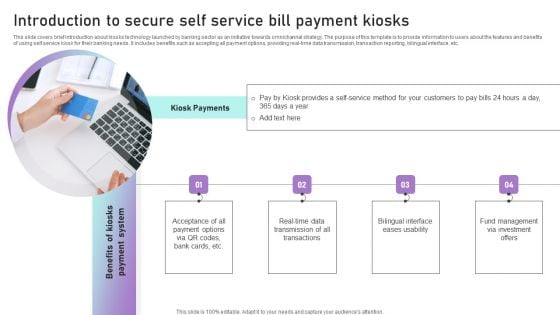
Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
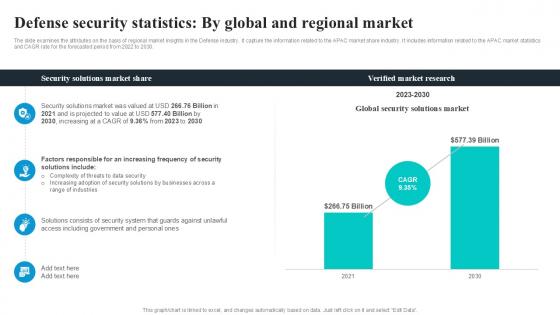
Defense Security Statistics By Global Security Industry PPT Sample IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates.Defense Security Statistics By Global Security Industry PPT Sample IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030.
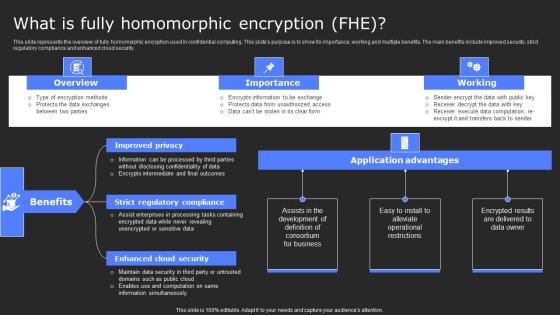
What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.
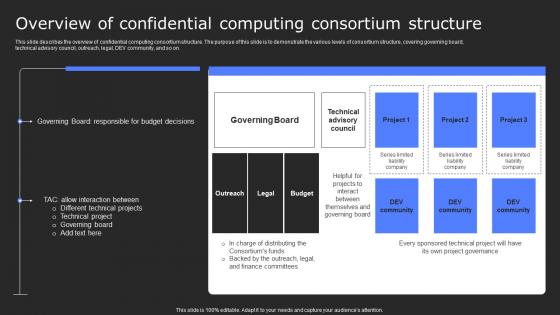
Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
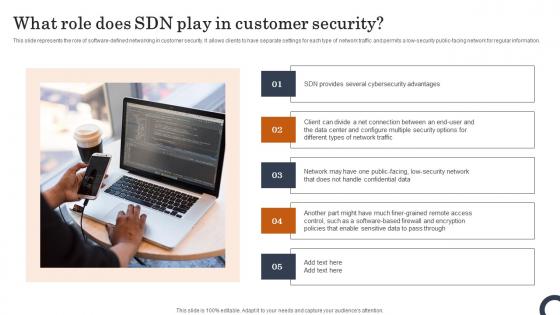
What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information.
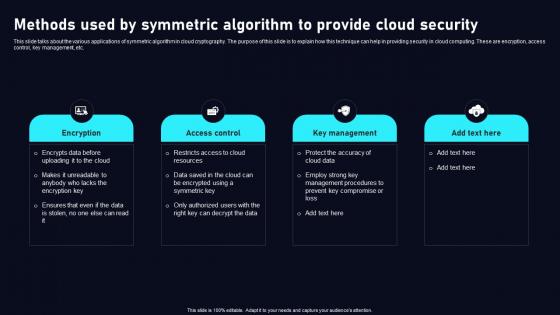
Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.

Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
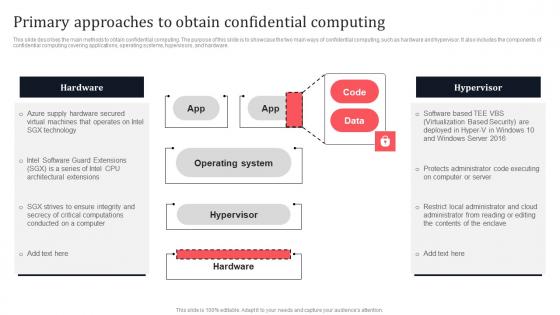
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
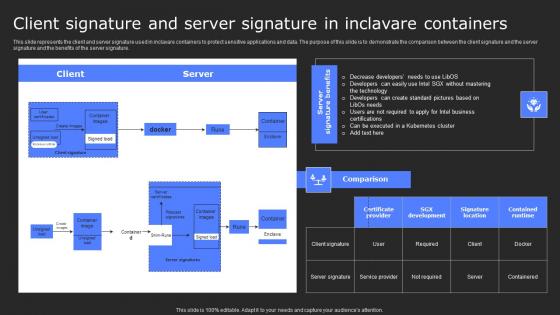
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.

Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost.

Secure Web Gateway Training Program Web Threat Protection System
This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Secure Web Gateway Training Program Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf
This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement.
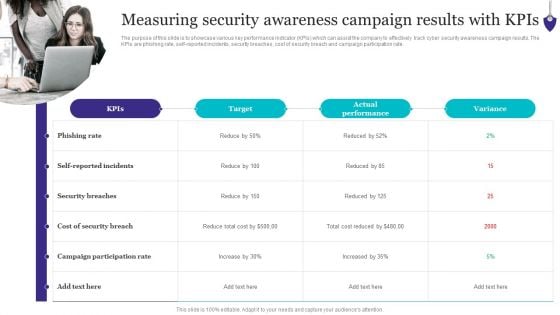
Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. Explore a selection of the finest Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Save Money Business PowerPoint Templates And PowerPoint Themes 1112
We present our Save Money Business PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because,To strive to give true form to your great dream. Use our Success PowerPoint Templates because, Our Template designs are State of the Art. Use our Business PowerPoint Templates because, Core Diagram:- Explore the various hues and layers existing in your in your plans and processes. Use our Money PowerPoint Templates because, Outline your targets to your team. Use our Finance PowerPoint Templates because, Support groups are an essential element of the ongoing struggle against cancer.Use these PowerPoint slides for presentations relating to Save money, security, success, business, money, finace. The prominent colors used in the PowerPoint template are Blue, Yellow, Black Performance evaluation is easier with our Save Money Business PowerPoint Templates And PowerPoint Themes 1112. They help you assess results accurately.

Lock With Money Protect Us Dollar Finance PowerPoint Templates And PowerPoint Themes 1112
Lock With Money Protect Us Dollar Finance PowerPoint Templates And PowerPoint Themes 1112-Visually support your Microsoft office PPT Presentation with our above template illustrating dollar money along with the lock signifying its security. This PowerPoint Template signifies the concept of Finance, Profit, Loss, money, economics, business, investment, backing, sponsorship, funding etc. Present your views using our innovative slides and be assured of leaving a lasting impression.-Lock With Money Protect Us Dollar Finance PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-US Money locked in a padlock, Money, Finance, Security, Business, Design Achieve performance reengineering with our Lock With Money Protect Us Dollar Finance PowerPoint Templates And PowerPoint Themes 1112. They will make you look good.
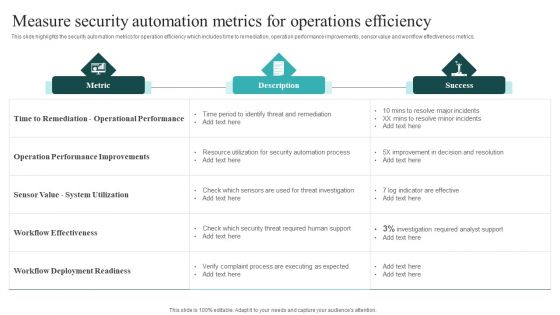
IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.


 Continue with Email
Continue with Email

 Home
Home


































