Safety Plan

IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. This is a IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organization, Customers, Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
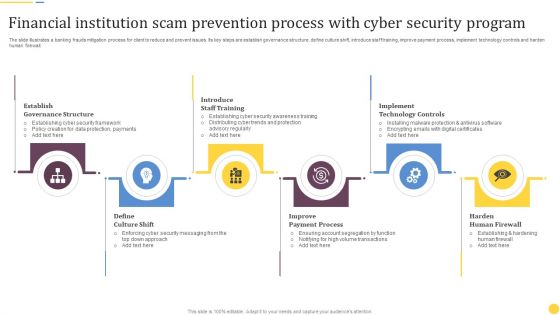
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF
This slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF
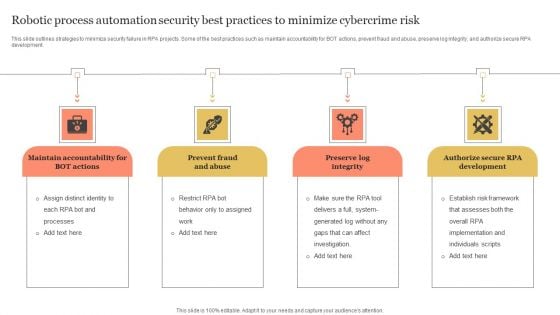
Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF
This slide outlines strategies to minimize security failure in RPA projects. Some of the best practices such as maintain accountability for BOT actions, prevent fraud and abuse, preserve log integrity, and authorize secure RPA development. Presenting Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Maintain Accountability, Prevent Fraud And Abuse, Preserve Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
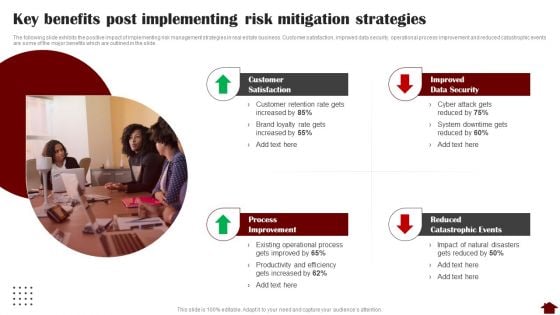
Key Benefits Post Implementing Risk Mitigation Strategies Professional PDF
The following slide exhibits the positive impact of implementing risk management strategies in real estate business. Customer satisfaction, improved data security, operational process improvement and reduced catastrophic events are some of the major benefits which are outlined in the slide. This is a Key Benefits Post Implementing Risk Mitigation Strategies Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Improvement, Reduced Catastrophic Events, Improved Data Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Assessment Tools And Techniques Ppt PowerPoint Presentation Gallery Picture PDF
The slide highlights various tools of cloud audit to guide and improve the vendors performance. Various tools and techniques included are cloud controls matrix, STAR questionnaire and CSA best practices. Persuade your audience using this Cloud Assessment Tools And Techniques Ppt PowerPoint Presentation Gallery Picture PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Controls Matrix, Security, Trust, Assurance, Risk Security Questionnaire. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
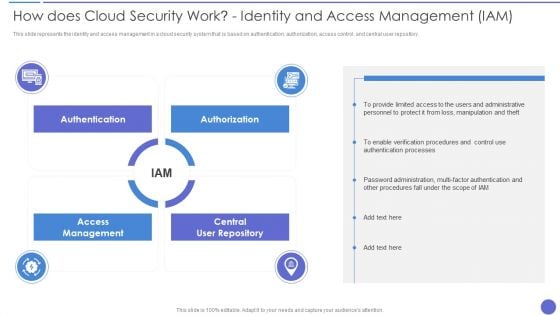
How Does Cloud Security Work Identity And Access Management IAM Professional PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a How Does Cloud Security Work Identity And Access Management IAM Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Accessibility, Security, Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
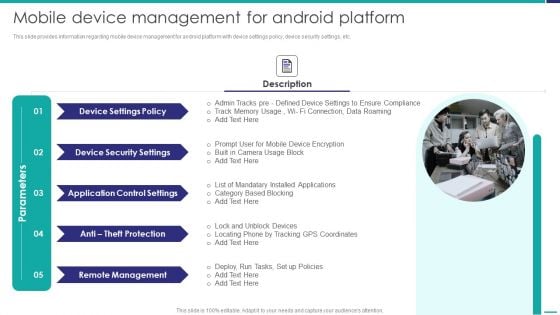
Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Presenting Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Device Security, Application Control, Remote Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
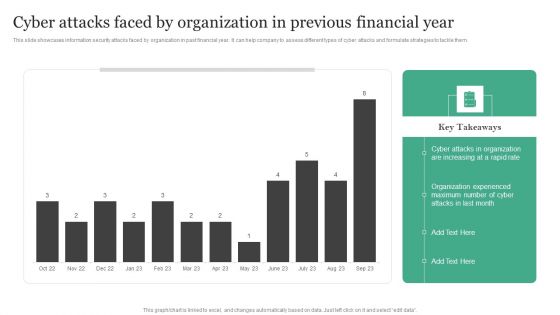
Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them.Create an editable Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
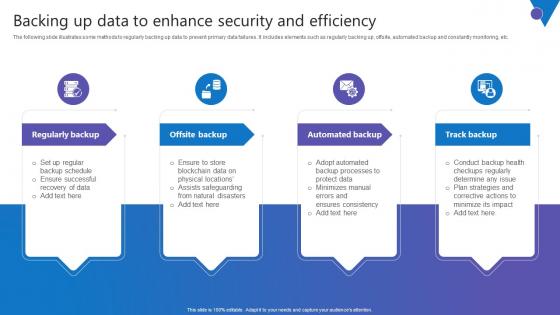
Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf. The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc.
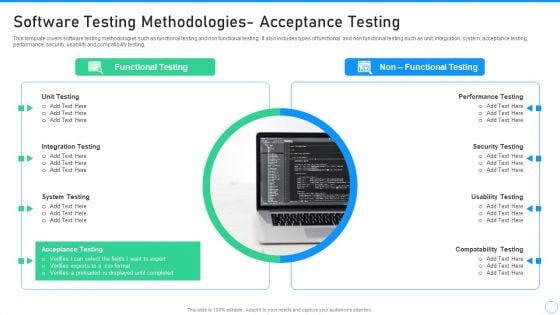
Application Designing And Programming Playbook Software Testing Methodologies Template PDF
This template covers software testing methodologies such as functional testing and non functional testing. It also includes types of functional and non functional testing such as unit, integration, system, acceptance testing, performance, security, usability and compatibility testing. This is a Application Designing And Programming Playbook Software Testing Methodologies Template PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Performance Testing, Usability Testing, Compatibility Testing You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Slidegeeks has constructed Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Information Technology Security Program Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Information Technology Security Program Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

IT Security Awareness Training Program Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this IT Security Awareness Training Program Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty four slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Slidegeeks has constructed Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
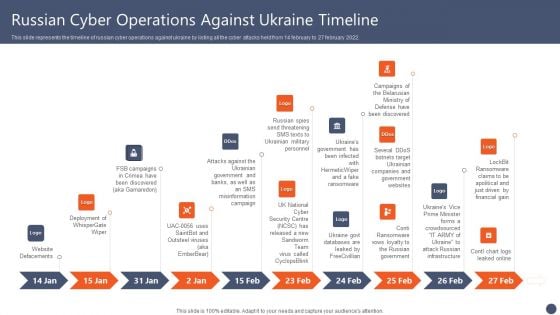
Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF
This slide represents the timeline of russian cyber operations against ukraine by listing all the cyber attacks held from 14 february to 27 february 2022. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Quarterly Business Project Management Calendar With Task Status Ppt Professional Maker PDF
This slide covers the quarterly timeline for project management which includes milestones, deliverables, alignment, research and evaluation with group staffing, budgetary reports, usage analytics, team review, idea generation, design research, securing budget, etc. Showcasing this set of slides titled Quarterly Business Project Management Calendar With Task Status Ppt Professional Maker PDF. The topics addressed in these templates are Preparing Presentation, Requirements Signoff, Usage Analytics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
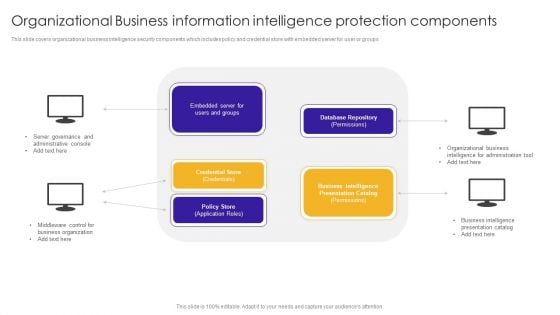
Organizational Business Information Intelligence Protection Components Background PDF
This slide covers organizational business intelligence security components which includes policy and credential store with embedded server for user or groups. Presenting Organizational Business Information Intelligence Protection Components Background PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Administrative Console, Server Governance, Middleware Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
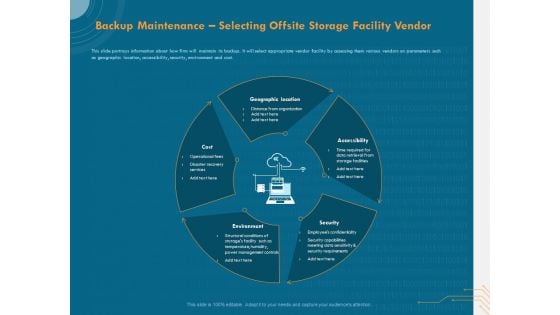
Cyber Security Implementation Framework Backup Maintenance Selecting Offsite Storage Facility Vendor Rules PDF
Presenting this set of slides with name cyber security implementation framework backup maintenance selecting offsite storage facility vendor rules pdf. This is a five stage process. The stages in this process are geographic location, accessibility, security, environment, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
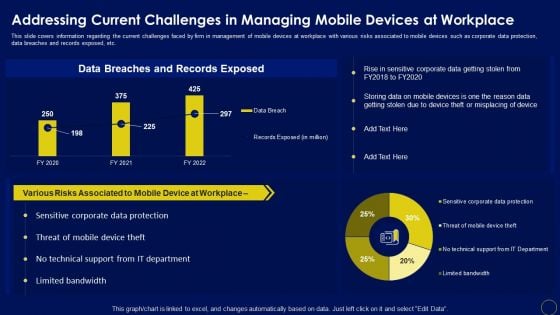
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Our Solution Email And Data Protection Platform Capital Funding Pitch Deck PPT Sample
This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA-compliant email encryption. Make sure to capture your audiences attention in your business displays with our gratis customizable Our Solution Email And Data Protection Platform Capital Funding Pitch Deck PPT Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA-compliant email encryption.
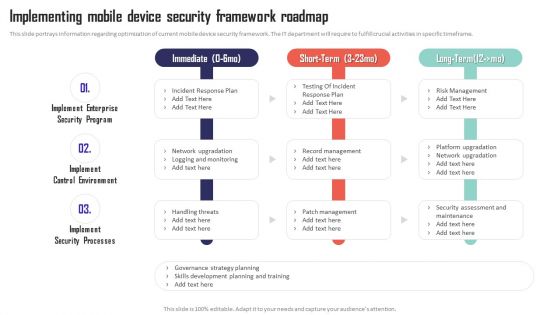
Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Get a simple yet stunning designed Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
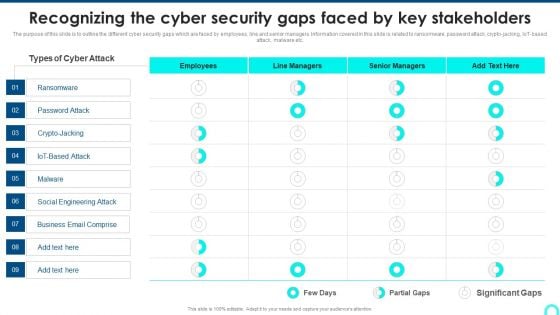
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Deliver and pitch your topic in the best possible manner with this Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF. Use them to share invaluable insights on Ransomware, Engineering Attack, Email Comprise and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Utilization Of Digital Industry Evolution Methods Ways To Bridge The Digital Transformation Skills Gap In Banking Download PDF
This slide shows the then ways and methods to close and bridge the digital skills gap in banking such as outsourcing IT tasks related to cybersecurity, providing IT training and being open to workers, embracing the tech talent from within etc. Deliver an awe inspiring pitch with this creative utilization of digital industry evolution methods ways to bridge the digital transformation skills gap in banking download pdf bundle. Topics like intelligence, infrastructure, management, security, concentrate, detection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Efficiency Execution Strategy Improve Quality Current Operational Process Improvement Guidelines PDF
This slide shows some of the current Operational Process Improvement challenges and issues that are faced by the company. Deliver and pitch your topic in the best possible manner with this operational efficiency execution strategy improve quality current operational process improvement guidelines pdf. Use them to share invaluable insights on management, process development, security, risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
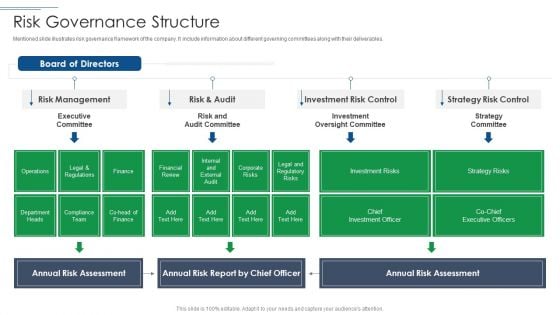
IT Security Risk Management Approach Introduction Risk Governance Structure Mockup PDF
Mentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Risk Governance Structure Mockup PDF. Use them to share invaluable insights on Risk Management, Investment Risk Control, Strategy Risk Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

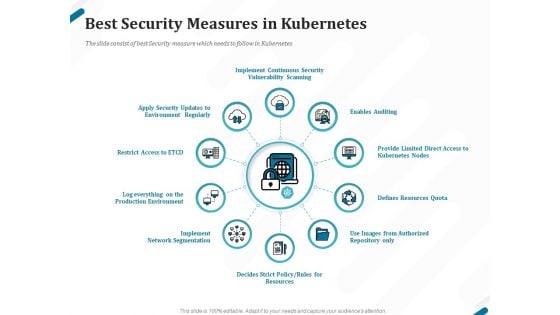
Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Kubernetes Containers Architecture Overview Best Security Measures In Kubernetes Ppt Pictures File Formats PDF
Presenting this set of slides with name kubernetes containers architecture overview best security measures in kubernetes ppt pictures file formats pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Mobile Device Management For Android Platform Business Mobile Device Security Management Graphics PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Slidegeeks is here to make your presentations a breeze with Mobile Device Management For Android Platform Business Mobile Device Security Management Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Complete Beginners Guide Solutions To Protect Bitcoin Against Security Threats Fin SS V
This slide shows solutions to various types of threats associated with Bitcoin s security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc. Boost your pitch with our creative Complete Beginners Guide Solutions To Protect Bitcoin Against Security Threats Fin SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide shows solutions to various types of threats associated with Bitcoin s security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc.
Information Systems Security Assessment Framework Ppt PowerPoint Presentation Portfolio Graphics Pictures Cpb
Presenting this set of slides with name information systems security assessment framework ppt powerpoint presentation portfolio graphics pictures cpb. This is an editable Powerpoint four stages graphic that deals with topics like information systems security assessment framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Information Security Controls Framework Ppt PowerPoint Presentation Infographic Template Gallery Cpb
Presenting this set of slides with name information security controls framework ppt powerpoint presentation infographic template gallery cpb. This is an editable Powerpoint eleven stages graphic that deals with topics like information security controls framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
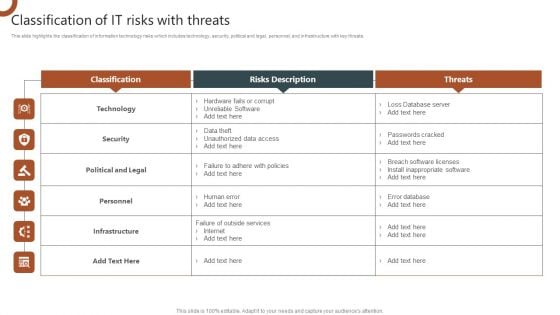
Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
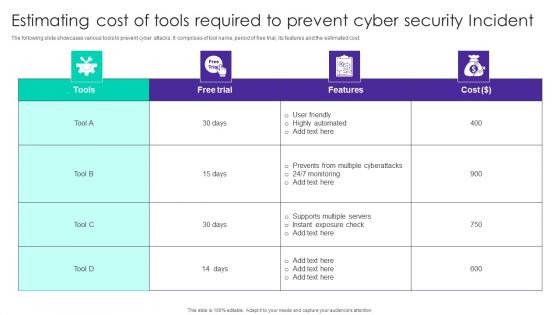
Estimating Cost Of Tools Required To Prevent Cyber Security Incident Ppt Gallery Master Slide PDF
The following slide showcases various tools to prevent cyber attacks. It comprises of tool name, period of free trial, its features and the estimated cost. Showcasing this set of slides titled Estimating Cost Of Tools Required To Prevent Cyber Security Incident Ppt Gallery Master Slide PDF. The topics addressed in these templates are Free Trial, Cost, User Friendly, Highly Automated. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
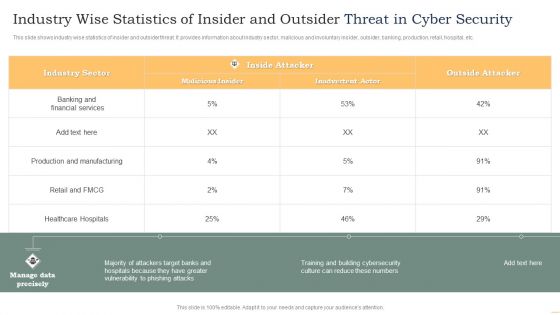
Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
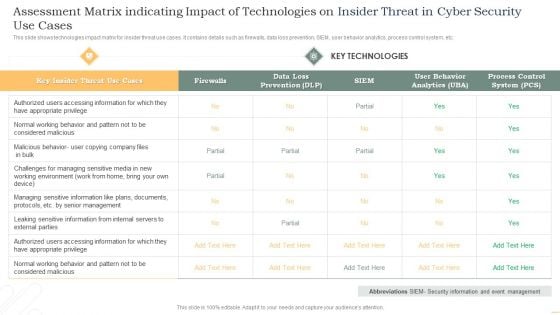
Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Kubernetes Containers Architecture Overview Table Of Content Ppt Summary Layout Ideas PDF
Presenting this set of slides with name kubernetes containers architecture overview table of content ppt summary layout ideas pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
8 Components Graphics For Business Security Techniques Ppt Inspiration Shapes PDF
Persuade your audience using this 8 components graphics for business security techniques ppt inspiration shapes pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 components graphics for business security techniques. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
PowerPoint Presentation Chart Lego Blocks Ppt Backgrounds
PowerPoint Presentation Chart Lego Blocks PPT Backgrounds-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Secure your promotion with our PowerPoint Presentation Chart Lego Blocks Ppt Backgrounds. Download without worries with our money back guaranteee.
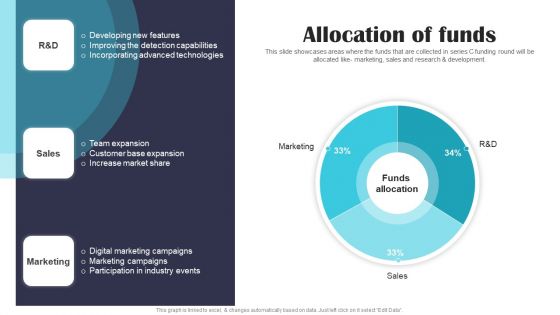
Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF
This slide showcases areas where the funds that are collected in series C funding round will be allocated like- marketing, sales and research and development. If you are looking for a format to display your unique thoughts, then the professionally designed Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
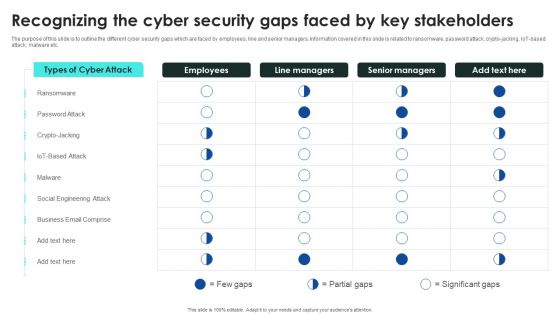
Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Get a simple yet stunning designed Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Analysis And Valuation Of Equity Securities Ppt PowerPoint Presentation Show Infographics
This is a analysis and valuation of equity securities ppt powerpoint presentation show infographics. This is a three stage process. The stages in this process are industry analysis, financial statement analysis, management, marketing, business, strategy.
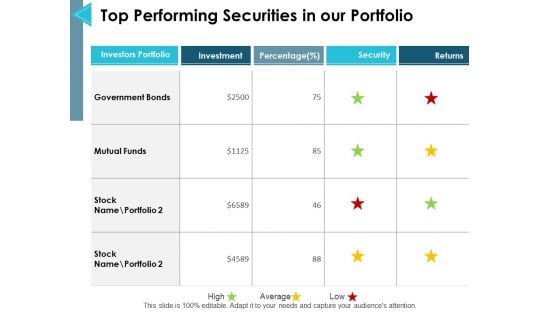
Top Performing Securities In Our Portfolio Ppt PowerPoint Presentation Ideas Slides
This is a top performing securities in our portfolio ppt powerpoint presentation ideas slides. The topics discussed in this diagram are mutual funds, management, marketing, business, strategy. This is a completely editable PowerPoint presentation and is available for immediate download.
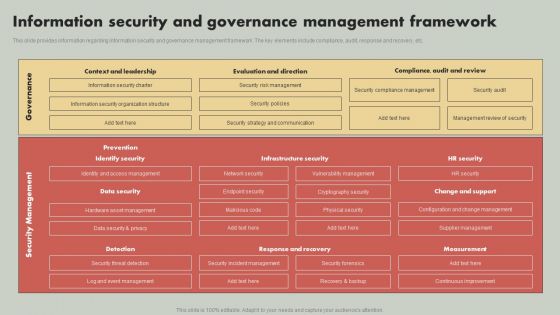
IT Reducing Costs And Management Tips Information Security And Governance Management Framework Demonstration PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate IT Reducing Costs And Management Tips Information Security And Governance Management Framework Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
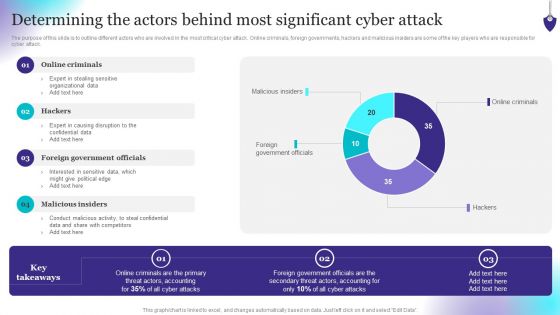
Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
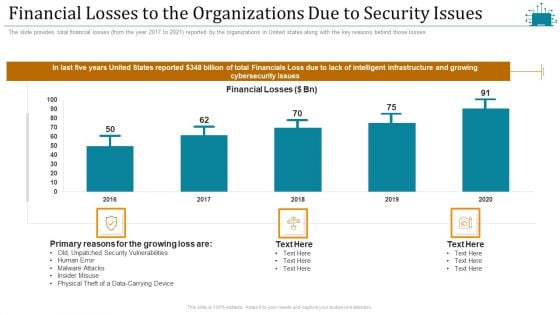
Cloud Intelligence Framework For Application Consumption Financial Losses To The Organizations Due To Security Issues Mockup PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption financial losses to the organizations due to security issues mockup pdf bundle. Topics like security vulnerabilities, primary reasons for the growing, physical theft of a data-carrying device, 2016 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
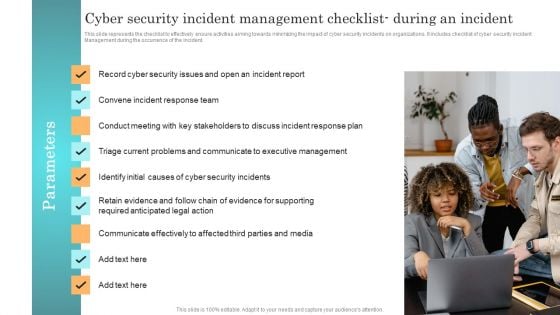
Incident Response Techniques Deployement Cyber Security Incident Management Checklist During An Incident Professional PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident Management during the occurrence of the incident. Create an editable Incident Response Techniques Deployement Cyber Security Incident Management Checklist During An Incident Professional PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Incident Response Techniques Deployement Cyber Security Incident Management Checklist During An Incident Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
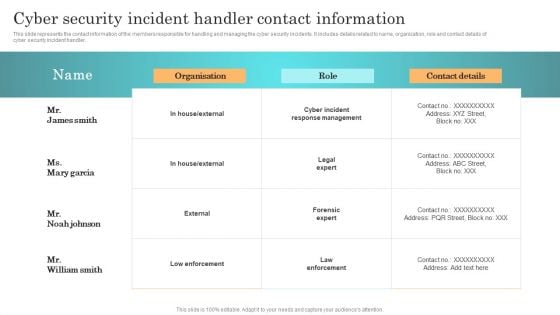
Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Get a simple yet stunning designed Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
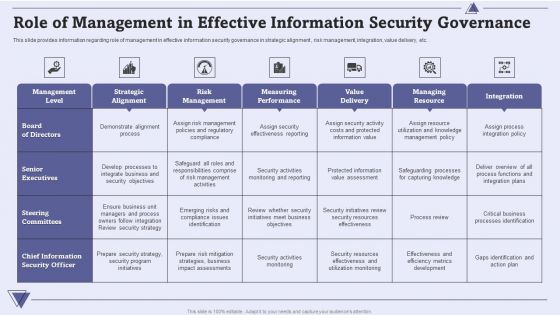
CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver and pitch your topic in the best possible manner with this CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF. Use them to share invaluable insights on Management Level, Strategic Alignment, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Environments Best Suited For Efficient And Secure Supply Chains Ppt Show Example PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains ppt show example pdf bundle. Topics like efficient supply chains, operations strategy, inventory investment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Environments Best Suited For Efficient And Secure Supply Chains Diagrams PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver and pitch your topic in the best possible manner with environments best suited for efficient and secure supply chains diagrams pdf. Use them to share invaluable insights on operations strategy, inventory investment, efficient supply chains, responsible supply chains and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Implementation Framework Backup Maintenance Developing Alternate Sites Ppt PowerPoint Presentation Model Images PDF
Presenting this set of slides with name cyber security implementation framework backup maintenance developing alternate sites ppt powerpoint presentation model images pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
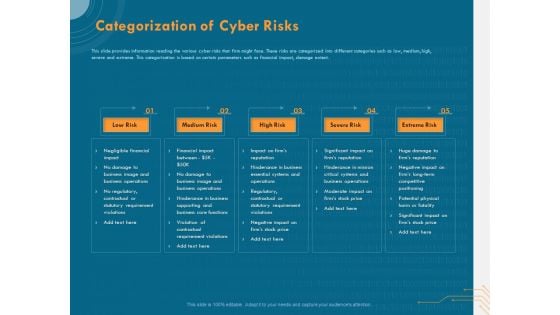
Cyber Security Implementation Framework Categorization Of Cyber Risks Ppt PowerPoint Presentation Portfolio Sample PDF
Presenting this set of slides with name cyber security implementation framework categorization of cyber risks ppt powerpoint presentation portfolio sample pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Cybersecurity Risk Management Worksheet Ppt Ideas Format PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity risk management worksheet ppt ideas format pdf. The topics discussed in these slides are risk priority, identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Implementation Framework Dashboard Incident Tracking Ppt Styles Topics PDF
Presenting this set of slides with name cyber security implementation framework dashboard incident tracking ppt styles topics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































