Safety Plan

E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF
This slide shows potential threats along with prevention for online business websites that could damage the business and also lose trust of online customers. the certain threats includes direct site attacks, password assault, social engineering and malwares. Showcasing this set of slides titled E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF. The topics addressed in these templates are Business Security Risks, Threat Type, Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Audit Demanded, Enable Collaboration, Industrialize Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
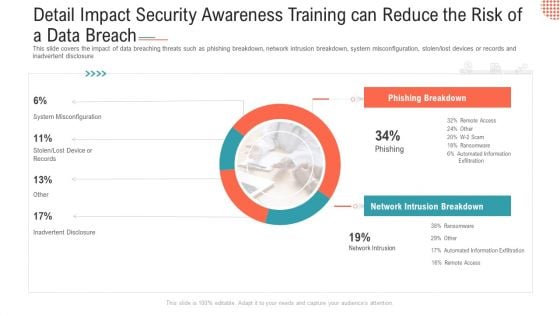
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Explore a selection of the finest CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
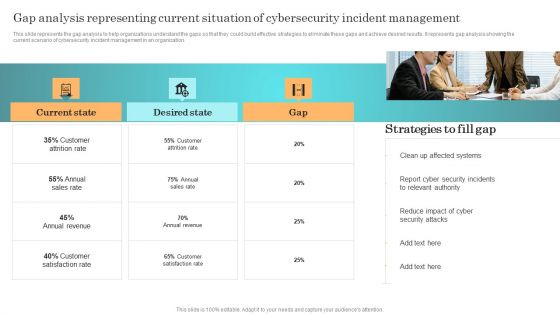
Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
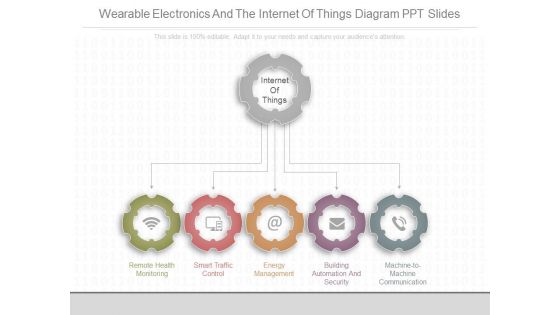
Wearable Electronics And The Internet Of Things Diagram Ppt Slides
This is a wearable electronics and the internet of things diagram ppt slides. This is a five stage process. The stages in this process are remote health monitoring, smart traffic control, energy management, building automation and security, machine to machine communication, internet of things.
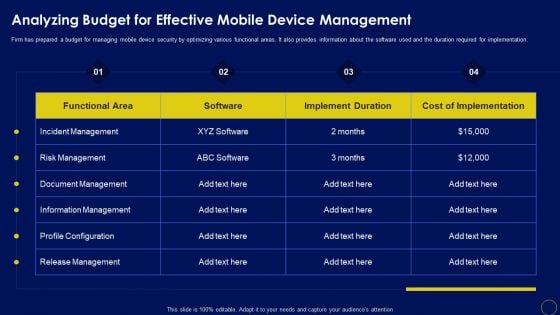
Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Explore a selection of the finest Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Cyber Exploitation IT Interview Schedule For New Professionals Icons PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking. Deliver and pitch your topic in the best possible manner with this cyber exploitation it interview schedule for new professionals icons pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Data Audit Report With Description Ppt PowerPoint Presentation Inspiration Example PDF
Showcasing this set of slides titled security data audit report with description ppt powerpoint presentation inspiration example pdf. The topics addressed in these templates are attribute, description, audit status, comments, data backup, data and application management, data disaster recovery system integration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Web Tools To Prevent Cyber Security Attack Ppt Summary Graphic Tips PDF
This slide defines the web tools to prevent from cyber attacks. It includes information related to different softwares, features and description. Showcasing this set of slides titled Web Tools To Prevent Cyber Security Attack Ppt Summary Graphic Tips PDF. The topics addressed in these templates are Software Tools, Solarwinds Identity Monitor, Free Tool. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
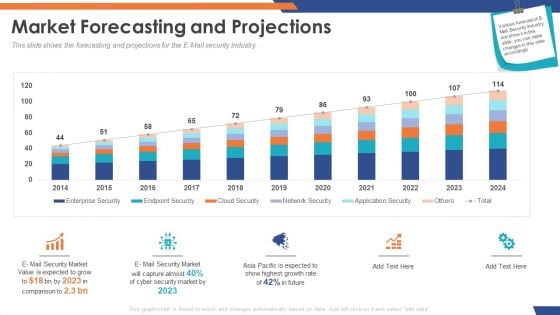
Email Security Market Research Report Market Forecasting And Projections Infographics PDF
Presenting this set of slides with name email security market research report market forecasting and projections infographics pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
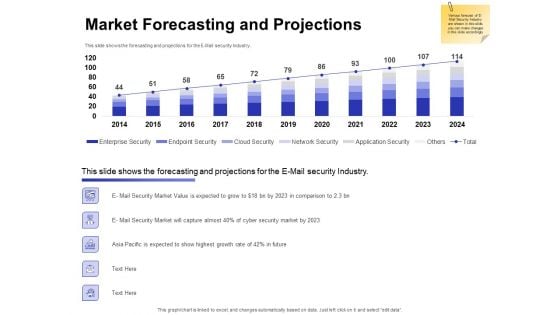
Global Cloud Based Email Security Market Market Forecasting And Projections Professional PDF
Presenting this set of slides with name global cloud based email security market market forecasting and projections professional pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Stages Circular Process Business Cyber Security Ppt PowerPoint Presentation Icon Tips
Presenting this set of slides with name five stages circular process business cyber security ppt powerpoint presentation icon tips. This is a five stage process. The stages in this process are technology, strategy, steps approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Ppt Pictures File Formats PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness ppt pictures file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technologies, financial control procedures, operating system maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Image Of Internet Security Virus PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Present our Arrows PowerPoint Templates because You can Bind your ideas with our PowerPoint Templates and Slides. They will add great value to the worth of your package. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Use our Finance PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Use our Success PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level.Use these PowerPoint slides for presentations relating to Internet Virus, technology, arrows, signs, finance, success. The prominent colors used in the PowerPoint template are Yellow, Black, White. Professionals tell us our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. You can be sure our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 will make you look like a winner. PowerPoint presentation experts tell us our arrows PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Our Image Of Internet Security Virus PowerPoint Templates Ppt Backgrounds For Slides 0113 are like angels. They take extraordinary care of your thoughts.
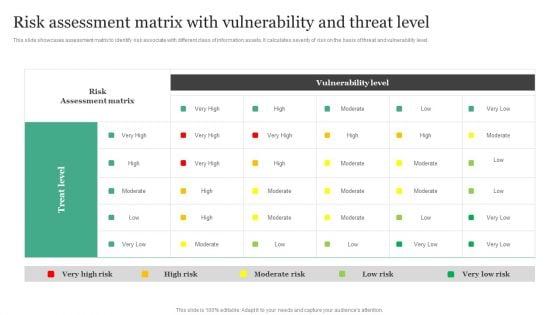
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF
This slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level.Boost your pitch with our creative Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
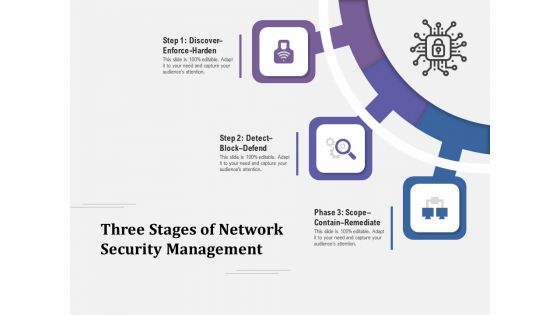
Three Stages Of Network Security Management Ppt PowerPoint Presentation Layouts Influencers PDF
Presenting three stages of network security management ppt powerpoint presentation layouts influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Three Phases Of Network Security Issues Ppt PowerPoint Presentation Icon Portrait PDF
Presenting three phases of network security issues ppt powerpoint presentation icon portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda Of Risk Management For Organization Essential Assets Elements PDF
This is a agenda of risk management for organization essential assets elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital assets, people, financial assets, physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
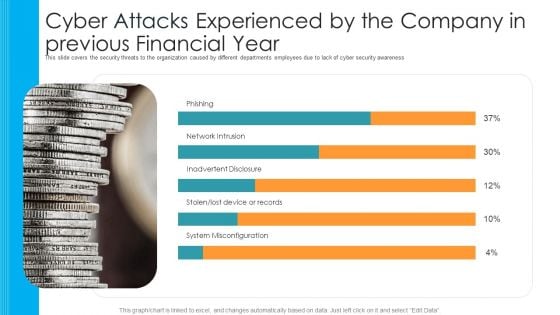
Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
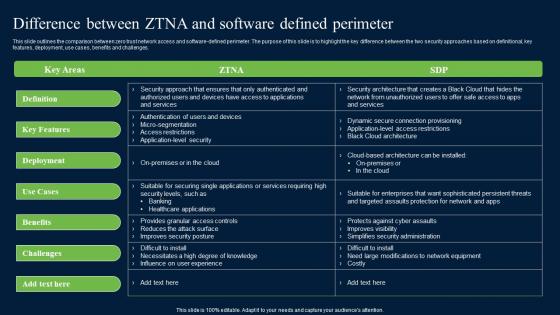
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
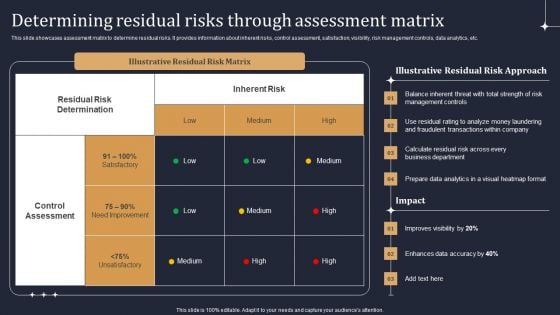
KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Company Inward Marketing Strategy Key Barriers Statistics Icons PDF
This slide covers top challenges of inbound marketing strategy that reduces its effectiveness. It includes generation of traffic, proving ROI for marketing activities, securing budget, technology update, website management, hiring talent and training team.Pitch your topic with ease and precision using this Company Inward Marketing Strategy Key Barriers Statistics Icons PDF. This layout presents information on Difficult To Search, Insufficient Traffic, Setting Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
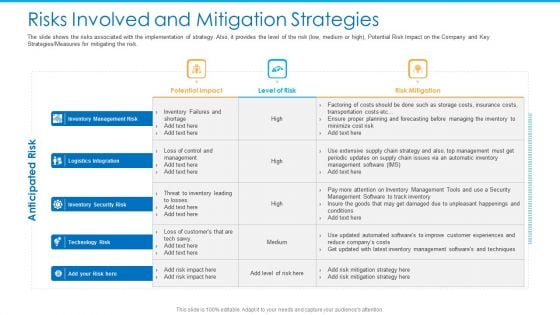
Risks Involved And Mitigation Strategies Infographics PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies or Measures for mitigating the risk.Deliver an awe inspiring pitch with this creative risks involved and mitigation strategies infographics pdf bundle. Topics like inventory management risk, logistics integration, inventory security risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risks Involved And Mitigation Strategies Demonstration PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk.Deliver an awe-inspiring pitch with this creative risks involved and mitigation strategies demonstration pdf. bundle. Topics like inventory management risk, logistics integration, inventory security risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risks Involved And Mitigation Strategies Designs PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, and Key Strategies Measures for effectively mitigating the risk.Deliver and pitch your topic in the best possible manner with this risks involved and mitigation strategies designs pdf. Use them to share invaluable insights on warehousing and logistics risks, online security and privacy risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risks Involved And Mitigation Strategies Background PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, and Key Strategies Measures for effectively mitigating the risk.Deliver and pitch your topic in the best possible manner with this risks involved and mitigation strategies background pdf. Use them to share invaluable insights on warehousing and logistics risks, online security and privacy risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
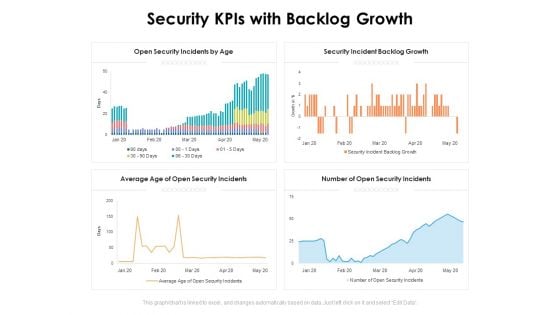
Security Kpis With Backlog Growth Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name security kpis with backlog growth ppt powerpoint presentation inspiration ideas pdf. The topics discussed in these slides are open security incidents by age, security incident backlog growth, number of open security incidents, average age of open security incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
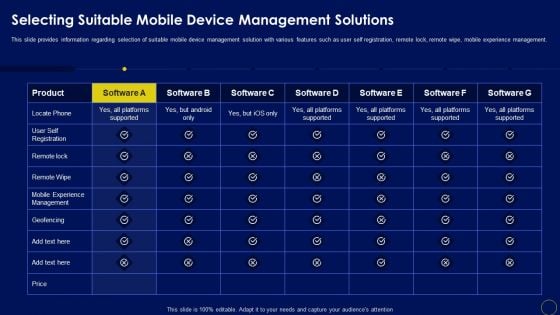
Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Find highly impressive Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
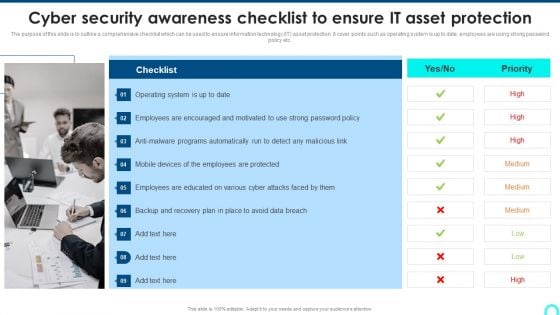
Cyber Security Awareness Checklist To Ensure IT Asset Protection Microsoft PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password.This is a Cyber Security Awareness Checklist To Ensure IT Asset Protection Microsoft PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees Encouraged, Programs Automatically, Employees Protected. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
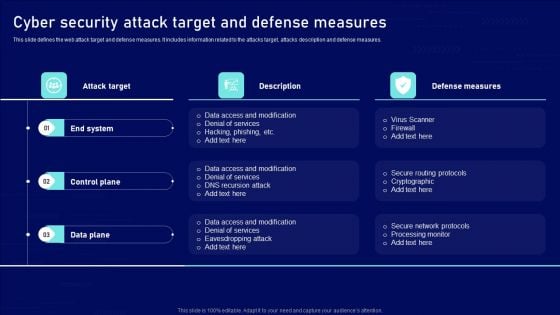
Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
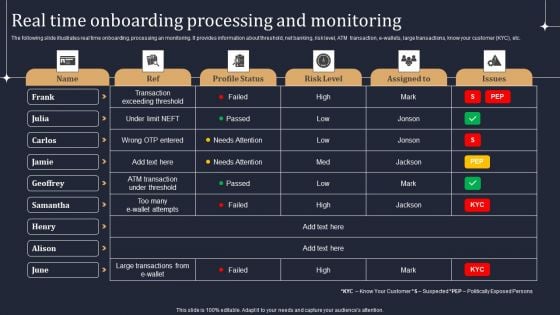
KYC Transaction Monitoring System Business Security Real Time Onboarding Processing And Monitoring Demonstration PDF
The following slide illustrates real time onboarding, processing an monitoring. It provides information about threshold, net banking, risk level, ATM transaction, e-wallets, large transactions, know your customer KYC, etc. Slidegeeks has constructed KYC Transaction Monitoring System Business Security Real Time Onboarding Processing And Monitoring Demonstration PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
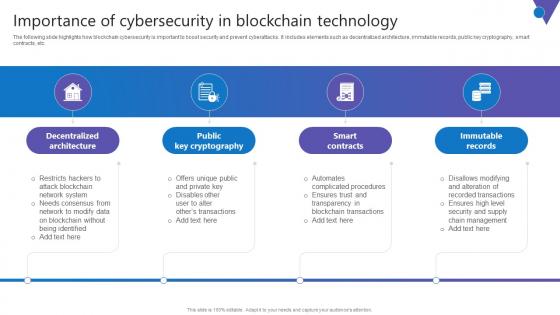
Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Find highly impressive Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
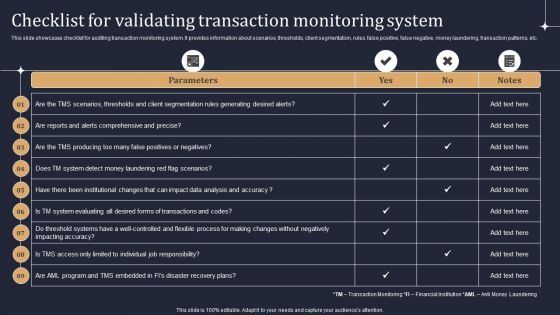
KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF
This slide showcases checklist for auditing transaction monitoring system. It provides information about scenarios, thresholds, client segmentation, rules, false positive, false negative, money laundering, transaction patterns, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
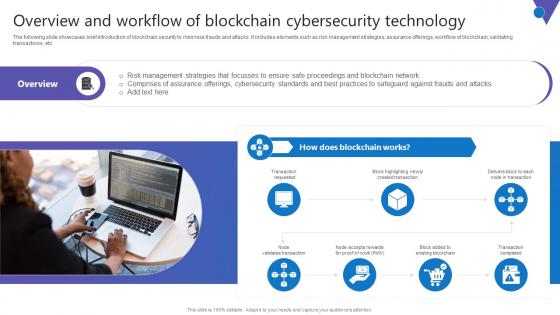
Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Explore a selection of the finest Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc.

Detailed Requirements Collection Chart Of IT Companies Ppt Summary Show PDF
This slide shows information technology IT company requirements collection form. It provides information such as application usage, networking issues, operating system, capabilities, features, etc. Presenting Detailed Requirements Collection Chart Of IT Companies Ppt Summary Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Each Problem, Problem Security, Market. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Devops Data Use Case Configuration Management Data Record Cases Of Devops IT Elements PDF
This template covers DevOps configuration management including customer requirements, and appropriate solutions. This is a devops data use case configuration management data record cases of devops it elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, system, security, strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
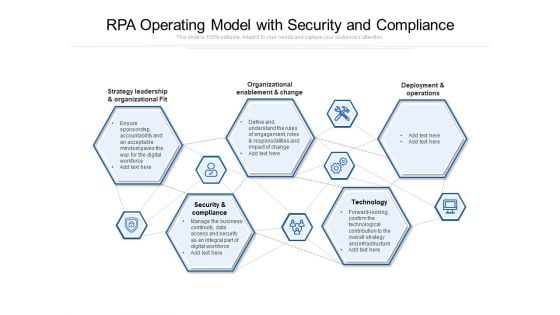
RPA Operating Model With Security And Compliance Ppt PowerPoint Presentation Model Styles PDF
Presenting rpa operating model with security and compliance ppt powerpoint presentation model styles pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including strategy leadership and organizational fit, organizational enablement and change, deployment and operations, security and compliance, technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Environments Best Suited For Efficient And Secure Supply Chains Topics PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe-inspiring pitch with this creative environments best suited for efficient and secure supply chains topics pdf bundle. Topics like factor, efficient supply chains, responsible supply chains can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
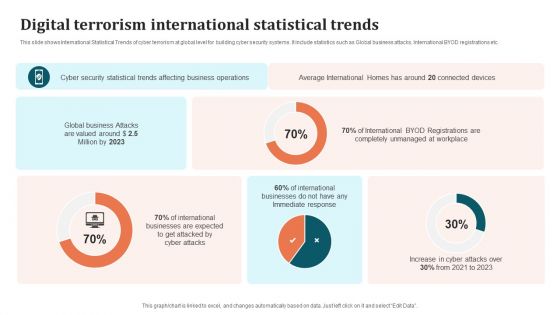
Digital Terrorism International Statistical Trends Brochure PDF
This slide shows International Statistical Trends of cyber terrorism at global level for building cyber security systems. It include statistics such as Global business attacks, International BYOD registrations etc. Showcasing this set of slides titled Digital Terrorism International Statistical Trends Brochure PDF. The topics addressed in these templates are International Businesses, Cyber Security Statistical Trends, Business Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mobile Device Management Determining Roles And Responsibilities For Risk Handling Microsoft PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Mobile Device Management Determining Roles And Responsibilities For Risk Handling Microsoft PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
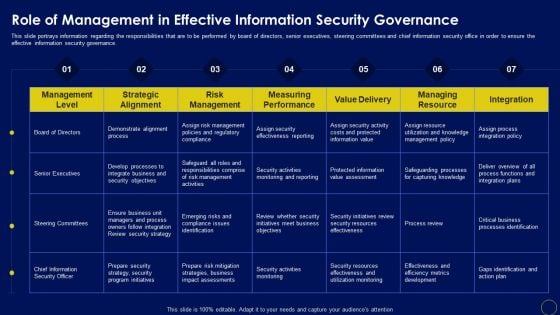
Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Government Strategies To Tackle Identity Fraud Background PDF
This slide showcases approaches followed by government to prevent fraud. This template focuses on following techniques to keep personal information safe and secure. It includes information related to reliable identity checks, early detection of fraud, etc. Persuade your audience using this Government Strategies To Tackle Identity Fraud Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Reliable Identity Checks, Early Detection Identity Fraud, Fast Assistance Victims Identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
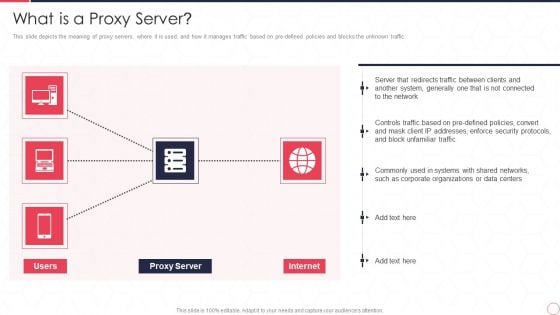
Reverse Proxy Server IT What Is A Proxy Server Ppt Infographics Infographics PDF
This slide depicts the meaning of proxy servers, where it is used, and how it manages traffic based on pre-defined policies and blocks the unknown traffic. This is a reverse proxy server it what is a proxy server ppt infographics infographics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, unfamiliar traffic, enforce security protocols, controls traffic based. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
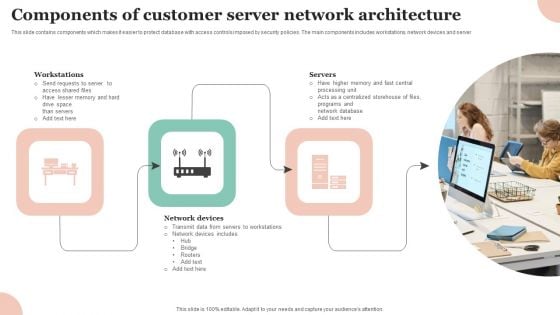
Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
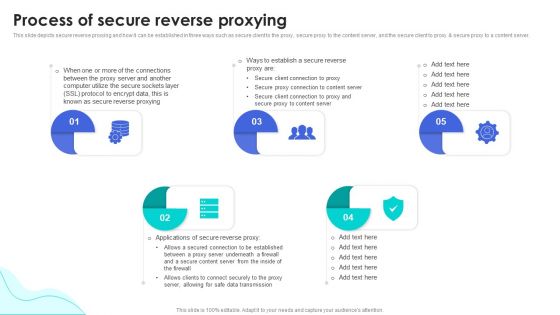
Reverse Proxy Web Server Process Of Secure Reverse Proxying Ppt Gallery Themes PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Make sure to capture your audiences attention in your business displays with our gratis customizable Reverse Proxy Web Server Process Of Secure Reverse Proxying Ppt Gallery Themes PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Strategies For Developers To Maximize Software Testing Organizational Efficiency Template PDF
This slide shows various strategies which can help software developers to enhance testing efficiency. These strategies are tool analysis, training and security.Presenting Strategies For Developers To Maximize Software Testing Organizational Efficiency Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Communication Platforms Umber Communication, Incorporate Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Integration Of Paas Whats Included In A Platform As A Service Paas Icons PDF
This slide describes the working of the platform as a service framework and it includes components such as users, applications, software, operating system, integrated development environment, network access, database, data security, data backup, application hosting, and hardware.. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of Paas Whats Included In A Platform As A Service Paas Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Complete Beginners Guide Two Factor Authentication For Improved Security Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Complete Beginners Guide Two Factor Authentication For Improved Security Fin SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Complete Beginners Guide Two Factor Authentication For Improved Security Fin SS V today and make your presentation stand out from the rest This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
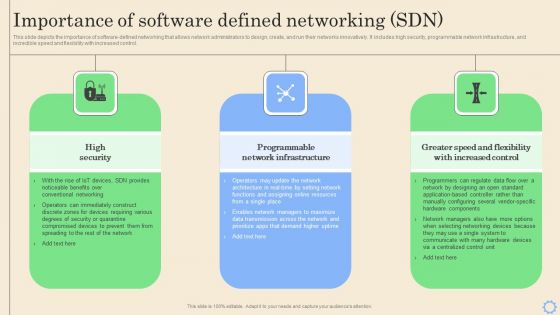
Software Defined Networking Development Strategies Importance Of Software Defined Networking SDN Brochure PDF
This slide depicts the importance of software-defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. This Software Defined Networking Development Strategies Importance Of Software Defined Networking SDN Brochure PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Software Defined Networking Development Strategies Importance Of Software Defined Networking SDN Brochure PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
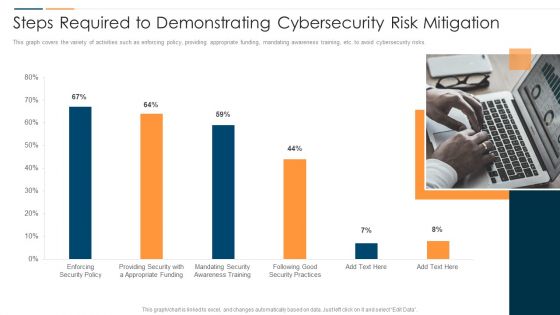
Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Devops Configuration Management IT Determine Additional Roles Pivotal For Successful Devops Contd Topics PDF
This slide provides information regarding the additional roles considered as pivotal for successful DevOps in terms of software tester developer, security engineer and experience assurance professional. This is a devops configuration management it determine additional roles pivotal for successful devops contd topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like software tester, security engineer, experience assurance professional. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
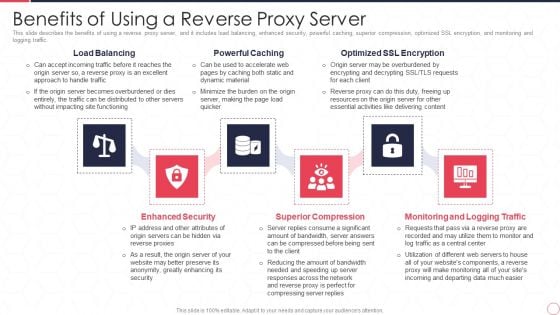
Reverse Proxy Server IT Benefits Of Using A Reverse Proxy Server Ppt Model Designs PDF
This slide describes the benefits of using a reverse proxy server, and it includes load balancing, enhanced security, powerful caching, superior compression, optimized SSL encryption, and monitoring and logging traffic. This is a reverse proxy server it benefits of using a reverse proxy server ppt model designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like load balancing, powerful caching, optimized ssl encryption, enhanced security, superior compression, monitoring and logging traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
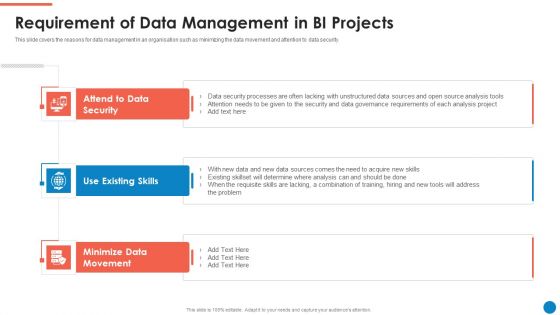
Data And Analytics Playbook Requirement Of Data Management In BI Projects Introduction PDF
This slide covers the reasons for data management in an organisation such as minimizing the data movement and attention to data security. This is a Data And Analytics Playbook Requirement Of Data Management In BI Projects Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Attend To Data Security, Use Existing Skills, Minimize Data Movement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
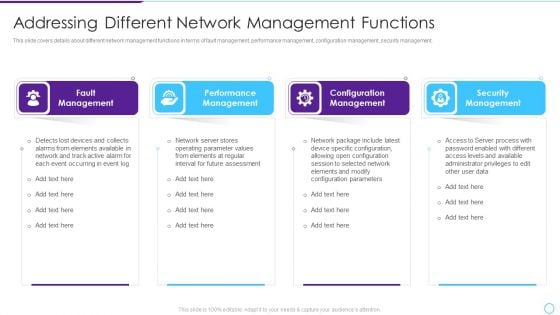
Intelligent Infrastructure Addressing Different Network Management Functions Background PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. Presenting Intelligent Infrastructure Addressing Different Network Management Functions Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Fault Management, Performance Management, Configuration Management, Security Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. Presenting Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Tracking Products, Securing Operations, Managing Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Venture Digitial Transformation Enterprise Technical Challenges Ppt PowerPoint Presentation File Slide PDF
This slide covers technical challenges such as environmental, compatibility, skills shortage and security in enterprise while making IT OT convergence. Presenting Smart Venture Digitial Transformation Enterprise Technical Challenges Ppt PowerPoint Presentation File Slide PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Environmental, Compatibility, Skills Shortage, Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































