Safety Plan

Damage Security Insurance Proposal Cover Letter For Liability Insurance Proposal Ppt Slides Graphic Tips PDF
Presenting damage security insurance proposal cover letter for liability insurance proposal ppt slides graphic tips pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cover letter. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Project Context For Liability Insurance Proposal Ppt File Examples PDF
This is a damage security insurance proposal project context for liability insurance proposal ppt file examples pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like liability, human resource, insurance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
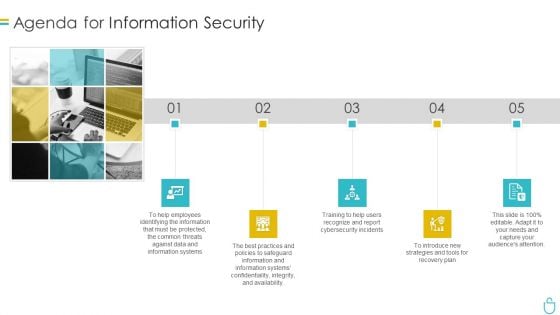
Agenda For Information Security Ppt Professional Good PDF
This is a agenda for information security ppt professional good pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, systems, data, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
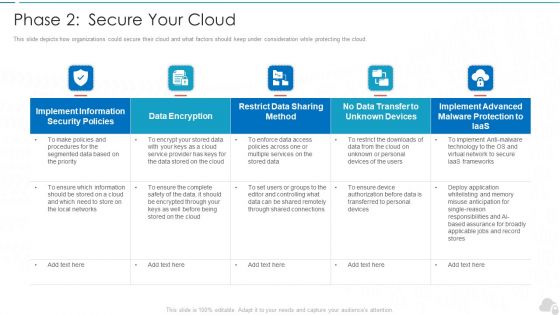
Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Employee Benefits Concept Social Security Ppt PowerPoint Presentation Outline Show
Presenting this set of slides with name employee benefits concept social security ppt powerpoint presentation outline show. The topics discussed in these slides are business, planning, strategy, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.
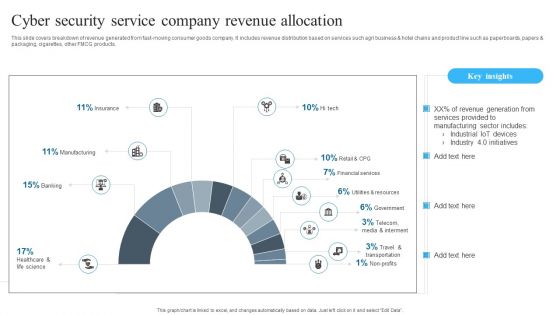
Cyber Security Service Company Revenue Allocation Background PDF
Showcasing this set of slides titled Cyber Security Service Company Revenue Allocation Background PDF. The topics addressed in these templates are Cyber Security, Service Company, Revenue Allocation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Software Testing Methodologies To Improve Data Security Graphics PDF
This slides signifies the application testing practises to increase data security. It covers information about steps like build secure environment, create team, simulate end user, adopt shifting left testing methodology and focus on regression testing. Presenting Software Testing Methodologies To Improve Data Security Graphics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Build Secure Testing Environment, Simulate End User Environment, Focus Regression Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
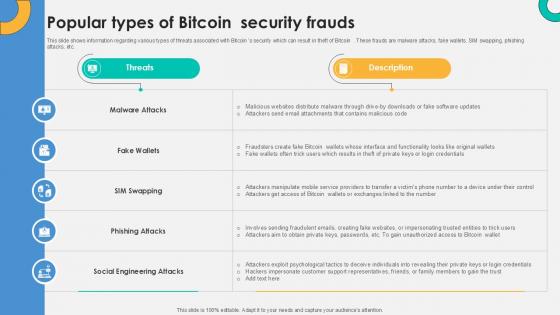
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.
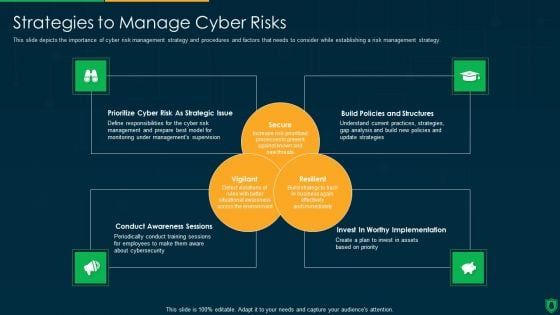
Info Security Strategies To Manage Cyber Risks Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a info security strategies to manage cyber risks ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like prioritize cyber risk as strategic issue, build policies and structures, conduct awareness sessions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
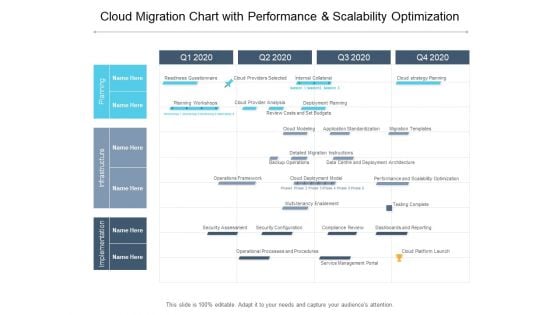
Cloud Migration Chart With Performance And Scalability Optimization Ppt PowerPoint Presentation Layouts Templates
Presenting this set of slides with name cloud migration chart with performance and scalability optimization ppt powerpoint presentation layouts templates. The topics discussed in these slides are cloud strategy planning, deployment planning, security configuration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. If you are looking for a format to display your unique thoughts, then the professionally designed IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
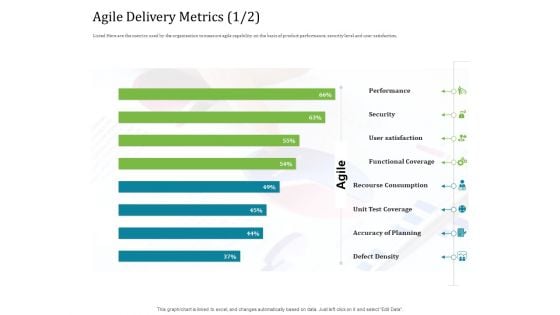
Agile Service Delivery Model Agile Delivery Metrics Security Professional PDF
Deliver an awe inspiring pitch with this creative agile service delivery model agile delivery metrics security professional pdf bundle. Topics like performance, security, user satisfaction, functional coverage, recourse consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
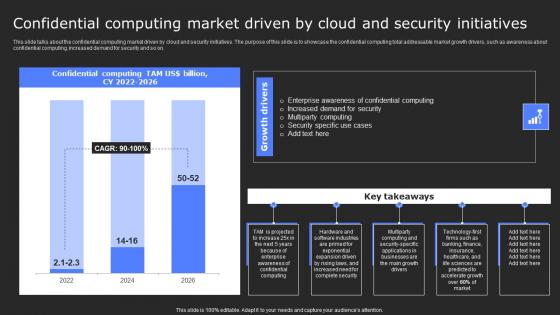
Secure Computing Framework Confidential Computing Market Driven By Mockup Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Find a pre-designed and impeccable Secure Computing Framework Confidential Computing Market Driven By Mockup Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
Document Verification Vector Icon Ppt PowerPoint Presentation Infographic Template Design Ideas
Presenting this set of slides with name document verification vector icon ppt powerpoint presentation infographic template design ideas. This is a one stage process. The stages in this process are check mark, business, planning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
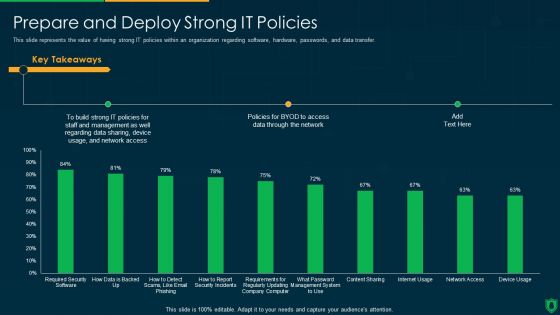
Info Security Prepare And Deploy Strong IT Policies Ppt PowerPoint Presentation File Model PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative info security prepare and deploy strong it policies ppt powerpoint presentation file model pdf bundle. Topics like build strong, it policies, data sharing, access data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
PowerPoint Slide Designs Download Swot Analysis Ppt Design
PowerPoint Slide Designs Download SWOT Analysis PPT Design.pptx-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Get classy with our PowerPoint Slide Designs Download Swot Analysis Ppt Design. They ensure A-list clients.

Strategies To Mitigate Cyber Security Risks Cyber Security Governance Ppt Styles Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cyber security governance ppt styles model pdf. This is a one stage process. The stages in this process are senior management, steering committee and executive management, ciso steering committee, business strategy, risk management, information, security strategy, security action plan, policies, standards organisation, objectives security requirements, security programs, implementation, security objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
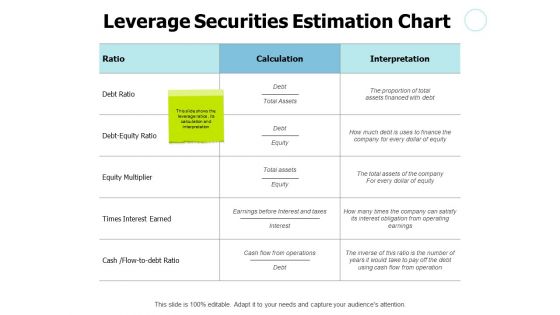
Leverage Securities Estimation Chart Ppt PowerPoint Presentation File Format
Presenting this set of slides with name leverage securities estimation chart ppt powerpoint presentation file format. The topics discussed in these slides are marketing, process, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
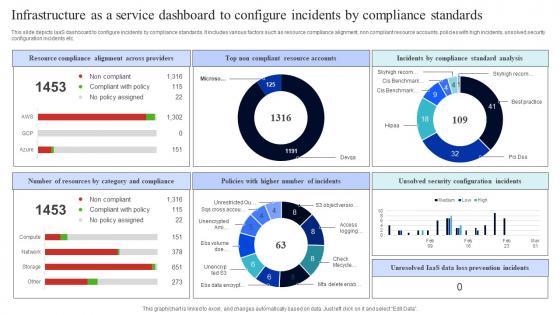
Infrastructure As A Service Dashboard To Configure Incidents By Compliance Standards Rules Pdf
This slide depicts IaaS dashboard to configure incidents by compliance standards. It includes various factors such as resource compliance alignment, non compliant resource accounts, policies with high incidents, unsolved security configuration incidents etc. Pitch your topic with ease and precision using this Infrastructure As A Service Dashboard To Configure Incidents By Compliance Standards Rules Pdf. This layout presents information on Resource Compliance Alignment, Across Providers, Top Non Compliant, Resource Accounts. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts IaaS dashboard to configure incidents by compliance standards. It includes various factors such as resource compliance alignment, non compliant resource accounts, policies with high incidents, unsolved security configuration incidents etc.

Security And Human Resource Services Business Profile Employee And Staff Welfare Inspiration PDF
This slide highlights the staff and employee welfare services which includes social security, insurance, medical, accommodation, pick and drop services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Security And Human Resource Services Business Profile Employee And Staff Welfare Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
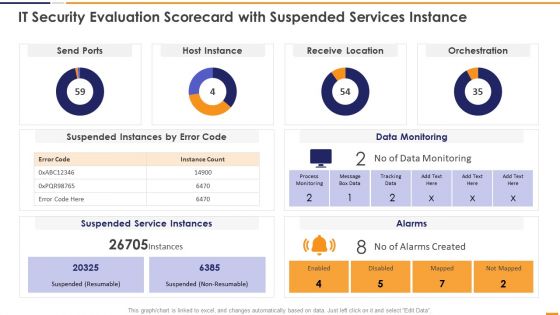
IT Security Evaluation Scorecard With Suspended Services Instance Graphics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Suspended Services Instance Graphics PDF. Use them to share invaluable insights on Send Ports Alarms, Host Instance Orchestration, Receive Location Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Employee Benefits Concept Social Security Ppt PowerPoint Presentation Icon Backgrounds
Presenting this set of slides with name employee benefits concept social security ppt powerpoint presentation icon backgrounds. This is a six stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Employee Benefits Template Social Security Ppt PowerPoint Presentation Layouts Guide
Presenting this set of slides with name employee benefits template social security ppt powerpoint presentation layouts guide. This is a eight stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Debentures Security Conversion Ppt PowerPoint Presentation Show Aids
Presenting this set of slides with name debentures security conversion ppt powerpoint presentation show aids. This is a four stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
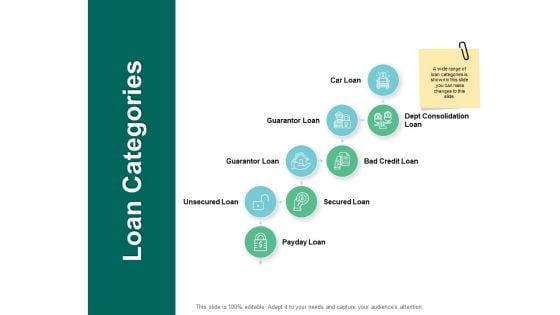
Loan Categories Security Checklist Ppt PowerPoint Presentation Portfolio Examples
Presenting this set of slides with name loan categories security checklist ppt powerpoint presentation portfolio examples. This is a eight stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Fixed Income Securities Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name fixed income securities ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Content Fixed Income Securities Categorization Ppt PowerPoint Presentation Inspiration Graphics
Presenting this set of slides with name content fixed income securities categorization ppt powerpoint presentation inspiration graphics. The topics discussed in these slides are marketing, process, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
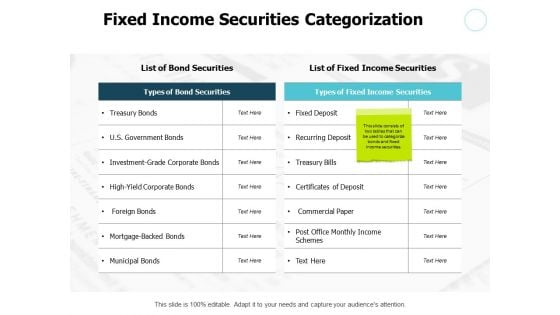
Fixed Income Securities Categorization Table Ppt PowerPoint Presentation Professional Outfit
Presenting this set of slides with name fixed income securities categorization table ppt powerpoint presentation professional outfit. The topics discussed in these slides are marketing, process, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
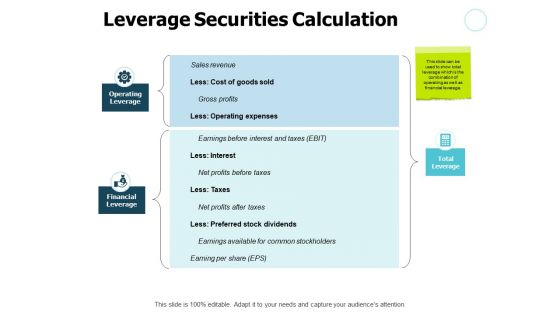
Leverage Securities Calculation Gears Ppt PowerPoint Presentation Slides Topics
Presenting this set of slides with name leverage securities calculation gears ppt powerpoint presentation slides topics. The topics discussed in these slides are marketing, process, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Internet Security Management In Powerpoint And Google Slides Cpb
Introducing our well designed Internet Security Management In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Internet Security Management. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Internet Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
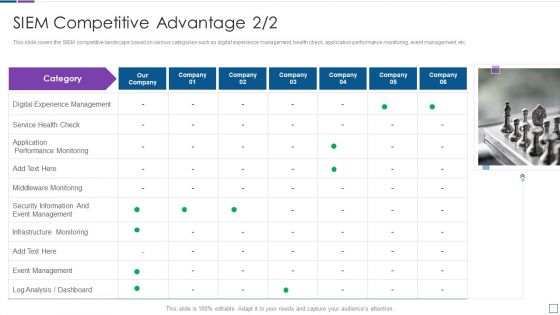
Real Time Assessment Of Security Threats SIEM Competitive Advantage Service Structure PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Presenting real time assessment of security threats siem competitive advantage service structure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like digital experience management, service health check, application performance monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
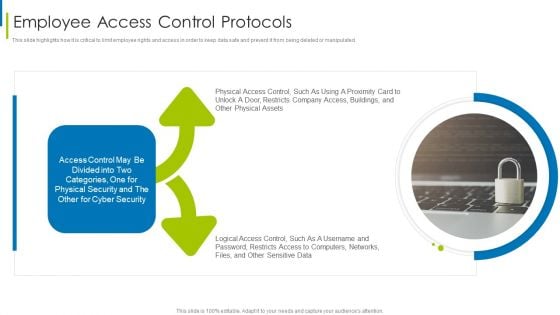
Cyber Terrorism Assault Employee Access Control Protocols Diagrams PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated.This is a cyber terrorism assault employee access control protocols diagrams pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Distributed Denial Of Service DDOS As Cyber Terrorism Tool You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
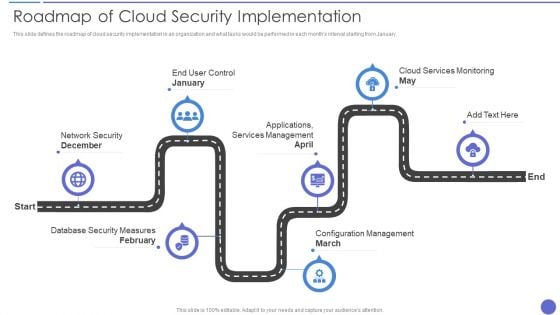
Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
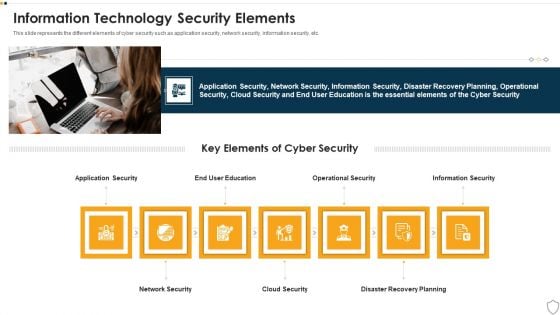
IT Security Information Technology Security Elements Ppt Images PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a it security information technology security elements ppt images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, disaster recovery planning, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Mitigate Cyber Security Risks Recovery Task List Maintenance Ppt Infographics Designs Download PDF
Presenting this set of slides with name strategies to mitigate cyber security risks recovery task list maintenance ppt infographics designs download pdf. This is a one stage process. The stages in this process are estimated time, actual time, assigned, comments, retrieve business continuity plans. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Products And Services Business Communication Improvement Platform Investor Template Pdf
This slide showcases the product and services of Aircall. It includes productsandservices such as phone system features, collaboration, call center features, productivity, analytics and admin security. Make sure to capture your audiences attention in your business displays with our gratis customizable Problems Statement Business Communication Improvement Platform Investor Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide showcases the product and services of Aircall. It includes productsandservices such as phone system features, collaboration, call center features, productivity, analytics and admin security.
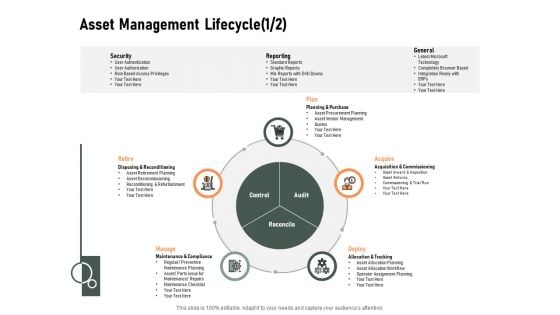
Construction Production Facilities Asset Management Lifecycle Security Designs PDF
Presenting this set of slides with name construction production facilities asset management lifecycle security designs pdf. This is a five stage process. The stages in this process are plan, acquire, deploy, retire, manage. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
PowerPoint Slides Executive Growth Social Media Icons Ppt Templates
PowerPoint Slides Executive Growth Social Media Icons PPT Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Command teams with our PowerPoint Slides Executive Growth Social Media Icons Ppt Templates. Download without worries with our money back guaranteee.
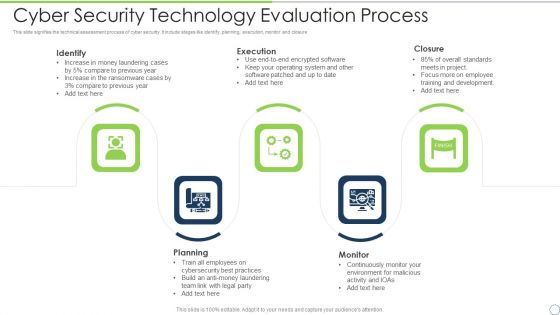
Cyber Security Technology Evaluation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Persuade your audience using this cyber security technology evaluation process ppt powerpoint presentation file visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, execution, closure, monitor, planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
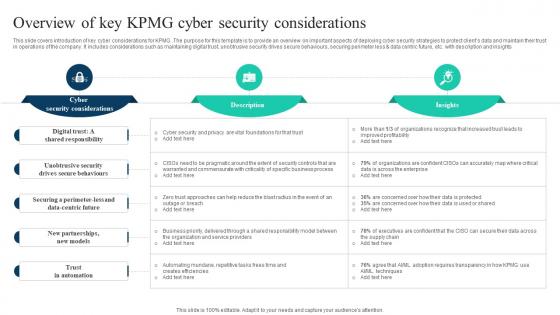
The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Find a pre-designed and impeccable The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights

Main Data Security Tokenization Techniques Securing Your Data Ppt Sample
This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. The Main Data Security Tokenization Techniques Securing Your Data Ppt Sample is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc.
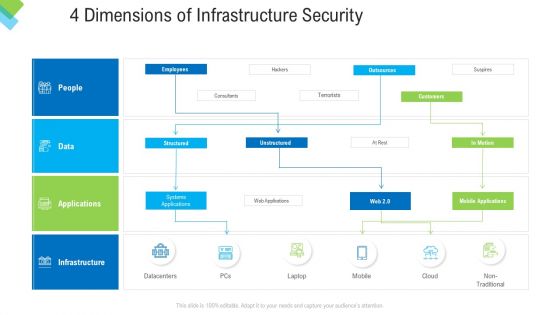
Construction Management Services 4 Dimensions Of Infrastructure Security Summary PDF
This is a construction management services 4 dimensions of infrastructure security summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
PowerPoint Design Executive Competition Targets Venn Pie Chart Diagram Ppt Theme
PowerPoint Design Executive Competition Targets Venn Pie Chart Diagram PPT Theme-These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Document growth with our PowerPoint Design Executive Competition Targets Venn Pie Chart Diagram Ppt Theme. Download without worries with our money back guaranteee.
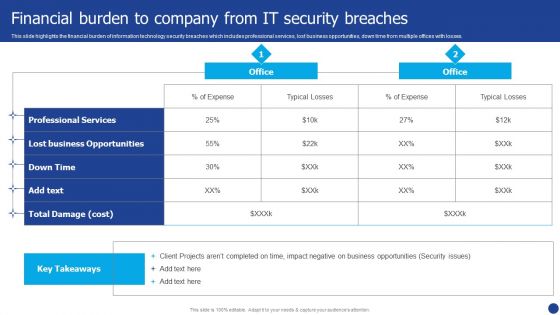
Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF. Use them to share invaluable insights on Professional Services, Lost Business Opportunities, Expense and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
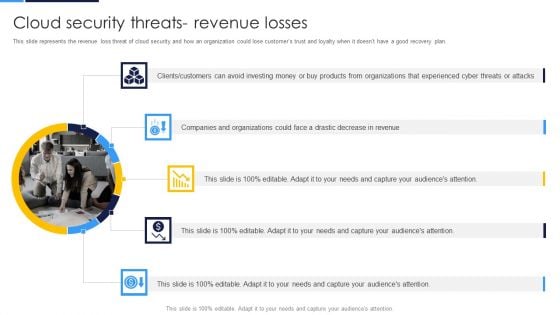
Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
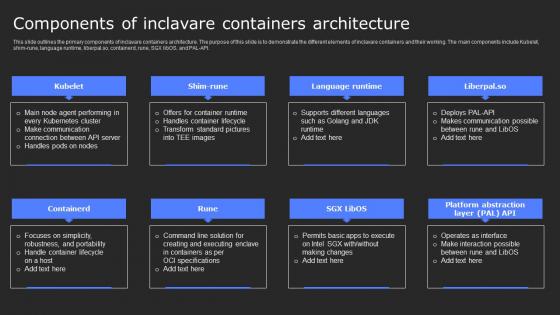
Components Of Inclavare Containers Secure Computing Framework Professional Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Secure Computing Framework Professional Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
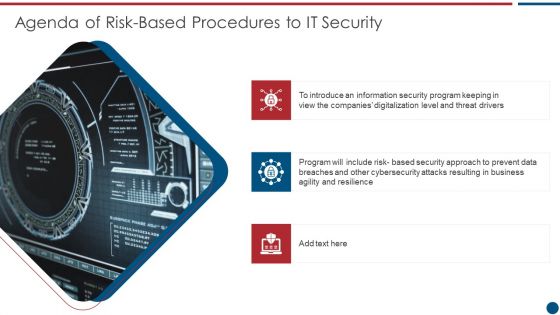
Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF
This is a Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Program Keeping, Threat Drivers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Elements Of Computer Security Operational Security Themes PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a desktop security management elements of computer security operational security themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, resources, require, security, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
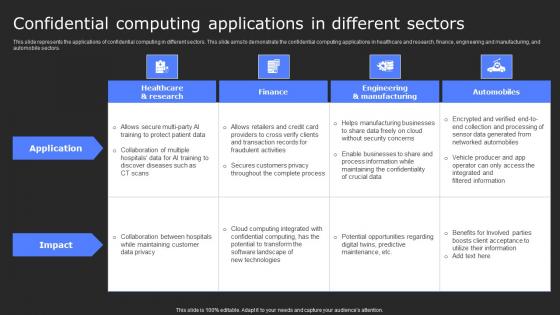
Confidential Computing Applications In Secure Computing Framework Demonstration Pdf
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Find highly impressive Confidential Computing Applications In Secure Computing Framework Demonstration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Confidential Computing Applications In Secure Computing Framework Demonstration Pdffor your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors.
Cyber Security Implementation Framework Recovery Task List Maintenance Ppt PowerPoint Presentation Icon Format Ideas PDF
Presenting this set of slides with name cyber security implementation framework recovery task list maintenance ppt powerpoint presentation icon format ideas pdf. The topics discussed in these slides are retrieve business continuity plans, retrieval department vital records, identify recovery site, actual time, estimated time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Secure Delivery Service Corporate Insurance Coverage Advertising Strategies Ppt PowerPoint Presentation Ideas Inspiration
This is a secure delivery service corporate insurance coverage advertising strategies ppt powerpoint presentation ideas inspiration. This is a three stage process. The stages in this process are secure delivery service, corporate insurance coverage, advertising strategies.

Main Data Security Tokenization Techniques PPT Powerpoint
This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. Boost your pitch with our creative Main Data Security Tokenization Techniques PPT Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc.

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc.
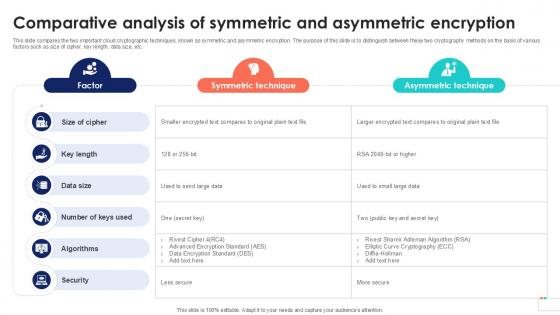
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
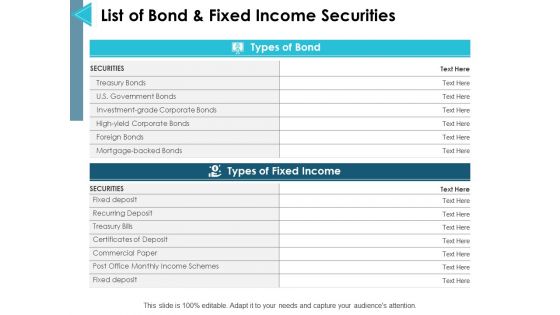
List Of Bond And Fixed Income Securities Ppt PowerPoint Presentation Layouts Graphics Design
This is a list of bond and fixed income securities ppt powerpoint presentation layouts graphics design. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.
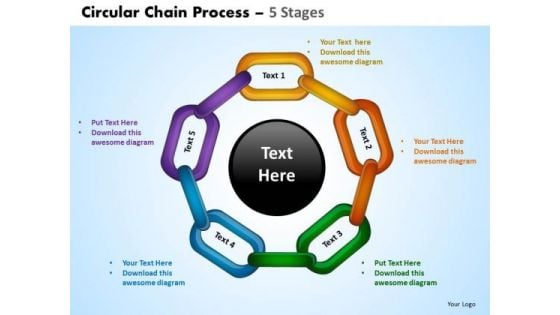
PowerPoint Process Chart Circular Chain Ppt Template
PowerPoint Process Chart Circular Chain PPT Template--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Embrace changes with our PowerPoint Process Chart Circular Chain Ppt Template. Develop the correct attitude for it.
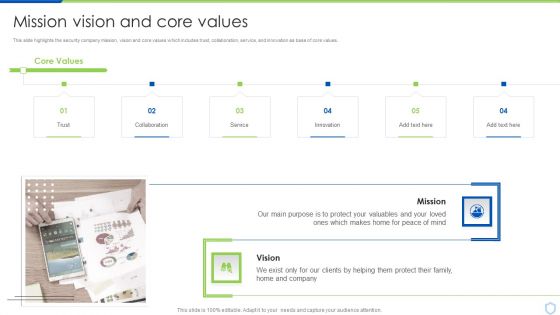
Security And Surveillance Company Profile Mission Vision And Core Values Clipart PDF
This slide highlights the security company mission, vision and core values which includes trust, collaboration, service, and innovation as base of core values.This is a Security And Surveillance Company Profile Mission Vision And Core Values Clipart PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Collaboration, Innovation, Protect Your Valuables . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
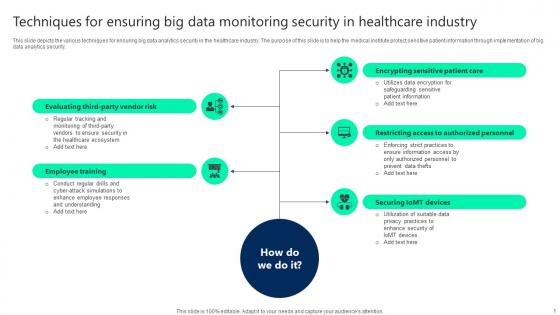
Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf
This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Pitch your topic with ease and precision using this Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf. This layout presents information on Employee Training, Securing Iomt Devices, Restricting Access. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security.


 Continue with Email
Continue with Email

 Home
Home


































