Safety Plan
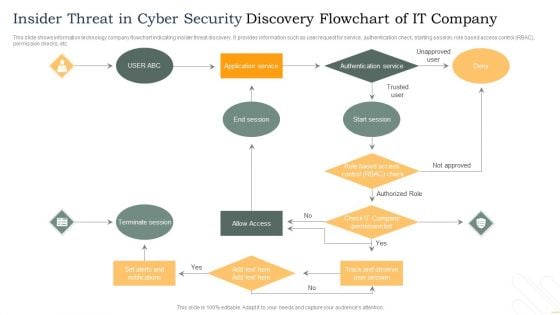
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
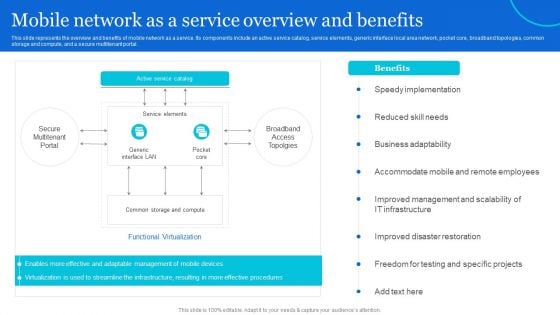
Naas Architectural Framework Mobile Network As A Service Overview And Benefits Demonstration PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Naas Architectural Framework Mobile Network As A Service Overview And Benefits Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Naas Architectural Framework Mobile Network As A Service Overview And Benefits Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
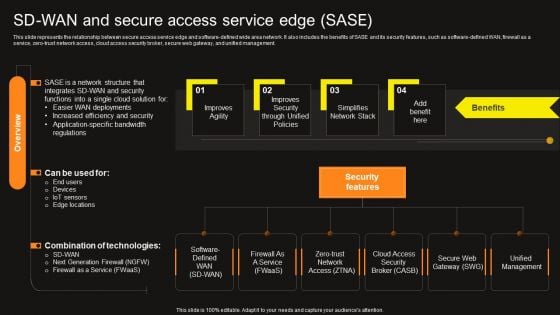
Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF today and make your presentation stand out from the rest.
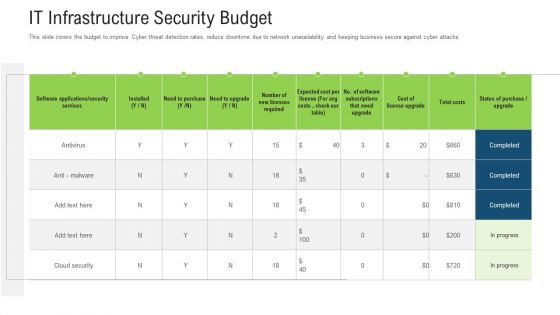
It Infrastructure Security Budget Ppt Outline Mockup PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this it infrastructure security budget ppt outline mockup pdf. Use them to share invaluable insights on services, software, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
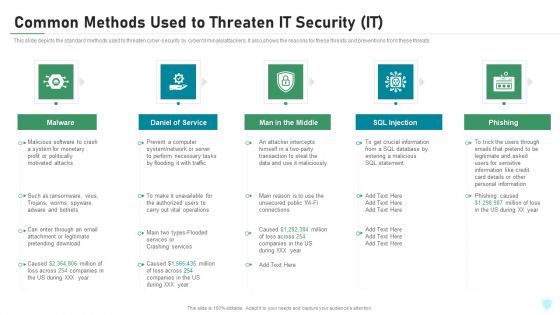
Common Methods Used To Threaten IT Security IT Ppt Inspiration Rules PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten it security it ppt inspiration rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Common Methods Used To Threaten Electronic Information Security Ppt Infographics Inspiration PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a cybersecurity common methods used to threaten electronic information security ppt infographics inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
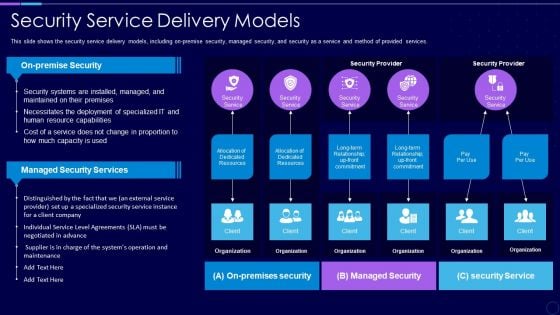
Everything As A Service Xaas For Cloud Computing IT Security Service Delivery Models Diagrams PDF
This slide shows the security service delivery models, including on-premise security, managed security, and security as a service and method of provided services. This is a everything as a service xaas for cloud computing it security service delivery models diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deployment, resource capabilities, security systems, security service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
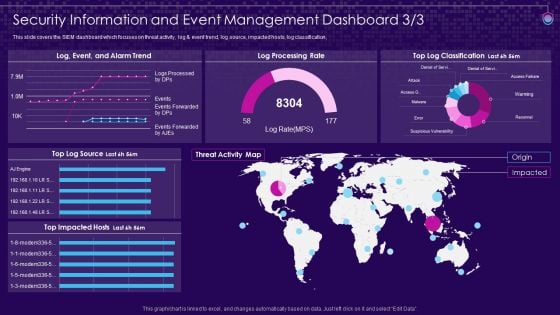
SIEM Services Security Information And Event Management Dashboard Source Ppt Outline Design Inspiration PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative siem services security information and event management dashboard source ppt outline design inspiration pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Strategy Cloud Security Architect Skills Scope Background PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative information technology strategy cloud security architect skills scope background pdf bundle. Topics like architecture and strategy, technical, leadership, operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
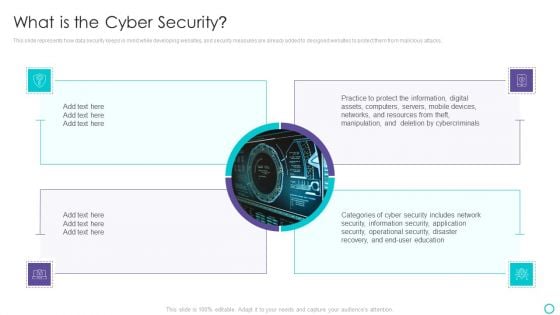
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Guidelines IT Information Security Policy For Employees Introduction PDF
This slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cybersecurity Guidelines IT Information Security Policy For Employees Introduction PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
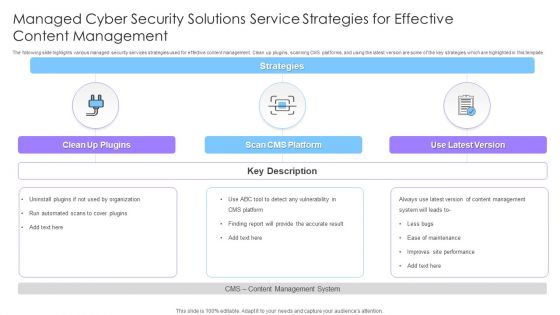
Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF
The following slide highlights various managed security services strategies used for effective content management. Clean up plugins, scanning CMS platforms, and using the latest version are some of the key strategies which are highlighted in this template. Persuade your audience using this Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Managed Cyber Security, Solutions Service Strategies, Effective Content Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
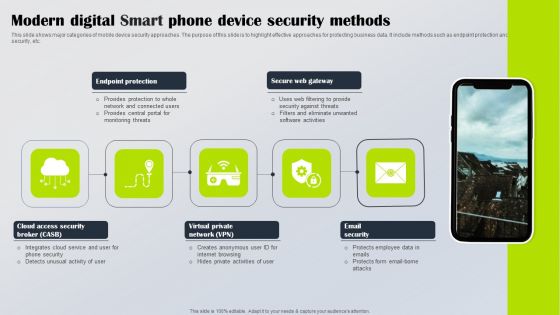
Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
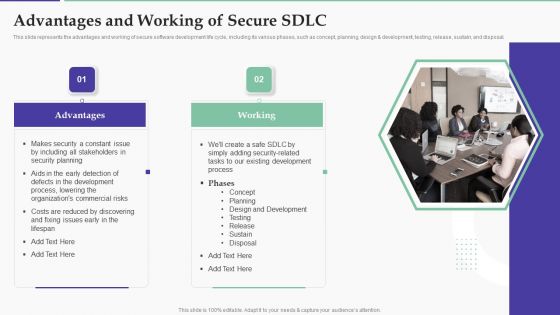
Solution Development Process Advantages And Working Of Secure SDLC Structure PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design development, testing, release, sustain, and disposal.Presenting Solution Development Process Advantages And Working Of Secure SDLC Structure PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Including Stakeholders, Security Planning, Process, Lowering Commercial. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Human Resource Services Business Profile Case Study Summary PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Create an editable Security And Human Resource Services Business Profile Case Study Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Security And Human Resource Services Business Profile Case Study Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
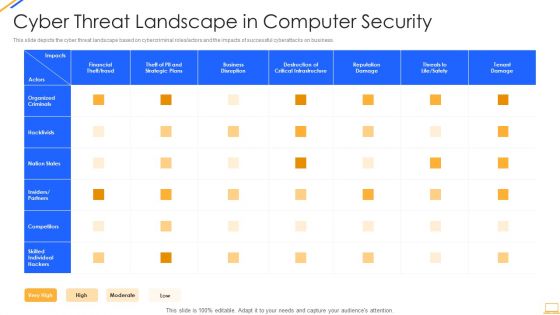
Desktop Security Management Cyber Threat Landscape In Computer Security Ideas PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this desktop security management cyber threat landscape in computer security ideas pdf. Use them to share invaluable insights on business disruption, strategic plans, financial, reputation damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
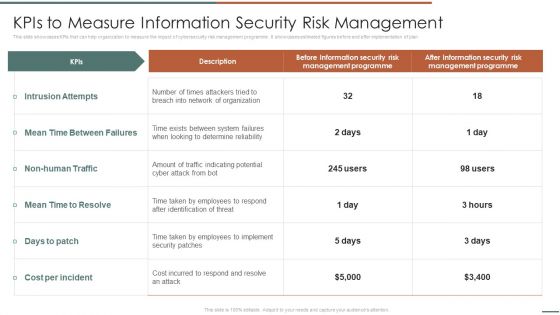
Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF bundle. Topics like Between Failures, Times Attackers, Management Programme can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Guidelines For Business Data Security Vector Icon Ppt PowerPoint Presentation Gallery Layout Ideas PDF
Persuade your audience using this guidelines for business data security vector icon ppt powerpoint presentation gallery layout ideas pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including guidelines for business data security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
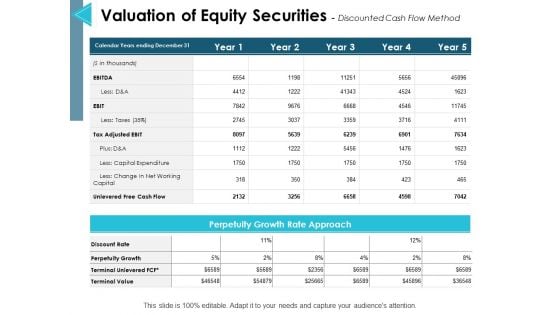
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Infographic Template Introduction
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation infographic template introduction. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.
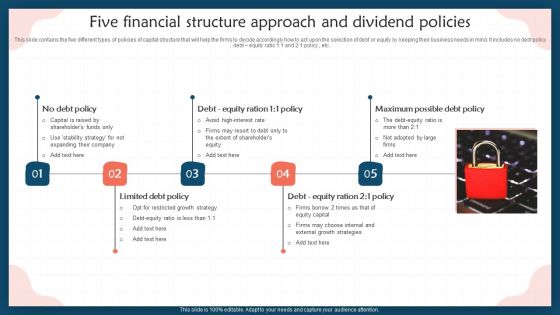
Five Financial Structure Approach And Dividend Policies Professional PDF
This slide contains the five different types of policies of capital structure that will help the firms to decide accordingly how to act upon the selection of debt or equity by keeping their business needs in mind. It includes no debt policy , debt equity ratio 1 1 and 2 1 policy , etc. Presenting Five Financial Structure Approach And Dividend Policies Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Capital, Stability Strategy, High Interest Rate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Emergency Strategy Process Flow For Natural Disaster And Security Threat Ppt PowerPoint Presentation Ideas Files PDF
Showcasing this set of slides titled emergency strategy process flow for natural disaster and security threat ppt powerpoint presentation ideas files pdf. The topics addressed in these templates are Business Contingency Plan, Natural Disasters, Earthquake. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
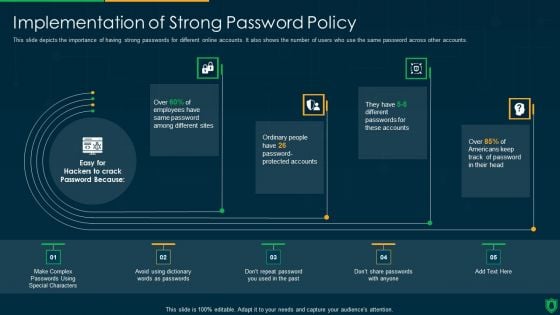
Info Security Implementation Of Strong Password Policy Ppt PowerPoint Presentation File Slide Download PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Deliver an awe inspiring pitch with this creative info security implementation of strong password policy ppt powerpoint presentation file slide download pdf bundle. Topics like implementation strong, password policy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
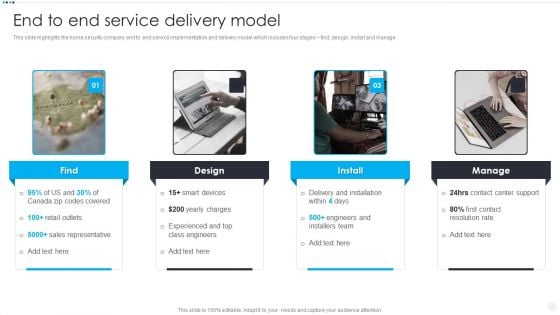
Smart Home Security Solutions Company Profile End To End Service Delivery Model Slides PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage. Presenting Smart Home Security Solutions Company Profile End To End Service Delivery Model Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Delivery And Installation, Contact Center Support, Contact Resolution Rate, Engineers And Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
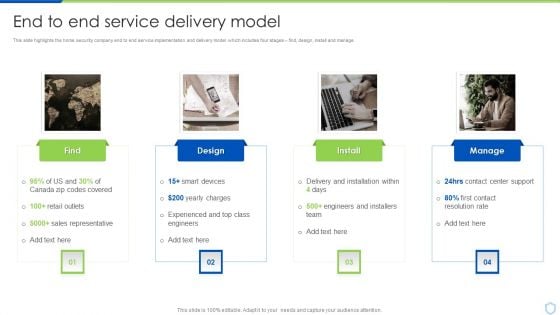
Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage.Presenting Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Sales Representative, Experienced Engineers, Engineers Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
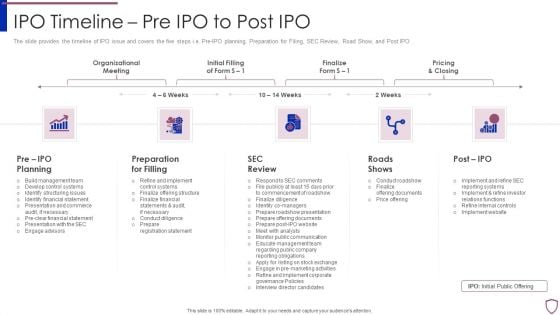
Financing Catalogue For Security Underwriting Agreement IPO Timeline Pre IPO To Post IPO Microsoft PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPO. Presenting financing catalogue for security underwriting agreement ipo timeline pre ipo to post ipo microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like pre ipo planning, preparation for filling, sec review, roads shows, post ipo. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

RPA Security Framework In Powerpoint And Google Slides Cpb
Introducing our well designed RPA Security Framework In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like RPA Security Framework. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our RPA Security Framework In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
PowerPoint Design Slides Chart Circular Puzzle Ppt Slides
PowerPoint Design Slides Chart Circular Puzzle PPT Slides--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Display your aptitude with our PowerPoint Design Slides Chart Circular Puzzle Ppt Slides. Ideas will flow effortlessly.

Information Security Frameworks List Ppt PowerPoint Presentation Visual Aids Outline Cpb
Presenting this set of slides with name information security frameworks list ppt powerpoint presentation visual aids outline cpb. This is an editable Powerpoint seven stages graphic that deals with topics like information security frameworks list to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
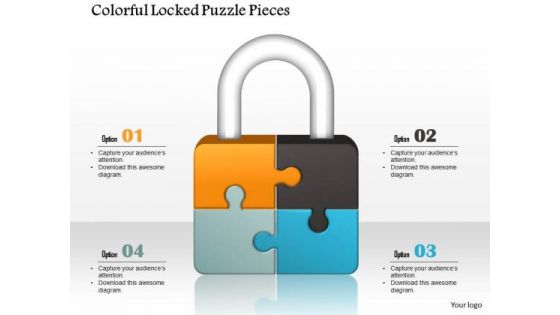
Consulting Slides Colorful Locked Puzzle Pieces Business Presentation
This interconnected puzzle pieces lock diagram make your audience understands essential elements of your overall strategy and also shows an organized view of business services and processes.
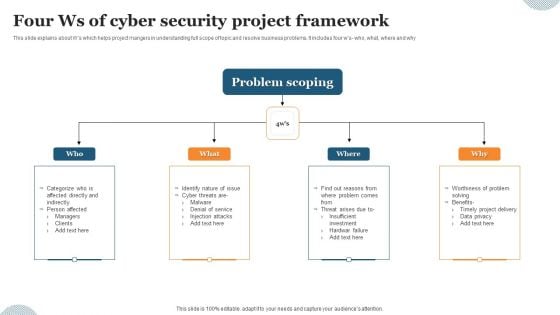
Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF
This slide explains about Ws which helps project mangers in understanding full scope of topic and resolve business problems. It includes four ws- who, what, where and why. Presenting Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Problem Scoping, Denial Service, Injection Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Online Payment Service Payment Security And Fraud Management Solutions End Structure PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. This is a online payment service payment security and fraud management solutions end structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like market basket analysis, optimization, geolocation analysis, customer velocity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
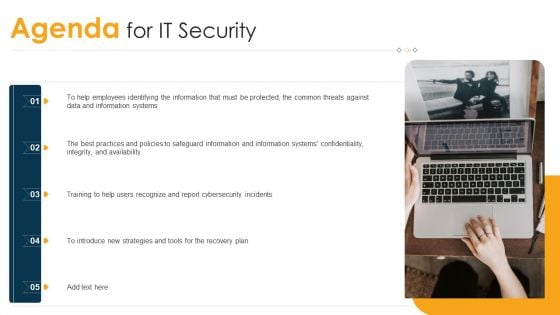
Agenda For IT Security Ppt Example File PDF
This is a agenda for it security ppt example file pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategies, cybersecurity, plan, safeguard, policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
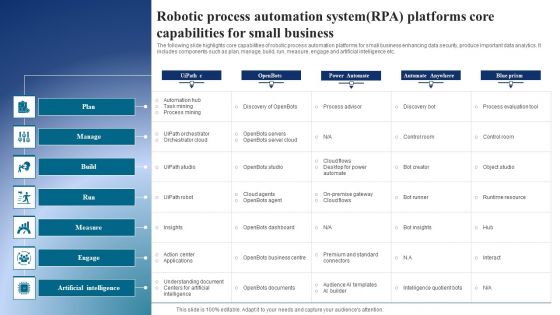
Robotic Process Automation Systemrpa Platforms Core Capabilities For Small Business Structure PDF
The following slide highlights core capabilities of robotic process automation platforms for small business enhancing data security, produce important data analytics. It includes components such as plan, manage, build, run, measure, engage and artificial intelligence etc. Showcasing this set of slides titled Robotic Process Automation Systemrpa Platforms Core Capabilities For Small Business Structure PDF. The topics addressed in these templates are Plan, Manage, Build . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
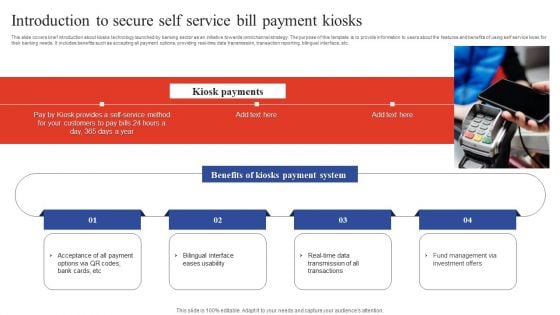
Deployment Of Omnichannel Banking Solutions Introduction To Secure Self Service Bill Payment Kiosks Portrait PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. Slidegeeks has constructed Deployment Of Omnichannel Banking Solutions Introduction To Secure Self Service Bill Payment Kiosks Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
Firewall For Security Brick Wall Vector Icon Ppt PowerPoint Presentation Infographics Files PDF
Presenting this set of slides with name firewall for security brick wall vector icon ppt powerpoint presentation infographics files pdf. The topics discussed in these slide is firewall for security brick wall vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Web Access Control Solution Different Types Of Secure Web Gateway Deployment
This slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Make sure to capture your audiences attention in your business displays with our gratis customizable Web Access Control Solution Different Types Of Secure Web Gateway Deployment. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment.
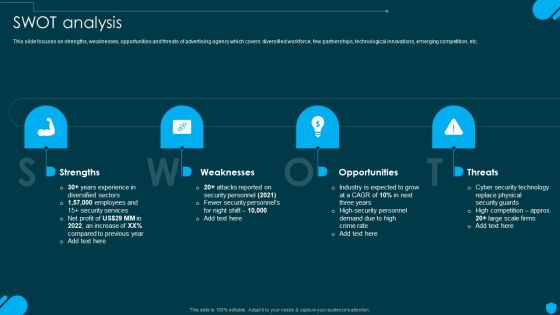
Security And Human Resource Services Business Profile SWOT Analysis Formats PDF
Retrieve professionally designed Security And Human Resource Services Business Profile SWOT Analysis Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
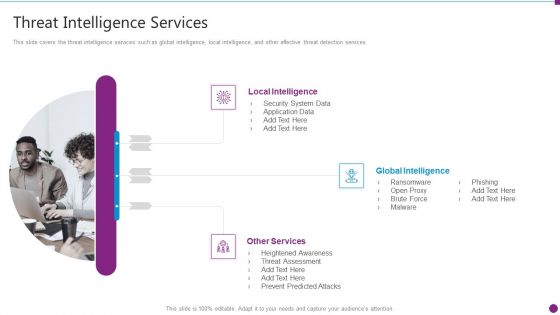
Security Information And Event Management Strategies For Financial Audit And Compliance Threat Intelligence Services Graphics PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Presenting security information and event management strategies for financial audit and compliance threat intelligence services graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like local intelligence, global intelligence, other services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document brilliant piece now.

Table Of Contents Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Security Services Proposal One Pager Sample Example Document brilliant piece now.

Cyber Security Implementation Framework Analyzing IT Department On NIST Cybersecurity Framework Topics PDF
Presenting this set of slides with name cyber security implementation framework analyzing it department on nist cybersecurity framework topics pdf. This is a one stage process. The stages in this process are asset management, governance, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF
This slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Persuade your audience using this IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Attack Vector, Examples, Objective Problem Identifier. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
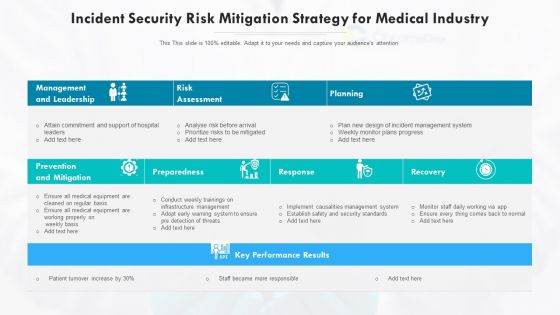
Incident Security Risk Mitigation Strategy For Medical Industry Ppt PowerPoint Presentation Gallery Diagrams PDF
Showcasing this set of slides titled incident security risk mitigation strategy for medical industry ppt powerpoint presentation gallery diagrams pdf. The topics addressed in these templates are preparedness, planning, prevention and mitigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
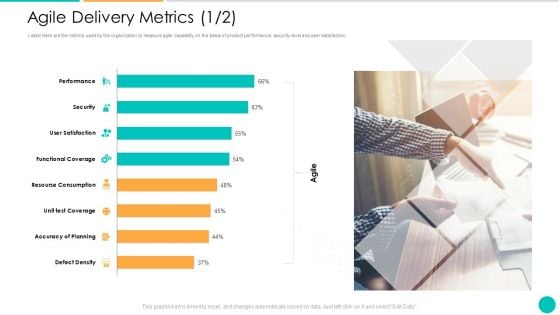
DAD Framework Agile Delivery Metrics Security Ppt Ideas Skills PDF
Listed Here are the metrics used by the organization to measure agile capability on the basis of product performance, security level and user satisfaction. Deliver and pitch your topic in the best possible manner with this DAD framework agile delivery metrics security ppt ideas skills pdf. Use them to share invaluable insights on security, accuracy of planning, functional coverage, performance, resourse consumption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Strategies To Mitigate Cyber Security Risks Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name strategies to mitigate cyber security risks ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are management, security breach, marketing, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
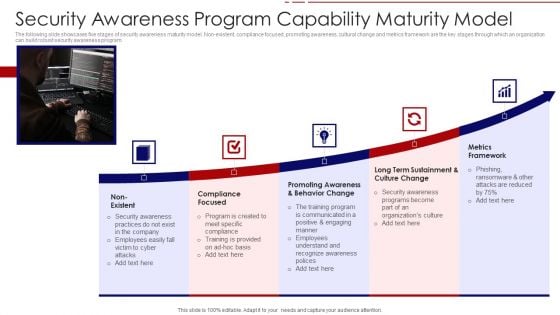
Security Awareness Program Capability Maturity Model Ppt PowerPoint Presentation File Portfolio PDF
The following slide showcases five stages of security awareness maturity model. Non-existent, compliance focused, promoting awareness, cultural change and metrics framework are the key stages through which an organization can build robust security awareness program. Persuade your audience using this security awareness program capability maturity model ppt powerpoint presentation file portfolio pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including non existent, compliance focused, promoting awareness and behavior change, long term sustainment and culture change, metrics framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
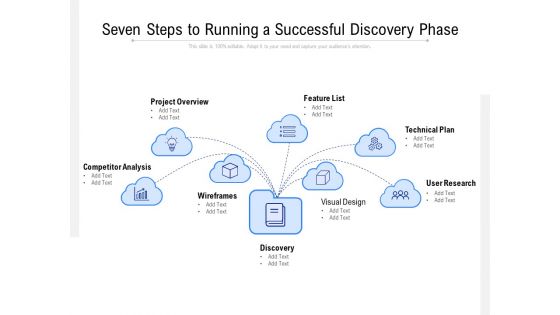
Seven Steps To Running A Successful Discovery Phase Ppt PowerPoint Presentation Professional Mockup PDF
Presenting this set of slides with name seven steps to running a successful discovery phase ppt powerpoint presentation professional mockup pdf. This is a seven stage process. The stages in this process are competitor analysis, wireframes, discovery, project overview, feature list, technical plan, user research, visual design. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF bundle. Topics like Operating Breakdown, Session Duration, Goal Completions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Agenda For IT Security IT Ppt Infographics Demonstration PDF
This is a agenda for it security it ppt infographics demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like training, cybersecurity, strategies, plan, integrity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
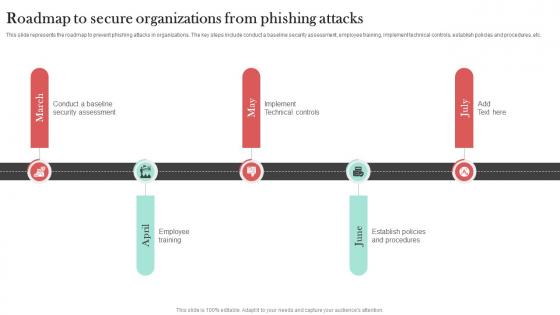
Roadmap To Secure Organizations Man In The Middle Phishing IT
This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roadmap To Secure Organizations Man In The Middle Phishing IT and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Table Of Contents For Working Space And FM Services Security Summary PDF
Find highly impressive Table Of Contents For Working Space And FM Services Security Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Working Space And FM Services Security Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
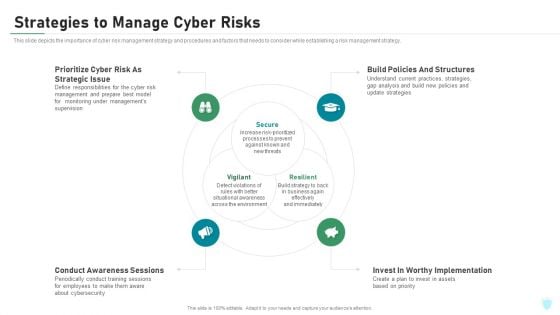
Strategies To Manage Cyber Risks IT Security IT Ppt Visual Aids Portfolio PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting strategies to manage cyber risks it security it ppt visual aids portfolio pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like prioritize cyber risk as strategic issue, conduct awareness sessions, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
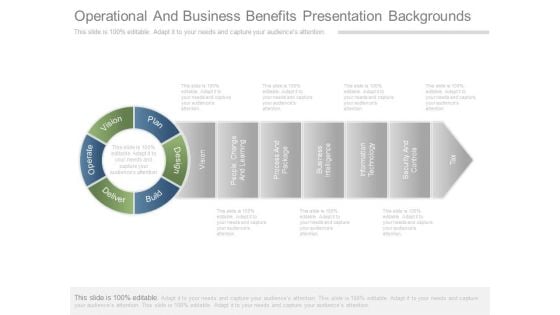
Operational And Business Benefits Presentation Backgrounds
This is a operational and business benefits presentation backgrounds. This is a seven stage process. The stages in this process are vision, plan, design, build, deliver, operate, people change and learning, process and package, business intelligence, information technology, security and controls, tax.

Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V
The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V from Slidegeeks and deliver a wonderful presentation. The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry.

Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc.

Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc. Find highly impressive Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc.

Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf today and make your presentation stand out from the rest This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
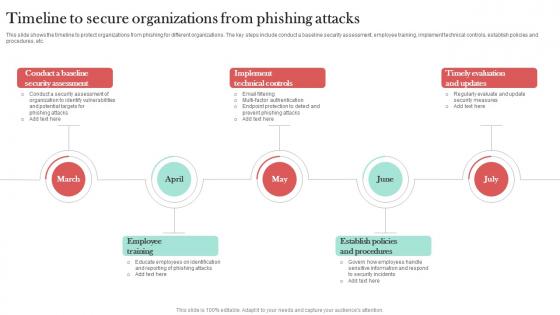
Timeline To Secure Organizations From Man In The Middle Phishing IT
This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. This Timeline To Secure Organizations From Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Timeline To Secure Organizations From Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Cyber Security Implementation Framework Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name cyber security implementation framework ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are business, management, marketing, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































