Safety Summary

Comparison Between ITIL V2 And ITIL V3 IT Service Management Framework Structure PDF
This slide represents the difference between ITIL v2 and ITIL v3, based on focus, approach, security management, number of processes, and functions.The Comparison Between ITIL V2 And ITIL V3 IT Service Management Framework Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF
The purpose of this slide is to showcase the dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Present like a pro with Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF
Slidegeeks is here to make your presentations a breeze with Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Agenda Development And Integration Of Cyber Security Incident Administration Information PDF
Slidegeeks is here to make your presentations a breeze with Agenda Development And Integration Of Cyber Security Incident Administration Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
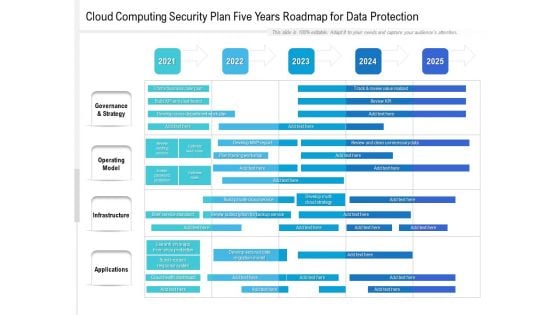
Cloud Computing Security Plan Five Years Roadmap For Data Protection Template
Introducing our cloud computing security plan five years roadmap for data protection template. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
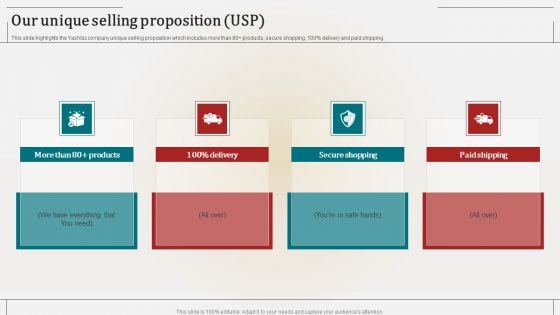
Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF
This slide highlights the Yashbiz company unique selling proposition which includes more than 80 products, secure shopping, 100 percent delivery and paid shipping. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
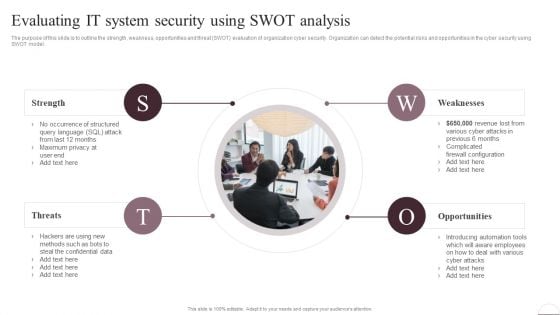
Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.

Computer Security Incident Handling Agenda For Cybersecurity Incident Management Template PDF
Presenting this set of slides with name computer security incident handling agenda for cybersecurity incident management template pdf. The topics discussed in these slides are department, priorities, maximum allowable downtime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Managing IT Operating System 4 Dimensions Of Infrastructure Security Template PDF
Presenting this set of slides with name managing it operating system 4 dimensions of infrastructure security template pdf. The topics discussed in these slides are infrastructure, applications, data, people. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Our Solution Email And Data Protection Platform Capital Funding Pitch Deck PPT Sample
This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA-compliant email encryption. Make sure to capture your audiences attention in your business displays with our gratis customizable Our Solution Email And Data Protection Platform Capital Funding Pitch Deck PPT Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA-compliant email encryption.
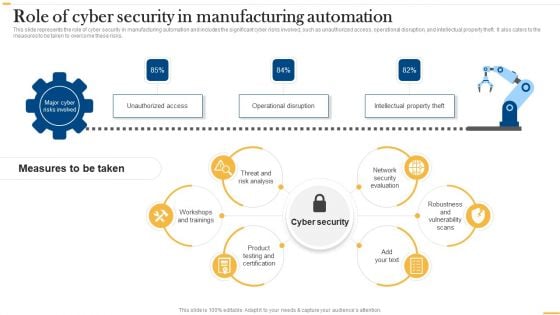
Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Are you searching for a Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF from Slidegeeks today.
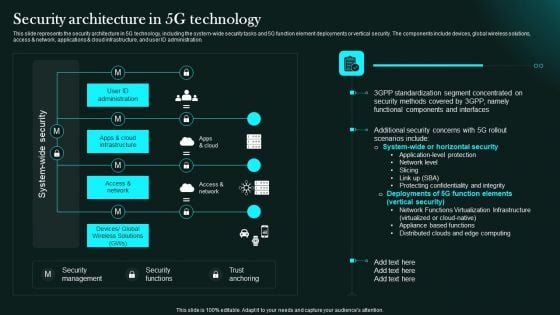
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
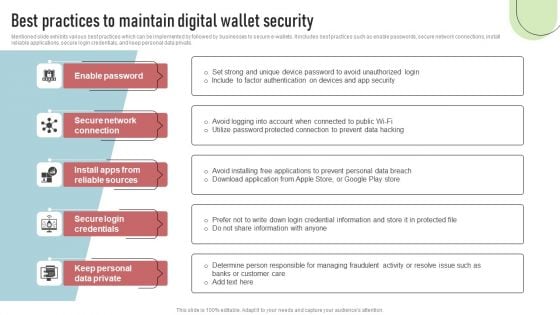
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
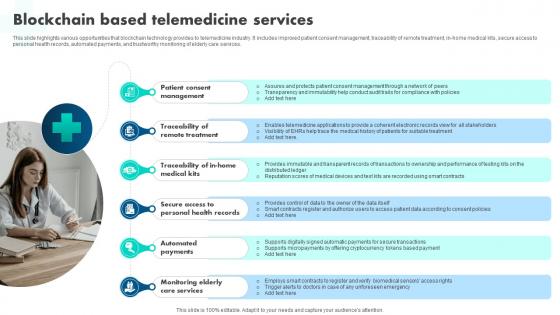
A55 How Blockchain Is Reshaping Blockchain Based Telemedicine Services BCT SS V
This slide highlights various opportunities that blockchain technology provides to telemedicine industry. It includes improved patient consent management, traceability of remote treatment, in-home medical kits, secure access to personal health records, automated payments, and trustworthy monitoring of elderly care services. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A55 How Blockchain Is Reshaping Blockchain Based Telemedicine Services BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights various opportunities that blockchain technology provides to telemedicine industry. It includes improved patient consent management, traceability of remote treatment, in-home medical kits, secure access to personal health records, automated payments, and trustworthy monitoring of elderly care services.
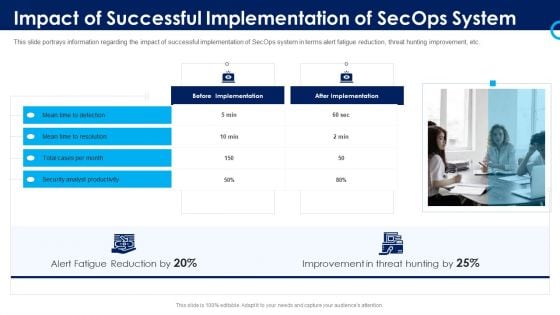
Organizational Security Solutions Impact Of Successful Implementation Of Secops System Designs PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting organizational security solutions impact of successful implementation of secops system designs pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
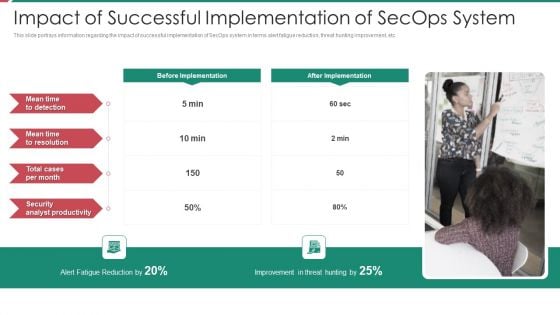
Security And Process Integration Impact Of Successful Implementation Of Secops System Diagrams PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting security and process integration impact of successful implementation of secops system diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
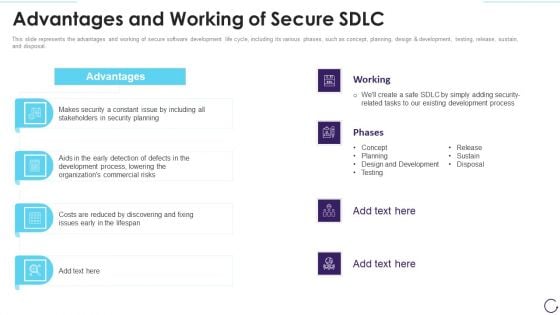
Application Development Life Cycle Advantages And Working Of Secure Sdlc Microsoft PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal. Presenting 30 60 90 days plan for software development life cycle structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advantages and working of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Existing Channel Development Strategy Infographics PDF
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Smart Home Security Solutions Company Profile Existing Channel Development Strategy Infographics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Direct To Home, Incentive Scheme Hubs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Staff Recruiting Criteria And Training Centre Designs PDF
This slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Presenting Security Agency Business Profile Staff Recruiting Criteria And Training Centre Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Selection Criteria, Authorized Training Centre. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
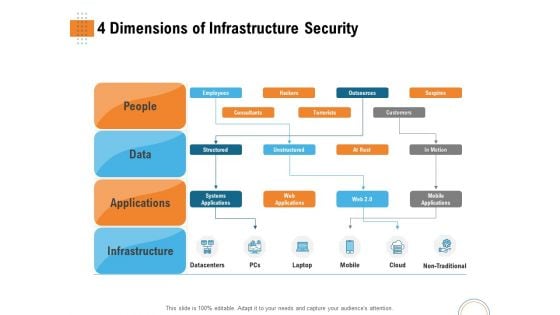
Utilizing Infrastructure Management Using Latest Methods 4 Dimensions Of Infrastructure Security Introduction PDF
Presenting utilizing infrastructure management using latest methods 4 dimensions of infrastructure security introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like people, data, applications, infrastructure, datacentres, mobile, cloud, non traditional. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Roadmap Inspiration PDF
Presenting case competition overpower the obstacle of cyber security in medicare roadmap inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap, 2017 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Timeline Sample PDF
Presenting case competition overpower the obstacle of cyber security in medicare timeline sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
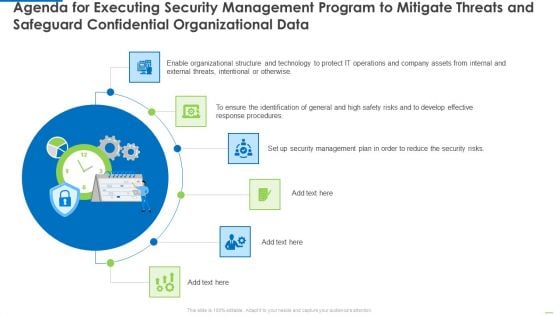
Agenda For Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Clipart PDF
Presenting Agenda for executing security management program to mitigate threats and safeguard confidential organizational data clipart pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like effective response procedures, intentional or otherwise, enable organizational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Roadmap Professional PDF
Presenting Executing security management program to mitigate threats and safeguard confidential organizational data roadmap professional pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Adopting Access Controls Demonstration PDF
Presenting security management plan steps in detail adopting access controls demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like logical access controls, control implementation, physical access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
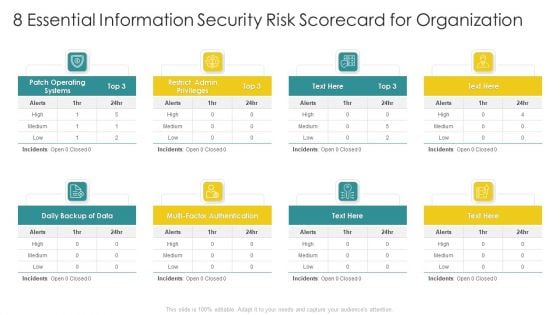
Cybersecurity Risk Scorecard 8 Essential Information Security Risk Scorecard For Organization Elements PDF
Presenting cybersecurity risk scorecard 8 essential information security risk scorecard for organization elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Techniques And Strategies To Reduce Security Management Risks Table Of Contents Structure PDF
Presenting techniques and strategies to reduce security management risks table of contents structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
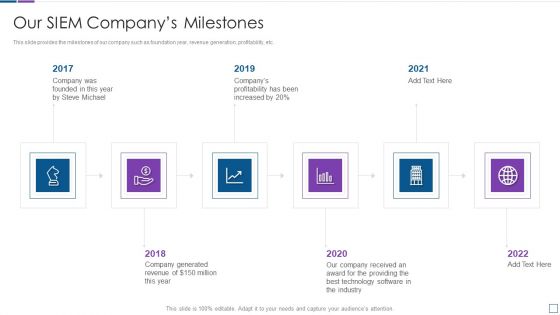
Real Time Assessment Of Security Threats Our SIEM Companys Milestones Slides PDF
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. Presenting real time assessment of security threats our siem companys milestones slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like our siem companys milestones. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF
Presenting Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Process Formulate, Management Plan, Mitigating Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
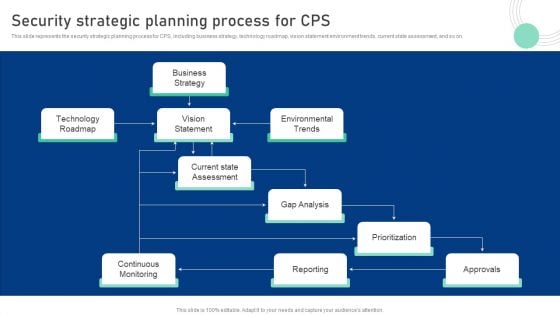
Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
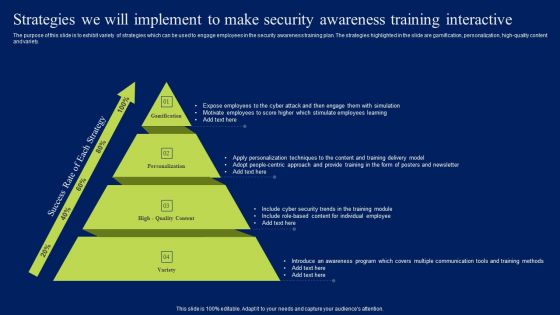
Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Slidegeeks is here to make your presentations a breeze with Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF
Pitch your topic with ease and precision using this Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF. This layout presents information on Virus Cyber Security, Attack Warning, Web Browser Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
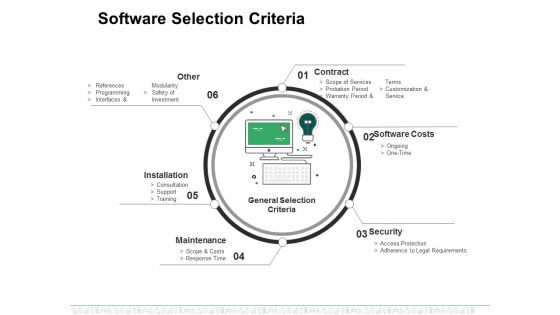
Software Selection Criteria Template 1 Ppt PowerPoint Presentation Gallery Slide
This is a software selection criteria template 1 ppt powerpoint presentation gallery slide. This is a six stage process. The stages in this process are other, installation, maintenance, security, software costs.

Employee Benefits Employees Allowance Ppt PowerPoint Presentation Show Graphics Template
This is a employee benefits employees allowance ppt powerpoint presentation show graphics template. This is a eight stage process. The stages in this process are social security, meal breaks, achievement award.
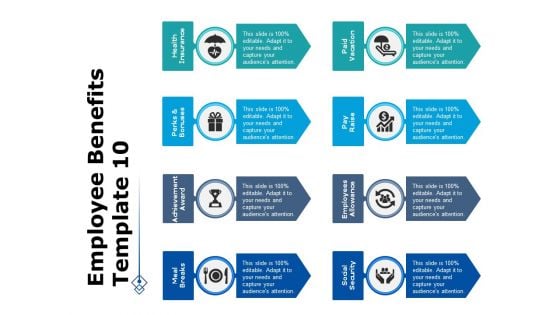
Employee Benefits Pay Vacation Ppt PowerPoint Presentation Infographic Template Shapes
This is a employee benefits pay vacation ppt powerpoint presentation infographic template shapes. This is a eight stage process. The stages in this process are employee benefit, health insurance, social security, achievement award, management.
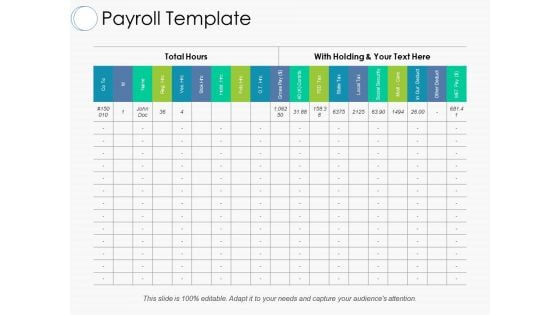
Payroll Template Ppt PowerPoint Presentation Gallery Master Slide
This is a payroll template ppt powerpoint presentation gallery master slide. This is a two stage process. The stages in this process are compare table, name, gross pay, state tax, local tax, social security.
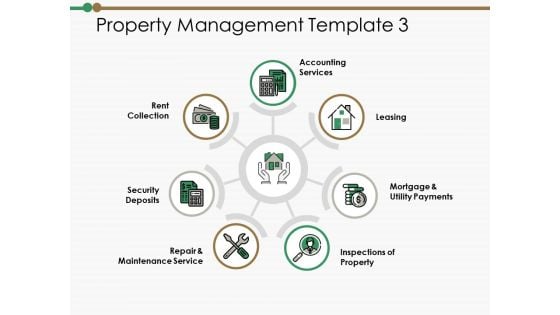
Property Management Template Ppt PowerPoint Presentation Styles Designs
This is a property management template ppt powerpoint presentation styles designs. This is a seven stage process. The stages in this process are rent collection, security deposits, inspections of property.
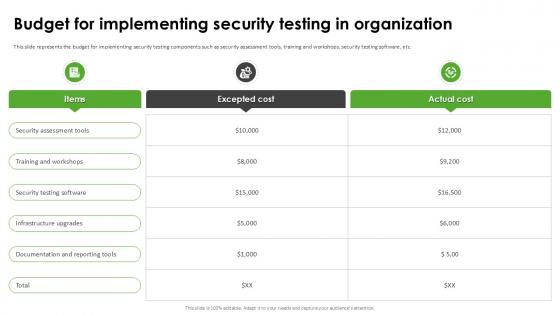
Budget For Implementing Harnessing The World Of Ethical Ppt Presentation
This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc. Get a simple yet stunning designed Budget For Implementing Harnessing The World Of Ethical Ppt Presentation It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget For Implementing Harnessing The World Of Ethical Ppt Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc.
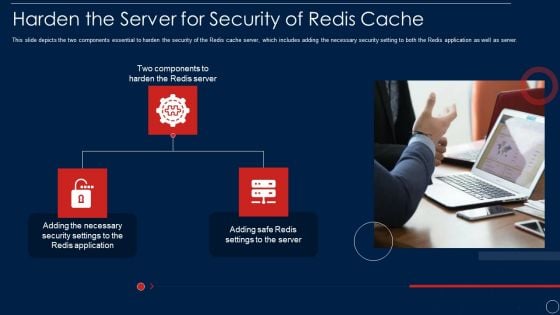
Redis Cache Data Structure IT Harden The Server For Security Of Redis Cache Template PDF
This slide depicts the two components essential to harden the security of the Redis cache server, which includes adding the necessary security setting to both the Redis application as well as server. This is a redis cache data structure it harden the server for security of redis cache template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like harden the server for security of redis cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Role, Position, Responsibility, Chief Information Officer, Information Management Manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
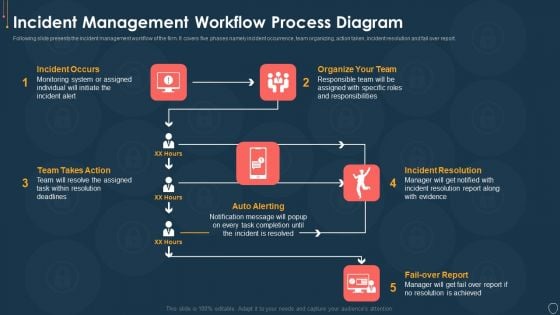
Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Presenting this PowerPoint presentation, titled CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
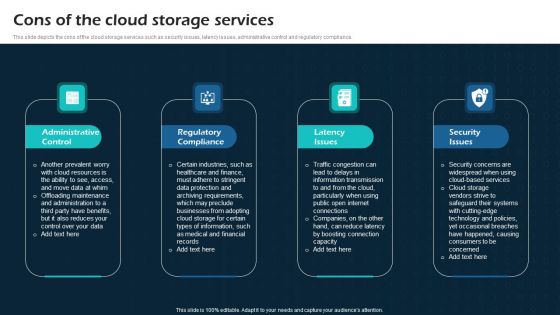
Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF
This slide depicts the cons of the cloud storage services such as security issues, latency issues, administrative control and regulatory compliance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

In Depth Business Assessment Business Insurance Ppt PowerPoint Presentation Gallery Brochure PDF
This is a in depth business assessment business insurance ppt powerpoint presentation gallery brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting assets and revenues, safeguarding organizations interests, securing wheels business, securing projects and profits, putting employees first. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
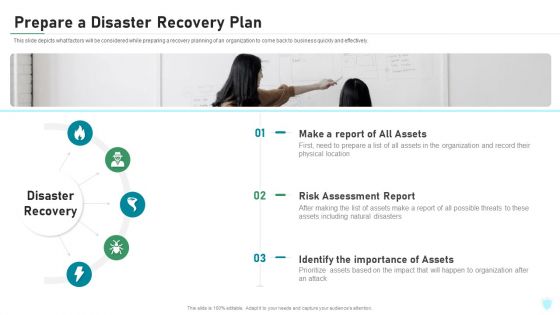
Prepare A Disaster Recovery Plan IT Security IT Ppt Ideas Graphics Design PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Presenting prepare a disaster recovery plan it security it ppt ideas graphics design pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like make a report of all assets, risk assessment report, identify the importance of assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Computer System Interface Icon With Cloud Storage Ppt File Backgrounds PDF
Persuade your audience using this Security Computer System Interface Icon With Cloud Storage Ppt File Backgrounds PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security Computer System, Interface Icon, Cloud Storage. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon Of Security Problem Management For Data Protection Ppt Infographics Designs Download PDF
Persuade your audience using this Icon Of Security Problem Management For Data Protection Ppt Infographics Designs Download PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Of Security, Problem Management, Data Protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Get a simple yet stunning designed Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Get a simple yet stunning designed Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
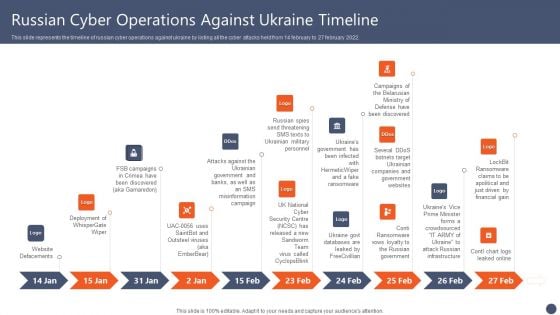
Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF
This slide represents the timeline of russian cyber operations against ukraine by listing all the cyber attacks held from 14 february to 27 february 2022. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Manpower Corporate Security Business Profile Executive Leadership And Management Team Template PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Manpower Corporate Security Business Profile Executive Leadership And Management Team Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Business, Security Operations, Resource Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
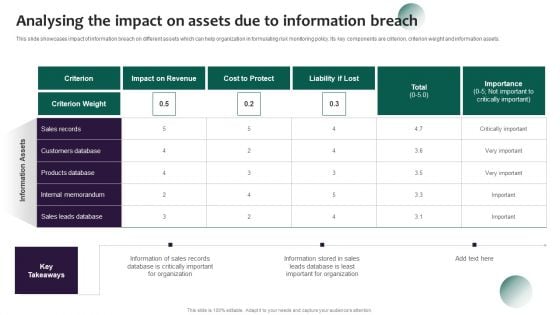
Information Systems Security And Risk Management Plan Analysing The Impact On Assets Due To Information Breach Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. This Information Systems Security And Risk Management Plan Analysing The Impact On Assets Due To Information Breach Introduction PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
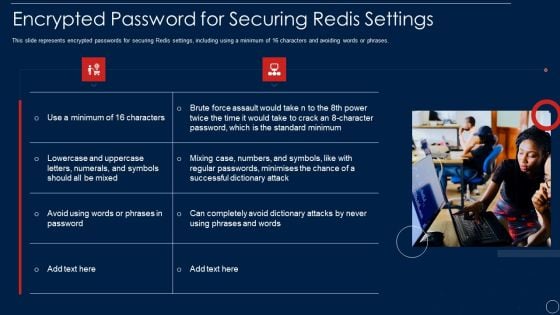
Redis Cache Data Structure IT Encrypted Password For Securing Redis Settings Formats PDF
This slide represents encrypted passwords for securing Redis settings, including using a minimum of 16 characters and avoiding words or phrases. This is a redis cache data structure it encrypted password for securing redis settings formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypted password for securing redis settings. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Sales CRM Cloud Solutions Deployment Securing Our Data With CRM Infographics PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a Sales CRM Cloud Solutions Deployment Securing Our Data With CRM Infographics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Storage And Failover, Communication Protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
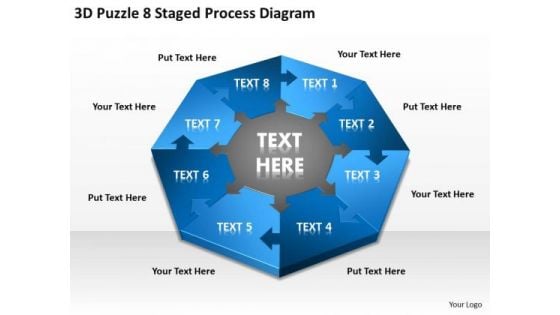
3d Puzzle 8 Staged Process Diagram Ppt Security Business Plan PowerPoint Slides
We present our 3d puzzle 8 staged process diagram ppt security business plan PowerPoint Slides.Download and present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download and present our Puzzles or Jigsaws PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Present our Flow Charts PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market.Use these PowerPoint slides for presentations relating to Puzzle, wheel, circular, colorful, concept, render, bright, circle, element, abstract, multicolored, creative, palette, illustration, creativity, shade, collection, design, blue, style, part, contrast, pattern . The prominent colors used in the PowerPoint template are Blue, White, Gray. Erase all ambiguity with our 3d Puzzle 8 Staged Process Diagram Ppt Security Business Plan PowerPoint Slides. They will put your point across in a decisive way.
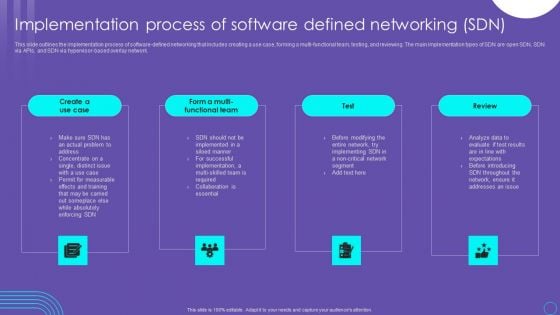
SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF
This slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. The SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
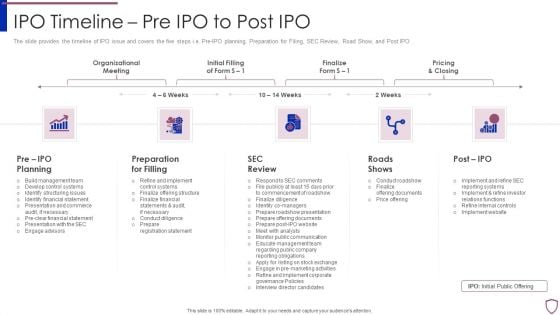
Financing Catalogue For Security Underwriting Agreement IPO Timeline Pre IPO To Post IPO Microsoft PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPO. Presenting financing catalogue for security underwriting agreement ipo timeline pre ipo to post ipo microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like pre ipo planning, preparation for filling, sec review, roads shows, post ipo. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































