Safety Summary
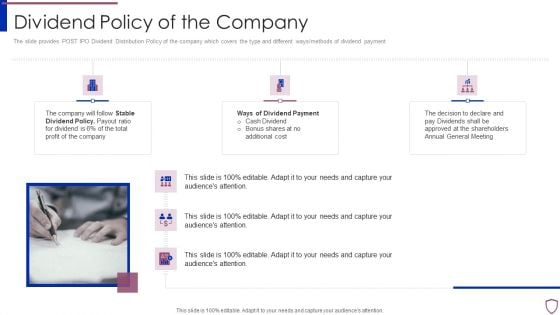
Financing Catalogue For Security Underwriting Agreement Dividend Policy Of The Company Elements PDF
The slide provides POST IPO Dividend Distribution Policy of the company which covers the type and different ways or methods of dividend payment. Presenting financing catalogue for security underwriting agreement dividend policy of the company elements pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like stable dividend policy, ways of dividend payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
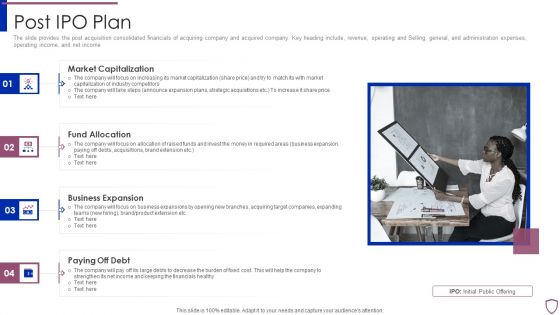
Financing Catalogue For Security Underwriting Agreement Post IPO Plan Inspiration PDF
The slide provides the post acquisition consolidated financials of acquiring company and acquired company. Key heading include, revenue, operating and Selling, general, and administration expenses, operating income, and net income. Presenting financing catalogue for security underwriting agreement post ipo plan inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like market capitalization, fund allocation, business expansion, paying off debt. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization threat management action plan introduction pdf
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Our SIEM Companys Security Information And Event Management Strategies For Financial Audit And Compliance Portrait PDF
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. Presenting our siem companys security information and event management strategies for financial audit and compliance portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like our siem companys milestones. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
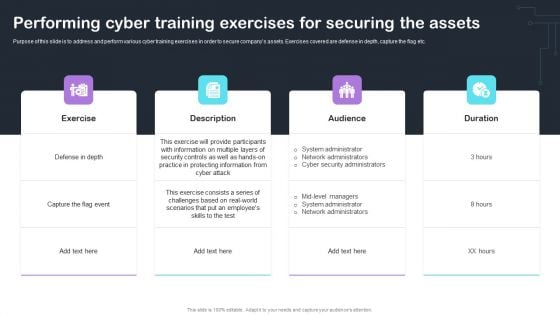
Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Retrieve professionally designed Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Retrieve professionally designed Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents For Cyber Physical System To Enhance Security Topics PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Cyber Physical System To Enhance Security Topics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Cyber Physical System To Enhance Security Topics PDF today and make your presentation stand out from the rest.
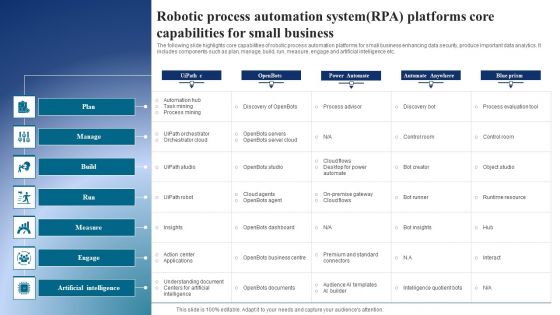
Robotic Process Automation Systemrpa Platforms Core Capabilities For Small Business Structure PDF
The following slide highlights core capabilities of robotic process automation platforms for small business enhancing data security, produce important data analytics. It includes components such as plan, manage, build, run, measure, engage and artificial intelligence etc. Showcasing this set of slides titled Robotic Process Automation Systemrpa Platforms Core Capabilities For Small Business Structure PDF. The topics addressed in these templates are Plan, Manage, Build . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
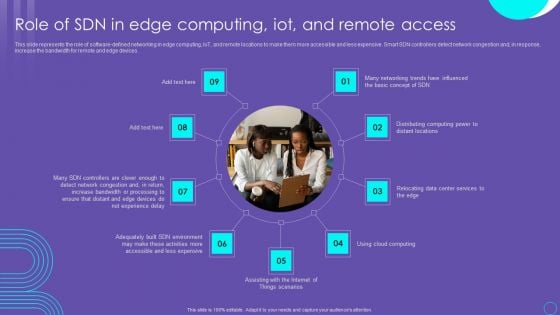
SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF
This slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Boost your pitch with our creative SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF
Pitch your topic with ease and precision using this Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF. This layout presents information on Compliance Trend, Risk Status, Risk Severity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF
Pitch your topic with ease and precision using this Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF. This layout presents information on Phishing Cyber Securit, Attack Unprotected, Web Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
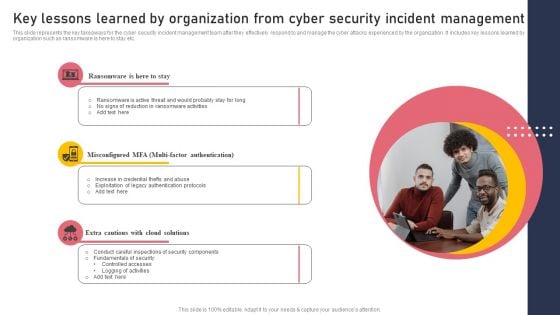
Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF today and make your presentation stand out from the rest.
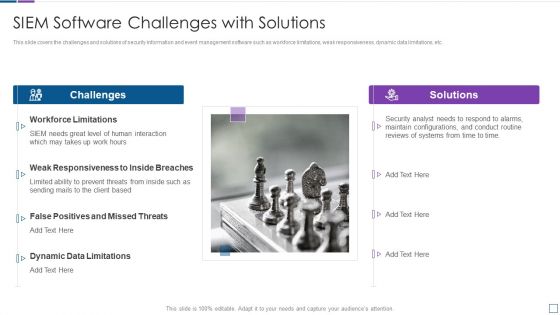
Real Time Assessment Of Security Threats SIEM Software Challenges With Solutions Inspiration PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a real time assessment of security threats siem software challenges with solutions inspiration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, false positives and missed threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
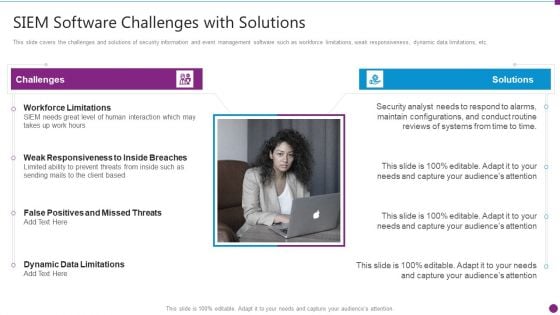
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Software Challenges Professional PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a security information and event management strategies for financial audit and compliance siem software challenges professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, siem needs great level of human interaction, dynamic data limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
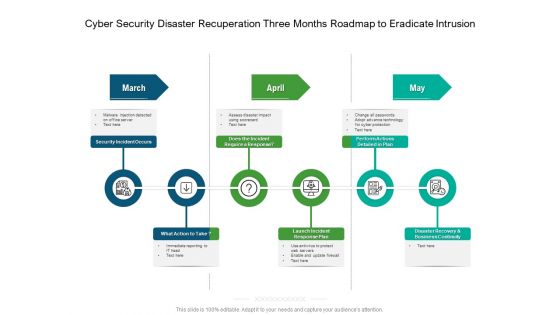
Cyber Security Disaster Recuperation Three Months Roadmap To Eradicate Intrusion Topics
Presenting our jaw-dropping cyber security disaster recuperation three months roadmap to eradicate intrusion topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
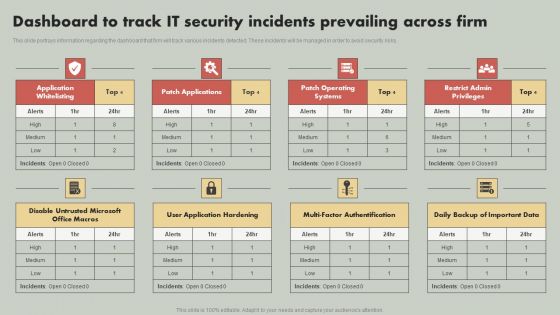
IT Reducing Costs And Management Tips Dashboard To Track IT Security Incidents Prevailing Across Firm Structure PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Boost your pitch with our creative IT Reducing Costs And Management Tips Dashboard To Track IT Security Incidents Prevailing Across Firm Structure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
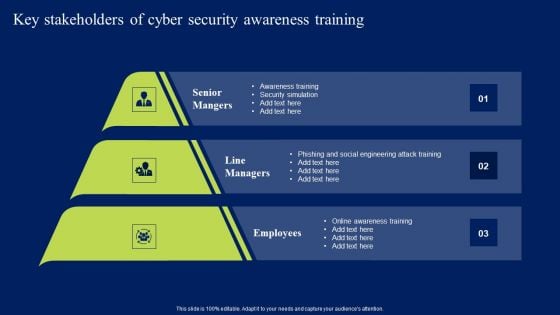
Key Stakeholders Of Cyber Security Awareness Training Ppt Ideas Good PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Key Stakeholders Of Cyber Security Awareness Training Ppt Ideas Good PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black. Aim for the skies with our Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides. You will come out on top.

E Commerce E Business Infrastructure Management Ppt PowerPoint Presentation Portfolio Tips PDF
Presenting this set of slides with name e commerce e business infrastructure management ppt powerpoint presentation portfolio tips pdf. This is a six stage process. The stages in this process are flexibility, costs, scope and performance, it security and compliance, reliability and trustworthiness, services and cloud management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
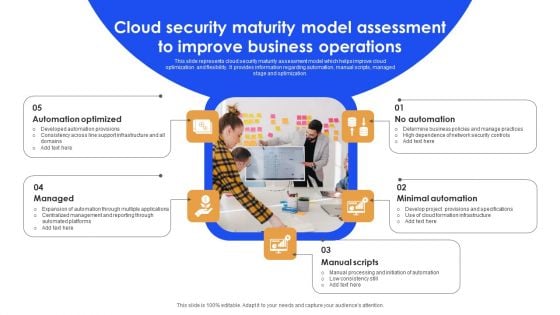
Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF
This slide represents cloud security maturity assessment model which helps improve cloud optimization and flexibility. It provides information regarding automation, manual scripts, managed stage and optimization. Persuade your audience using this Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Automation Optimized, Minimal Automation, Manual Scripts. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
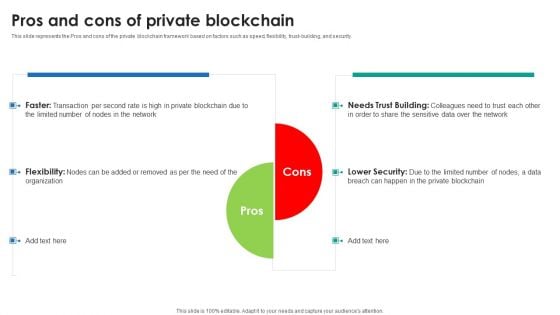
P2P Ledger Pros And Cons Of Private Blockchain Diagrams PDF
This slide represents the Pros and cons of the private blockchain framework based on factors such as speed, flexibility, trust-building, and security.Find a pre-designed and impeccable P2P Ledger Pros And Cons Of Private Blockchain Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF
This slide represents the importance of virtualization in software defined networking and how they complement one another. It also includes how SDN helps simplify the process of controlling data packet routing via a central server. Retrieve professionally designed SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
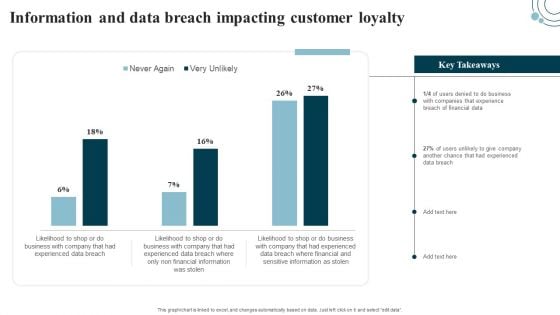
Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select edit data. Get a simple yet stunning designed Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
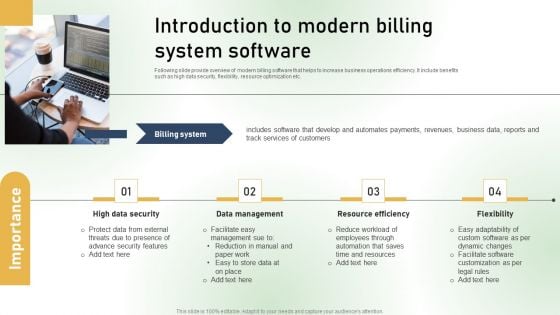
Introduction To Modern Billing System Software Ppt PowerPoint Presentation File Ideas PDF
Following slide provide overview of modern billing software that helps to increase business operations efficiency. It include benefits such as high data security, flexibility, resource optimization etc.Retrieve professionally designed Introduction To Modern Billing System Software Ppt PowerPoint Presentation File Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
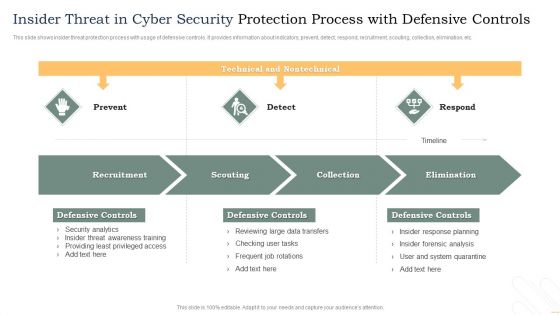
Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
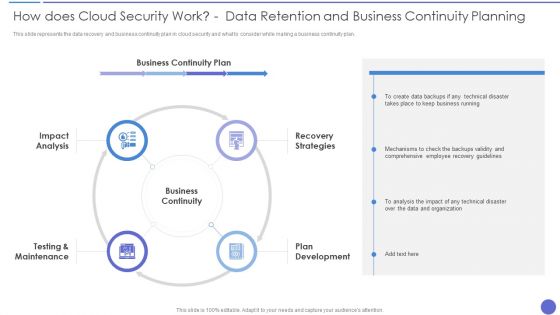
How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Presenting How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Continuity, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
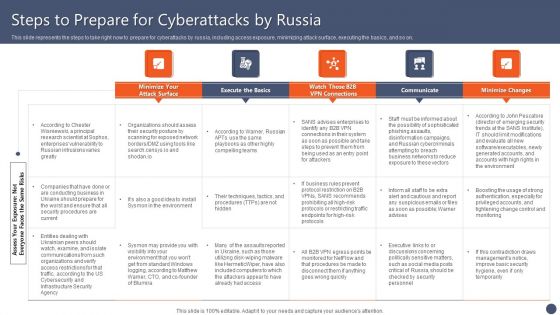
Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
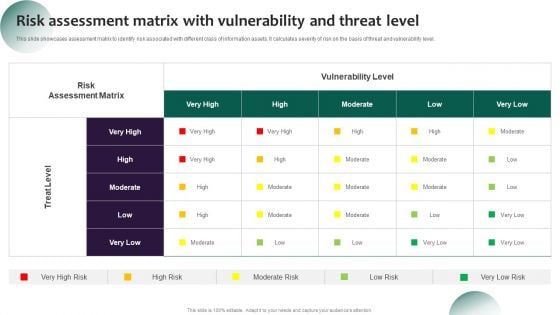
Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Explore a selection of the finest Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
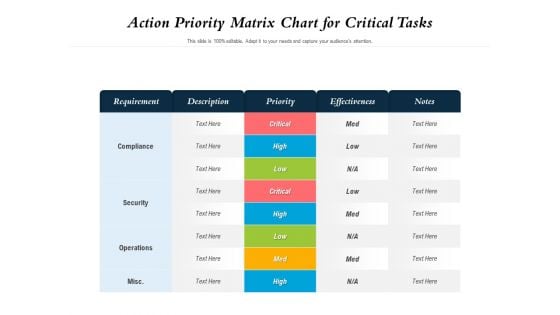
Action Priority Matrix Chart For Critical Tasks Ppt PowerPoint Presentation File Graphics Template PDF
Showcasing this set of slides titled action priority matrix chart for critical tasks ppt powerpoint presentation file graphics template pdf. The topics addressed in these templates are effectiveness, security, priority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
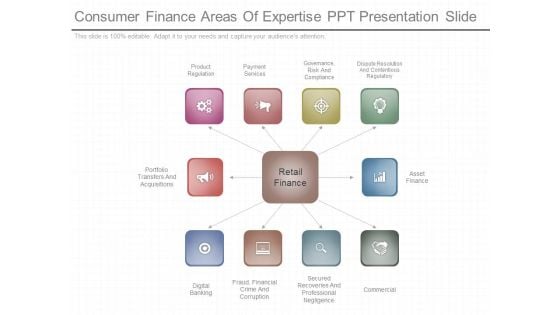
Consumer Finance Areas Of Expertise Ppt Presentation Slide
This is a consumer finance areas of expertise ppt presentation slide. This is a ten stage process. The stages in this process are product regulation, payment services, governance risk and compliance, dispute resolution and contentious regulatory, portfolio transfers and acquisitions, asset finance, retail finance, digital banking, fraud financial crime and corruption, secured recoveries and professional negligence, commercial.
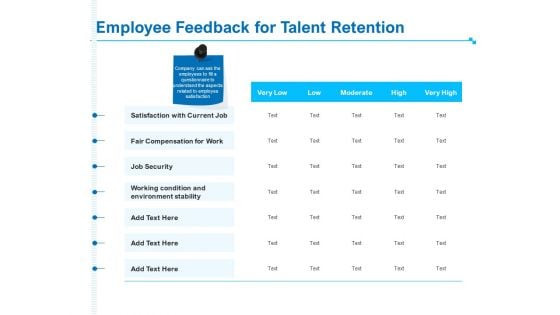
Strategic Talent Management Employee Feedback For Talent Retention Ppt PowerPoint Presentation Model Templates PDF
Deliver an awe-inspiring pitch with this creative strategic talent management employee feedback for talent retention ppt powerpoint presentation model templates pdf bundle. Topics like satisfaction with current job, fair compensation work, job security, working condition and environment stability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
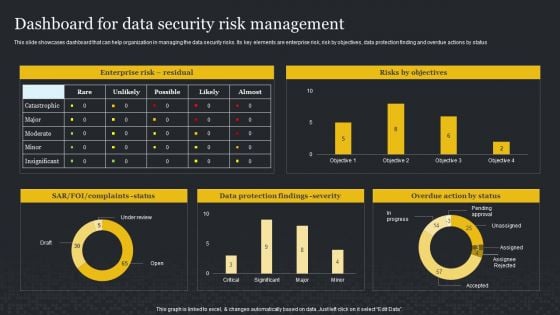
Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
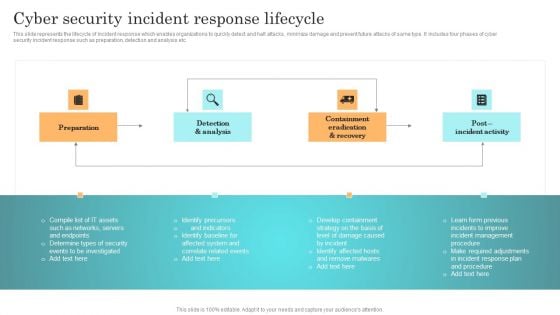
Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF

Information Technology Policy And Processes Information Security Policy For Employees Structure PDF
This slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Technology Policy And Processes Information Security Policy For Employees Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
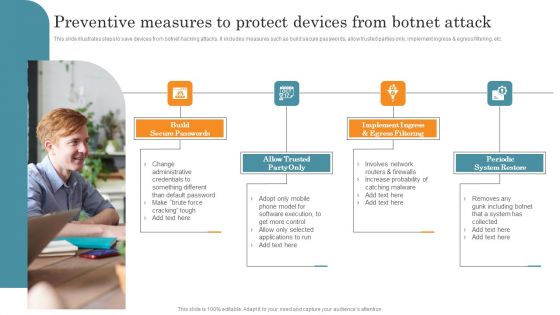
Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF
This slide illustrates steps to save devices from botnet hacking attacks. It includes measures such as build secure passwords, allow trusted parties only, implement ingress and egress filtering, etc. Presenting Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Build Secure Passwords, Allow Trusted Party Only, Implement Ingress. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
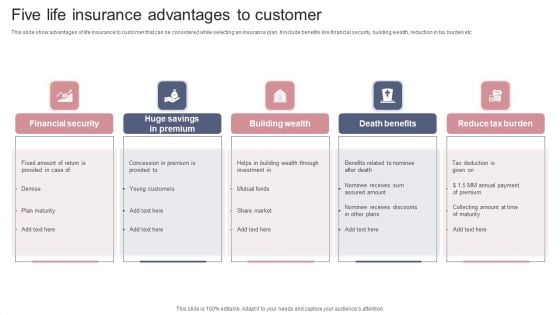
Five Life Insurance Advantages To Customer Themes PDF
This slide show advantages of life insurance to customer that can be considered while selecting an insurance plan. It include benefits like financial security, building wealth, reduction in tax burden etc. Presenting Five Life Insurance Advantages To Customer Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Financial Security, Building Wealth, Reduce Tax Burden. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information And Technology Security Operations Various Technologies For Effective Secops Process Infographics PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a information and technology security operations various technologies for effective secops process infographics pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
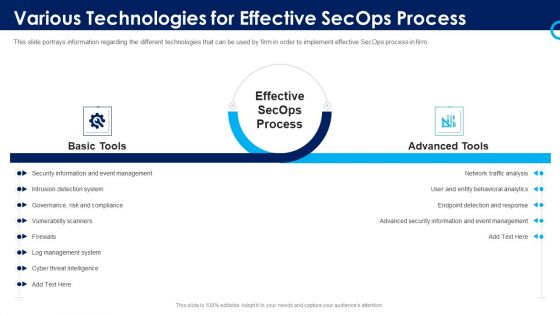
Organizational Security Solutions Various Technologies For Effective Secops Process Designs PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a organizational security solutions various technologies for effective secops process designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
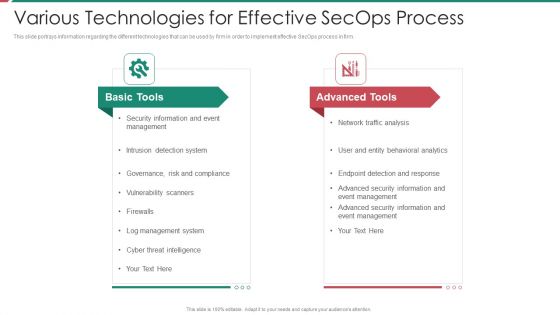
Security And Process Integration Various Technologies For Effective Secops Process Clipart PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a security and process integration various technologies for effective secops process clipart pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Food Receipt And Storage To Ensure Quality Food Security Excellence Ppt Portfolio Guide PDF
This slide provides information regarding food receipt and storage to ensure food quality by handling normal and potentially hazard food. This is a food receipt and storage to ensure quality food security excellence ppt portfolio guide pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like food storage, food receipt. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This is a Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Container Approach, Platform Approach, Critical Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Standard Mobile Device Management Components Mobile Device Security Management Information PDF
This slide provides information regarding essential standard mobile device management components terms of central management console, registry.This is a Determine Standard Mobile Device Management Components Mobile Device Security Management Information PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Console, Create Virtual, Synchronization Among. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management Assistance To Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. This is a Mobile Device Management Assistance To Mobile Device Security Management Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reducing Connection, Rendering Appropriate, Remote Configuration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Person Holding Smart Phone With Security Shield Vector Icon Ppt Infographics Format PDF
Presenting person holding smart phone with security shield vector icon ppt infographics format pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including person holding smart phone with security shield vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Operations Center Icon For Monitoring Functions Ppt Gallery Professional PDF
Presenting cyber security operations center icon for monitoring functions ppt gallery professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber security operations center icon for monitoring functions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Management Plan Framework With Security And Auditing Ppt Icon File Formats PDF
Presenting data management plan framework with security and auditing ppt icon file formats pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including data lifestyle management, data security, capability needs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Top 5 Issues In Security Problem Management Ppt Slides Show PDF
Presenting Top 5 Issues In Security Problem Management Ppt Slides Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Lack Threat Program, No Operational Exercises, Security Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Security Awareness Training Program Icon Ppt Slides Example File PDF
Presenting IT Security Awareness Training Program Icon Ppt Slides Example File PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including IT Security, Awareness Training, Program Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Analysis Of Various Banks To Secure Best Funding Offer Opening Retail Store In Untapped Themes PDF
The following slide showcases the comparison of different banks offering term loans to businesses. The comparison is drawn on the basis of interest rate, processing fees and equated monthly installment EMI. There are so many reasons you need a Comparative Analysis Of Various Banks To Secure Best Funding Offer Opening Retail Store In Untapped Themes PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementation Best Practices For IaaS Cloud Transforming Business With IaaS Download Pdf
This slide outlines the best practices for Infrastructure as a Service cloud model implementation. The guidelines include developing and testing the strategy, planning a long-term budget, leveraging expertise, and securing everything. There are so many reasons you need a Implementation Best Practices For IaaS Cloud Transforming Business With IaaS Download Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the best practices for Infrastructure as a Service cloud model implementation. The guidelines include developing and testing the strategy, planning a long-term budget, leveraging expertise, and securing everything.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
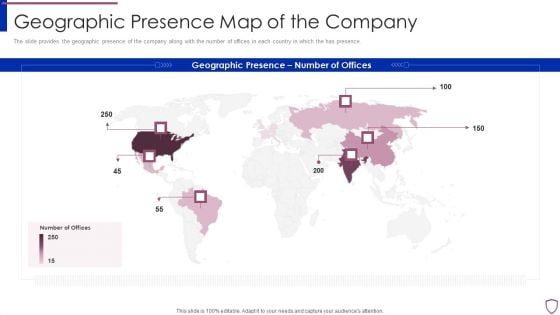
Financing Catalogue For Security Underwriting Agreement Geographic Presence Map Of The Company Template PDF
The slide provides the geographic presence of the company along with the number of offices in each country in which the has presence. Presenting financing catalogue for security underwriting agreement geographic presence map of the company template pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like geographic presence map of the company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
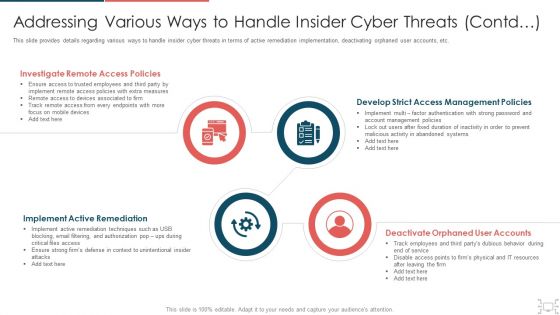
cyber security administration in organization addressing various ways to handle insider cyber active template pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting cyber security administration in organization addressing various ways to handle insider cyber active template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigate, access, policies, remediation, implement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































