Safety Summary
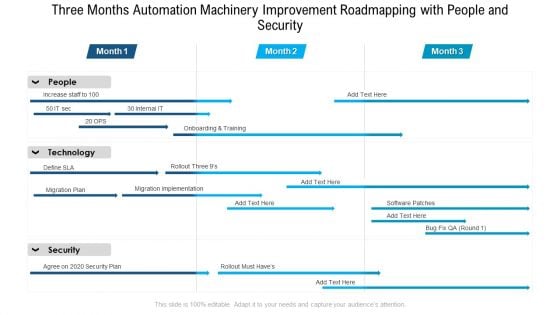
Three Months Automation Machinery Improvement Roadmapping With People And Security Designs
Introducing our three months automation machinery improvement roadmapping with people and security designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Evolution Of ESO System Center Ppt PowerPoint Presentation File Show PDF
This slide covers evolution of enterprise security operation center. It involves availability monitoring, reactive monitoring, proactive monitoring and monitoring with automation. Pitch your topic with ease and precision using this Evolution Of ESO System Center Ppt PowerPoint Presentation File Show PDF. This layout presents information on Availability Monitoring, Reactive Monitoring, Proactive Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
3 Stage Plan Cyber Security Plan For Data Protection Ppt Icon Picture PDF
This slide signifies the three stage cyber security program to improve data protection. It covers information about steps like prevention, response and remediation. Persuade your audience using this 3 Stage Plan Cyber Security Plan For Data Protection Ppt Icon Picture PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prevention, Response, Remediation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
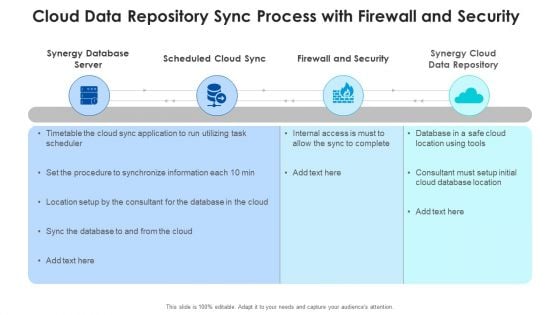
Cloud Data Repository Sync Process With Firewall And Security Brochure PDF
Presenting cloud data repository sync process with firewall and security brochure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including synergy database server, scheduled cloud sync, firewall and security, synergy cloud data repository . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
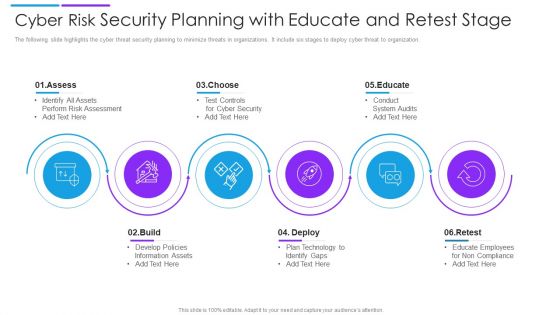
Cyber Risk Security Planning With Educate And Retest Stage Demonstration PDF
The following slide highlights the cyber threat security planning to minimize threats in organizations. It include six stages to deploy cyber threat to organization. Presenting cyber risk security planning with educate and retest stage demonstration pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including assess, choose, educate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
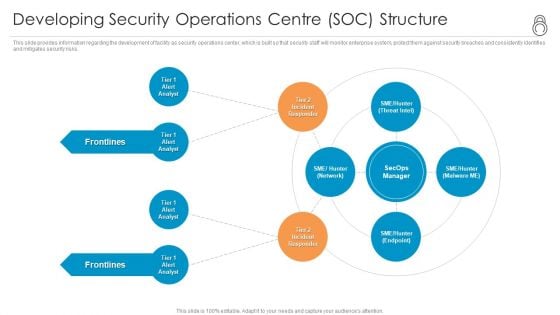
Enhanced Protection Corporate Event Administration Developing Security Operations Centre SOC Structure Formats PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting enhanced protection corporate event administration developing security operations centre soc structure formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.Presenting ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Asset Management, Operational Security, Physical And Environmental. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
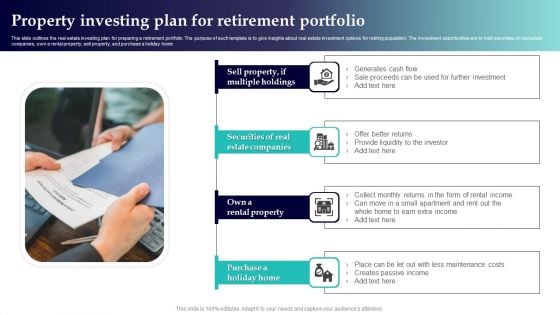
Property Investing Plan For Retirement Portfolio Themes PDF
This slide outlines the real estate investing plan for preparing a retirement portfolio. The purpose of such template is to give insights about real estate investment options for retiring population. The investment opportunities are to hold securities of real estate companies, own a rental property, sell property, and purchase a holiday home. Presenting Property Investing Plan For Retirement Portfolio Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Securities Real Estate Companies, Own Rental Property, Purchase Holiday Home. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
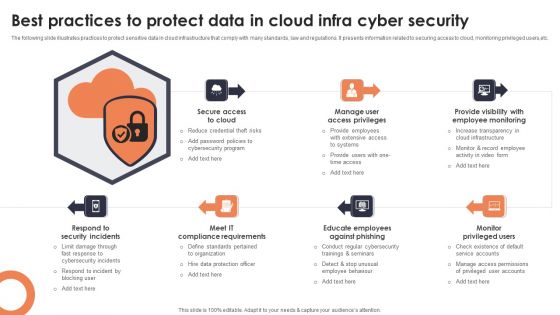
Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF
The following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users,etc. Presenting Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Secure Access Cloud, Manage User Access Privileges, Provide Visibility Employee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
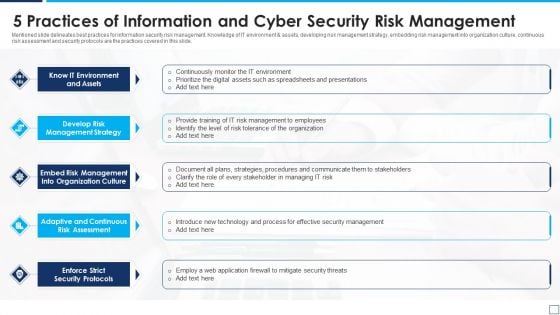
5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
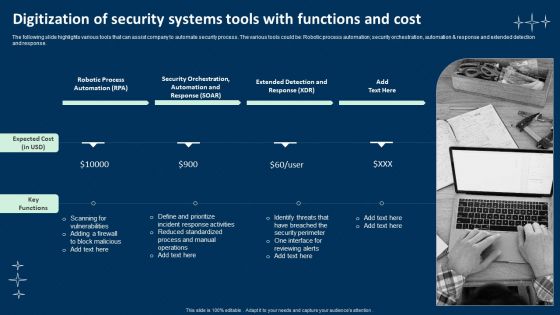
Digitization Of Security Systems Tools With Functions And Cost Mockup PDF
The following slide highlights various tools that can assist company to automate security process. The various tools could be Robotic process automation, security orchestration, automation and response and extended detection and response. Presenting Digitization Of Security Systems Tools With Functions And Cost Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Robotic Process Automation, Security Orchestration, Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
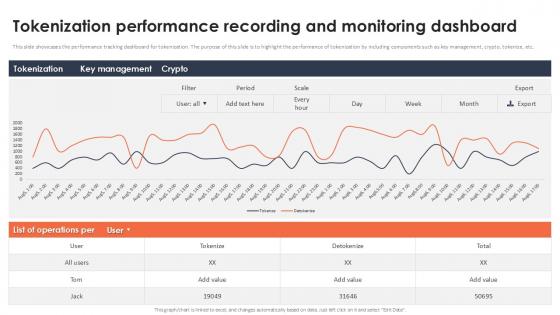
Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide
This slide showcases the performance tracking dashboard for tokenization. The purpose of this slide is to highlight the performance of tokenization by including components such as key management, crypto, tokenize, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide today and make your presentation stand out from the rest This slide showcases the performance tracking dashboard for tokenization. The purpose of this slide is to highlight the performance of tokenization by including components such as key management, crypto, tokenize, etc.
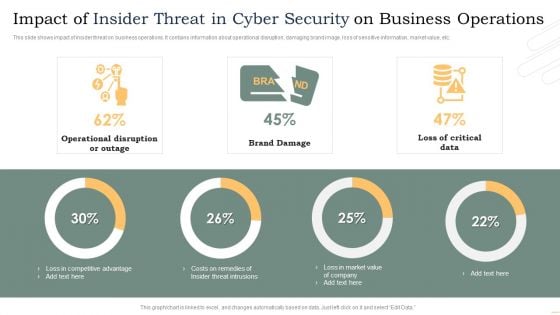
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
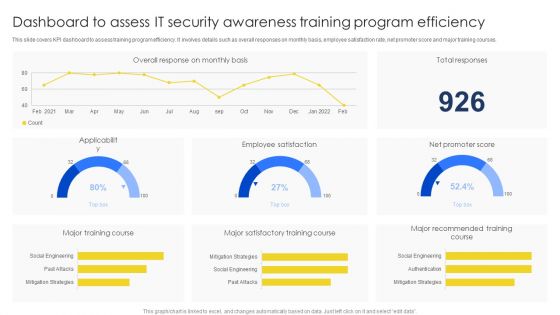
Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF
This slide covers KPI dashboard to assess training program efficiency. It involves details such as overall responses on monthly basis, employee satisfaction rate, net promoter score and major training courses. Pitch your topic with ease and precision using this Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF. This layout presents information on Major Training Course, Major Satisfactory, Training Course. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
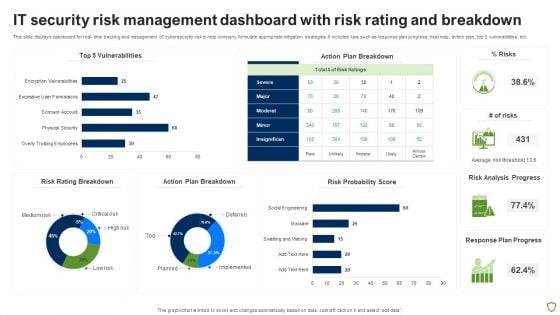
IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF
This slide displays dashboard for real- time tracking and management of cybersecurity risk to help company formulate appropriate mitigation strategies. It includes kpis such as response plan progress, heat map, action plan, top 5 vulnerabilities, etc. Pitch your topic with ease and precision using this IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF. This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Probability Score, Risk Analysis Progress. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
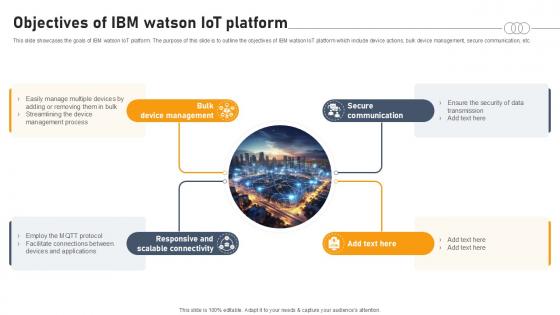
Objectives Of Ibm Watson IOT Platform Aws IOT Platform Ppt Slide
This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Objectives Of Ibm Watson IOT Platform Aws IOT Platform Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc.

Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF.

Redis Cache Data Structure IT Secure Server Configuration With Server Configuration Lock Diagrams PDF
This slide describes the secure server configuration with server configuration lock, which guarantees only users have access. Presenting redis cache data structure it secure server configuration with server configuration lock diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like securing, programmer, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
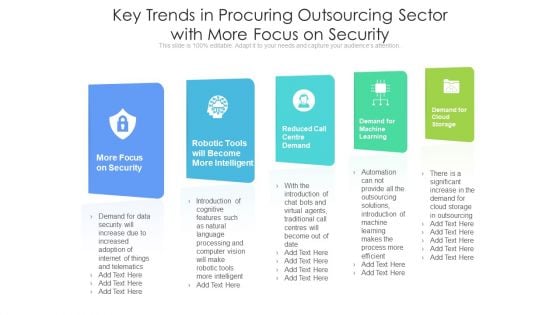
Key Trends In Procuring Outsourcing Sector With More Focus On Security Ppt Gallery Smartart PDF
Persuade your audience using this key trends in procuring outsourcing sector with more focus on security ppt gallery smartart pdf.This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including demand for machine learning, demand for cloud storage. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
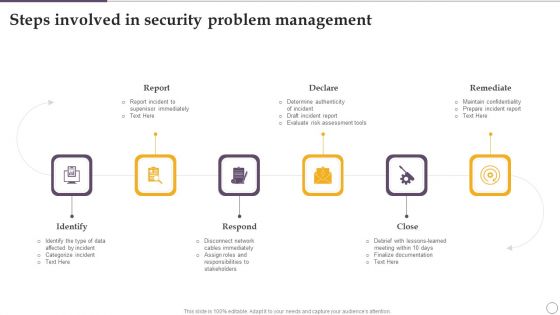
Steps Involved In Security Problem Management Ppt Inspiration Graphics Example PDF
Persuade your audience using this Steps Involved In Security Problem Management Ppt Inspiration Graphics Example PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Report, Declare, Remediate, Close, Respond, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icons Slide For Email Security Market Research Report Ppt Professional Examples PDF
Presenting this set of slides containing editable icons for topic icons slide for email security market research report ppt professional examples pdf. All icons in this slide are 100 percent editable. You can replace icons in your deck with any of these icons. Download now and impress your audience.
Icons Slide For Computer Security Incident Handling Ppt Ideas Example Topics PDF
Presenting this set of slides containing editable icons for topic icons slide for computer security incident handling ppt ideas example topics pdf. All icons in this slide are 100 percent editable. You can replace icons in your deck with any of these icons. Download now and impress your audience.
Icons Slide For Strategies To Mitigate Cyber Security Risks Ppt Icon Themes PDF
Presenting this set of slides containing editable icons for topic icons slide for strategies to mitigate cyber security risks ppt icon themes pdf. All icons in this slide are 100 percent editable. You can replace icons in your deck with any of these icons. Download now and impress your audience.
Icons Slide For Cloud Based Email Security Market Report Ppt Infographics Graphic Images PDF
Introducing our well designed icons slide for cloud based email security market report ppt infographics graphic images pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Workforce Security Realization Coaching Plan Icons Slide Ppt Ideas Topics PDF
Introducing our well-designed workforce security realization coaching plan icons slide ppt ideas topics pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For IT Security Evaluation Scorecard Ppt Icon Good PDF
Introducing our well designed Icons Slide For IT Security Evaluation Scorecard Ppt Icon Good PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Multiple Channel Banking Challenges And Solutions Template PDF
This slide mentions omnichannel banking challenges faced while implementation and corresponding solutions. The basis of differentiation include Implementation Cost, Technology and Digital Security. Pitch your topic with ease and precision using this Multiple Channel Banking Challenges And Solutions Template PDF. This layout presents information on Technology, Digital Security, Implementation Cost. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Agenda For Security Control Techniques For Real Estate Project Themes PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Security Control Techniques For Real Estate Project Themes PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Security Control Techniques For Real Estate Project Themes PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
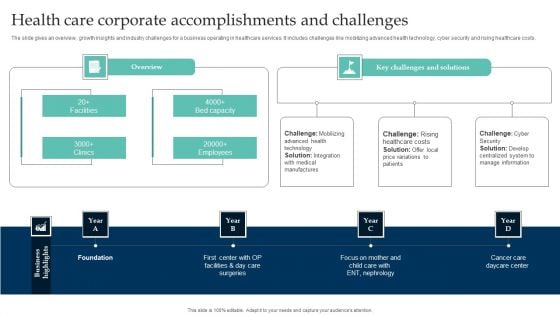
Health Care Corporate Accomplishments And Challenges Professional PDF
The slide gives an overview, growth insights and industry challenges for a business operating in healthcare services. It includes challenges like mobilizing advanced health technology, cyber security and rising healthcare costs. Persuade your audience using this Health Care Corporate Accomplishments And Challenges Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Employees, Healthcare Costs, Price. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
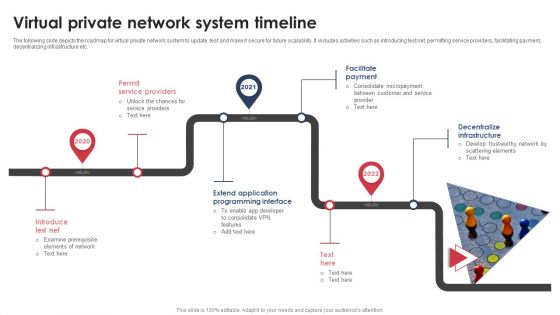
Virtual Private Network System Timeline Graphics PDF
The following slide depicts the roadmap for virtual private network system to update, test and make it secure for future scalability. It includes activities such as introducing test net, permitting service providers, facilitating payment, decentralizing infrastructure etc. Presenting Virtual Private Network System Timeline Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Permit Service Providers, Facilitate Payment, Decentralize Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Proposal For Enterprise Security System Case Study One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline. Presenting you an exemplary Proposal For Enterprise Security System Case Study One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Case Study One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document
The following slide displays the cover slide for the security system proposal, as it highlights the key details of the client requirement. Presenting you an exemplary Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Next Step One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on-site visit etc. Presenting you an exemplary Proposal For Enterprise Security System Next Step One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Next Step One Pager Sample Example Document brilliant piece now.
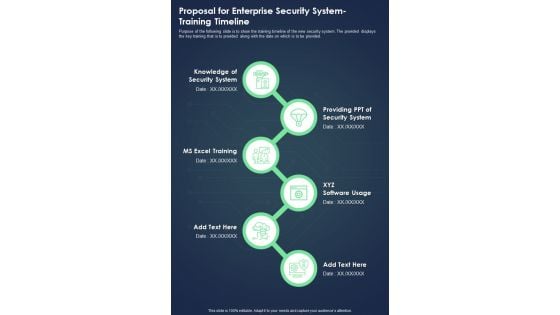
Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Your Investment One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system Presenting you an exemplary Proposal For Enterprise Security System Your Investment One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Your Investment One Pager Sample Example Document brilliant piece now.
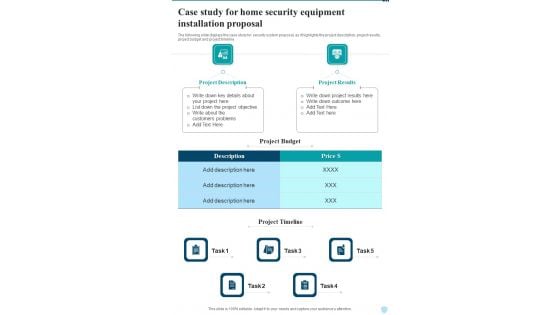
Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline Presenting you an exemplary Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the cover slide for the security system proposal, as it highlights the key details of the client requirement. Presenting you an exemplary Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on site visit etc. Presenting you an exemplary Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
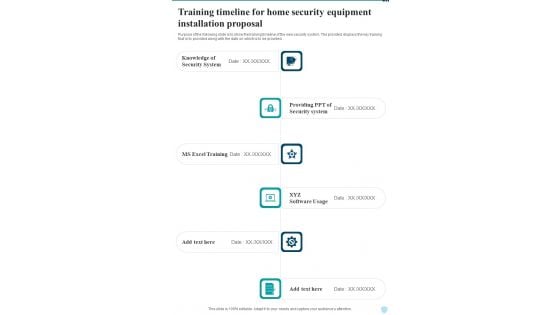
Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
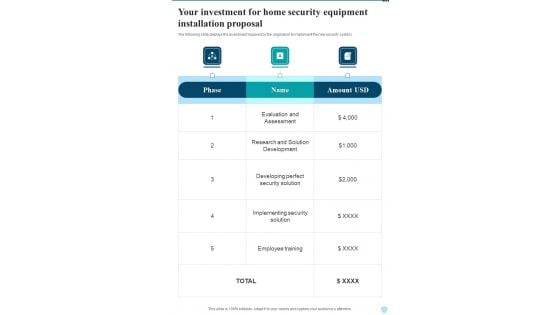
Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system. Presenting you an exemplary Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends Best, Smart Home Security, Systems Consumer Technology, Association Consumer Technology, Association Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Dependable Business, Security Information, Team Members. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF
The following slide showcases perceptive of expert analysts about IT company i.e. Awake Society. It showcase reviews of IT manager, chief information security officer and IT director. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
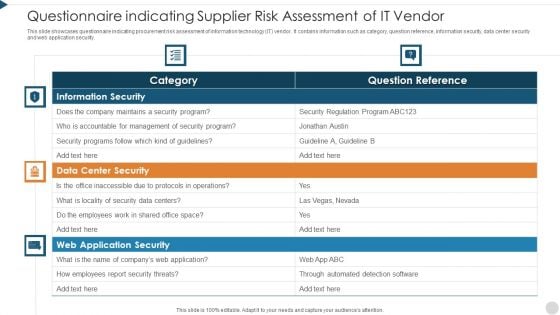
Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
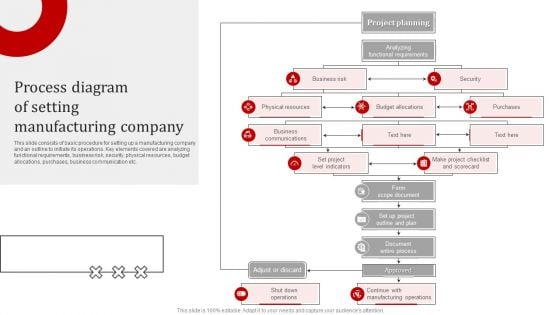
Process Diagram Of Setting Manufacturing Company Introduction PDF
This slide consists of basic procedure for setting up a manufacturing company and an outline to initiate its operations. Key elements covered are analyzing functional requirements, business risk, security, physical resources, budget allocations, purchases, business communication etc. Presenting Process Diagram Of Setting Manufacturing Company Introduction PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Business Risk, Security, Budget Allocations, Business Communications, Physical Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
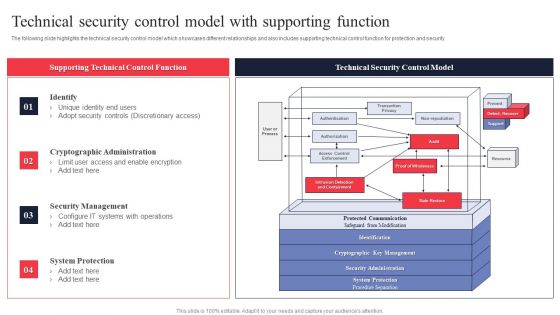
IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
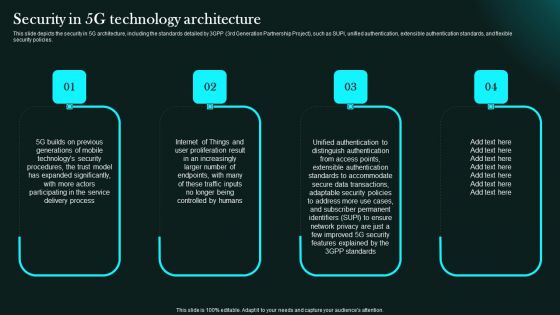
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Personalize Rewards Ppt PowerPoint Presentation Professional Gallery
This is a personalize rewards ppt powerpoint presentation professional gallery. This is a six stage process. The stages in this process are pay, promotion, recognition, job security.

Risk Categories Ppt PowerPoint Presentation Model Outfit
This is a risk categories ppt powerpoint presentation model outfit. This is a six stage process. The stages in this process are product performance, security, environment, design.

Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Do you know about Slidesgeeks Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
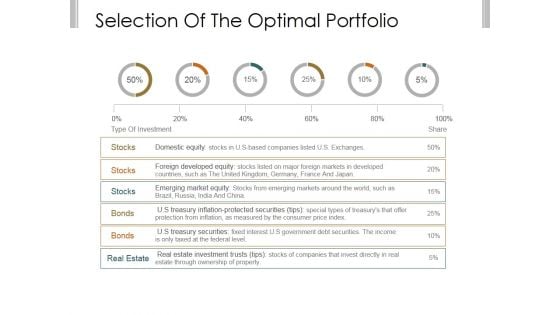
Selection Of The Optimal Portfolio Template 1 Ppt PowerPoint Presentation Diagrams
This is a selection of the optimal portfolio template 1 ppt powerpoint presentation diagrams. This is a six stage process. The stages in this process are domestic equity, foreign developed equity, emerging market equity, treasury securities, real estate investment trusts.

Impact Of Big Data Template 1 Ppt PowerPoint Presentation Background Images
This is a impact of big data template 1 ppt powerpoint presentation background images. This is a four stage process. The stages in this process are healthcare, science, security, business.

Impact Of Big Data Template 2 Ppt PowerPoint Presentation Portfolio Model
This is a impact of big data template 2 ppt powerpoint presentation portfolio model. This is a four stage process. The stages in this process are healthcare, science, security, business.
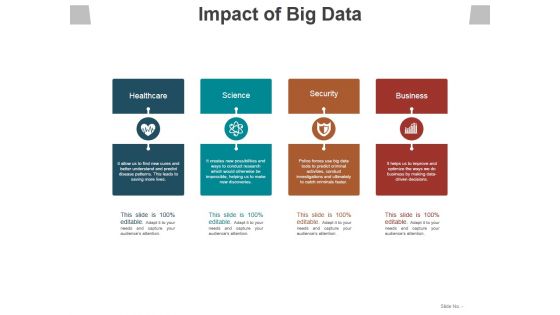
Impact Of Big Data Template 1 Ppt PowerPoint Presentation File Example File
This is a impact of big data template 1 ppt powerpoint presentation file example file. This is a four stage process. The stages in this process are healthcare, science, security, business.
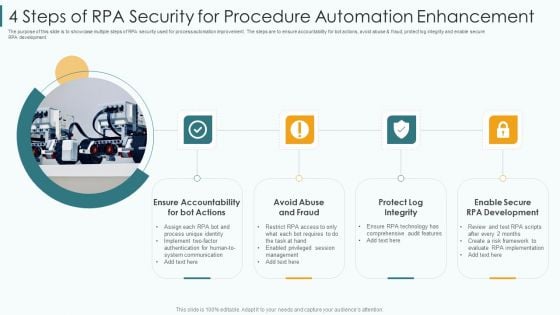
4 Steps Of RPA Security For Procedure Automation Enhancement Slides PDF
The purpose of this slide is to showcase multiple steps of RPA security used for process automation improvement. The steps are to ensure accountability for bot actions, avoid abuse and fraud, protect log integrity and enable secure RPA development. Presenting 4 steps of rpa security for procedure automation enhancement slides pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication, implement, requires. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
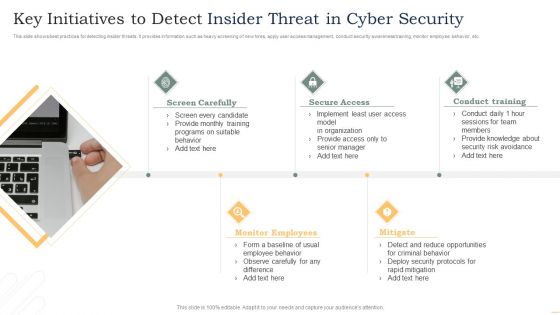
Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
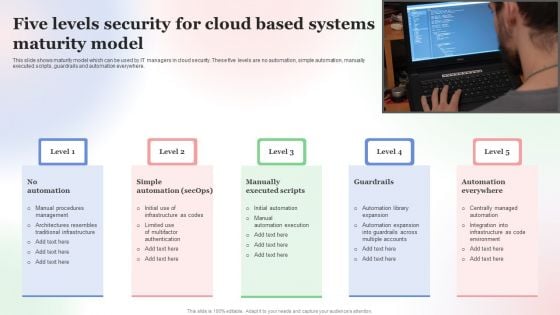
Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF
This slide shows maturity model which can be used by IT managers in cloud security. These five levels are no automation, simple automation, manually executed scripts, guardrails and automation everywhere. Presenting Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Five Levels Security, Cloud Based Systems, Maturity Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































