Safety Summary

Role Of IAP In Providing Internet Connections Demonstration Pdf
This slide presents main role of ISPs in providing internet services to individuals as well as organisations along with emails, domain registration and web hosting. It includes stronger network security, higher bandwidth, wide range of services and reliable network Pitch your topic with ease and precision using this Role Of IAP In Providing Internet Connections Demonstration Pdf. This layout presents information on Higher Bandwidth, Wide Range Of Services, Reliable Network. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents main role of ISPs in providing internet services to individuals as well as organisations along with emails, domain registration and web hosting. It includes stronger network security, higher bandwidth, wide range of services and reliable network
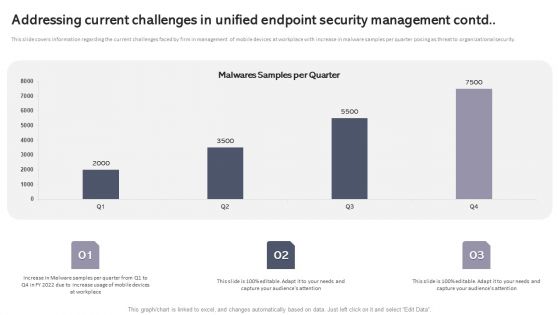
Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with increase in malware samples per quarter posing as threat to organizational security. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF.
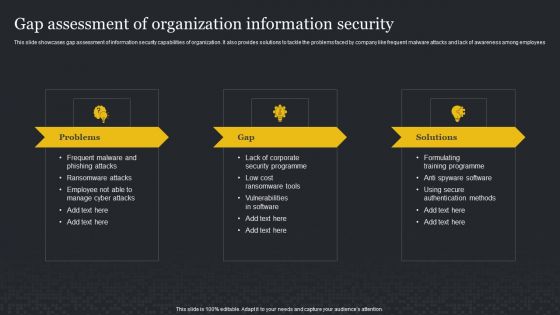
Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF.
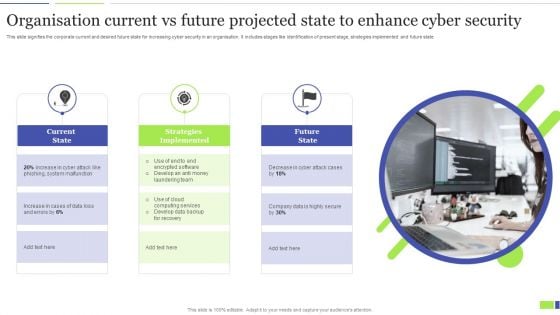
Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF
This slide signifies the corporate current and desired future state for increasing cyber security in an organisation. It includes stages like identification of present stage, strategies implemented and future state. Presenting Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Current State, Strategies Implemented, Future State. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
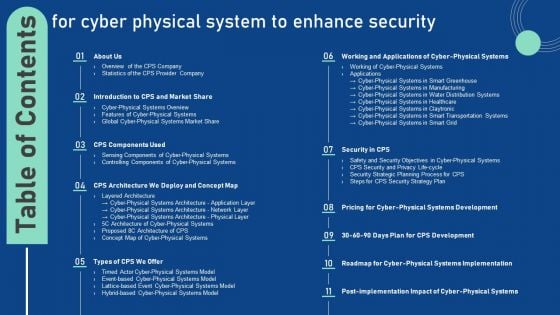
Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF.
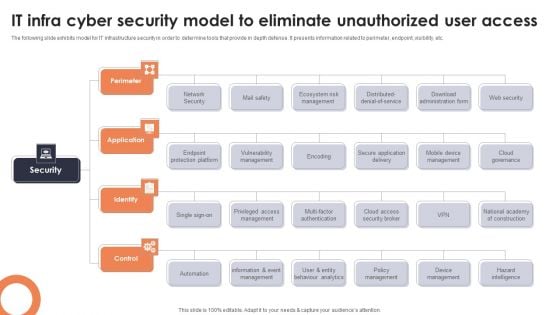
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
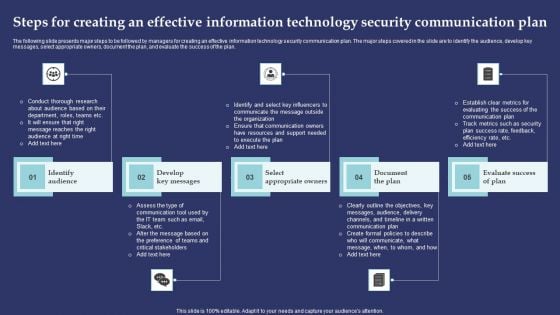
Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF
The following slide presents major steps to be followed by managers for creating an effective information technology security communication plan. The major steps covered in the slide are to identify the audience, develop key messages, select appropriate owners, document the plan, and evaluate the success of the plan. Presenting Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Audience, Develop Key Messages, Select Appropriate Owners. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.m

Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks.If you are looking for a format to display your unique thoughts, then the professionally designed Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
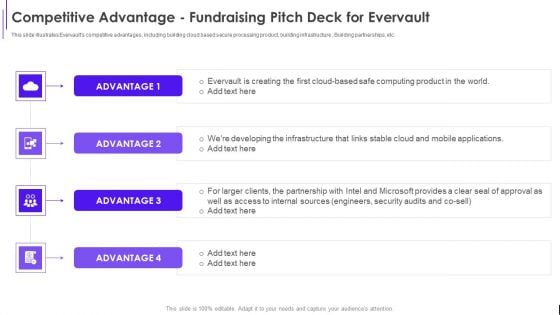
Competitive Advantage Fundraising Pitch Deck For Evervault Ppt Inspiration Background Images PDF
This slide illustrates Evervaults competitive advantages, including building cloud based secure processing product, building infrastructure , Building partnerships, etc. Presenting Competitive Advantage Fundraising Pitch Deck For Evervault Ppt Inspiration Background Images PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Evervault Creating, Cloud Based, Internal Sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
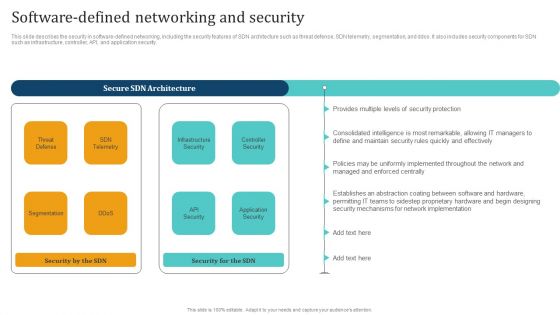
Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
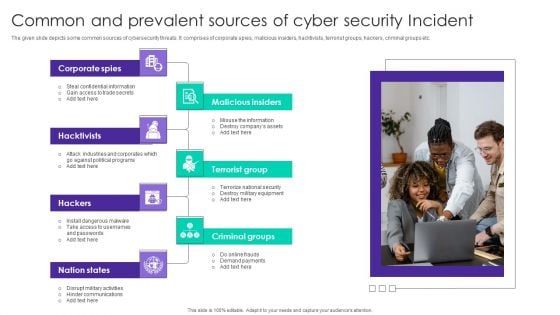
Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Requisites For Developing Website Application Standards Ideas PDF
This slide mentions the requisites for developing website application standards to build rich interactive website experience. It includes web coding standard, page loading standard, compatibility and security benchmarks. Persuade your audience using this Requisites For Developing Website Application Standards Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Compatibility, Security Benchmarks, Web Coding Standard. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Introduction To Branchless Banking In Next Generation Payments Ppt Icon Background Designs PDF
This slide covers introduction to branchless banking services offered by banking sector. The purpose of this template is to provide an overview on benefits of using branchless banking services. It includes advantages such as supporting multiple transactions, advanced payment security, contactless payment solutions along with categories covering digital wallets, IVR bill payments, API bill payments and credit card bills. Welcome to our selection of the Introduction To Branchless Banking In Next Generation Payments Ppt Icon Background Designs PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf
Do you know about Slidesgeeks Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. Our Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Non Governmental Organization Action Plan To Secure Human Rights And Dignity Mockup PDF
This slide covers the strategic plan adopted by NGO non governmental organization to secure rights and dignity for all. The purpose of this template is to depict the NGO strategic plan. It also includes details related to vision, mission, goals, etc.Persuade your audience using this Non Governmental Organization Action Plan To Secure Human Rights And Dignity Mockup PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Crowdfunding Through, Social Responsibility, Collecting Recycling. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
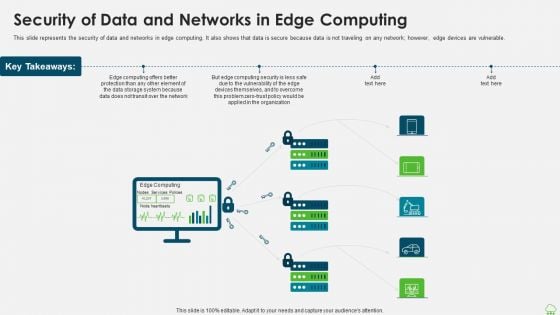
Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
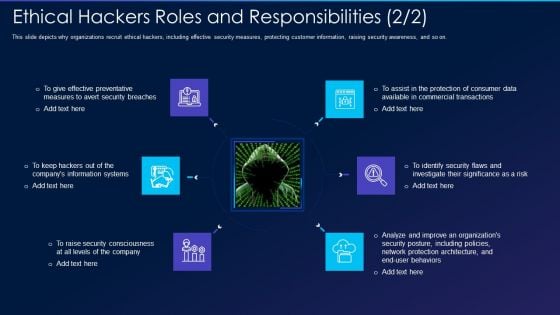
Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development quality control, and evaluation of the companys security regulatory compliance.Presenting IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems, Applications, Correcting Security, Regulatory Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Develop Corporate Cyber Security Risk Mitigation Plan Organization Mission And Vision Statement Download PDF
Presenting develop corporate cyber security risk mitigation plan organization mission and vision statement download pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like vision, mission. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Post It Notes Hacking Prevention Awareness Training For IT Security Slides PDF
Presenting post it notes hacking prevention awareness training for it security slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Mission Vision And Core Values Microsoft PDF
Presenting Security Agency Business Profile Mission Vision And Core Values Microsoft PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Mission Vision, Core Values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icon For Comparative Analysis Of Cloud And Traditional Computing It Security Rules PDF
Showcasing this set of slides titled Icon For Comparative Analysis Of Cloud And Traditional Computing It Security Rules PDF. The topics addressed in these templates are Icon Comparative Analysis Cloud, Traditional Computing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workforce Security Realization Coaching Plan Communication Plan General Format Brochure PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Presenting workforce security realization coaching plan communication plan general format brochure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, description, frequency, audience. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Management Plan Steps In Detail Identifying Goals And Objectives Clipart PDF
Presenting security management plan steps in detail identifying goals and objectives clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like implementation of security, organizational objectives, represent the business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
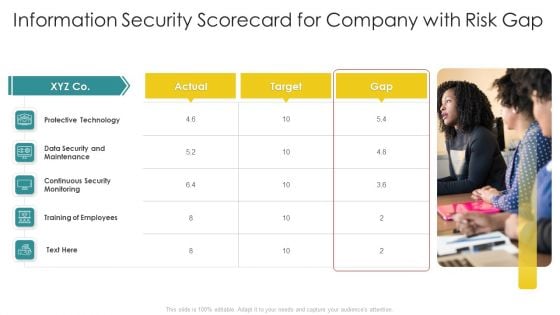
Cybersecurity Risk Scorecard Information Security Scorecard For Company With Risk Gap Professional PDF
Presenting cybersecurity risk scorecard information security scorecard for company with risk gap professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like protective technology, continuous security monitoring, training of employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
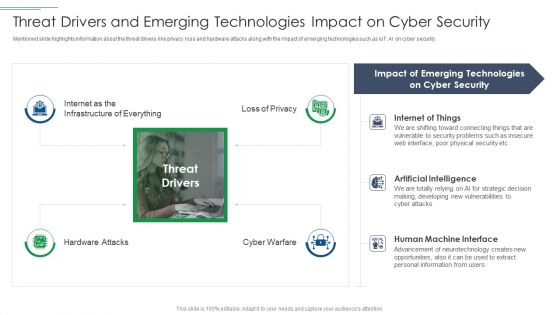
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Table Of Contents For IT Professional Data Certification Program Security Icons PDF
Presenting Table Of Contents For IT Professional Data Certification Program Security Icons PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Certified Information Systems, Security Professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Proposal For Enterprise Security System About Us One Pager Sample Example Document
Purpose of the following slide is to show the information about the origination as it displays the Company introduction, company background etc. Presenting you an exemplary Proposal For Enterprise Security System About Us One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System About Us One Pager Sample Example Document brilliant piece now.
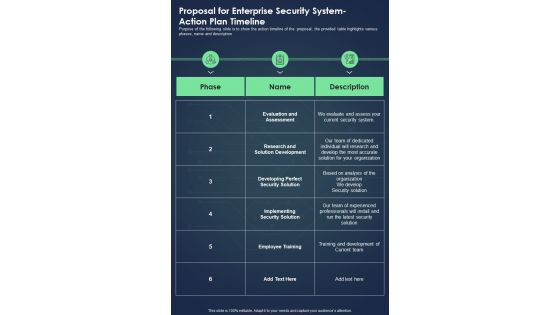
Proposal For Enterprise Security System Action Plan Timeline One Pager Sample Example Document
Purpose of the following slide is to show the action timeline of the proposal, the provided table highlights various phases, name and description Presenting you an exemplary Proposal For Enterprise Security System Action Plan Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Action Plan Timeline One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Client Testimonial One Pager Sample Example Document
The following slide displays the client testimonials that has been provided by multiple clienteles to the origination. The provided also displays the name and designation of client. Presenting you an exemplary Proposal For Enterprise Security System Client Testimonial One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Client Testimonial One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Our Management One Pager Sample Example Document
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc. Presenting you an exemplary Proposal For Enterprise Security System Our Management One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Our Management One Pager Sample Example Document brilliant piece now.

About Us For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the information about the origination as it displays the Company introduction, company background etc. Presenting you an exemplary About Us For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this About Us For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
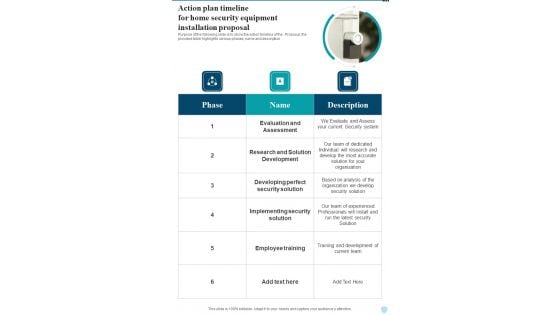
Action Plan Timeline For Home Security Equipment Installation One Pager Sample Example Document
Purpose of the following slide is to show the action timeline of the Proposal, the provided table highlights various phases, name and description. Presenting you an exemplary Action Plan Timeline For Home Security Equipment Installation One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Home Security Equipment Installation One Pager Sample Example Document brilliant piece now.

Client Testimonial For Home Security Equipment Installation One Pager Sample Example Document
The following slide displays the client testimonials that has been provided by multiple clienteles to the origination. The provided also displays the name and designation of client. Presenting you an exemplary Client Testimonial For Home Security Equipment Installation One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Client Testimonial For Home Security Equipment Installation One Pager Sample Example Document brilliant piece now.

Our Management For Home Security Equipment Installation One Pager Sample Example Document
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc. Presenting you an exemplary Our Management For Home Security Equipment Installation One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Management For Home Security Equipment Installation One Pager Sample Example Document brilliant piece now.

Our Team For Security Camera Sarvices One Pager Sample Example Document
This slide shows the project execution team with the individual members name, designation, and brief work description. Presenting you an exemplary Our Team For Security Camera Sarvices One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Team For Security Camera Sarvices One Pager Sample Example Document brilliant piece now.

IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT Ss V
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.
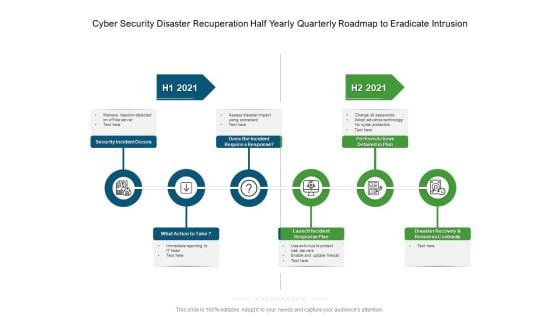
Cyber Security Disaster Recuperation Half Yearly Quarterly Roadmap To Eradicate Intrusion Graphics
Presenting our innovatively-structured cyber security disaster recuperation half yearly quarterly roadmap to eradicate intrusion graphics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
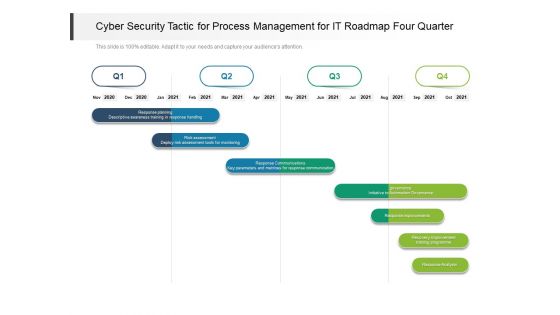
Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
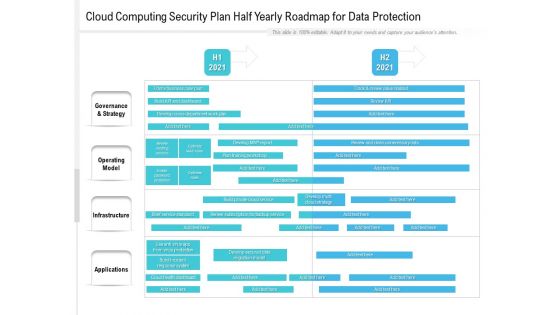
Cloud Computing Security Plan Half Yearly Roadmap For Data Protection Formats
Presenting our innovatively structured cloud computing security plan half yearly roadmap for data protection formats Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
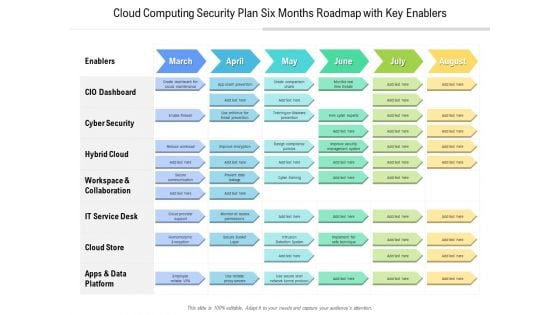
Cloud Computing Security Plan Six Months Roadmap With Key Enablers Ideas
Presenting our innovatively structured cloud computing security plan six months roadmap with key enablers ideas Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
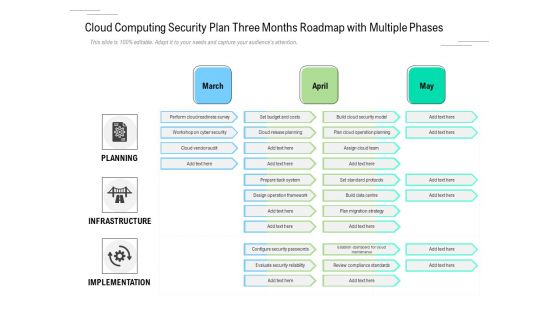
Cloud Computing Security Plan Three Months Roadmap With Multiple Phases Clipart
Presenting our innovatively structured cloud computing security plan three months roadmap with multiple phases clipart Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
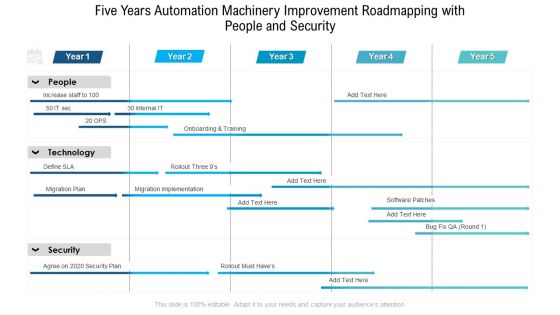
Five Years Automation Machinery Improvement Roadmapping With People And Security Download
Presenting our innovatively structured five years automation machinery improvement roadmapping with people and security download Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
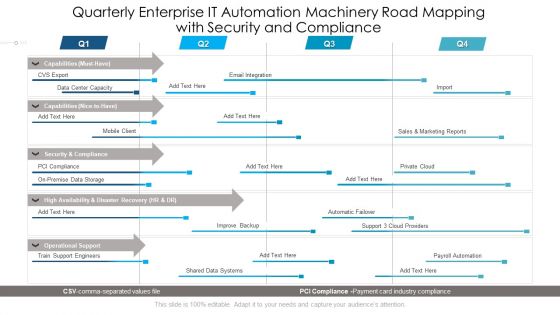
Quarterly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Diagrams
Presenting our innovatively structured quarterly enterprise it automation machinery road mapping with security and compliance diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
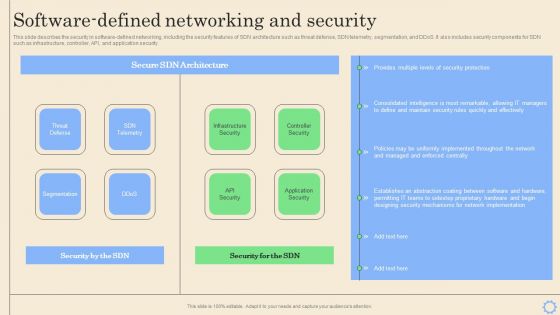
Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Want to ace your presentation in front of a live audience Our Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF
This slide depicts the career opportunities in cybersecurity, including various job roles such as chief information security officer, chief security office, security engineers, architects, analysts and penetration testers. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
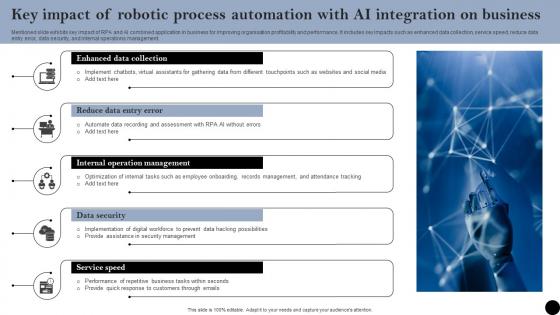
Key Impact Of Robotic Process Automation With AI Integration On Business Infographics Pdf
Mentioned slide exhibits key impact of RPA and AI combined application in business for improving organisation profitability and performance. It includes key impacts such as enhanced data collection, service speed, reduce data entry error, data security, and internal operations management. Showcasing this set of slides titled Key Impact Of Robotic Process Automation With AI Integration On Business Infographics Pdf. The topics addressed in these templates are Reduce Data Entry, Data Security, Internal Operations Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Mentioned slide exhibits key impact of RPA and AI combined application in business for improving organisation profitability and performance. It includes key impacts such as enhanced data collection, service speed, reduce data entry error, data security, and internal operations management.
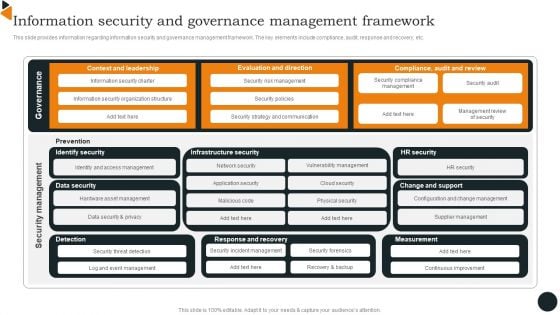
Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF
This slide showcases assessing impact on major operations and workflows. It provides information about customer understanding, knowledge, data management, financial risk management, customer relationship management, client onboarding, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF.
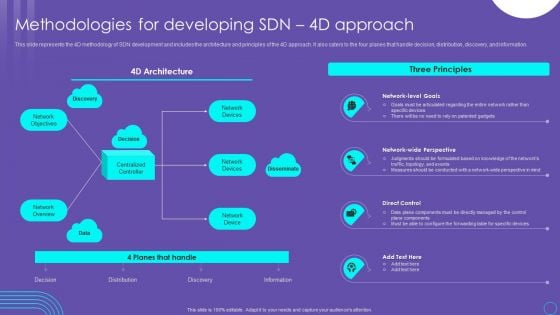
SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF
This slide represents the 4D methodology of SDN development and includes the architecture and principles of the 4D approach. It also caters to the four planes that handle decision, distribution, discovery, and information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF.
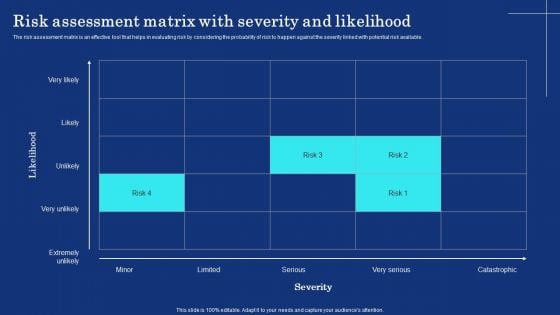
Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF.
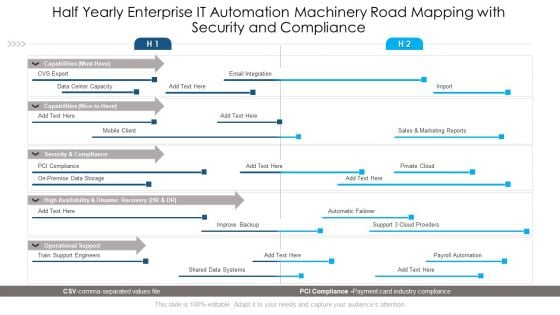
Half Yearly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Inspiration
Introducing our half yearly enterprise it automation machinery road mapping with security and compliance inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF
This This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting 6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prioritize, Evaluate, Analyse, Treat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security KPI With Measures Taken By The Company Formats PDF
This slide covers the KPIs of the company used for the security of data or privacy of the customers or businesss own confidential information. It also includes the things that is to be covered under each KPI. Some of them are NHT, days to patch, intrusion attempts ,etc. Presenting Information Technology Security KPI With Measures Taken By The Company Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Key Performance Indicators, Measures Taken, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
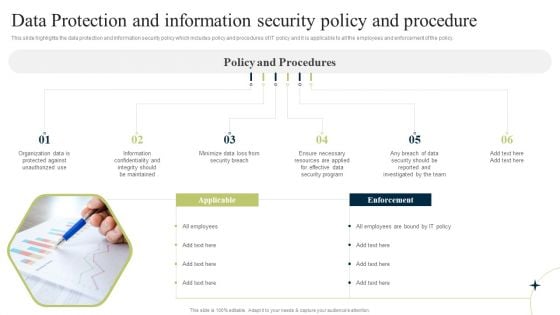
New Staff Onboarding Program Data Protection And Information Security Policy And Procedure Sample PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Want to ace your presentation in front of a live audience Our New Staff Onboarding Program Data Protection And Information Security Policy And Procedure Sample PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Checklist For Technological Smart Homes Devices And Firewall Security Microsoft PDF
This side showcase the checklist of working condition and firewall security of smart home to know updates of standard devices and their benchmarks. It includes status of devices such as garage locks, remote access, data sharing, door openers, policies of devices and update cycle. Presenting Checklist For Technological Smart Homes Devices And Firewall Security Microsoft PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Devices Firewall, Working Condition, Access Points. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
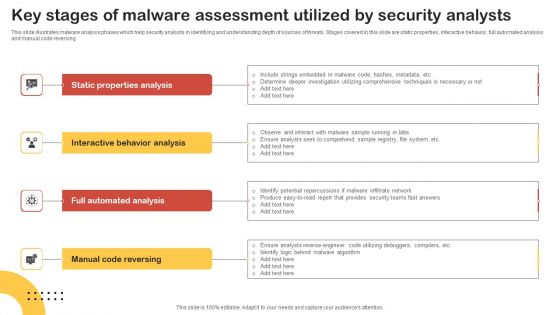
Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF
This slide illustrates malware analysis phases which help security analysts in identifying and understanding depth of sources of threats. Stages covered in this slide are static properties, interactive behavior, full automated analysis and manual code reversing. Presenting Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Static Properties Analysis, Interactive Behavior Analysis, Full Automated Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
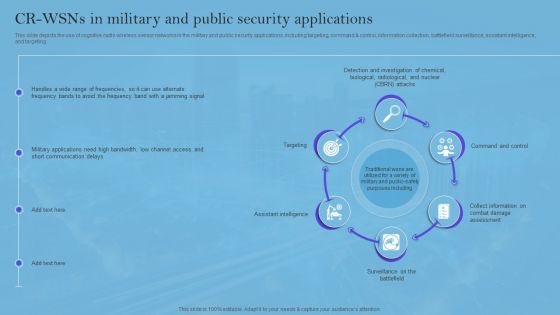
Smart Wireless Sensor Networks CR Wsns In Military And Public Security Applications Elements PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Want to ace your presentation in front of a live audience Our Smart Wireless Sensor Networks CR Wsns In Military And Public Security Applications Elements PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.


 Continue with Email
Continue with Email

 Home
Home


































