Security Architecture

Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in eighty nine slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now. Our Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
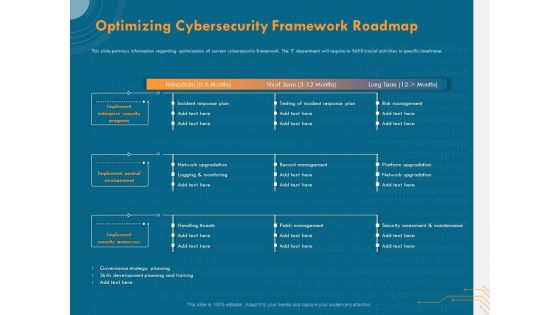
Cyber Security Implementation Framework Optimizing Cybersecurity Framework Roadmap Ppt Outline Background PDF
Presenting this set of slides with name cyber security implementation framework optimizing cybersecurity framework roadmap ppt outline background pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes, incident response plan, testing incident response plan, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Workplace Safety Protocol And Security Practices Ppt Powerpoint Presentation Complete Deck With Slides
Incorporate this Workplace Safety Protocol And Security Practices Ppt Powerpoint Presentation Complete Deck With Slides to grab your audiences attention towards your business and its cost effective services. This predesigned PPT complete deck comprises a suitable graphic to highlight your business and has sufficient space to help you present your content. The combination of colors makes it special. Grab this vibrant and professional PowerPoint template to create your business publicity material. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now. Our Workplace Safety Protocol And Security Practices Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Security Service Provider Business Model Powerpoint Ppt Template Bundles BMC V

Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V
The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory.
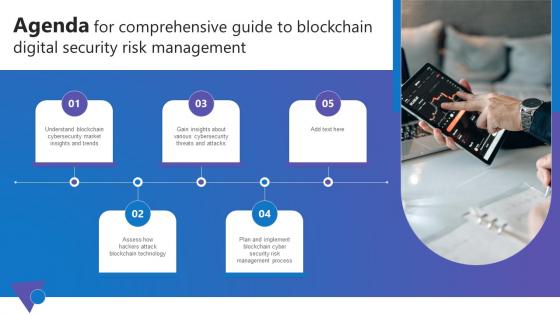
Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf
Slidegeeks has constructed Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. Our Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents Global Data Security Industry Report IR SS V
Slidegeeks has constructed Table Of Contents Global Data Security Industry Report IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Our Table Of Contents Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
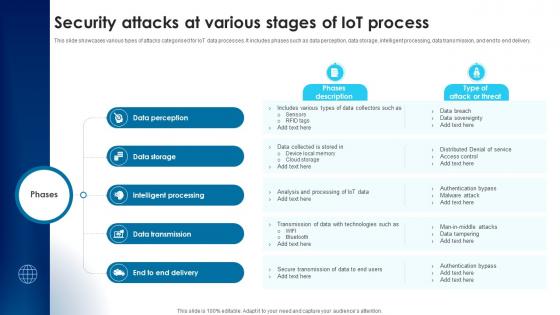
Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V
This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Create an editable Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery.
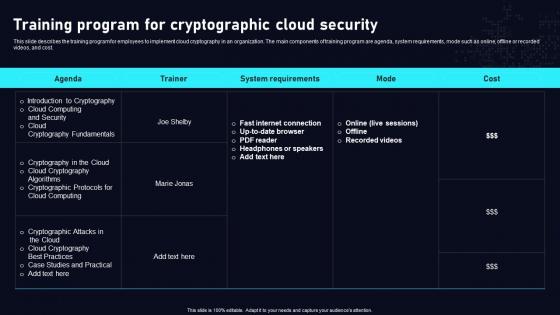
Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf
This slide showcases customer testimonials of customer which are using open source platform for virtual assistance application which is offered by business. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide showcases customer testimonials of customer which are using open source platform for virtual assistance application which is offered by business.

Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf
This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities.

Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. This Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.

Zero Trust Model Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. This modern and well-arranged Zero Trust Model Features Of Zero Trust Network Access Security Model provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides
Incorporate this Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides to make your business idea and proposal stand out. This will also ensure that your proposal,in seventeen slides of this complete deck,is well organized and professional. You can also add variables like market opportunity,value proposition,innovative solutions,and more for any business concern or issue that you might be facing. Download this design now. The 100 percent customizable nature of the template adds to the beauty of the entire concept of the off the shelf presentation concept that we have mastered. Our Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides
This incisive,comprehensive Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides details important features of running a business. One learns about things like result areas,planning and strategic framework just a glance of this comprehensive deck of eighty five slides. Use this PPT template to present your unique perspective of business technicalities and experience the way a good presentation can give new meaning to similarly placed facts. Use this template to leave a roomful of people wondering at the expert you have gathered in closing a business deal. The completely editable and customisable nature of the presentation is a unique bonus. Download now. Our Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf
The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer. This Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer.
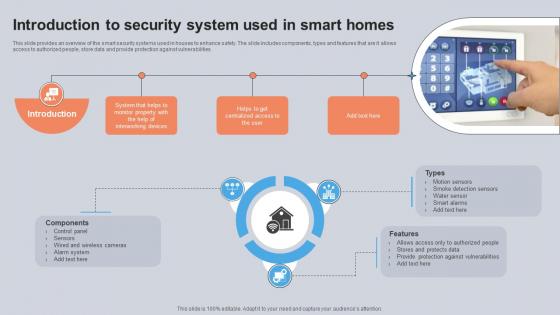
Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Create an editable Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.
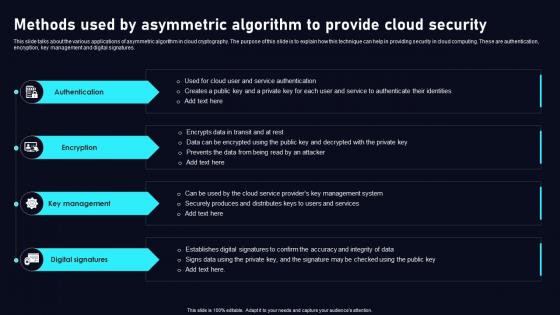
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.

Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Explore a selection of the finest Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc.
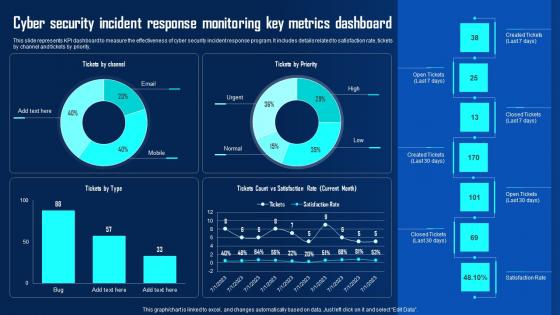
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority.

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.

Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf
This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector. Explore a selection of the finest Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector.
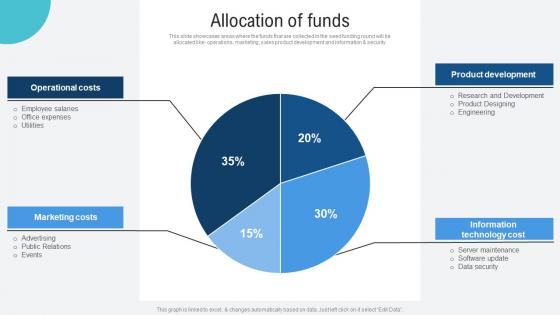
Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security. If you are looking for a format to display your unique thoughts, then the professionally designed Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security.
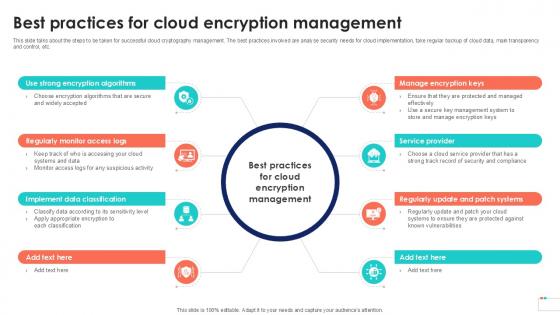
Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template today and make your presentation stand out from the rest This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.

Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Create an editable Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.

Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck
Take advantage of this well-researched and professionally-designed Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the twenty one-slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below. Our Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V
This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc. Welcome to our selection of the Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc.

Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. This Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc.
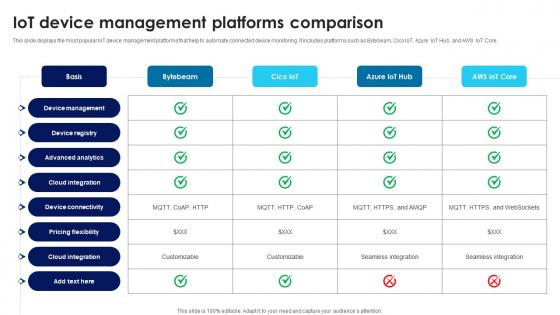
Building Trust With IoT Security IoT Device Management Platforms Comparison IoT SS V
This slide displays the most popular IoT device management platforms that help to automate connected device monitoring. It includes platforms such as Bytebeam, Cico IoT, Azure IoT Hub, and AWS IoT Core. The Building Trust With IoT Security IoT Device Management Platforms Comparison IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide displays the most popular IoT device management platforms that help to automate connected device monitoring. It includes platforms such as Bytebeam, Cico IoT, Azure IoT Hub, and AWS IoT Core.

Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V
This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access. Find a pre-designed and impeccable Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access.
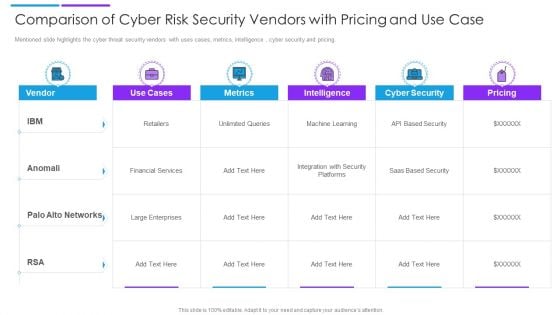
Comparison Of Cyber Risk Security Vendors With Pricing And Use Case Formats PDF
Mentioned slide highlights the cyber threat security vendors with uses cases, metrics, intelligence , cyber security and pricing. Pitch your topic with ease and precision using this comparison of cyber risk security vendors with pricing and use case formats pdf. This layout presents information on financial services, cyber security, intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
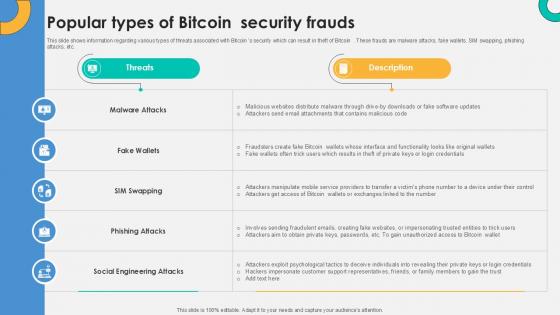
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.

Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks.

Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF
This slide outlines the strategic security framework created by an organization to overcome potential external or internal threats along with security programs. Risks include hacking and accidental data disclosure with certain protective programs like anti-spyware software and cloud security. Presenting Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Program, Threats And Risks, Protected Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
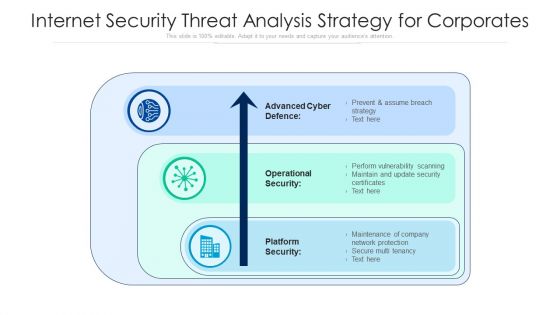
Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

30 60 90 Days Plan Of Application Security Testing Ppt Powerpoint Sample
Find a pre-designed and impeccable 30 60 90 Days Plan Of Application Security Testing Ppt Powerpoint Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our 30 60 90 Days Plan Of Application Security Testing Ppt Powerpoint Sample are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Our Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
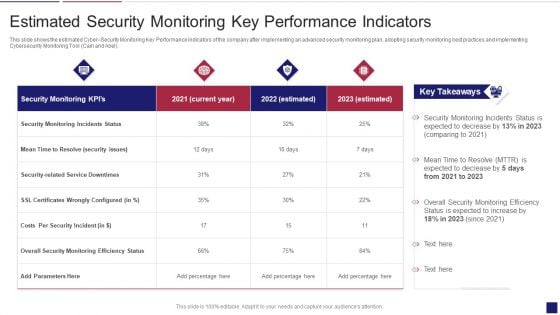
Continuous Development Evaluation Plan Eliminate Cyber Attacks Estimated Security Monitoring Designs PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks estimated security monitoring designs pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
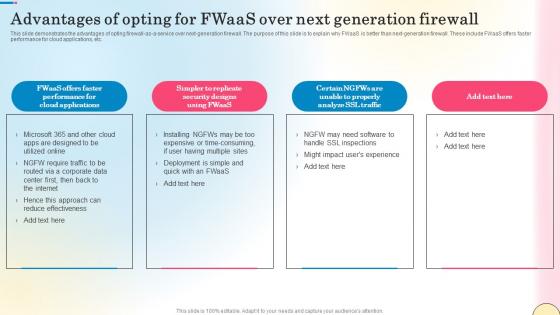
Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf
This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc. Create an editable Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc.

CASB 2 0 IT Cloud Access Security Broker And User Authentication
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Cloud Access Security Broker And User Authentication to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0.
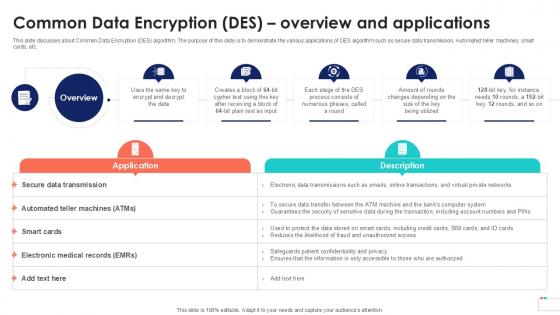
Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc.
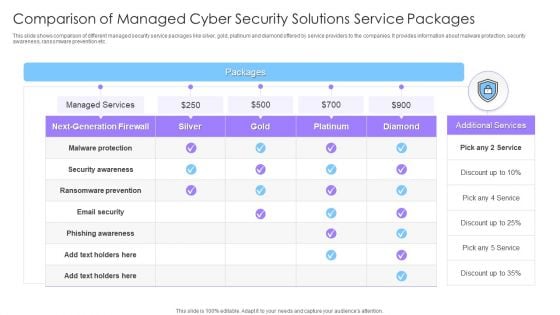
Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF
This slide shows comparison of different managed security service packages like silver, gold, platinum and diamond offered by service providers to the companies. It provides information about malware protection, security awareness, ransomware prevention etc. Pitch your topic with ease and precision using this Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF. This layout presents information on Email Security, Phishing Awareness, Security Awareness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
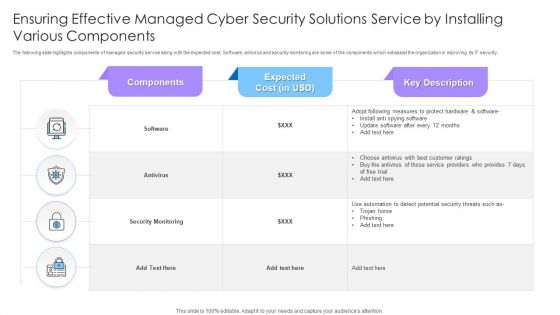
Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF
The following slide highlights components of managed security service along with the expected cost. Software, antivirus and security monitoring are some of the components which will assist the organization in improving its IT security. Showcasing this set of slides titled Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF. The topics addressed in these templates are Security Monitoring, Antivirus, Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
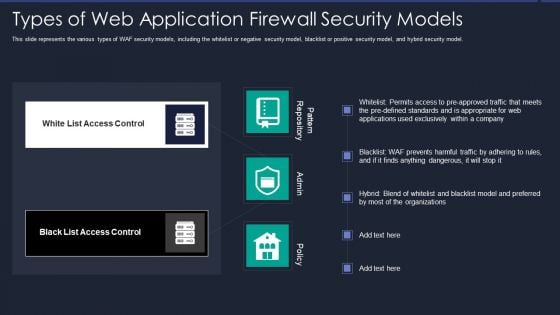
Web App Firewall Services IT Types Of Web Application Firewall Security Models Background PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting web app firewall services it types of web application firewall security models background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like applications, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V
This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc.

CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Dependable Business, Security Information, Team Members. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF
This slide represents 3 year cyber security plan road map of a company for website enhancement and implementing security to operational work with specific standards. It consists security standards, training and awareness phishing users and sensitive data management. Showcasing this set of slides titled Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF. The topics addressed in these templates are Website Enhancement, Governance Subcommittee, Security Standards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
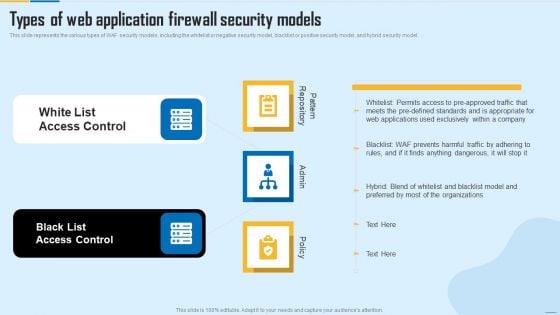
Types Of Web Application Firewall Security Models WAF Platform Themes PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting Types Of Web Application Firewall Security Models WAF Platform Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like White List Access Control, Black List Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf
Slidegeeks is here to make your presentations a breeze with Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Our Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide highlights the positive impacts from the workplace safety which showcases reduce medical compensation, zero regulatory fines, few legal repercussion and reduce indirect costs. Explore a selection of the finest Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide highlights the positive impacts from the workplace safety which showcases reduce medical compensation, zero regulatory fines, few legal repercussion and reduce indirect costs.

Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Create an editable Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc.
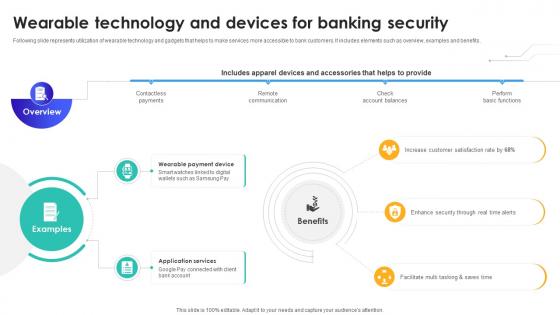
Wearable Technology And Devices For Banking Security IoT In Banking For Digital Future IoT SS V
Following slide represents utilization of wearable technology and gadgets that helps to make services more accessible to bank customers. It includes elements such as overview, examples and benefits. Create an editable Wearable Technology And Devices For Banking Security IoT In Banking For Digital Future IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Wearable Technology And Devices For Banking Security IoT In Banking For Digital Future IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Following slide represents utilization of wearable technology and gadgets that helps to make services more accessible to bank customers. It includes elements such as overview, examples and benefits.
Contact Us Voice Assistance Security Platform Investor Funding Presentation Download Pdf
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Contact Us Voice Assistance Security Platform Investor Funding Presentation Download Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Our Contact Us Voice Assistance Security Platform Investor Funding Presentation Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
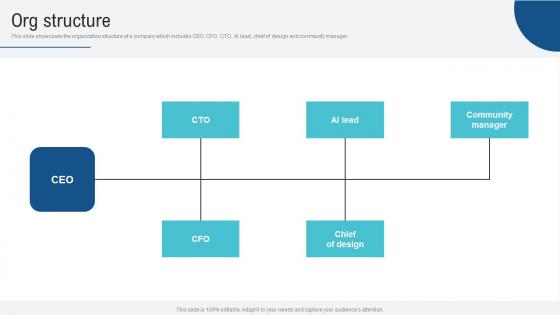
Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf
This slide showcases the organization structure of a company which includes CEO, CFO, CTO, AI lead, chief of design and community manager. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf. This slide showcases the organization structure of a company which includes CEO, CFO, CTO, AI lead, chief of design and community manager.

Table Of Contents For Global Data Security Industry Report IR SS V
Retrieve professionally designed Table Of Contents For Global Data Security Industry Report IR SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our Table Of Contents For Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V
Retrieve professionally designed SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































