Security Architecture

Table Of Contents For Data Security In Cloud Computing Ppt Slide
Slidegeeks is here to make your presentations a breeze with Table Of Contents For Data Security In Cloud Computing Ppt Slide With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Our Table Of Contents For Data Security In Cloud Computing Ppt Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
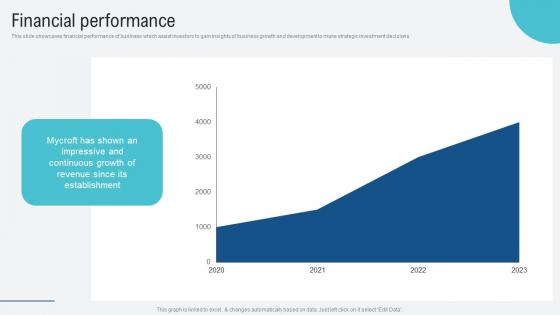
Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf
This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions. Explore a selection of the finest Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions.

Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example
This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc. This Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc.

Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Get a simple yet stunning designed Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.

Table Of Content For Data Security In Cloud Computing Ppt Slide
Present like a pro with Table Of Content For Data Security In Cloud Computing Ppt Slide. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Our Table Of Content For Data Security In Cloud Computing Ppt Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
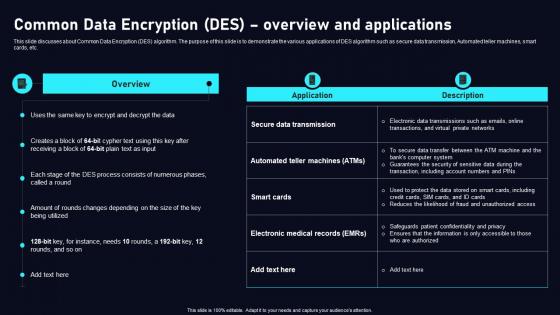
Common Data Encryption Des Cloud Data Security Using Cryptography Slides Pdf
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Welcome to our selection of the Common Data Encryption Des Cloud Data Security Using Cryptography Slides Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc.

Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V
The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding. This modern and well-arranged Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding.
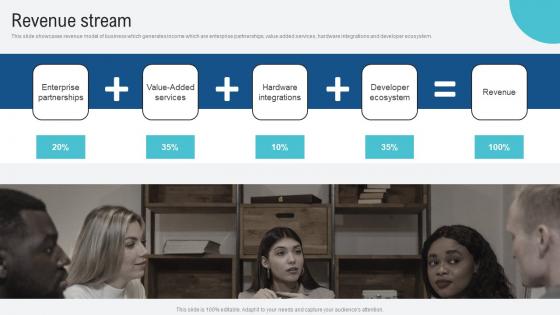
Revenue Stream Voice Assistance Security Platform Investor Funding Presentation Information Pdf
This slide showcases revenue model of business which generates income which are enterprise partnerships, value added services, hardware integrations and developer ecosystem. Find a pre designed and impeccable Revenue Stream Voice Assistance Security Platform Investor Funding Presentation Information Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases revenue model of business which generates income which are enterprise partnerships, value added services, hardware integrations and developer ecosystem.
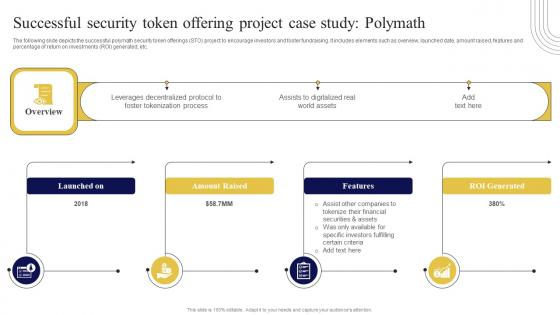
Successful Security Token Offering Project Case Exploring Investment Opportunities Summary Pdf
The following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. This Successful Security Token Offering Project Case Exploring Investment Opportunities Summary Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc.
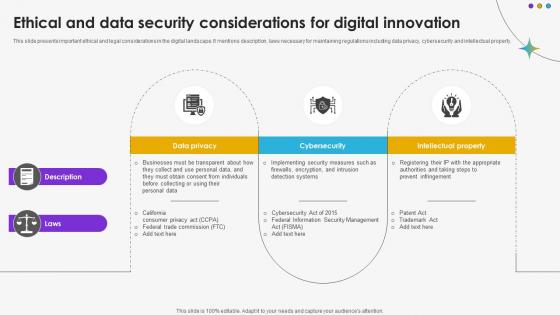
Ethical And Data Security Considerations For Digital Innovation DT SS V
This slide presents important ethical and legal considerations in the digital landscape. It mentions description, laws necessary for maintaining regulations including data privacy, cybersecurity and intellectual property.Find a pre-designed and impeccable Ethical And Data Security Considerations For Digital Innovation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents important ethical and legal considerations in the digital landscape. It mentions description, laws necessary for maintaining regulations including data privacy, cybersecurity and intellectual property.
Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf
Pitch your topic with ease and precision using this Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf This layout presents information on Futuristic Approach, Data Driven Decisions, Exposed Assets It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the comparative analysis of cybersecurity KPIs for small businesses which helps an organization to carefully choose, select the best metric to track performance. It include details such as goal oriented, actionable, easy to understand, etc.
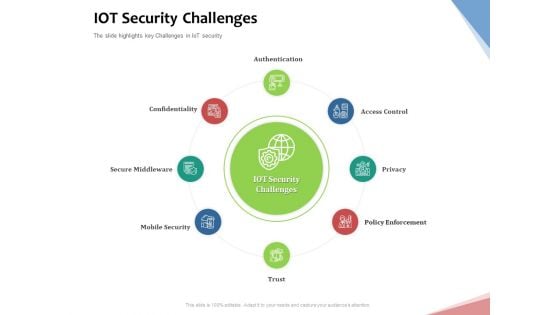
Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
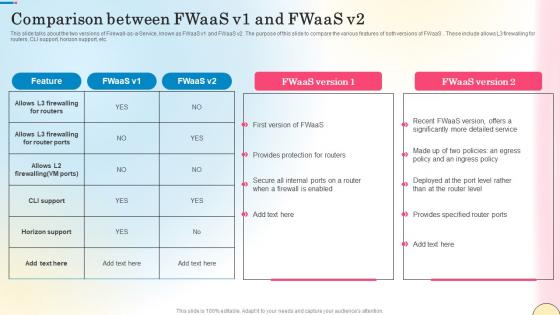
Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf
This slide talks about the two versions of Firewall-as-a-Service, known as FWaaS v1 and FWaaS v2. The purpose of this slide to compare the various features of both versions of FWaaS . These include allows L3 firewalling for routers, CLI support, horizon support, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the two versions of Firewall-as-a-Service, known as FWaaS v1 and FWaaS v2. The purpose of this slide to compare the various features of both versions of FWaaS . These include allows L3 firewalling for routers, CLI support, horizon support, etc.
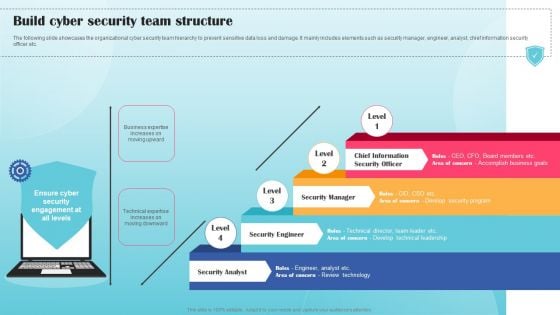
Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF
The following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
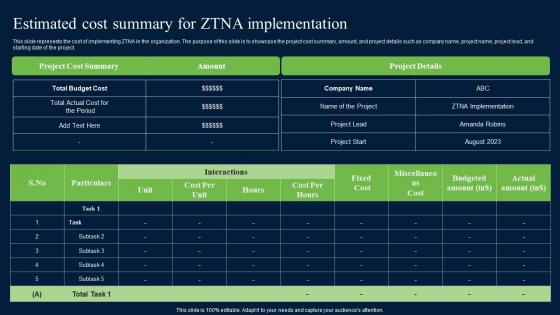
Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.
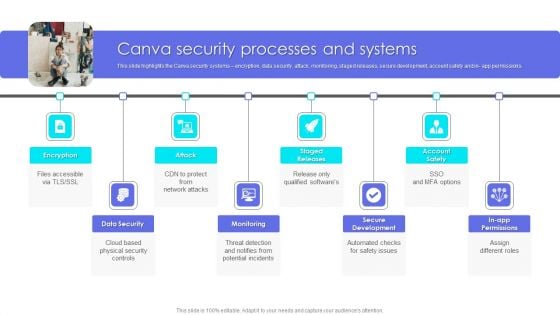
Canva Pro Business Profile Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in app permissions. Presenting Business Profile Canva Security Processes And Systems Elements PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Data Security, Monitoring, Secure Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.
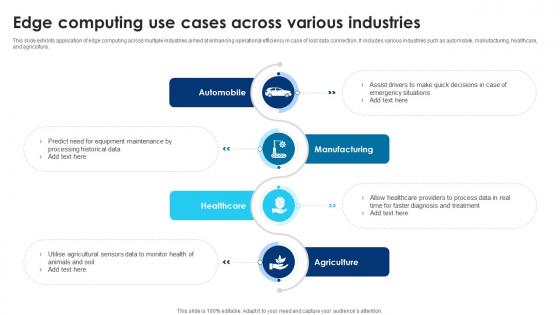
Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V
This slide exhibits application of edge computing across multiple industries aimed at enhancing operational efficiency in case of lost data connection. It includes various industries such as automobile, manufacturing, healthcare, and agriculture. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide exhibits application of edge computing across multiple industries aimed at enhancing operational efficiency in case of lost data connection. It includes various industries such as automobile, manufacturing, healthcare, and agriculture.

Network Security Using Firewall As A Service Table Of Contents Designs Pdf
This slide demonstrates the flow of traffic within a network secured with firewall. The purpose of this slide is to illustrate the meaning of good and bad traffic. This slide also highlights the factors which are used to analyze the nature of data packets. This Network Security Using Firewall As A Service Table Of Contents Designs Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the flow of traffic within a network secured with firewall. The purpose of this slide is to illustrate the meaning of good and bad traffic. This slide also highlights the factors which are used to analyze the nature of data packets.
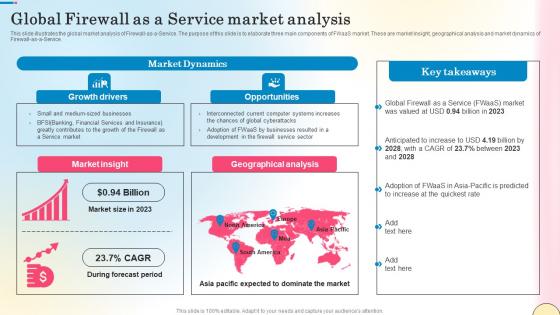
Global Firewall As A Service Market Analysis Network Security Pictures Pdf
This slide illustrates the global market analysis of Firewall-as-a-Service. The purpose of this slide is to elaborate three main components of FWaaS market. These are market insight, geographical analysis and market dynamics of Firewall-as-a-Service. This modern and well-arranged Global Firewall As A Service Market Analysis Network Security Pictures Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide illustrates the global market analysis of Firewall-as-a-Service. The purpose of this slide is to elaborate three main components of FWaaS market. These are market insight, geographical analysis and market dynamics of Firewall-as-a-Service.

Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty eight slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking. Our Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fiveteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now. Our Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
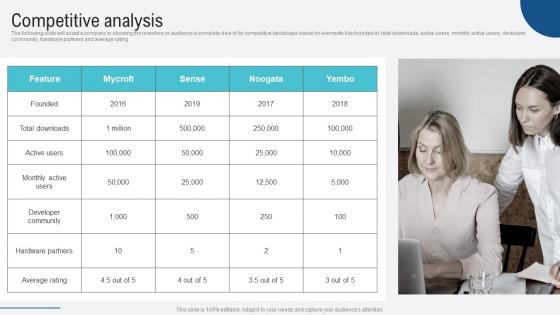
Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf
The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating.

Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising sixteen slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
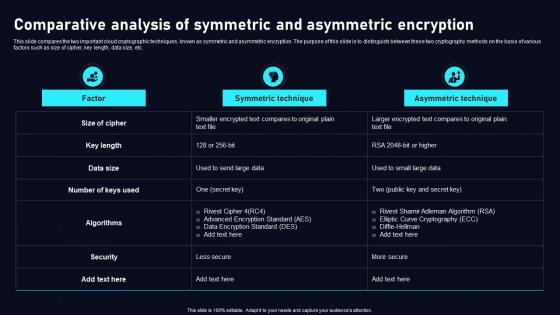
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.

Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V
The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa. Explore a selection of the finest Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa.
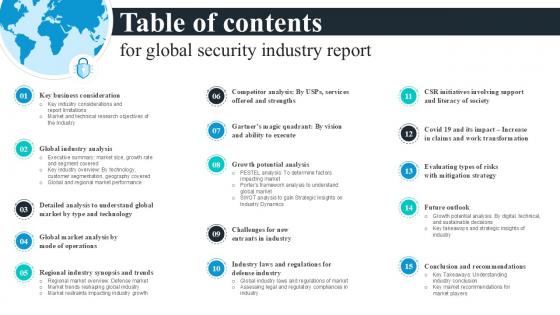
Table Of Contents For Global Security Industry Report PPT Template IR SS V
Slidegeeks has constructed Table Of Contents For Global Security Industry Report PPT Template IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Our Table Of Contents For Global Security Industry Report PPT Template IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
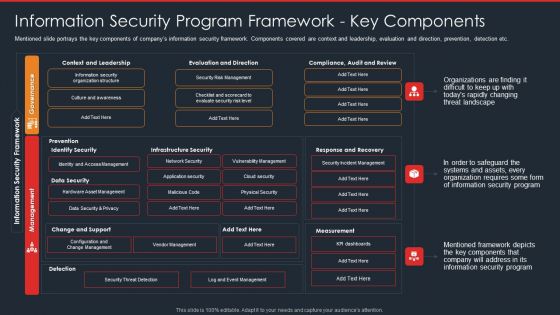
Data Safety Initiatives Information Security Program Framework Key Components Diagrams PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this data safety initiatives information security program framework key components diagrams pdf. Use them to share invaluable insights on governance, management, context and leadership, evaluation and direction, infrastructure security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
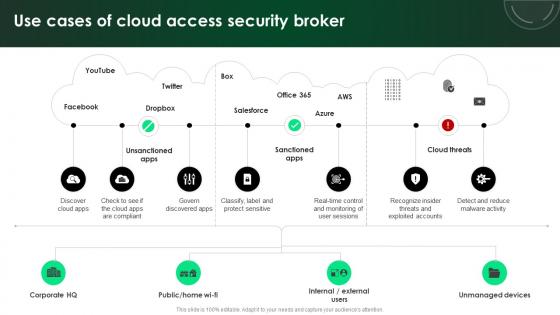
CASB 2 0 IT Use Cases Of Cloud Access Security Broker
This modern and well-arranged CASB 2 0 IT Use Cases Of Cloud Access Security Broker provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Our CASB 2 0 IT Use Cases Of Cloud Access Security Broker are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
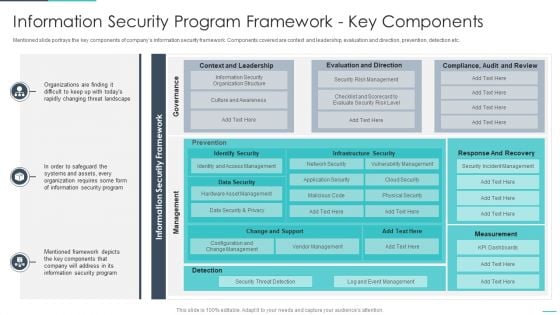
Handling Cyber Threats Digital Era Information Security Program Framework Ppt Model Summary PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era information security program framework ppt model summary pdf. Use them to share invaluable insights on information security program framework key components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
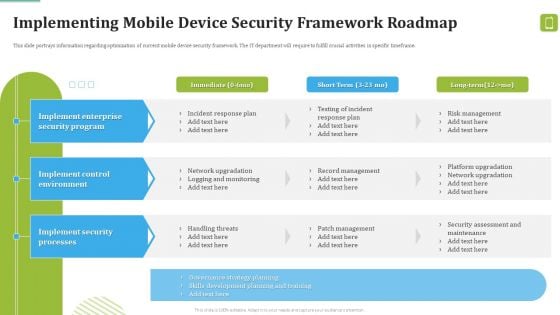
MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF bundle. Topics like Implement Enterprise, Security Program, Implement Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
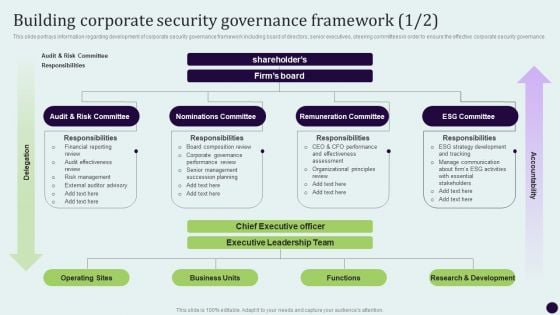
Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF
This slide portrays information regarding development of corporate security governance framework including board of directors, senior executives, steering committees in order to ensure the effective corporate security governance. Create an editable Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Various Designs Of Main Door Lock System For Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various types of smart lock systems. Major types covered are sleek fingerprint scanner, doorknob lock with a password, phone-operated smart lock, video intercom and a combination of code and fingerprint sensor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Various Designs Of Main Door Lock System For Security Utilizing Smart Appliances IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides an overview of the various types of smart lock systems. Major types covered are sleek fingerprint scanner, doorknob lock with a password, phone-operated smart lock, video intercom and a combination of code and fingerprint sensor.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
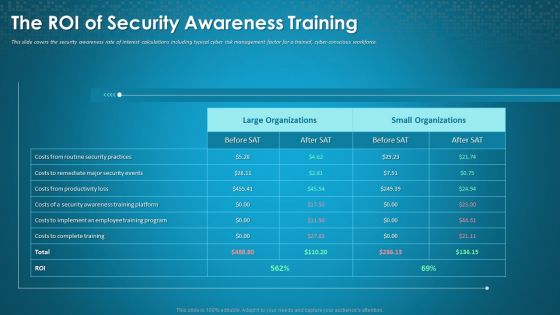
Organizational Network Staff Learning The ROI Of Security Awareness Training Designs PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this organizational network staff learning the roi of security awareness training designs pdf. Use them to share invaluable insights on employee training program, security awareness training platform, productivity loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Intelligence Framework For Application Consumption Growing Cyber Security Issues Ppt File Shapes PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident. Presenting cloud intelligence framework for application consumption growing cyber security issues ppt file shapes pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like mobile devices, security plans, organizations, cloud technologies, loss or theft of equipment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF. Use them to share invaluable insights on Security And Compliance, SAML Authentication, Data Subject Requests and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. This Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges.
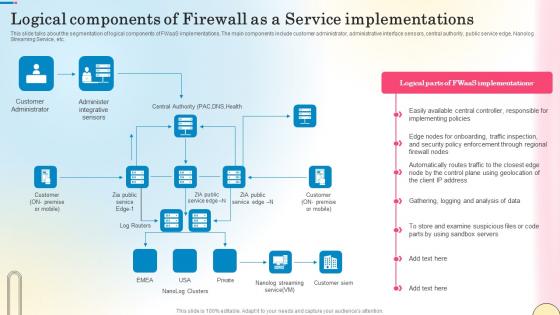
Logical Components Of Firewall As A Service Network Security Designs Pdf
This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Logical Components Of Firewall As A Service Network Security Designs Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Logical Components Of Firewall As A Service Network Security Designs Pdf. This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc.

Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Designs PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it information security process to manage firms sensitive data designs pdf. Use them to share invaluable insights on privileged password management, daily tasks performed by network administrator, network security audit checklist and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
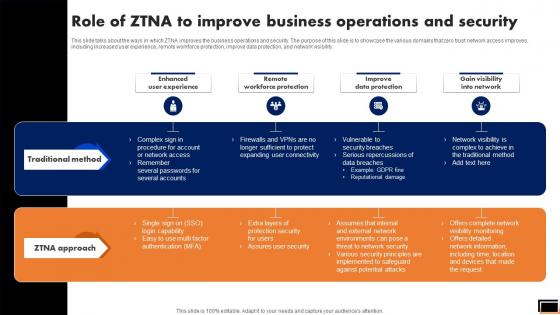
Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
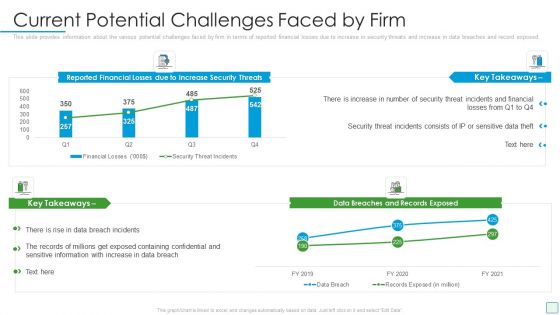
Developing Firm Security Strategy Plan Current Potential Challenges Faced By Firm Designs PDF
This slide provides information about the various potential challenges faced by firm in terms of reported financial losses due to increase in security threats and increase in data breaches and record exposed. Deliver an awe inspiring pitch with this creative developing firm security strategy plan current potential challenges faced by firm designs pdf bundle. Topics like security, financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Managing Electronic Information Security 30 Days Plan Ppt Layouts Design Ideas PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this cybersecurity managing electronic information security 30 days plan ppt layouts design ideas pdf. Use them to share invaluable insights on measured, metric, awareness, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
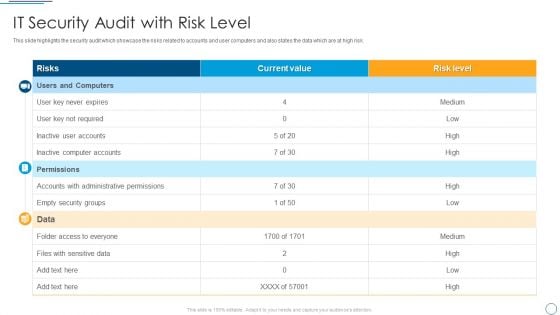
Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk.Deliver an awe inspiring pitch with this creative Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF bundle. Topics like Administrative Permissions, Empty Security, Computer Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda IT Security Automation Tools Integration Ppt Summary Design Templates PDF
This is a Agenda IT Security Automation Tools Integration Ppt Summary Design Templates PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IT Environment, Security Processes, Security Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V
This slide provides an overview of the cloud computing platform used to streamline industrial working. The slide further includes consideration factors and benefits that are scalability, flexibility, connectivity and data storage. This Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides an overview of the cloud computing platform used to streamline industrial working. The slide further includes consideration factors and benefits that are scalability, flexibility, connectivity and data storage.
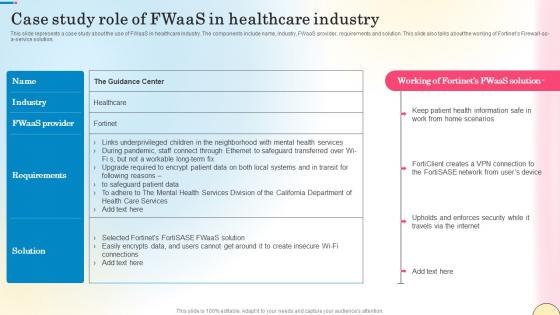
Case Study Role Of Fwaas In Healthcare Industry Network Security Slides Pdf
This slide represents a case study about the use of FWaaS in healthcare industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the working of Fortinets Firewall-as-a-service solution. Slidegeeks is here to make your presentations a breeze with Case Study Role Of Fwaas In Healthcare Industry Network Security Slides Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents a case study about the use of FWaaS in healthcare industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the working of Fortinets Firewall-as-a-service solution.
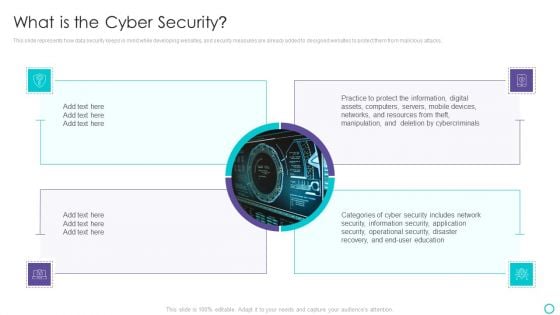
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc. Create an editable Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc.
CCTV For Home Security Vector Icon Ppt PowerPoint Presentation Pictures Example PDF
Presenting this set of slides with name cctv for home security vector icon ppt powerpoint presentation pictures example pdf. The topics discussed in these slide is cctv for home security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Iot Security Smart Home Vector Icon Ppt PowerPoint Presentation Diagram Templates PDF
Presenting iot security smart home vector icon ppt powerpoint presentation diagram templates pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including iot security smart home vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
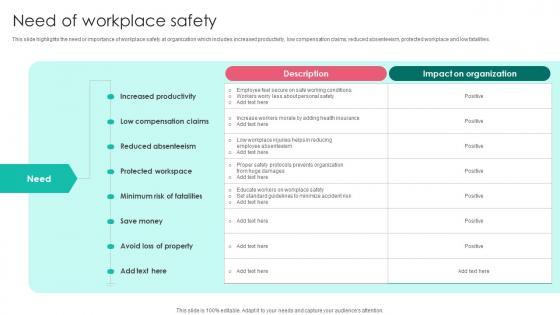
Need Of Workplace Safety Workplace Safety Protocol And Security Practices Template Pdf
This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities. Retrieve professionally designed Need Of Workplace Safety Workplace Safety Protocol And Security Practices Template Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities.

Security Camera System Company Profile Executive Leadership And Management Team Designs PDF
This slide highlights the security company leadership and management team which includes president CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Security Camera System Company Profile Executive Leadership And Management Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Security, Southern University, Management Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
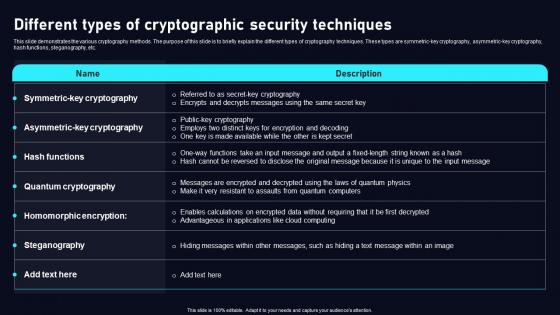
Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf
This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc. Slidegeeks has constructed Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc.
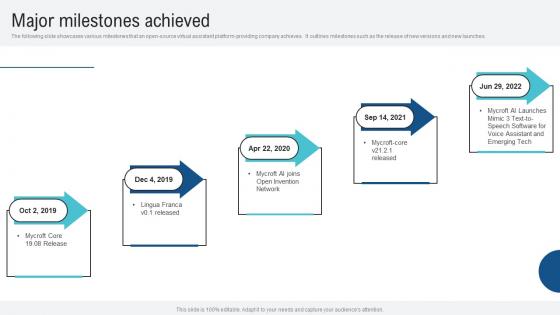
Major Milestones Achieved Voice Assistance Security Platform Investor Funding Presentation Slides Pdf
The following slide showcases various milestones that an open source virtual assistant platform providing company achieves. It outlines milestones such as the release of new versions and new launches. Slidegeeks has constructed Major Milestones Achieved Voice Assistance Security Platform Investor Funding Presentation Slides Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. The following slide showcases various milestones that an open source virtual assistant platform providing company achieves. It outlines milestones such as the release of new versions and new launches.

Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Get a simple yet stunning designed Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.


 Continue with Email
Continue with Email

 Home
Home


































