Security Architecture
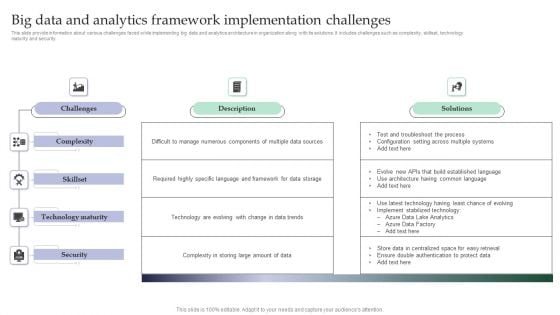
Big Data And Analytics Framework Implementation Challenges Themes PDF
This slide provide information about various challenges faced while implementing big data and analytics architecture in organization along with its solutions. It includes challenges such as complexity, skillset, technology maturity and security Pitch your topic with ease and precision using this Big Data And Analytics Framework Implementation Challenges Themes PDF. This layout presents information on Challenges, Description, Solutions . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Website Audit To Increase Conversion Rate Different Areas Of Website SEO Audit Demonstration PDF
This slide highlights the areas of website audit which includes security audit, performance audit, code audit, website theme audit, UX or UI audit and website architecture audit. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Website Audit To Increase Conversion Rate Different Areas Of Website SEO Audit Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
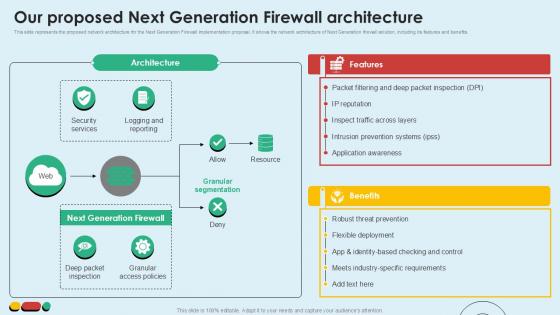
Our Proposed Next Generation Intelligent Intrusion Prevention System Ppt Presentation
This slide represents the proposed network architecture for the Next Generation Firewall implementation proposal. It shows the network architecture of Next Generation firewall solution, including its features and benefits.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Our Proposed Next Generation Intelligent Intrusion Prevention System Ppt Presentation. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Our Proposed Next Generation Intelligent Intrusion Prevention System Ppt Presentation today and make your presentation stand out from the rest This slide represents the proposed network architecture for the Next Generation Firewall implementation proposal. It shows the network architecture of Next Generation firewall solution, including its features and benefits.
Business Objects Model Powerpoint Ideas

Critical Success Factors Powerpoint Presentation Examples
This is a critical success factors powerpoint presentation examples. This is a four stage process. The stages in this process are critical success factors, network architecture plan, business objects model, business activity modelling.
Hypervisor Based Replication Technology Comparative Assessment Matrix Icons PDF
The purpose of this slide is to compare the various technologies to be used for data protection. The comparison of technologies are categorized into two groupings such as architecture and replication. Showcasing this set of slides titled Hypervisor Based Replication Technology Comparative Assessment Matrix Icons PDF. The topics addressed in these templates are Architecture, Replication, Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Top To Down Approach For Business Information Protection Demonstration PDF
This slide covers top to down approach for business security which includes security leadership, program, policies and management. Further, it includes user management and information asset security.Pitch your topic with ease and precision using this Top To Down Approach For Business Information Protection Demonstration PDF. This layout presents information on Security Leadership, Security Program, Security Policies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
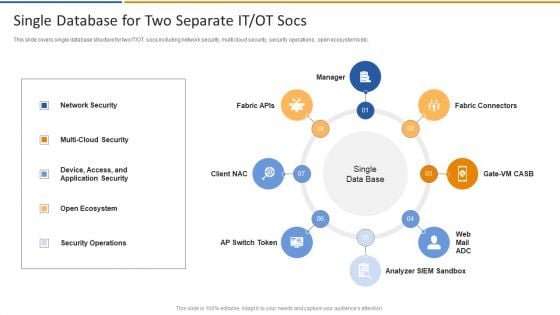
Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Network Security, Multi Cloud Security, Device Access, Application Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
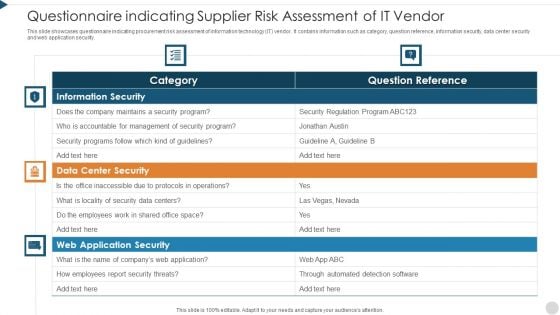
Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API.
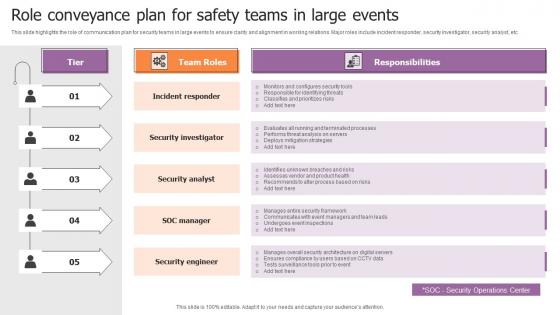
Role Conveyance Plan For Safety Teams In Large Events Ideas Pdf
This slide highlights the role of communication plan for security teams in large events to ensure clarity and alignment in working relations. Major roles include incident responder, security investigator, security analyst, etc. Showcasing this set of slides titled Role Conveyance Plan For Safety Teams In Large Events Ideas Pdf. The topics addressed in these templates are Incident Responder, Security Investigator, Security Analyst. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the role of communication plan for security teams in large events to ensure clarity and alignment in working relations. Major roles include incident responder, security investigator, security analyst, etc.

Stock Photo Blue Umbrella Over Usa Flag Print Text PowerPoint Slide
This Power Point slide has been designed with graphic of blue umbrella and US flag design. This image slide contains the concept of USA security and protection schemes. Use this professional design to build presentation for security related topics.
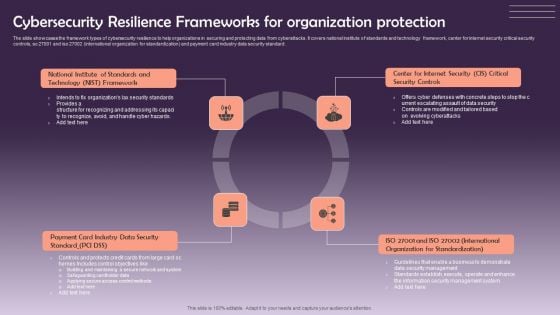
Cybersecurity Resilience Frameworks For Organization Protection Information PDF
The slide showcases the framework types of cybersecurity resilience to help organizations in securing and protecting data from cyberattacks. It covers national institute of standards and technology framework, center for internet security critical security controls, so 27001 and iso 27002 international organization for standardization and payment card industry data security standard. Presenting Cybersecurity Resilience Frameworks For Organization Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Security, Organization For Standardization, Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
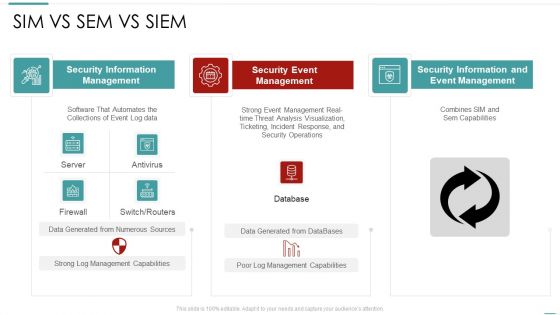
Risk Recognition Automation Sim Vs Sem Vs Siem Ppt Professional Background Designs PDF
Deliver and pitch your topic in the best possible manner with this risk recognition automation sim vs sem vs siem ppt professional background designs pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Ecommerce Payment Gateway System Evaluation And Deployment Of Enhanced Portrait Pdf
This slide represents the architecture showing the ways in which payment gateway validates consumers card details securely and ensures availability of funds and eventually enables merchants to get paid. Find highly impressive Ecommerce Payment Gateway System Evaluation And Deployment Of Enhanced Portrait Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Ecommerce Payment Gateway System Evaluation And Deployment Of Enhanced Portrait Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide represents the architecture showing the ways in which payment gateway validates consumers card details securely and ensures availability of funds and eventually enables merchants to get paid.

Business Information Application Protection Testing Flow Chart Themes PDF
This slide covers business application security testing flow chart which includes secure application model, security standard recognition and privacy testing.Pitch your topic with ease and precision using this Business Information Application Protection Testing Flow Chart Themes PDF. This layout presents information on Security Consistency, Target Weighting, Target Recognition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
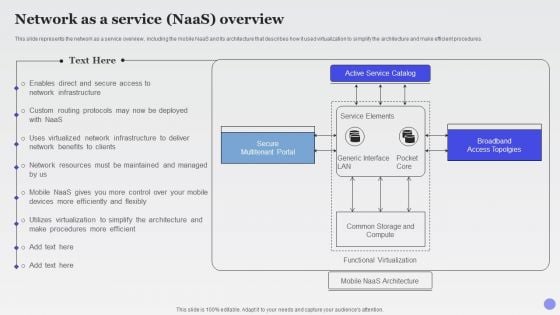
Network As A Service Naas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Show Example PDF
This slide represents the network as a service overview, including the mobile NaaS and its architecture that describes how it used virtualization to simplify the architecture and make efficient procedures.Deliver an awe inspiring pitch with this creative Network As A Service Naas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Show Example PDF bundle. Topics like Broadband Access, Multitenant Portal, Service Catalog can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
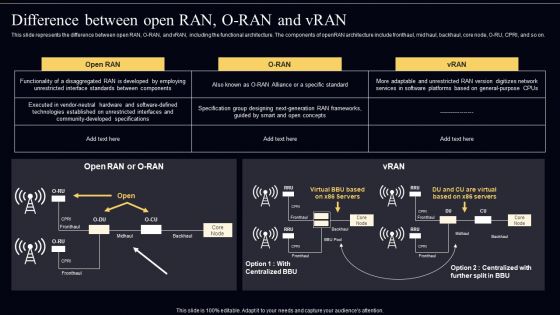
Open Radio Access Network IT Difference Between Open RAN O RAN And Vran Topics PDF
This slide represents the difference between open RAN, O RAN, and vRAN, including the functional architecture. The components of openRAN architecture include fronthaul, mid haul, backhaul, core node, O-RU, CPRI, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Open Radio Access Network IT Difference Between Open RAN O RAN And Vran Topics PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
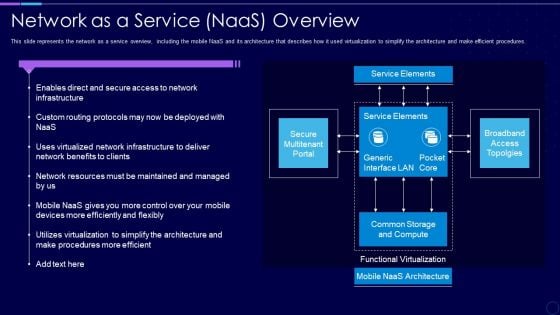
Everything As A Service Xaas For Cloud Computing IT Network As A Service Naas Overview Introduction PDF
This slide represents the network as a service overview, including the mobile NaaS and its architecture that describes how it used virtualization to simplify the architecture and make efficient procedures. Deliver an awe inspiring pitch with this creative everything as a service xaas for cloud computing it network as a service naas overview introduction pdf bundle. Topics like network as a service naas overview can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
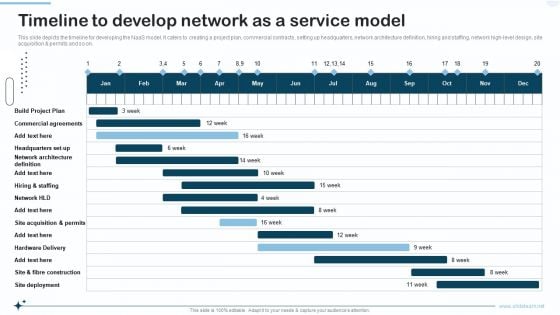
Naas Integrated Solution IT Timeline To Develop Network As A Service Model Pictures PDF
This slide depicts the timeline for developing the NaaS model. It caters to creating a project plan, commercial contracts, setting up headquarters, network architecture definition, hiring and staffing, network high level design, site acquisition and permits and so on. Deliver and pitch your topic in the best possible manner with this Naas Integrated Solution IT Timeline To Develop Network As A Service Model Pictures PDF. Use them to share invaluable insights on Network Architecture Definition, Commercial Agreements, Build Project Plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Conveyance Plan For Safety Touchpoints In Large Events Icons Pdf
This slide consists of a communication plan for security touchpoints in large events which need to be addressed by security teams to ensure the seamless movement of attendees. Major security touchpoints are outside venue, entrances, interior areas and admission events. Pitch your topic with ease and precision using this Conveyance Plan For Safety Touchpoints In Large Events Icons Pdf. This layout presents information on Outside Venue, Entrances, Interior Areas. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide consists of a communication plan for security touchpoints in large events which need to be addressed by security teams to ensure the seamless movement of attendees. Major security touchpoints are outside venue, entrances, interior areas and admission events.
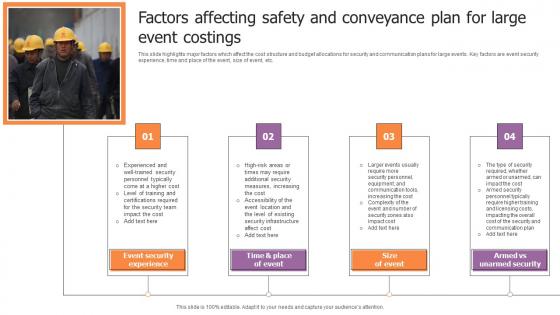
Factors Affecting Safety And Conveyance Plan For Large Event Costings Pictures Pdf
This slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc. Pitch your topic with ease and precision using this Factors Affecting Safety And Conveyance Plan For Large Event Costings Pictures Pdf. This layout presents information on Event Security Experience, Size Of Event, Armed Vs Unarmed Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc.
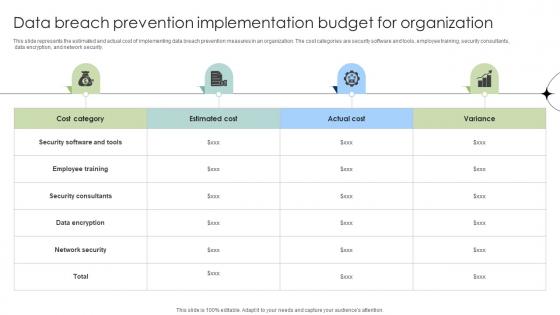
Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.

Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint
This slide represents the major challenges of security testing with solutions such as dynamic threat landscape, false positives in security testing, limitation of security testing efficiency, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint This slide represents the major challenges of security testing with solutions such as dynamic threat landscape, false positives in security testing, limitation of security testing efficiency, etc.
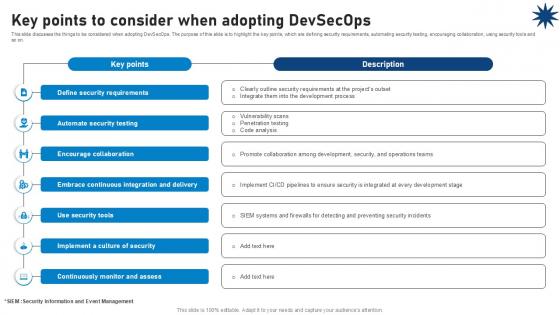
Key Points To Consider When Adopting Devsecops Role Of Devsecops Ppt Sample
This slide discusses the things to be considered when adopting DevSecOps. The purpose of this slide is to highlight the key points, which are defining security requirements, automating security testing, encouraging collaboration, using security tools and so on. Find a pre-designed and impeccable Key Points To Consider When Adopting Devsecops Role Of Devsecops Ppt Sample The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the things to be considered when adopting DevSecOps. The purpose of this slide is to highlight the key points, which are defining security requirements, automating security testing, encouraging collaboration, using security tools and so on.
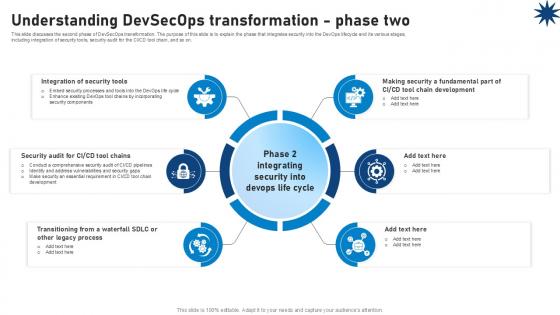
Understanding Devsecops Transformation Phase Two Role Of Devsecops Ppt Powerpoint
This slide discusses the second phase of DevSecOps transformation. The purpose of this slide is to explain the phase that integrates security into the DevOps lifecycle and its various stages, including integration of security tools, security audit for the CICD tool chain, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Understanding Devsecops Transformation Phase Two Role Of Devsecops Ppt Powerpoint and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the second phase of DevSecOps transformation. The purpose of this slide is to explain the phase that integrates security into the DevOps lifecycle and its various stages, including integration of security tools, security audit for the CICD tool chain, and so on.
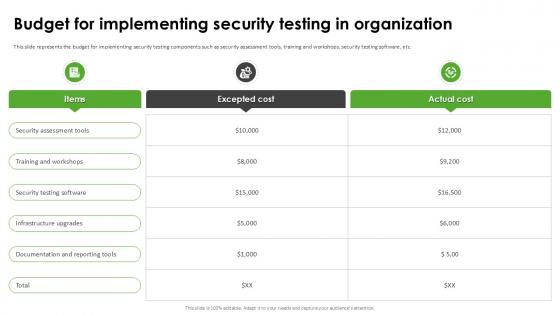
Budget For Implementing Harnessing The World Of Ethical Ppt Presentation
This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc. Get a simple yet stunning designed Budget For Implementing Harnessing The World Of Ethical Ppt Presentation It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget For Implementing Harnessing The World Of Ethical Ppt Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc.
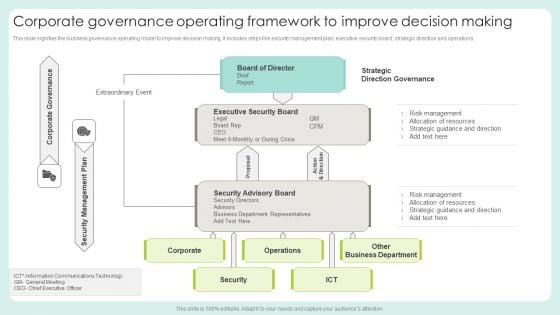
Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
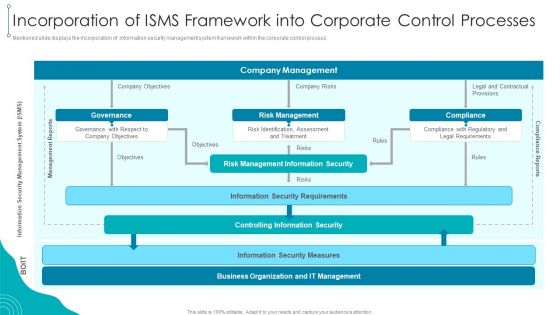
Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF. Use them to share invaluable insights on Management Information, Security Requirements, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
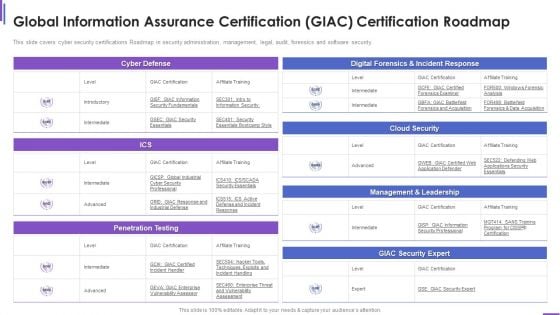
Collection Of Information Technology Certifications Global Information Assurance Designs PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this collection of information technology certifications global information assurance designs pdf. Use them to share invaluable insights on global information assurance certification giac certification roadmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
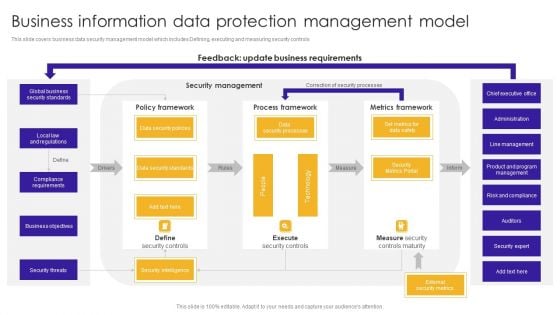
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
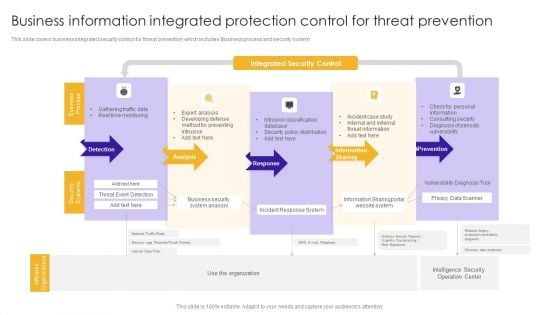
Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
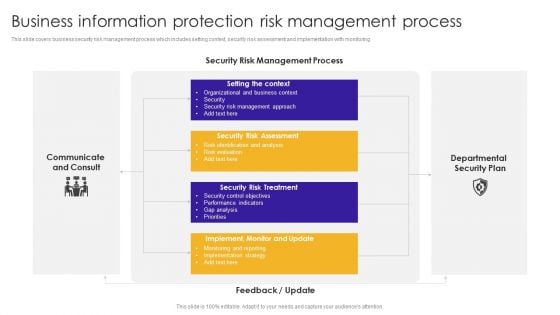
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
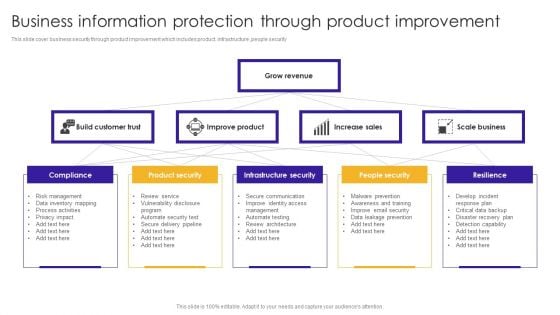
Business Information Protection Through Product Improvement Infographics PDF
This slide cover business security through product improvement which includes product, infrastructure ,people security. Pitch your topic with ease and precision using this Business Information Protection Through Product Improvement Infographics PDF. This layout presents information on Improve Product, Scale Business, Infrastructure Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
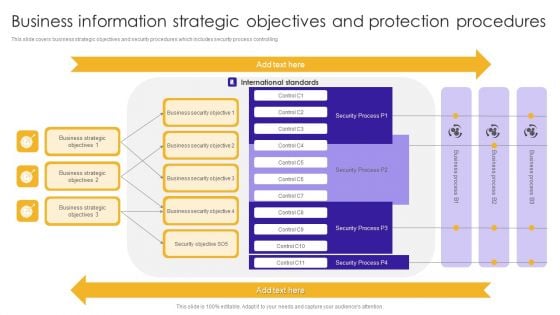
Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
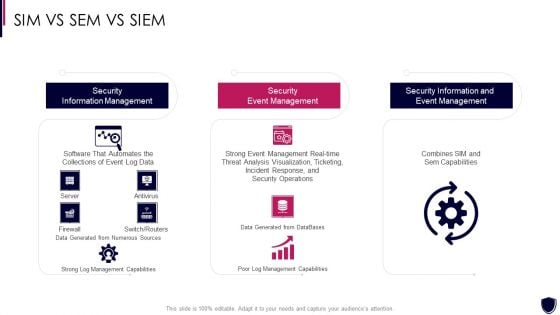
Enhancing Cyber Safety With Vulnerability Administration SIM Vs SEM Vs SIEM Brochure PDF
Presenting enhancing cyber safety with vulnerability administration sim vs sem vs siem brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF
This slide covers annual awareness training program schedule for employees. It includes training for network security, cyber security fundamentals, insider threats, malicious code, etc.Showcasing this set of slides titled Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF. The topics addressed in these templates are Insider Threats, Network Security, Risk Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF
This slide covers various courses for employees to aware about IT security threats. It includes identification of compliance stands, audit standards, incident trends, organisations security awareness, etc.Showcasing this set of slides titled Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF. The topics addressed in these templates are Compliance Standards, Identify Audit Standards, Security Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
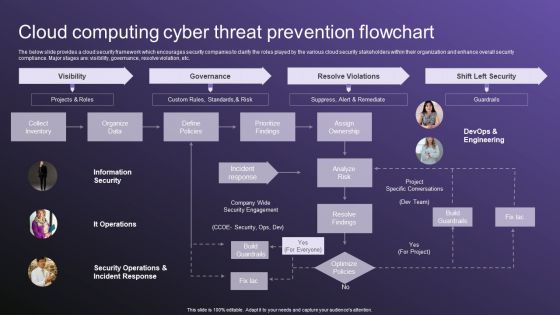
Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Effective IT Risk Management Process Roles And Responsibilities For Managing Elements PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a effective it risk management process roles and responsibilities for managing elements pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, development, security, organizational, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF
The following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assessment Methodology, Risk QuestionsCyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phishing Attacks Awareness Training Program Plan Inspiration PDF
This slide covers phishing awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public Wi-Fi, removable media, mobile device security and passwords and authentication. Persuade your audience using this Phishing Attacks Awareness Training Program Plan Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Security, Mobile Device Security, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
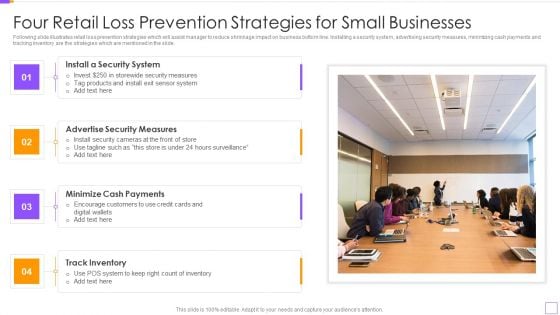
Four Retail Loss Prevention Strategies For Small Businesses Themes PDF
Following slide illustrates retail loss prevention strategies which will assist manager to reduce shrinkage impact on business bottom line. Installing a security system, advertising security measures, minimizing cash payments and tracking inventory are the strategies which are mentioned in the slide. Persuade your audience using this Four Retail Loss Prevention Strategies For Small Businesses Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Install A Security System, Advertise Security Measures, Minimize Cash Payments, Track Inventory. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
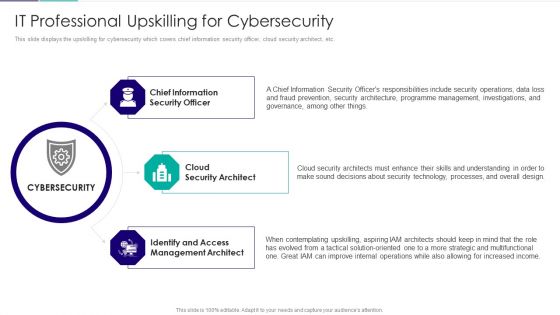
Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc.Presenting Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Chief Information Security, Cloud Security Architect, Identify And Access Management Architect In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
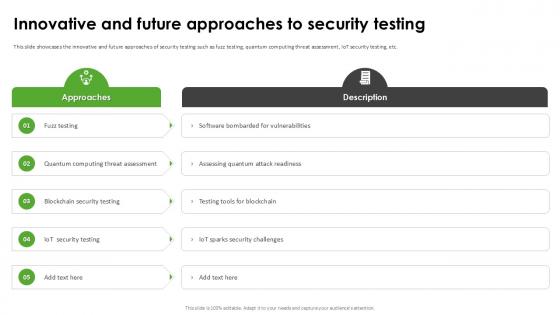
Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide
This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc.
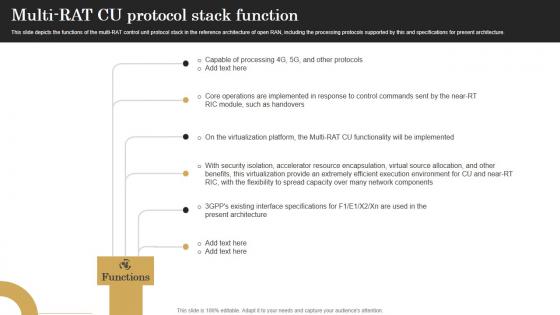
Multi Rat Cu Protocol Stack Function Revolutionizing Mobile Networks Download PDF
This slide depicts the functions of the multi-RAT control unit protocol stack in the reference architecture of open RAN, including the processing protocols supported by this and specifications for present architecture. If you are looking for a format to display your unique thoughts, then the professionally designed Multi Rat Cu Protocol Stack Function Revolutionizing Mobile Networks Download PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Multi Rat Cu Protocol Stack Function Revolutionizing Mobile Networks Download PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the functions of the multi-RAT control unit protocol stack in the reference architecture of open RAN, including the processing protocols supported by this and specifications for present architecture.

Zero Trust Model Working Functions Of Zero Trust Network Access
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Model Working Functions Of Zero Trust Network Access was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Model Working Functions Of Zero Trust Network Access. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
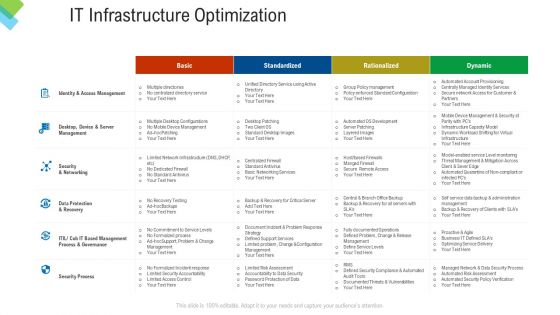
Construction Management Services IT Infrastructure Optimization Themes PDF
Deliver and pitch your topic in the best possible manner with this construction management services it infrastructure optimization themes pdf. Use them to share invaluable insights on security process, security and networking, management process, data protection, server management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF
Presenting Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Information System Categorization, Security Control Selection, Security Control Implementation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Diagram Magnifying Glass With Puzzle Pieces Slide Presentation Template
This business plan power point template has been designed with graphic of lock which is made by puzzles pieces and with one missing puzzle. This PPT contains the concept of security and solution development. Add this PPT in your presentations and display solution and security related topics.
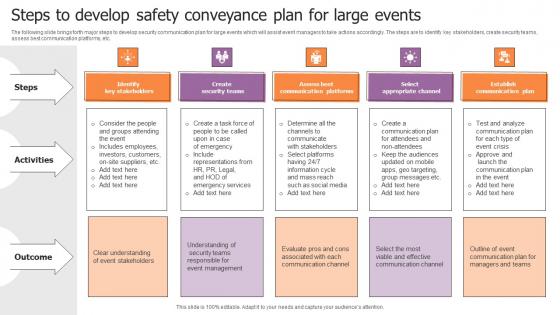
Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf
The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc. Showcasing this set of slides titled Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf. The topics addressed in these templates are Identify Key Stakeholders, Create Security Teams, Select Appropriate Channel. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc.

IOT Technology Trends In Cybersecurity Management Inspiration Pdf
This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection. Pitch your topic with ease and precision using this IOT Technology Trends In Cybersecurity Management Inspiration Pdf This layout presents information on Cybersecurity Mesh, Security At Manufacturing, Network Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection.
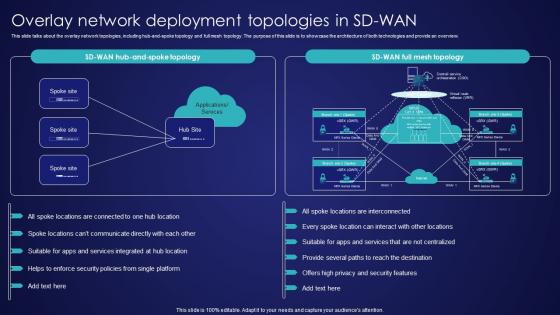
Overlay Network Deployment Topologies In SD Wan Wide Area Network Services Inspiration Pdf
This slide talks about the overlay network topologies, including hub-and-spoke topology and full mesh topology. The purpose of this slide is to showcase the architecture of both technologies and provide an overview. Make sure to capture your audiences attention in your business displays with our gratis customizable Overlay Network Deployment Topologies In SD Wan Wide Area Network Services Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the overlay network topologies, including hub-and-spoke topology and full mesh topology. The purpose of this slide is to showcase the architecture of both technologies and provide an overview.
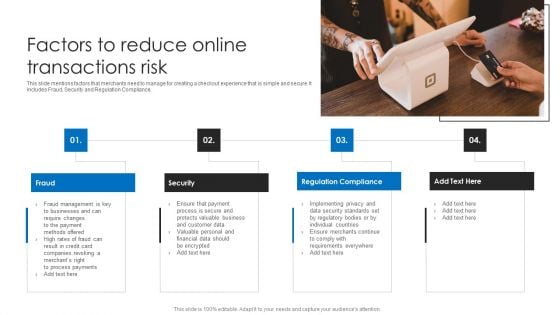
Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF
This slide mentions factors that merchants need to manage for creating a checkout experience that is simple and secure. It includes Fraud, Security and Regulation Compliance. Presenting Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fraud, Security, Regulation Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Risk Management For Organization Essential Assets Brochure PDF
Presenting table of contents risk management for organization essential assets brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, natural calamity threats, ensuring physical security, security against workplace. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
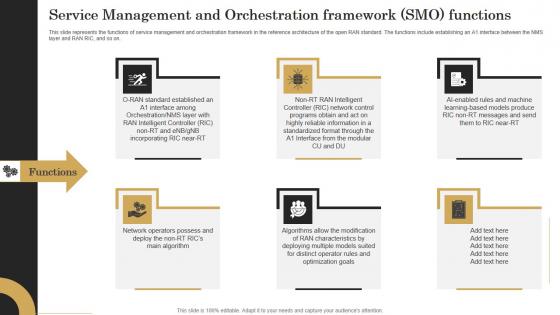
Service Management And Orchestration Revolutionizing Mobile Networks Themes PDF
This slide represents the functions of service management and orchestration framework in the reference architecture of the open RAN standard. The functions include establishing an A1 interface between the NMS layer and RAN RIC, and so on. The Service Management And Orchestration Revolutionizing Mobile Networks Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the functions of service management and orchestration framework in the reference architecture of the open RAN standard. The functions include establishing an A1 interface between the NMS layer and RAN RIC, and so on.
Solid Waste Handling Vehicle Tracking System Framework Implementation Of E Waste Guidelines
This slide showcases the architecture of the solid waste monitoring and garbage vehicle tracking system that helps in enhancing route planning. It includes four key components such as smart bins, vehicle with sensors, GSM network, and monitoring station. There are so many reasons you need a Solid Waste Handling Vehicle Tracking System Framework Implementation Of E Waste Guidelines. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases the architecture of the solid waste monitoring and garbage vehicle tracking system that helps in enhancing route planning. It includes four key components such as smart bins, vehicle with sensors, GSM network, and monitoring station.


 Continue with Email
Continue with Email

 Home
Home


































