Security Architecture
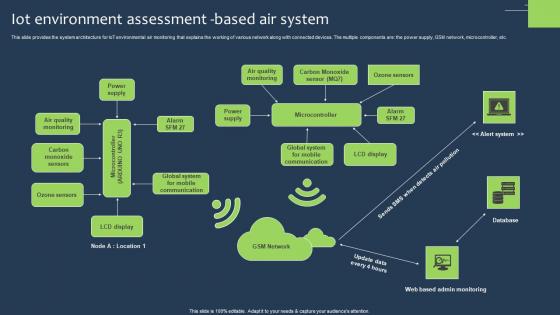
IOT Environment Assessment Based Air System Graphics Pdf
This slide provides the system architecture for IoT environmental air monitoring that explains the working of various network along with connected devices. The multiple components are the power supply, GSM network, microcontroller, etc. Showcasing this set of slides titled IOT Environment Assessment Based Air System Graphics Pdf The topics addressed in these templates are Ozone Sensors, Carbon Monoxide, Communication All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provides the system architecture for IoT environmental air monitoring that explains the working of various network along with connected devices. The multiple components are the power supply, GSM network, microcontroller, etc.

Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.

5g Technology Used To Improve Connectivity And Response Optimizing Inventory Management IoT SS V
This slide provides an overview of the 5G technology used in IoT. The slide further includes architecture and key insights regarding various networks connectivity and coverage. Find a pre-designed and impeccable 5g Technology Used To Improve Connectivity And Response Optimizing Inventory Management IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of the 5G technology used in IoT. The slide further includes architecture and key insights regarding various networks connectivity and coverage.
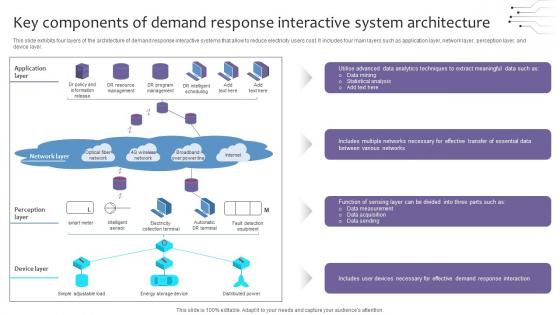
Empowering The Future Key Components Of Demand Response Interactive IoT SS V
This slide exhibits four layers of the architecture of demand response interactive systems that allow to reduce electricity users cost. It includes four main layers such as application layer, network layer, perception layer, and device layer. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Empowering The Future Key Components Of Demand Response Interactive IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide exhibits four layers of the architecture of demand response interactive systems that allow to reduce electricity users cost. It includes four main layers such as application layer, network layer, perception layer, and device layer.
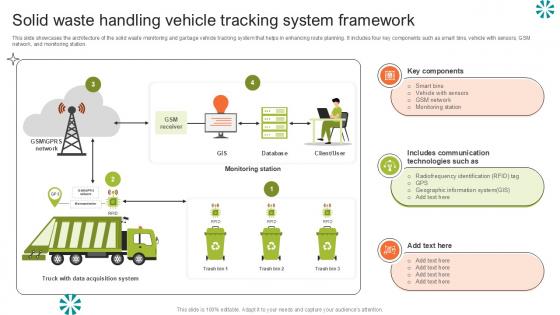
Solid Waste Handling Vehicle Step By Step Guide For Electronic Ppt Presentation
This slide showcases the architecture of the solid waste monitoring and garbage vehicle tracking system that helps in enhancing route planning. It includes four key components such as smart bins, vehicle with sensors, GSM network, and monitoring station. Want to ace your presentation in front of a live audience Our Solid Waste Handling Vehicle Step By Step Guide For Electronic Ppt Presentation can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the architecture of the solid waste monitoring and garbage vehicle tracking system that helps in enhancing route planning. It includes four key components such as smart bins, vehicle with sensors, GSM network, and monitoring station.
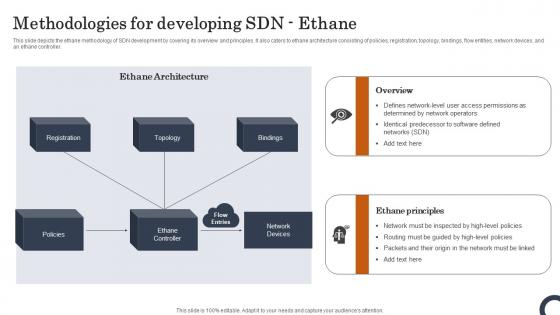
Methodologies For Developing SDN Ethane Evolution Of SDN Controllers Template Pdf
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. Retrieve professionally designed Methodologies For Developing SDN Ethane Evolution Of SDN Controllers Template Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller.
Customer Identity Access Management API Structure With Icons Ppt File Smartart PDF
This slide represents the CIAM API architecture for social media including elements like multifactor authentication, profile registration and update etc. Showcasing this set of slides titled customer identity access management api structure with icons ppt file smartart pdf. The topics addressed in these templates are data stores, client applications, multifactor authentication, access management, social media. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
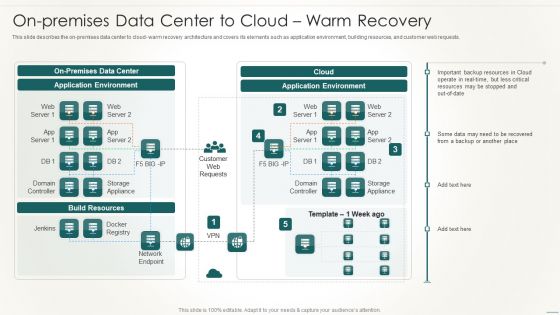
Information Technology Disaster Resilience Plan On-Premises Data Center To Cloudwarm Recovery Ideas PDF
This slide describes the on-premises data center to cloud- warm recovery architecture and covers its elements such as application environment, building resources, and customer web requests.Deliver an awe inspiring pitch with this creative Information Technology Disaster Resilience Plan On-Premises Data Center To Cloudwarm Recovery Ideas PDF bundle. Topics like Domain Controller, Storage Appliance, Network Endpoint can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
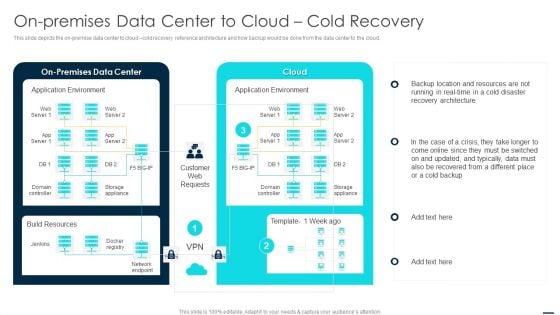
On Premises Data Center To Cloud Cold Recovery Ideas PDF
This slide depicts the on premise data center to cloud cold recovery reference architecture and how backup would be done from the data center to the cloud. Deliver an awe inspiring pitch with this creative On Premises Data Center To Cloud Cold Recovery Ideas PDF bundle. Topics like Application Environment, Build Resources, Network Endpoint can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

On Premises Data Center To Cloud Warm Recovery Background PDF
This slide describes the on premises data center to cloud warm recovery architecture and covers its elements such as application environment, building resources, and customer web requests. Deliver and pitch your topic in the best possible manner with this On Premises Data Center To Cloud Warm Recovery Background PDF. Use them to share invaluable insights on Application Environment, Build Resources, Network Endpoint and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
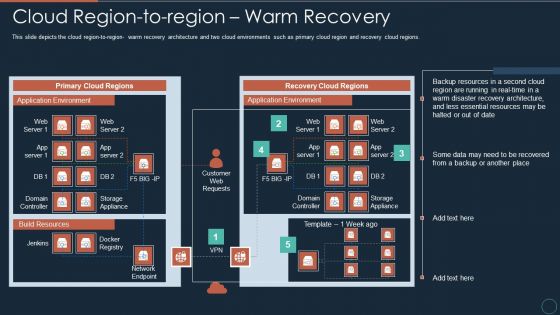
Implementing DRP IT Cloud Region To Region Warm Recovery Ppt PowerPoint Presentation Layouts Backgrounds PDF
This slide depicts the cloud region to region warm recovery architecture and two cloud environments such as primary cloud region and recovery cloud regions.Deliver and pitch your topic in the best possible manner with this implementing drp it cloud region to region warm recovery ppt powerpoint presentation layouts backgrounds pdf Use them to share invaluable insights on network endpoint, docker registry, domain controller and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
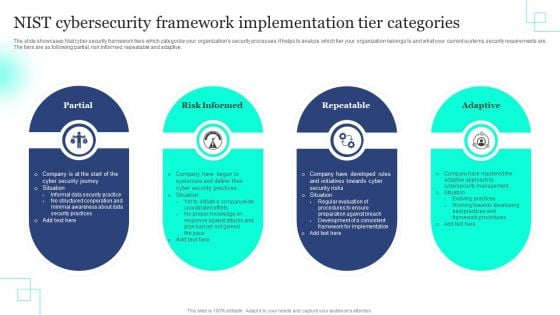
NIST Cybersecurity Framework Implementation Tier Categories Rules PDF
The slide showcases Nist cyber security framework tiers which categorize your organizations security processes, it helps to analyze which tier your organization belongs to and what your current systems security requirements are. The tiers are as following partial, risk informed, repeatable and adaptive. Persuade your audience using this NIST Cybersecurity Framework Implementation Tier Categories Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Partial, Risk Informed, Repeatable . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Safety Initiatives Overview Of New IT Policy Framework Pictures PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. This is a data safety initiatives overview of new it policy framework pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it policy framework, it security and usage policies, data policies, it security policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Intelligence Framework For Application Consumption Determining The Suitable Software For Organization Icons PDF
The slide provides the key features comparison of various software that will help the company to achieve its objective of process automation and data security. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption determining the suitable software for organization icons pdf. Use them to share invaluable insights on process automation, data security, improve productivity, process automation and data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
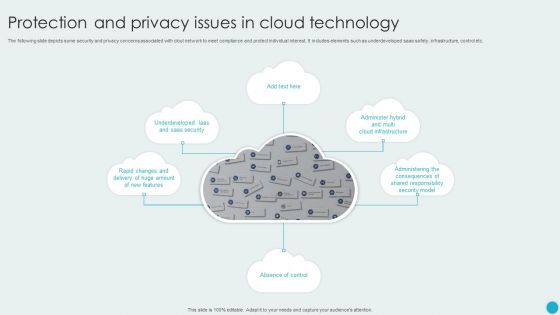
Protection And Privacy Issues In Cloud Technology Rules PDF
The following slide depicts some security and privacy concerns associated with clout network to meet compliance and protect individual interest. It includes elements such as underdeveloped saas safety, infrastructure, control etc. Persuade your audience using this Protection And Privacy Issues In Cloud Technology Rules PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Absence Of Control, Saas Security, Security Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
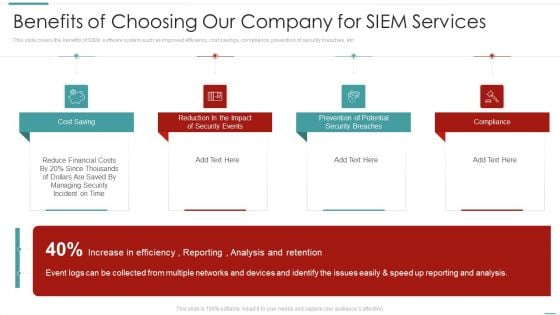
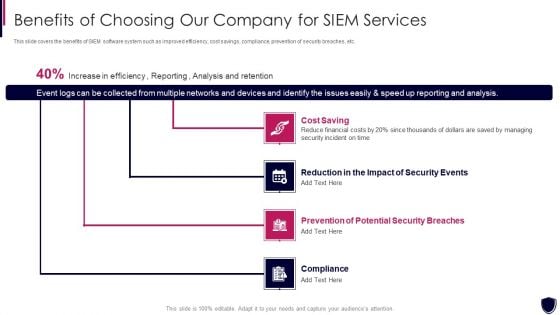
Risk Recognition Automation Benefits Of Choosing Our Company For Siem Services Ppt Gallery Design Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a risk recognition automation benefits of choosing our company for siem services ppt gallery design inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, prevention of potential security breaches, compliance, reduction in the impact of security events. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
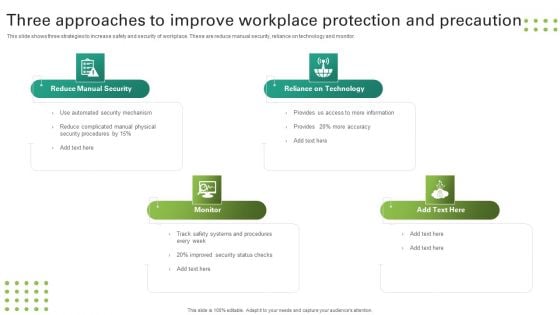
Three Approaches To Improve Workplace Protection And Precaution Background PDF
This slide shows three strategies to increase safety and security of workplace. These are reduce manual security, reliance on technology and monitor. Persuade your audience using this Three Approaches To Improve Workplace Protection And Precaution Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Reduce Manual Security, Reliance On Technology, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
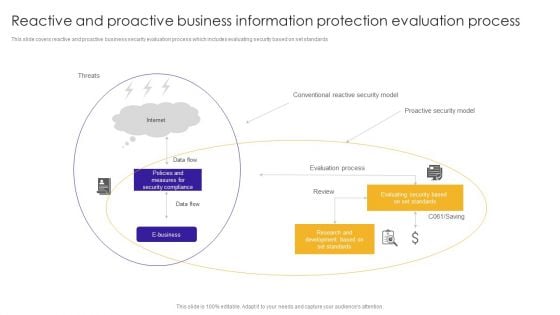
Reactive And Proactive Business Information Protection Evaluation Process Sample PDF
This slide covers reactive and proactive business security evaluation process which includes evaluating security based on set standards. Persuade your audience using this Reactive And Proactive Business Information Protection Evaluation Process Sample PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Conventional Reactive, Proactive Security, Evaluation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Key Performance Indicators With Applications Summary Pdf
Pitch your topic with ease and precision using this Cybersecurity Key Performance Indicators With Applications Summary Pdf This layout presents information on Identify Weaknesses, Review Improvement, Security Policies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc.
Enhancing Cyber Safety With Vulnerability Administration Benefits Of Choosing Our Company Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting enhancing cyber safety with vulnerability administration benefits of choosing our company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
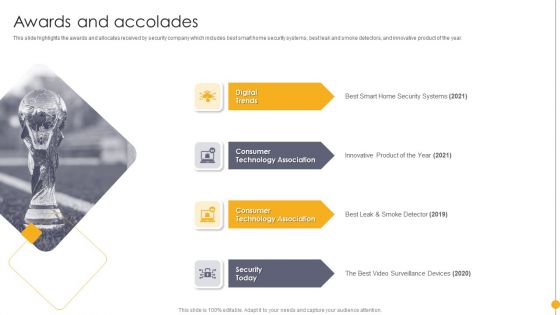
Portable Home Safety Systems Company Profile Awards And Accolades Brochure PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Portable Home Safety Systems Company Profile Awards And Accolades Brochure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends, Consumer, Technology Association, Consumer Technology Association, Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Influencer Marketing 4 Months Project Status Update Icon Slides PDF
This slide covers the four months project status update of software implementation project undertaken by the IT team. It includes various activities to be performed under IT help desk, web server, network and global security.Showcasing this set of slides titled Influencer Marketing 4 Months Project Status Update Icon Slides PDF. The topics addressed in these templates are Global Security, Network Speed, Security Plan . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SIEM Benefits Of Choosing Our Company For SIEM Services Ppt File Outfit PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting siem benefits of choosing our company for siem services ppt file outfit pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
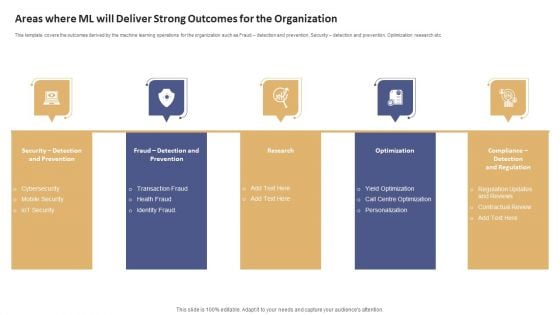
Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. Presenting Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Mobile Security, IoT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
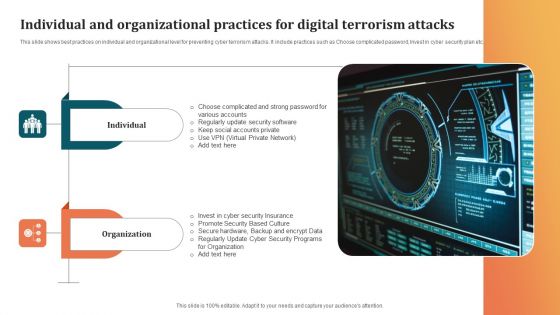
Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
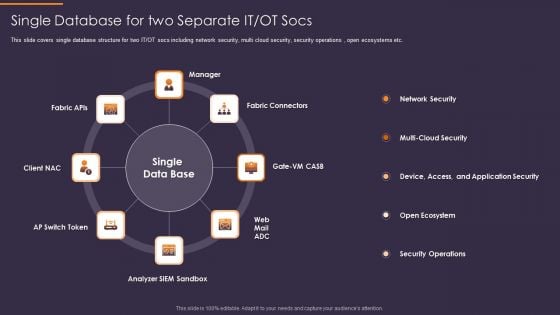
Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Fabric Connectors, Analyzer SIEM Sandbox, AP Switch Token, Client NAC, Fabric APIs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
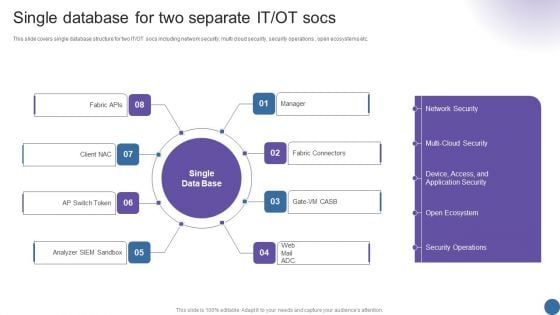
Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF
This slide covers single database structure for two IT OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Single Database, Two Separate, Fabric Connectors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
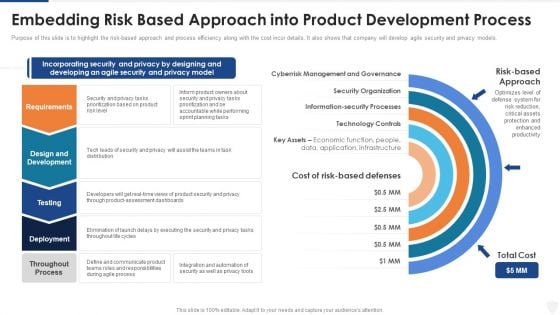
Embedding Risk Based Approach Into Product Development Process Ppt Model Files PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Presenting embedding risk based approach into product development process ppt model files pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like technology controls, information security processes, security organization, economic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
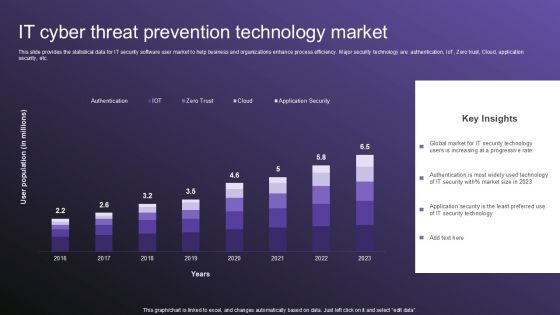
IT Cyber Threat Prevention Technology Market Topics PDF
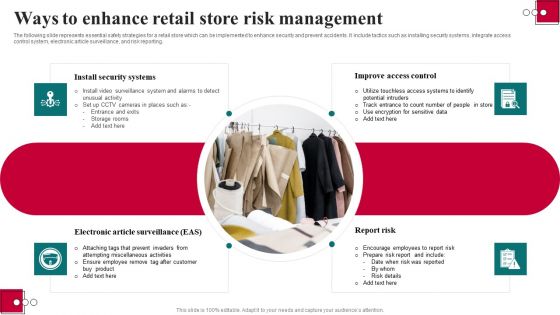
Ways To Enhance Retail Store Risk Management Introduction PDF
The following slide represents essential safety strategies for a retail store which can be implemented to enhance security and prevent accidents. It include tactics such as installing security systems, integrate access control system, electronic article surveillance, and risk reporting. Pitch your topic with ease and precision using this Ways To Enhance Retail Store Risk Management Introduction PDF. This layout presents information on Electronic Article Surveillance, Report Risk, Install Security Systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
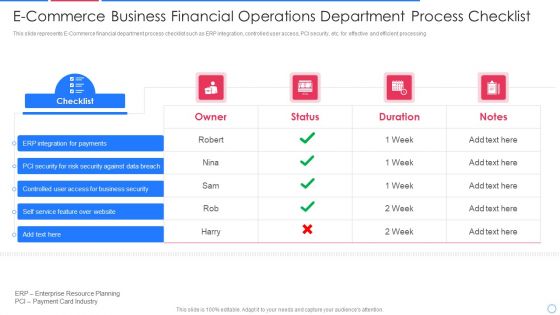
E Commerce Business Financial Operations Department Process Checklist Information PDF
This slide represents E-Commerce financial department process checklist such as ERP integration, controlled user access, PCI security, etc. for effective and efficient processing Pitch your topic with ease and precision using this e commerce business financial operations department process checklist information pdf This layout presents information on integration for payments, security for risk security against, controlled user access It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
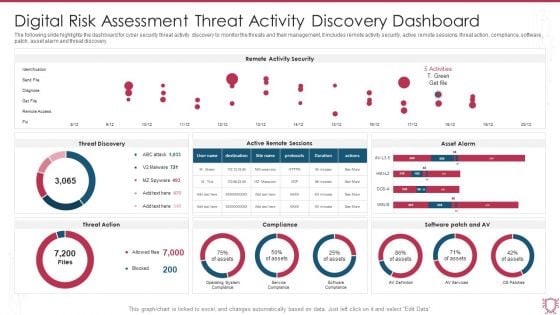
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
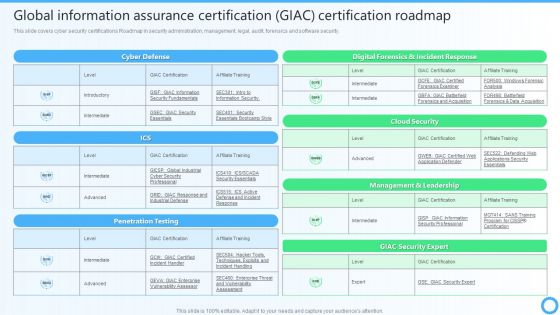
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF
This slide covers enterprise security operation center team roles and responsibilities. It involves key roles such as incident responder, security investigator, advanced security analyst and SOC manager. Pitch your topic with ease and precision using this ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF. This layout presents information on SOC Team Roles, Responsibilities, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
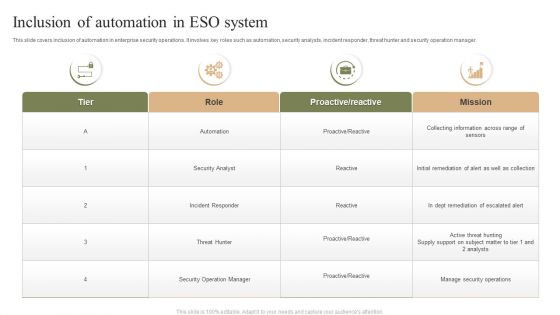
Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF
This slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Pitch your topic with ease and precision using this Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF. This layout presents information on Mission, Role, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
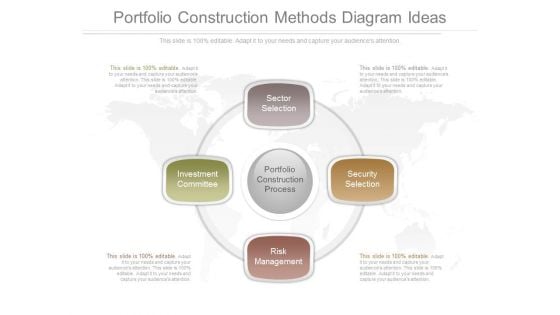
Portfolio Construction Methods Diagram Ideas
This is a portfolio construction methods diagram ideas. This is a four stage process. The stages in this process are portfolio construction process, sector selection, investment committee, risk management, security selection.
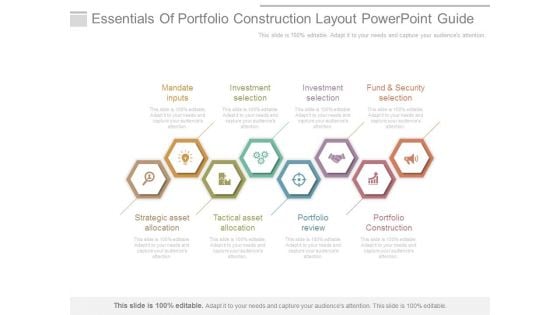
Essentials Of Portfolio Construction Layout Powerpoint Guide
This is a essentials of portfolio construction layout powerpoint guide. This is a eight stage process. The stages in this process are mandate inputs, investment selection, fund and security selection, strategic asset allocation, tactical asset allocation, portfolio review, portfolio construction.
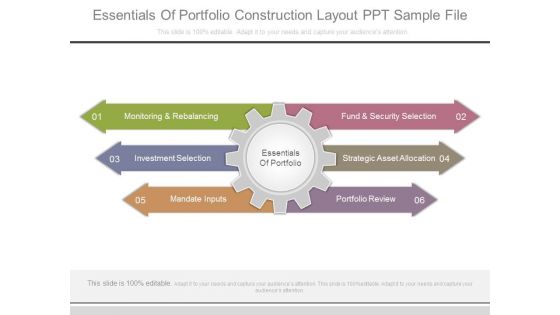
Essentials Of Portfolio Construction Layout Ppt Sample File
This is a essentials of portfolio construction layout ppt sample file. This is a six stage process. The stages in this process are monitoring and rebalancing, investment selection, mandate inputs, fund and security selection, strategic asset allocation, portfolio review.
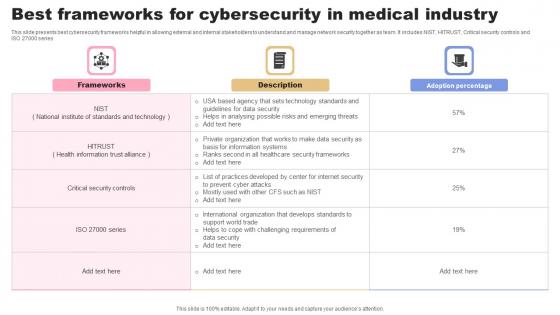
Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf
This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series Showcasing this set of slides titled Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf. The topics addressed in these templates are Frameworks, Description, Adoption Percentage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series
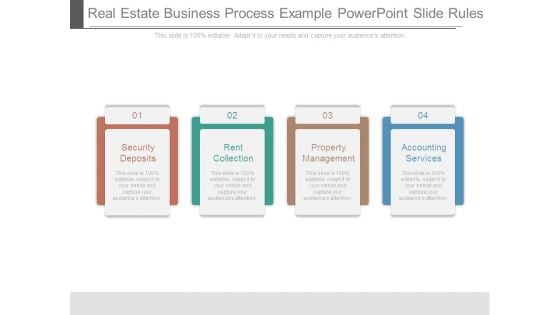
Real Estate Business Process Example Powerpoint Slide Rules
This is a real estate business process example powerpoint slide rules. This is a four stage process. The stages in this process are security deposits, rent collection, property management, accounting services.
Business Framework Entry Barrier 1 PowerPoint Presentation
This business framework PPT diagram has been designed with graphic of traffic cones and barrier. This PPT diagram contains the concept of security and construction. Use this PPT diagram for your road safety and traffic rules related presentations.

Stock Photo 3d Key And Keyhole For Safety Image Graphics For PowerPoint Slide
This image slide has been designed with graphics of golden key with key hole. This professional slide contains golden key to displays security and safety concepts. This unique image provides impressive background for your presentations.
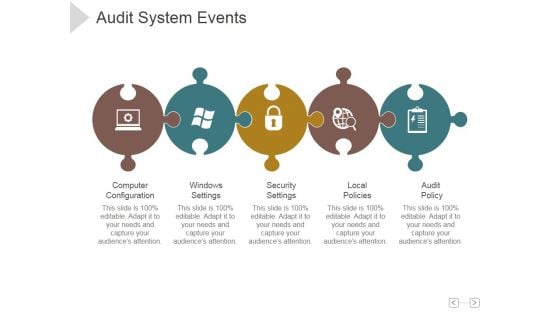
Audit System Events Ppt PowerPoint Presentation Model
This is a audit system events ppt powerpoint presentation model. This is a five stage process. The stages in this process are computer configuration, windows settings , security settings , local policies, audit policy.
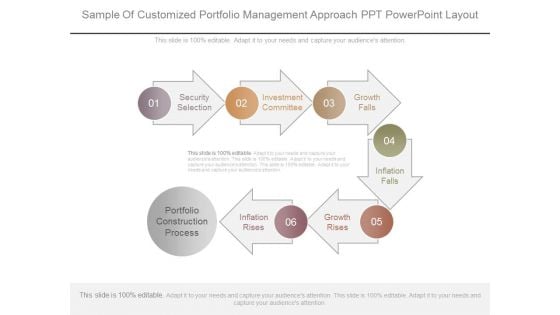
Sample Of Customized Portfolio Management Approach Ppt Powerpoint Layout
This is a sample of customized portfolio management approach ppt powerpoint layout. This is a six stage process. The stages in this process are security selection, investment committee, growth falls, portfolio construction process, inflation rises, growth rises, inflation falls.
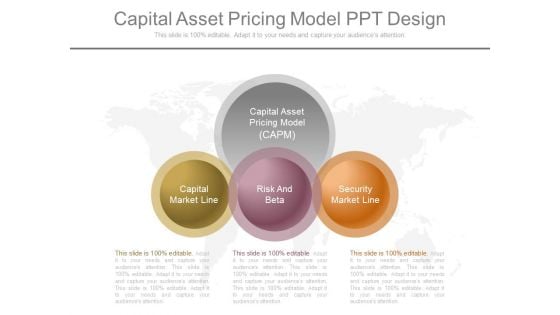
Capital Asset Pricing Model Ppt Design
This is a capital asset pricing model ppt design. This is a three stage process. The stages in this process are capital market line, risk and beta, security market line, capital asset pricing model.

Our Services Template 2 Ppt PowerPoint Presentation Show Design Inspiration
This is a our services template 2 ppt powerpoint presentation show design inspiration. This is a four stage process. The stages in this process are digital advertising, marketing and analytics, digital care package, security and maintenance.

Property Management Spreadsheet Template Powerpoint Slides Background Designs
This is a property management spreadsheet template powerpoint slides background designs. This is a five stage process. The stages in this process are mortgage and utility payments, leasing, security deposits, accounting services, repair and maintenance service.
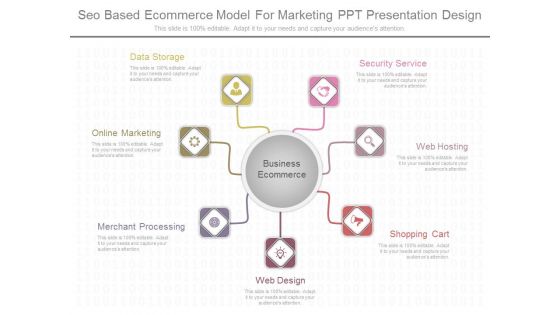
Seo Based Ecommerce Model For Marketing Ppt Presentation Design
This is a seo based ecommerce model for marketing ppt presentation design. This is a seven stage process. The stages in this process are security service, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.
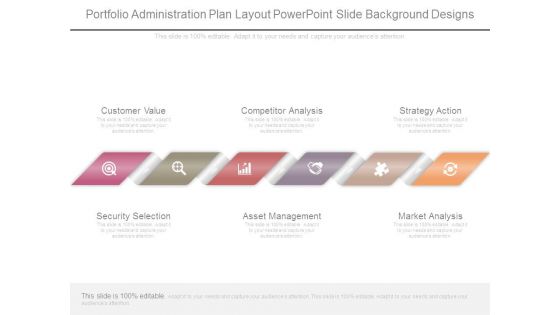
Portfolio Administration Plan Layout Powerpoint Slide Background Designs
This is a portfolio administration plan layout powerpoint slide background designs. This is a six stage process. The stages in this process are customer value, competitor analysis, strategy action, market analysis, asset management, security selection.
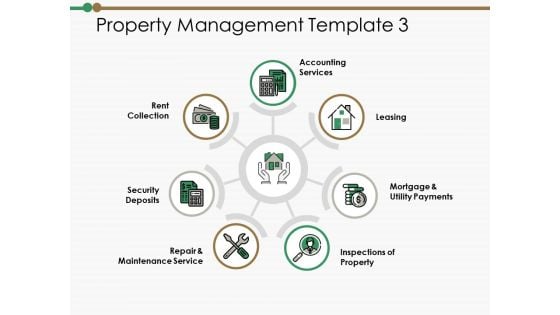
Property Management Template Ppt PowerPoint Presentation Styles Designs
This is a property management template ppt powerpoint presentation styles designs. This is a seven stage process. The stages in this process are rent collection, security deposits, inspections of property.

Challenges With Devsecops Implementation And Solutions Role Of Devsecops Ppt Powerpoint
This slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc. There are so many reasons you need a Challenges With Devsecops Implementation And Solutions Role Of Devsecops Ppt Powerpoint The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc.
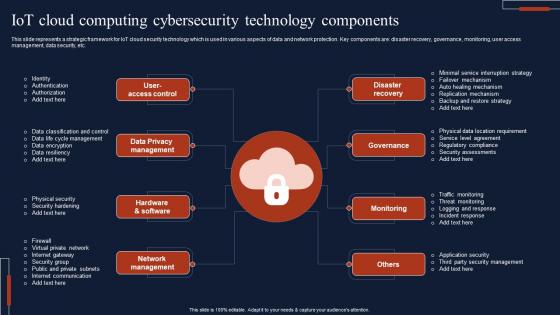
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc.

Stock Photo Key With Red Heart Shaped Lock PowerPoint Slide
This image slide has been designed with key and red heart shaped lock. Use this image to define concepts like lock, security heart protection. Make amazing presentations with this image.
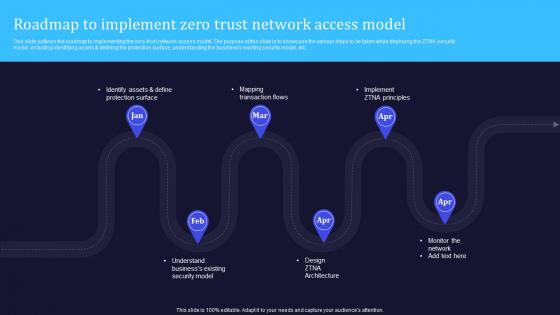
A20 Zero Trust Model Roadmap To Implement Zero Trust Network Access
This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the businesss existing security model, etc. Find a pre-designed and impeccable A20 Zero Trust Model Roadmap To Implement Zero Trust Network Access. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the businesss existing security model, etc.

Stock Photo Blue Colored Pen Drive With Combination Lock PowerPoint Slide
Graphic of blue colored pen drive and combination lock has been used to design this power point template. This PPT contains the concept of data security and data technology. Use this PPT for your business and marketing related presentations.
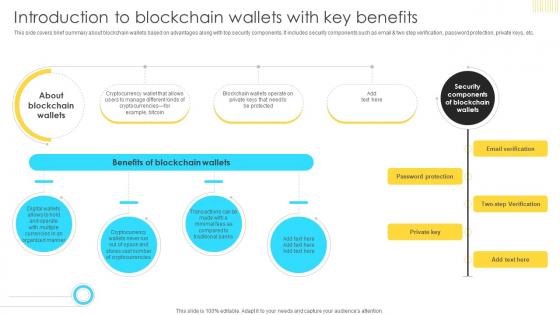
Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V
This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc Do you know about Slidesgeeks Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc
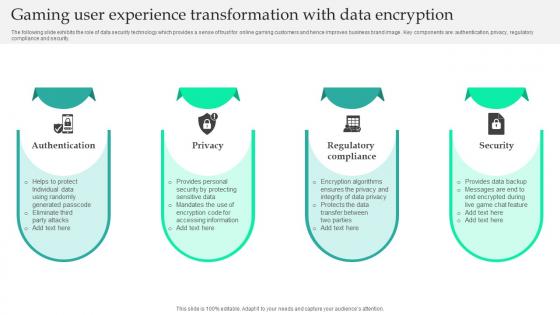
Gaming User Experience Transformation With Data Encryption Portrait Pdf
The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security. Pitch your topic with ease and precision using this Gaming User Experience Transformation With Data Encryption Portrait Pdf. This layout presents information on Authentication, Privacy, Regulatory Compliance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security.
Stock Photo 3d Dollar Symbol With Chain And Text Boxes PowerPoint Slide
This image slide has been designed with graphic of dollar notes locked with chain. This slide depicts concept of financial security and investment. Use this editable slide for your wealth and finance related topics.
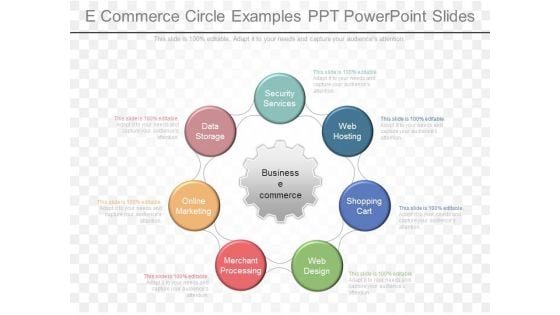
E Commerce Circle Examples Ppt Powerpoint Slides
This is a e commerce circle examples ppt powerpoint slides. This is a seven stage process. The stages in this process are business e commerce, security services, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.


 Continue with Email
Continue with Email

 Home
Home


































