Security Architecture
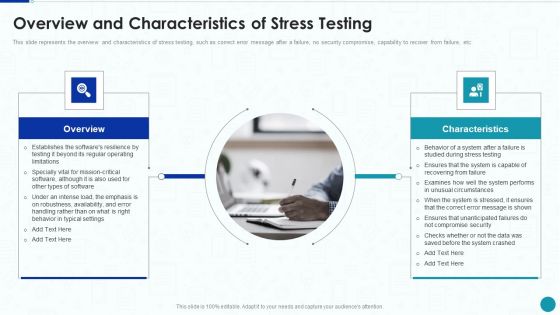
Compliance Testing IT Overview And Characteristics Of Stress Testing Summary PDF
This slide represents the overview and characteristics of stress testing, such as correct error message after a failure, no security compromise, capability to recover from failure, etc. Presenting Compliance Testing IT Overview And Characteristics Of Stress Testing Summary PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Compromise Security, System Crashed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
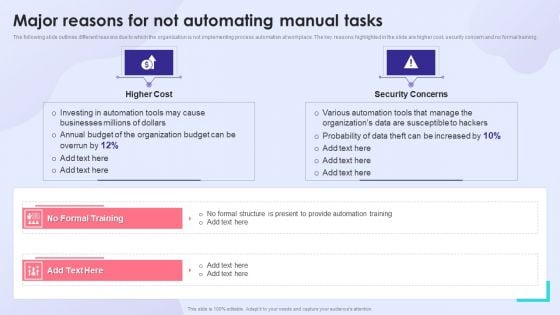
Major Reasons For Not Automating Manual Tasks Inspiration PDF
The following slide outlines different reasons due to which the organization is not implementing process automation at workplace. The key reasons highlighted in the slide are higher cost, security concern and no formal training. Presenting Major Reasons For Not Automating Manual Tasks Inspiration PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Higher Cost, Security Concerns. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
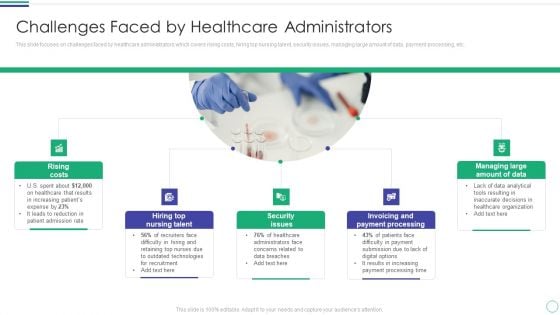
Challenges Faced By Healthcare Administrators Sample PDF
This slide focuses on challenges faced by healthcare administrators which covers rising costs, hiring top nursing talent, security issues, managing large amount of data, payment processing, etc.Presenting Challenges Faced By Healthcare Administrators Sample PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Issues, Payment Processing, Managing Large In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
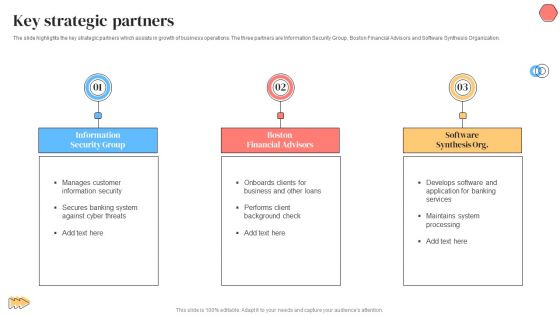
Banking Solutions Company Overview Key Strategic Partners Diagrams PDF
The slide highlights the key strategic partners which assists in growth of business operations. The three partners are Information Security Group, Boston Financial Advisors and Software Synthesis Organization. Presenting Banking Solutions Company Overview Key Strategic Partners Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Information Security Group, Boston Financial Advisors, Software Synthesis Org. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
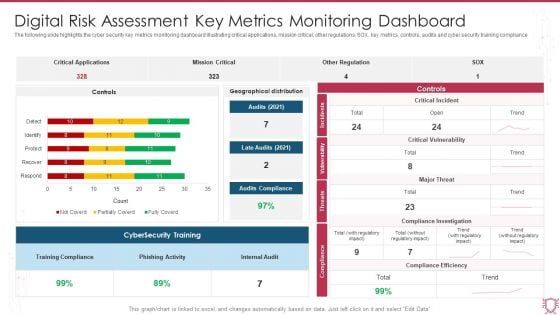
Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF
The following slide highlights the cyber security key metrics monitoring dashboard illustrating critical applications, mission critical, other regulations, SOX, key metrics, controls, audits and cyber security training compliance. Showcasing this set of slides titled Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF. The topics addressed in these templates are Critical Applications, Mission Critical, Other Regulation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
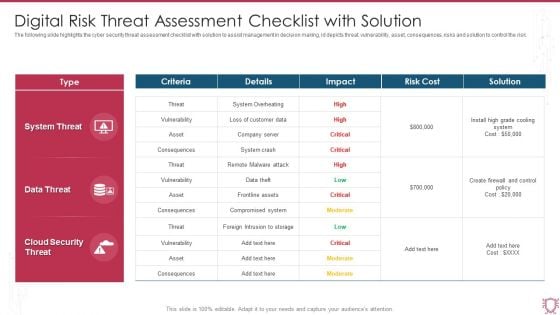
Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Apache Hadoop Software Deployment Disadvantages Of Hadoop Structure PDF
This slide represents the disadvantages of Hadoop on the basis of security, vulnerability by design, not suitable for small data, and potential stability concerns.This is a Apache Hadoop Software Deployment Disadvantages Of Hadoop Structure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing Complicated, Security Breaches, Potential Stability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Integrated Software Why Do We Need Hospital Management System Themes PDF
This slide illustrates the need for hospital management system such as cost effectiveness, reduction in errors, maintains security of information, improves patient care, etc.Presenting Implementing Integrated Software Why Do We Need Hospital Management System Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cost Effective, Reduction Errors, Information Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
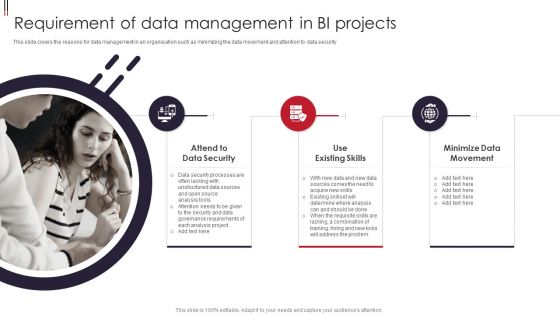
Information Visualizations Playbook Requirement Of Data Management In BI Projects Ideas PDF
This slide covers the reasons for data management in an organisation such as minimizing the data movement and attention to data security Presenting Information Visualizations Playbook Requirement Of Data Management In BI Projects Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Data Security, Use Existing Skills, Minimize Data Movement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
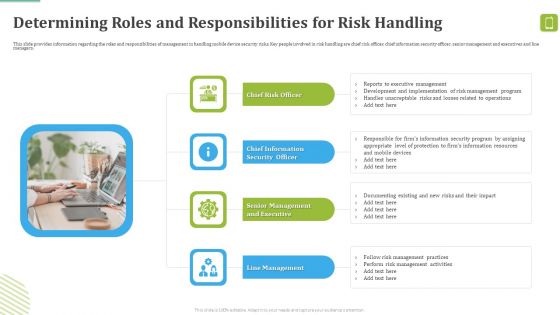
MDM Strategies At Office Determining Roles And Responsibilities For Risk Handling Formats PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Presenting MDM Strategies At Office Determining Roles And Responsibilities For Risk Handling Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Chief Information, Senior Management, Line Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Venture Digitial Transformation Enterprise Technical Challenges Ppt PowerPoint Presentation File Slide PDF
This slide covers technical challenges such as environmental, compatibility, skills shortage and security in enterprise while making IT OT convergence. Presenting Smart Venture Digitial Transformation Enterprise Technical Challenges Ppt PowerPoint Presentation File Slide PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Environmental, Compatibility, Skills Shortage, Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
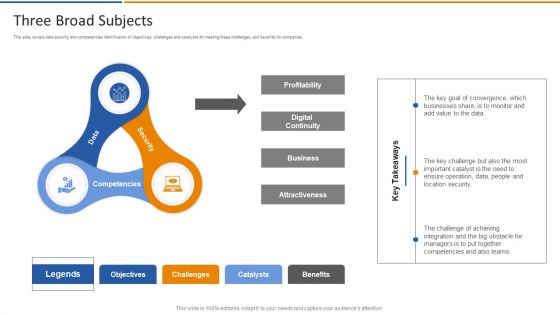
Smart Venture Digitial Transformation Three Broad Subjects Ppt Gallery Graphics Template PDF
This slide covers data security and competencies identification of objectives, challenges and catalysts for meeting these challenges, and benefits for companies. Presenting Smart Venture Digitial Transformation Three Broad Subjects Ppt Gallery Graphics Template PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Data, Security, Competencies, Attractiveness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Devops Capabilities Top Skills Essential For Devops Engineer Ppt PowerPoint Presentation Ideas Good PDF
This slide provides the glimpse about the top skills which a devops engineer must have such as communication and collaboration, soft skills, security skills, automation skills, etc.Presenting Devops Capabilities Top Skills Essential For Devops Engineer Ppt PowerPoint Presentation Ideas Good PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Communication Collaboration, Understanding Relevant, Security Skills. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
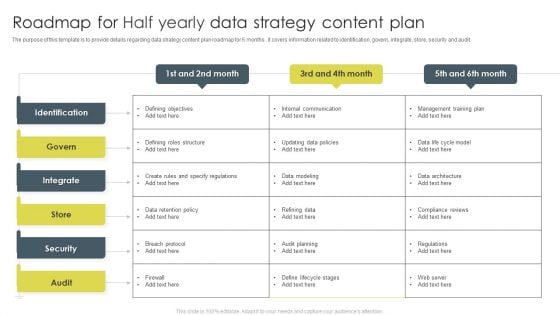
Roadmap For Half Yearly Data Strategy Content Plan Ppt Professional Background PDF
The purpose of this template is to provide details regarding data strategy contents plan roadmap for 6months. It covers information related to identification, govern, integrate, store, security and audit. Showcasing this set of slides titled Roadmap For Half Yearly Data Strategy Content Plan Ppt Professional Background PDF. The topics addressed in these templates are Identification, Integrate, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
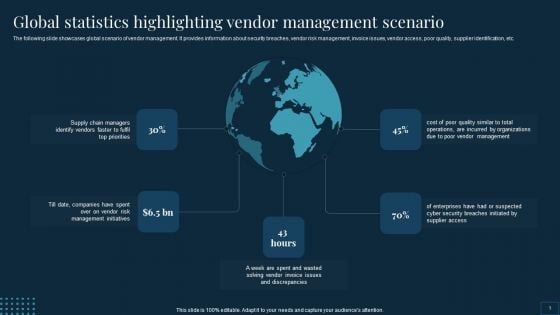
Vendor Management To Handle Purchase Global Statistics Highlighting Vendor Management Scenario Elements PDF
The following slide showcases global scenario of vendor management. It provides information about security breaches, vendor risk management, invoice issues, vendor access, poor quality, supplier identification, etc.Presenting Vendor Management To Handle Purchase Global Statistics Highlighting Vendor Management Scenario Elements PDF to provide visual cues and insights. Share and navigate important information on five stage that need your due attention. This template can be used to pitch topics like Management Initiatives, Vendor Invoice, Security Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Infrastructure Library Methodology Implementation Comparison Between ITIL V2 And ITIL V3 Icons PDF
This slide represents the difference between ITIL v2 and ITIL v3, based on focus, approach, security management, number of processes, and functions. This is a IT Infrastructure Library Methodology Implementation Comparison Between ITIL V2 And ITIL V3 Icons PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Management, Evaluation, Strategy And Design. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
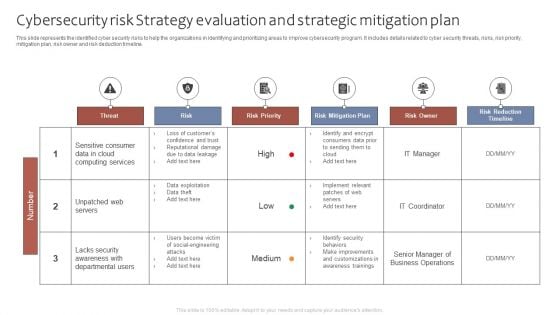
Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF
This slide represents the identified cyber security risks to help the organizations in identifying and prioritizing areas to improve cybersecurity program. It includes details related to cyber security threats, risks, risk priority, mitigation plan, risk owner and risk deduction timeline. Showcasing this set of slides titled Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF. The topics addressed in these templates are Threat, Risk, Risk Priority, Risk Mitigation Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Roles And Responsibilities Of Risk Management Team Cybersecurity Risk Assessment Infographics PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roles And Responsibilities Of Risk Management Team Cybersecurity Risk Assessment Infographics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
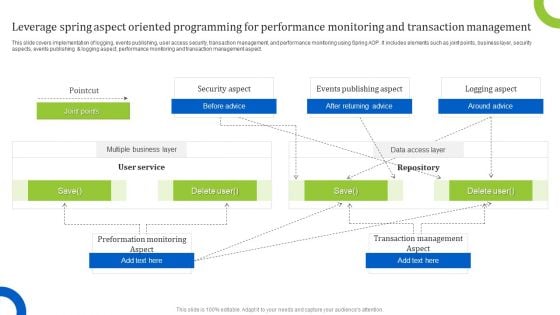
Leverage Spring Aspect Oriented Programming For Performance Monitoring And Transaction Management Clipart PDF
This slide covers implementation of logging, events publishing, user access security, transaction management, and performance monitoring using Spring AOP. It includes elements such as joint points, business layer, security aspects, events publishing and logging aspect, performance monitoring and transaction management aspect. Showcasing this set of slides titled Leverage Spring Aspect Oriented Programming For Performance Monitoring And Transaction Management Clipart PDF. The topics addressed in these templates are After Returning Advice, Around Advice, Events Publishing Aspect. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
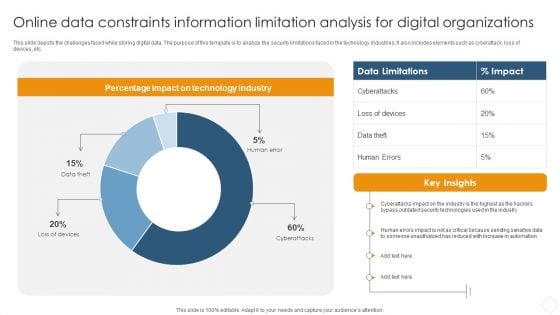
Online Data Constraints Information Limitation Analysis For Digital Organizations Information PDF
This slide depicts the challenges faced while storing digital data. The purpose of this template is to analyze the security limitations faced in the technology industries. It also includes elements such as cyberattack, loss of devices, etc.Pitch your topic with ease and precision using this Online Data Constraints Information Limitation Analysis For Digital Organizations Information PDF. This layout presents information on Percentage Impact, Technology Industry, Security Technologies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
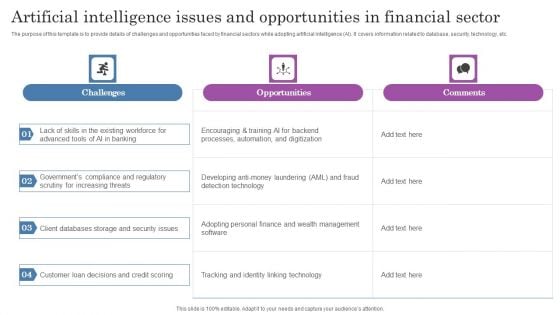
Artificial Intelligence Issues And Opportunities In Financial Sector Demonstration PDF
The purpose of this template is to provide details of challenges and opportunities faced by financial sectors while adopting artificial intelligence AI. It covers information related to database, security, technology, etc. Showcasing this set of slides titled Artificial Intelligence Issues And Opportunities In Financial Sector Demonstration PDF. The topics addressed in these templates are Opportunities, Security Issues, Customer Loan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
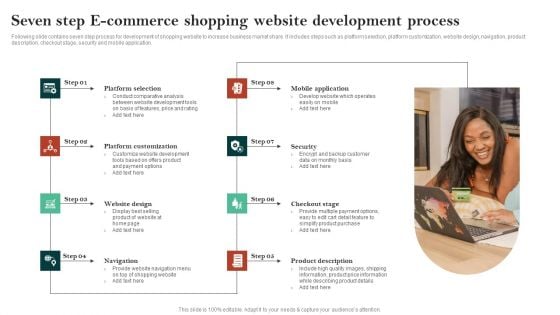
Seven Step E Commerce Shopping Website Development Process Guidelines PDF
Following slide contains seven step process for development of shopping website to increase business market share. It includes steps such as platform selection, platform customization, website design, navigation, product description, checkout stage, security and mobile application. Presenting Seven Step E Commerce Shopping Website Development Process Guidelines PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Platform Selection, Mobile Application, Security, Checkout Stage, Product Description. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Business Collaboration Plan Key Activities Information PDF
This slide presents a schedule timeline for tracking and monitoring key activities in order to successful completion of project. Its key tasks includes combined event action plan, short term security generation, competitive intelligence processes, branding, linking contacts in datasets, etc. Showcasing this set of slides titled Business Collaboration Plan Key Activities Information PDF. The topics addressed in these templates are Branding, Acquisition Positioning, Partners Communication, Short Term Security Generation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
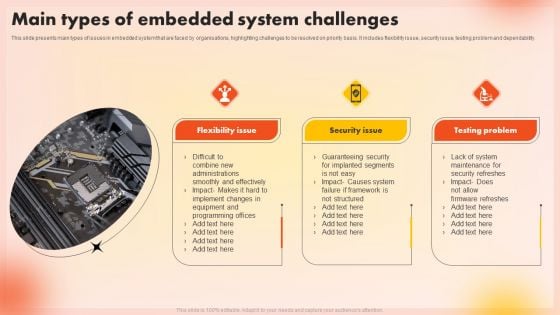
Main Types Of Embedded System Challenges Download PDF
This slide presents main types of issues in embedded system that are faced by organisations, highlighting challenges to be resolved on priority basis. It includes flexibility issue, security issue, testing problem and dependability. Showcasing this set of slides titled Main Types Of Embedded System Challenges Download PDF. The topics addressed in these templates are Flexibility Issue, Security Issue, Testing Problem. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
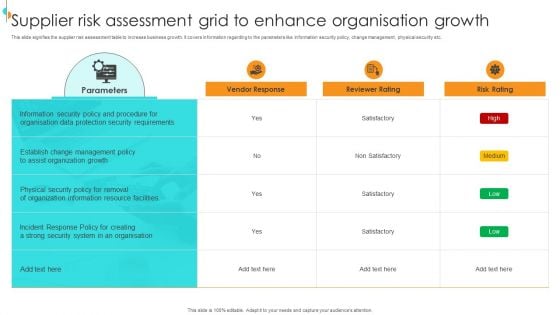
Supplier Risk Assessment Grid To Enhance Organisation Growth Download PDF

Why CASB Is Important For Businesses Ppt PowerPoint Presentation File Example File PDF
This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Why CASB Is Important For Businesses Ppt PowerPoint Presentation File Example File PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
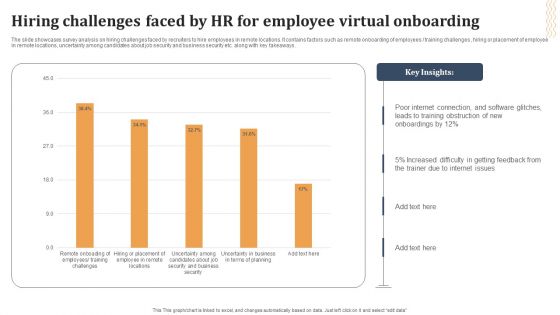
Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF
The slide showcases survey analysis on hiring challenges faced by recruiters to hire employees in remote locations. It contains factors such as remote onboarding of employees training challenges , hiring or placement of employee in remote locations, uncertainty among candidates about job security and business security etc. along with key takeaways. Showcasing this set of slides titled Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF. The topics addressed in these templates are Internet Connection, Software Glitches, Internet Issues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
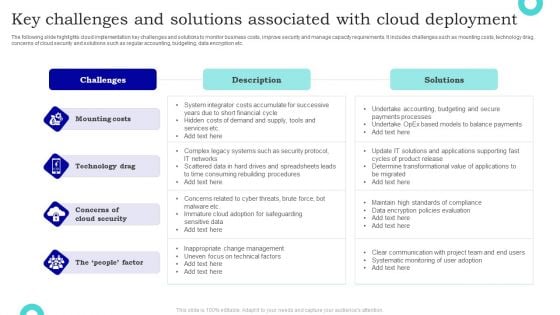
Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF
The following slide highlights cloud implementation key challenges and solutions to monitor business costs, improve security and manage capacity requirements. It includes challenges such as mounting costs, technology drag, concerns of cloud security and solutions such as regular accounting, budgeting, data encryption etc. Pitch your topic with ease and precision using this Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF. This layout presents information on Challenges, Description, Solutions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key AI Trends Associated With Financial Sector Applications And Impact Themes Pdf
This slide represents key artificial intelligence tools related to financial sector. It includes huperautomation, AI-powered advisory, financial security and personalized offering. Find a pre-designed and impeccable Key AI Trends Associated With Financial Sector Applications And Impact Themes Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents key artificial intelligence tools related to financial sector. It includes huperautomation, AI-powered advisory, financial security and personalized offering.
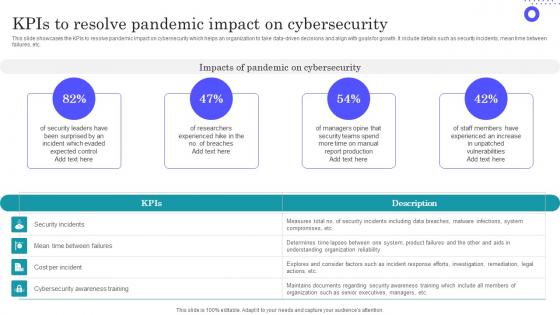
KPIs To Resolve Pandemic Impact On Cybersecurity Microsoft Pdf
Pitch your topic with ease and precision using this KPIs To Resolve Pandemic Impact On Cybersecurity Microsoft Pdf This layout presents information on Understanding Organization, Security Incidents, Malware Infections It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the KPIs to resolve pandemic impact on cybersecurity which helps an organization to take data driven decisions and align with goals for growth. It include details such as security incidents, mean time between failures, etc.
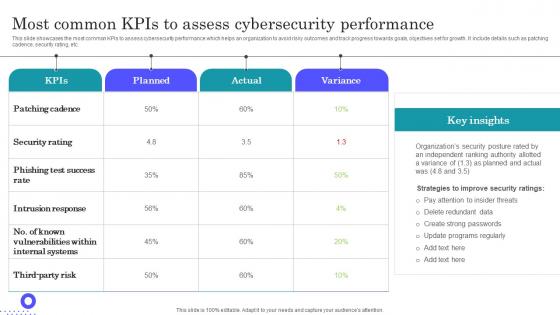
Most Common KPIs To Assess Cybersecurity Performance Slides Pdf
Showcasing this set of slides titled Most Common KPIs To Assess Cybersecurity Performance Slides Pdf The topics addressed in these templates are Intrusion Response, Phishing Test Success, Security Rating All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the most common KPIs to assess cybersecurity performance which helps an organization to avoid risky outcomes and track progress towards goals, objectives set for growth. It include details such as patching cadence, security rating, etc.
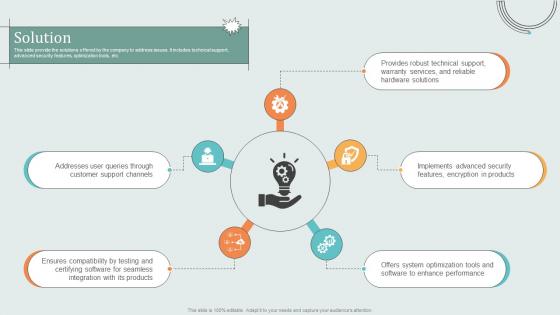
Solution Hardware Technology Provider Business Model BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Hardware Technology Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.
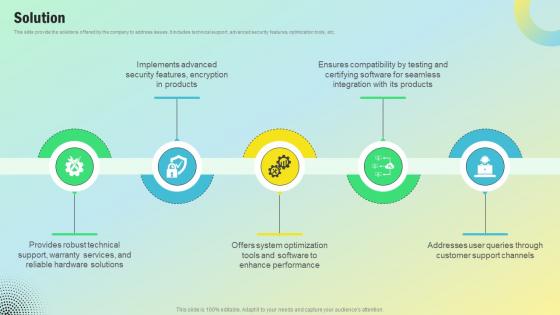
Solution Personal Computing Company Revenue Model BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Personal Computing Company Revenue Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.

Address Challenges Associated With Legacy Systems DT SS V
This slide addresses the challenges associated with legacy systems and how it impact digital transformation of SMEs. It includes outdated technology, security vulnerabilities and lack of flexibility.Find a pre-designed and impeccable Address Challenges Associated With Legacy Systems DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide addresses the challenges associated with legacy systems and how it impact digital transformation of SMEs. It includes outdated technology, security vulnerabilities and lack of flexibility.
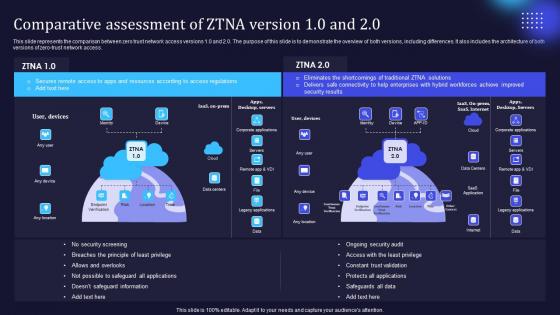
Zero Trust Model Comparative Assessment Of ZTNA Version 1 0 And 2 0
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Comparative Assessment Of ZTNA Version 1 0 And 2 0 can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Comparative Assessment Of ZTNA Version 1 0 And 2 0 and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.
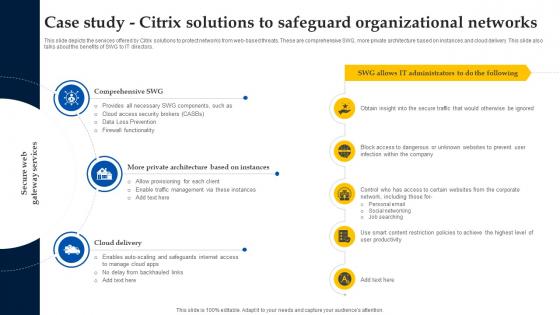
Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks
This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors. Find highly impressive Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors.

IoT Based Energy Management System Multi Internet Of Things Solutions To Enhance Energy IoT SS V
This slide exhibits four layers energy management system architecture utilising IoT technology. It includes four layers such as applications layer, cognition layer, network layer, and sensing layer. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IoT Based Energy Management System Multi Internet Of Things Solutions To Enhance Energy IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IoT Based Energy Management System Multi Internet Of Things Solutions To Enhance Energy IoT SS V This slide exhibits four layers energy management system architecture utilising IoT technology. It includes four layers such as applications layer, cognition layer, network layer, and sensing layer.

IoT Based Satellite Platform For Maritime Transport Services IoT In Orbit Unleashing The Power IoT SS V
This slide exhibits IoT satellite system architecture that helps to establish efficient communication infrastructure for maritime operations. It includes key elements such as IoT devices, smart IoT gateway, 5G cellular network, Teleport, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than IoT Based Satellite Platform For Maritime Transport Services IoT In Orbit Unleashing The Power IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab IoT Based Satellite Platform For Maritime Transport Services IoT In Orbit Unleashing The Power IoT SS V today and make your presentation stand out from the rest This slide exhibits IoT satellite system architecture that helps to establish efficient communication infrastructure for maritime operations. It includes key elements such as IoT devices, smart IoT gateway, 5G cellular network, Teleport, etc.
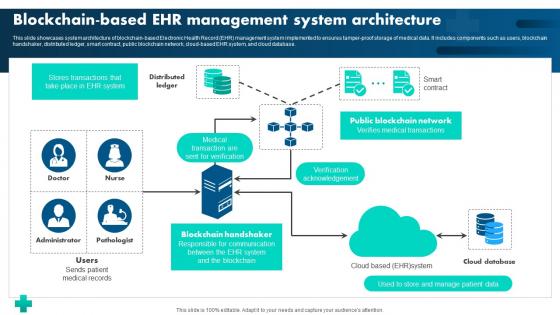
How Blockchain Is Reshaping Blockchain Based EHR Management System BCT SS V
This slide showcases system architecture of blockchain-based Electronic Health Record EHR management system implemented to ensures tamper-proof storage of medical data. It includes components such as users, blockchain handshaker, distributed ledger, smart contract, public blockchain network, cloud-based EHR system, and cloud database. Whether you have daily or monthly meetings, a brilliant presentation is necessary. How Blockchain Is Reshaping Blockchain Based EHR Management System BCT SS V can be your best option for delivering a presentation. Represent everything in detail using How Blockchain Is Reshaping Blockchain Based EHR Management System BCT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases system architecture of blockchain-based Electronic Health Record EHR management system implemented to ensures tamper-proof storage of medical data. It includes components such as users, blockchain handshaker, distributed ledger, smart contract, public blockchain network, cloud-based EHR system, and cloud database.

Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Deliver an awe inspiring pitch with this creative Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF bundle. Topics like Processing Data, Information, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Intelligent Computing System Sensing Components Of Cyber Physical Systems Elements PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Sensing Components Of Cyber Physical Systems Elements PDF bundle. Topics like Information Acquired, Analyze, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Estate Construction And Engineering Company Profile Table Of Contents Topics PDF
Deliver an awe inspiring pitch with this creative Real Estate Construction And Engineering Company Profile Table Of Contents Topics PDF bundle. Topics like Line Expansion, Security Consulting, Sourcing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
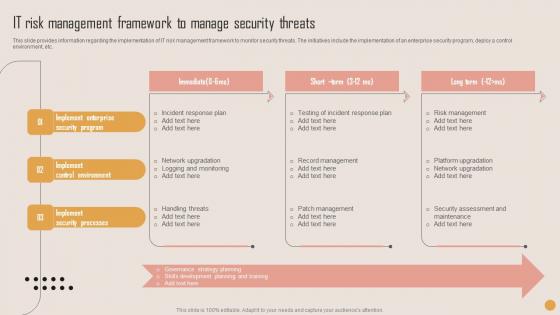
IT Risk Management Framework Playbook For Strategic Actions To Improve IT Performance Topics Pdf
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download IT Risk Management Framework Playbook For Strategic Actions To Improve IT Performance Topics Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the IT Risk Management Framework Playbook For Strategic Actions To Improve IT Performance Topics Pdf. This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc.

Big Data Analysis Requirements Ppt Professional Format Ideas PDF
Deliver and pitch your topic in the best possible manner with this big data analysis requirements ppt professional format ideas pdf. Use them to share invaluable insights on data movement, existing skills, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
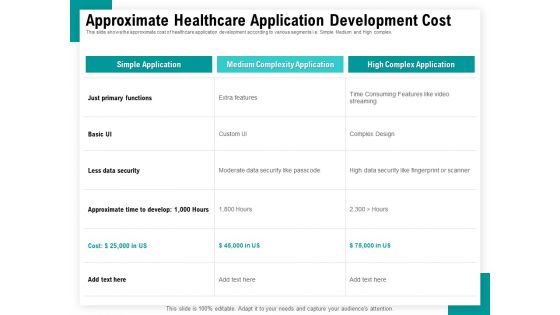
Android Framework For Apps Development And Deployment Approximate Healthcare Application Development Cost Structure PDF
Presenting this set of slides with name android framework for apps development and deployment approximate healthcare application development cost structure pdf. The topics discussed in these slides are simple application, medium complexity application, high complex application, extra features, moderate data security like passcode. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
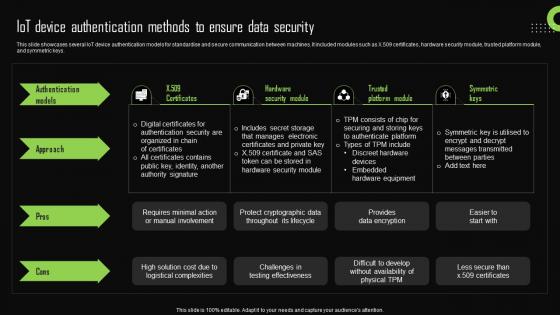
Iot Device Authentication Methods To Ensure Data Iot Device Management Download Pdf
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.

Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file-sharing options and spam and viruses overwhelming email systems. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file-sharing options and spam and viruses overwhelming email systems.
Banners With Globe Bulb Clock And Lock Icons Powerpoint Templates
This PowerPoint template has been designed with graphics of banners with business icons. You may use this slide to display global technology and security concepts. This diagram provides an effective way of displaying information you can edit text, color, shade and style as per you need.

Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers customer reviews about the email security company. It includes positive feedback related to user-friendly secure email software, helpful and professional team, seamless integration with Gmail. Create an editable Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide covers customer reviews about the email security company. It includes positive feedback related to user-friendly secure email software, helpful and professional team, seamless integration with Gmail.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

API Integration Software Development Present Application Programming Interface Issues Designs PDF
Presenting this set of slides with name api integration software development present application programming interface issues designs pdf. This is a four stage process. The stages in this process are technological complexity, security risks, high consumption of time, expensive. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.
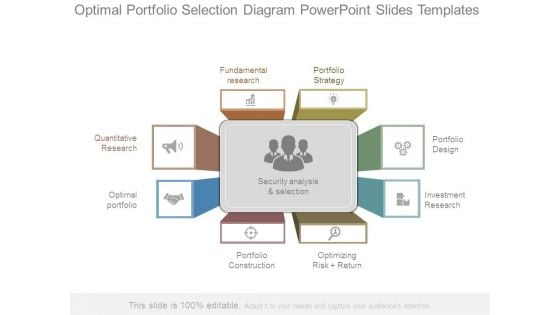
Optimal Portfolio Selection Diagram Powerpoint Slides Templates
This is a optimal portfolio selection diagram powerpoint slides templates. This is a eight stage process. The stages in this process are quantitative research, optimal portfolio, fundamental research, portfolio construction, security analysis and selection, portfolio strategy, optimizing risk return, portfolio design, investment research.
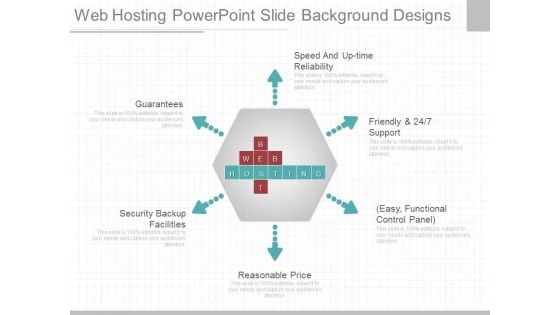
Web Hosting Powerpoint Slide Background Designs
This is a web hosting powerpoint slide background designs. This is a six stage process. The stages in this process are speed and up time reliability, friendly and support, easy, functional control panel, reasonable price, security backup facilities, guarantees, best, web, hosting.

API Management For Building Software Applications Present Application Programming Interface Issues Guidelines PDF
Presenting this set of slides with name api management for building software applications present application programming interface issues guidelines pdf. This is a four stage process. The stages in this process are technological complexity, security risks, high consumption time, expensive. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
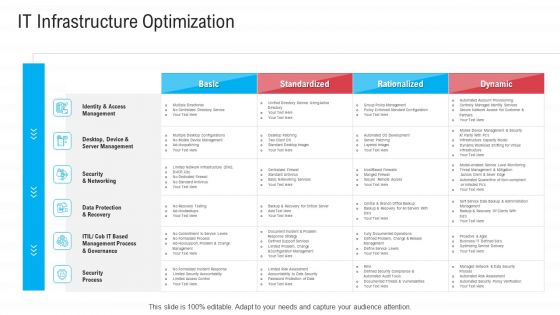
Infrastructure Designing And Administration IT Infrastructure Optimization Portrait PDF
Deliver an awe inspiring pitch with this creative infrastructure designing and administration it infrastructure optimization portrait pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
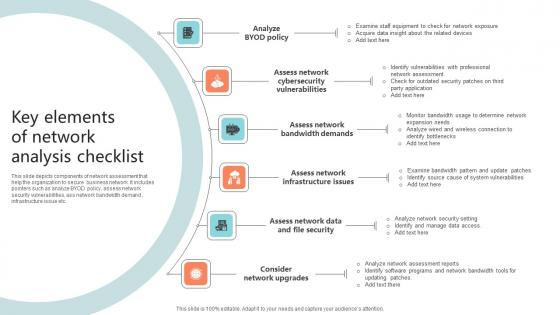
Key Elements Of Network Analysis Checklist Microsoft Pdf
This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.Pitch your topic with ease and precision using this Key Elements Of Network Analysis Checklist Microsoft Pdf This layout presents information on Cybersecurity Vulnerabilities, Bandwidth Demands, Assess Network It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
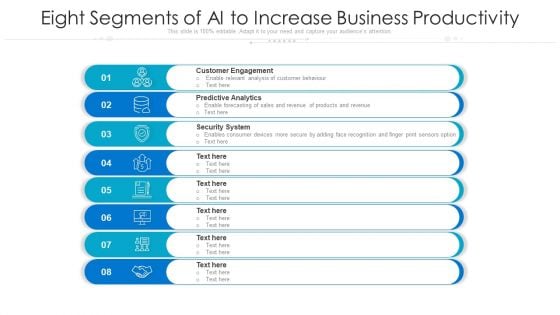
Eight Segments Of AI To Increase Business Productivity Ppt PowerPoint Presentation File Background Designs PDF
Presenting eight segments of ai to increase business productivity ppt powerpoint presentation file background designs pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including customer engagement, predictive analytics, security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































