Security Architecture
Construction Sector Project Risk Management Impact Of Mobile Devices On Safety Template PDF
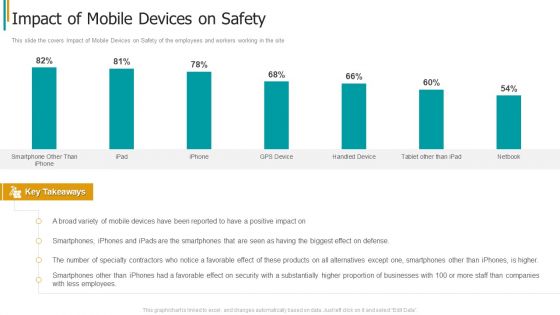
This slide the covers Impact of Mobile Devices on Safety of the employees and workers working in the site. Deliver an awe inspiring pitch with this creative construction sector project risk management impact of mobile devices on safety template pdf bundle. Topics like businesses, substantially, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
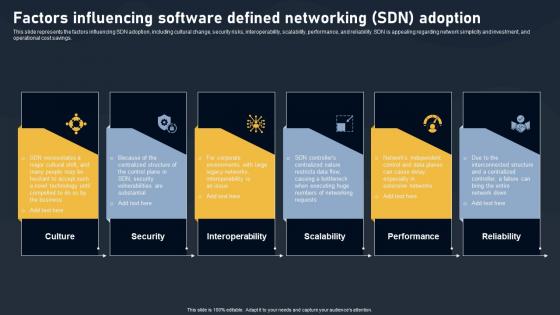
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.
Large Event Safety And Conveyance Plan Checklist Portrait Pdf
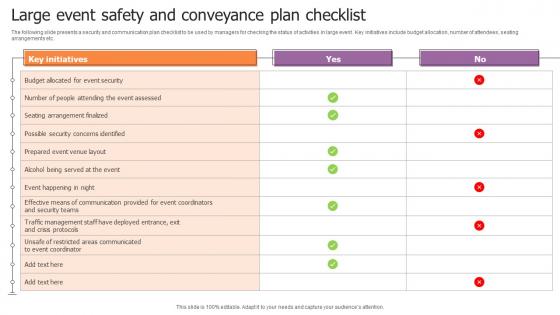
The following slide presents a security and communication plan checklist to be used by managers for checking the status of activities in large event. Key initiatives include budget allocation, number of attendees, seating arrangements etc. Pitch your topic with ease and precision using this Large Event Safety And Conveyance Plan Checklist Portrait Pdf. This layout presents information on Key Initiatives, Safety And Conveyance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide presents a security and communication plan checklist to be used by managers for checking the status of activities in large event. Key initiatives include budget allocation, number of attendees, seating arrangements etc.

Unlocking The Potential Of Risks Associated With Blockchain Based Gaming BCT SS V
This slide highlights various risks associated with blockchain powered gaming ecosystem. It includes cryptocurrency volatility, security vulnerabilities, scalability issue, user adoption complexity and market saturation. This modern and well-arranged Unlocking The Potential Of Risks Associated With Blockchain Based Gaming BCT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide highlights various risks associated with blockchain powered gaming ecosystem. It includes cryptocurrency volatility, security vulnerabilities, scalability issue, user adoption complexity and market saturation.
Before Vs After Zero Trust Network Access Brochure Pdf
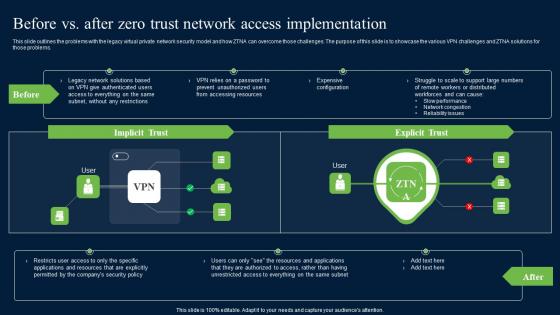
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Implement General Data Protection Regulation DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.
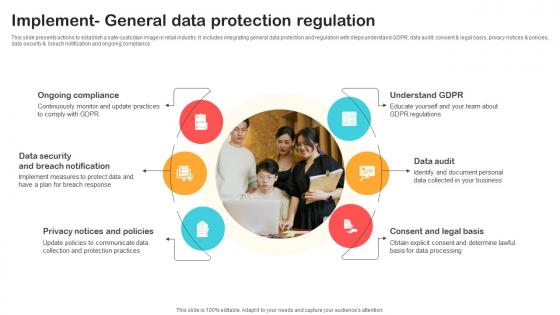
Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.

Enhancing Information Technology With Strategic IT Risk Management Framework Graphics PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Slidegeeks is here to make your presentations a breeze with Enhancing Information Technology With Strategic IT Risk Management Framework Graphics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Workplace Portable Device Monitoring And Administration Determining Roles And Responsibilities For Risk Handling Designs PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. This modern and well arranged Workplace Portable Device Monitoring And Administration Determining Roles And Responsibilities For Risk Handling Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
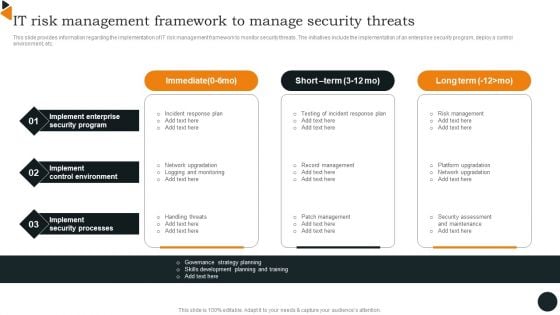
Chief Information Officers Guide On Technology Plan IT Risk Management Framework Infographics PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Chief Information Officers Guide On Technology Plan IT Risk Management Framework Infographics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
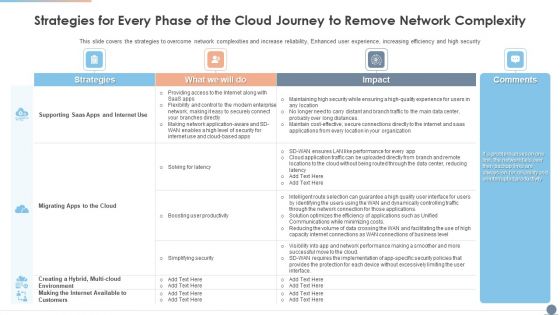
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Deliver and pitch your topic in the best possible manner with this Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF. Use them to share invaluable insights on Environment, Strategies, Productivity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
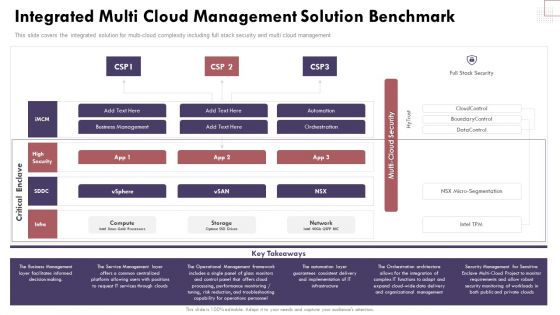
Integrated Multi Cloud Management Solution Benchmark Cloud Computing Complexities And Solutions Graphics PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management.Find a pre-designed and impeccable Integrated Multi Cloud Management Solution Benchmark Cloud Computing Complexities And Solutions Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
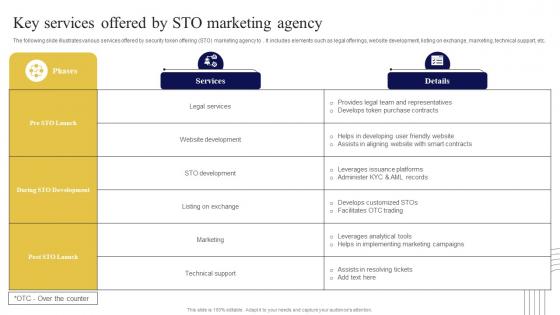
Key Services Offered By STO Exploring Investment Opportunities Topics Pdf
The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc. Slidegeeks has constructed Key Services Offered By STO Exploring Investment Opportunities Topics Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc.
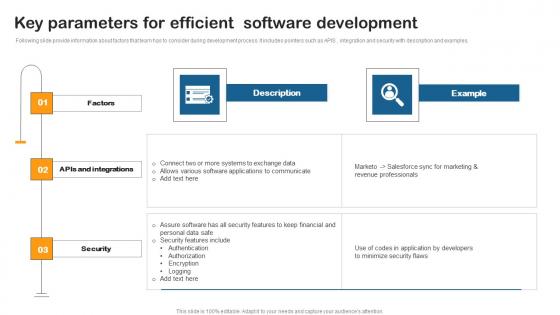
Key Parameters Efficient Software Building Utility Billing Invoicing Management System Mockup Pdf
Following slide provide information about factors that team has to consider during development process. It includes pointers such as APIS , integration and security with description and examples. This modern and well arranged Key Parameters Efficient Software Building Utility Billing Invoicing Management System Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide provide information about factors that team has to consider during development process. It includes pointers such as APIS , integration and security with description and examples.

R78 Solutions To Challenges Faced In Implementing Product Analytics Implementation Data Analytics V
This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solutions To Challenges Faced In R78 Solutions To Challenges Faced In Implementing Product Analytics Implementation Data Analytics V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality.
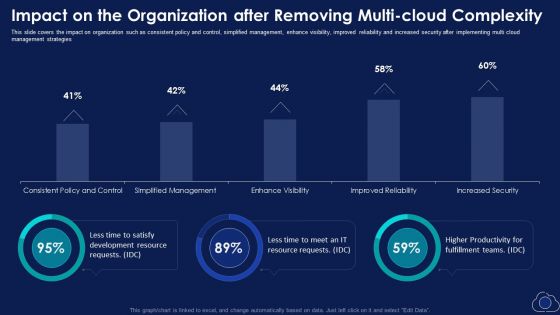
Impact On The Organization After Removing Multi Cloud Complexity Portrait PDF
This slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies. Deliver an awe inspiring pitch with this creative Impact On The Organization After Removing Multi Cloud Complexity Portrait PDF bundle. Topics like Development Resource, Productivity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Multiple AML Technology Integration Challenges Mapping Out The Anti Money Fin SS V
The following slide presents various challenges faced during AML and technology integration that hinders the operational process. The different challenges are data security concerns, integrity complexity, cost constraints, and regulatory challenges. Do you know about Slidesgeeks Multiple AML Technology Integration Challenges Mapping Out The Anti Money Fin SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide presents various challenges faced during AML and technology integration that hinders the operational process. The different challenges are data security concerns, integrity complexity, cost constraints, and regulatory challenges.
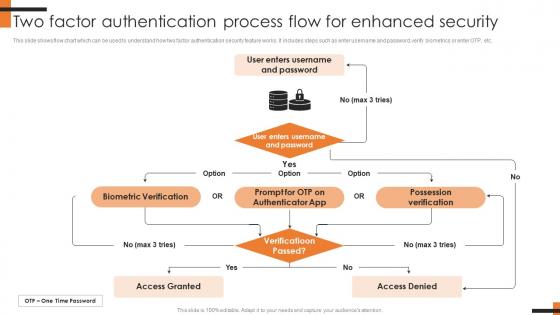
Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. The Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
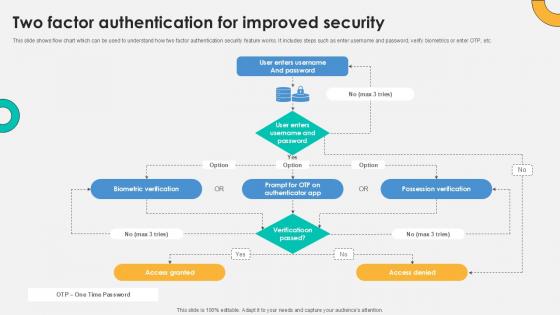
Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
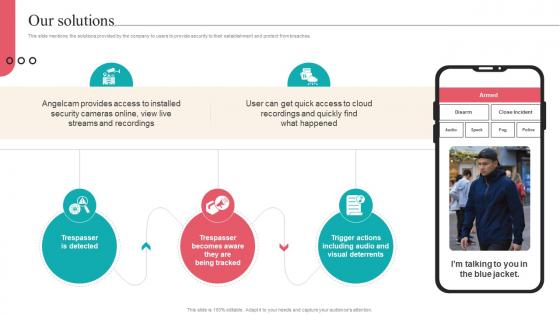
Our Solutions Camera Management Platform Investor Funding Elevator Pitch Deck
This slide mentions the solutions provided by the company to users to provide security to their establishment and protect from breaches. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Our Solutions Camera Management Platform Investor Funding Elevator Pitch Deck template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Our Solutions Camera Management Platform Investor Funding Elevator Pitch Deck that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide mentions the solutions provided by the company to users to provide security to their establishment and protect from breaches.
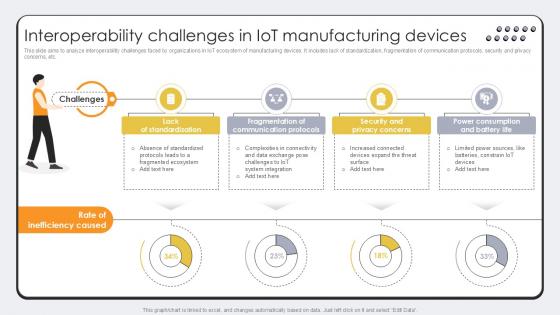
Interoperability Challenges In Revolutionizing Production IoT Ppt Sample
This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc. Slidegeeks has constructed Interoperability Challenges In Revolutionizing Production IoT Ppt Sample after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc.

Problem Statement Travel Technology Company Business Model BMC SS V
This slide showcases the major problems addressed by company. The problems covered are complex booking procedures, hidden charges and data security threats. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Travel Technology Company Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Travel Technology Company Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the major problems addressed by company. The problems covered are complex booking procedures, hidden charges and data security threats.
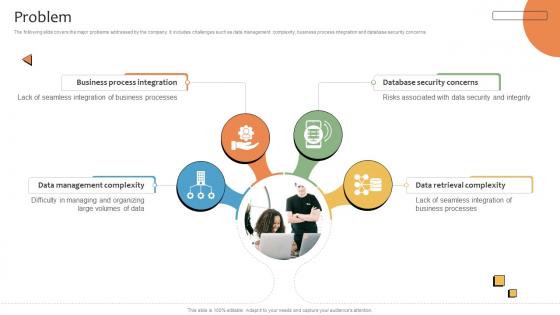
Problem CRMS Platform Business Model BMC SS V
The following slide covers the major problems addressed by the company. It includes challenges such as data management complexity, business process integration and database security concerns. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem CRMS Platform Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem CRMS Platform Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide covers the major problems addressed by the company. It includes challenges such as data management complexity, business process integration and database security concerns.

Seamless Integration The Power Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Seamless Integration The Power Comparative Analysis Of Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases.

Understanding Various Blockchain Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. Present like a pro with Understanding Various Blockchain Comparative Analysis Of Blockchain Interoperability BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases.
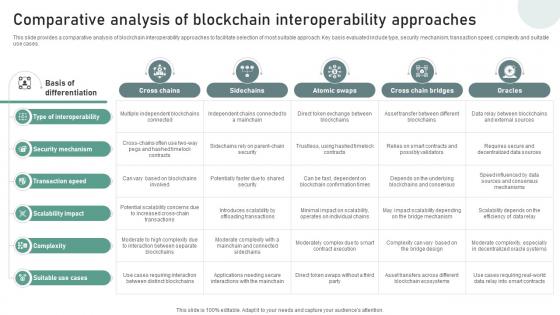
Bridging Blockchains A Deep Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Bridging Blockchains A Deep Comparative Analysis Of Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases.
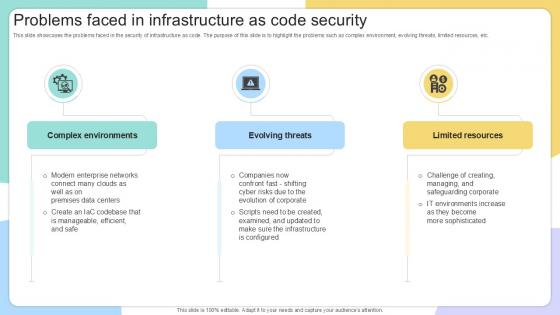
Problems Faced In Infrastructure As IAC Tools For Performance Analysis PPT PowerPoint
This slide showcases the problems faced in the security of infrastructure as code. The purpose of this slide is to highlight the problems such as complex environment, evolving threats, limited resources, etc. Present like a pro with Problems Faced In Infrastructure As IAC Tools For Performance Analysis PPT PowerPoint. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the problems faced in the security of infrastructure as code. The purpose of this slide is to highlight the problems such as complex environment, evolving threats, limited resources, etc.
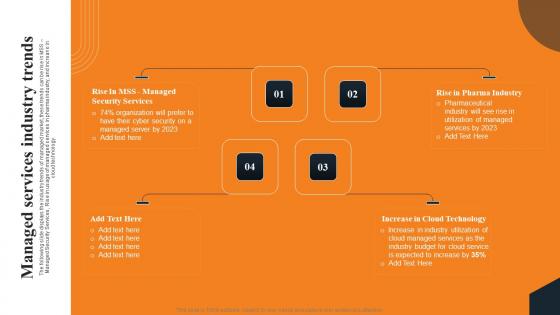
Managed Services Industry Trends Layered Pricing Strategy For Managed Services Brochure Pdf
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. This modern and well arranged Managed Services Industry Trends Layered Pricing Strategy For Managed Services Brochure Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology.
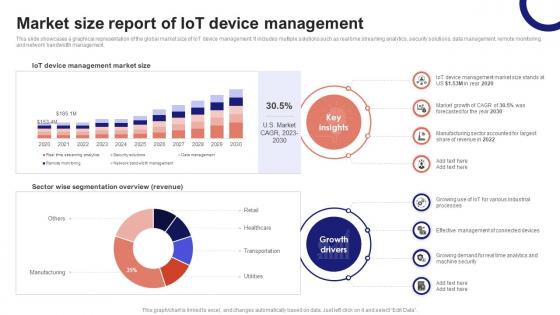
IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT Ss V
This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management. Slidegeeks has constructed IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management.
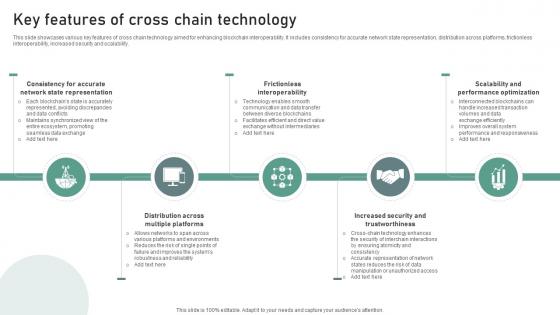
Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Slidegeeks has constructed Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
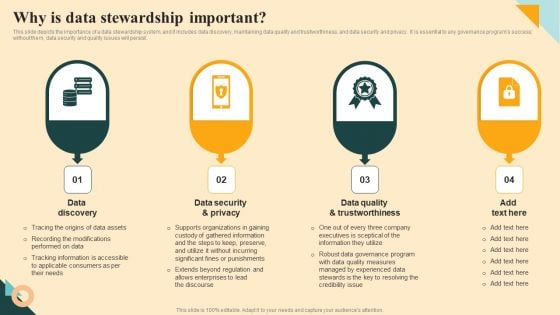
Why Is Data Stewardship Important Sample PDF
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. Slidegeeks has constructed Why Is Data Stewardship Important Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
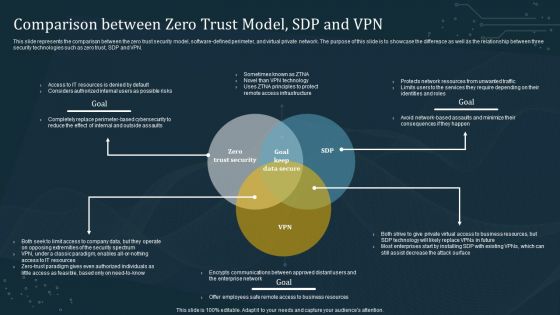
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Strategic Influencer Marketing Plan To Create Exploring Investment Opportunities Ideas Pdf
The following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc. Slidegeeks has constructed Strategic Influencer Marketing Plan To Create Exploring Investment Opportunities Ideas Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc.
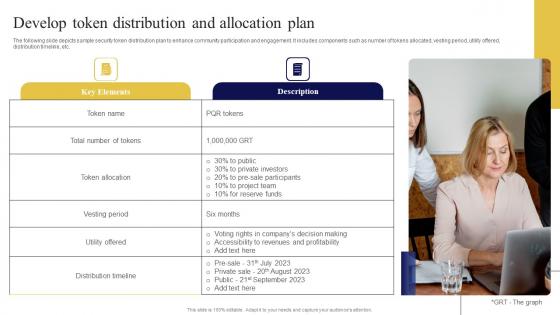
Develop Token Distribution And Exploring Investment Opportunities Template Pdf
The following slide depicts sample security token distribution plan to enhance community participation and engagement. It includes components such as number of tokens allocated, vesting period, utility offered, distribution timeline, etc. Cafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Develop Token Distribution And Exploring Investment Opportunities Template Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Develop Token Distribution And Exploring Investment Opportunities Template Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide depicts sample security token distribution plan to enhance community participation and engagement. It includes components such as number of tokens allocated, vesting period, utility offered, distribution timeline, etc.
Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
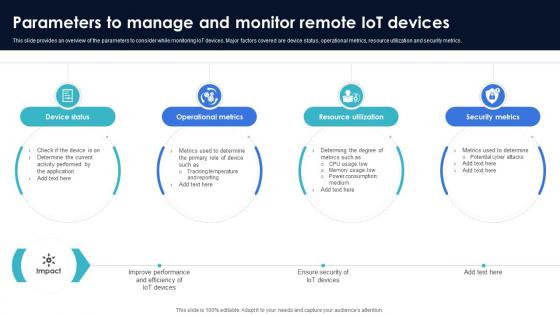
Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V
This slide provides an overview of the parameters to consider while monitoring IoT devices. Major factors covered are device status, operational metrics, resource utilization and security metrics. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides an overview of the parameters to consider while monitoring IoT devices. Major factors covered are device status, operational metrics, resource utilization and security metrics.
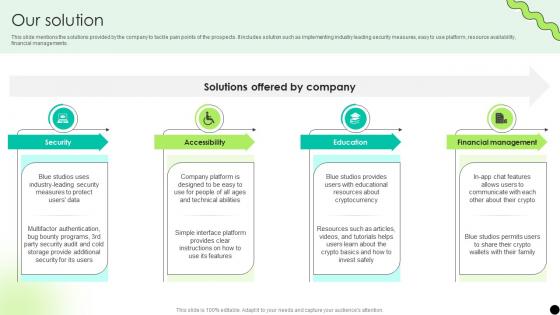
Our Solution Digital Payment Platform Pitch Deck
This slide mentions the solutions provided by the company to tackle pain points of the prospects. It includes solution such as implementing industry leading security measures, easy to use platform, resource availability, financial managements. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Our Solution Digital Payment Platform Pitch Deck template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Our Solution Digital Payment Platform Pitch Deck that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide mentions the solutions provided by the company to tackle pain points of the prospects. It includes solution such as implementing industry leading security measures, easy to use platform, resource availability, financial managements.

IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT Ss V
This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc.
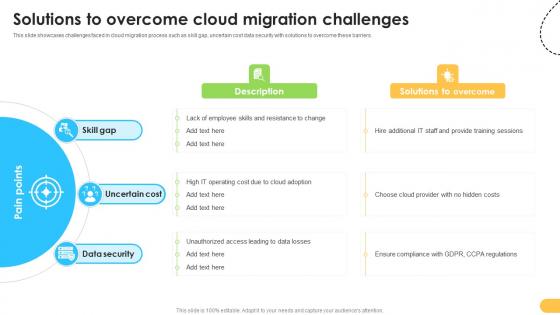
Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises
This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers. Slidegeeks has constructed Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers.

Statistical Analysis Challenges Data Analytics For Informed Decision Ppt Example
The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints. Slidegeeks has constructed Statistical Analysis Challenges Data Analytics For Informed Decision Ppt Example after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints.
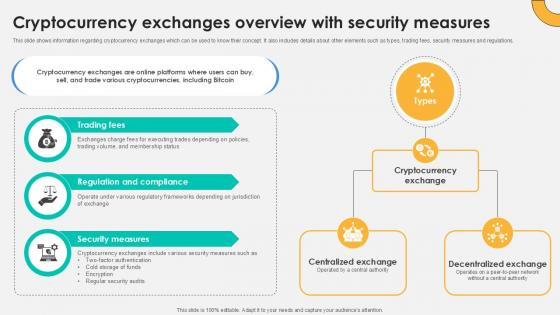
Cryptocurrency Exchanges Overview Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cryptocurrency Exchanges Overview Everything About Bitcoin PPT PowerPoint Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cryptocurrency Exchanges Overview Everything About Bitcoin PPT PowerPoint Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations.

Multiple Risks Associated With Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows detailed information which can be used to evaluate various types of risks associated with Bitcoin . These risks are price volatility, regulatory uncertainty, security vulnerabilities, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Multiple Risks Associated With Everything About Bitcoin PPT PowerPoint Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Multiple Risks Associated With Everything About Bitcoin PPT PowerPoint Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide shows detailed information which can be used to evaluate various types of risks associated with Bitcoin . These risks are price volatility, regulatory uncertainty, security vulnerabilities, etc.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
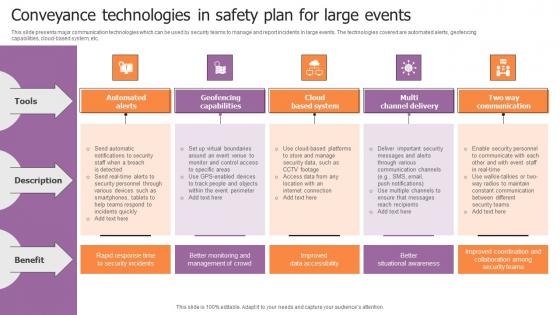
Conveyance Technologies In Safety Plan For Large Events Brochure Pdf
This slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud-based system, etc. Showcasing this set of slides titled Conveyance Technologies In Safety Plan For Large Events Brochure Pdf. The topics addressed in these templates are Automated Alerts, Geofencing Capabilities, Cloud Based System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud-based system, etc.
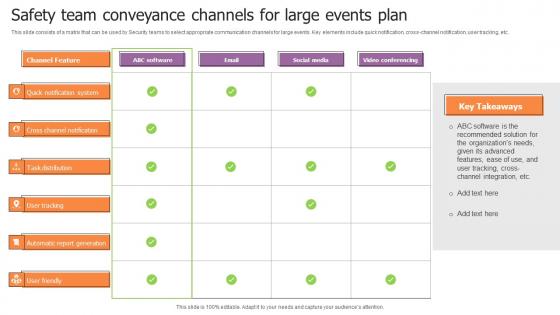
Safety Team Conveyance Channels For Large Events Plan Brochure Pdf
This slide consists of a matrix that can be used by Security teams to select appropriate communication channels for large events. Key elements include quick notification, cross-channel notification, user tracking, etc. Showcasing this set of slides titled Safety Team Conveyance Channels For Large Events Plan Brochure Pdf. The topics addressed in these templates are Channel Feature, Software, Email, Social Media. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide consists of a matrix that can be used by Security teams to select appropriate communication channels for large events. Key elements include quick notification, cross-channel notification, user tracking, etc.
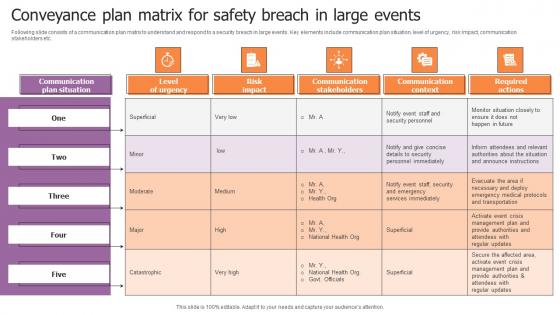
Conveyance Plan Matrix For Safety Breach In Large Events Diagrams Pdf
Following slide consists of a communication plan matrix to understand and respond to a security breach in large events. Key elements include communication plan situation, level of urgency, risk impact, communication stakeholders etc. Pitch your topic with ease and precision using this Conveyance Plan Matrix For Safety Breach In Large Events Diagrams Pdf. This layout presents information on Level Of Urgency, Risk Impact, Communication Stakeholders. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide consists of a communication plan matrix to understand and respond to a security breach in large events. Key elements include communication plan situation, level of urgency, risk impact, communication stakeholders etc.

Incident Conveyance Plan Timeline For Safety Teams In Large Events Inspiration Pdf
The following slide presents an Incident communication plan timeline to be followed by security teams in case of breach or mishappening in large events. Key elements covered are incident communicated by attendee or staff, incident verified, action plan developed, etc. Showcasing this set of slides titled Incident Conveyance Plan Timeline For Safety Teams In Large Events Inspiration Pdf. The topics addressed in these templates are Operations Resume, Treatment Validation . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide presents an Incident communication plan timeline to be followed by security teams in case of breach or mishappening in large events. Key elements covered are incident communicated by attendee or staff, incident verified, action plan developed, etc.
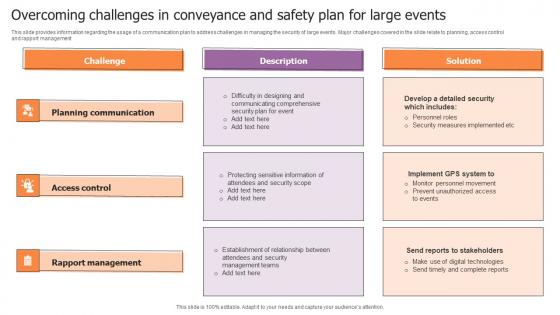
Overcoming Challenges In Conveyance And Safety Plan For Large Events Clipart Pdf
This slide provides information regarding the usage of a communication plan to address challenges in managing the security of large events. Major challenges covered in the slide relate to planning, access control and rapport management. Pitch your topic with ease and precision using this Overcoming Challenges In Conveyance And Safety Plan For Large Events Clipart Pdf. This layout presents information on Planning Communication, Access Control, Rapport Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides information regarding the usage of a communication plan to address challenges in managing the security of large events. Major challenges covered in the slide relate to planning, access control and rapport management.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

IoT Device Management Fundamentals IoT Technologies Utilised In Smart Homes IoT Ss V
This slide showcase smart home devices intended to make home more conformable and safer. These devices include smart thermostat, smart leak detectors, lighting, smart home, smart security cameras, and smart locks. This modern and well-arranged IoT Device Management Fundamentals IoT Technologies Utilised In Smart Homes IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcase smart home devices intended to make home more conformable and safer. These devices include smart thermostat, smart leak detectors, lighting, smart home, smart security cameras, and smart locks.
Strategies For Conveyance Of Large Event Safety Plan Icons Pdf
This slide highlights major strategies to communicate effectively for large event security plans in order to ensure the safety of the business and enhance confidence among stakeholders. Key strategies are to inspect the venue, conduct a risk assessment, assess large-scale attacks, etc. Pitch your topic with ease and precision using this Strategies For Conveyance Of Large Event Safety Plan Icons Pdf. This layout presents information on Inspect The Venue, Conduct Risk Assessment, Crowd Controlling Measures. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights major strategies to communicate effectively for large event security plans in order to ensure the safety of the business and enhance confidence among stakeholders. Key strategies are to inspect the venue, conduct a risk assessment, assess large-scale attacks, etc.
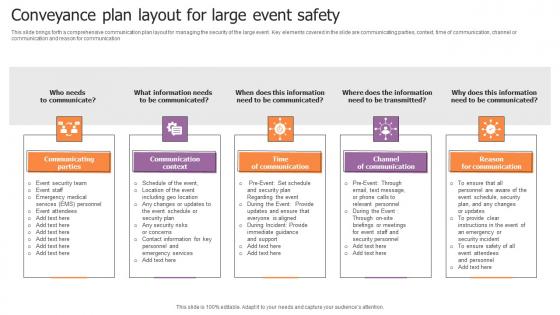
Conveyance Plan Layout For Large Event Safety Themes Pdf
This slide brings forth a comprehensive communication plan layout for managing the security of the large event. Key elements covered in the slide are communicating parties, context, time of communication, channel or communication and reason for communication. Showcasing this set of slides titled Conveyance Plan Layout For Large Event Safety Themes Pdf. The topics addressed in these templates are Communicating Parties, Communication Context, Time Of Communication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a comprehensive communication plan layout for managing the security of the large event. Key elements covered in the slide are communicating parties, context, time of communication, channel or communication and reason for communication.
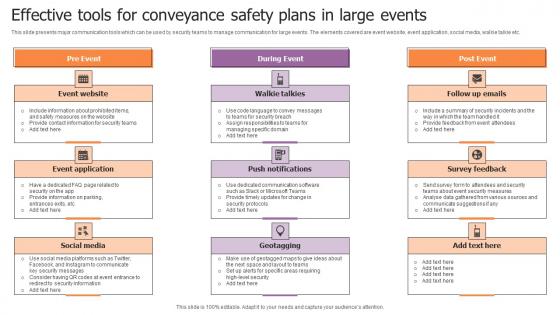
Effective Tools For Conveyance Safety Plans In Large Events Sample Pdf
This slide presents major communication tools which can be used by security teams to manage communication for large events. The elements covered are event website, event application, social media, walkie talkie etc. Showcasing this set of slides titled Effective Tools For Conveyance Safety Plans In Large Events Sample Pdf. The topics addressed in these templates are Event Website, Walkie Talkies, Push Notifications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents major communication tools which can be used by security teams to manage communication for large events. The elements covered are event website, event application, social media, walkie talkie etc.
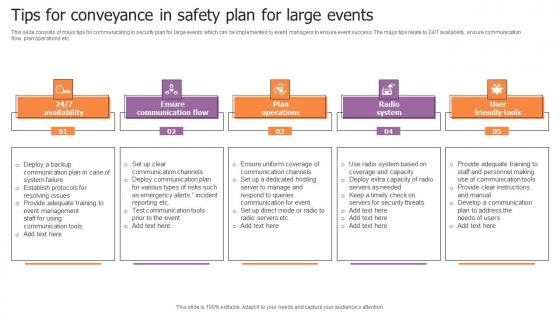
Tips For Conveyance In Safety Plan For Large Events Sample Pdf
This slide consists of major tips for communicating in security plan for large events which can be implemented by event managers to ensure event success. The major tips relate to 247 availability, ensure communication flow, plan operations etc. Showcasing this set of slides titled Tips For Conveyance In Safety Plan For Large Events Sample Pdf. The topics addressed in these templates are Ensure Communication Flow, Plan Operations, Radio System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide consists of major tips for communicating in security plan for large events which can be implemented by event managers to ensure event success. The major tips relate to 247 availability, ensure communication flow, plan operations etc.
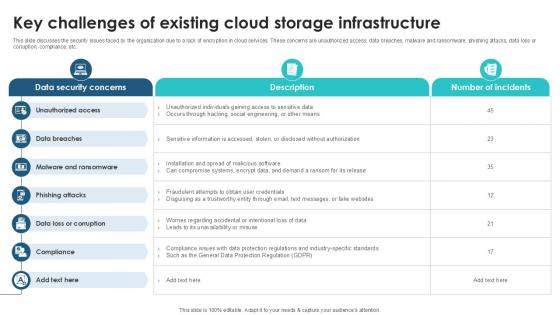
Key Challenges Of Existing Cloud Client Side Encryption PPT Slide
This slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc. This modern and well-arranged Key Challenges Of Existing Cloud Client Side Encryption PPT Slide provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc.
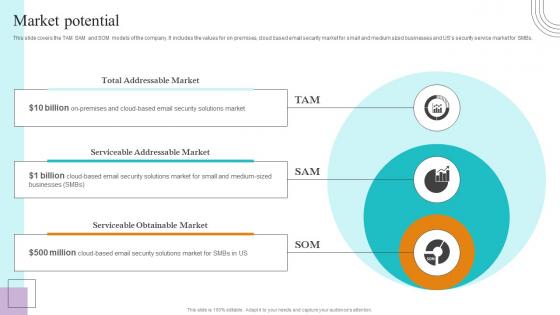
Market Potential Paubox Capital Funding Pitch Deck Diagrams Pdf
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. This modern and well arranged Market Potential Paubox Capital Funding Pitch Deck Diagrams Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.
Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf
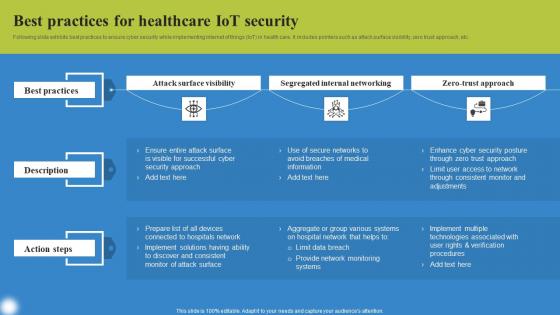
Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. This modern and well arranged Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc.

Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V
This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights. This modern and well-arranged Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights.


 Continue with Email
Continue with Email

 Home
Home


































