Security Assessment

Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.
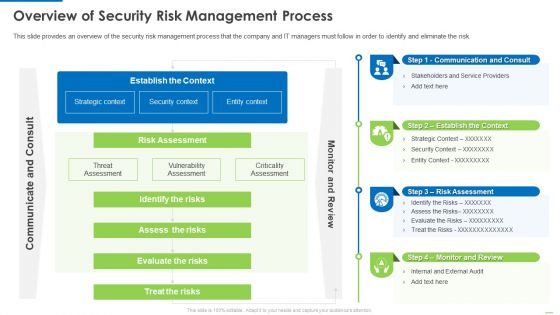
Overview Of Security Risk Management Process Demonstration PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver and pitch your topic in the best possible manner with this Overview of security risk management process demonstration pdf. Use them to share invaluable insights on identify the risks, assess the risks, evaluate the risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Training Program Frameworks Ppt Outline Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this security training program frameworks ppt outline layout ideas pdf. Use them to share invaluable insights on requirements, metrics, systems security, materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
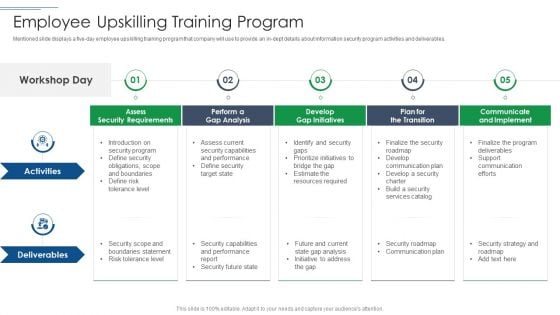
IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables. This is a IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Develop Gap Initiatives, Communicate And Implement, Assess Security Requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Companys Data Safety Recognition Security Training Program Frameworks Icons PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative companys data safety recognition security training program frameworks icons pdf bundle. Topics like requirements, target audience, metrics, training materials can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Breach Prevention Recognition Security Training Program Frameworks Mockup PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security training program frameworks mockup pdf. Use them to share invaluable insights on target audience, training success, instruction information sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Solution Security PowerPoint Templates And PowerPoint Themes 0512
Key Solution Security PowerPoint Templates And PowerPoint Themes PPT designs-Microsoft Powerpoint Templates and Background with solution concept Experiment and evaluate with our Key Solution Security PowerPoint Templates And PowerPoint Themes 0512. Be assured of accurate results.

National Security France PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Download and present our Business PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Use our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Present our Signs PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter.Use these PowerPoint slides for presentations relating to Key with french flag, security, success, business, shapes, signs. The prominent colors used in the PowerPoint template are Blue navy, White, Red. We assure you our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter successul in his career/life. Professionals tell us our security PowerPoint templates and PPT Slides will save the presenter time. We assure you our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 look good visually. The feedback we get is that our security PowerPoint templates and PPT Slides are incredible easy to use. Customers tell us our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. Customers tell us our french PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Say farewell to uncertainties with our National Security France PowerPoint Templates Ppt Backgrounds For Slides 0113. They help ensure desired results.
Identification Theft Alert Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with identification theft alert on a monitor with reflections Evaluate performance with our Identification Theft Alert Security PowerPoint Backgrounds And Templates 1210. They help you deliver with accuracy.
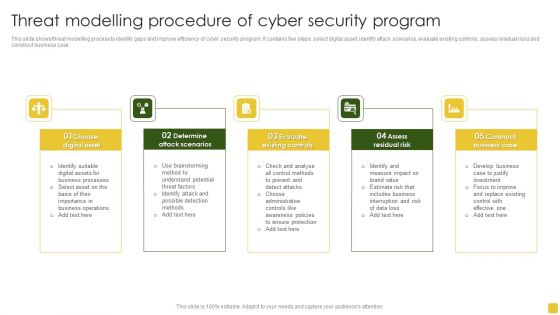
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF Use them to share invaluable insights on Assessing Information Security, Safeguarding Valuable, Vulnerability Intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Locked House Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Secuity PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download and present our Real estate PowerPoint Templates because Your audience will believe you are the cats whiskers. Present our Business PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Present our Construction PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team.Use these PowerPoint slides for presentations relating to Key with house, security, success, real estate, business, construction. The prominent colors used in the PowerPoint template are Blue, White, Gray. We assure you our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our real PowerPoint templates and PPT Slides are second to none. Presenters tell us our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Professionals tell us our real PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. The feedback we get is that our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides will help them to explain complicated concepts. Experience acclaim with our Locked House Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Your thoughts will acquire true fame.
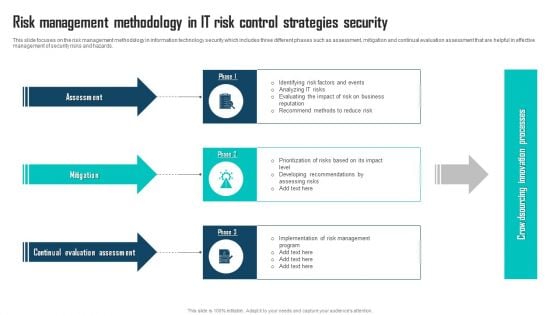
Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
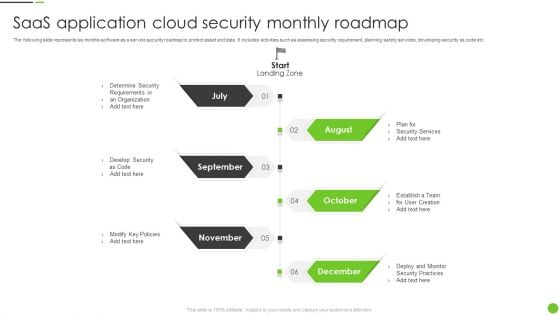
Saas Application Cloud Security Monthly Roadmap Ppt PowerPoint Presentation File Format PDF
The following slide represents six months software as a service security roadmap to protect asset and data. It includes activities such as assessing security requirement, planning safety services, developing security as code etc. Presenting Saas Application Cloud Security Monthly Roadmap Ppt PowerPoint Presentation File Format PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Determine Security, Develop Security, Modify Key Policies. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Solution Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Solution Key Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Real estate PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Present our Sales PowerPoint Templates because You can Bask in the warmth of our PowerPoint Templates and Slides. Enjoy the heartfelt glowing response of your listeners. Use our Marketing PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Download and present our Signs PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Download and present our Security PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Red house-shape key, real estate, sales, marketing, signs, security. The prominent colors used in the PowerPoint template are Red, Yellow, Gray. We assure you our Solution Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our real PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Presenters tell us our Solution Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Professionals tell us our real PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. The feedback we get is that our Solution Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. PowerPoint presentation experts tell us our signs PowerPoint templates and PPT Slides are incredible easy to use. Charge to success with our Solution Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113. You will come out on top.

Business Context Diagram 3d Man With Chain Security PowerPoint Slides
We present our business context diagram 3d man with chain security PowerPoint Slides.Download our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will effectively help you save your valuable time. They are readymade to fit into any presentation structure. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Use our Process and Flows PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time.Use these PowerPoint slides for presentations relating to 3d, Business, Chain, Connect, Connection, Heavy, Industrial, Industry, Isolated, Link, Linked, Man, Metal, Power, Powerful, Protection, Secure, Steel, Strength, Support, Symbol, Teamwork, Weak, White. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. The feedback we get is that our Industry PowerPoint templates and PPT Slides are designed to make your presentations professional. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Connection PowerPoint templates and PPT Slides are designed by professionals PowerPoint presentation experts tell us our business context diagram 3d man with chain security PowerPoint Slides look good visually. You can be sure our Industry PowerPoint templates and PPT Slides will make you look like a winner. You've found a treasure for presentations. Get goingwith our Business Context Diagram 3d Man With Chain Security PowerPoint Slides. You'll deliver your best presentation yet.
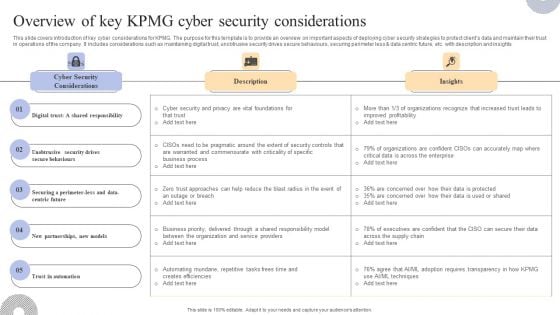
Overview Of Key KPMG Cyber Security Considerations Inspiration PDF
This slide covers an introduction to KPMG company ESG strategy to improve reporting to stakeholders. The purpose of this template is to provide overview on introducing ESG strategy, benefits along with reporting insights. It includes benefits such as helping organization assess and improve sustainable performance, establishing strong reputation and trust, attracting investors and customers, etc. Welcome to our selection of the Overview Of Key KPMG Cyber Security Considerations Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Overview Of Cyber Security Awareness Course Ppt Ideas Styles PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Slidegeeks is here to make your presentations a breeze with Overview Of Cyber Security Awareness Course Ppt Ideas Styles PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Effective IT Risk Management Process Impact On Security Infrastructure Structure PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this effective it risk management process impact on security infrastructure structure pdf. Use them to share invaluable insights on target, risk, performance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
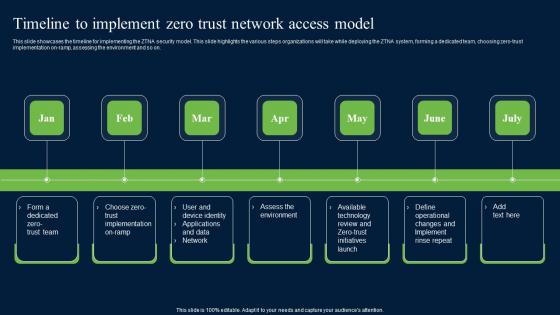
Timeline To Implement Zero Trust Network Security Themes Pdf
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Zero Trust Network Security Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Organizational Network Staff Learning Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
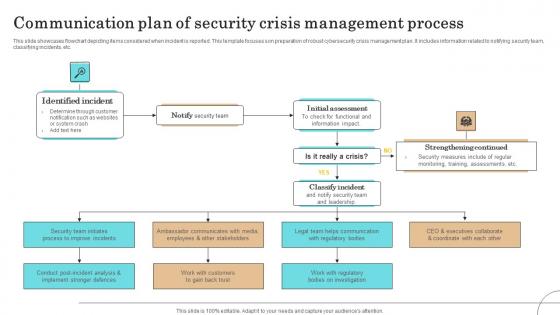
Communication Plan Of Security Crisis Management Process Pictures Pdf
This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.Pitch your topic with ease and precision using this Communication Plan Of Security Crisis Management Process Pictures Pdf This layout presents information on Identified Incident, Initial Assessment, Strengthening Continued It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.
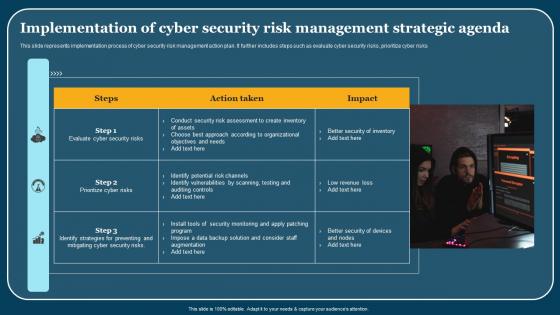
Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks.
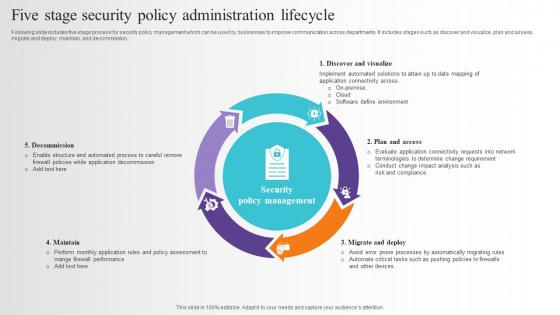
Five Stage Security Policy Administration Lifecycle Pictures Pdf
Following slide includes five stage process for security policy management which can be used by businesses to improve communication across departments. It includes stages such as discover and visualize, plan and assess, migrate and deploy, maintain, and decommission. Pitch your topic with ease and precision using this Five Stage Security Policy Administration Lifecycle Pictures Pdf. This layout presents information on Plan And Assess, Migrate And Deploy, Maintain, Decommission. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide includes five stage process for security policy management which can be used by businesses to improve communication across departments. It includes stages such as discover and visualize, plan and assess, migrate and deploy, maintain, and decommission.
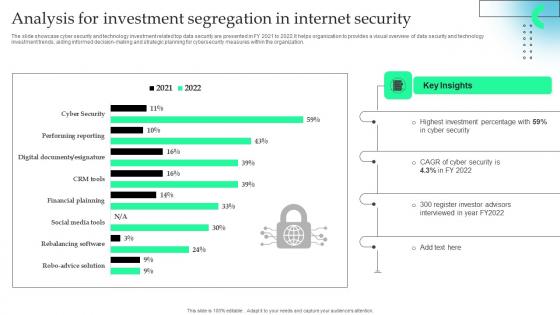
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.
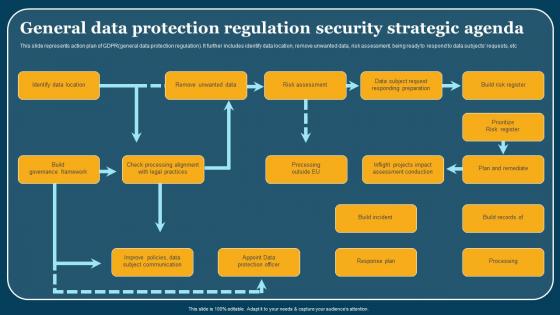
General Data Protection Regulation Security Strategic Agenda Formats Pdf
This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc. Pitch your topic with ease and precision using this General Data Protection Regulation Security Strategic Agenda Formats Pdf. This layout presents information on Identify Data Location, Build Governance Framework, Build Incident. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc.
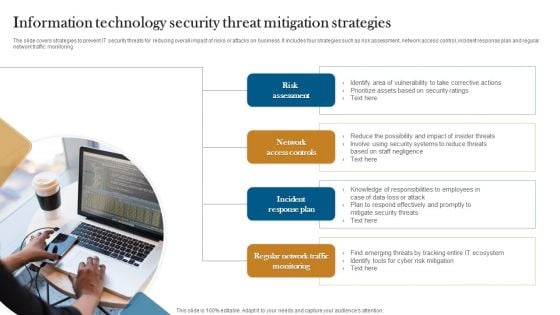
Information Technology Security Threat Mitigation Strategies Formats PDF
The slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring. Persuade your audience using this Information Technology Security Threat Mitigation Strategies Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment, Network Access Controls, Incident Response Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Overview Of Platform Tokenization In Data Security PPT Sample
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Find a pre-designed and impeccable Overview Of Platform Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.
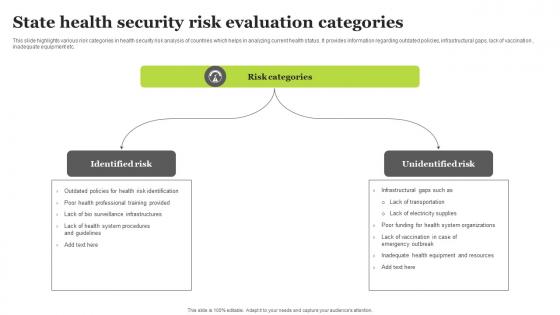
State Health Security Risk Evaluation Categories Sample Pdf
This slide highlights various risk categories in health security risk analysis of countries which helps in analyzing current health status. It provides information regarding outdated policies, infrastructural gaps, lack of vaccination , inadequate equipment etc. Showcasing this set of slides titled State Health Security Risk Evaluation Categories Sample Pdf. The topics addressed in these templates are Identified Risk, Unidentified Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights various risk categories in health security risk analysis of countries which helps in analyzing current health status. It provides information regarding outdated policies, infrastructural gaps, lack of vaccination , inadequate equipment etc.
Security Strategic Planning Process For CPS Ppt Slides Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver and pitch your topic in the best possible manner with this Security Strategic Planning Process For CPS Ppt Slides Icons PDF. Use them to share invaluable insights on Business Strategy, Technology Roadmap, Environmental Trends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today. This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security.

Data Security Agreement Operate Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name data security agreement operate ppt powerpoint presentation complete deck. The topics discussed in these slides are operate, data, accountability framework, data privacy, public interest, risk assessment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
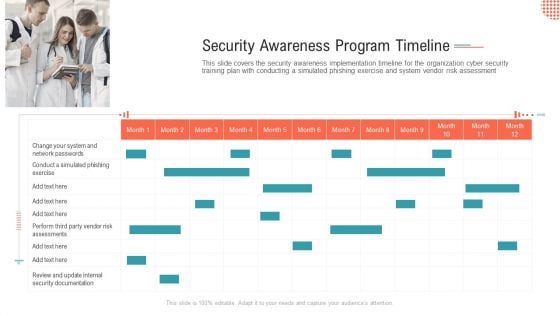
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Model Traditional Perimeter Based Network Security Overview
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Traditional Perimeter Based Network Security Overview is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Traditional Perimeter Based Network Security Overview and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
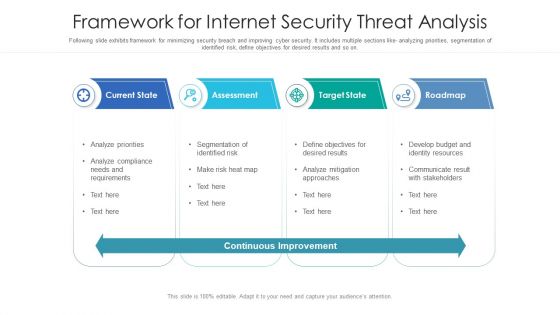
Framework For Internet Security Threat Analysis Structure PDF
Following slide exhibits framework for minimizing security breach and improving cyber security. It includes multiple sections like- analyzing priorities, segmentation of identified risk, define objectives for desired results and so on. Showcasing this set of slides titled framework for internet security threat analysis structure pdf. The topics addressed in these templates are current state, assessment, target state, roadmap. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Program Strategic Agenda Process Microsoft Pdf
This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc. Showcasing this set of slides titled Information Security Program Strategic Agenda Process Microsoft Pdf. The topics addressed in these templates are Assets And Inventory, Evaluate Risk, Manage Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc.
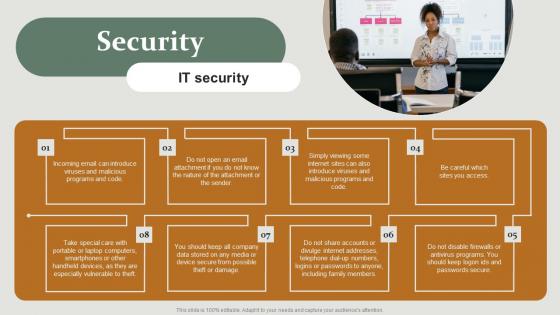
Security HR Policy Overview Powerpoint Presentation Ppt Template Pdf
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Security HR Policy Overview Powerpoint Presentation Ppt Template Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security HR Policy Overview Powerpoint Presentation Ppt Template Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. Our Security HR Policy Overview Powerpoint Presentation Ppt Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
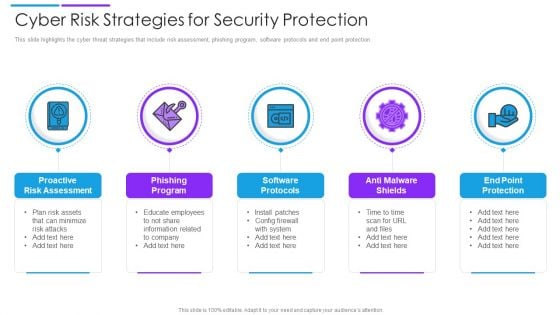
Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
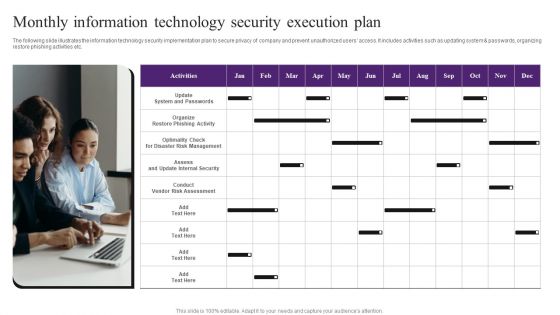
Monthly Information Technology Security Execution Plan Template PDF
The following slide illustrates the information technology security implementation plan to secure privacy of company and prevent unauthorized users access. It includes activities such as updating system and passwords, organizing restore phishing activities etc. Presenting Monthly Information Technology Security Execution Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Update System And Passwords, Conduct Vendor Risk Assessment, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
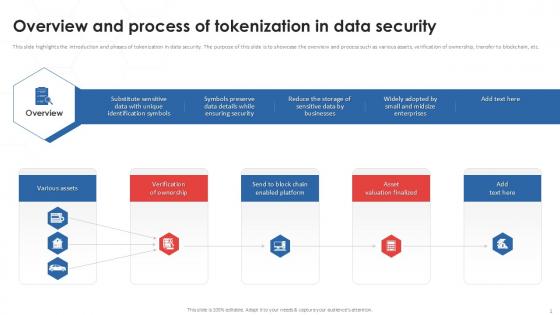
Overview And Process Of Tokenization In Data Security PPT Example
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Find a pre-designed and impeccable Overview And Process Of Tokenization In Data Security PPT Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc.
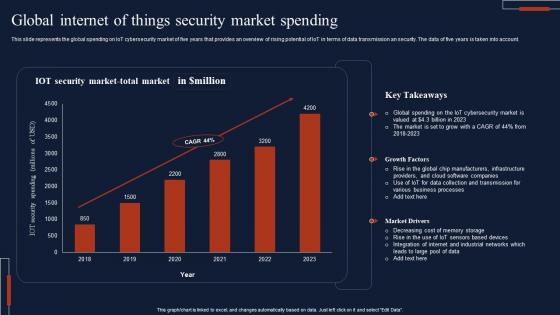
Global Internet Of Things Security Market Spending Download Pdf
This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account. Pitch your topic with ease and precision using this Global Internet Of Things Security Market Spending Download Pdf This layout presents information on IOT Security, Market Total, Key Takeaways It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account.
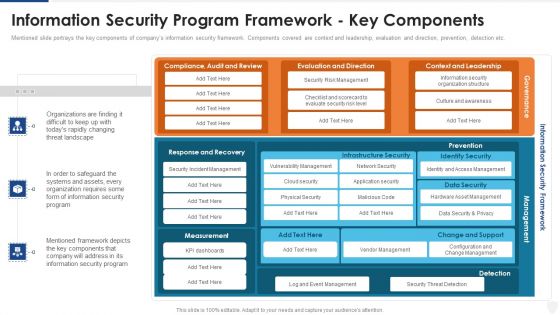
Information Security Program Framework Key Components Ppt Inspiration Ideas PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this information security program framework key components ppt inspiration ideas pdf. Use them to share invaluable insights on network security, application security, vendor management, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CASB 2 0 IT Cloud Security Standards And Control Frameworks
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. This CASB 2 0 IT Cloud Security Standards And Control Frameworks from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA.
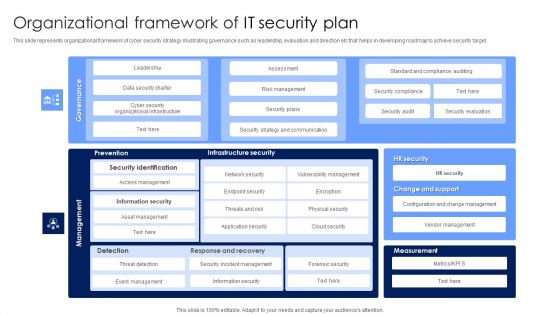
Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Crisis Communication Process Framework Icons PDF
This slide showcases a model of crisis communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Presenting Cyber Security Crisis Communication Process Framework Icons PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Implement Strategy, Identify Community, Set Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
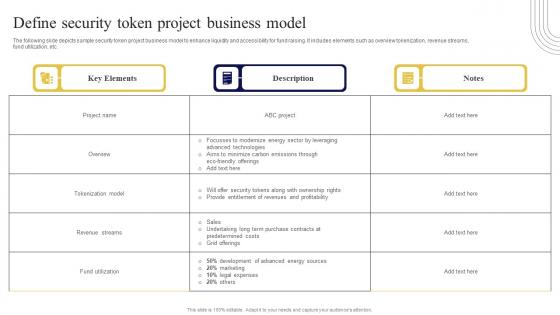
Define Security Token Project Business Exploring Investment Opportunities Ideas Pdf
The following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Define Security Token Project Business Exploring Investment Opportunities Ideas Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc.
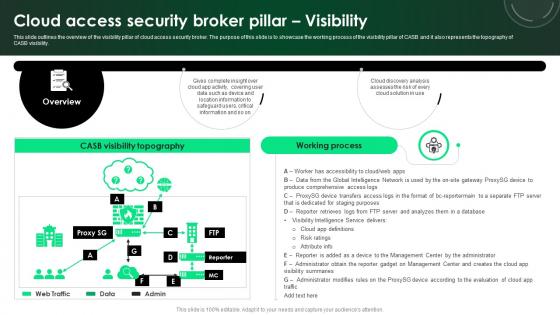
CASB 2 0 IT Cloud Access Security Broker Pillar Visibility
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Slidegeeks has constructed CASB 2 0 IT Cloud Access Security Broker Pillar Visibility after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility.
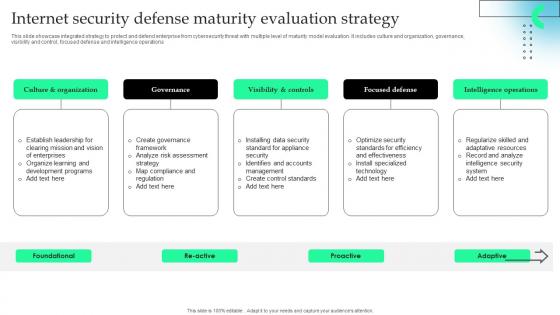
Internet Security Defense Maturity Evaluation Strategy Information Pdf
This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.Pitch your topic with ease and precision using this Internet Security Defense Maturity Evaluation Strategy Information Pdf This layout presents information on Visibility Controls, Focused Defense, Intelligence Operations It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.
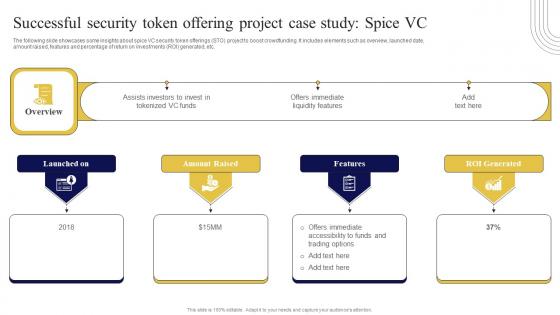
Successful Security Token Offering Project Exploring Investment Opportunities Professional Pdf
The following slide showcases some insights about spice VC security token offerings STO project to boost crowdfunding. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Take your projects to the next level with our ultimate collection of Successful Security Token Offering Project Exploring Investment Opportunities Professional Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide showcases some insights about spice VC security token offerings STO project to boost crowdfunding. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc.
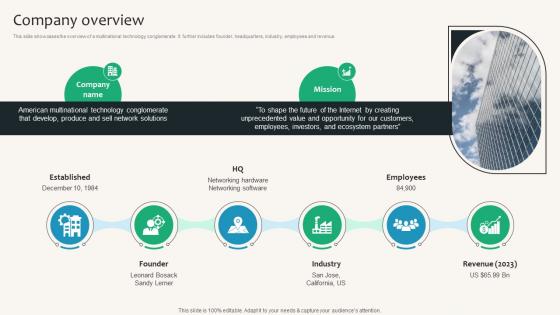
Company Overview Security Service Provider Business Model BMC SS V
This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue. Create an editable Company Overview Security Service Provider Business Model BMC SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Company Overview Security Service Provider Business Model BMC SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue.
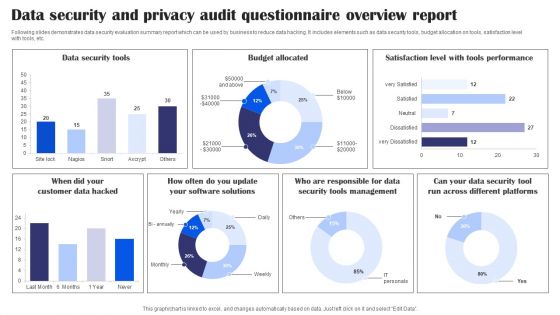
Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
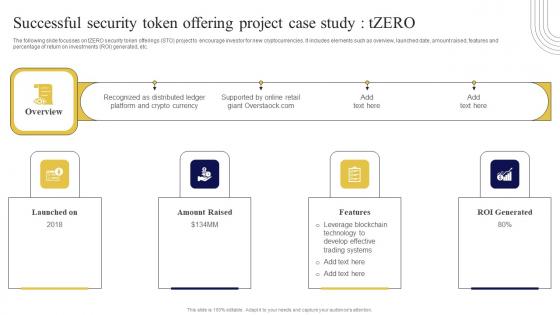
Successful Security Token Offering Exploring Investment Opportunities Background Pdf
The following slide focusses on tZERO security token offerings STO project to encourage investor for new cryptocurrencies. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Successful Security Token Offering Exploring Investment Opportunities Background Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Successful Security Token Offering Exploring Investment Opportunities Background Pdf. The following slide focusses on tZERO security token offerings STO project to encourage investor for new cryptocurrencies. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc.

About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Slidegeeks is here to make your presentations a breeze with About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.
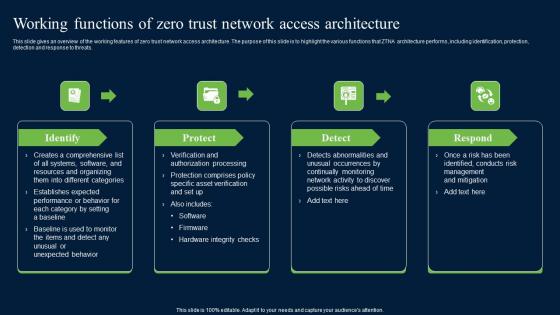
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
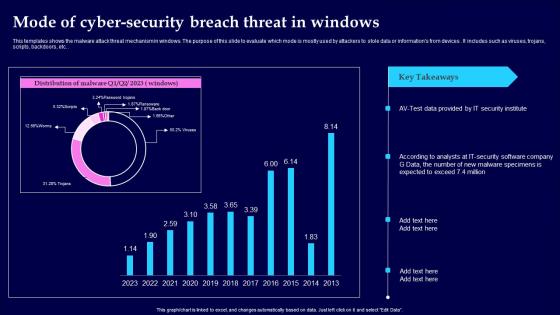
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.
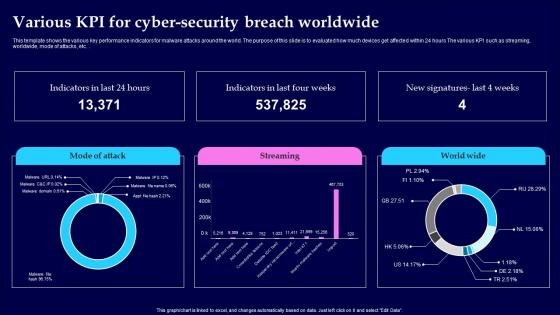
Various KPI For Cyber Security Breach Worldwide Pictures Pdf
This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc. Showcasing this set of slides titled Various KPI For Cyber Security Breach Worldwide Pictures Pdf The topics addressed in these templates are Cyber Security Breach, Worldwide All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc.


 Continue with Email
Continue with Email

 Home
Home


































