Security Assessment
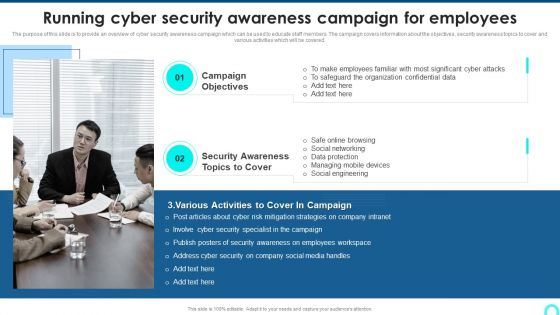
Running Cyber Security Awareness Campaign For Employees Clipart PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered.Presenting Running Cyber Security Awareness Campaign For Employees Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Campaign Objectives, Security Awareness, Security Awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
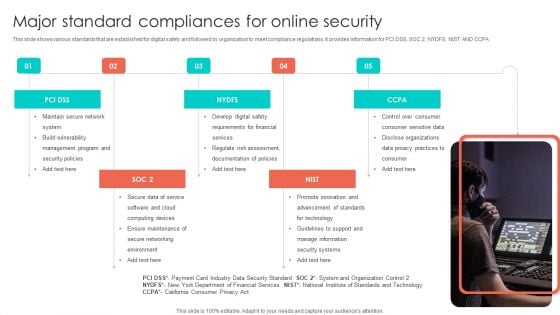
Major Standard Compliances For Online Security Pictures PDF
This slide shows various standards that are established for digital safety and followed by organization to meet compliance regulations. It provides information for PCI DSS, SOC 2, NYDFS, NIST AND CCPA. Persuade your audience using this Major Standard Compliances For Online Security Pictures PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Digital Safety, Requirements For Financial, Regulate Risk Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
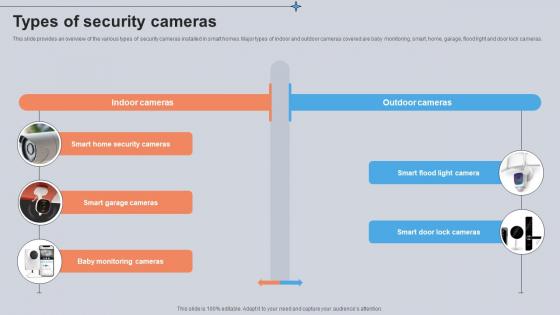
Types Of Security Cameras Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Types Of Security Cameras Utilizing Smart Appliances IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Types Of Security Cameras Utilizing Smart Appliances IoT SS V today and make your presentation stand out from the rest This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras.
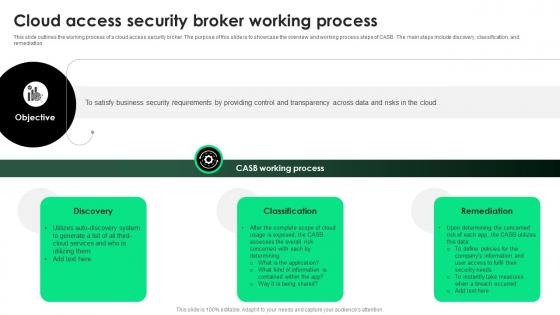
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.
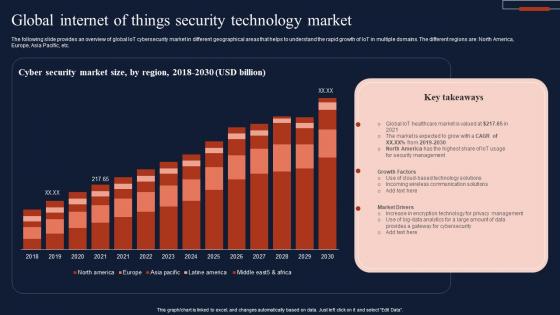
Global Internet Of Things Security Technology Market Infographics Pdf
The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc. Showcasing this set of slides titled Global Internet Of Things Security Technology Market Infographics Pdf The topics addressed in these templates are Cyber Security, Market Size, Technology Market All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc.
Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.Create an editable Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.
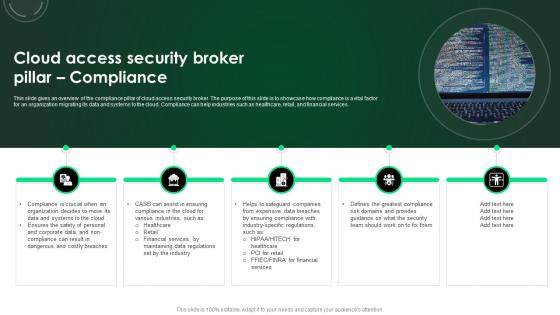
CASB 2 0 IT Cloud Access Security Broker Pillar Compliance
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CASB 2 0 IT Cloud Access Security Broker Pillar Compliance from Slidegeeks and deliver a wonderful presentation. This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services.
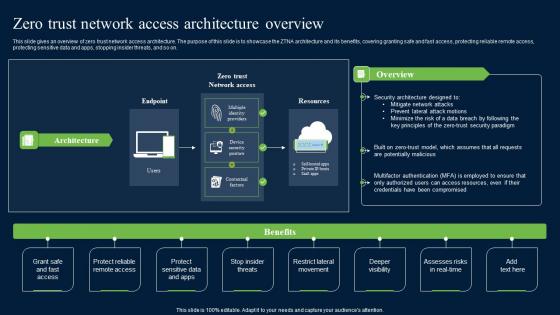
Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.
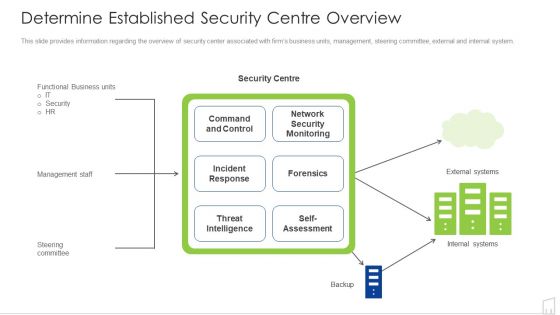
Determine Established Security Centre Overview Ppt Show Visual Aids PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative determine established security centre overview ppt show visual aids pdf bundle. Topics like security, network, systems, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Change Analysis And Evaluation Icon Ideas PDF
Presenting Security Change Analysis And Evaluation Icon Ideas PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Change, Analysis And Evaluation Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
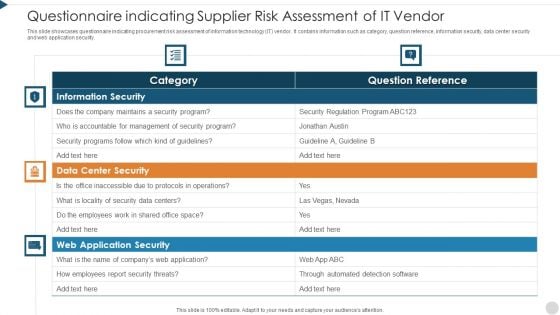
Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Overview Flow Chart Of Cyber Security Breach Summary Pdf
This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices Pitch your topic with ease and precision using this Overview Flow Chart Of Cyber Security Breach Summary Pdf This layout presents information on Email Delivered, Sending Commands, Injected Into It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices
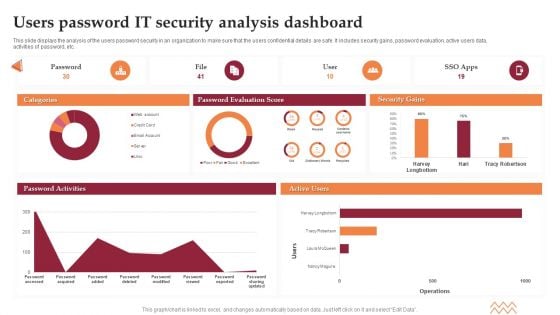
Users Password IT Security Analysis Dashboard Elements PDF
This slide displays the analysis of the users password security in an organization to make sure that the users confidential details are safe. It includes security gains, password evaluation, active users data, activities of password, etc. Showcasing this set of slides titled Users Password IT Security Analysis Dashboard Elements PDF. The topics addressed in these templates are Password Evaluation Score, Security Gains. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
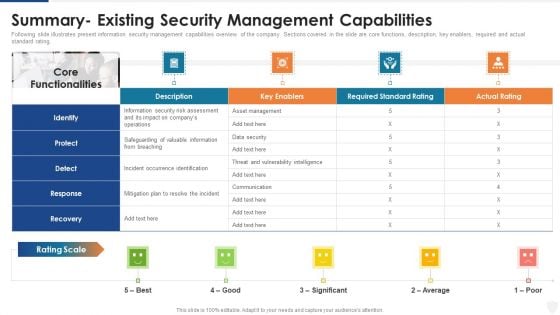
Summary Existing Security Management Capabilities Ppt Outline Themes PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative summary existing security management capabilities ppt outline themes pdf bundle. Topics like security, information, average can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
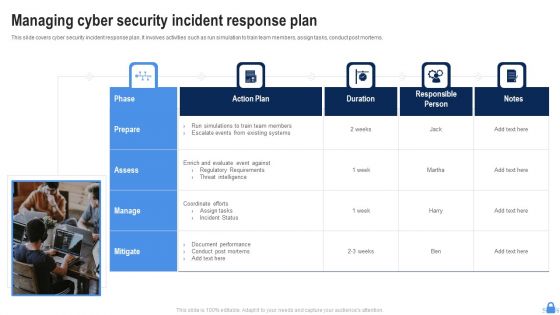
Managing Cyber Security Incident Response Plan Ppt Styles Diagrams PDF
This slide covers cyber security incident response plan. It involves activities such as run simulation to train team members, assign tasks, conduct post mortems. Persuade your audience using this Managing Cyber Security Incident Response Plan Ppt Styles Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Assess, Action Plan, Duration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
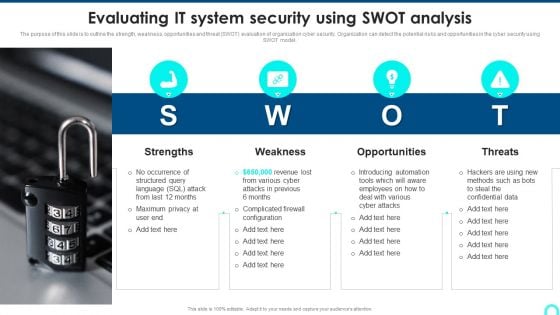
Evaluating IT System Security Using SWOT Analysis Portrait PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Presenting Evaluating IT System Security Using SWOT Analysis Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
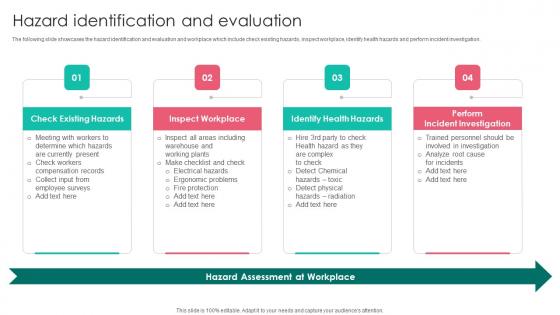
Hazard Identification Workplace Safety Protocol And Security Practices Background Pdf
The following slide showcases the hazard identification and evaluation and workplace which include check existing hazards, inspect workplace, identify health hazards and perform incident investigation. This modern and well arranged Hazard Identification Workplace Safety Protocol And Security Practices Background Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide showcases the hazard identification and evaluation and workplace which include check existing hazards, inspect workplace, identify health hazards and perform incident investigation.
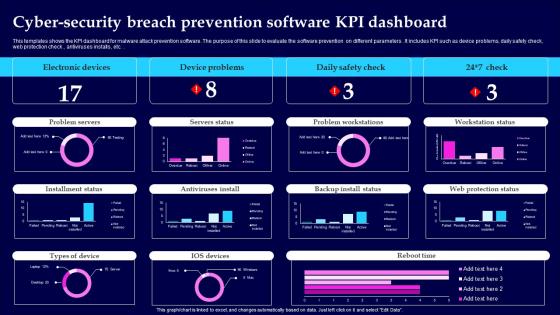
Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc.
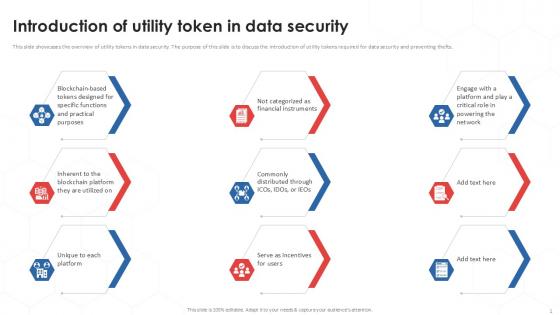
Introduction Of Utility Tokenization Strategies For Data Security PPT Presentation
This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Boost your pitch with our creative Introduction Of Utility Tokenization Strategies For Data Security PPT Presentation. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts.
Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.
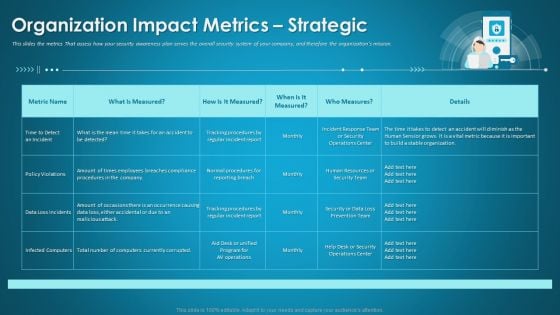
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
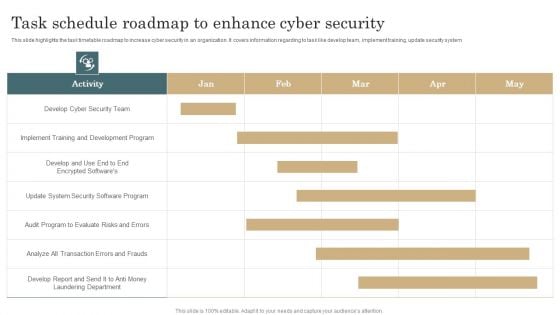
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
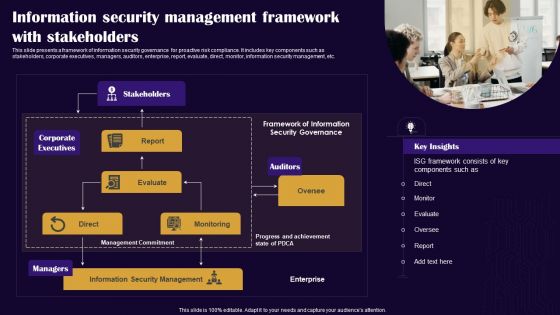
Information Security Management Framework With Stakeholders Diagrams PDF
This slide presents a framework of information security governance for proactive risk compliance. It includes key components such as stakeholders, corporate executives, managers, auditors, enterprise, report, evaluate, direct, monitor, information security management, etc. Persuade your audience using this Information Security Management Framework With Stakeholders Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Stakeholders, Auditors, Corporate Executives. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
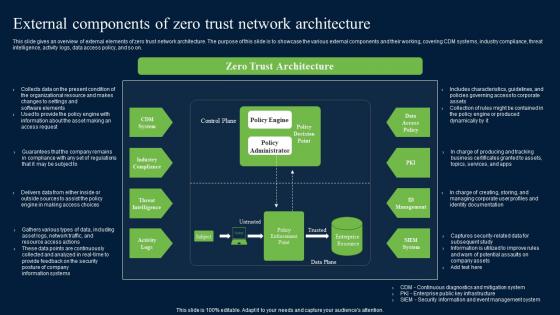
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
Overview Security Management Ppt PowerPoint Presentation Model Structure Cpb
Presenting this set of slides with name overview security management ppt powerpoint presentation model structure cpb. This is an editable Powerpoint three stages graphic that deals with topics like overview security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Overview Cyber Security Ppt PowerPoint Presentation Styles Microsoft Cpb
Presenting this set of slides with name overview cyber security ppt powerpoint presentation styles microsoft cpb. This is an editable Powerpoint four stages graphic that deals with topics like overview cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
IT Security Hacker Overview Of Hacking Sample PDF
This slide illustrates the overview of hacking and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers.Deliver an awe inspiring pitch with this creative IT Security Hacker Overview Of Hacking Sample PDF bundle. Topics like Process Of Discovering, Circumvent Security, Example Of Hacking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
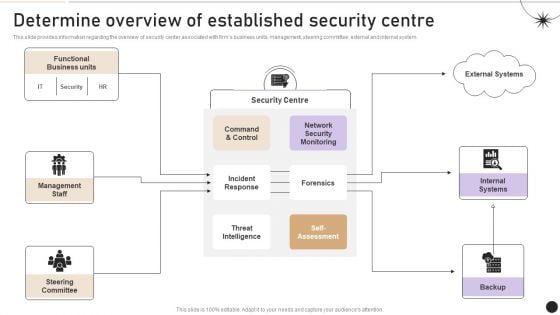
Determine Overview Of Established Security Centre Themes PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. There are so many reasons you need a Determine Overview Of Established Security Centre Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Running Cyber Security Awareness Campaign For Employees Background PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Running Cyber Security Awareness Campaign For Employees Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Key To Success Security PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with a key and stock charts Respond to feedback with our Key To Success Security PowerPoint Templates And PowerPoint Backgrounds 0311. Download without worries with our money back guaranteee.

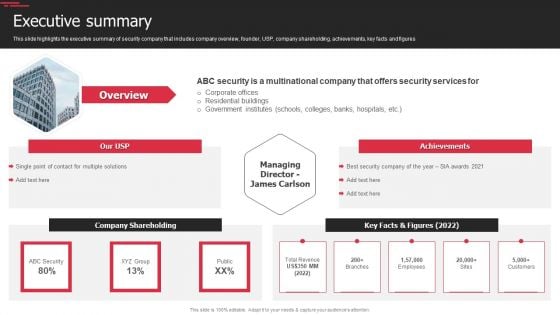
Manpower Corporate Security Business Profile Executive Summary Template PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Executive Summary Template PDF bundle. Topics like Total Revenue, Employees, Customers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
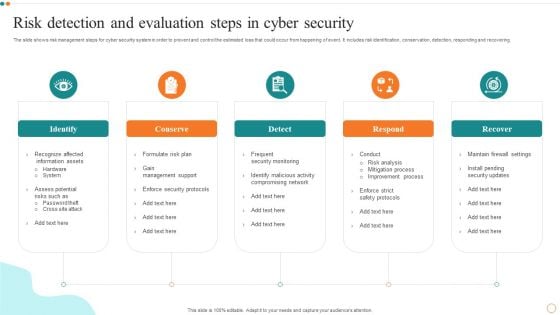
Risk Detection And Evaluation Steps In Cyber Security Designs PDF
Persuade your audience using this Risk Detection And Evaluation Steps In Cyber Security Designs PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Detection, Evaluation Steps. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
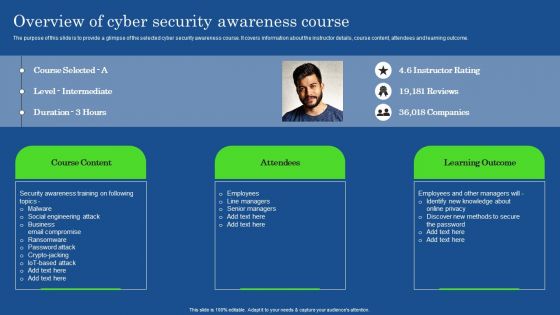
Overview Of Cyber Security Awareness Course Brochure PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Cyber Security Awareness Course Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Cyber Security Awareness Course Brochure PDF.
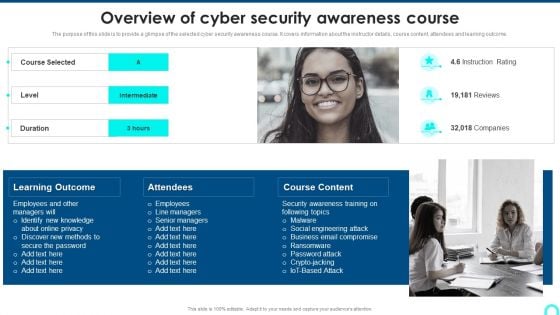
Overview Of Cyber Security Awareness Course Clipart PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This is a Overview Of Cyber Security Awareness Course Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Learning Outcome, Attendees, Course Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
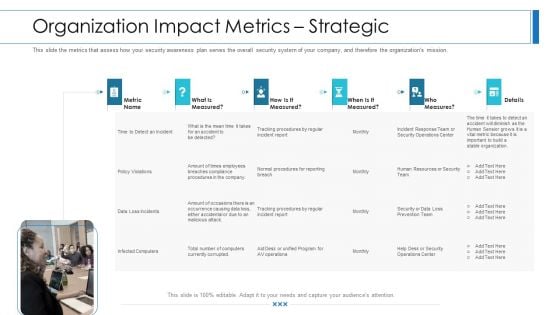
Workforce Security Realization Coaching Plan Organization Impact Metrics Strategic Infographics PDF
This slide the metrics that assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan organization impact metrics strategic infographics pdf. Use them to share invaluable insights on organization impact metrics strategicand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
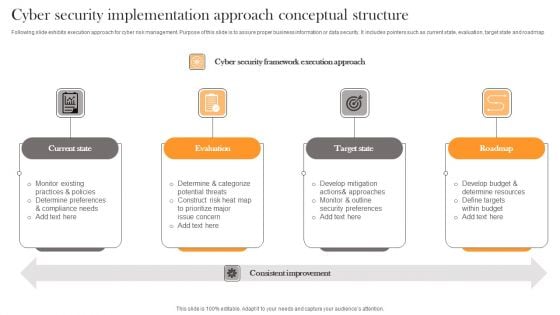
Cyber Security Implementation Approach Conceptual Structure Professional PDF
Following slide exhibits execution approach for cyber risk management. Purpose of this slide is to assure proper business information or data security. It includes pointers such as current state, evaluation, target state and roadmap. Presenting Cyber Security Implementation Approach Conceptual Structure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State, Evaluation, Target State . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
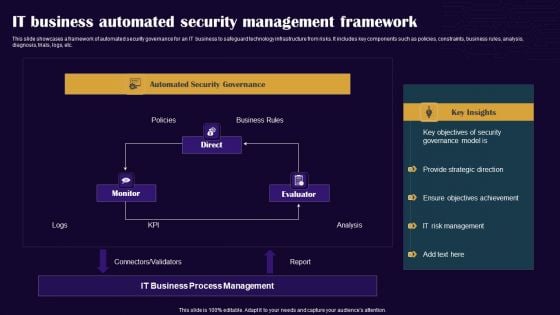
IT Business Automated Security Management Framework Professional PDF
This slide showcases a framework of automated security governance for an IT business to safeguard technology infrastructure from risks. It includes key components such as policies, constraints, business rules, analysis, diagnosis, trials, logs, etc. Showcasing this set of slides titled IT Business Automated Security Management Framework Professional PDF. The topics addressed in these templates are Monitor, Direct, Evaluator. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Running Cyber Security Awareness Campaign For Employees Portrait PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. This modern and well-arranged Running Cyber Security Awareness Campaign For Employees Portrait PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
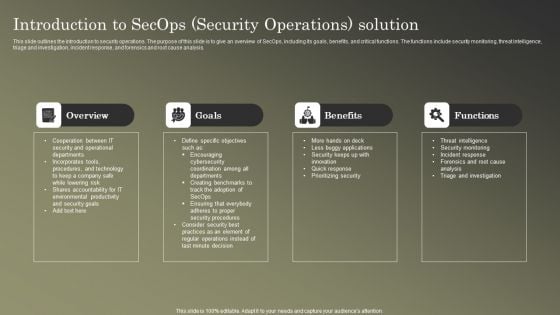
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
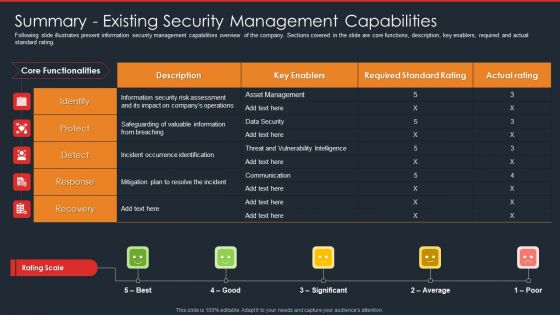
Data Safety Initiatives Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver and pitch your topic in the best possible manner with this data safety initiatives summary existing security management capabilities topics pdf. Use them to share invaluable insights on key enablers, rating scale, incident occurrence identification, asset management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
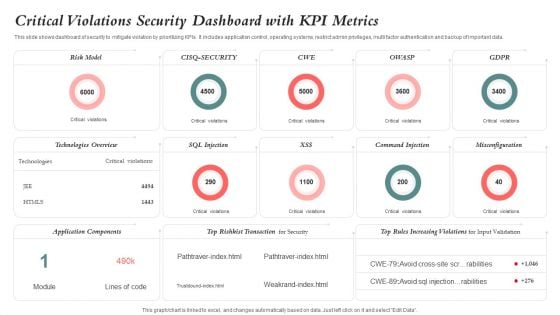
Critical Violations Security Dashboard With KPI Metrics Graphics PDF
This slide shows dashboard of security to mitigate violation by prioritizing KPIs. It includes application control, operating systems, restrict admin privileges, multi factor authentication and backup of important data. Showcasing this set of slides titled Critical Violations Security Dashboard With KPI Metrics Graphics PDF. The topics addressed in these templates are Risk Model, Application Components, Technologies Overview. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
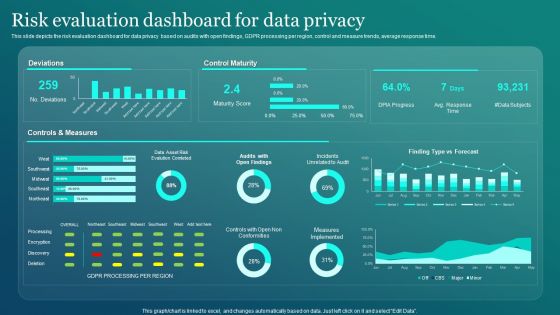
Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF
This slide depicts the risk evaluation dashboard for data privacy based on audits with open findings, GDPR processing per region, control and measure trends, average response time. There are so many reasons you need a Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Security Agency Business Profile Executive Summary Graphics PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures. This is a Security Agency Business Profile Executive Summary Graphics PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Total Revenue, Employees, Customers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
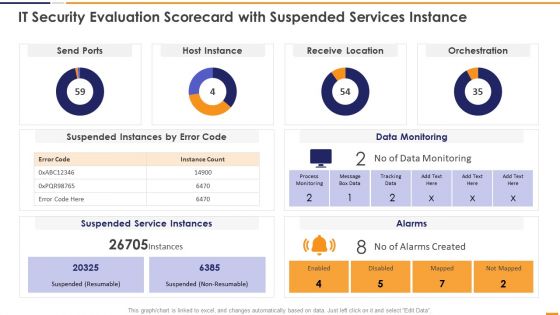
IT Security Evaluation Scorecard With Suspended Services Instance Graphics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Suspended Services Instance Graphics PDF. Use them to share invaluable insights on Send Ports Alarms, Host Instance Orchestration, Receive Location Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
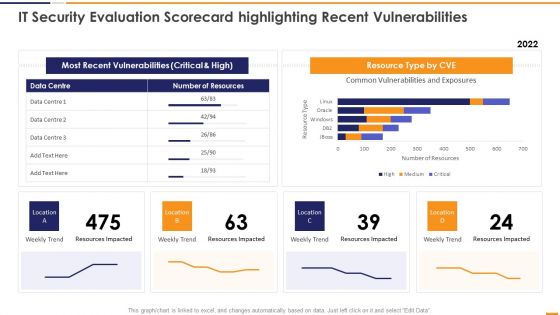
IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF bundle. Topics like Most Recent Vulnerabilities, Resource Type CVE, Weekly Trend Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
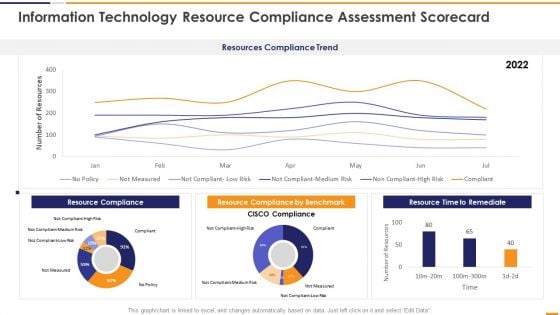
IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF. Use them to share invaluable insights on Resources Compliance Trend, Resource Compliance 2022, Resource Compliance Benchmark, Resource Time Remediate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
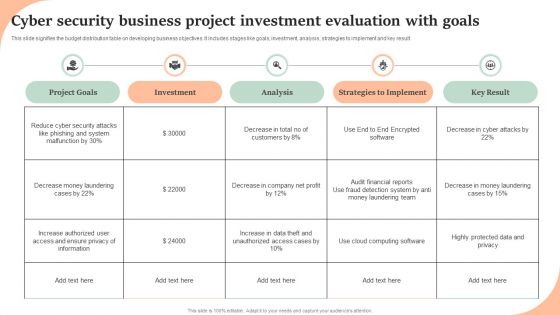
Cyber Security Business Project Investment Evaluation With Goals Structure PDF
This slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Showcasing this set of slides titled Cyber Security Business Project Investment Evaluation With Goals Structure PDF. The topics addressed in these templates are Project Goals, Investment, Analysis, Strategies To Implement, Key Result. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Best Data Security Software Table Of Contents Introduction PDF
Presenting this set of slides with name best data security software table of contents introduction pdf. The topics discussed in these slides are project context and objectives, our process, your investment, company overview, our past experience, statement of work and contract, next steps. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents Security And Surveillance Company Profile Formats PDF
Deliver an awe inspiring pitch with this creative Table Of Contents Security And Surveillance Company Profile Formats PDF bundle. Topics like Executive Summary, Company Overview, Business Model can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
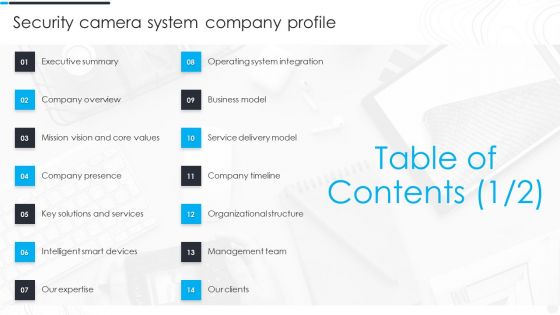
Table Of Contents Security Camera System Company Profile Download PDF
Deliver an awe inspiring pitch with this creative Table Of Contents Security Camera System Company Profile Download PDF bundle. Topics like Executive Summary, Company Overview, Company Presence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Table Of Contents Inspiration PDF
Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Table Of Contents Inspiration PDF bundle. Topics like Executive Summary, Company Overview, Company Presence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
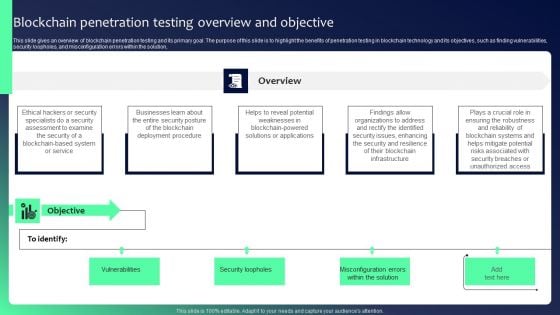
Blockchain Security Solutions Deployment Blockchain Penetration Testing Overview Clipart PDF
This slide gives an overview of blockchain penetration testing and its primary goal. The purpose of this slide is to highlight the benefits of penetration testing in blockchain technology and its objectives, such as finding vulnerabilities, security loopholes, and misconfiguration errors within the solution. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Blockchain Security Solutions Deployment Blockchain Penetration Testing Overview Clipart PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
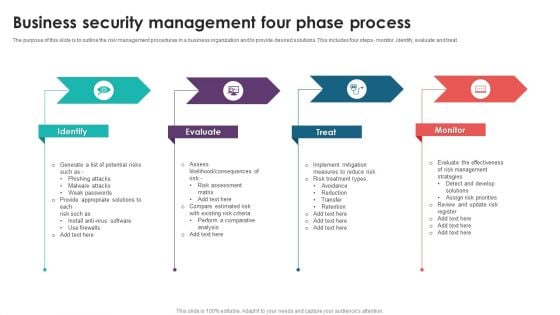
Business Security Management Four Phase Process Topics PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Presenting Business Security Management Four Phase Process Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Evaluate, Treat, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
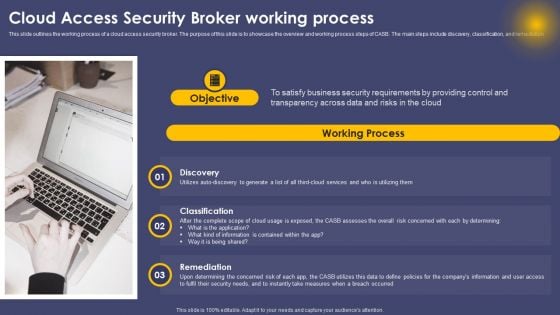
Cloud Access Security Broker Working Process Ppt Slides Portrait PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Boost your pitch with our creative Cloud Access Security Broker Working Process Ppt Slides Portrait PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
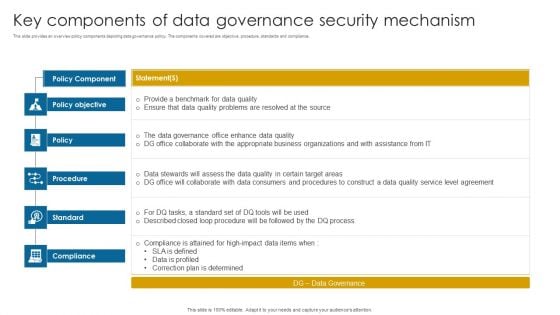
Key Components Of Data Governance Security Mechanism Information PDF
This slide provides an overview policy components depicting data governance policy. The components covered are objective, procedure, standards and compliance.Pitch your topic with ease and precision using this Key Components Of Data Governance Security Mechanism Information PDF. This layout presents information on Data Governance, Compliance Attained, Correction Determined. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Business Security Management 4 Step Workflow Icons PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Persuade your audience using this Business Security Management 4 Step Workflow Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Treat, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
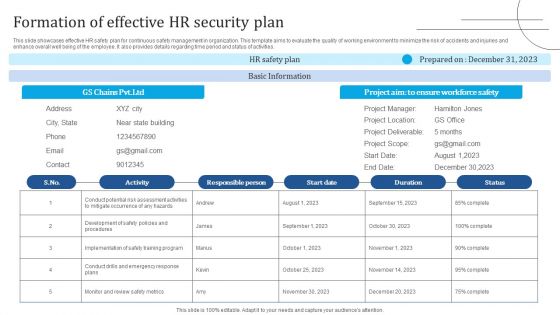
Formation Of Effective HR Security Plan Information PDF
This slide showcases effective HR safety plan for continuous safety management in organization. This template aims to evaluate the quality of working environment to minimize the risk of accidents and injuries and enhance overall well being of the employee. It also provides details regarding time period and status of activities. Presenting Formation Of Effective HR Security Plan Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Activity, Responsible Person, Basic Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
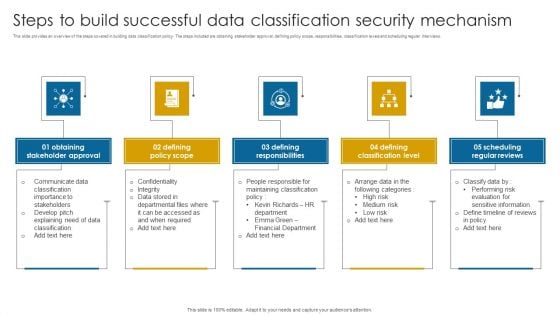
Steps To Build Successful Data Classification Security Mechanism Structure PDF
This slide provides an overview of the steps covered in building data classification policy. The steps included are obtaining stakeholder approval, defining policy scope, responsibilities, classification levels and scheduling regular interviews.Presenting Steps To Build Successful Data Classification Security Mechanism Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Stakeholder Approval, Defining Policy Scope, Defining Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































