Security Management
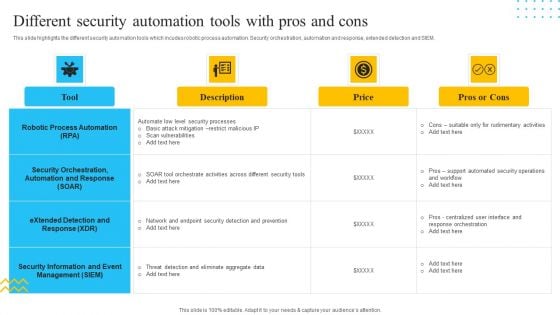
IT Security Automation Tools Integration Different Security Automation Tools With Pros And Cons Summary PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Different Security Automation Tools With Pros And Cons Summary PDF. Use them to share invaluable insights on Robotic Process Automation, Security Orchestration, Price and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
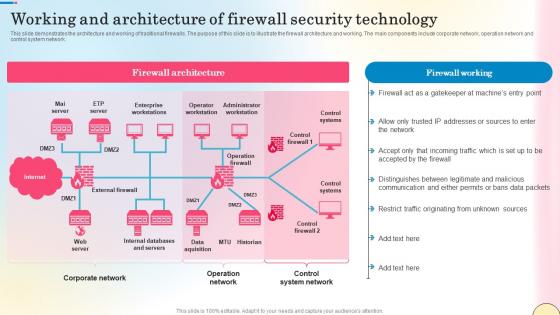
Working And Architecture Of Firewall Security Technology Network Security Summary Pdf
This slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Working And Architecture Of Firewall Security Technology Network Security Summary Pdf can be your best option for delivering a presentation. Represent everything in detail using Working And Architecture Of Firewall Security Technology Network Security Summary Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network.

Workforce Security Realization Coaching Plan Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting workforce security realization coaching plan security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementing security awareness, sustaining security awareness, security awareness program. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Addressing Different Security Priorities At Organization Background PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of fraud or threat protection, physical security and business continuity. This is a developing firm security strategy plan addressing different security priorities at organization background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fraud or threat protection, physical security, business continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
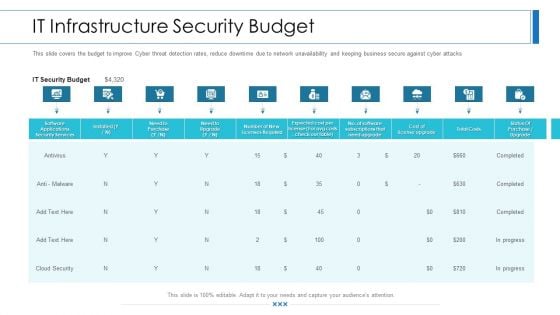
Workforce Security Realization Coaching Plan IT Infrastructure Security Budget Background PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan it infrastructure security budget background pdf bundle. Topics like software applications security services, business, it security budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Our Process For Migrating Firewall Network Security Cloud Security Firewall Proposal
This slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc.Take your presentations to the next level with our Our Process For Migrating Firewall Network Security Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights. This slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc.
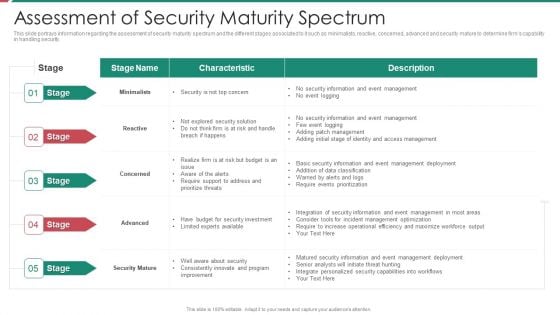
Security And Process Integration Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security and process integration assessment of security maturity spectrum slides pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
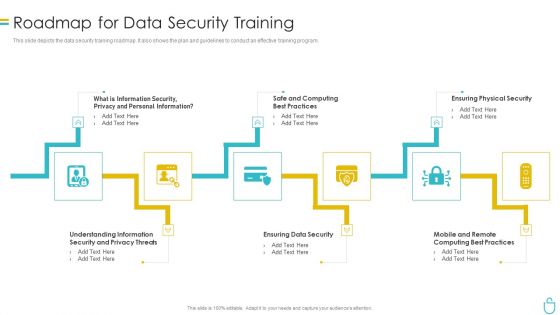
Information Security Roadmap For Data Security Training Ppt Model Show PDF
This slide depicts the data security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a information security roadmap for data security training ppt model show pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, ensuring data security, ensuring physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
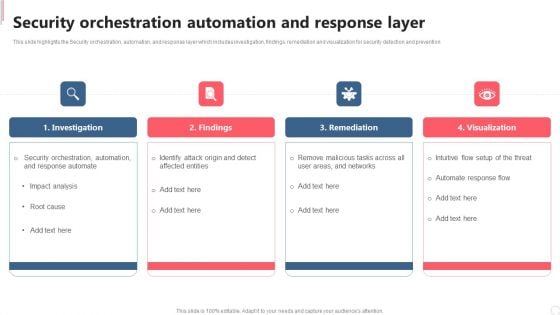
Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Get a simple yet stunning designed Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
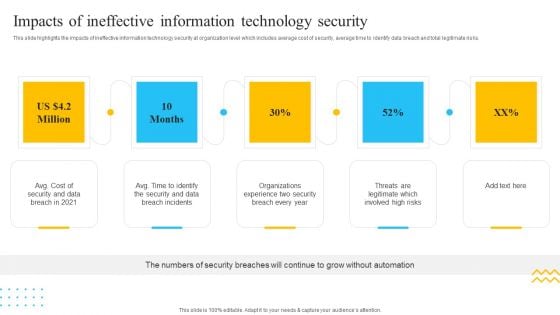
IT Security Automation Tools Integration Impacts Of Ineffective Information Technology Security Elements PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Presenting IT Security Automation Tools Integration Impacts Of Ineffective Information Technology Security Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cost Security, Data Breach, Security And Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
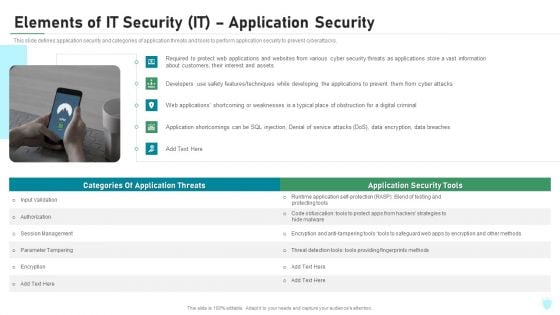
Elements Of IT Security IT Application Security Ppt Layouts Ideas PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. This is a elements of it security it application security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, encryption, authorization, techniques, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why Cloud Security Is Important Cloud Computing Security IT Ppt Slides Graphics Template PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver and pitch your topic in the best possible manner with this why cloud security is important cloud computing security it ppt slides graphics template pdf. Use them to share invaluable insights on centralized security, cost effective, diminished administration, reliability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Building Trust With IoT Security Emerging Technologies Enhancing IoT Security And Privacy IoT SS V
This slide includes key technologies integrated with IoT ecosystem that helps to tackle cyberattacks and resolve any other issues. It includes technologies such as blockchain technology, artificial intelligence and machine learning and quantum computing. Make sure to capture your audiences attention in your business displays with our gratis customizable Building Trust With IoT Security Emerging Technologies Enhancing IoT Security And Privacy IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide includes key technologies integrated with IoT ecosystem that helps to tackle cyberattacks and resolve any other issues. It includes technologies such as blockchain technology, artificial intelligence and machine learning and quantum computing.
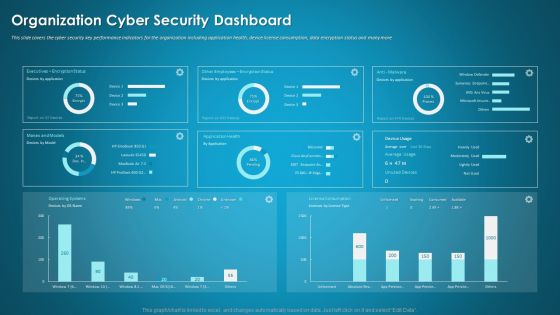
Organizational Network Security Awareness Staff Learning Organization Cyber Security Dashboard Elements PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization cyber security dashboard elements pdf. Use them to share invaluable insights on organization cyber security dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
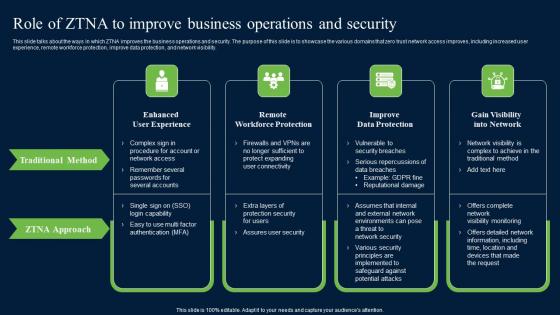
Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.

Strategies To Mitigate Cyber Security Risks Agenda For Cyber Security Risks Ppt Infographics Graphics Design PDF
Presenting this set of slides with name strategies to mitigate cyber security risks agenda for cyber security risks ppt infographics graphics design pdf. This is a one stage process. The stages in this process are determining roles and responsibilities, senior management, executives responsible, risk management, presenting optimize cybersecurity, risk framework. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
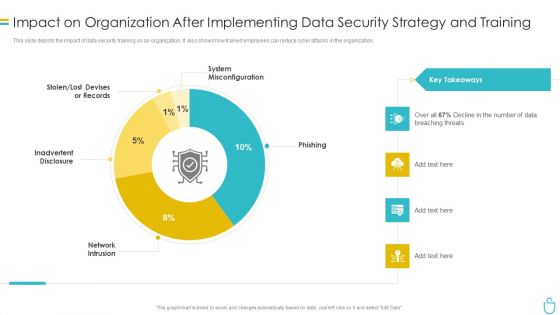
Information Security Impact On Organization After Implementing Data Security Strategy And Training Ppt Ideas Images PDF
This slide depicts the impact of data security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this information security impact on organization after implementing data security strategy and training ppt ideas images pdf. Use them to share invaluable insights on organization, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Firm Security Strategy Plan Addressing Role Of Chief Security Officer At Workplace Formats PDF
This slide provides information regarding role of chief security officer at workplace and determine their key priorities in terms of day to day operations, security, compliance, innovation, etc. Presenting developing firm security strategy plan addressing role of chief security officer at workplace formats pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like day to day operations, security, compliance, innovation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Best Practices Cloud Computing Security IT Ppt Portfolio Master Slide PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an awe inspiring pitch with this creative cloud security best practices cloud computing security it ppt portfolio master slide pdf bundle. Topics like cloud protection, cloud utilization and risk, authentication process, security policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Security Company Strategic Partnerships Graphics PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Strategic Partnerships Graphics PDF. Use them to share invaluable insights on Technology Partner, Installation Centres, Partnership Type and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
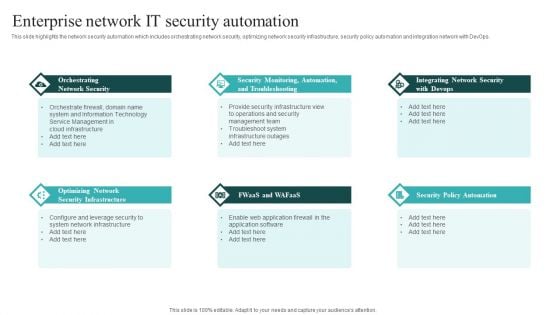
IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
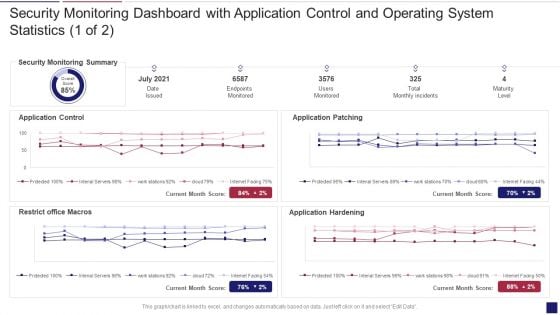
Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Security Brochure PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard security brochure pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard Sample PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard sample pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
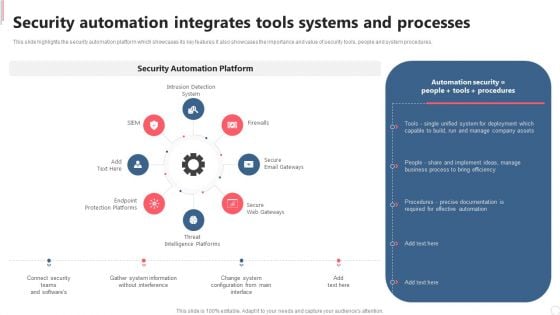
Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. There are so many reasons you need a Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cloud Information Security Hybrid Cloud Security Solutions Ppt Infographics Professional PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy. Deliver an awe inspiring pitch with this creative Cloud Information Security Hybrid Cloud Security Solutions Ppt Infographics Professional PDF bundle. Topics like Categorization Services, Enable Organizations, Security Properly can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
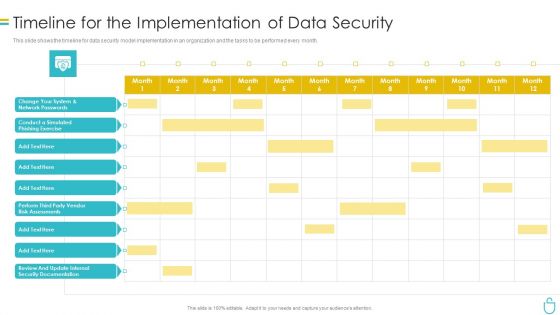
Information Security Timeline For The Implementation Of Data Security Ppt Gallery Topics PDF
This slide shows the timeline for data security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this information security timeline for the implementation of data security ppt gallery topics pdf. Use them to share invaluable insights on timeline for the implementation of data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Timeline For The Implementation Of Information Technology Security Structure PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative it security timeline for the implementation of information technology security structure pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
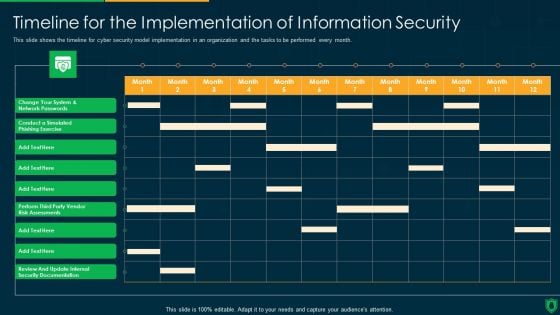
Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
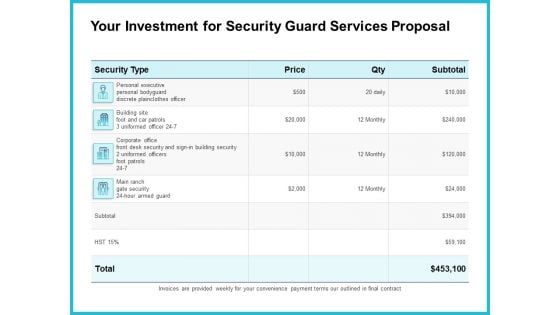
Uniformed Security Your Investment For Security Guard Services Proposal Graphics PDF
Deliver an awe inspiring pitch with this creative uniformed security your investment for security guard services proposal graphics pdf bundle. Topics like executive, security, corporate, price can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
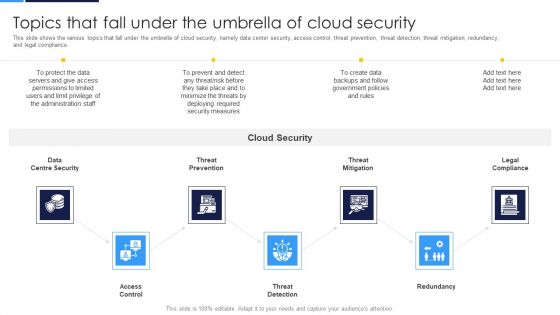
Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance.This is a Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threat Prevention, Access Control, Centre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Workforce Security Realization Coaching Plan Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a workforce security realization coaching plan security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
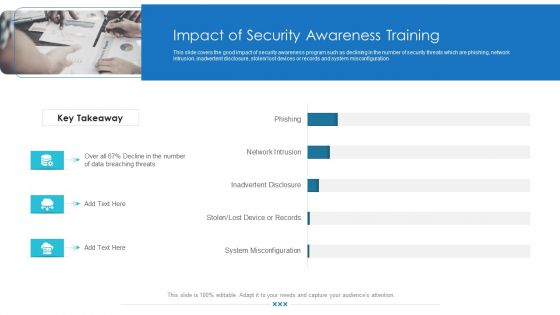
Workforce Security Realization Coaching Plan Impact Of Security Awareness Training Pictures PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan impact of security awareness training pictures pdf bundle. Topics like impact of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
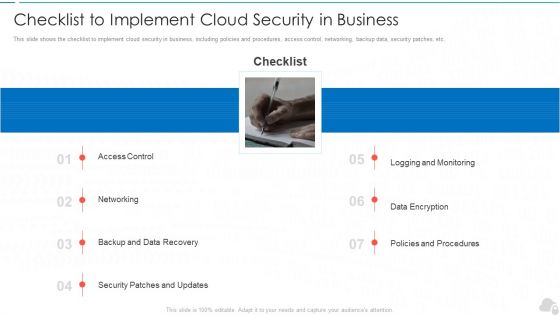
Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Data Security Software Client Testimonials For Company Online Database Security Guidelines PDF
Presenting this set of slides with name best data security software client testimonials for company online database security guidelines pdf. This is a three stage process. The stages in this process are client testimonials, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Roadmap For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software roadmap for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are roadmap, company, online database security, 2016 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
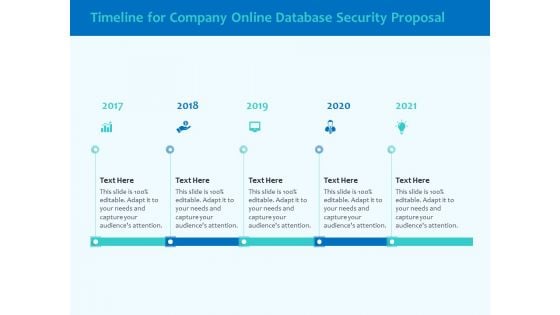
Best Data Security Software Timeline For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software timeline for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are timeline, company, online database security, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Security Assessment Cloud Security Checklist Policies And Procedures Background PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization.Presenting Cloud Security Assessment Cloud Security Checklist Policies And Procedures Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Implement Policies, Security Solutions, Security Procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Security Company Strategic Partnerships Ideas PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Security Company Strategic Partnerships Ideas PDF. Use them to share invaluable insights on Mobile Security Application, CCTV Installation Centres, Technology Partner Partnership and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Data Security Awareness Training For Staff Ppt Visual Aids Pictures PDF
This slide represents the data security awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this information security data security awareness training for staff ppt visual aids pictures pdf. Use them to share invaluable insights on project managers, developers, senior executives, planning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
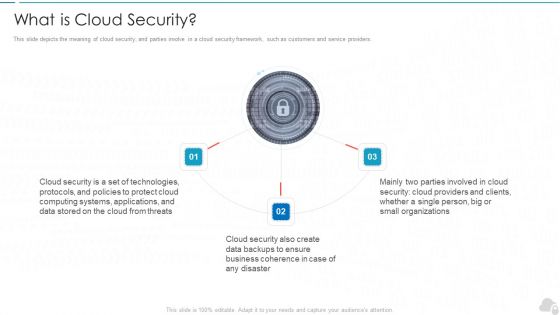
What Is Cloud Security Cloud Computing Security IT Ppt File Graphics PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Presenting what is cloud security cloud computing security it ppt file graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, technologies, protocols, business, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
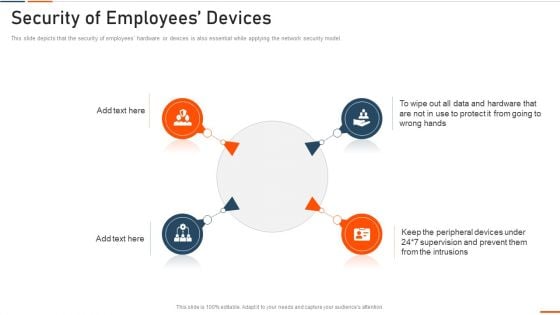
Information Technology Security Security Of Employees Devices Ppt File Portrait PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the network security model. Presenting information technology security security of employees devices ppt file portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
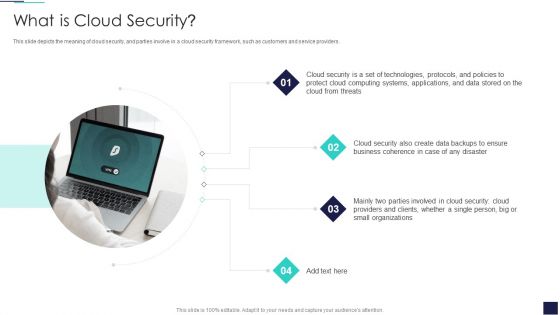
Cloud Information Security What Is Cloud Security Ppt Inspiration Mockup PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. This is a Cloud Information Security What Is Cloud Security Ppt Inspiration Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Business Coherence, Small Organizations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Roadmap For Information Technology Security Training Ppt Layouts Vector PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a it security roadmap for information technology security training ppt layouts vector pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, ensuring data security, mobile and remote computing best practices, safe and computing best practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Training Roadmap Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a security awareness training roadmap hacking prevention awareness training for it security template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, physical security, privacy threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Elements Of Electronic Information Security Cloud Security Ppt Outline Background Designs PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a cybersecurity elements of electronic information security cloud security ppt outline background designs pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, risks, resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Program Timeline Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This is a security awareness program timeline hacking prevention awareness training for it security professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perform, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Asset Security Categorization Professional PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Deliver an awe inspiring pitch with this creative cyber security administration in organization addressing asset security categorization professional pdf bundle. Topics like executive, ownership, categorization, integrity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Compliance Dashboard Of Data Security Ppt Icon Vector PDF
This slide depicts the data security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative information security compliance dashboard of data security ppt icon vector pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
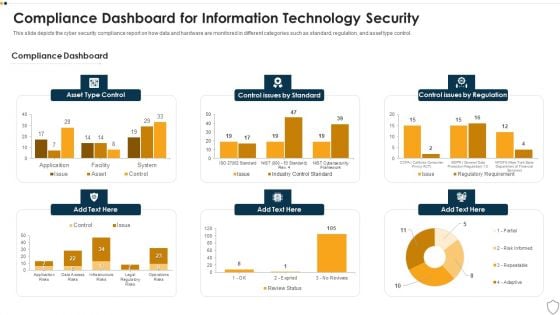
IT Security Compliance Dashboard For Information Technology Security Ppt Slides Brochure PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative it security compliance dashboard for information technology security ppt slides brochure pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
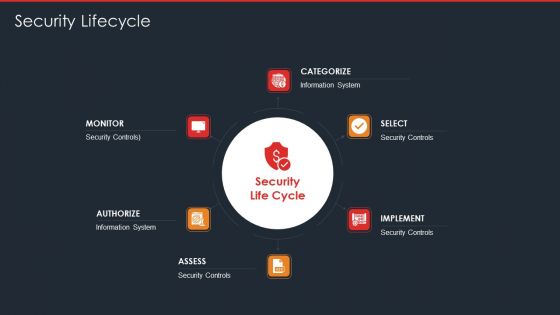
Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Cyber Security Administration In Organization Security Sample PDF
This is a table of contents cyber security administration in organization security sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring, financial, assets, security, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
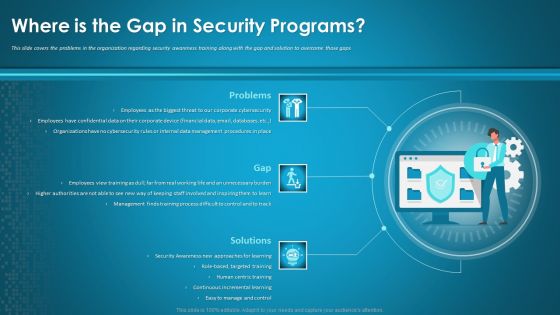
Organizational Network Security Awareness Staff Learning Where Is The Gap In Security Programs Template PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a organizational network security awareness staff learning where is the gap in security programs template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, management, organizations, targeted training, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
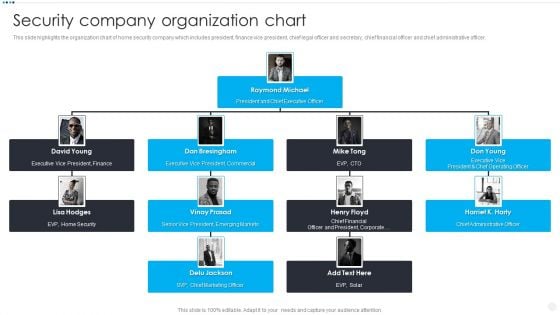
Smart Home Security Solutions Company Profile Security Company Organization Chart Diagrams PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Smart Home Security Solutions Company Profile Security Company Organization Chart Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Executive Vice President, EVP Home Security, Chief Marketing Officer, Chief Administrative Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
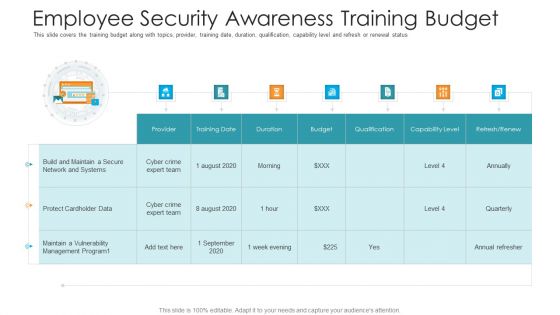
Employee Security Awareness Training Budget Hacking Prevention Awareness Training For IT Security Guidelines PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver and pitch your topic in the best possible manner with this employee security awareness training budget hacking prevention awareness training for it security guidelines pdf. Use them to share invaluable insights on training, maintain, management, budget, capability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
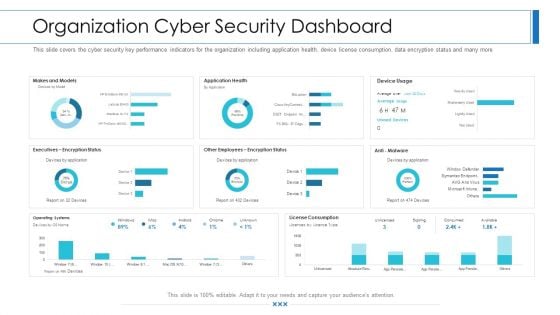
Workforce Security Realization Coaching Plan Organization Cyber Security Dashboard Template PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization cyber security dashboard template pdf bundle. Topics like makes and models, operating systems, encryption status, application health, license consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhanced Protection Corporate Event Administration Role Of Security Operations Centre In Security Operations Brochure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting enhanced protection corporate event administration role of security operations centre in security operations brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
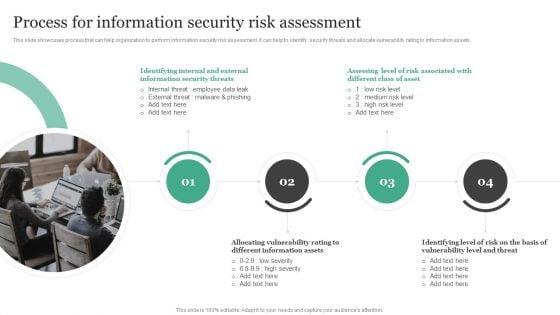
Process For Information Security Risk Assessment Information Security Risk Administration Demonstration PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help to identify security threats and allocate vulnerability rating to information assets.Take your projects to the next level with our ultimate collection of Process For Information Security Risk Assessment Information Security Risk Administration Demonstration PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.


 Continue with Email
Continue with Email

 Home
Home


































