Security Management

Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF.
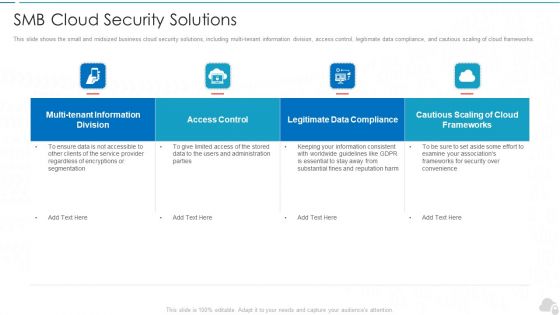
Smb Cloud Security Solutions Cloud Computing Security IT Ppt Portfolio Files PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. Deliver an awe inspiring pitch with this creative smb cloud security solutions cloud computing security it ppt portfolio files pdf bundle. Topics like access control, frameworks, legitimate data compliance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
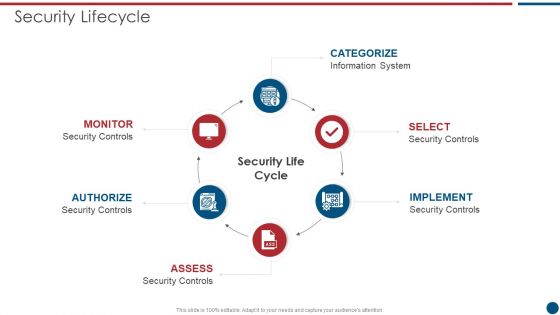
Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF
This is a Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information System, Security Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Are you searching for a Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF from Slidegeeks today.
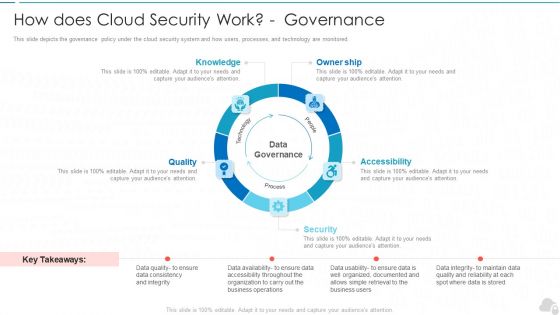
How Does Cloud Security Work Governance Cloud Computing Security IT Ppt Layouts Structure PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a how does cloud security work governance cloud computing security it ppt layouts structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like knowledge, owner ship, quality, security, accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF. Use them to share invaluable insights on Monitory Services, Company Shareholding, Extensive Customization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Create an editable Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
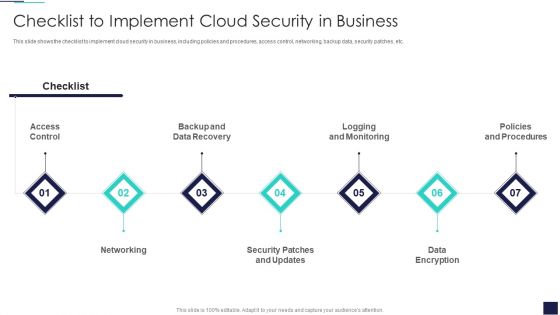
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
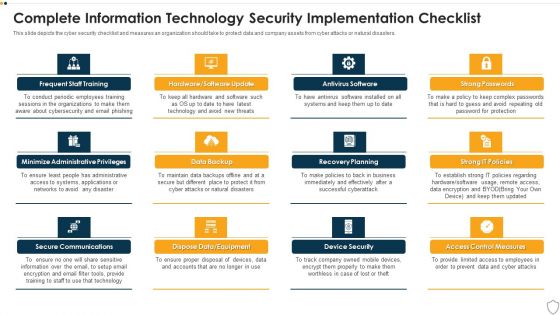
IT Security Complete Information Technology Security Implementation Checklist Ppt Inspiration Templates PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting it security complete information technology security implementation checklist ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like frequent staff training, secure communications, data backup, recovery planning, device security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
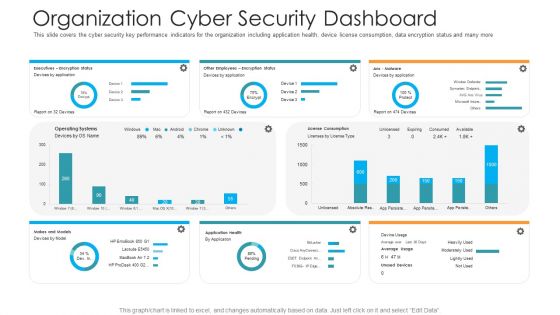
Organization Cyber Security Dashboard Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on executives, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
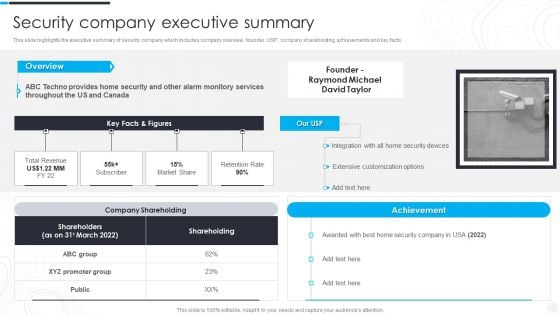
Security Camera System Company Profile Security Company Executive Summary Formats PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Executive Summary Formats PDF bundle. Topics like Company Shareholding, Customization Options, Raymond Michael can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
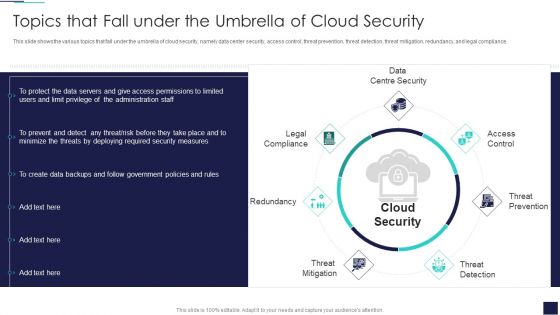
Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. This is a Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Threat Prevention, Threat Detection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
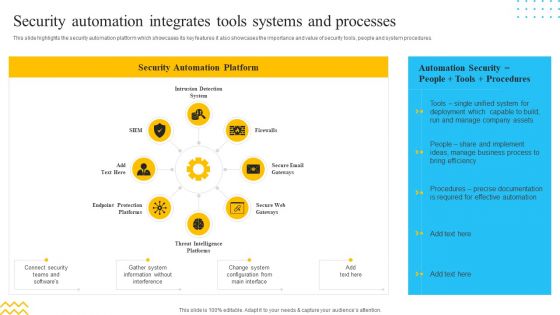
IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. This is a IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection System, Firewalls, Secure Email Gateways. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workforce Security Realization Coaching Plan Automated Security Awareness Platform And Cost Elements PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan automated security awareness platform and cost elements pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. This is a Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cost Effective, Diminished Administration, Centralized Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like, frequent malware attacks and lack of awareness among employees.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF bundle. Topics like Frequent Malware, Phishing Attacks, Ransomware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
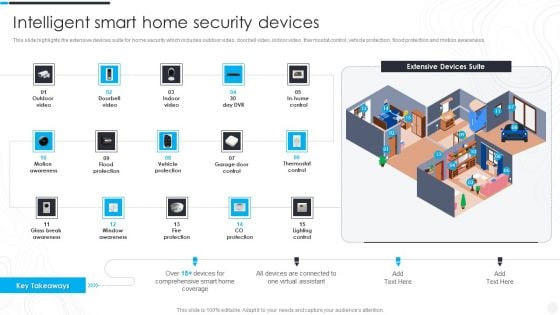
Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF bundle. Topics like Flood Protection, Motion Awareness, Vehicle Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
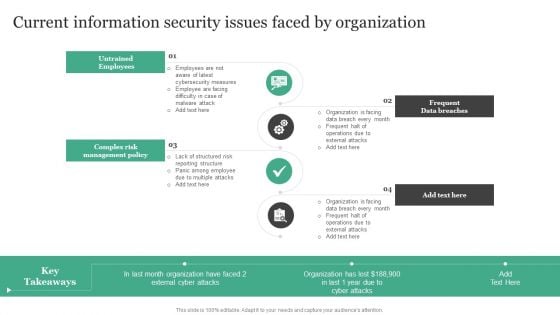
Current Information Security Issues Faced By Organization Information Security Risk Administration Summary PDF
Find a pre-designed and impeccable Current Information Security Issues Faced By Organization Information Security Risk Administration Summary PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
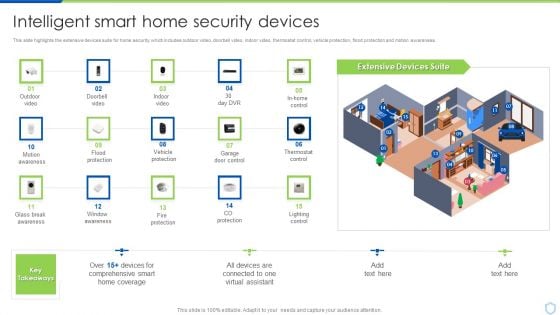
Security And Surveillance Company Profile Intelligent Smart Home Security Devices Brochure PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Intelligent Smart Home Security Devices Brochure PDF bundle. Topics like Awareness Campaign, Empower And Educate, Empowering Lives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
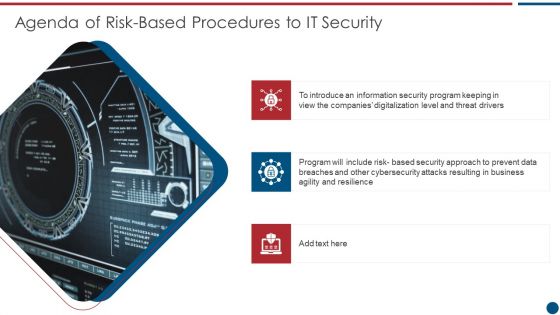
Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF
This is a Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Program Keeping, Threat Drivers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cloud Information Security Cloud Security Best Practices Ppt Infographic Template Example Topics PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Cloud Security Best Practices Ppt Infographic Template Example Topics PDF. Use them to share invaluable insights onSecure Cloud, Cloud Protection, Cloud Utilization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Presenting Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Implement Policies, Protect Data, Security Procedures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
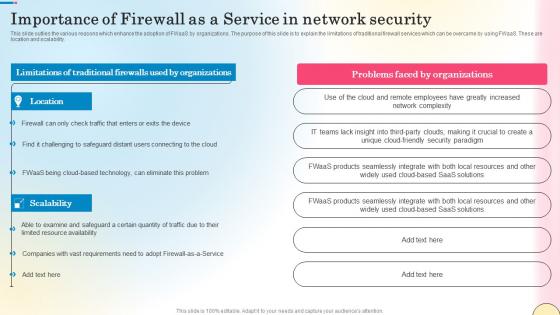
Importance Of Firewall As A Service In Network Security Network Security Designs Pdf
This slide outlies the various reasons which enhance the adoption of FWaaS by organizations. The purpose of this slide is to explain the limitations of traditional firewall services which can be overcame by using FWaaS. These are location and scalability. The Importance Of Firewall As A Service In Network Security Network Security Designs Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlies the various reasons which enhance the adoption of FWaaS by organizations. The purpose of this slide is to explain the limitations of traditional firewall services which can be overcame by using FWaaS. These are location and scalability.
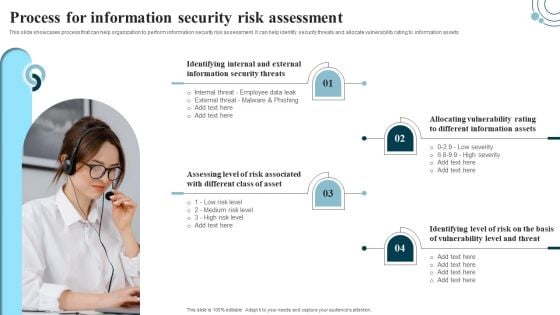
Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF.
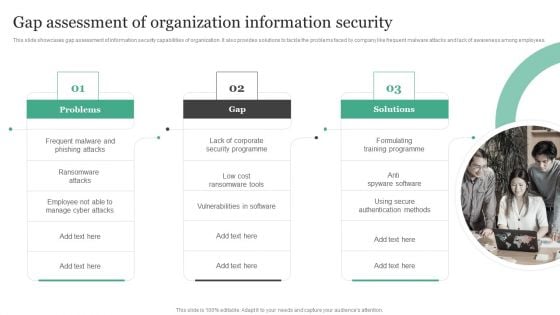
Gap Assessment Of Organization Information Security Information Security Risk Administration Summary PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees.Find highly impressive Gap Assessment Of Organization Information Security Information Security Risk Administration Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Gap Assessment Of Organization Information Security Information Security Risk Administration Summary PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
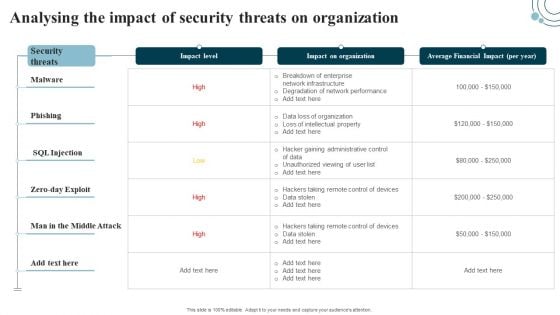
Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cloud Security Checklist Policies And Procedures Cloud Computing Security IT Ppt Layouts Show PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. This is a cloud security checklist policies and procedures cloud computing security it ppt layouts show pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implement policies, cloud security, organization, policy violation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
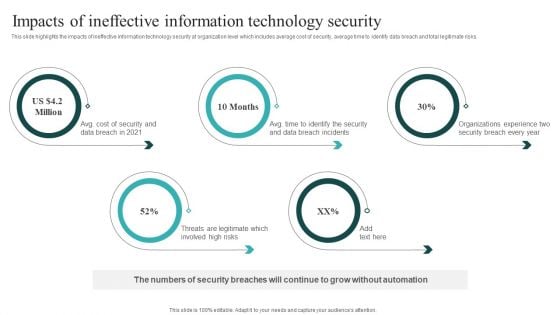
IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Get a simple yet stunning designed IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
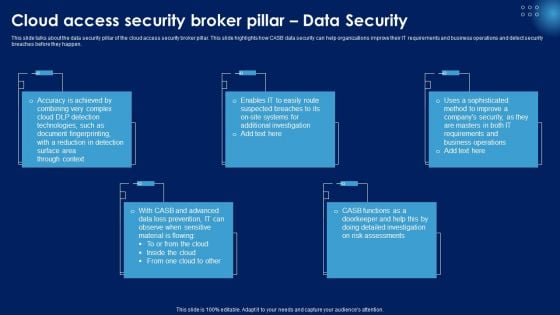
Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Slidegeeks is here to make your presentations a breeze with Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
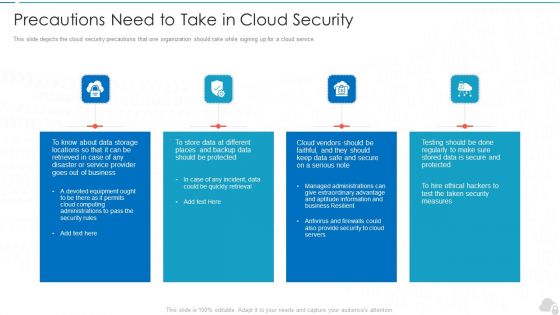
Precautions Need To Take In Cloud Security Cloud Computing Security IT Ppt Inspiration Templates PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service. Presenting precautions need to take in cloud security cloud computing security it ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, service, security measures, computing administrations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
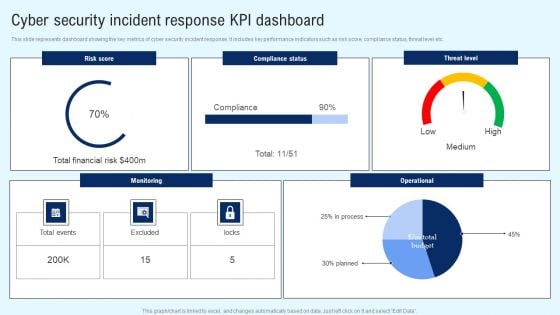
Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
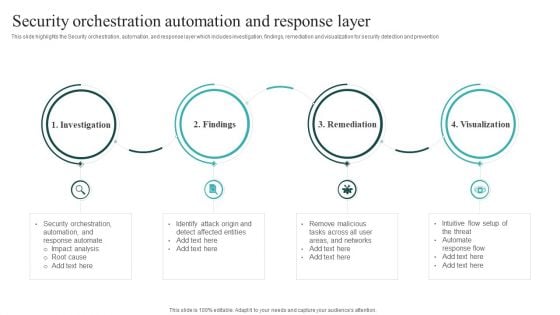
IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF can be your best option for delivering a presentation. Represent everything in detail using IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
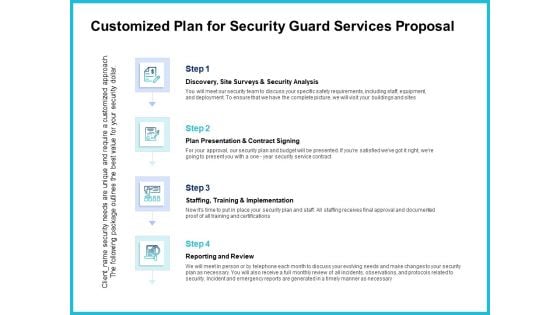
Uniformed Security Customized Plan For Security Guard Services Proposal Portrait PDF
Presenting uniformed security customized plan for security guard services proposal portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security analysis, plan presentation, training and implementation, reporting and review. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
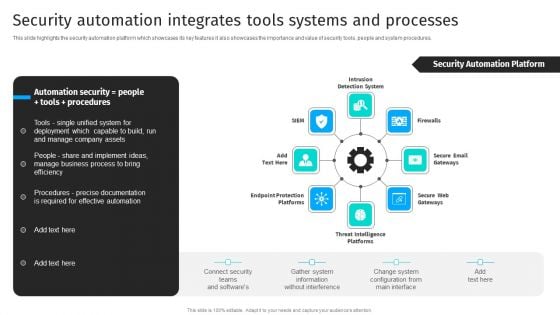
Security Automation Integrates Security Automation To Analyze And Mitigate Cyberthreats Slides PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures.Present like a pro with Security Automation Integrates Security Automation To Analyze And Mitigate Cyberthreats Slides PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Create an editable Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
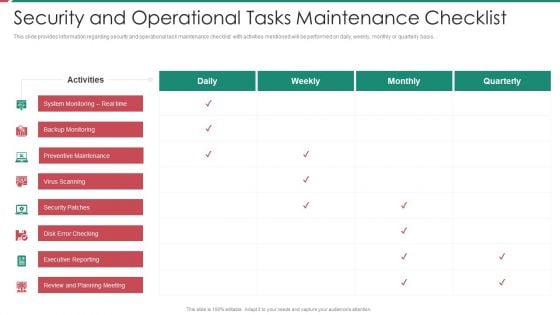
Security And Process Integration Security And Operational Tasks Maintenance Checklist Diagrams PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security and process integration security and operational tasks maintenance checklist diagrams pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

KYC Transaction Monitoring System Business Security Key Members Of Financial Security Department Pictures PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Want to ace your presentation in front of a live audience Our KYC Transaction Monitoring System Business Security Key Members Of Financial Security Department Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
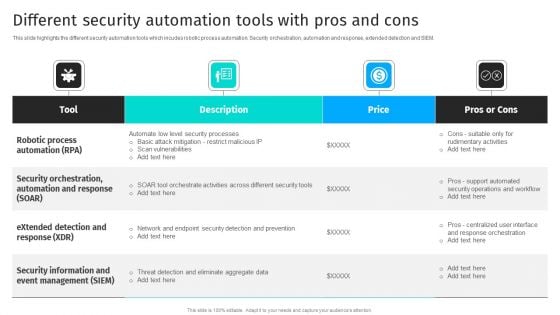
Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF can be your best option for delivering a presentation. Represent everything in detail using Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
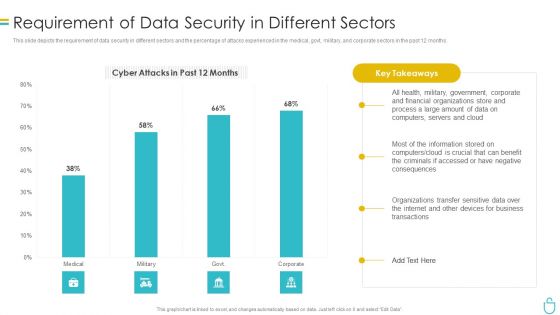
Information Security Requirement Of Data Security In Different Sectors Ppt File Infographic Template PDF
This slide depicts the requirement of data security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative information security requirement of data security in different sectors ppt file infographic template pdf bundle. Topics like process, financial, organizations, data, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Requirement Of Information Technology Security In Different Sectors Ppt File Display PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative it security requirement of information technology security in different sectors ppt file display pdf bundle. Topics like business transactions, organizations, financial, process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
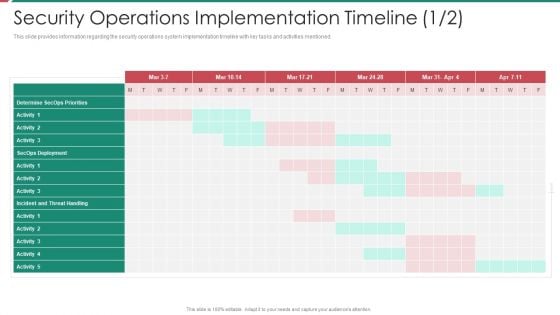
Security And Process Integration Security Operations Implementation Timeline Activity Inspiration PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative security and process integration security operations implementation timeline activity inspiration pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
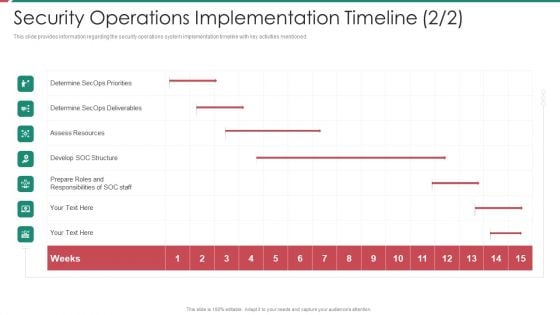
Security And Process Integration Security Operations Implementation Timeline Staff Ideas PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this security and process integration security operations implementation timeline staff ideas pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
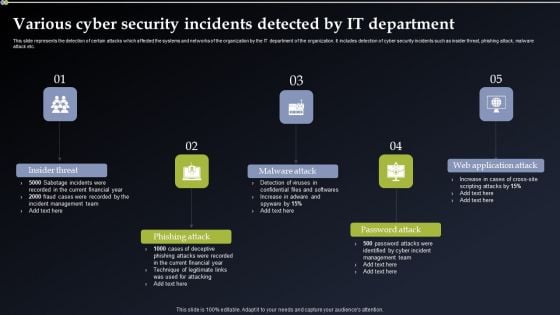
Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you searching for a Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF from Slidegeeks today.
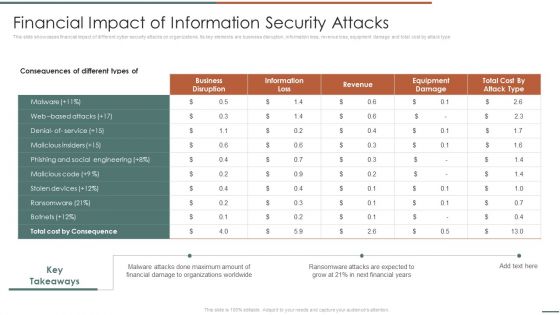
Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF bundle. Topics like Business Disruption, Cost By Consequence, Malware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
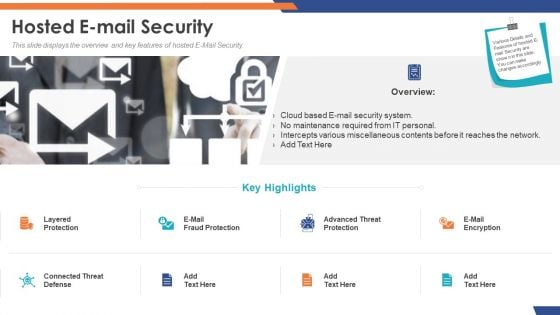
Email Security Market Research Report Hosted E Mail Security Formats PDF
Presenting this set of slides with name email security market research report hosted e mail security formats pdf. This is a two stage process. The stages in this process are cloud based e mail security system, no maintenance required from it personal, intercepts various miscellaneous contents before it reaches the network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Hosted E Mail Security Portrait PDF
Presenting this set of slides with name global cloud based email security market hosted e mail security portrait pdf. This is a two stage process. The stages in this process are cloud based e mail security system, no maintenance required from it personal, intercepts various miscellaneous contents before it reaches the network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information And Technology Security Operations Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this information and technology security operations security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Security Solutions Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this organizational security solutions security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
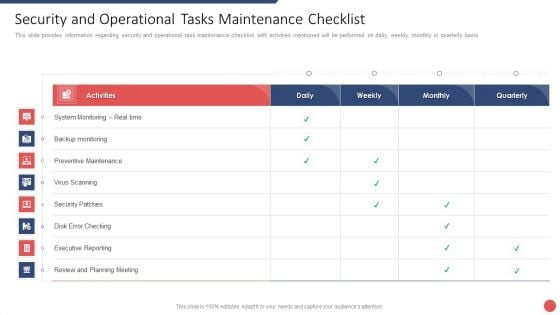
Security Functioning Centre Security And Operational Tasks Maintenance Checklist Inspiration PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security functioning centre security and operational tasks maintenance checklist inspiration pdf. Use them to share invaluable insights on executive reporting, review and planning meeting, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets.This is a Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identifying Internal, Allocating Vulnerability, Assessing Level. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
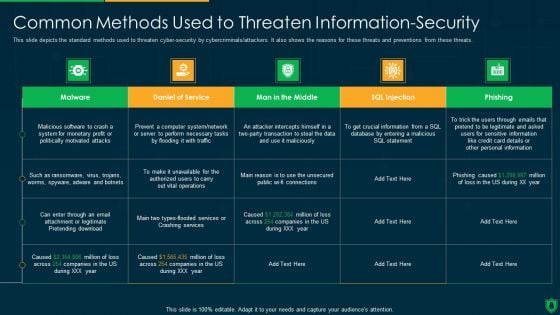
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
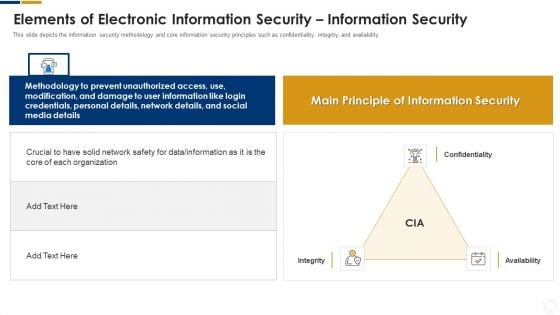
Cybersecurity Elements Of Electronic Information Security Information Security Ppt Pictures Slide PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a cybersecurity elements of electronic information security information security ppt pictures slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, network, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
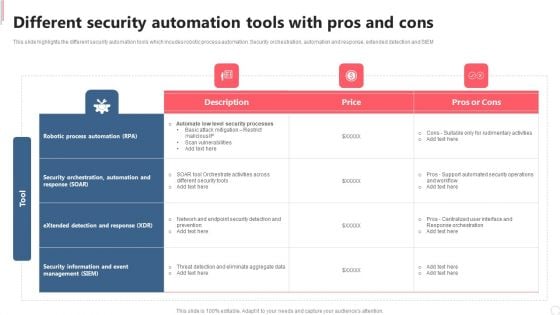
Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
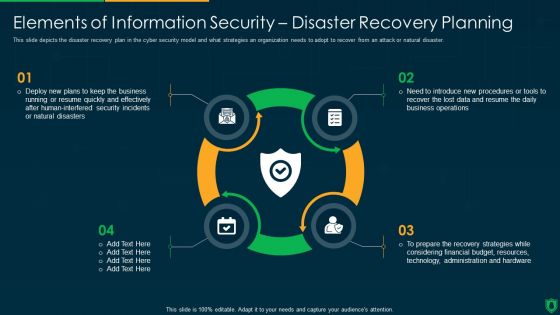
Info Security Elements Of Information Security Disaster Recovery Planning Ppt PowerPoint Presentation Gallery Designs PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a info security elements of information security disaster recovery planning ppt powerpoint presentation gallery designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deploy new plans, quickly and effectively, security incidents, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Data Security Software Why Us For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software why us for company online database security proposal themes pdf. This is a four stage process. The stages in this process are our team includes elite software engineers and cyber security experts to keep our culture fresh, innovative and energetic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
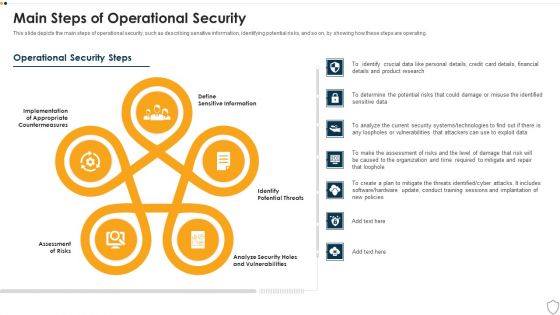
IT Security Main Steps Of Operational Security Ppt Show Design Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting it security main steps of operational security ppt show design inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like assessment of risks, potential threats, sensitive information, analyze security holes and vulnerabilities, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
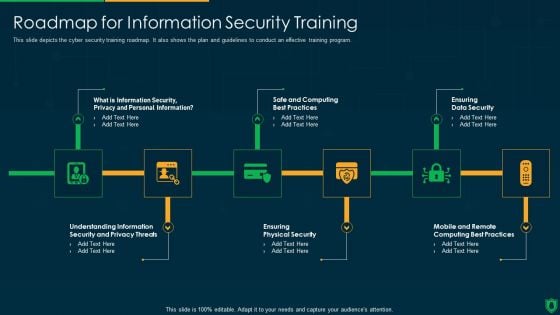
Info Security Roadmap For Information Security Training Ppt PowerPoint Presentation File Inspiration PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a info security roadmap for information security training ppt powerpoint presentation file inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, personal information, safe and computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































