Security Management
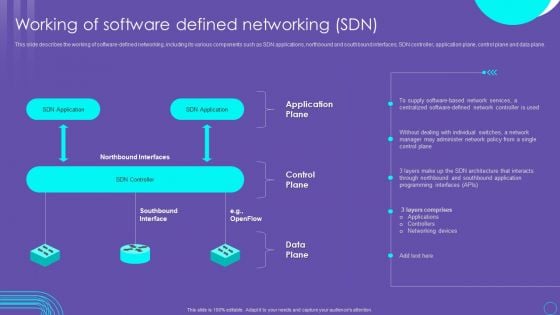
SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF
This slide describes the working of software defined networking, including its various components such as SDN applications, northbound and southbound interfaces, SDN controller, application plane, control plane and data plane. Slidegeeks is here to make your presentations a breeze with SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
Collection Of Interrelated Tasks 6 Stages Security Business Plan PowerPoint Slides
We present our collection of interrelated tasks 6 stages security business plan PowerPoint Slides.Download and present our Arrows PowerPoint Templates because You will get more than you ever bargained for. Download our Circle Charts PowerPoint Templates because It can Bubble and burst with your ideas. Present our Shapes PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Download and present our Business PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Download and present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team.Use these PowerPoint slides for presentations relating to arrow, circular, process, round, flow, business, vector, graphic, part, green, red, concept, yellow, presentation, symbol, circle, orange, repeat, cycle, illustration, icon, pink, six, purple, blue, repetitive. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Rule the roost with our Collection Of Interrelated Tasks 6 Stages Security Business Plan PowerPoint Slides. They will enthrone your thoughts.
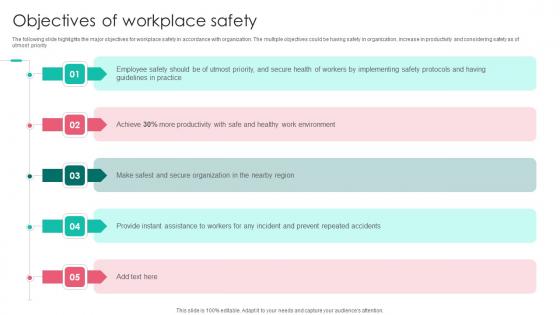
Objectives Of Workplace Safety Workplace Safety Protocol And Security Practices Ideas Pdf
The following slide highlights the major objectives for workplace safety in accordance with organization. The multiple objectives could be having safety in organization, increase in productivity and considering safety as of utmost priority. Slidegeeks has constructed Objectives Of Workplace Safety Workplace Safety Protocol And Security Practices Ideas Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. The following slide highlights the major objectives for workplace safety in accordance with organization. The multiple objectives could be having safety in organization, increase in productivity and considering safety as of utmost priority.

House Made Of Dollars Golden Key Security PowerPoint Templates And PowerPoint Themes 1112
We present our House Made Of Dollars Golden Key Security PowerPoint Templates And PowerPoint Themes 1112.Use our Americana PowerPoint Templates because, The Venn graphic comprising interlinking circles geometrically demonstate how various functions operating independantly, to a large extent, are essentially interdependant. Use our Business PowerPoint Templates because,Marketing Strategy Business Template:- Maximising sales of your product is the intended destination. Use our Finance PowerPoint Templates because, This business powerpoint template helps expound on the logic of your detailed thought process to take your company forward. Use our Money PowerPoint Templates because, All elements of the venture are equally critical. Use our Sales PowerPoint Templates because, Unravel the desired and essential elements of your overall strategy.Use these PowerPoint slides for presentations relating to House made from hundred Americana Business Finance Money Sales. The prominent colors used in the PowerPoint template are Yellow, Gray, Black Attend to details with our House Made Of Dollars Golden Key Security PowerPoint Templates And PowerPoint Themes 1112. You will come out on top.
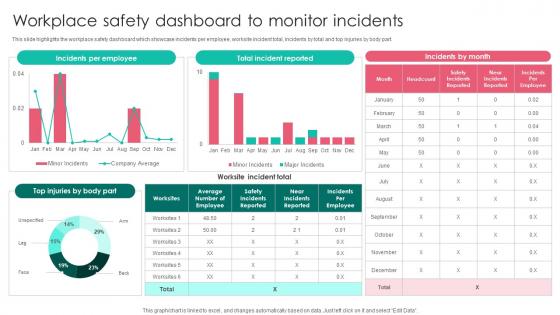
Workplace Safety Dashboard Monitor Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide highlights the workplace safety dashboard which showcase incidents per employee, worksite incident total, incidents by total and top injuries by body part. Present like a pro with Workplace Safety Dashboard Monitor Workplace Safety Protocol And Security Practices Demonstration Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide highlights the workplace safety dashboard which showcase incidents per employee, worksite incident total, incidents by total and top injuries by body part.

Consequence Worksite Injuries Workplace Safety Protocol And Security Practices Infographics Pdf
This slide highlights the consequences of accidents on workers and employers which includes loss of job, loss of income, and damage to organization equipments etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Consequence Worksite Injuries Workplace Safety Protocol And Security Practices Infographics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide highlights the consequences of accidents on workers and employers which includes loss of job, loss of income, and damage to organization equipments etc.

Impact Of Workplace Accidents Workplace Safety Protocol And Security Practices Graphics Pdf
The following slide highlights the effect of workplace accidents on the organization which includes regulatory fines, medical compensation, fatal workplace injuries, replace worker and loss productivity. Welcome to our selection of the Impact Of Workplace Accidents Workplace Safety Protocol And Security Practices Graphics Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today The following slide highlights the effect of workplace accidents on the organization which includes regulatory fines, medical compensation, fatal workplace injuries, replace worker and loss productivity.
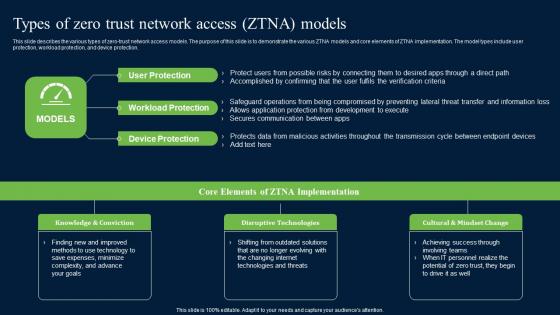
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.

Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF
The purpose of this slide is to showcase the dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Present like a pro with Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Safety Guidelines Detect Prevent Alcohol Workplace Safety Protocol And Security Practices Clipart Pdf
This slide highlights the preventive and detective measures for alcohol abuse which showcase multiple ways to deal the situation with training program, and experts assistance. Boost your pitch with our creative Safety Guidelines Detect Prevent Alcohol Workplace Safety Protocol And Security Practices Clipart Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the preventive and detective measures for alcohol abuse which showcase multiple ways to deal the situation with training program, and experts assistance.

Problem Related Drug Alcohol Abuse Workplace Safety Protocol And Security Practices Brochure Pdf
The following slide highlights the problems with excessive drug and alcohol at workplace which showcases the alcohol abuse leads to multiple problems and major drinking habits that creates issues for work. Take your projects to the next level with our ultimate collection of Problem Related Drug Alcohol Abuse Workplace Safety Protocol And Security Practices Brochure Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide highlights the problems with excessive drug and alcohol at workplace which showcases the alcohol abuse leads to multiple problems and major drinking habits that creates issues for work.
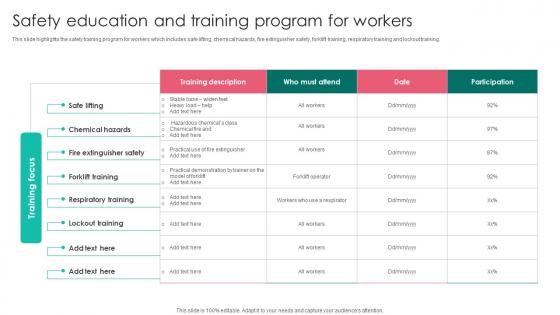
Safety Education And Training Program Workplace Safety Protocol And Security Practices Clipart Pdf
This slide highlights the safety training program for workers which includes safe lifting, chemical hazards, fire extinguisher safety, forklift training, respiratory training and lockout training. Do you know about Slidesgeeks Safety Education And Training Program Workplace Safety Protocol And Security Practices Clipart Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide highlights the safety training program for workers which includes safe lifting, chemical hazards, fire extinguisher safety, forklift training, respiratory training and lockout training.
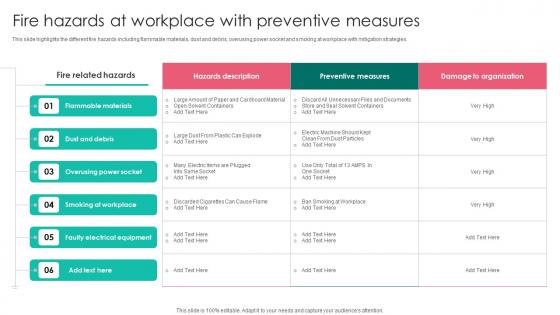
Fire Hazards At Workplace With Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide highlights the different fire hazards including flammable materials, dust and debris, overusing power socket and smoking at workplace with mitigation strategies. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fire Hazards At Workplace With Workplace Safety Protocol And Security Practices Demonstration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights the different fire hazards including flammable materials, dust and debris, overusing power socket and smoking at workplace with mitigation strategies.
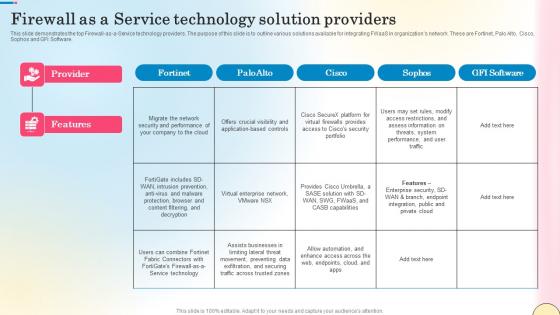
Firewall As A Service Technology Solution Providers Network Security Pictures Pdf
This slide demonstrates the top Firewall-as-a-Service technology providers. The purpose of this slide is to outline various solutions available for integrating FWaaS in organizations network. These are Fortinet, Palo Alto, Cisco, Sophos and GFI Software. Make sure to capture your audiences attention in your business displays with our gratis customizable Firewall As A Service Technology Solution Providers Network Security Pictures Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the top Firewall-as-a-Service technology providers. The purpose of this slide is to outline various solutions available for integrating FWaaS in organizations network. These are Fortinet, Palo Alto, Cisco, Sophos and GFI Software.
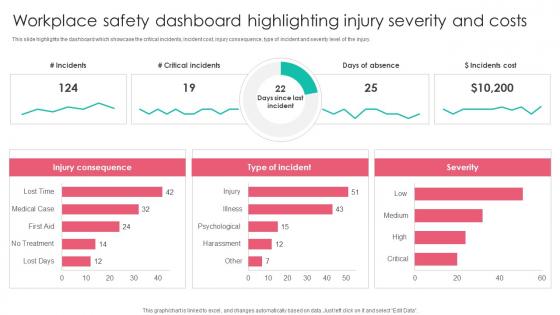
Workplace Safety Dashboard Highlighting Workplace Safety Protocol And Security Practices Elements Pdf
This slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Workplace Safety Dashboard Highlighting Workplace Safety Protocol And Security Practices Elements Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury.

Pictograms To Specify Details Workplace Safety Protocol And Security Practices Download Pdf
This slide highlights the pictograms of chemical hazards which showcase health hazard, flame, exclamation mark, gas cylinder, exploding bomb, cross bones to alert the workers. This Pictograms To Specify Details Workplace Safety Protocol And Security Practices Download Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the pictograms of chemical hazards which showcase health hazard, flame, exclamation mark, gas cylinder, exploding bomb, cross bones to alert the workers.
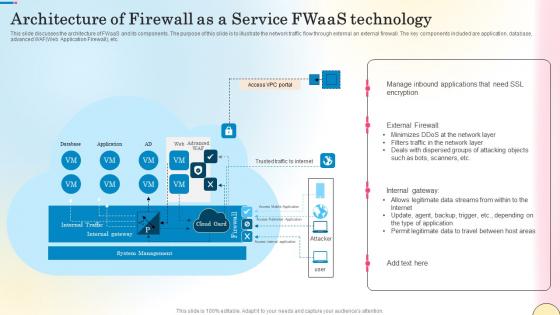
Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf
This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc. Want to ace your presentation in front of a live audience Our Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc.

Information Security Accountability Principle Of GDPR Law Ppt PowerPoint Presentation File Backgrounds PDF
This slide shows the accountability principle, which implies that the data controller or organization is responsible for adhering to all the standards of GDPR and showing compliance if required. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Information Security Accountability Principle Of GDPR Law Ppt PowerPoint Presentation File Backgrounds PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Employee Security Coaching Matrix Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured employee security coaching matrix ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
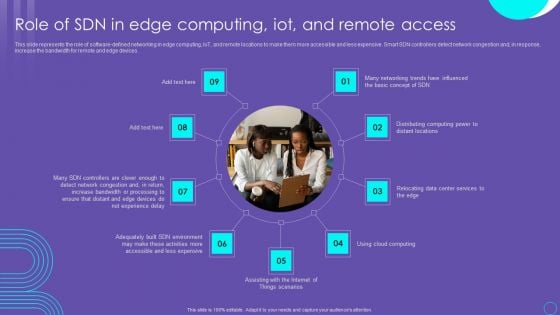
SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF
This slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Boost your pitch with our creative SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
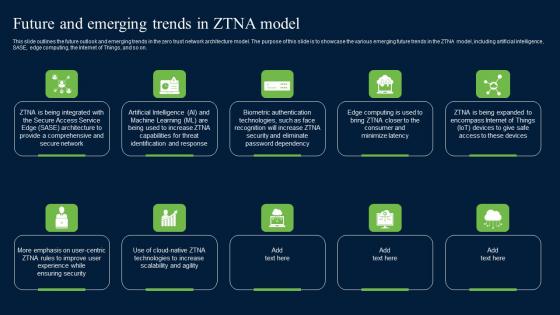
Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.
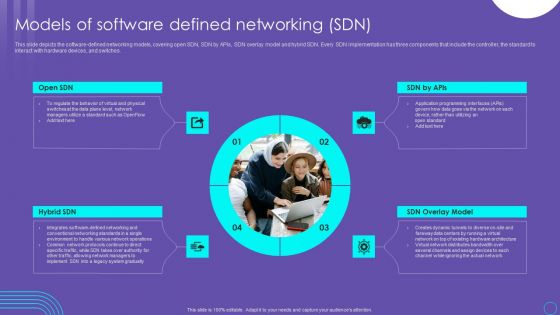
SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF
This slide depicts the software defined networking models, covering open SDN, SDN by APIs, SDN overlay model and hybrid SDN. Every SDN implementation has three components that include the controller, the standard to interact with hardware devices, and switches. Do you know about Slidesgeeks SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
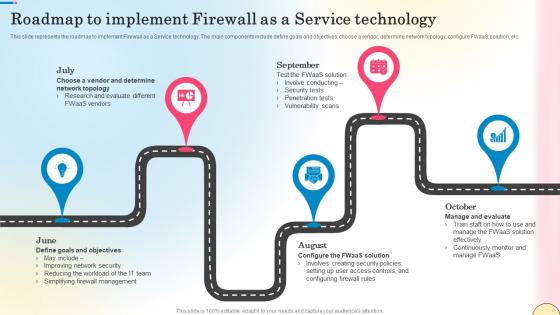
Roadmap To Implement Firewall As A Service Technology Network Security Themes Pdf
This slide represents the roadmap to implement Firewall as a Service technology. The main components include define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roadmap To Implement Firewall As A Service Technology Network Security Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the roadmap to implement Firewall as a Service technology. The main components include define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.
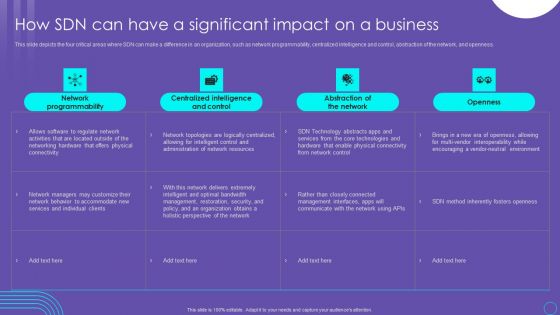
SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF
This slide depicts the four critical areas where SDN can make a difference in an organization, such as network programmability, centralized intelligence and control, abstraction of the network, and openness. Welcome to our selection of the SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today
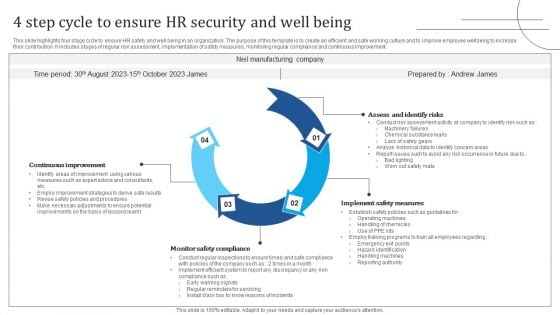
4 Step Cycle To Ensure HR Security And Well Being Graphics PDF
This slide highlights four stage cycle to ensure HR safety and well being in an organization. The purpose of this template is to create an efficient and safe working culture and to improve employee wellbeing to increase their contribution. It includes stages of regular risk assessment, implementation of safety measures, monitoring regular compliance and continuous improvement. Presenting 4 Step Cycle To Ensure HR Security And Well Being Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assess And Identify Risks, Implement Safety Measures, Monitor Safety Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
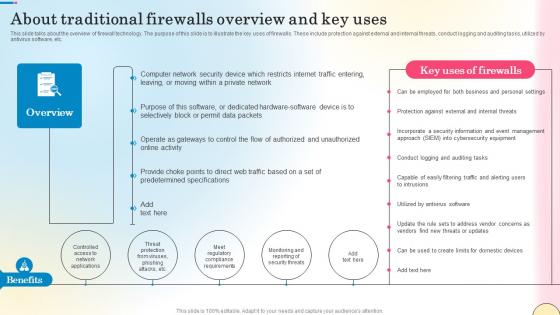
About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf
This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc. Boost your pitch with our creative About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc.
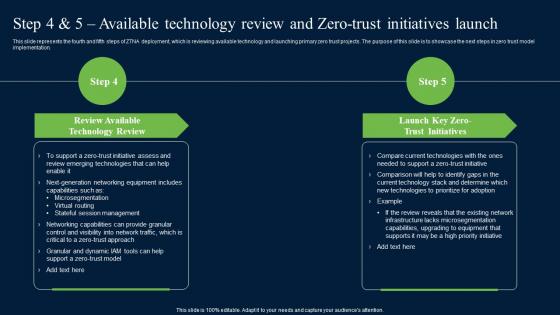
Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. There are so many reasons you need a Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF
This slide represents the importance of virtualization in software defined networking and how they complement one another. It also includes how SDN helps simplify the process of controlling data packet routing via a central server. Retrieve professionally designed SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Technologies Used In Zero Trust Network Access Zero Trust Network Security Portrait Pdf
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Present like a pro with Technologies Used In Zero Trust Network Access Zero Trust Network Security Portrait Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.

Cyber Security Components To Enhance Processes Types Of Cyber Attackers Professional PDF
This slide represents the types of cyber attackers, including cyber criminals, hacktivists, state sponsored attackers, and insider threats. Insider threats can be occurred from within the organization and can be malicious, accidental or negligent. Present like a pro with Cyber Security Components To Enhance Processes Types Of Cyber Attackers Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
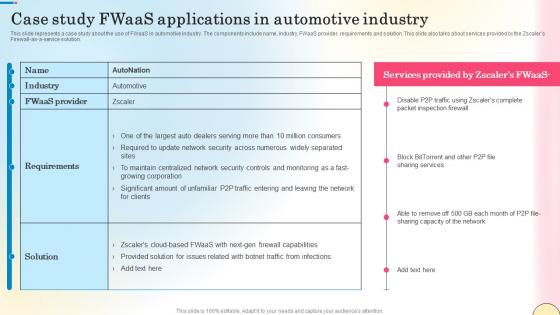
Case Study Fwaas Applications In Automotive Industry Network Security Clipart Pdf
This slide represents a case study about the use of FWaaS in automotive industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about services provided by the Zscalers Firewall-as-a-service solution. Present like a pro with Case Study Fwaas Applications In Automotive Industry Network Security Clipart Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents a case study about the use of FWaaS in automotive industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about services provided by the Zscalers Firewall-as-a-service solution.
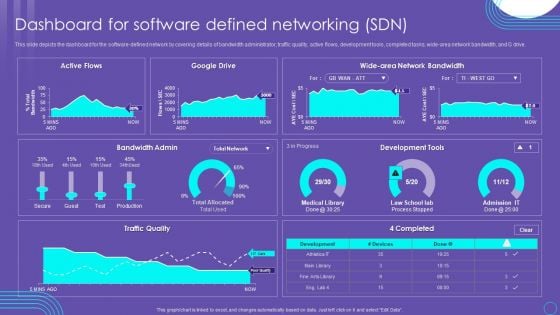
SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF
This slide depicts the dashboard for the software defined network by covering details of bandwidth administrator, traffic quality, active flows, development tools, completed tasks, wide area network bandwidth, and G drive. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
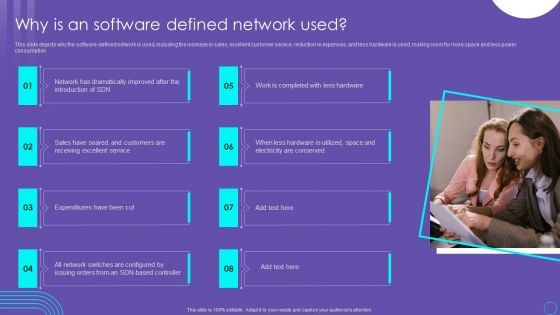
SDN Security Architecture Why Is An Software Defined Network Used Themes PDF
This slide depicts why the software defined network is used, including the increase in sales, excellent customer service, reduction in expenses, and less hardware is used, making room for more space and less power consumption. Present like a pro with SDN Security Architecture Why Is An Software Defined Network Used Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.
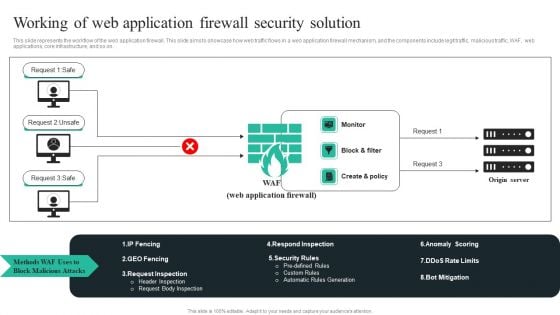
WAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF
This slide represents the workflow of the web application firewall. This slide aims to showcase how web traffic flows in a web application firewall mechanism, and the components include legit traffic, malicious traffic, WAF, web applications, core infrastructure, and so on. Take your projects to the next level with our ultimate collection ofWAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Overview And Workflow Process Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Overview And Workflow Process Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks and deliver a wonderful presentation. The following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc.
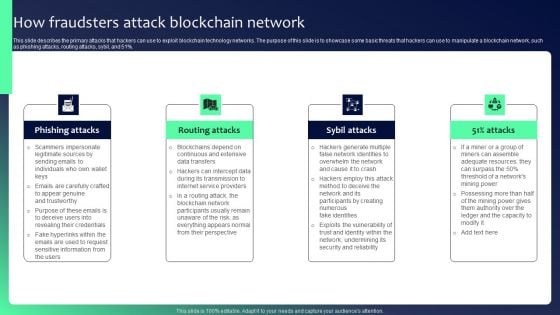
Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF
This slide describes the primary attacks that hackers can use to exploit blockchain technology networks. The purpose of this slide is to showcase some basic threats that hackers can use to manipulate a blockchain network, such as phishing attacks, routing attacks, sybil, and 51 percent. Present like a pro with Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.
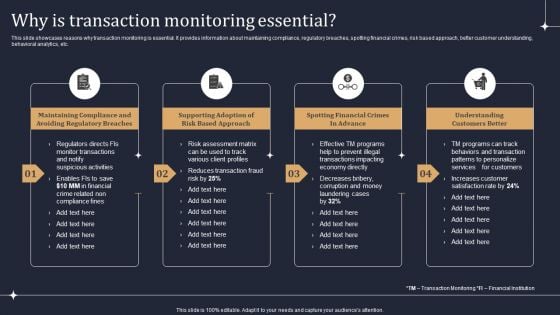
KYC Transaction Monitoring System Business Security Why Is Transaction Monitoring Essential Designs PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Present like a pro with KYC Transaction Monitoring System Business Security Why Is Transaction Monitoring Essential Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Major Cryptocurrency Blockchain Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide showcases major cryptocurrency and blockchain cybersecurity scams throughout the globe. It includes elements such as Decentralized autonomous organization DAO attack, gox attack, plus token scams, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Major Cryptocurrency Blockchain Comprehensive Guide To Blockchain Digital Security Download Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The following slide showcases major cryptocurrency and blockchain cybersecurity scams throughout the globe. It includes elements such as Decentralized autonomous organization DAO attack, gox attack, plus token scams, etc.
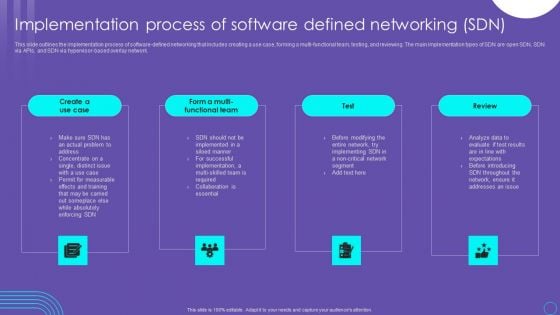
SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF
This slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. The SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
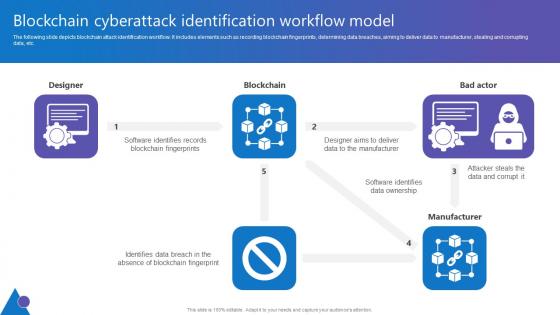
Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf
The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Take your projects to the next level with our ultimate collection of Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc.
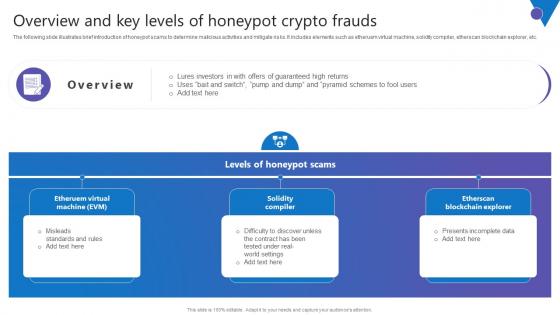
Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf
The following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as etheruem virtual machine, solidity compiler, etherscan blockchain explorer, etc. Welcome to our selection of the Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today The following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as etheruem virtual machine, solidity compiler, etherscan blockchain explorer, etc.
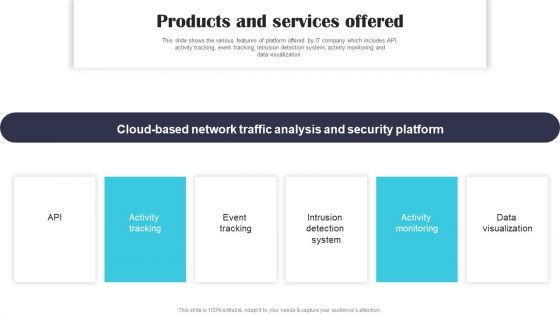
Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF
This slide shows the various features of platform offered by IT company which includes API, activity tracking, event tracking, intrusion detection system, activity monitoring and data visualization. This modern and well arranged Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
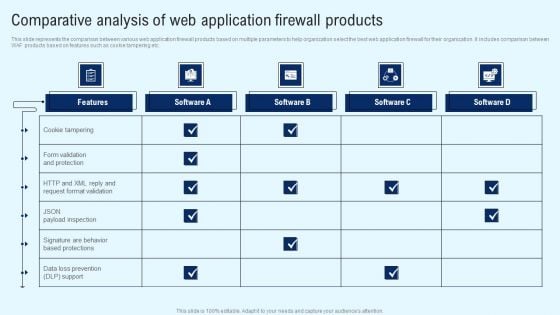
Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Security Software Company Investor Funding Pitch Deck Exit Strategy Information PDF
The slide provides most profitable or feasible ways for investors to exit from their investment in the company. It includes IPO, merger, private offerings, acquisition by venture capital firm etc. Present like a pro with Security Software Company Investor Funding Pitch Deck Exit Strategy Information PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
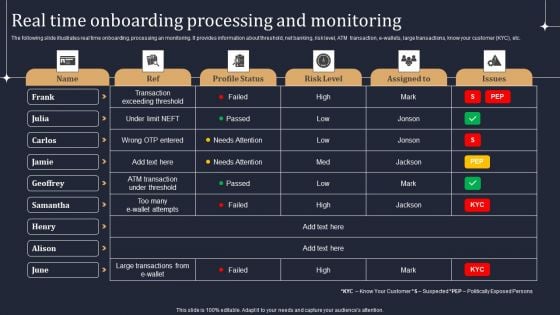
KYC Transaction Monitoring System Business Security Real Time Onboarding Processing And Monitoring Demonstration PDF
The following slide illustrates real time onboarding, processing an monitoring. It provides information about threshold, net banking, risk level, ATM transaction, e-wallets, large transactions, know your customer KYC, etc. Slidegeeks has constructed KYC Transaction Monitoring System Business Security Real Time Onboarding Processing And Monitoring Demonstration PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Industrial Security System For Large Areas Technology Process Ppt PowerPoint Presentation Complete Deck
Boost your confidence and team morale with this well-structured industrial security system for large areas technology process ppt powerpoint presentation complete deck. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of eleven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
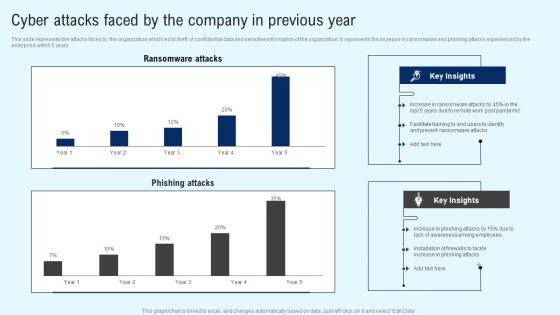
Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
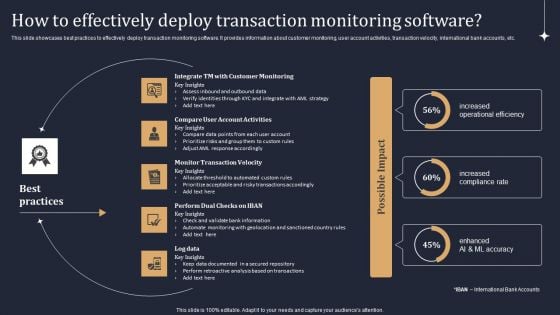
KYC Transaction Monitoring System Business Security How To Effectively Deploy Transaction Brochure PDF
This slide showcases best practices to effectively deploy transaction monitoring software. It provides information about customer monitoring, user account activities, transaction velocity, international bank accounts, etc. Do you know about Slidesgeeks KYC Transaction Monitoring System Business Security How To Effectively Deploy Transaction Brochure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

KYC Transaction Monitoring System Business Security Importance Of Regular Financial Activity Observation Elements PDF
This slide showcases importance of regular transaction monitoring. It provides information about enhanced efficiency, optimal client segmentation, cost reduction, improved oversight, false positives, fraud detection, investigation, visibility, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate KYC Transaction Monitoring System Business Security Importance Of Regular Financial Activity Observation Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
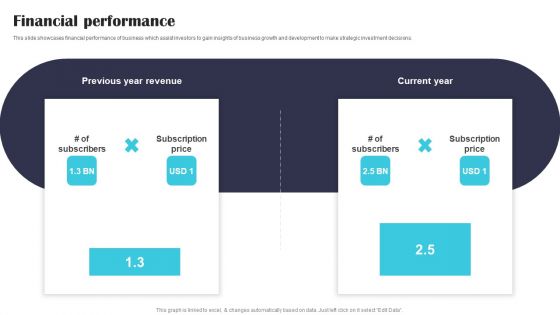
Security Software Company Investor Funding Pitch Deck Financial Performance Formats PDF
This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Software Company Investor Funding Pitch Deck Financial Performance Formats PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
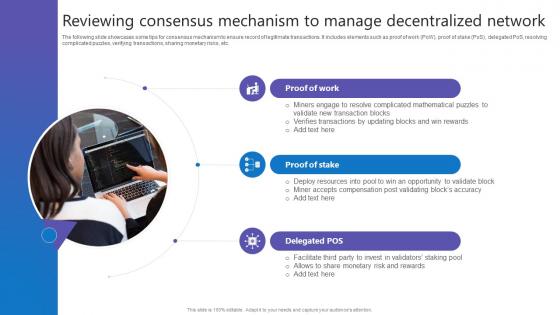
Reviewing Consensus Mechanism Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases some tips for consensus mechanism to ensure record of legitimate transactions. It includes elements such as proof of work PoW, proof of stake PoS, delegated PoS, resolving complicated puzzles, verifying transactions, sharing monetary risks, etc. Find a pre designed and impeccable Reviewing Consensus Mechanism Comprehensive Guide To Blockchain Digital Security Summary Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide showcases some tips for consensus mechanism to ensure record of legitimate transactions. It includes elements such as proof of work PoW, proof of stake PoS, delegated PoS, resolving complicated puzzles, verifying transactions, sharing monetary risks, etc.

Comprehensive Guide For Ensuring IT Infrastructure Security Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Comprehensive Guide For Ensuring IT Infrastructure Security Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Enhancing Cloud Security With CASB Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Enhancing Cloud Security With CASB Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc.

On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
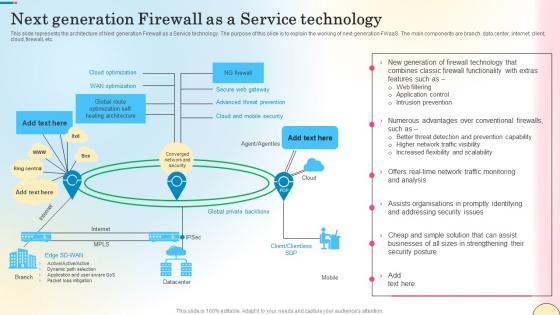
Next Generation Firewall As A Service Technology Network Security Mockup Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Do you know about Slidesgeeks Next Generation Firewall As A Service Technology Network Security Mockup Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc.


 Continue with Email
Continue with Email

 Home
Home


































