Security Management
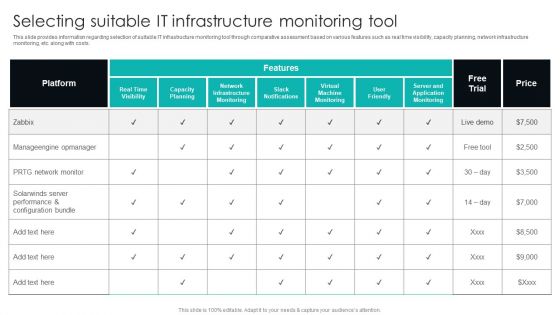
IT Infrastructure Library Procedure Management Playbook Selecting Suitable IT Infrastructure Monitoring Tool Designs PDF
This slide provides information regarding selection of suitable IT infrastructure monitoring tool through comparative assessment based on various features such as real time visibility, capacity planning, network infrastructure monitoring, etc. along with costs. Present like a pro with IT Infrastructure Library Procedure Management Playbook Selecting Suitable IT Infrastructure Monitoring Tool Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
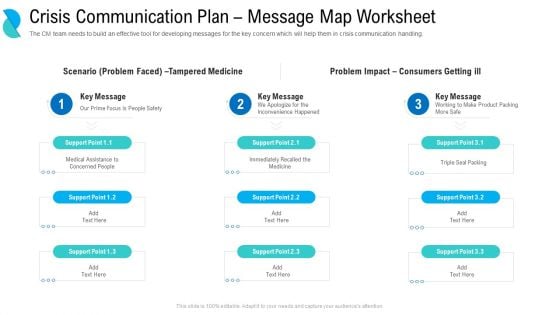
Determining Crisis Management BCP Crisis Communication Plan Message Map Worksheet Graphics PDF
The CM team needs to build an effective tool for developing messages for the key concern which will help them in crisis communication handling. Presenting determining crisis management bcp crisis communication plan message map worksheet graphics pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like scenario problem faced, tampered medicine, problem impact consumers getting ill, our prime focus is people safety, we apologize for the inconvenience happened, working to make product packing more safe. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective Brand Reputation Management Deploying Customer Reward Program To Enhance Slides PDF
This slide provides information regarding customer reward system deployed by brand in order to increase brand loyalty. The reward system is categorized based on the type of rewards, value offered, uniqueness, accessibility, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Effective Brand Reputation Management Deploying Customer Reward Program To Enhance Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Selecting The Best Talent Using External Sources Of General Management Introduction Pdf
The following slide showcases various sources of external recruitment which can be used by healthcare professionals to identify the right talent for the given position. Advertisements, job portals, official career site and social networking platforms are the major sources which are mentioned in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Selecting The Best Talent Using External Sources Of General Management Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide showcases various sources of external recruitment which can be used by healthcare professionals to identify the right talent for the given position. Advertisements, job portals, official career site and social networking platforms are the major sources which are mentioned in the slide.

Red Flags To Be Cautious For Cryptocurrency Scams Cryptocurrency Management With Blockchain
This slide discusses the red flags that should be considered while doing transactions in cryptocurrency. This slide aims to highlight flags such as promises of guaranteed returns, lack of project transparency, pressure to act quickly, etc.Slidegeeks is here to make your presentations a breeze with Red Flags To Be Cautious For Cryptocurrency Scams Cryptocurrency Management With Blockchain With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide discusses the red flags that should be considered while doing transactions in cryptocurrency. This slide aims to highlight flags such as promises of guaranteed returns, lack of project transparency, pressure to act quickly, etc.

Major Drivers For Adopting Industrial Internet Of Things Optimizing Inventory Management IoT SS V
This slide provides an overview of the main drivers for adopting IoT in manufacturing and streamlining operations. Major drivers covered are reduced cost, shorter marketing time, mass personalization and better safety. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Drivers For Adopting Industrial Internet Of Things Optimizing Inventory Management IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide provides an overview of the main drivers for adopting IoT in manufacturing and streamlining operations. Major drivers covered are reduced cost, shorter marketing time, mass personalization and better safety.
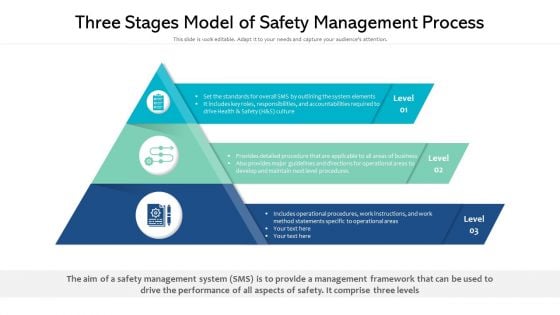
Three Stages Model Of Safety Management Process Ppt PowerPoint Presentation Professional Brochure PDF
Persuade your audience using this v. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including set the standards for overall sms by outlining the system elements, provides detailed procedure that are applicable to all areas of business, includes operational procedures, work instructions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Supply Network Logistics Management Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of twenty five slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

Developing An Action Plan For Supply Network Management Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fortyfive slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
Business Strategy Formulation Focal Point Hub And Spoke 3 Stages Management
We present our business strategy formulation focal point hub and spoke 3 stages management.Present our Marketing PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Download our Business PowerPoint Templates because you should once Tap the ingenuity of our PowerPoint Templates and Slides. They are programmed to succeed. Download and present our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will effectively help you save your valuable time. They are readymade to fit into any presentation structure. Download our Process and Flows PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process.Use these PowerPoint slides for presentations relating to Arrow, Blue, Box, Brochure, Business, Button, Catalog, Chart, Circle, Company, Cross, Data, Design, Diagram, Direction, Document, Financial, Glossy, Goals, Graph, Junction, Management, Market, Marketing, Model, Multicolored, Multiple, Navigation, Network, Options, Orange, Pie, Plan, Presentation, Process, Red, Results, Shiny, Sphere, Statistics, Stock, Structure, Template. The prominent colors used in the PowerPoint template are White, Gray, Black. Complete your presentation with our Business Strategy Formulation Focal Point Hub And Spoke 3 Stages Management. Just download, type and present.

Product Portfolio Management For New Target Region Addressing Business Summary PDF
This slide shows the product analysis of XYZ company with their products details such as clients, safety, size, cost, etc.This is a Efficient Ways For Successful Project Administration Product Analysis Including Details And Costs Topics PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Function, Manufacture, Cost, Aesthetics, Safety You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Relationship Management Tool Partner Enablement Challenges And Their Solutions Diagrams PDF
This slide covers the challenges faced by partner enablement such as message inconsistency, inefficient sales, growing networks, etc. along with their solutions. Presenting This slide provides the reasons for introducing partner enablement in the company such as decreasing sales, lack of knowledge and training for selling products and services, etc. to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like consistency, credibility, organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
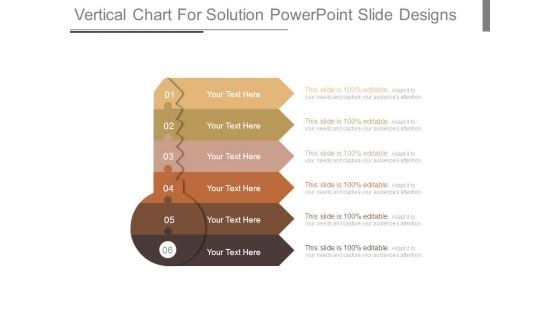
Vertical Chart For Solution Powerpoint Slide Designs
This is a vertical chart for solution powerpoint slide designs. This is a six stage process. The stages in this process are business, success, management, strategy, security.

Strategies To Enhance Managed Service Business Managed Services Industry Trends Information PDF
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. There are so many reasons you need a Strategies To Enhance Managed Service Business Managed Services Industry Trends Information PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Three Level Business Continuity Diagram Ppt Slides
This is a three level business continuity diagram ppt slides. This is a three stage process. The stages in this process are business continuity planning, security management, disaster recovery, technology, roles, testing, risk management, data assessment, coordination, communicating plan, policy, technology, services, procedures, incident response.
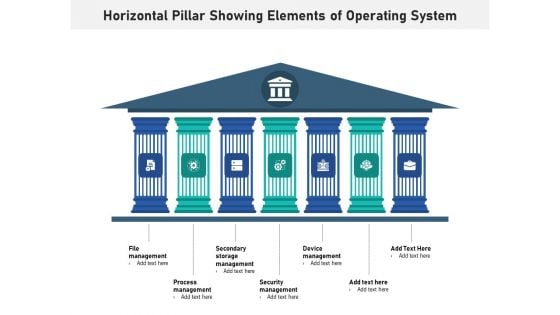
Horizontal Pillar Showing Elements Of Operating System Ppt PowerPoint Presentation Layouts Graphics Pictures PDF
Presenting horizontal pillar showing elements of operating system ppt powerpoint presentation layouts graphics pictures pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including file management, process management, secondary storage management, security management, device management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
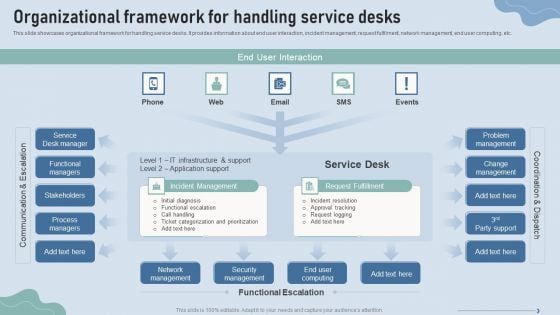
Improve IT Service Desk Organizational Framework For Handling Service Desks Background PDF
This slide showcases organizational framework for handling service desks. It provides information about end user interaction, incident management, request fulfilment, network management, end user computing, etc. Deliver and pitch your topic in the best possible manner with this Improve IT Service Desk Organizational Framework For Handling Service Desks Background PDF. Use them to share invaluable insights on Security Management, Network Management, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
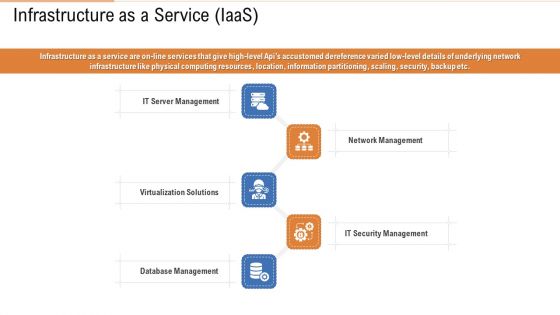
Public Vs Privatized Vs Hybrid Vs Alliance In Cloud Storage Infrastructure As A Service Iaas Formats PDF
This is a public vs privatized vs hybrid vs alliance in cloud storage infrastructure as a service iaas formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network management, security management, database management, server management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V
This slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc.
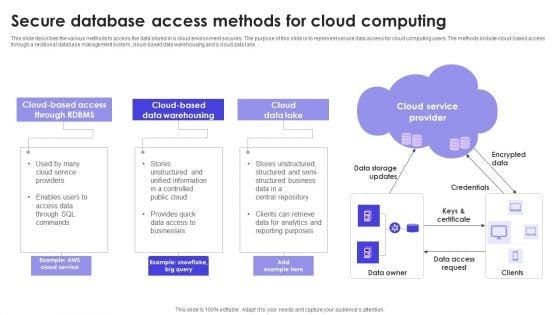
Secure Database Access Methods For Cloud Computing Formats PDF
This slide describes the various methods to access the data stored in a cloud environment securely. The purpose of this slide is to represent secure data access for cloud computing users. The methods include cloud-based access through a relational database management system, cloud-based data warehousing and a cloud data lake. Persuade your audience using this Secure Database Access Methods For Cloud Computing Formats PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Data Lake, Data Warehousing, Cloud Service Provider. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
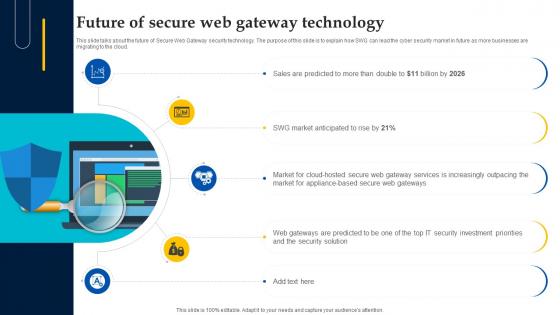
Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.

Future Of Secure Web Gateway Technology Web Threat Protection System
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Future Of Secure Web Gateway Technology Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.
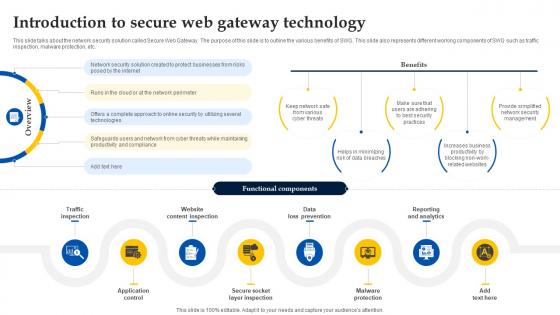
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
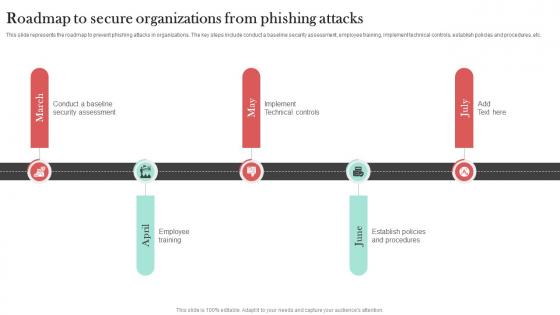
Roadmap To Secure Organizations Man In The Middle Phishing IT
This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roadmap To Secure Organizations Man In The Middle Phishing IT and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Data Safety And Privacy Benefits Of Fomfarm Digital Platform To Fred Farming Company Management Strategy Portrait PDF
This slide shows data safety and privacy benefits of fomfarm digital platform to fred farming company such as ownership, collection and control, transparency, choice, liability and security etc.This is a Data Safety And Privacy Benefits Of Fomfarm Digital Platform To Fred Farming Company Management Strategy Portrait PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Platform Is Committed, Contractual Agreement, Reasonable Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Web Access Control Solution Checklist To Implement Secure Web Gateway
This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Web Access Control Solution Checklist To Implement Secure Web Gateway and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.
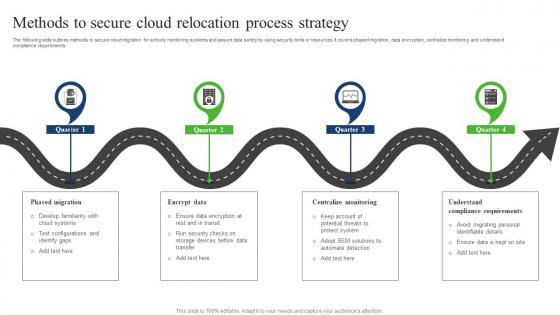
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements.
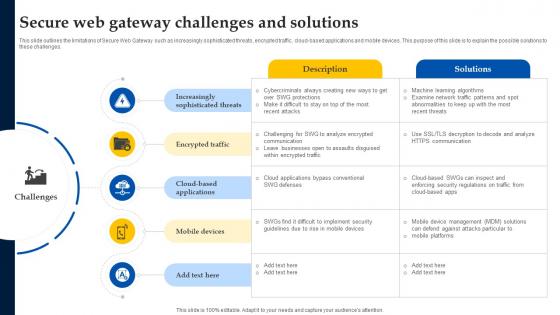
Web Access Control Solution Secure Web Gateway Challenges And Solutions
This slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges. Want to ace your presentation in front of a live audience Our Web Access Control Solution Secure Web Gateway Challenges And Solutions can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges.

Web Access Control Solution Secure Web Gateway Training Program
This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Slidegeeks is here to make your presentations a breeze with Web Access Control Solution Secure Web Gateway Training Program With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.
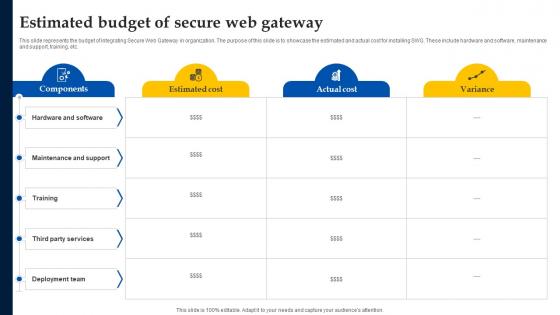
Web Access Control Solution Estimated Budget Of Secure Web Gateway
This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Web Access Control Solution Estimated Budget Of Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Web Access Control Solution Estimated Budget Of Secure Web Gateway. This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
Proportional Reasoning Powerpoint Slides
This is a proportional reasoning powerpoint slides. This is a six stage process. The stages in this process are puzzle, key, security, strategy, management, business.
Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard
This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc. Get a simple yet stunning designed Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc.

Service Agreement For Securing More Clients Brochure PDF
Purpose of this slide is to show service agreement that will assist service managers in gaining the attention on new clients. Sections covered in the agreement are parties, invoices, list of service and signature.Deliver an awe inspiring pitch with this creative Service Agreement For Securing More Clients Brochure PDF bundle. Topics like Agreement Is Entered, Services Provide, Term Of Agreement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
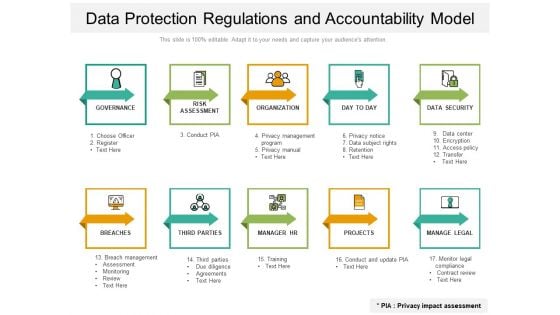
Data Protection Regulations And Accountability Model Ppt PowerPoint Presentation Styles Microsoft PDF
Presenting data protection regulations and accountability model ppt powerpoint presentation styles microsoft pdf. to dispense important information. This template comprises ten stages. It also presents valuable insights into the topics including organization, data security, manage legal, projects, manager hr, governance, risk assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Web Gateway Implementation Scenarios Web Access Control Solution
This slide represents the different types of Secure Web Gateway deployment methods. The purpose of this slide is to outline SWG implementation methodologies. These are inline, explicit, transparent and SPAN Switched Port Analyzer port. Want to ace your presentation in front of a live audience Our Secure Web Gateway Implementation Scenarios Web Access Control Solution can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the different types of Secure Web Gateway deployment methods. The purpose of this slide is to outline SWG implementation methodologies. These are inline, explicit, transparent and SPAN Switched Port Analyzer port.
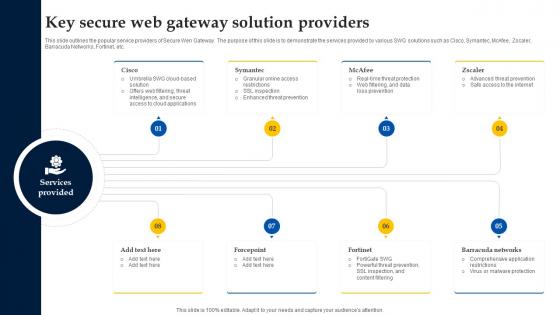
Web Access Control Solution Key Secure Web Gateway Solution Providers
This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Web Access Control Solution Key Secure Web Gateway Solution Providers to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Web Access Control Solution Key Secure Web Gateway Solution Providers. This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc.
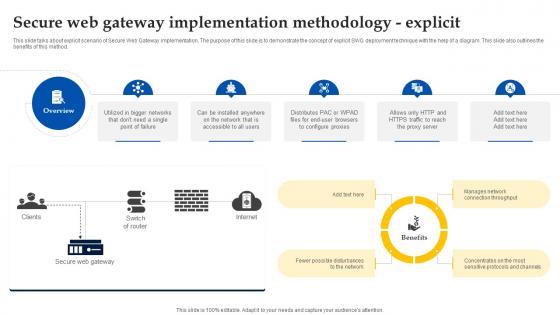
Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit
This slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit a try. Our experts have put a lot of knowledge and effort into creating this impeccable Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
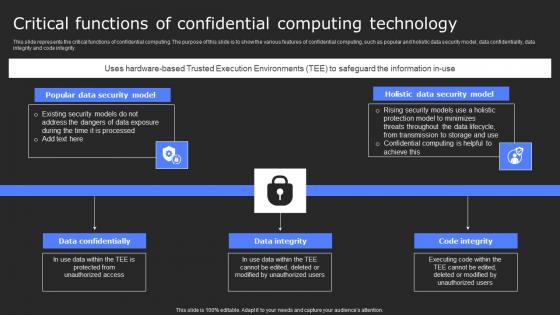
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
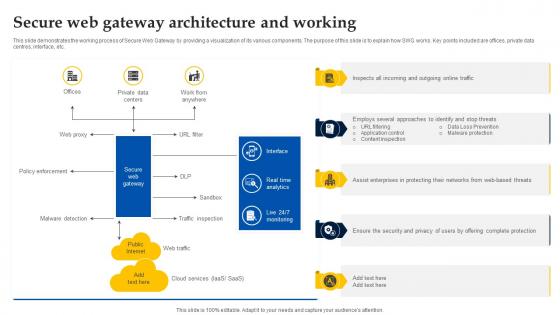
Web Access Control Solution Secure Web Gateway Architecture And Working
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Web Access Control Solution Secure Web Gateway Architecture And Working for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.
Types Of Convertible Securities Ppt PowerPoint Presentation Model Portrait
This is a types of convertible securities ppt powerpoint presentation model portrait. This is a six stage process. The stages in this process are business, management, marketing, process.

Types Of Convertible Securities Ppt PowerPoint Presentation File Information
This is a types of convertible securities ppt powerpoint presentation file information. This is a six stage process. The stages in this process are business, management, marketing.
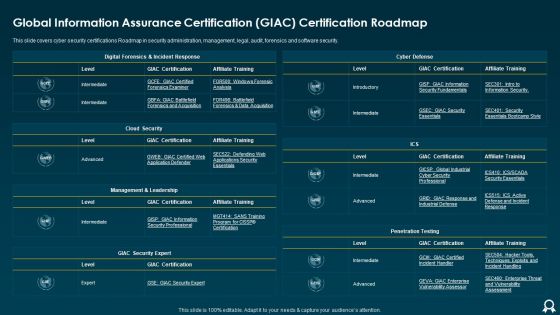
Global Information Assurance Certification GIAC Certification Roadmap Formats PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver an awe inspiring pitch with this creative Global Information Assurance Certification GIAC Certification Roadmap Formats PDF bundle. Topics like Cloud Security, Cyber Defense, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
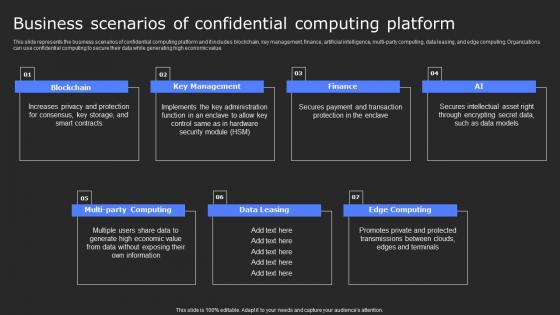
Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
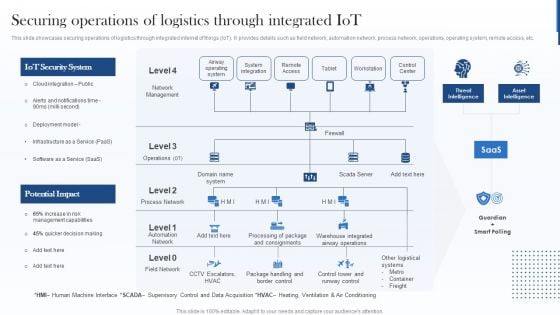
Securing Operations Of Logistics Through Integrated Iot Guidelines PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Deliver and pitch your topic in the best possible manner with this Securing Operations Of Logistics Through Integrated Iot Guidelines PDF. Use them to share invaluable insights on Iot Security System, Potential Impact, Warehouse and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Types Of Convertible Securities Ppt PowerPoint Presentation Layouts Graphics Template
This is a types of convertible securities ppt powerpoint presentation layouts graphics template. This is a six stage process. The stages in this process are management, marketing, business, strategy, process.

Valuation Of Equity Securities Ppt PowerPoint Presentation Inspiration Picture
This is a valuation of equity securities ppt powerpoint presentation inspiration picture. This is a six stage process. The stages in this process are management, marketing, business, strategy, process.

Valuation Of Equity Securities Ppt PowerPoint Presentation Outline Professional
This is a valuation of equity securities ppt powerpoint presentation outline professional. The topics discussed in this diagram are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation, and is available for immediate download.
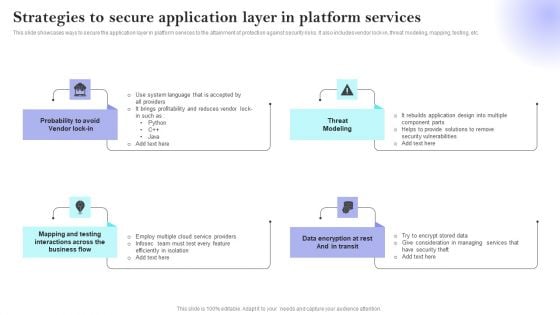
Strategies To Secure Application Layer In Platform Services Topics PDF
This slide showcases ways to secure the application layer in platform services to the attainment of protection against security risks. It also includes vendor lock-in, threat modeling, mapping, testing, etc. Presenting Strategies To Secure Application Layer In Platform Services Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Probability, Threat Modeling, Data Encryption Rest Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
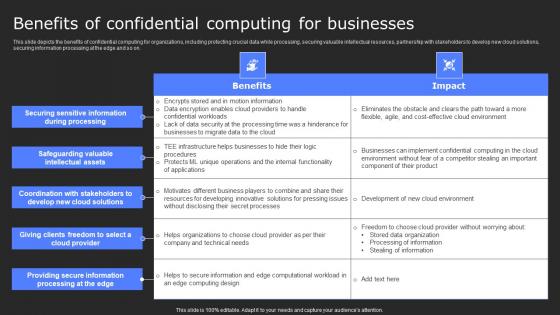
Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.

Secure Web Gateway Implementation Methodology Inline Web Access Control Solution
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Create an editable Secure Web Gateway Implementation Methodology Inline Web Access Control Solution that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Secure Web Gateway Implementation Methodology Inline Web Access Control Solution is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.

Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. This Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.

Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
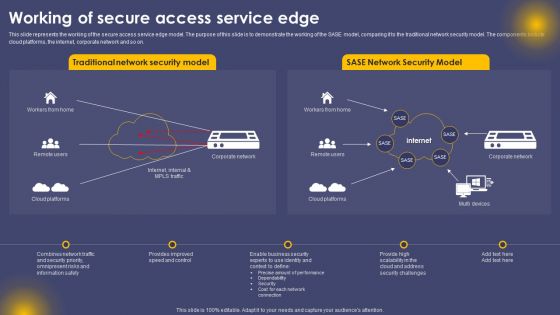
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Secure Home Network Diagram In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Home Network Diagram In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Home Network Diagram that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Secure Home Network Diagram In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Estimated Budget Of Secure Web Gateway Web Threat Protection System
This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Estimated Budget Of Secure Web Gateway Web Threat Protection System can be your best option for delivering a presentation. Represent everything in detail using Estimated Budget Of Secure Web Gateway Web Threat Protection System and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc.

Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf
This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Get a simple yet stunning designed Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD.

Comparison Between ZTNA And Secure Access Service Edge Professional PDF
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparison Between ZTNA And Secure Access Service Edge Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Secure Web Gateways Market In Powerpoint And Google Slides Cpb
Introducing our well-designed Secure Web Gateways Market In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Web Gateways Market. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Web Gateways Market In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Sdlc Policy Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































