Security Management
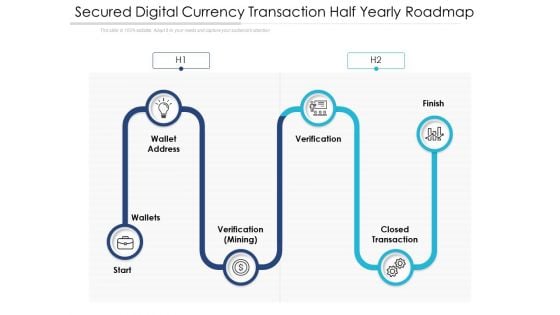
Secured Digital Currency Transaction Half Yearly Roadmap Portrait
Introducing our secured digital currency transaction half yearly roadmap portrait. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
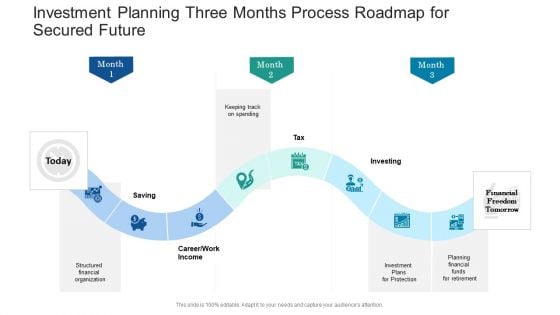
Investment Planning Three Months Process Roadmap For Secured Future Slides
Presenting our jaw dropping investment planning three months process roadmap for secured future slides. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
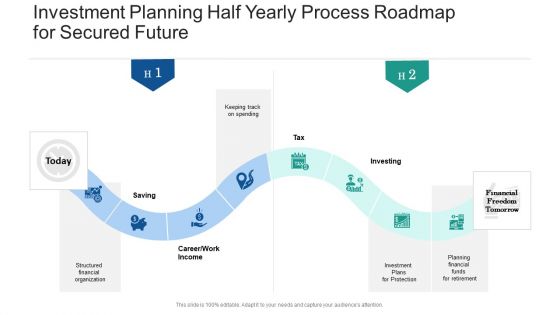
Investment Planning Half Yearly Process Roadmap For Secured Future Topics
Presenting the investment planning half yearly process roadmap for secured future topics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

P2P Ledger Is Blockchain Technology Secure Download PDF
This slide describes the impact of blockchain technology on the organization post-implementation and how it will help businesses grow from various prospects.This modern and well-arranged P2P Ledger Is Blockchain Technology Secure Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
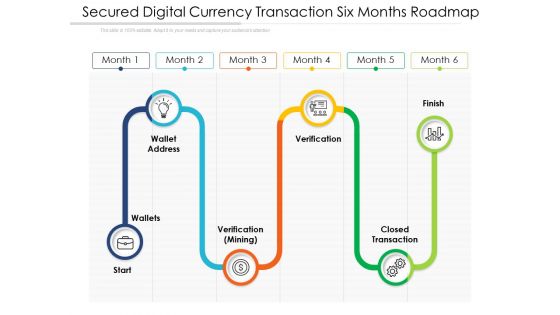
Secured Digital Currency Transaction Six Months Roadmap Guidelines
Presenting the secured digital currency transaction six months roadmap guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
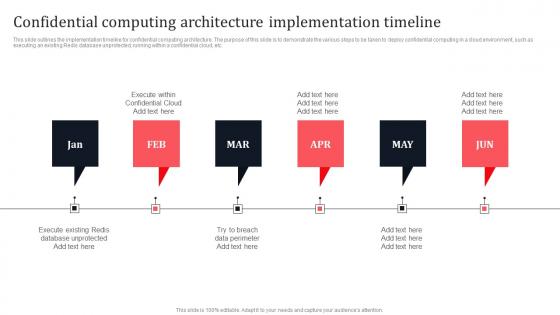
Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Find highly impressive Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.

Mutual Fund Accounting Plan Ppt Powerpoint Slide Designs
This is a mutual fund accounting plan ppt powerpoint slide designs. This is a four stage process. The stages in this process are returns, investors, securities, fund managers.
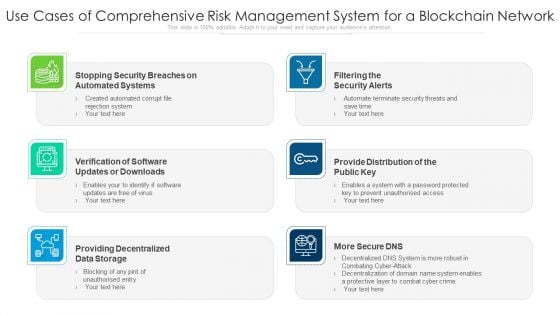
Use Cases Of Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Outline Background Designs PDF
Presenting use cases of comprehensive risk management system for a blockchain network ppt powerpoint presentation outline background designs pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including filtering the security alerts, provide distribution of the public key, providing decentralized data storage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
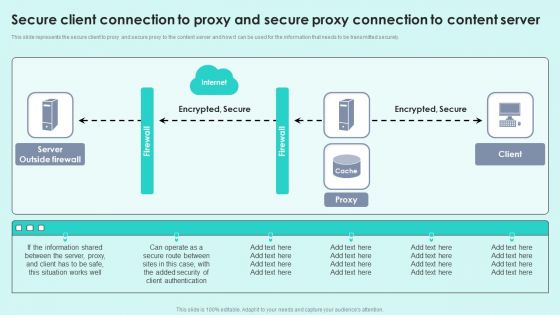
Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely.Deliver and pitch your topic in the best possible manner with this Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF. Use them to share invaluable insights on Server Outside, Between Server, Situation Works and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
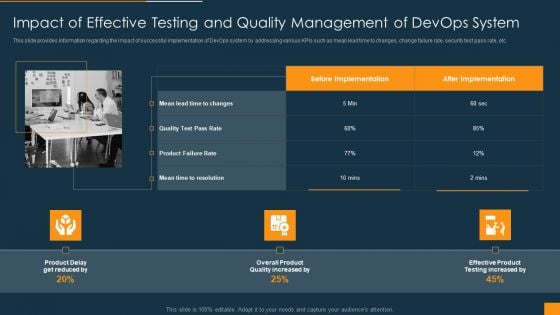
Function Of Quality Assurance In Devops IT Impact Of Effective Testing And Quality Management Of Devops System Formats PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. This is a function of quality assurance in devops it impact of effective testing and quality management of devops system formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like merging of teams, performance and quality metrics, development collaboration You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
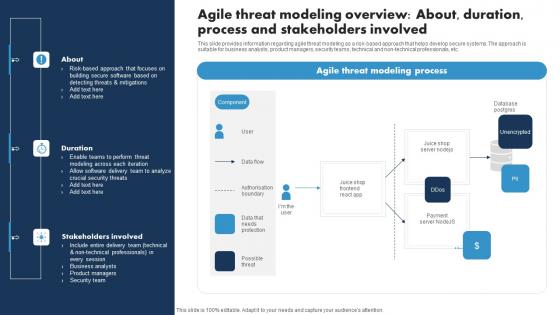
Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.
Distributed Computing IT Dashboard For Edge Computing Tracking Template PDF
This slide depicts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details. Deliver and pitch your topic in the best possible manner with this distributed computing it dashboard for edge computing tracking template pdf. Use them to share invaluable insights on monitoring, security, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
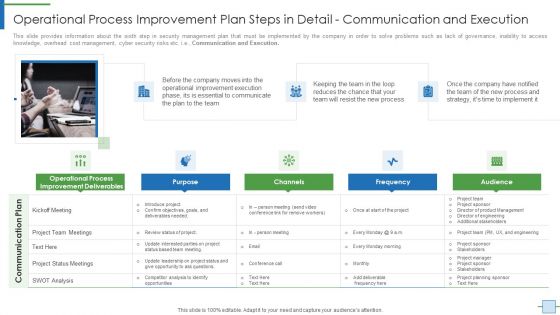
Operational Process Improvement Plan Steps In Detail Communication And Execution Information PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like communicate, team, process, reduces, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Graphics PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational efficiency execution strategy improve quality operational process improvement plan graphics pdfS template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like team, resource, process, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
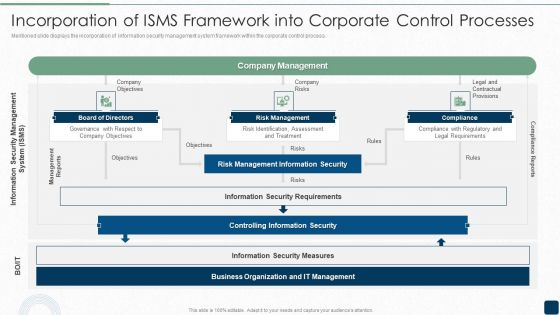
Incorporation Of ISMS Framework Into Corporate Control Processes Inspiration PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Inspiration PDF. Use them to share invaluable insights on Risk Management, Management Information, Controlling Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
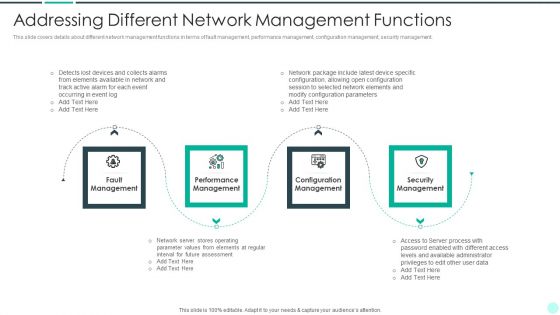
Executing Advance Data Analytics At Workspace Addressing Different Network Rules PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing different network rules pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, performance, security, elements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
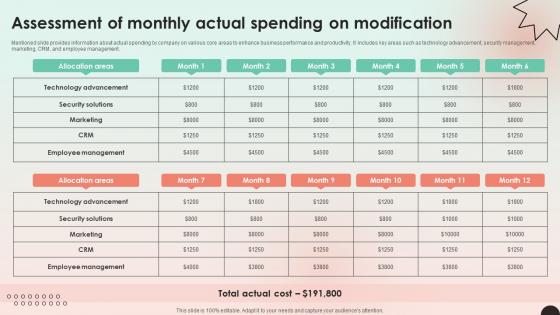
Web Consulting Business Assessment Of Monthly Actual Spending On Modification
Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management. Present like a pro with Web Consulting Business Assessment Of Monthly Actual Spending On Modification. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management.

Web Consulting Business Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. The Web Consulting Business Estimated Annual Budget Plan For Web Company is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management.
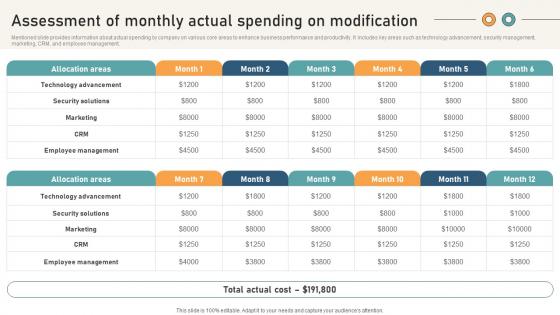
Comprehensive Guide For Website Assessment Of Monthly Actual Spending On Modification
Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management. Get a simple yet stunning designed Comprehensive Guide For Website Assessment Of Monthly Actual Spending On Modification. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Guide For Website Assessment Of Monthly Actual Spending On Modification can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management.
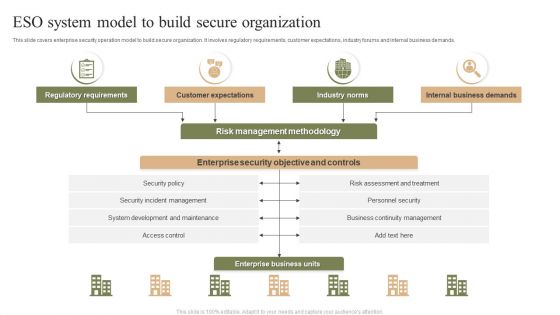
ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF
This slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Showcasing this set of slides titled ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF. The topics addressed in these templates are Customer Expectations, Industry Norms, Internal Business Demands. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
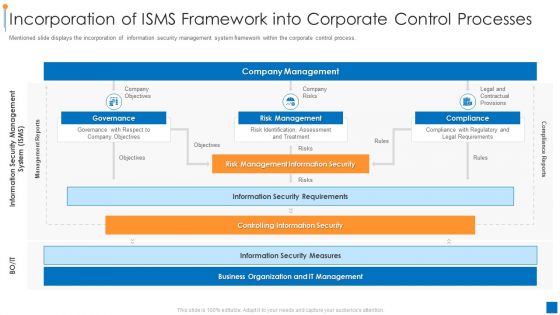
International Organization Standardization 270001 Incorporation Of Isms Framework Into Corporate Control Processes Summary PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process. Deliver an awe inspiring pitch with this creative international organization standardization 270001 incorporation of isms framework into corporate control processes summary pdf bundle. Topics like company objectives, risk management, compliance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
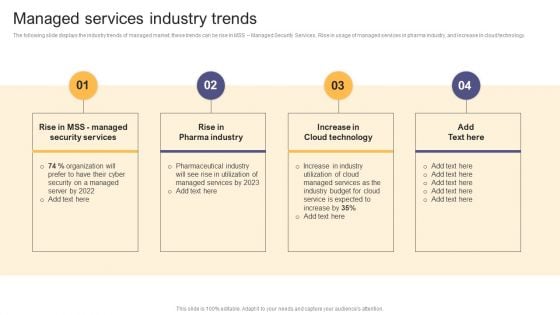
Per Device Pricing Strategy For Managed Solutions Managed Services Industry Trends Mockup PDF
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. Are you searching for a Per Device Pricing Strategy For Managed Solutions Managed Services Industry Trends Mockup PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Per Device Pricing Strategy For Managed Solutions Managed Services Industry Trends Mockup PDF from Slidegeeks today.
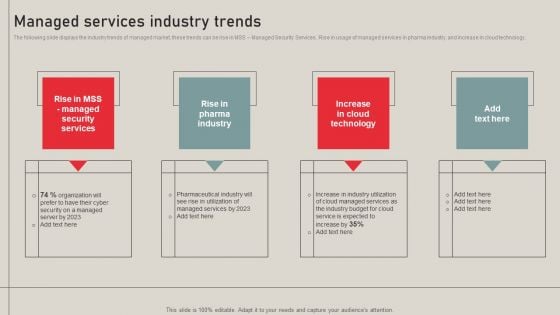
Individualized Pricing Approach For Managed Services Managed Services Industry Trends Infographics PDF
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Individualized Pricing Approach For Managed Services Managed Services Industry Trends Infographics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Health Protection Plan For Secured Life Vector Icon Ppt PowerPoint Presentation Slides Examples PDF
Pitch your topic with ease and precision using this health protection plan for secured life vector icon ppt powerpoint presentation slides examples pdf. This layout presents information on health protection plan for secured life vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Protection Vector Showing Secured Bitcoin With Dollar Symbol Ppt PowerPoint Presentation Infographic Template Icon PDF
Showcasing this set of slides titled protection vector showing secured bitcoin with dollar symbol ppt powerpoint presentation infographic template icon pdf. The topics addressed in these templates are protection vector showing secured bitcoin with dollar symbol. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
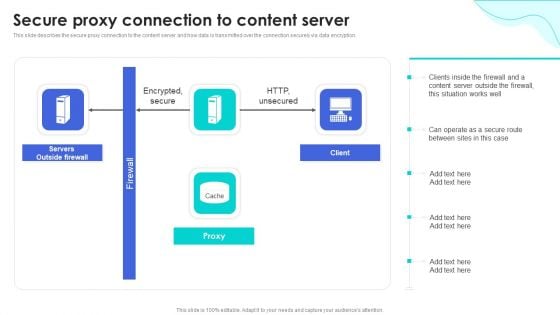
Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Find a pre-designed and impeccable Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
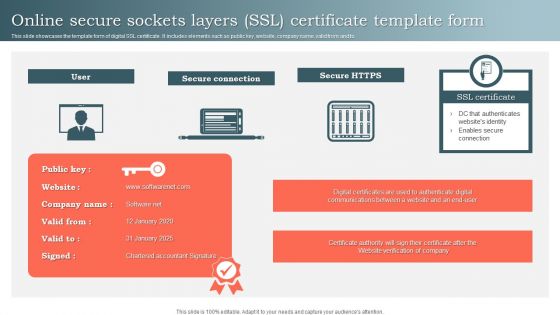
Online Secure Sockets Layers SSL Certificate Template Form Ppt Summary Examples PDF
This slide showcases the template form of digital SSL certificate. It includes elements such as public key, website, company name, valid from and to. Presenting Online Secure Sockets Layers SSL Certificate Template Form Ppt Summary Examples PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User, Secure Connection, Secure HTTPS, SSL Certificate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
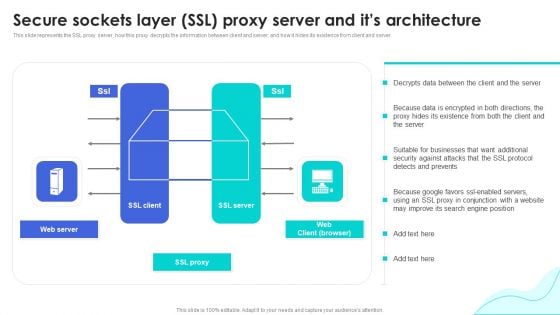
Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF
This slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. Boost your pitch with our creative Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Audit Committee Corporate Priorities Ppt Examples
This is a audit committee corporate priorities ppt examples. This is a nine stage process. The stages in this process are audit committee, corporate priorities, programmed statements, business plan, senior management committee, security committee, senior executive committee, people management committee.
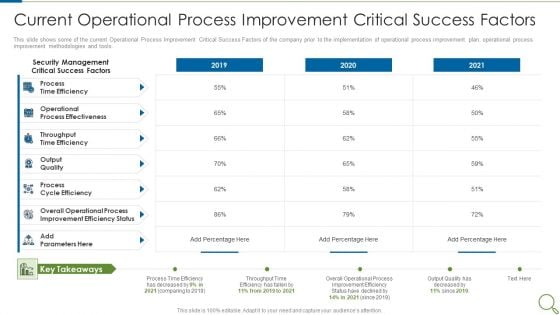
Current Operational Process Improvement Critical Success Factors Topics PDF
This slide shows some of the current Operational Process Improvement Critical Success Factors of the company prior to the implementation of operational process improvement plan, operational process improvement methodologies and tools. Deliver and pitch your topic in the best possible manner with this current operational process improvement critical success factors topics pdf. Use them to share invaluable insights on process, output quality, security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
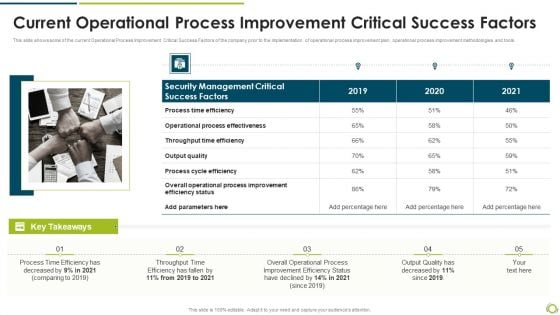
Current Operational Process Improvement Critical Success Factors Sample PDF
This slide shows some of the current Operational Process Improvement Critical Success Factors of the company prior to the implementation of operational process improvement plan, operational process improvement methodologies and tools.Deliver an awe inspiring pitch with this creative current operational process improvement critical success factors sample pdf bundle. Topics like security management critical, process time efficiency, throughput time efficiency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
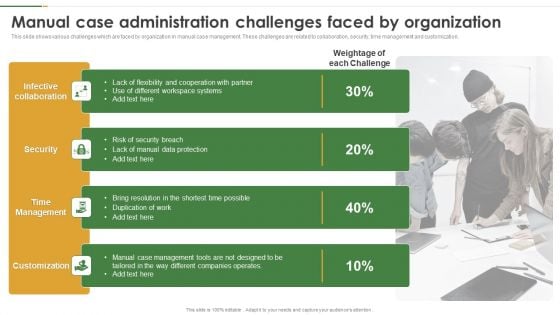
Manual Case Administration Challenges Faced By Organization Sample PDF
This slide shows various challenges which are faced by organization in manual case management. These challenges are related to collaboration, security, time management and customization. Presenting Manual Case Administration Challenges Faced By Organization Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Time Management, Customization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
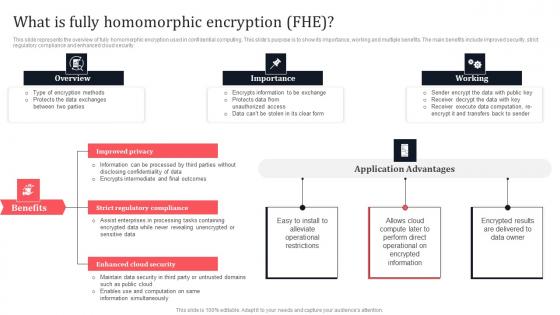
What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Make sure to capture your audiences attention in your business displays with our gratis customizable What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.

COVID 19 Effect Management Strategies Risk Response Plan Sports Sector Firms During COVID 19 Action Information PDF
Presenting this set of slides with name covid 19 effect management strategies risk response plan sports sector firms during covid 19 action information pdf. The topics discussed in these slides are developing, protection, global, plan, financial. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
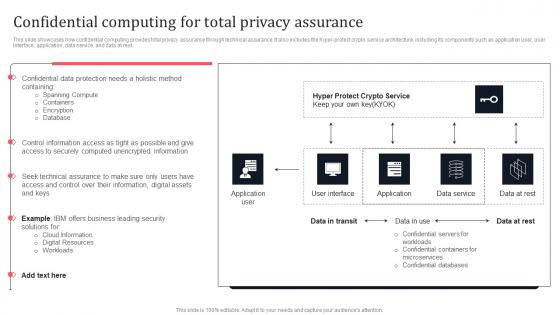
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
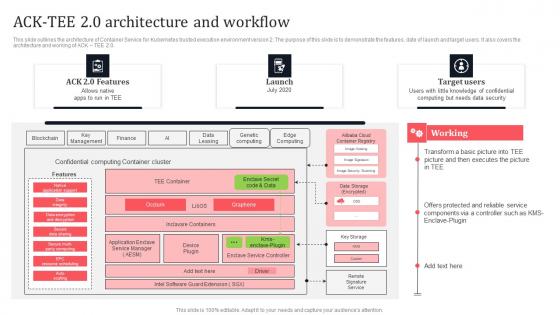
Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
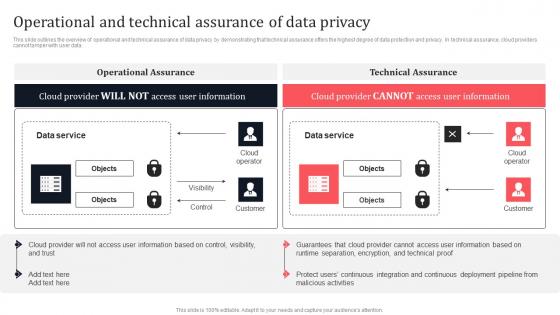
Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. There are so many reasons you need a Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.
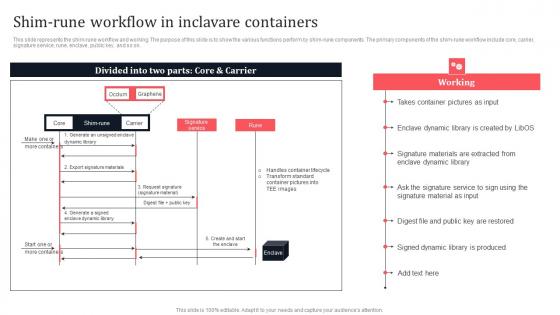
Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.
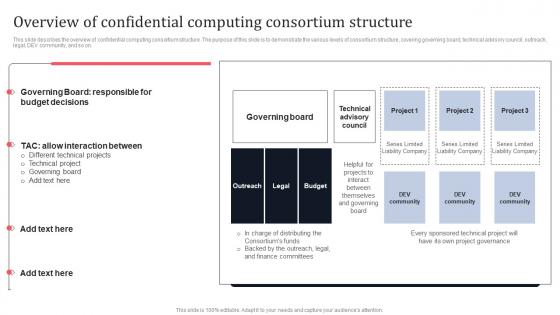
Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
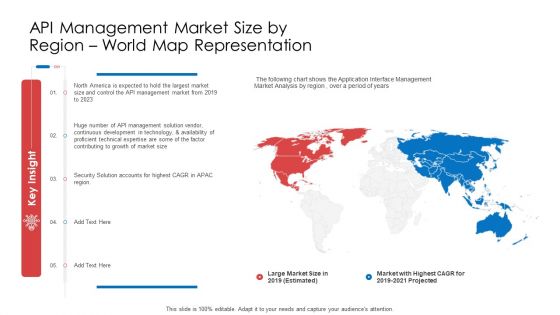
API Administration Solution API Management Market Size By Region World Map Representation Ppt Outline Graphics Download PDF
Presenting api administration solution api management market size by region world map representation ppt outline graphics download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, growth, technical, development, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
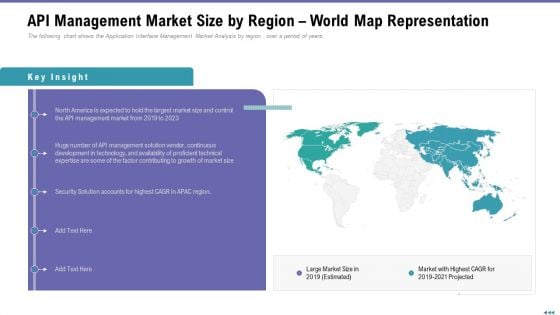
Market Viewpoint Application Programming Interface Governance API Management Market Size By Region World Map Representation Ideas PDF
Presenting market viewpoint application programming interface governance api management market size by region world map representation ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, growth, technical, development, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
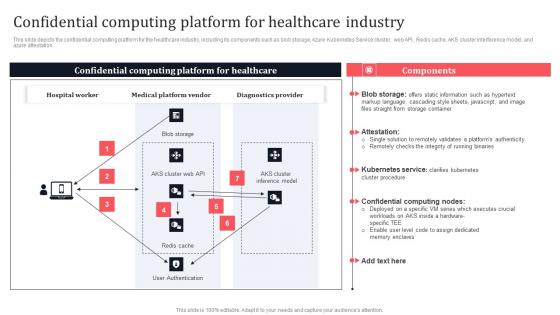
Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. This modern and well-arranged Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation.
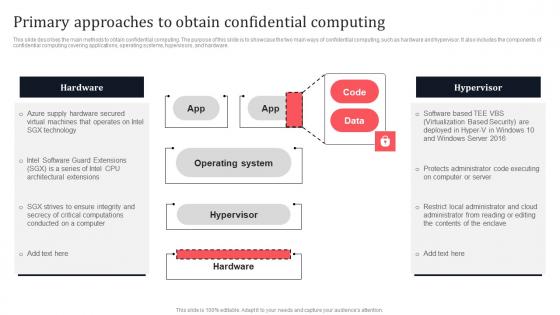
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
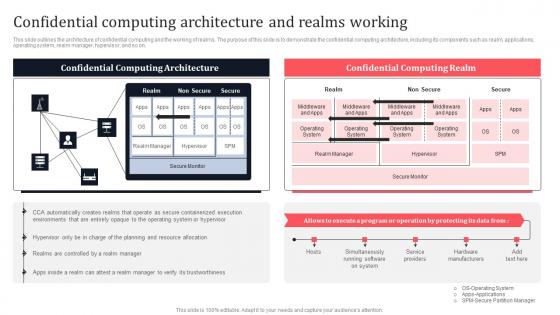
Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Slidegeeks is here to make your presentations a breeze with Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
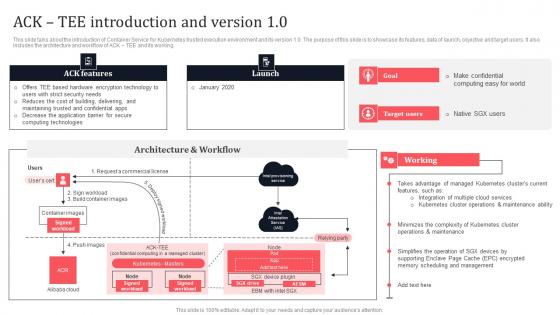
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
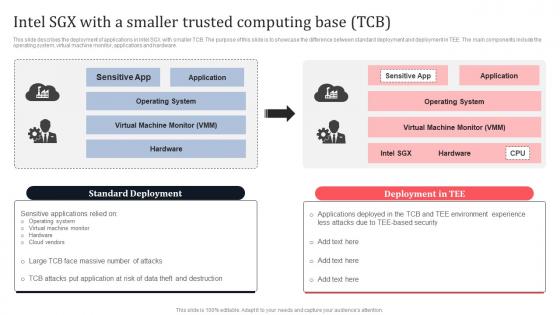
Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Take your projects to the next level with our ultimate collection of Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. This Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
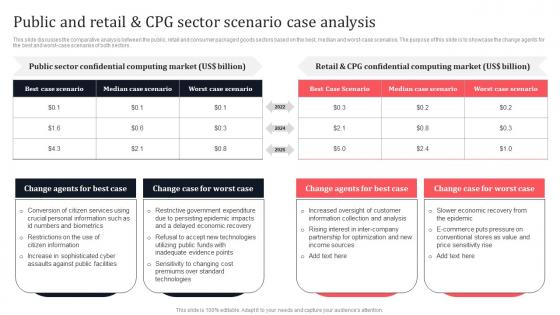
Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Slidegeeks is here to make your presentations a breeze with Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
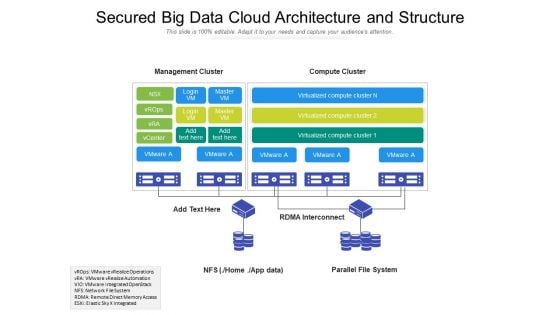
Secured Big Data Cloud Architecture And Structure Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name secured big data cloud architecture and structure ppt powerpoint presentation gallery example pdf. The topics discussed in these slide is secured big data cloud architecture and structure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Fixed Income Securities Icons Slide Gears Dollar Ppt PowerPoint Presentation Ideas Guidelines
Presenting this set of slides with name fixed income securities icons slide gears dollar ppt powerpoint presentation ideas guidelines. The topics discussed in these slides are marketing, process, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
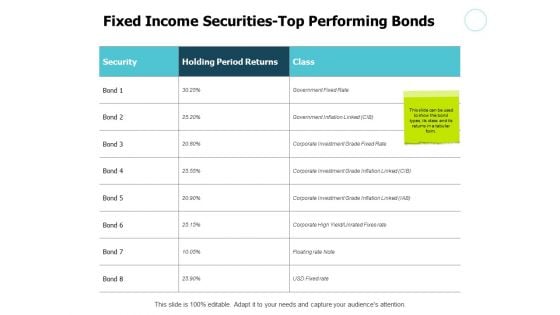
Fixed Income Securities Top Performing Bonds Ppt PowerPoint Presentation Layouts Portrait
Presenting this set of slides with name fixed income securities top performing bonds ppt powerpoint presentation layouts portrait. The topics discussed in these slides are marketing, process, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
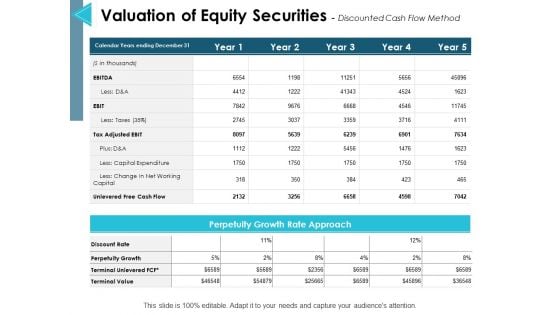
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Infographic Template Introduction
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation infographic template introduction. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.

Financial Instruments Bonds And Fixed Income Securities Ppt PowerPoint Presentation Show Graphics Pictures
Presenting this set of slides with name financial instruments bonds and fixed income securities ppt powerpoint presentation show graphics pictures. The topics discussed in these slides are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Execute Operational Procedure Plan Steps In Detail Process Redesigning Professional PDF
This slide provides information about the Third and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail process redesigning professional pdf bundle. Topics like potential consequence, several practices, process redesigning practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
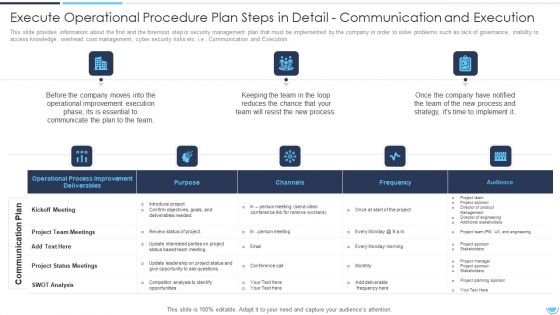
Execute Operational Procedure Plan Steps In Detail Communication And Execution Clipart PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail communication and execution clipart pdf bundle. Topics like operational process improvement deliverables, project team meetings, project status meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Execute Operational Procedure Plan Steps In Detail Process Mapping Background PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping.Deliver and pitch your topic in the best possible manner with this execute operational procedure plan steps in detail process mapping background pdf. Use them to share invaluable insights on workflow applications, process mapping, process improvement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Communication And Execution Guidelines PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improvement, communicate, team, process, implement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
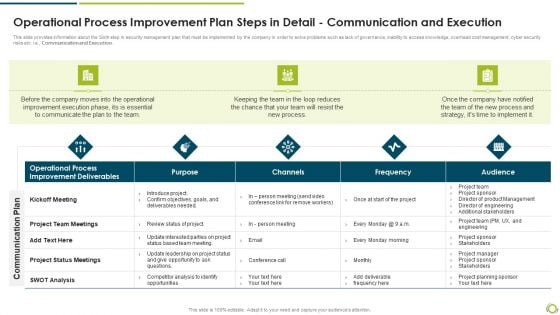
Operational Process Improvement Plan Steps In Detail Communication And Execution Rules PDF
This slide provides information about the Sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail communication and execution rules pdf bundle. Topics like improvement deliverables, operational process, project team meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Process Redesigning Graphics PDF
This slide provides information about the Third step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning graphics pdf. Use them to share invaluable insights on potential consequence, process redesigning practices, practice implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
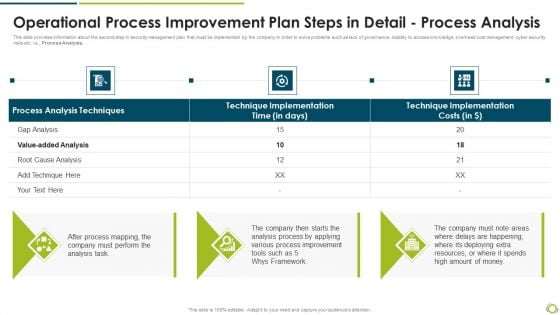
Operational Process Improvement Plan Steps In Detail Process Analysis Formats PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. Presenting operational process improvement plan steps in detail process analysis formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technique implementation, process analysis techniques, process improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































