Security Services
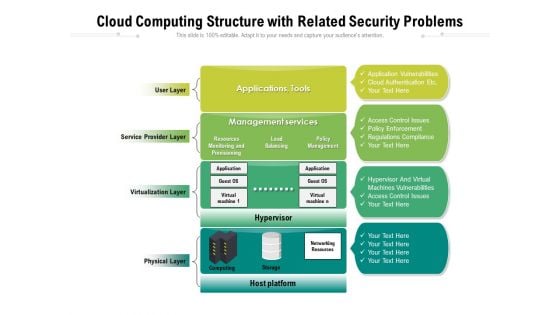
Cloud Computing Structure With Related Security Problems Ppt PowerPoint Presentation Gallery Infographics PDF
Presenting this set of slides with name cloud computing structure with related security problems ppt powerpoint presentation gallery infographics pdf. This is a four stage process. The stages in this process are management, services, virtualization. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
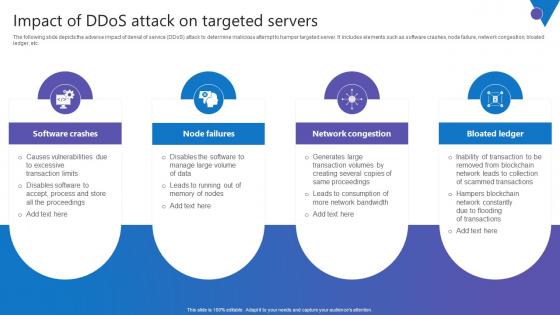
Impact Of DDoS Attack Comprehensive Guide To Blockchain Digital Security Sample Pdf
The following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Slidegeeks is here to make your presentations a breeze with Impact Of DDoS Attack Comprehensive Guide To Blockchain Digital Security Sample Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.
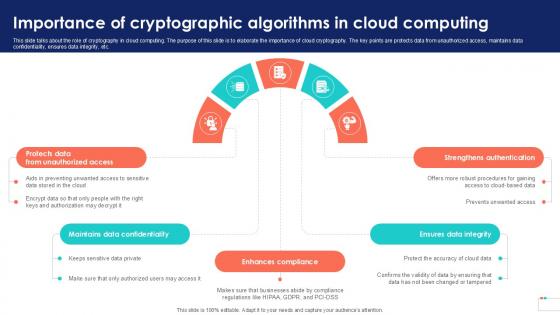
Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Presenting this PowerPoint presentation, titled Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.

Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty eight slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking. Our Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fiveteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now. Our Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V
This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing.
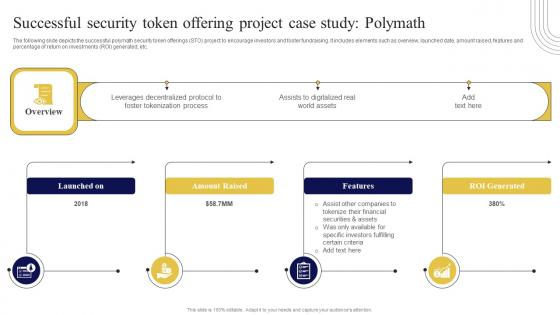
Successful Security Token Offering Project Case Exploring Investment Opportunities Summary Pdf
The following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. This Successful Security Token Offering Project Case Exploring Investment Opportunities Summary Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc.

Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Presenting this PowerPoint presentation, titled Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc.

Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V
The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding. This modern and well-arranged Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding.
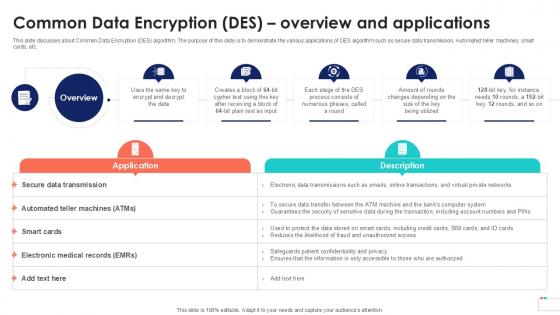
Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc.
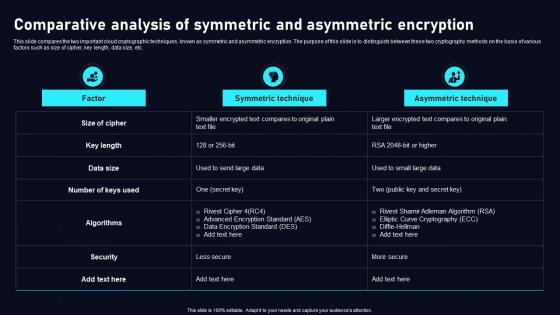
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.

Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising sixteen slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
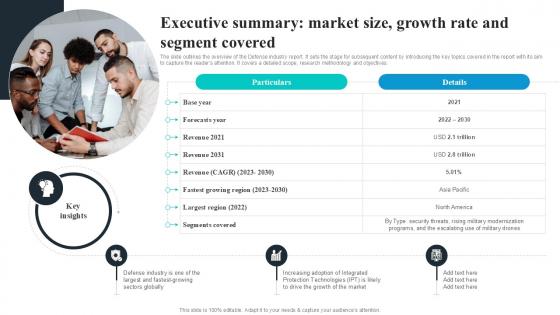
Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V
The slide outlines the overview of the Defense industry report. It sets the stage for subsequent content by introducing the key topics covered in the report with its aim to capture the readers attention. It covers a detailed scope, research methodology and objectives. Find highly impressive Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The slide outlines the overview of the Defense industry report. It sets the stage for subsequent content by introducing the key topics covered in the report with its aim to capture the readers attention. It covers a detailed scope, research methodology and objectives.
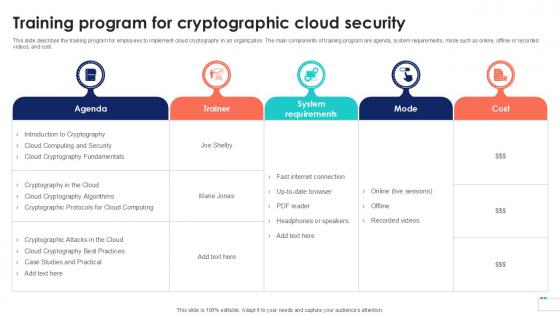
Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V
This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V. This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.
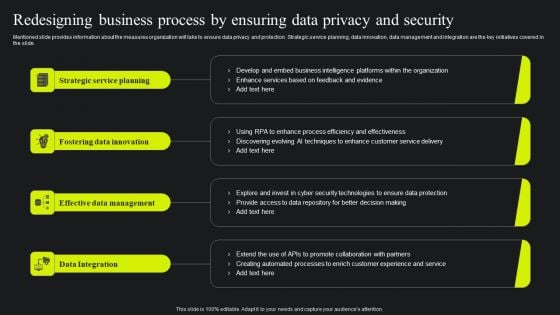
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Slidegeeks is here to make your presentations a breeze with Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
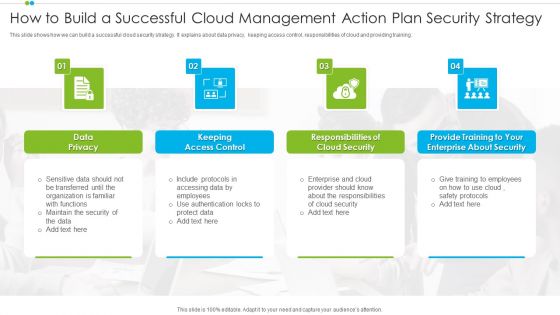
How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF
This slide shows how we can build a successful cloud security strategy. It explains about data privacy, keeping access control, responsibilities of cloud and providing training.Presenting How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Enterprise, Data Privacy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
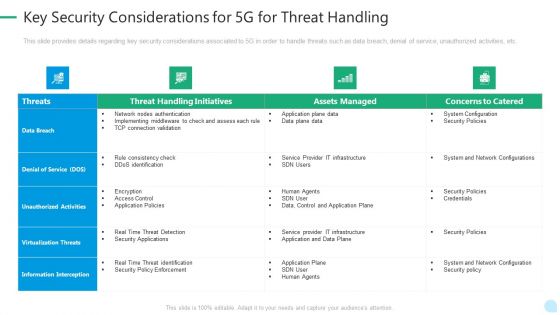
5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Computer Keyboard With Security Keys PowerPoint Templates And PowerPoint Themes 0912
Computer Keyboard With Security Keys PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with Computer keyboard with security key Encourage your community to take action. Get them to back the cause you champion.
Security Systems Smart Grid Training Ppt PowerPoint Presentation Visual Aids Example File
This is a security systems smart grid training ppt powerpoint presentation visual aids example file. This is a ten stage process. The stages in this process are security systems, smart grid training.
Marketing Communications Collaboration Business Security System Process Management Ppt PowerPoint Presentation Graphics
This is a marketing communications collaboration business security system process management ppt powerpoint presentation graphics. This is a five stage process. The stages in this process are marketing communications collaboration, business security system, process management.
lead generation industry security outsourcing firms professional development ppt powerpoint presentation styles guide
This is a lead generation industry security outsourcing firms professional development ppt powerpoint presentation styles guide. This is a four stage process. The stages in this process are lead generation industry, security outsourcing firms, professional development.
Project Portfolio Management Digital Security Management Financial Planning Ppt PowerPoint Presentation Inspiration Icons
This is a project portfolio management digital security management financial planning ppt powerpoint presentation inspiration icons. This is a five stage process. The stages in this process are project portfolio management, digital security management, financial planning.
Business Business Relationship Marketing Monitor Employee Security Outsourcing Ppt PowerPoint Presentation Portfolio Graphics Template
This is a business business relationship marketing monitor employee security outsourcing ppt powerpoint presentation portfolio graphics template. This is a four stage process. The stages in this process are business business relationship marketing, monitor employee, security outsourcing.
Mobile Device Security Best Practices Ppt PowerPoint Presentation Outline Rules Cpb
This is a mobile device security best practices ppt powerpoint presentation outline rules cpb. This is a four stage process. The stages in this process are mobile device security best practices.
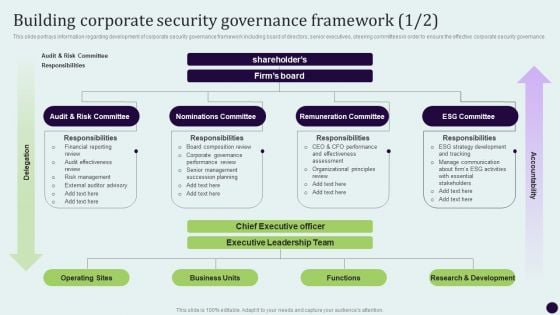
Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF
This slide portrays information regarding development of corporate security governance framework including board of directors, senior executives, steering committees in order to ensure the effective corporate security governance. Create an editable Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
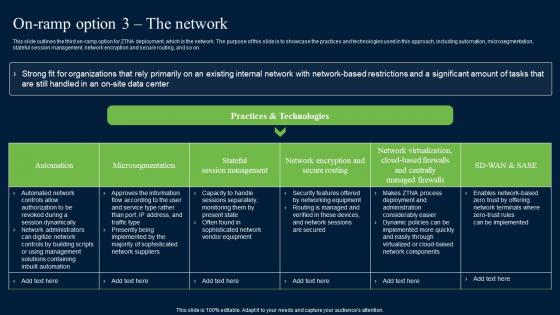
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
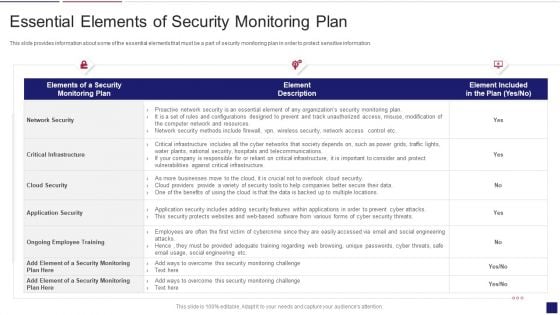
Continuous Development Evaluation Plan Eliminate Cyber Attacks Essential Elements Of Security Monitoring Elements PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
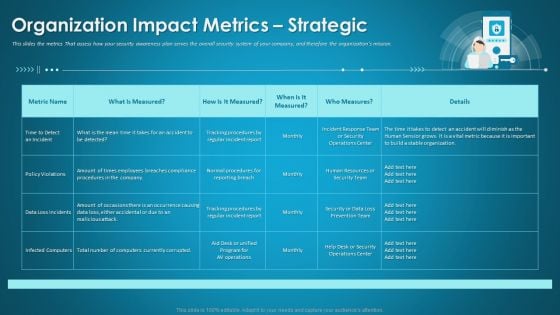
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
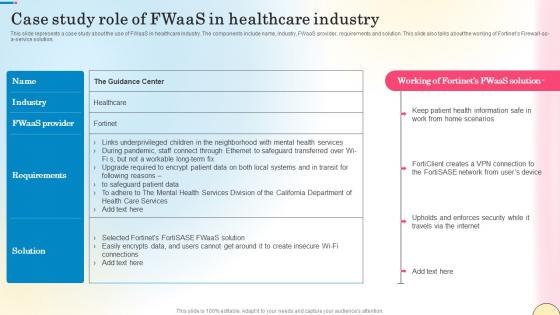
Case Study Role Of Fwaas In Healthcare Industry Network Security Slides Pdf
This slide represents a case study about the use of FWaaS in healthcare industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the working of Fortinets Firewall-as-a-service solution. Slidegeeks is here to make your presentations a breeze with Case Study Role Of Fwaas In Healthcare Industry Network Security Slides Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents a case study about the use of FWaaS in healthcare industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the working of Fortinets Firewall-as-a-service solution.

Information Security Process To Manage Firms Sensitive Data Ppt Infographics Background Image PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative information security process to manage firms sensitive data ppt infographics background image pdf bundle. Topics like management, system, security, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
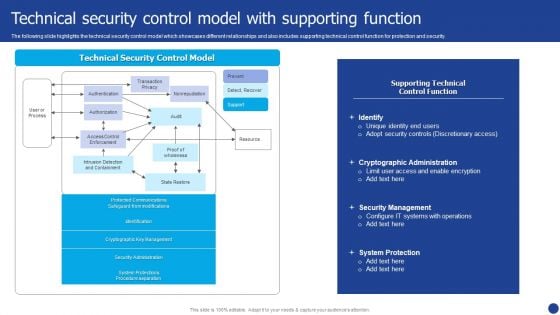
Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Protection Cyber Security Cyber Threat Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name it protection cyber security cyber threat ppt powerpoint presentation complete deck. The topics discussed in these slides are network protection, cyber security, cyber threat, laptop protected, security breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an awe inspiring pitch with this creative Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF bundle. Topics like Security And Compliance, Factor Authentication, Security Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
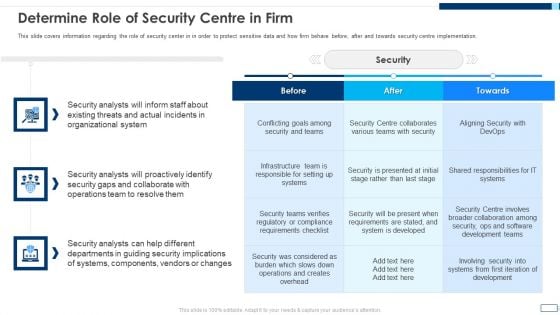
Evolving BI Infrastructure Determine Role Of Security Centre In Firm Summary PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative evolving bi infrastructure determine role of security centre in firm summary pdf bundle. Topics like organizational, security analysts, collaborate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
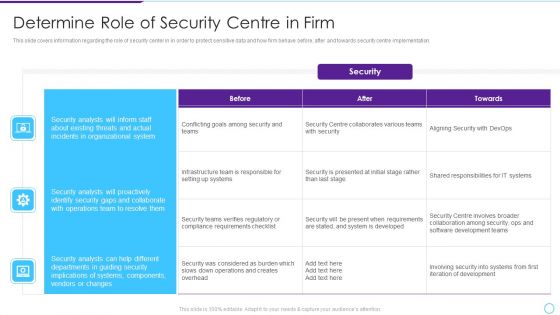
Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF bundle. Topics like Security, Organizational System, Operations Team, Conflicting Goals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
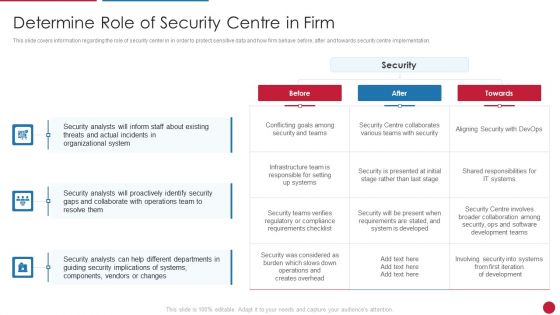
Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF bundle. Topics like Organizational System, Security Analysts, Collaborate With Operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
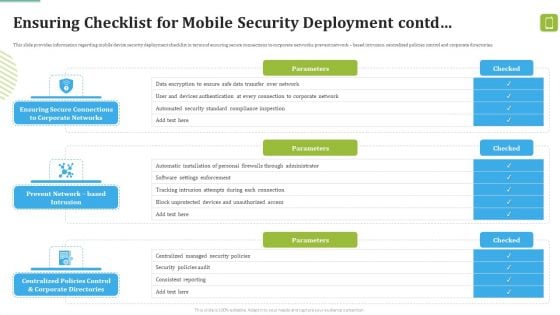
MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF. Use them to share invaluable insights on Against Malicious, Device Security, Automatic Configuration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
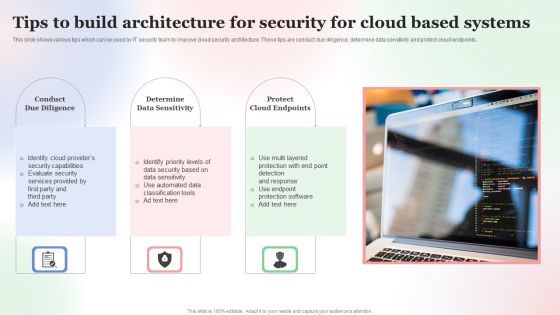
Tips To Build Architecture For Security For Cloud Based Systems Designs PDF
This slide shows various tips which can be used by IT security team to improve cloud security architecture. These tips are conduct due diligence, determine data sensitivity and protect cloud endpoints. Persuade your audience using this Tips To Build Architecture For Security For Cloud Based Systems Designs PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Tips To Build, Architecture For Security, Cloud Based Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
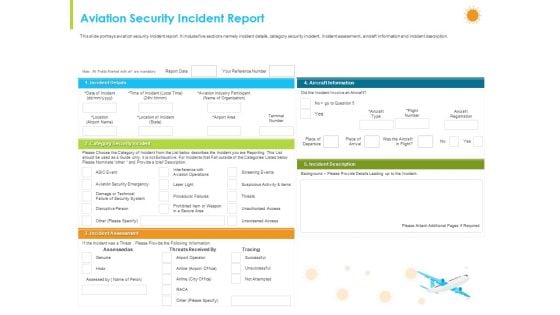
How Aviation Industry Coping With COVID 19 Pandemic Aviation Security Incident Report Template PDF
This slide portrays aviation security incident report. It include five sections namely incident details, category security incident, incident assessment, aircraft information and incident description.Deliver an awe inspiring pitch with this creative how aviation industry coping with COVID 19 pandemic aviation security incident report template pdf. bundle. Topics like suspicious activity and items, aircraft information, category security incident, incident assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
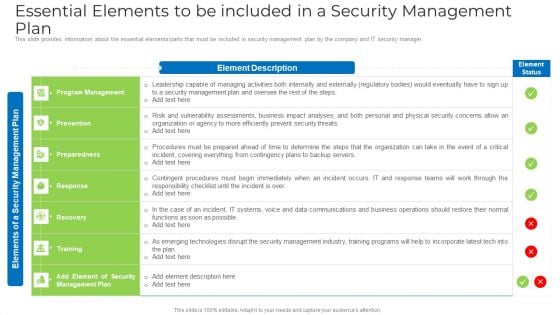
Essential Elements To Be Included In A Security Management Plan Elements PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan elements pdf bundle. Topics like risk, organization, security, systems, data communications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

International Organization Standardization 270001 Performance Indicators To Measure Information Security Controls Clipart PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this international organization standardization 270001 performance indicators to measure information security controls clipart pdf. Use them to share invaluable insights on information security policy, information security training, incident response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF bundle. Topics like Traditional It Security, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
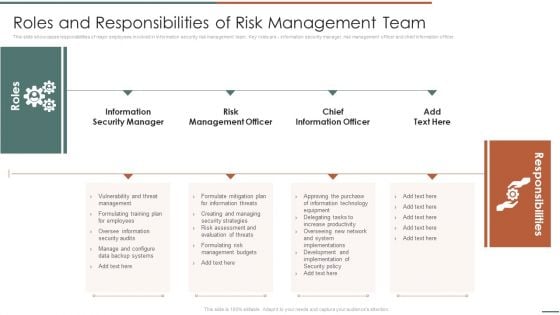
Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF bundle. Topics like Information Security Manager, Risk Management, Chief Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

About Us For Our Firewall Solutions Company Cloud Security Firewall Proposal
This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry-leading organizations, and history.Elevate your presentations with our intuitive About Us For Our Firewall Solutions Company Cloud Security Firewall Proposal template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression. This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry-leading organizations, and history.
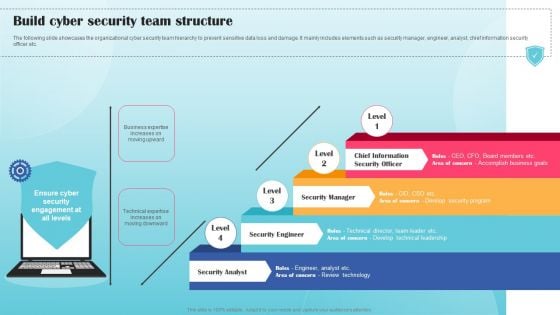
Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF
The following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Organizational Network Security Awareness Staff Learning Table Of Contents Introduction PDF
Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning table of contents introduction pdf. Use them to share invaluable insights on security awareness training, organization impact metrics, security awareness, communication plan, budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Do you know about Slidesgeeks Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls.

Email Security Market Research Report Industry Trends Ppt Infographics Styles PDF
Presenting this set of slides with name email security market research report industry trends ppt infographics styles pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Industry Trends Ppt Professional Example PDF
Presenting this set of slides with name global cloud based email security market industry trends ppt professional example pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
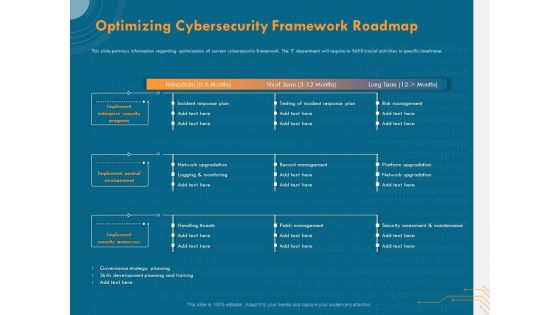
Cyber Security Implementation Framework Optimizing Cybersecurity Framework Roadmap Ppt Outline Background PDF
Presenting this set of slides with name cyber security implementation framework optimizing cybersecurity framework roadmap ppt outline background pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes, incident response plan, testing incident response plan, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
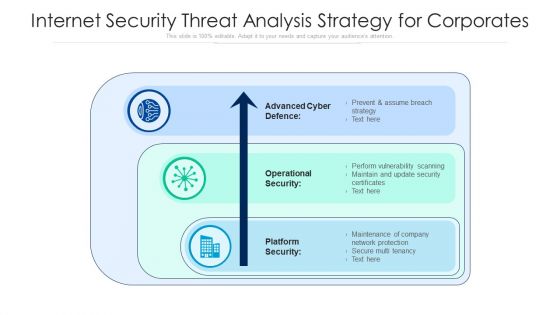
Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Guidelines To Create An Advanced Security Management Plan Table Of Contents Pictures PDF
Deliver an awe inspiring pitch with this creative guidelines to create an advanced security management plan table of contents pictures pdf bundle. Topics like essential elements, security management challenges, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
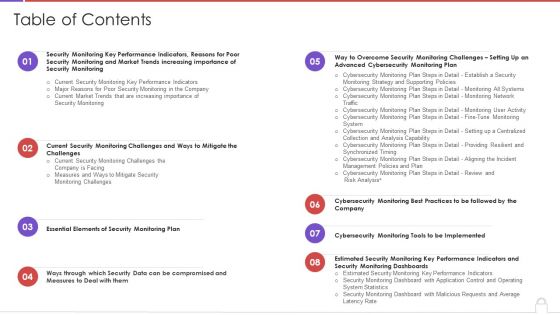
Table Of Contents Methods To Develop Advanced It Security Monitoring Plan Structure PDF
Deliver and pitch your topic in the best possible manner with this table of contents methods to develop advanced it security monitoring plan structure pdf. Use them to share invaluable insights on security monitoring, key performance indicators, security monitoring plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
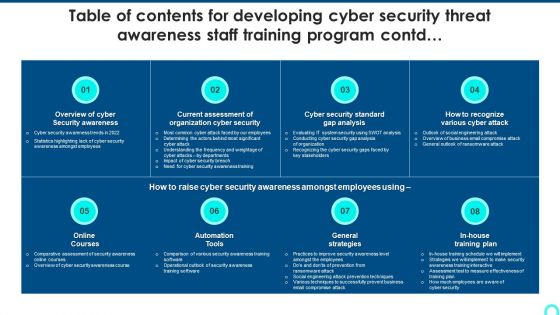
Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF bundle. Topics like Security Awareness, Current Assessment, Security Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































