Security Services
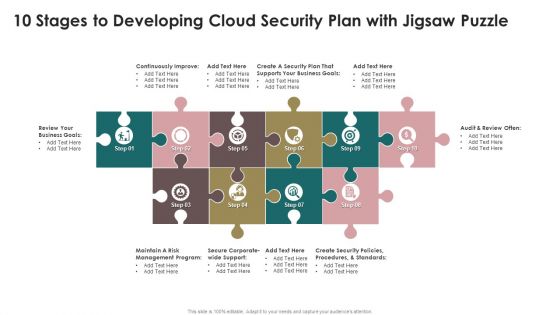
10 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Themes PDF
Presenting 10 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Themes PDF to dispense important information. This template comprises ten stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
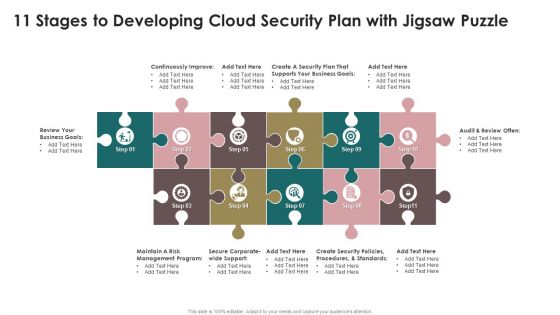
11 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Topics PDF
Presenting 11 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Topics PDF to dispense important information. This template comprises eleven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
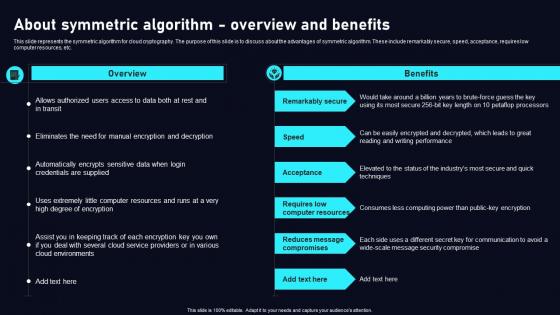
About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
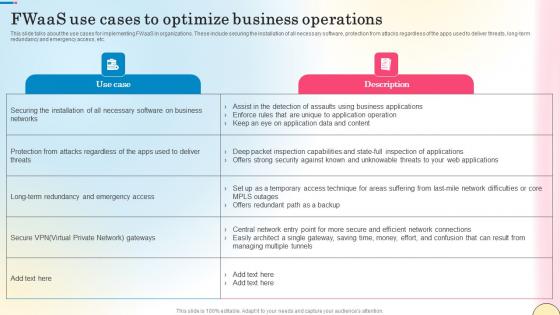
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc.

Training Program For Zero Trust Network Access Model Security Inspiration Pdf
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Find a pre-designed and impeccable Training Program For Zero Trust Network Access Model Security Inspiration Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Create an editable Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.

About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Want to ace your presentation in front of a live audience Our About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.

Competitive Dynamics And Developments Global Security Industry PPT Template IR SS V
The slide represents a detailed overview of competitive landscape. The purpose of this slide is to help stakeholders in understanding the competitive environment and aids in making informed strategic decision. The key players list include major Defense companies. There are so many reasons you need a Competitive Dynamics And Developments Global Security Industry PPT Template IR SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide represents a detailed overview of competitive landscape. The purpose of this slide is to help stakeholders in understanding the competitive environment and aids in making informed strategic decision. The key players list include major Defense companies.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.
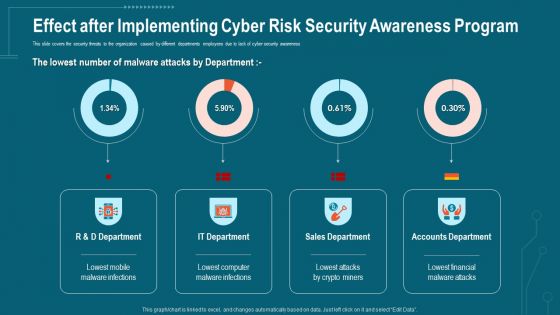
Companys Data Safety Recognition Effect After Implementing Cyber Risk Security Awareness Program Formats PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition effect after implementing cyber risk security awareness program formats pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
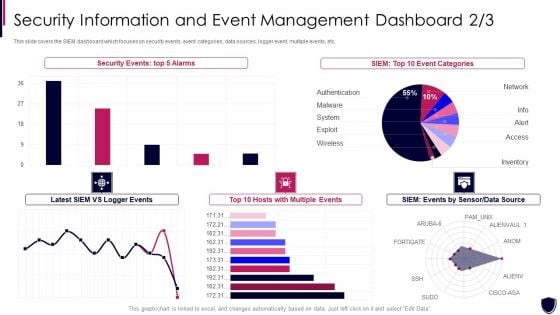
Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Formats PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration security information and event formats pdf bundle. Topics like security events, event categories, data source, multiple events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Safety Initiatives Checklist For Effectively Managing Asset Security Themes PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this data safety initiatives checklist for effectively managing asset security themes pdf. Use them to share invaluable insights on system monitoring, data backup, security patches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
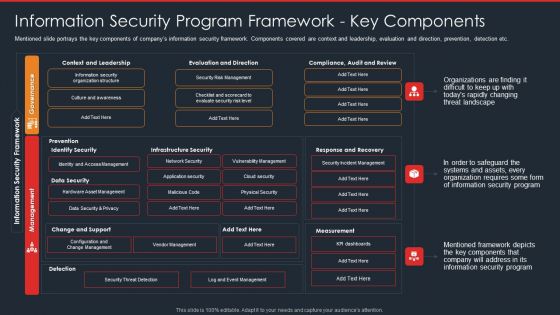
Data Safety Initiatives Information Security Program Framework Key Components Diagrams PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this data safety initiatives information security program framework key components diagrams pdf. Use them to share invaluable insights on governance, management, context and leadership, evaluation and direction, infrastructure security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
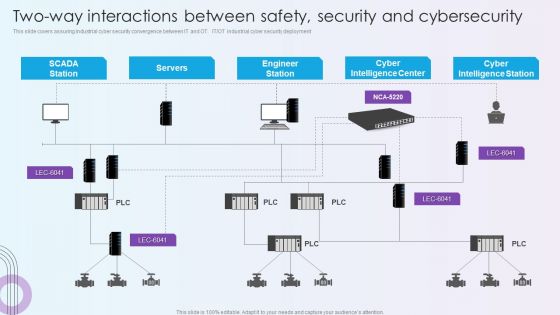
Digitalization Of Operative Enterprises Two Way Interactions Between Safety Security And Cybersecurity Themes PDF
This slide covers assuring industrial cyber security convergence between IT and OT. IT or OT industrial cyber security deployment. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises Two Way Interactions Between Safety Security And Cybersecurity Themes PDF. Use them to share invaluable insights on Cyber Intelligence Center, Cyber Intelligence Station, Engineer Station and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
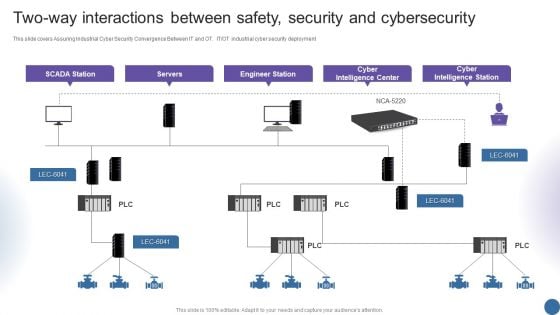
Two Way Interactions Between Safety Security And Cybersecurity Managing Organizational Transformation Summary PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT OT industrial cyber security deployment. Deliver an awe inspiring pitch with this creative Two Way Interactions Between Safety Security And Cybersecurity Managing Organizational Transformation Summary PDF bundle. Topics like Servers, Engineer Station, Intelligence Center can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
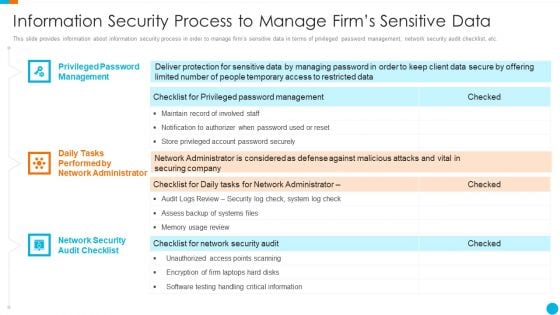
Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Practices For Website Security Management Step By Step Guide Ideas PDF
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices For Website Security Management Step By Step Guide Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.

Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Designs PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it information security process to manage firms sensitive data designs pdf. Use them to share invaluable insights on privileged password management, daily tasks performed by network administrator, network security audit checklist and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
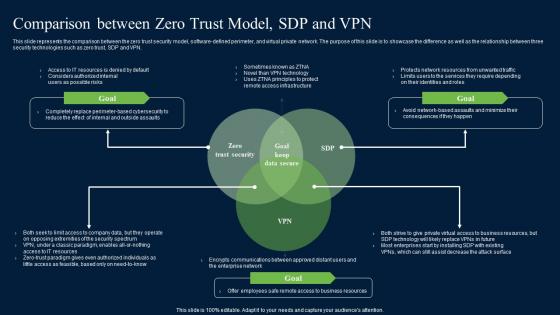
Comparison Between Zero Trust Model SDP Zero Trust Network Security Guidelines Pdf
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparison Between Zero Trust Model SDP Zero Trust Network Security Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V
The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices.
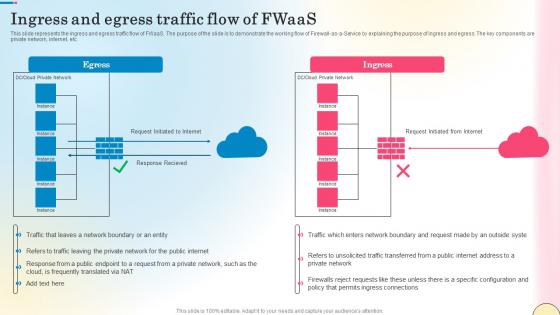
Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf
This slide represents the ingress and egress traffic flow of FWaaS. The purpose of the slide is to demonstrate the working flow of Firewall-as-a-Service by explaining the purpose of ingress and egress. The key components are private network, internet, etc. Are you searching for a Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf from Slidegeeks today. This slide represents the ingress and egress traffic flow of FWaaS. The purpose of the slide is to demonstrate the working flow of Firewall-as-a-Service by explaining the purpose of ingress and egress. The key components are private network, internet, etc.
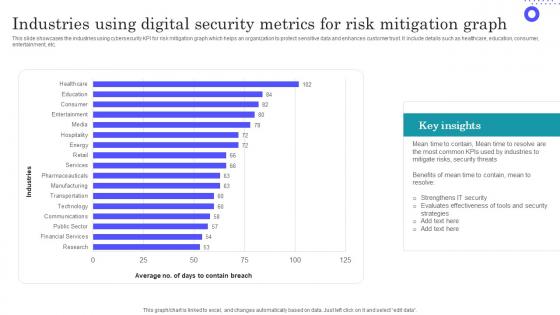
Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf
Showcasing this set of slides titled Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf The topics addressed in these templates are Evaluates Effectiveness, Most Common, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the industries using cybersecurity KPI for risk mitigation graph which helps an organization to protect sensitive data and enhances customer trust. It include details such as healthcare, education, consumer, entertainment, etc.
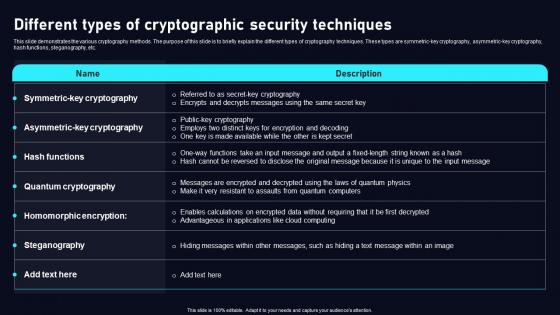
Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf
This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc. Slidegeeks has constructed Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc.
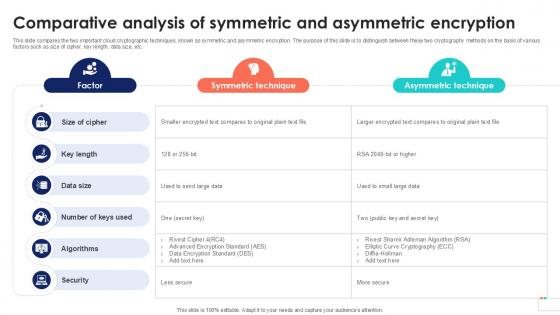
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
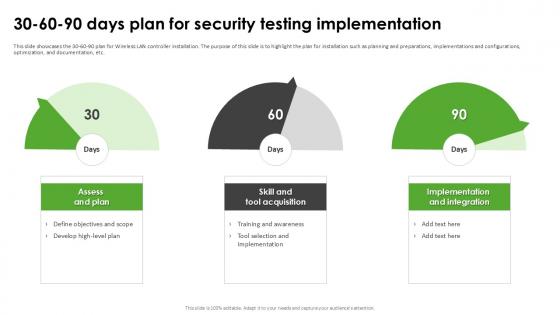
30 60 90 Days Plan For Security Harnessing The World Of Ethical Ppt Sample
This slide showcases the 30-60-90 plan for Wireless LAN controller installation. The purpose of this slide is to highlight the plan for installation such as planning and preparations, implementations and configurations, optimization, and documentation, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate 30 60 90 Days Plan For Security Harnessing The World Of Ethical Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases the 30-60-90 plan for Wireless LAN controller installation. The purpose of this slide is to highlight the plan for installation such as planning and preparations, implementations and configurations, optimization, and documentation, etc.
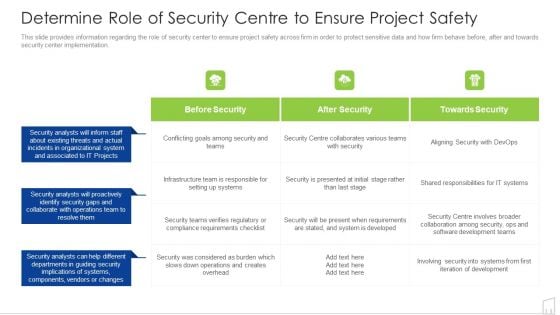
Determine Role Of Security Centre To Ensure Project Safety Ppt Professional Example PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative determine role of security centre to ensure project safety ppt professional example pdf bundle. Topics like security, system, developed, requirements, teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
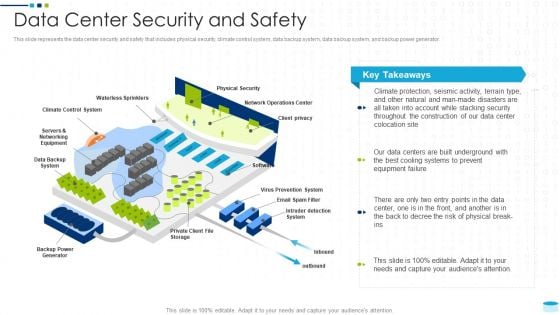
Data Center Infrastructure Management IT Data Center Security And Safety Demonstration PDF
This slide represents the data center security and safety that includes physical security, climate control system, data backup system, data backup system, and backup power generator. Deliver an awe inspiring pitch with this creative data center infrastructure management it data center security and safety demonstration pdf bundle. Topics like client privacy, physical security, waterless sprinklers, data backup system, virus prevention system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
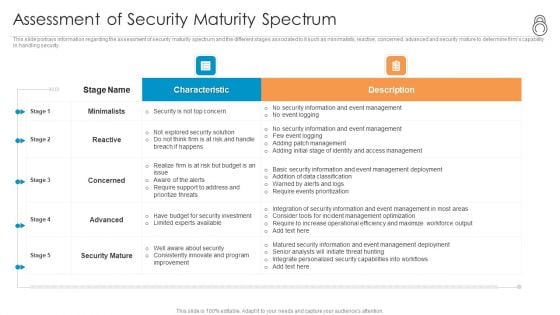
Enhanced Protection Corporate Event Administration Assessment Of Security Maturity Spectrum Background PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration assessment of security maturity spectrum background pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Companys Data Safety Recognition Security Awareness Tracking Kpis Culture Mockup PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a companys data safety recognition security awareness tracking kpis culture mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, incident reduction, security culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives Key Security Controls To Be Addressed In The Program Summary PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative data safety initiatives key security controls to be addressed in the program summary pdf bundle. Topics like prevents attacks, limits extent of attacks, data recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Impact Of Security Awareness Training Sample PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative data breach prevention recognition impact of security awareness training sample pdf bundle. Topics like security awareness program, security threats, network intrusion, inadvertent disclosure, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
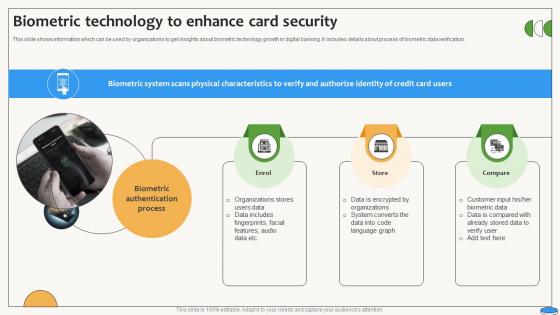
Biometric Technology To Enhance Card Security Swipe Smartly A Practical Guide Fin SS V
This slide shows information which can be used by organizations to get insights about biometric technology growth in digital banking. It includes details about process of biometric data verification. There are so many reasons you need a Biometric Technology To Enhance Card Security Swipe Smartly A Practical Guide Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide shows information which can be used by organizations to get insights about biometric technology growth in digital banking. It includes details about process of biometric data verification.

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Graphics PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail evaluating information processing assets graphics pdf. Use them to share invaluable insights on security management plan steps in detail evaluating information processing assets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Summary PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis summary pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Security Controls To Be Addressed In The Program Ppt Professional Vector PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. This is a key security controls to be addressed in the program ppt professional vector pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like key security controls to be addressed in the program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
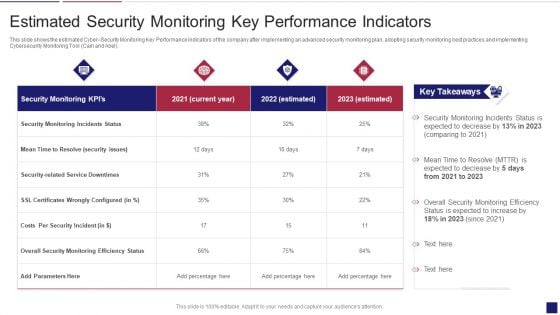
Continuous Development Evaluation Plan Eliminate Cyber Attacks Estimated Security Monitoring Designs PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks estimated security monitoring designs pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
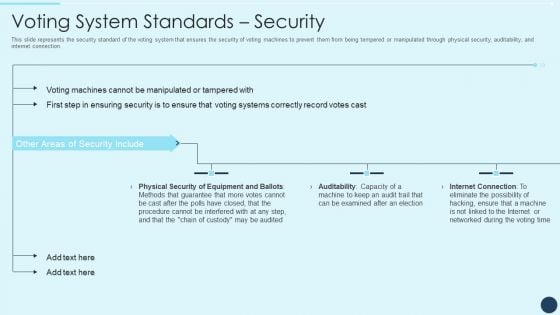
Electoral Mechanism IT Voting System Standards Security Ppt Professional Sample PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection. Deliver an awe inspiring pitch with this creative electoral mechanism it voting system standards security ppt professional sample pdf bundle. Topics like physical security of equipment and ballots, auditability, internet connection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Strategy Role Of Chief Information Security Officer Rules PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. This is a information technology strategy role of chief information security officer rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information, stay informed, monthly reports. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends Best, Smart Home Security, Systems Consumer Technology, Association Consumer Technology, Association Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Dependable Business, Security Information, Team Members. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF
This slide represents 3 year cyber security plan road map of a company for website enhancement and implementing security to operational work with specific standards. It consists security standards, training and awareness phishing users and sensitive data management. Showcasing this set of slides titled Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF. The topics addressed in these templates are Website Enhancement, Governance Subcommittee, Security Standards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF
The following slide highlights multiple solutions to prevent security risks and issues. It also includes elements such as risk evaluation, security awareness, checklist, policies and regulation, recovery plan etc. Presenting Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Risk Evaluation, Security Awareness, Security Checklist, Policies And Regulation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF
The following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Run Security Test, Planned Backup, New Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
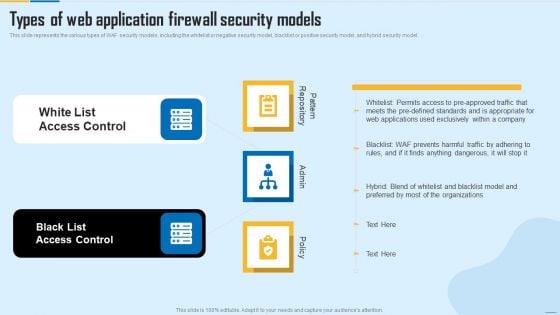
Types Of Web Application Firewall Security Models WAF Platform Themes PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting Types Of Web Application Firewall Security Models WAF Platform Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like White List Access Control, Black List Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Awareness Topics To Considered For Effective Training Program Brochure PDF
This slide covers cybersecurity awareness topics to considered for effective training. It involves topics such as removable media, cloud security, public wi-fi and physical security. Presenting IT Security Awareness Topics To Considered For Effective Training Program Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Removable Media, Cloud Security, Physical Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Home System Security Threats Utilizing Smart Appliances IoT SS V
This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Take your projects to the next level with our ultimate collection of Smart Home System Security Threats Utilizing Smart Appliances IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft.
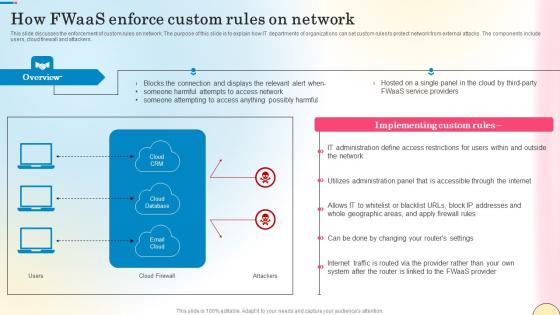
How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers.
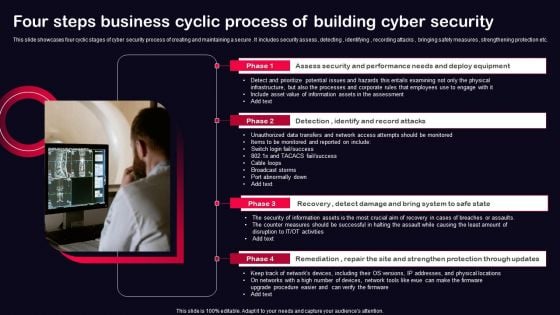
Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
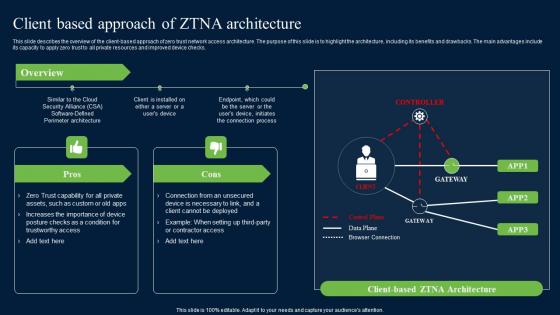
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
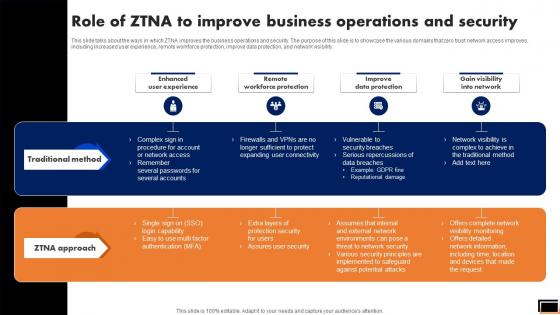
Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
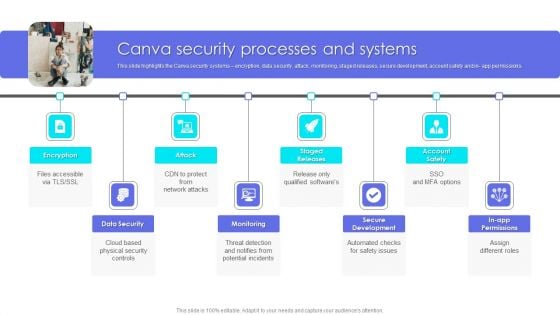
Canva Pro Business Profile Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in app permissions. Presenting Business Profile Canva Security Processes And Systems Elements PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Data Security, Monitoring, Secure Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V
This slide provides an overview of the cloud computing platform used to streamline industrial working. The slide further includes consideration factors and benefits that are scalability, flexibility, connectivity and data storage. This Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides an overview of the cloud computing platform used to streamline industrial working. The slide further includes consideration factors and benefits that are scalability, flexibility, connectivity and data storage.
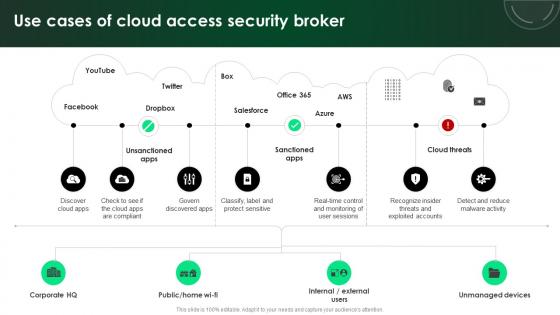
CASB 2 0 IT Use Cases Of Cloud Access Security Broker
This modern and well-arranged CASB 2 0 IT Use Cases Of Cloud Access Security Broker provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Our CASB 2 0 IT Use Cases Of Cloud Access Security Broker are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
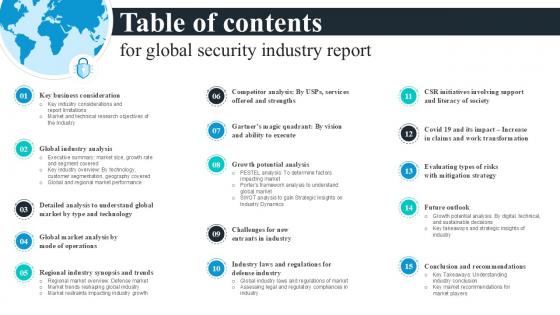
Table Of Contents For Global Security Industry Report PPT Template IR SS V
Slidegeeks has constructed Table Of Contents For Global Security Industry Report PPT Template IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Our Table Of Contents For Global Security Industry Report PPT Template IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
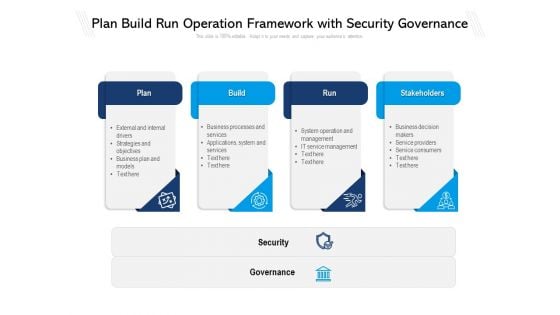
Plan Build Run Operation Framework With Security Governance Ppt PowerPoint Presentation Infographics Master Slide PDF
Presenting plan build run operation framework with security governance ppt powerpoint presentation infographics master slide pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Plan, Build, Run, Stakeholders, Security, Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































