Security Services

Gantt Chart For Cloud Security Firewall Proposal
Power up your presentations with our Gantt Chart For Cloud Security Firewall Proposal single-slide PPT template. Our visually-stunning template will help you deliver your message with confidence. With easy-to-use editing options and fully customizable features, you can create polished and captivating presentations in no time. Say goodbye to boring slides and hello to impactful presentations with our top-quality template. Download now and get ready to wow your audience. singles Our Gantt Chart For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Strategic Agenda Checklist Mockup Pdf
This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status. Showcasing this set of slides titled Cyber Security Strategic Agenda Checklist Mockup Pdf. The topics addressed in these templates are Cyber Security, Strategic Agenda Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status.

Cover Letter For Cloud Security Firewall Proposal
Take your presentations to the next level with our Cover Letter For Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights. Cover Letter, Cloud Security Firewall Proposal
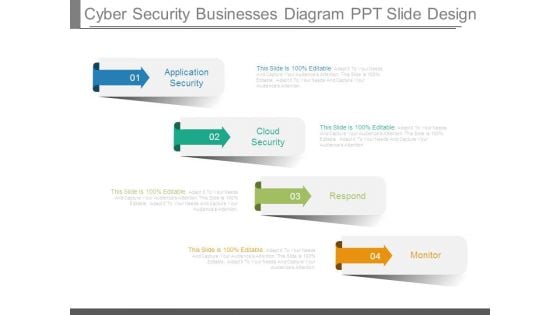
Cyber Security Businesses Diagram Ppt Slide Design
This is a cyber security businesses diagram ppt slide design. This is a four stage process. The stages in this process are application security, cloud security, respond, monitor.

Sustainable Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Create an editable Sustainable Improving Security By Green Computing Technology that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Sustainable Improving Security By Green Computing Technology is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
Big Data Monitoring Security Icon Download pdf
Pitch your topic with ease and precision using this Big Data Monitoring Security Icon Download pdf. This layout presents information on Big Data Monitoring, Security Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Big Data Monitoring Security Icon Download pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
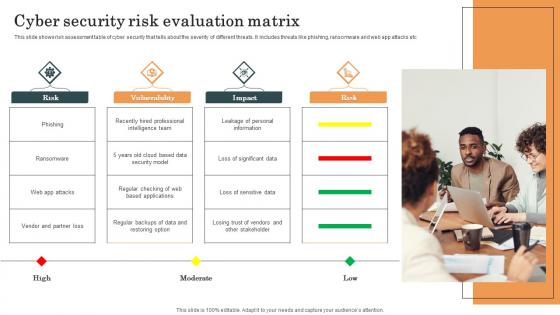
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.
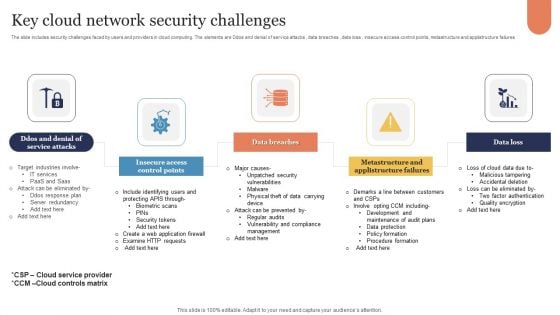
Key Cloud Network Security Challenges Sample PDF
The slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures Persuade your audience using this Key Cloud Network Security Challenges Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Insecure Access Control Points, Data Breaches, Data Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Construction Worker Security Checklist Icon Portrait Pdf
Pitch your topic with ease and precision using this Construction Worker Security Checklist Icon Portrait Pdf. This layout presents information on Construction Worker, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Construction Worker Security Checklist Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Food Quality Security Checklist Icon Guidelines Pdf
Pitch your topic with ease and precision using this Food Quality Security Checklist Icon Guidelines Pdf. This layout presents information on Food Quality, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Food Quality Security Checklist Icon Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Security Compliance System Icon Clipart Pdf
Pitch your topic with ease and precision using this Data Security Compliance System Icon Clipart Pdf. This layout presents information on Data Security, Compliance System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Security Compliance System Icon Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icon Showcasing Security Network Analysis Structure Pdf
Pitch your topic with ease and precision using this Icon Showcasing Security Network Analysis Structure Pdf This layout presents information on Icon Showcasing Security, Network Analysis It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Icon Showcasing Security Network Analysis Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
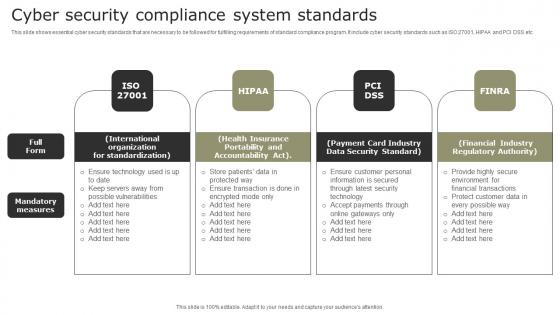
Cyber Security Compliance System Standards Demonstration Pdf
This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc. Showcasing this set of slides titled Cyber Security Compliance System Standards Demonstration Pdf. The topics addressed in these templates are International Organization, Health Insurance, Payment Card Industry. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc.
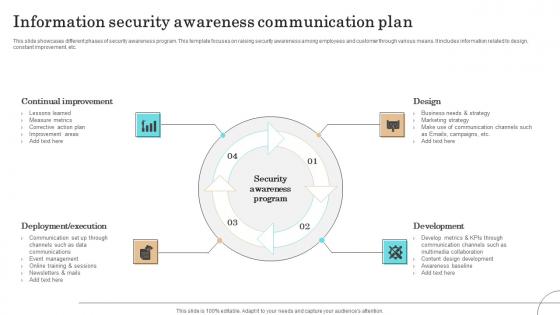
Information Security Awareness Communication Plan Formats Pdf
This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.Pitch your topic with ease and precision using this Information Security Awareness Communication Plan Formats Pdf This layout presents information on Continual Improvement, Deployment Execution, Communication It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.

Timeline For Implementing Efficient Application Security Testing
This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Are you searching for a Timeline For Implementing Efficient Application Security Testing that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Timeline For Implementing Efficient Application Security Testing from Slidegeeks today. This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc.
Icons Slide For Cloud Security Firewall Proposal
Elevate your presentations with our intuitive Icons Slide For Cloud Security Firewall Proposal template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression. Our Icons Slide For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
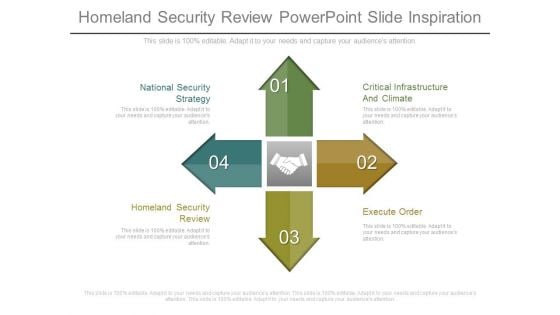
Homeland Security Review Powerpoint Slide Inspiration
This is a homeland security review powerpoint slide inspiration. This is a four stage process. The stages in this process are national security strategy, critical infrastructure and climate, homeland security review, execute order.
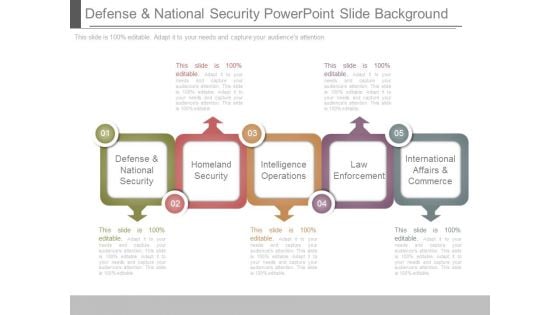
Defense And National Security Powerpoint Slide Background
This is a defense and national security powerpoint slide background. This is a five stage process. The stages in this process are defense and national security, homeland security, intelligence operations, law enforcement, international affairs and commerce.

Security Operations Management Sample Presentation Images
This is a security operations management sample presentation images. This is a five stage process. The stages in this process are compliance and validation, security organization, device control, security operations, patch management.

Essential Pillars Of Cloud Security Brochure PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Essential Pillars Of Cloud Security Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Based Security, Network Security, Identity Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
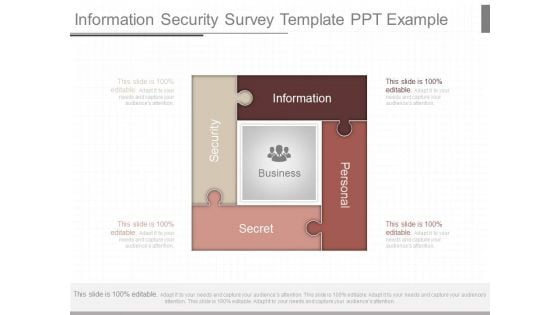
Information Security Survey Template Ppt Example
This is a information security survey template ppt example. This is a four stage process. The stages in this process are information, security, personal, secret.
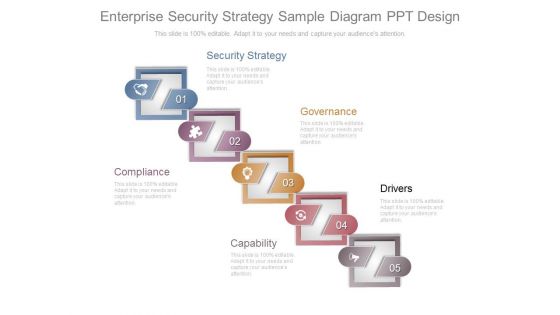
Enterprise Security Strategy Sample Diagram Ppt Design
This is a enterprise security strategy sample diagram ppt design. This is a five stage process. The stages in this process are security strategy, governance, drivers, compliance, capability.
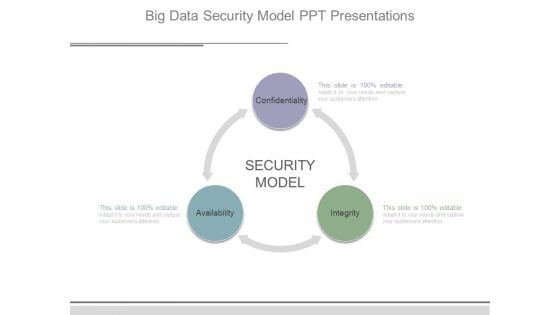
Big Data Security Model Ppt Presentations
This is a big data security model ppt presentations. This is a three stage process. The stages in this process are security model, confidentiality, availability, integrity.
Cyber Security Ppt PowerPoint Presentation Slides Cpb
This is a cyber security ppt powerpoint presentation slides cpb. This is a three stage process. The stages in this process are cyber security.
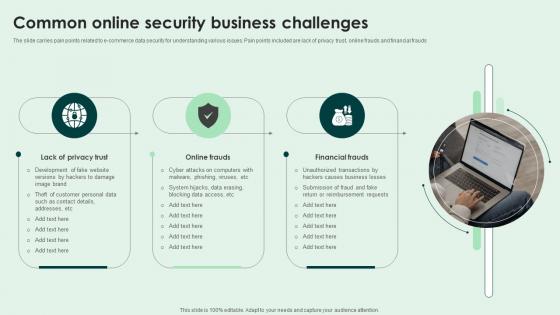
Common Online Security Business Challenges Guidelines Pdf
Showcasing this set of slides titled Common Online Security Business Challenges Guidelines Pdf. The topics addressed in these templates are Lack Of Privacy Trust, Online Frauds, Financial Frauds. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Common Online Security Business Challenges Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
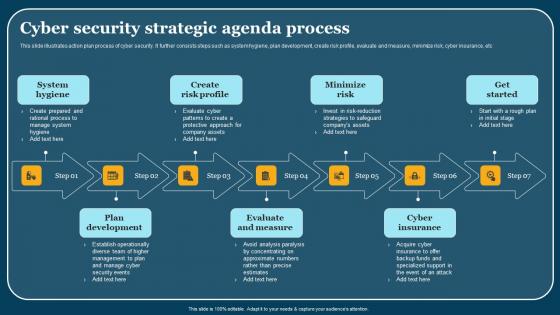
Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc.
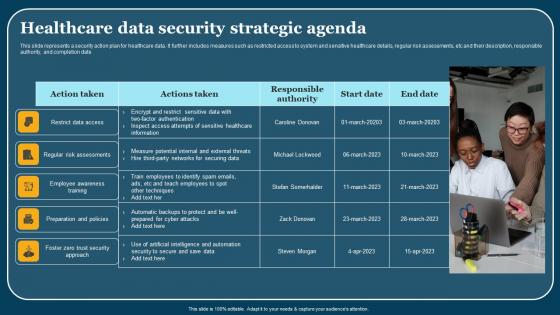
Healthcare Data Security Strategic Agenda Themes Pdf
This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date. Showcasing this set of slides titled Healthcare Data Security Strategic Agenda Themes Pdf. The topics addressed in these templates are Employee Awareness Training, Action Taken. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date.

Security Handbook For Corporate Personnel Information Pdf
Create an editable Security Handbook For Corporate Personnel Information Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Handbook For Corporate Personnel Information Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Following slide exhibits impact of effective internal communication on employee based on measurement performance indicators. It include elements such as engagement rate, turnover rate, productivity etc.

Implementing Authentication In Application Security PPT Example

Cloud Security Implementation Strategy Ppt Presentation

Mobile Application Security Testing PPT Sample

Cloud Native Application Security PPT Template

Data Security In Cloud Computing Ppt Presentation

Cloud Security Implementation Strategy Ppt Template
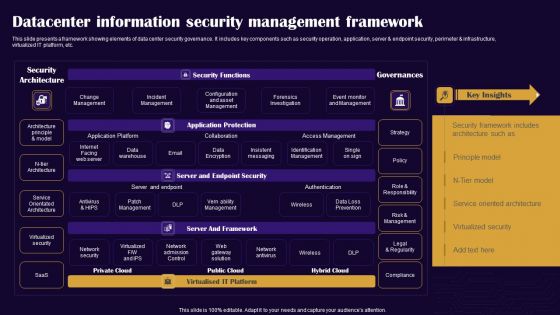
Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
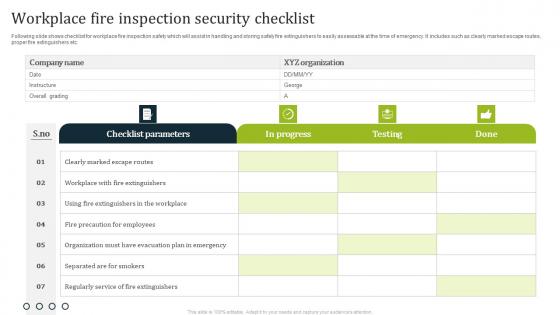
Workplace Fire Inspection Security Checklist Diagrams Pdf
Following slide shows checklist for workplace fire inspection safety which will assist in handling and storing safely fire extinguishers to easily assessable at the time of emergency. It includes such as clearly marked escape routes, proper fire extinguishers etc. Showcasing this set of slides titled Workplace Fire Inspection Security Checklist Diagrams Pdf. The topics addressed in these templates are Checklist Parameters, Done, Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows checklist for workplace fire inspection safety which will assist in handling and storing safely fire extinguishers to easily assessable at the time of emergency. It includes such as clearly marked escape routes, proper fire extinguishers etc.
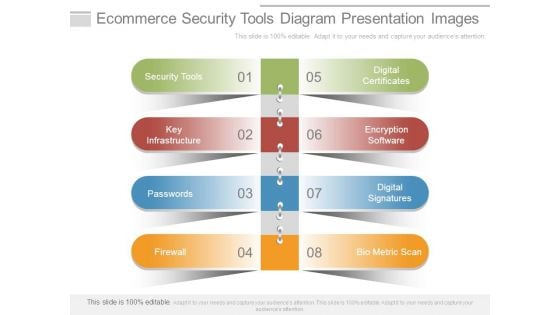
Ecommerce Security Tools Diagram Presentation Images
This is a ecommerce security tools diagram presentation images. This is a eight stage process. The stages in this process are security tools, key infrastructure, passwords, firewall, digital certificates, encryption software, digital signatures, bio metric scan.
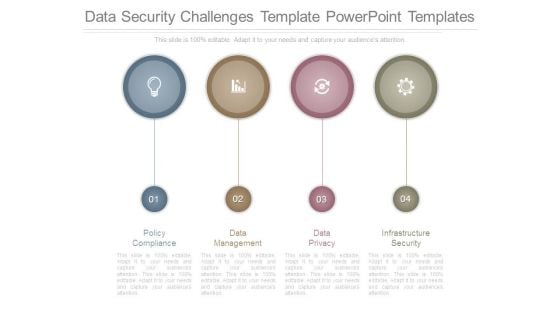
Data Security Challenges Template Powerpoint Templates
This is a data security challenges template powerpoint templates. This is a four stage process. The stages in this process are policy compliance, data management, data privacy, infrastructure security.
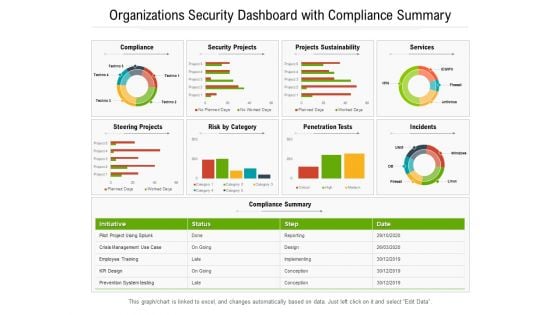
Organizations Security Dashboard With Compliance Summary Ppt PowerPoint Presentation Gallery Layouts PDF
Presenting this set of slides with name organizations security dashboard with compliance summary ppt powerpoint presentation gallery layouts pdf. The topics discussed in these slides are sustainability, security, services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
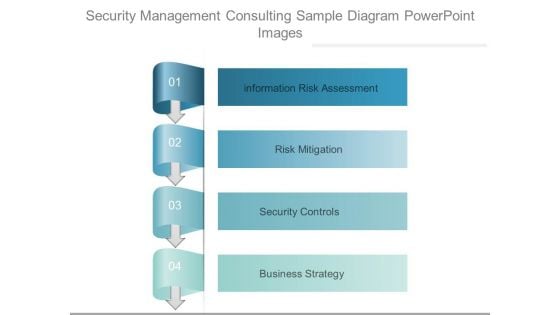
Security Management Consulting Sample Diagram Powerpoint Images
This is a security management consulting sample diagram powerpoint images. This is a four stage process. The stages in this process are information risk assessment, risk mitigation, security controls, business strategy.
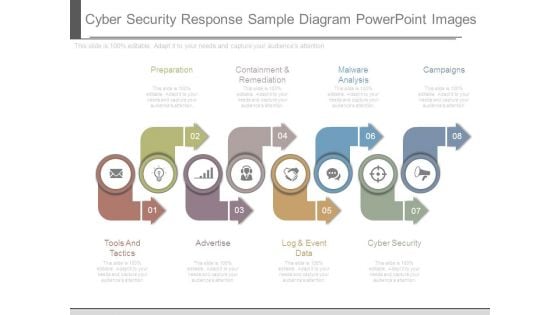
Cyber Security Response Sample Diagram Powerpoint Images
This is a cyber security response sample diagram powerpoint images. This is a eight stage process. The stages in this process are preparation, containment and remediation, malware analysis, campaigns, cyber security, log and event data, advertise, tools and tactics.
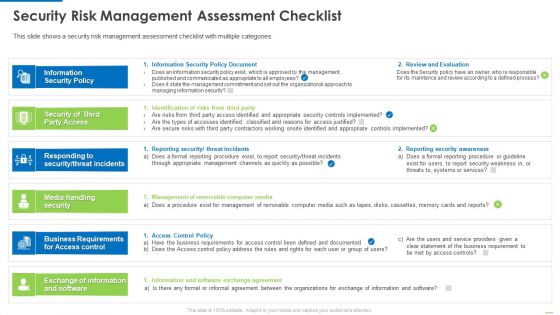
Security Risk Management Assessment Checklist Inspiration PDF
This is a security risk management assessment checklist inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security policy, security of third party access, media handling security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Risk Management Assessment Checklist Structure PDF
Presenting security risk management assessment checklist structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, media handling security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Risk Management Assessment Checklist Brochure PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver and pitch your topic in the best possible manner with this security risk management assessment checklist brochure pdf. Use them to share invaluable insights on security, management, requirements, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Computer Safety And Security Icon Infographics PDF
Persuade your audience using this Computer Safety And Security Icon Infographics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Computer Safety, Security Icon Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
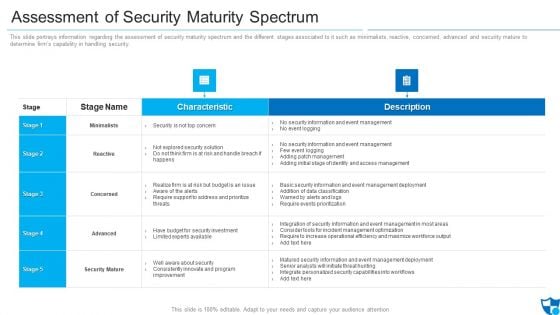
Assessment Of Security Maturity Spectrum Clipart PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative assessment of security maturity spectrum clipart pdf bundle. Topics like security is not top concern, require support to address, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
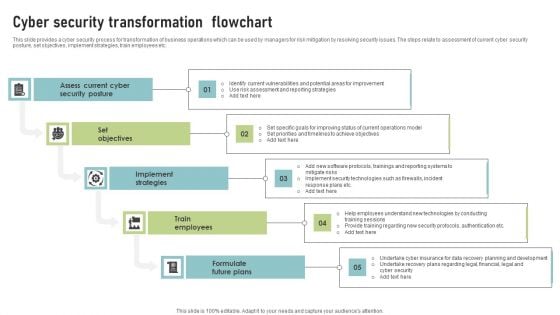
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Website Template Powerpoint Slide Background Designs
This is a security website template powerpoint slide background designs. This is a six stage process. The stages in this process are inventory, secure coding, secure testing, remediation plan, define next steps, deep scan.
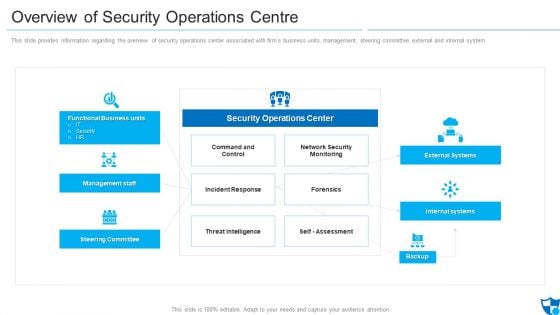
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
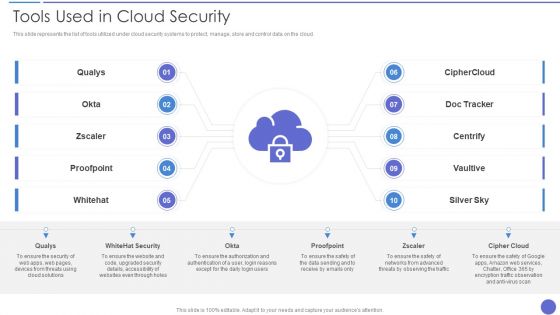
Tools Used In Cloud Security Template PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Presenting Tools Used In Cloud Security Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Qualys, Whitehat Security, Cipher Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internet Security Diagram Template Ppt Slide Styles
This is a internet security diagram template ppt slide styles. This is a five stage process. The stages in this process are search, protection, password, antivirus, firewall.
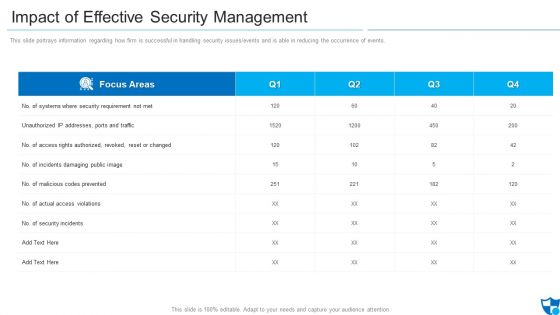
Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this impact of effective security management information pdf. Use them to share invaluable insights on malicious codes prevented, unauthorized ip addresses ports and traffic, security incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
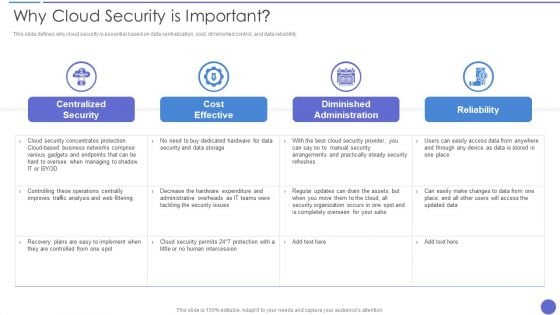
Why Cloud Security Is Important Demonstration PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver an awe inspiring pitch with this creative Why Cloud Security Is Important Demonstration PDF bundle. Topics like Cost Effective, Centralized Security, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
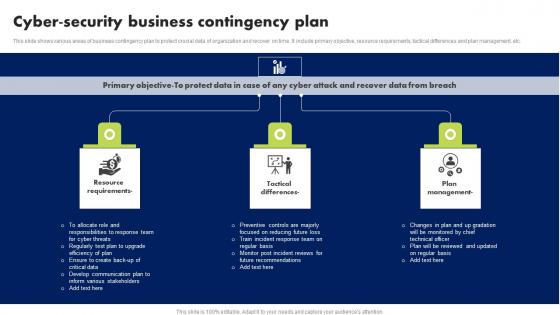
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc.

Main Data Security Tokenization Techniques PPT Powerpoint
This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. Boost your pitch with our creative Main Data Security Tokenization Techniques PPT Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc.

Weakest Link Security PowerPoint Template 0510
weakest link in the chain on a white background Get comfy with our Weakest Link Security PowerPoint Template 0510. Make your audience feel at ease.

Weak Link Chain Security PowerPoint Template 0910
red man breaks the chain on white background Remove confusionswith our Weak Link Chain Security PowerPoint Template 0910. You'll deliver your best presentation yet.

Binary Internet Security PowerPoint Template 1110
Graphic depicting binary data escaping through a keyhole Make our Binary Internet Security PowerPoint Template 1110 the abode for your thoughts. They will exist in complete comfort.

Identity Theft Security PowerPoint Template 1110
Hand punching through the image grabbing documents Get people out of bed with our Identity Theft Security PowerPoint Template 1110. Just download, type and present.


 Continue with Email
Continue with Email

 Home
Home


































