Security Steps
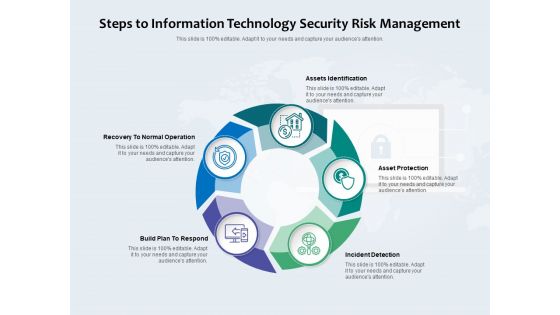
Steps To Information Technology Security Risk Management Ppt PowerPoint Presentation Gallery Example File PDF
Presenting steps to information technology security risk management ppt powerpoint presentation gallery example file pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including assets identification, asset protection, incident detection, build plan to respond, recovery to normal operation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
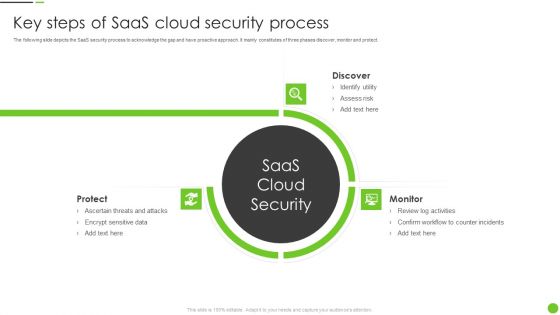
Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide depicts the SaaS security process to acknowledge the gap and have proactive approach. It mainly constitutes of three phases discover, monitor and protect. Persuade your audience using this Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Discover, Monitor, Protect, Identify Utility, Assess Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
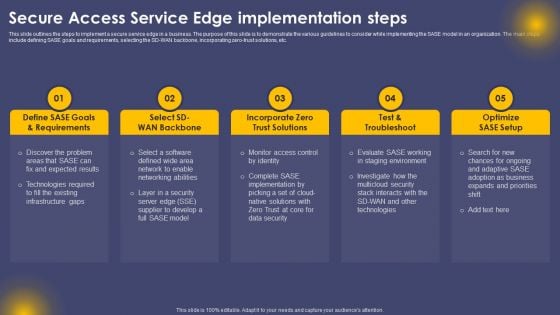
Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF
This slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Get a simple yet stunning designed Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Next Step For Safety And Security System Services Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be team meeting ,on-site visit etc. Presenting you an exemplary Next Step For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Four Steps Arrow For Business Data Security Process Ppt PowerPoint Presentation File Background Image PDF
Presenting four steps arrow for business data security process ppt powerpoint presentation file background image pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including four steps arrow for business data security process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Five Steps Circular Process For Application Security Testing Ppt PowerPoint Presentation Styles Icon
Presenting this set of slides with name five steps circular process for application security testing ppt powerpoint presentation styles icon. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Eight Steps Of Portfolio Management With Security Analysis Ppt PowerPoint Presentation Gallery Deck PDF
Persuade your audience using this eight steps of portfolio management with security analysis ppt powerpoint presentation gallery deck pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including security analysis, portfolio analysis, portfolio evaluation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
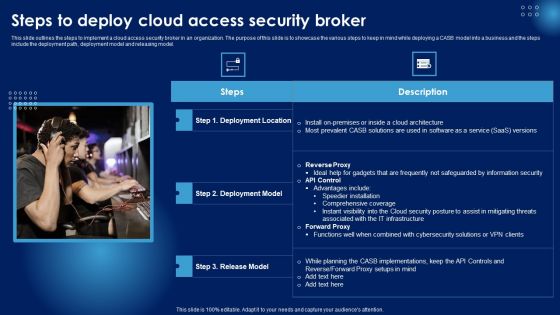
Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
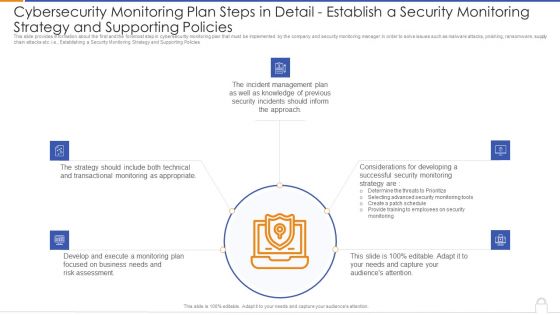
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Supporting Policies Microsoft PDF
Presenting cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like transactional monitoring, develop and execute, incident management plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
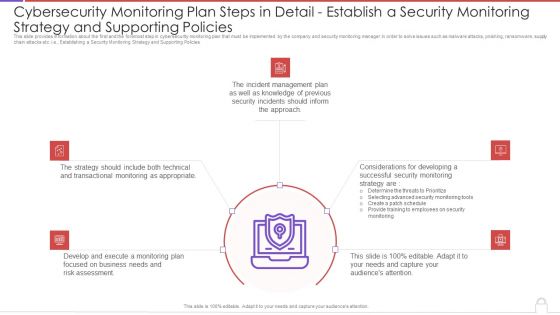
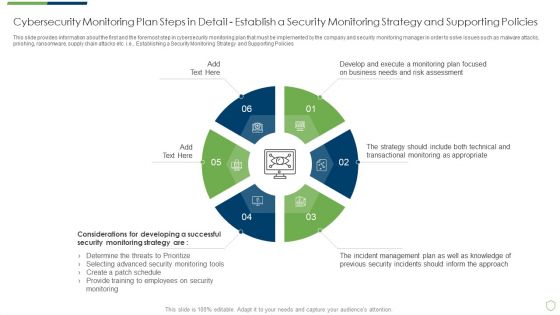
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
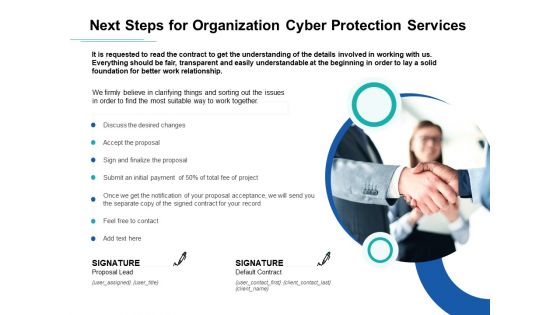
Develop Corporate Cyber Security Risk Mitigation Plan Next Steps For Organization Cyber Protection Services Topics PDF Themes PDF
Presenting develop corporate cyber security risk mitigation plan next steps for organization cyber protection services topics pdf themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like desired changes, initial payment, organization, cyber protection services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
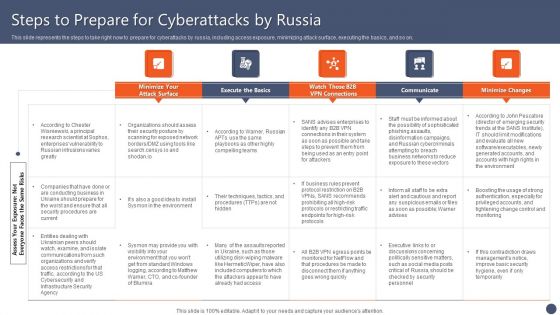
Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF
The following slide highlights multistep process of digitization of security systems. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked. Presenting Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
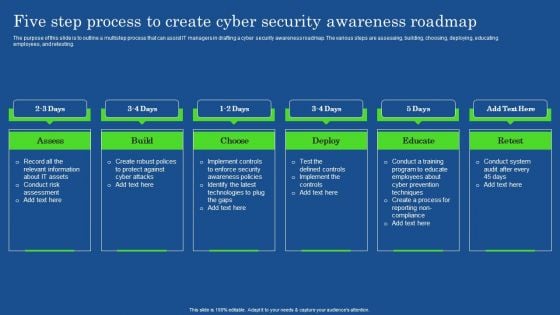
Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF
The purpose of this slide is to outline a multistep process that can assist IT managers in drafting a cyber security awareness roadmap. The various steps are assessing, building, choosing, deploying, educating employees, and retesting. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
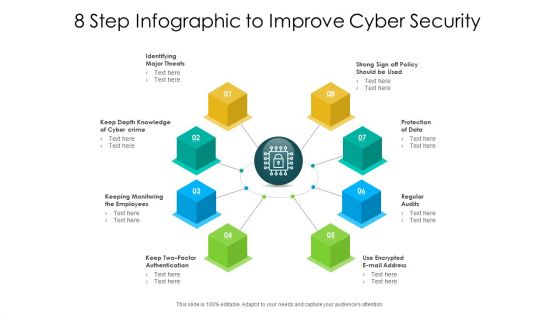
8 Step Infographic To Improve Cyber Security Ppt PowerPoint Presentation Layouts Themes PDF
Presenting 8 step infographic to improve cyber security ppt powerpoint presentation layouts themes pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including identifying major threats, keep depth knowledge of cyber crime, protection of data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
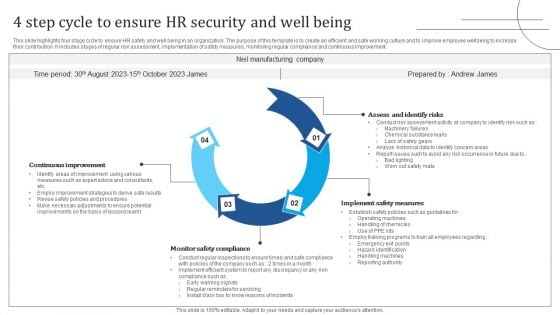
4 Step Cycle To Ensure HR Security And Well Being Graphics PDF
This slide highlights four stage cycle to ensure HR safety and well being in an organization. The purpose of this template is to create an efficient and safe working culture and to improve employee wellbeing to increase their contribution. It includes stages of regular risk assessment, implementation of safety measures, monitoring regular compliance and continuous improvement. Presenting 4 Step Cycle To Ensure HR Security And Well Being Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assess And Identify Risks, Implement Safety Measures, Monitor Safety Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
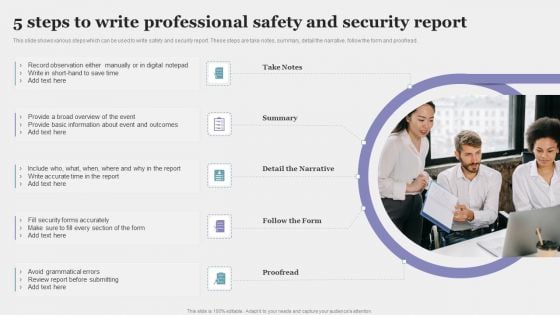
5 Steps To Write Professional Safety And Security Report Formats PDF
This slide shows various steps which can be used to write safety and security report. These steps are take notes, summary, detail the narrative, follow the form and proofread. Presenting 5 Steps To Write Professional Safety And Security Report Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Forms Accurately, Basic Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
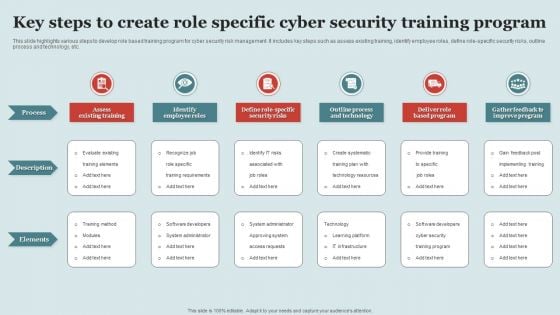
Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
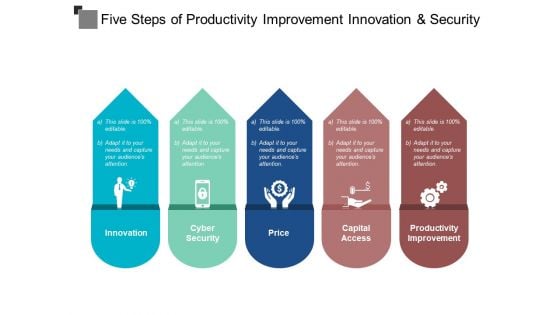
Five Steps Of Productivity Improvement Innovation And Security Ppt PowerPoint Presentation Layouts Inspiration
This is a five steps of productivity improvement innovation and security ppt powerpoint presentation layouts inspiration. This is a five stage process. The stages in this process are risk management, risk factors, risk variable.
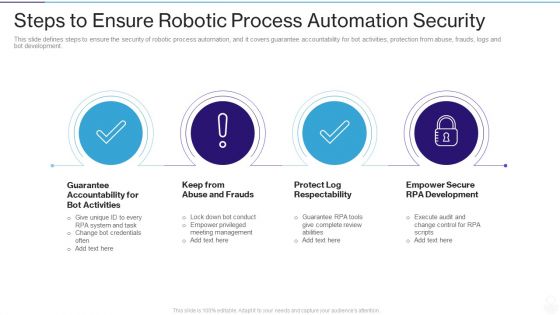
RPA IT Steps To Ensure Robotic Process Automation Security Ppt Layouts Layout Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a rpa it steps to ensure robotic process automation security ppt layouts layout ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like guarantee accountability for bot activities, keep from abuse and frauds, protect log respectability, empower secure rpa development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development.This is a Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Empower Secure, Log Respectability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
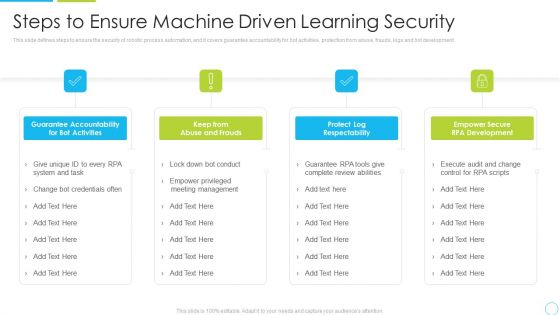
Steps To Ensure Machine Driven Learning Security Ppt Inspiration Structure PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. Presenting steps to ensure machine driven learning security ppt inspiration structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like system, management, development, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
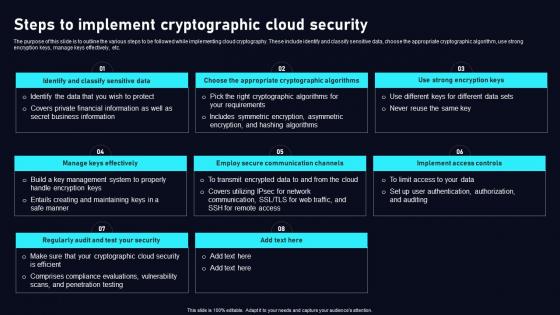
Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Find highly impressive Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.
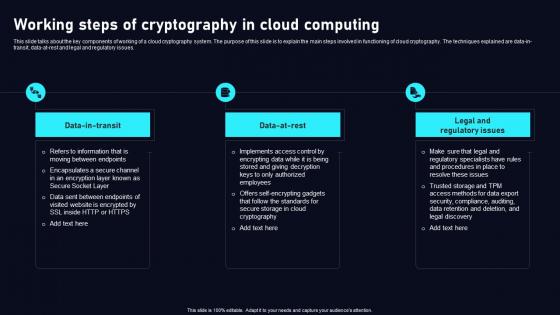
Working Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. There are so many reasons you need aWorking Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
8 Steps Circle Of Internal Audit And Cyber Security Ppt PowerPoint Presentation Gallery Themes PDF
Persuade your audience using this 8 steps circle of internal audit and cyber security ppt powerpoint presentation gallery themes pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 steps circle of internal audit and cyber security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
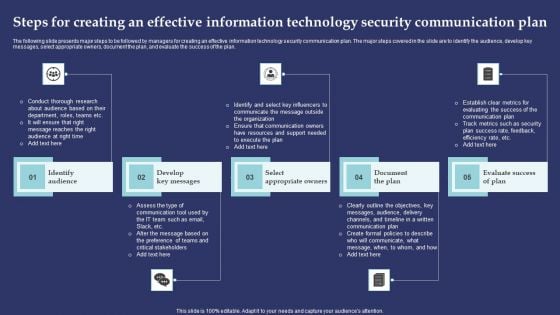
Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF
The following slide presents major steps to be followed by managers for creating an effective information technology security communication plan. The major steps covered in the slide are to identify the audience, develop key messages, select appropriate owners, document the plan, and evaluate the success of the plan. Presenting Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Audience, Develop Key Messages, Select Appropriate Owners. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.m
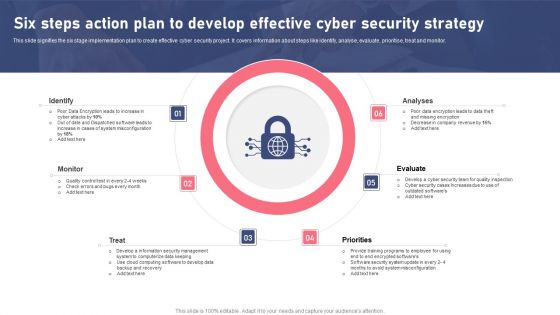
Six Steps Action Plan To Develop Effective Cyber Security Strategy Ppt Layouts Designs Download PDF
This slide signifies the six stage implementation plan to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor. Presenting Six Steps Action Plan To Develop Effective Cyber Security Strategy Ppt Layouts Designs Download PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Identify, Monitor, Priorities, Evaluate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
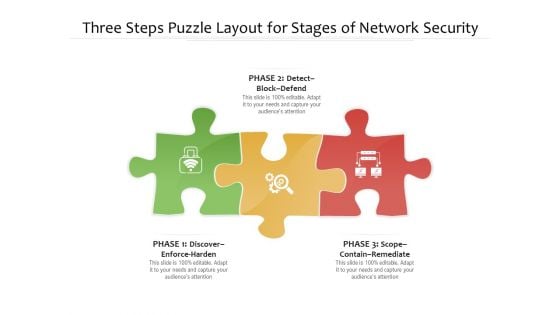
Three Steps Puzzle Layout For Stages Of Network Security Ppt PowerPoint Presentation File Vector PDF
Persuade your audience using this three steps puzzle layout for stages of network security ppt powerpoint presentation file vector pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
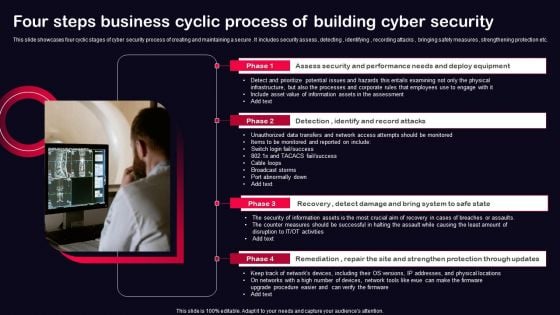
Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Six Steps Of System Development Service Delivery And Data Security Ppt PowerPoint Presentation Icon Slide Download
This is a six steps of system development service delivery and data security ppt powerpoint presentation icon slide download. This is a six stage process. The stages in this process are risk management, risk factors, risk variable.
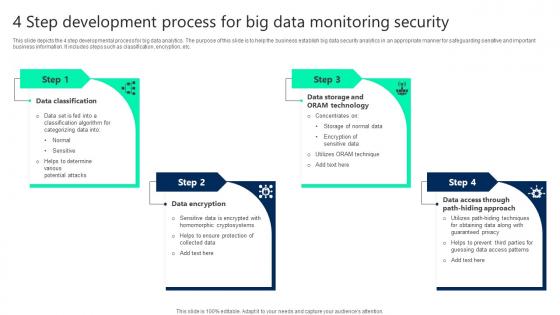
4 Step Development Process For Big Data Monitoring Security Demonstration pdf
This slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc. Showcasing this set of slides titled 4 Step Development Process For Big Data Monitoring Security Demonstration pdf. The topics addressed in these templates are Data Classification, Data Access, Data Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc.
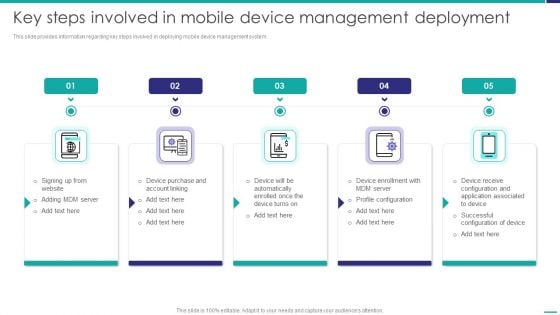
Key Steps Involved In Mobile Device Management Deployment Mobile Device Security Management Infographics PDF
This slide provides information regarding key steps involved in deploying mobile device management system. Presenting Key Steps Involved In Mobile Device Management Deployment Mobile Device Security Management Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Device Purchase, Device Automatically, Profile Configuration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
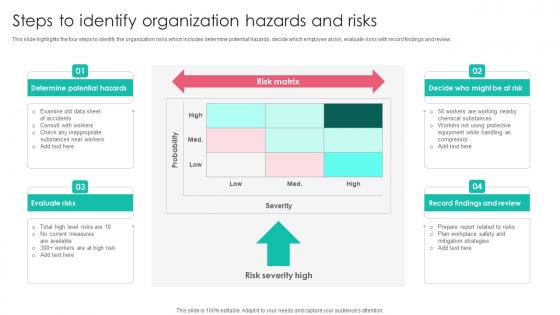
Steps To Identify Organization Hazards Workplace Safety Protocol And Security Practices Template Pdf
This slide highlights the four steps to identify the organization risks which includes determine potential hazards, decide which employee at risk, evaluate risks with record findings and review. Want to ace your presentation in front of a live audience Our Steps To Identify Organization Hazards Workplace Safety Protocol And Security Practices Template Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide highlights the four steps to identify the organization risks which includes determine potential hazards, decide which employee at risk, evaluate risks with record findings and review.
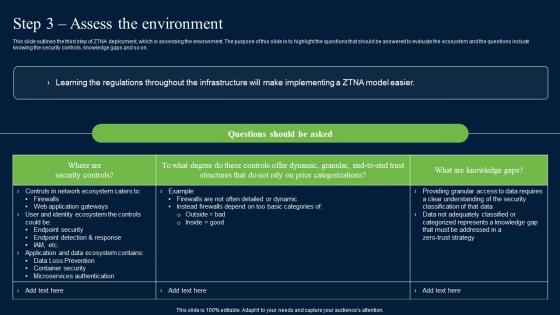
Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Want to ace your presentation in front of a live audience Our Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
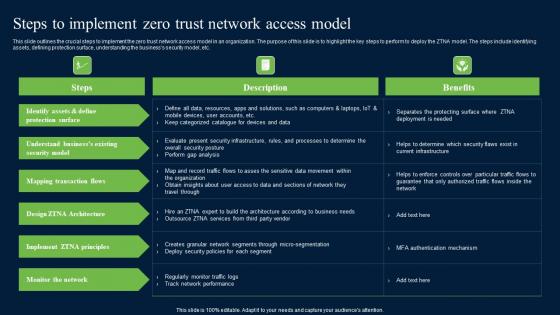
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
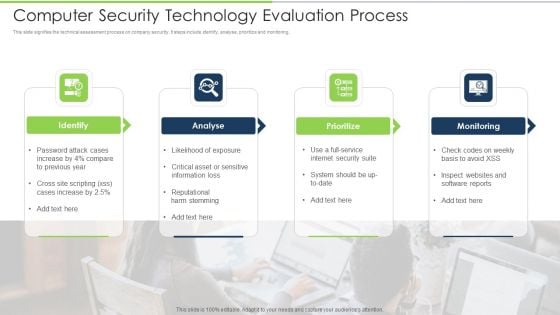
Computer Security Technology Evaluation Process Download PDF
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
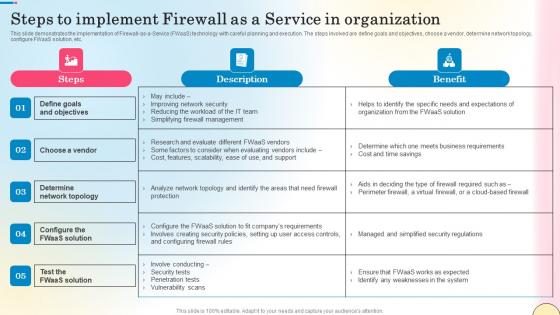
Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf
This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Get a simple yet stunning designed Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.

Key Steps Involved In Mobile Device Management Deployment Business Mobile Device Security Topics PDF
This slide provides information regarding key steps involved in deploying mobile device management system. Get a simple yet stunning designed Key Steps Involved In Mobile Device Management Deployment Business Mobile Device Security Topics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Key Steps Involved In Mobile Device Management Deployment Business Mobile Device Security Topics PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
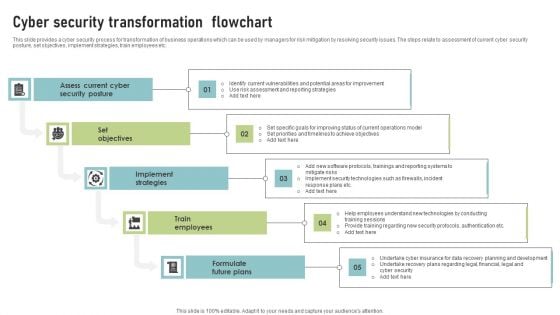
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Website Template Powerpoint Slide Background Designs
This is a security website template powerpoint slide background designs. This is a six stage process. The stages in this process are inventory, secure coding, secure testing, remediation plan, define next steps, deep scan.
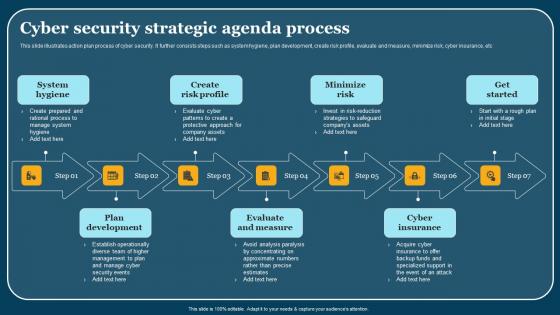
Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
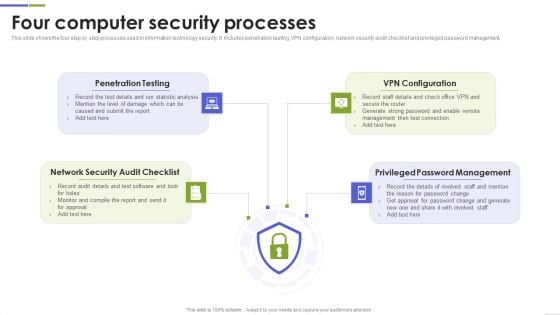
Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
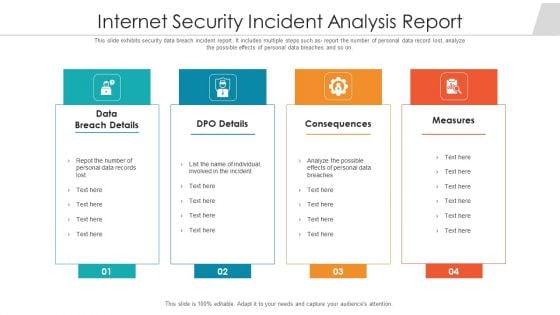
Internet Security Incident Analysis Report Template PDF
This slide exhibits security data breach incident report. It includes multiple steps such as- report the number of personal data record lost, analyze the possible effects of personal data breaches and so on. Showcasing this set of slides titled internet security incident analysis report template pdf. The topics addressed in these templates are data breach details, consequences, measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Techniques And Strategies To Reduce Security Management Risks Security Detail Risk Assessment And Analysis Template PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks security detail risk assessment and analysis template pdf Use them to share invaluable insights on security breach, perform a threat, several measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
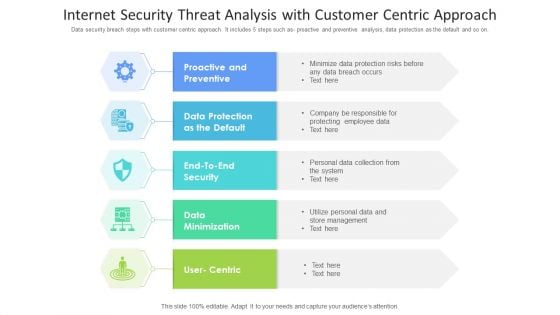
Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
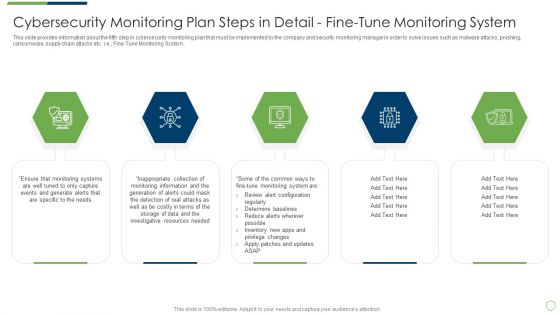
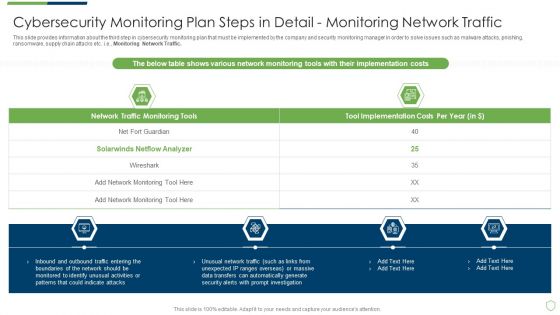
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
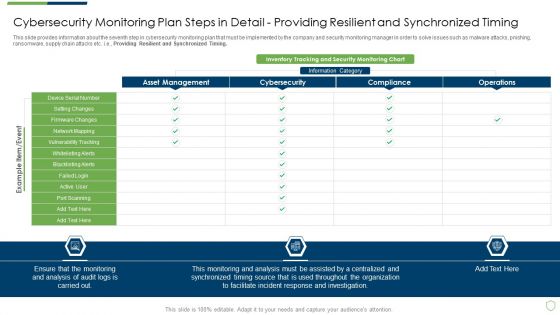
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
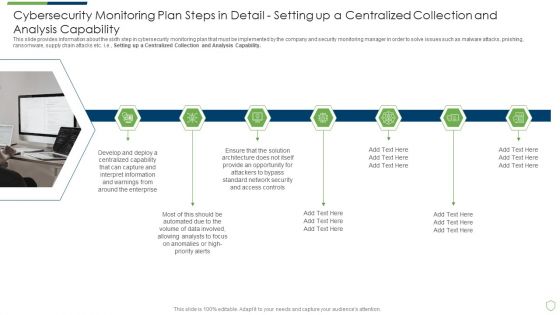
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
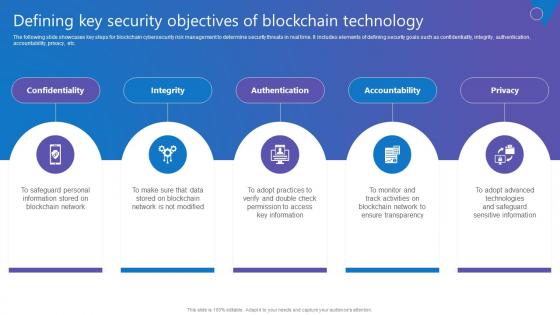
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc.

Techniques And Strategies To Reduce Security Management Risks Security Detail System Maintenance And Monitoring Mockup PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. This is a techniques and strategies to reduce security management risks security detail system maintenance and monitoring mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perfective maintenance, corrective maintenance, perfective maintenance You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
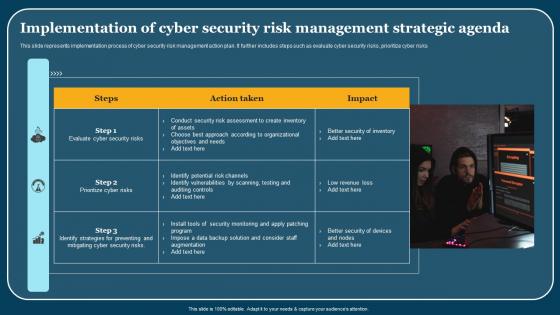
Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks.

Information Security Risk Evaluation Timeline For Information Security Risk Management Training Background PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Timeline For Information Security Risk Management Training Background PDF bundle. Topics like Cybersecurity Awareness, Malware Detection, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Chain Security PowerPoint Templates And PowerPoint Themes 1012
Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template consists of an image of many linked chains connected to one circular green chain. This image represents the concept of security or steps of business strategies. This template also emphasize strong group between family, business etc. Present your views using our innovative slides and be assured of leaving a lasting impression. -Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chains of design, communication, security, business, teamwork, industrial Set a good example with our Chain Security PowerPoint Templates And PowerPoint Themes 1012. Be the benchmark for others to follow.

Information Systems Security And Risk Management Plan Timeline For Information Security Risk Management Training Inspiration PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Present like a pro with Information Systems Security And Risk Management Plan Timeline For Information Security Risk Management Training Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

 Home
Home