Security Steps

Blockchain Security Solutions Deployment How Organizations Maintaining Blockchain Mockup PDF
This slide represents the various organizations that are taking security measures to prevent cyberattacks on blockchain network. The purpose of this slide is to highlight the various steps taken by US based organizations to prevent blockchain from cyber attacks and frauds. Slidegeeks is here to make your presentations a breeze with Blockchain Security Solutions Deployment How Organizations Maintaining Blockchain Mockup PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Locked House Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Secuity PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download and present our Real estate PowerPoint Templates because Your audience will believe you are the cats whiskers. Present our Business PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Present our Construction PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team.Use these PowerPoint slides for presentations relating to Key with house, security, success, real estate, business, construction. The prominent colors used in the PowerPoint template are Blue, White, Gray. We assure you our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our real PowerPoint templates and PPT Slides are second to none. Presenters tell us our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Professionals tell us our real PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. The feedback we get is that our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides will help them to explain complicated concepts. Experience acclaim with our Locked House Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Your thoughts will acquire true fame.
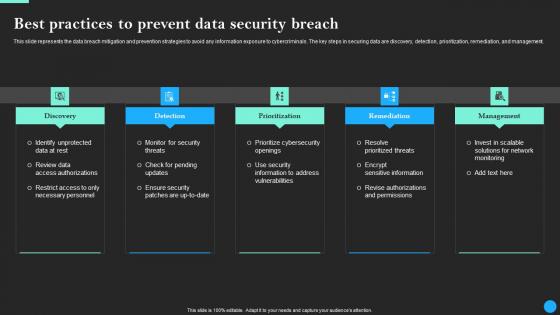
Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.
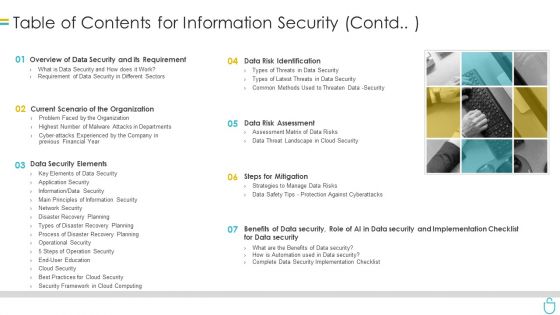
Table Of Contents For Information Security Contd Ppt Show Topics PDF
This is a table of contents for information security contd ppt show topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, requirement, data security, data risk assessment, steps for mitigation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
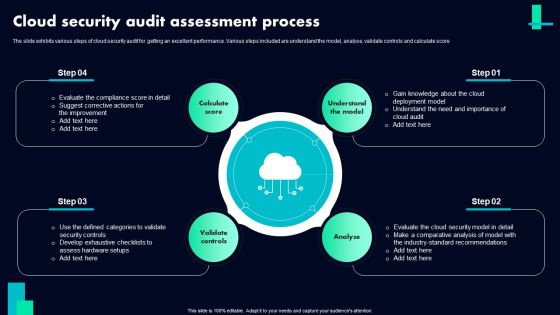
Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF
The slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Persuade your audience using this Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF. This PPT design covers FOUR stages, thus making it a great tool to use. It also caters to a variety of topics including Calculate Score, Understand The Model, Analyse Validate Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
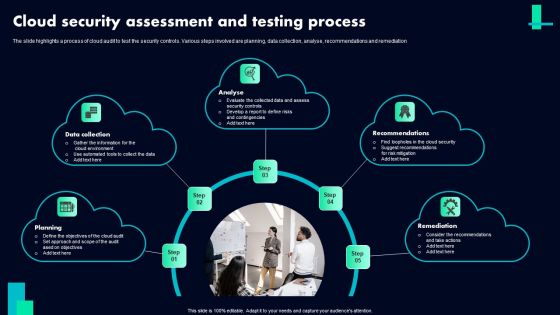
Cloud Security Assessment And Testing Process Ppt PowerPoint Presentation File Outline PDF
The slide highlights a process of cloud audit to test the security controls. Various steps involved are planning, data collection, analyse, recommendations and remediation Persuade your audience using this Cloud Security Assessment And Testing Process Ppt PowerPoint Presentation File Outline PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Analyse, Recommendations, Remediation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Data Security Software Table Of Contents Introduction PDF
Presenting this set of slides with name best data security software table of contents introduction pdf. The topics discussed in these slides are project context and objectives, our process, your investment, company overview, our past experience, statement of work and contract, next steps. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Data Security Strategy Ppt PowerPoint Presentation Portfolio Infographic Template Cpb
Presenting this set of slides with name data security strategy ppt powerpoint presentation portfolio infographic template cpb. This is an editable Powerpoint three stages graphic that deals with topics like data security strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
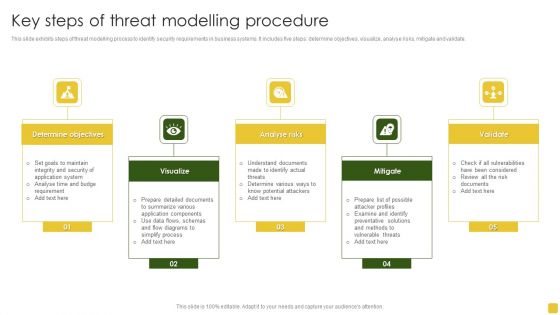
Key Steps Of Threat Modelling Procedure Brochure PDF
This slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate.Persuade your audience using this Key Steps Of Threat Modelling Procedure Brochure PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Determine Objectives, Preventative Solutions, Determine Various Ways. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
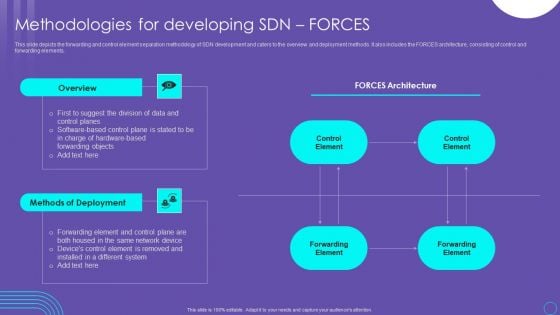
SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF
This slide depicts the forwarding and control element separation methodology of SDN development and caters to the overview and deployment methods. It also includes the FORCES architecture, consisting of control and forwarding elements. Take your projects to the next level with our ultimate collection of SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF
This slide highlights security risks occurred in the company. The purpose of this template is to report the severity of security threats. It also includes action steps taken in prevention or resolution of security incidents along with risk categories. Showcasing this set of slides titled Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF. The topics addressed in these templates are Incidents, Category, Severity, Response Action Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
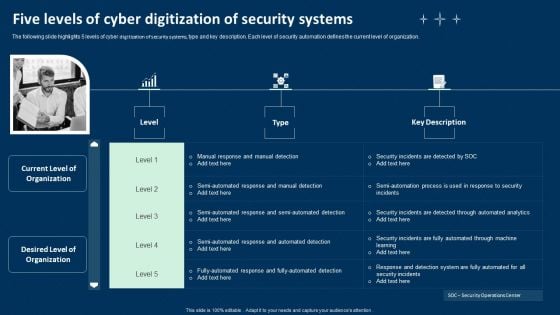
Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF
The following slide highlights 5 levels of cyber digitization of security systems, type and key description. Each level of security automation defines the current level of organization. Presenting Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
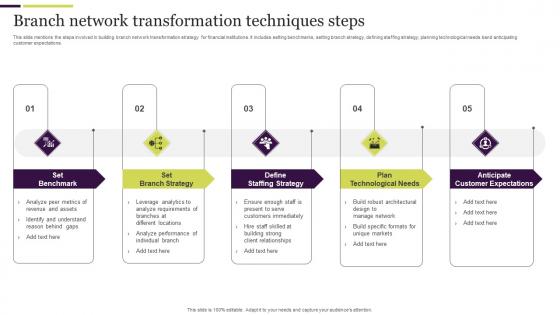
Branch Network Transformation Techniques Steps Ideas Pdf
This slide mentions the steps involved in building branch network transformation strategy for financial institutions. It includes setting benchmarks, setting branch strategy, defining staffing strategy, planning technological needs band anticipating customer expectations. Pitch your topic with ease and precision using this Branch Network Transformation Techniques Steps Ideas Pdf. This layout presents information on Plan Technological Needs, Anticipate Customer Expectations, Set Benchmark. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide mentions the steps involved in building branch network transformation strategy for financial institutions. It includes setting benchmarks, setting branch strategy, defining staffing strategy, planning technological needs band anticipating customer expectations.

Traces Green Foot Steps Technology PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with traces of footsteps going to something certain Bid adieu to difficulty. Our Traces Green Foot Steps Technology PowerPoint Backgrounds And Templates 1210 ensure you fare well.
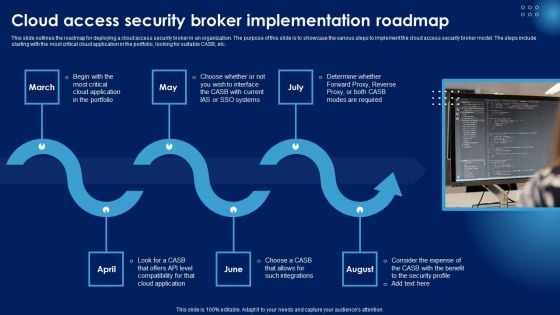
Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
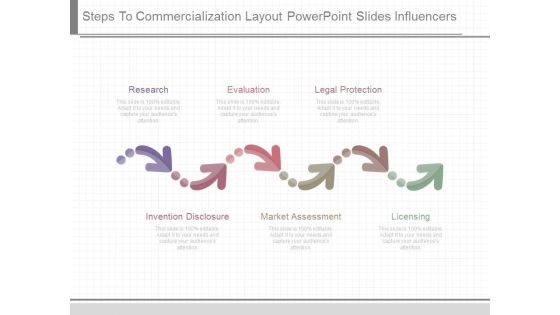
Steps To Commercialization Layout Powerpoint Slides Influencers
This is a steps to commercialization layout powerpoint slides influencers. This is a six stage process. The stages in this process are research, evaluation, legal protection, invention disclosure, market assessment, licensing.
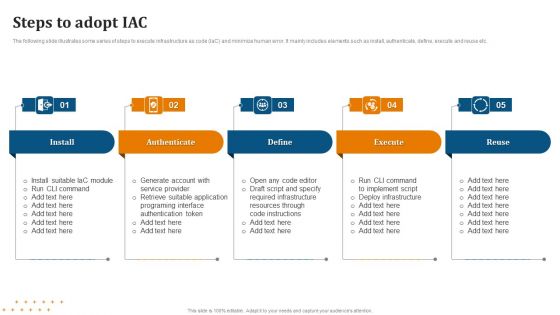
Steps To Adopt IAC Structure PDF
Presenting Steps To Adopt IAC Structure PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Install, Authenticate, Define. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
PowerPoint Templates Arrows 2 Steps Activuty Diagram
We present our powerpoint templates arrows 2 steps activuty diagram.Download and present our Advertising PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Use our Marketing PowerPoint Templates because Your audience will believe you are the cats whiskers. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Use our Signs PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Use our Process and Flows PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides.Use these PowerPoint slides for presentations relating to Activity, Agreement, Assistance, Business, Career, Concept, Cooperation, Development, Diagram, Employment, Entrance, Graphic, Growth, Helping, Improvement, Increase, Job, Lifestyle, Meeting, Merger, Motion, Moving, Opportunity, Partnership, Puppet, Purpose, Rise, Schedule, Staircase, Steps, Strategy, Success, Team, Teamwork. The prominent colors used in the PowerPoint template are Green, Yellow, White. Customers tell us our powerpoint templates arrows 2 steps activuty diagram have awesome images to get your point across. We assure you our Business PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Use our powerpoint templates arrows 2 steps activuty diagram are topically designed to provide an attractive backdrop to any subject. You can be sure our Development PowerPoint templates and PPT Slides will make you look like a winner. PowerPoint presentation experts tell us our powerpoint templates arrows 2 steps activuty diagram are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. The feedback we get is that our Assistance PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Expand on your theory with our PowerPoint Templates Arrows 2 Steps Activuty Diagram. Establish the cause of your confidence.
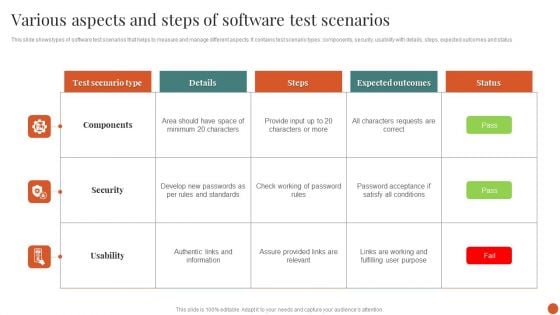
Various Aspects And Steps Of Software Test Scenarios Formats PDF
This slide shows types of software test scenarios that helps to measure and manage different aspects. It contains test scenario types components, security, usability with details, steps, expected outcomes and status.Showcasing this set of slides titled Various Aspects And Steps Of Software Test Scenarios Formats PDF. The topics addressed in these templates are Expected Outcomes, Characters Requests, Assure Provided. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
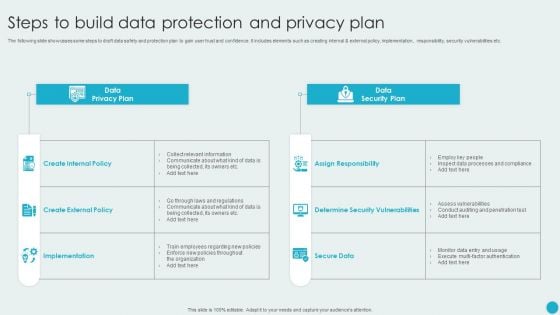
Steps To Build Data Protection And Privacy Plan Diagrams PDF
The following slide showcases some steps to draft data safety and protection plan to gain user trust and confidence. It includes elements such as creating internal and external policy, implementation, responsibility, security vulnerabilities etc. Showcasing this set of slides titled Steps To Build Data Protection And Privacy Plan Diagrams PDF. The topics addressed in these templates are Data Privacy Plan, Data Security Plan, Implementation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Business Diagram Three Key Steps For Business Success Presentation Template
The above template displays a diagram of three keys. This diagram has been professionally designed to emphasize on key steps of success. Grab center stage with this slide. Capture the attention of your audience.

Major Steps To Develop Protection And Precaution Strategy Themes PDF
This slide shows multi steps process to build safety and security strategy. These strategies are assess vulnerabilities, adopt safety measures, control access, alert authorities and audit procedures. Persuade your audience using this Major Steps To Develop Protection And Precaution Strategy Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Assess Vulnerabilities, Adopt Safety Measures, Control Access. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
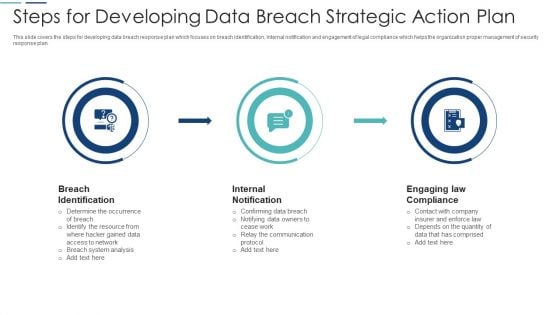
Steps For Developing Data Breach Strategic Action Plan Professional PDF
This slide covers the steps for developing data breach response plan which focuses on breach identification, internal notification and engagement of legal compliance which helps the organization proper management of security response plan. Persuade your audience using this steps for developing data breach strategic action plan professional pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including breach identification, internal notification, engaging law compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
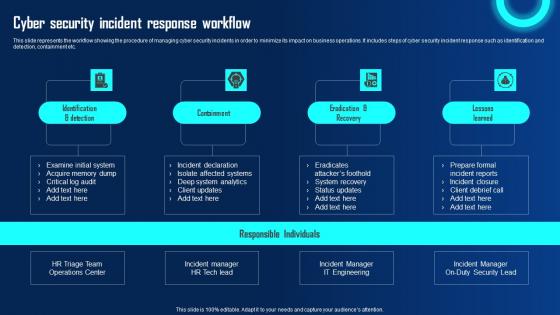
Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf
This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc. This Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc.
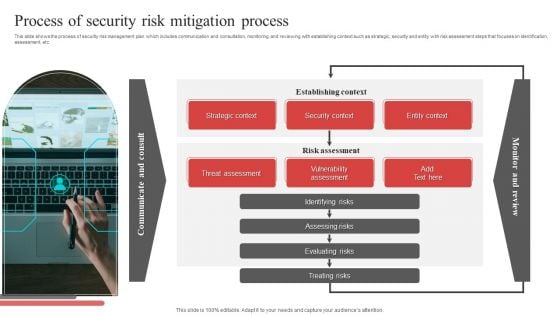
Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide shows the process of security risk management plan which includes communication and consultation, monitoring and reviewing with establishing context such as strategic, security and entity with risk assessment steps that focuses on identification, assessment, etc. Presenting Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Strategic Context, Security Context, Entity Context, Establishing Context. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
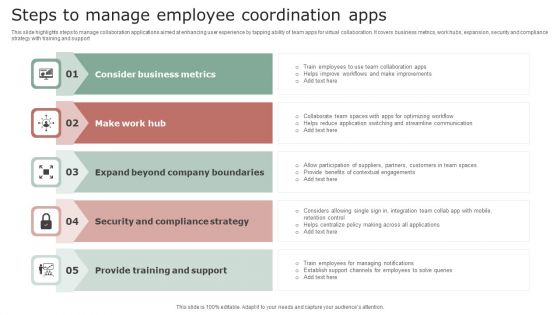
Steps To Manage Employee Coordination Apps Clipart PDF
This slide highlights steps to manage collaboration applications aimed at enhancing user experience by tapping ability of team apps for virtual collaboration. It covers business metrics, work hubs, expansion, security and compliance strategy with training and support. Presenting Steps To Manage Employee Coordination Apps Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Consider Business Metrics, Make Work Hub, Expand Beyond Company. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
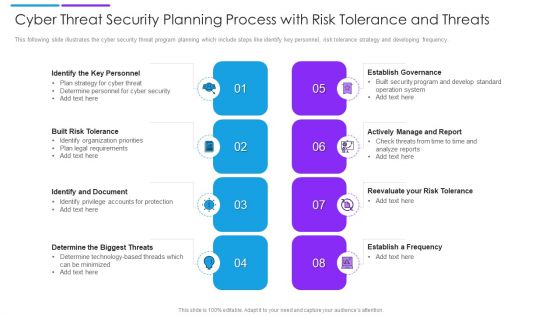
Cyber Threat Security Planning Process With Risk Tolerance And Threats Formats PDF
This following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Persuade your audience using this cyber threat security planning process with risk tolerance and threats formats pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including establish governance, actively manage and report, built risk tolerance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF
This slide signifies the strategic plan timeline to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor Persuade your audience using this Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Analyse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the action plan timeline for security guard service proposal as it displays steps of the process such as training and evaluating etc. Presenting you an exemplary Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the action plan timeline for security guard service proposal as it displays steps of the process such as training and evaluating etc. Presenting you an exemplary Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.
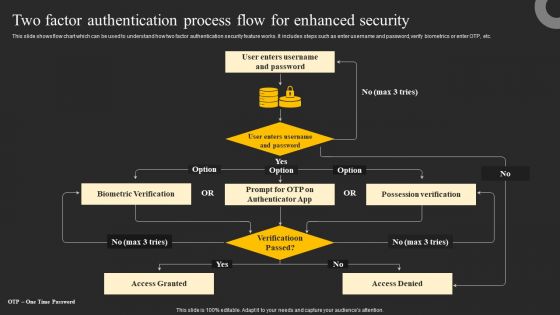
Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Explore a selection of the finest Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
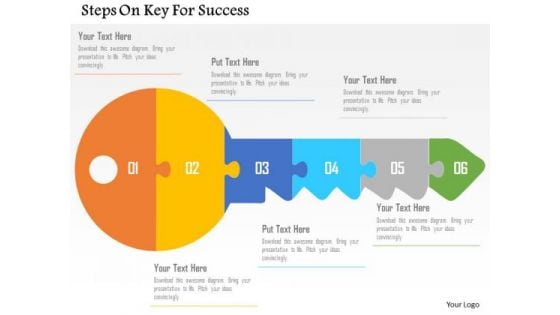
Business Diagram Steps On Key For Success Presentation Template
The above template displays a diagram of a success key. This diagram has been professionally designed to emphasize the steps of success. Grab center stage with this slide. Capture the attention of your audience.
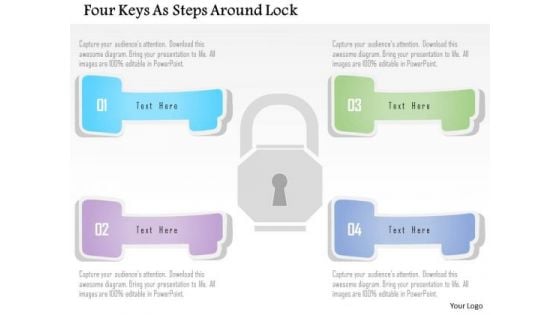
Business Diagram Four Keys As Steps Around Lock Presentation Template
This business diagram slide has been designed with graphic of four keys and lock. This PowerPoint template helps to display safety options in your presentations. Use this to make impressive presentations.
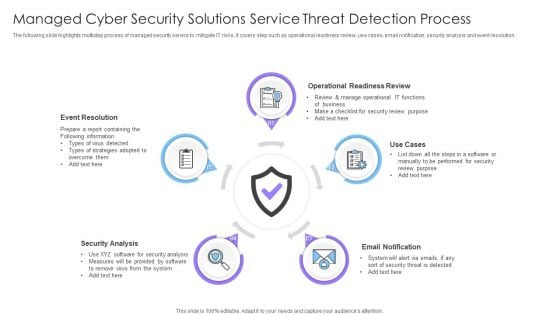
Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
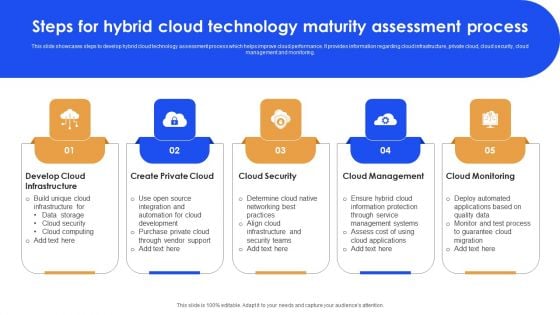
Steps For Hybrid Cloud Technology Maturity Assessment Process Microsoft PDF
This slide showcases steps to develop hybrid cloud technology assessment process which helps improve cloud performance. It provides information regarding cloud infrastructure, private cloud, cloud security, cloud management and monitoring. Persuade your audience using this Steps For Hybrid Cloud Technology Maturity Assessment Process Microsoft PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Cloud Infrastructure, Cloud Security, Cloud Monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
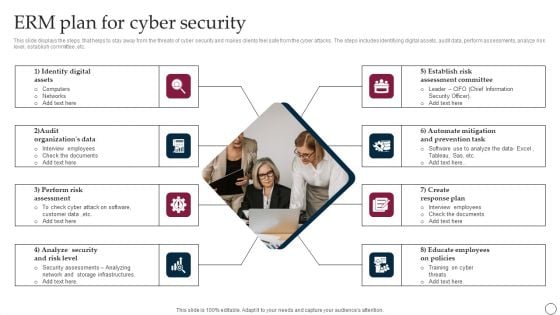
ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
3 Stage Plan Cyber Security Plan For Data Protection Ppt Icon Picture PDF
This slide signifies the three stage cyber security program to improve data protection. It covers information about steps like prevention, response and remediation. Persuade your audience using this 3 Stage Plan Cyber Security Plan For Data Protection Ppt Icon Picture PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prevention, Response, Remediation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
6 Stage Yearly Business Planning Cycle For Cyber Security Project Icons PDF
This slide signifies the six step yearly planning life cycle for cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor.Persuade your audience using this 6 Stage Yearly Business Planning Cycle For Cyber Security Project Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Money Laundering, System Malfunction, Financial Transaction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps For Successful Business Diversification Market Expansion Through Formats Pdf
This slide showcases process that can help organization to formulate business diversification strategy. Its key steps are establish supportive corporate centre, select capable division managers, performance measures, secure competitive advantage, align corporate culture and set incentives. The Steps For Successful Business Diversification Market Expansion Through Formats Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases process that can help organization to formulate business diversification strategy. Its key steps are establish supportive corporate centre, select capable division managers, performance measures, secure competitive advantage, align corporate culture and set incentives.

Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112
We present our Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Emphasise on any critical or key factors within them. Use our Technology PowerPoint Templates because,And watch them strenthen your companys sinews. Use our Business PowerPoint Templates because,Show them how you can save the day. Use our Internet PowerPoint Templates because, Set out the goals and your plan of action for them. Use our Security PowerPoint Templates because, Clarity of thought has been the key to your growth.Use these PowerPoint slides for presentations relating to Safety first concept, computer, technology, business, internet, security . The prominent colors used in the PowerPoint template are Red, White, Black Index your ascent with our Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112. Illustrate every step of the way.
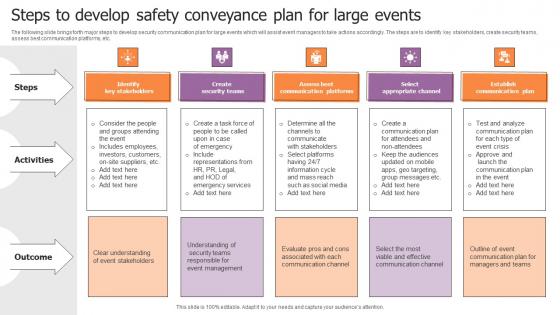
Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf
The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc. Showcasing this set of slides titled Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf. The topics addressed in these templates are Identify Key Stakeholders, Create Security Teams, Select Appropriate Channel. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc.
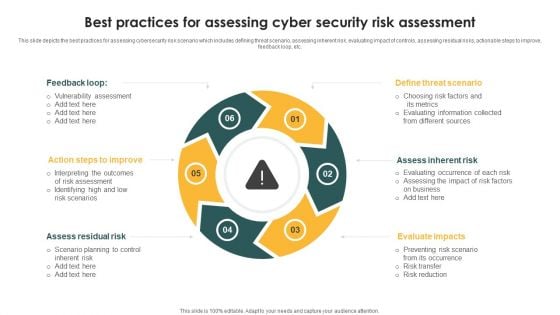
Best Practices For Assessing Cyber Security Risk Assessment Ppt PowerPoint Presentation File Graphics Template PDF
This slide depicts the best practices for assessing cybersecurity risk scenario which includes defining threat scenario, assessing inherent risk, evaluating impact of controls, assessing residual risks, actionable steps to improve, Presenting Best Practices For Assessing Cyber Security Risk Assessment Ppt PowerPoint Presentation File Graphics Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Feedback Loop, Assess Residual Risk, Evaluate Impacts, Assess Inherent Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
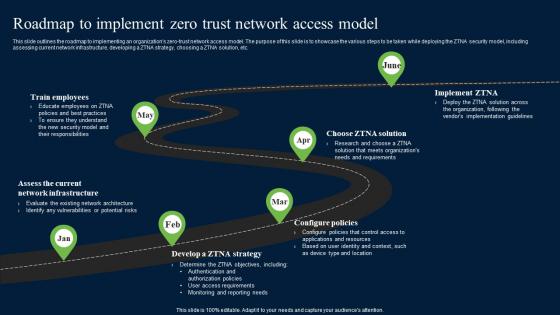
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.
Five Key Steps For Business Analysis Powerpoint Template
This PowerPoint template has been designed with five icons around key. This PowerPoint template helps to exhibit directions for strategic planning. Use this diagram slide to build an exclusive presentation.
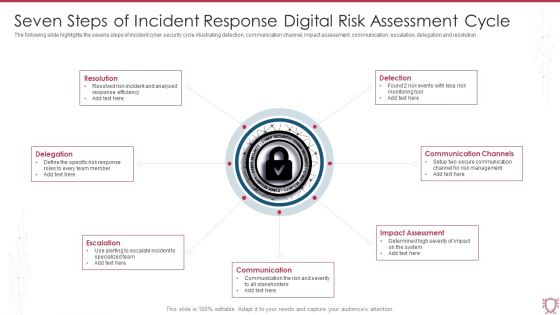
Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Golden Key With Coins Security Finance PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Golden Key With Coins Security Finance PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Finance PowerPoint Templates because you can Bullet-point your thoughts and ideas to profitably accomplish every step of every stage along the way. Present our Security PowerPoint Templates because clear thnking is your strength, transmit your thoughts to your eager team. Use our Money PowerPoint Templates because if making a mark is your obsession, then let others get Obsessed with you. Download and present our Success PowerPoint Templates because you can expound on how you plan to gain their confidence and assure them of continued and consistent excellence in quality of service. Download and present our Future PowerPoint Templates because you require care and diligence to function well.Use these PowerPoint slides for presentations relating to Keys to financial success, finance, security, money, success, future. The prominent colors used in the PowerPoint template are Yellow, Brown, Black. Professionals tell us our Golden Key With Coins Security Finance PowerPoint Templates PPT Backgrounds For Slides 1212 are Energetic. Use our future PowerPoint templates and PPT Slides will save the presenter time. We assure you our Golden Key With Coins Security Finance PowerPoint Templates PPT Backgrounds For Slides 1212 are Majestic. We assure you our security PowerPoint templates and PPT Slides are Luxuriant. Presenters tell us our Golden Key With Coins Security Finance PowerPoint Templates PPT Backgrounds For Slides 1212 are visually appealing. PowerPoint presentation experts tell us our financial PowerPoint templates and PPT Slides are Bright. Fill out your thoughts with our Golden Key With Coins Security Finance PowerPoint Templates Ppt Backgrounds For Slides 1212. They will get bigger and better.

Operational Process Improvement Plan Steps In Detail Process Analysis Brochure PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Analysis. Presenting operational process improvement plan steps in detail process analysis brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like analysis, analysis process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
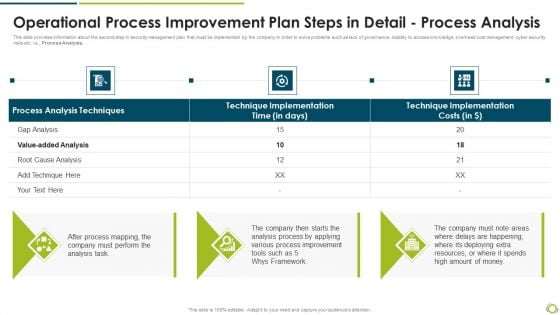
Operational Process Improvement Plan Steps In Detail Process Analysis Formats PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. Presenting operational process improvement plan steps in detail process analysis formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technique implementation, process analysis techniques, process improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Assigning Resources Background PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Assigning Resources. Presenting operational process improvement plan steps in detail assigning resources background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reducing communication issues, perform process visualizations, roles and responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Mapping Mockup PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping. Presenting operational process improvement plan steps in detail process mapping mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, graphic software, applications, accountability, productivity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF
The following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assessment Methodology, Risk QuestionsCyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
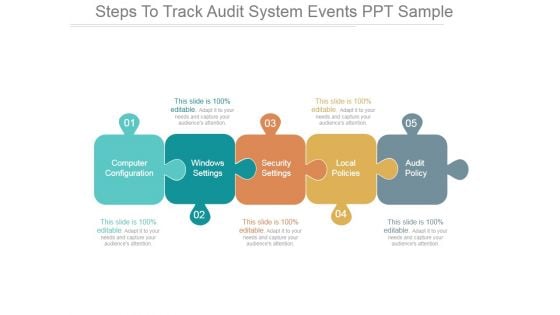
Steps To Track Audit System Events Ppt PowerPoint Presentation Summary
This is a steps to track audit system events ppt powerpoint presentation summary. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.

Steps To Create Virtual Communication And Engagement Policy Themes PDF
This slide mentions the steps to create digital communication policy for organizations. It includes establishing governance, dictating security protocol, defining channels and setting standards for responsiveness. Persuade your audience using this Steps To Create Virtual Communication And Engagement Policy Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Dictate Security Protocol, Establish Governance, Define Channels. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
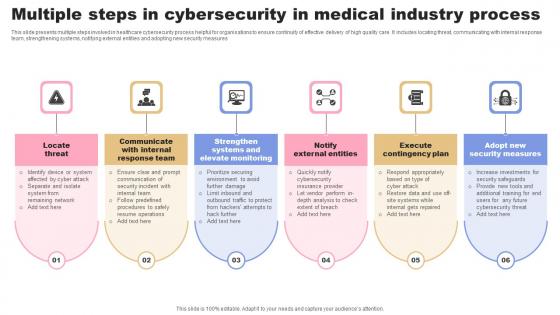
Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf
This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures Pitch your topic with ease and precision using this Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf This layout presents information on Locate Threat, Response Team, Elevate Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures

Operational Process Improvement Plan Steps In Detail Process Redesigning Slides PDF
This slide provides information about the Third and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning slides pdf. Use them to share invaluable insights on potential consequence, implementation, strategies, risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
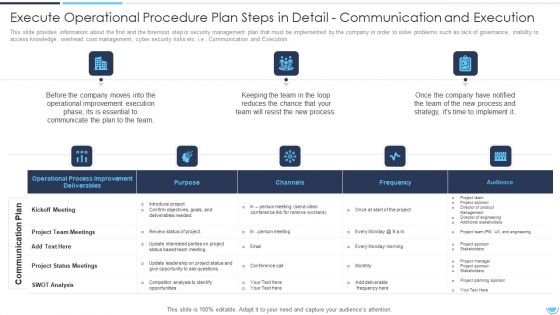
Execute Operational Procedure Plan Steps In Detail Communication And Execution Clipart PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail communication and execution clipart pdf bundle. Topics like operational process improvement deliverables, project team meetings, project status meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Execute Operational Procedure Plan Steps In Detail Process Mapping Background PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping.Deliver and pitch your topic in the best possible manner with this execute operational procedure plan steps in detail process mapping background pdf. Use them to share invaluable insights on workflow applications, process mapping, process improvement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home