System Security

Piggy Bank Secured With Padlock PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Piggy Bank Secured With Padlock PowerPoint Templates PPT Backgrounds For Slides 0313.Download and present our Finance PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Download our Money PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Present our Security PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will let your ideas bloom. Create a bed of roses for your audience. Present our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock and chain, finance, money, security, chains, marketing. The prominent colors used in the PowerPoint template are Pink, Gray, Black. Be the favourite with our Piggy Bank Secured With Padlock PowerPoint Templates Ppt Backgrounds For Slides 0313. Boost your chances of coming out on top.

Man Holding Secured Puzzle Piece Business PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Man Holding Secured Puzzle Piece Business PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Security PowerPoint Templates because you are the star of your enlightened team. Present our Puzzles or Jigsaws PowerPoint Templates because you can Refine them all as you take them through the numerous filtering stages of the funnel of your quality control process. Use our Finance PowerPoint Templates because this diagram helps you to develop your marketing strategy and communicate your enthusiasm and motivation to raise the bar. Present our Business PowerPoint Templates because the great Bald headed Eagle embodies your personality. the eagle eye to seize upon the smallest of opportunities. Present our Competition PowerPoint Templates because your marketing strategies can funnel down to the cone, stage by stage, refining as you go along.Use these PowerPoint slides for presentations relating to Holding the key to the solution, security, business, finance, puzzles or jigsaws, competition. The prominent colors used in the PowerPoint template are Red, White, Black. Professionals tell us our Man Holding Secured Puzzle Piece Business PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. Use our key PowerPoint templates and PPT Slides are Graceful. We assure you our Man Holding Secured Puzzle Piece Business PowerPoint Templates PPT Backgrounds For Slides 1212 are Glamorous. We assure you our to PowerPoint templates and PPT Slides are Second to none. Presenters tell us our Man Holding Secured Puzzle Piece Business PowerPoint Templates PPT Backgrounds For Slides 1212 are Amazing. PowerPoint presentation experts tell us our key PowerPoint templates and PPT Slides will make the presenter successul in his career/life. Our Man Holding Secured Puzzle Piece Business PowerPoint Templates Ppt Backgrounds For Slides 1212 make a delicious offering. The audience will be drooling for more.

Golden Key With Coins Secure Investment PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Golden Key With Coins Secure Investment PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Money PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Present our security PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Download and present our Business PowerPoint Templates because Your audience will believe you are the cats whiskers. Present our Signs PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience.Use these PowerPoint slides for presentations relating to Gold yen coin key, money, security, business, sign, shapes. The prominent colors used in the PowerPoint template are Black, Orange, Gray. Spice up the discourse with our Golden Key With Coins Secure Investment PowerPoint Templates Ppt Backgrounds For Slides 0213. Strengthen the flavour of your thoughts.

Secured Money Bank Future PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secured Money Bank Future PowerPoint Templates PPT Backgrounds For Slides 0313.Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Download and present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Download and present our Shapes PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Use our Business PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Download and present our Signs PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides.Use these PowerPoint slides for presentations relating to Piggy bank and keys, security, finance, shapes, business, signs. The prominent colors used in the PowerPoint template are Pink, Yellow, Black. Define the course with our Secured Money Bank Future PowerPoint Templates Ppt Backgrounds For Slides 0313. Channel them in the correct direction.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Secure Internet Browser Internet PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Use our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Present our Security PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Download our Business PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time.Use these PowerPoint slides for presentations relating to Secure Internet Browser, technology, arrows, security, business, success. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Professionals tell us our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. You can be sure our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 are topically designed to provide an attractive backdrop to any subject. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 are the best it can get when it comes to presenting. PowerPoint presentation experts tell us our Browser PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Make your audience feel exclusive with our Secure Internet Browser Internet PowerPoint Templates Ppt Backgrounds For Slides 0113. Give them special attention with your thoughts.

Always Keep Secure Your Data PowerPoint Templates Ppt Backgrounds For Slides 0513
Document the process on our Always Keep Secure Your Data PowerPoint Templates PPT Backgrounds For Slides. Make a record of every detail. Satiate desires with our Communication PowerPoint Templates. Give them all they want and more. Be the doer with our Shapes PowerPoint Templates. Put your thoughts into practice. Become a leader with our Always Keep Secure Your Data PowerPoint Templates Ppt Backgrounds For Slides 0513. You will come out on top.
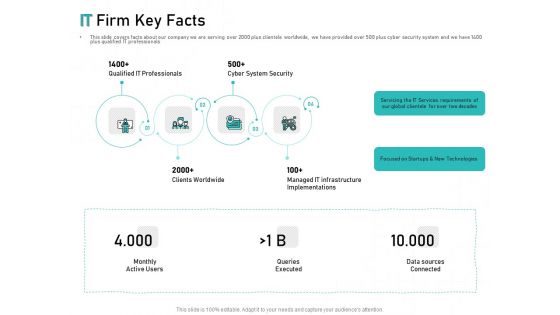
Tech Support Services Cost And Pricing IT Firm Key Facts Ppt PowerPoint Presentation Slides File Formats
Presenting this set of slides with name tech support services cost and pricing it firm key facts ppt powerpoint presentation slides file formats. This is a four stage process. The stages in this process are technologies, services, implementations, infrastructure, cyber system security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Managed Services Pricing Guide IT Firm Key Facts Ppt Infographics Visuals PDF
Presenting this set of slides with name cloud managed services pricing guide it firm key facts ppt infographics visuals pdf. The topics discussed in these slides are qualified it professionals, clients worldwide, cyber system security, managed it infrastructure implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
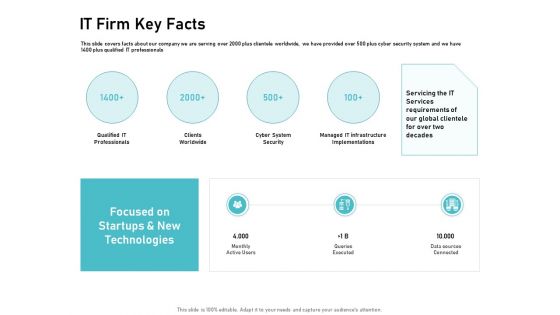
IT Support And Monitoring Services Pricing IT Firm Key Facts Ppt Portfolio Styles PDF
Presenting this set of slides with name it support and monitoring services pricing it firm key facts ppt portfolio styles pdf. The topics discussed in these slides are qualified it professionals, clients worldwide, cyber system security, managed it infrastructure implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Welfare Work Value IT Firm Key Facts Ppt Pictures Icon PDF
Presenting this set of slides with name welfare work value it firm key facts ppt pictures icon pdf. This is a four stage process. The stages in this process are clients worldwide, cyber system security, infrastructure, implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
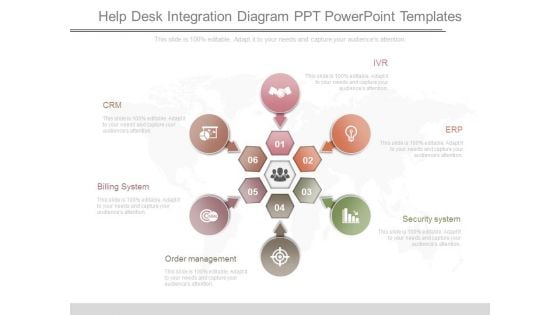
Help Desk Integration Diagram Ppt Powerpoint Templates
This is a help desk integration diagram ppt powerpoint templates. This is a six stage process. The stages in this process are crm, billing system, order management, ivr, erp, security system.

Portable Home Safety Systems Company Profile Executive Leadership And Management Team Rules PDF
This slide highlights the security company leadership and management team which includes president and CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Portable Home Safety Systems Company Profile Executive Leadership And Management Team Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Finance, Home Security, Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Secure File Locked Document Vector Icon Ppt PowerPoint Presentation Infographics Clipart PDF
Presenting this set of slides with name secure file locked document vector icon ppt powerpoint presentation infographics clipart pdf. This is a two stage process. The stages in this process are secure file locked document vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vector Showing Multi Channel For Secured Experience Ppt PowerPoint Presentation Professional Skills PDF
Presenting this set of slides with name vector showing multi channel for secured experience ppt powerpoint presentation professional skills pdf. This is a two stage process. The stages in this process are vector showing multi channel for secured experience. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc.

Secure Web Gateway Set Up Ongoing Maintenance Web Access Control Solution
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. There are so many reasons you need a Secure Web Gateway Set Up Ongoing Maintenance Web Access Control Solution. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc.
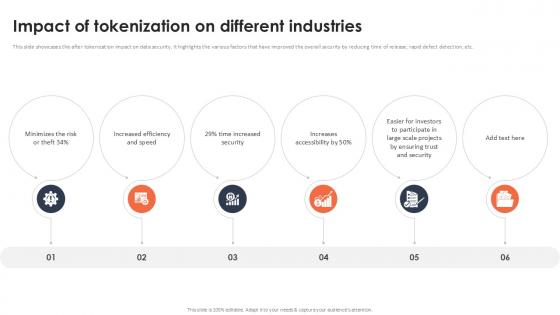
Impact Of Tokenization On Different Industries Securing Your Data Ppt Example
This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Welcome to our selection of the Impact Of Tokenization On Different Industries Securing Your Data Ppt Example These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc.
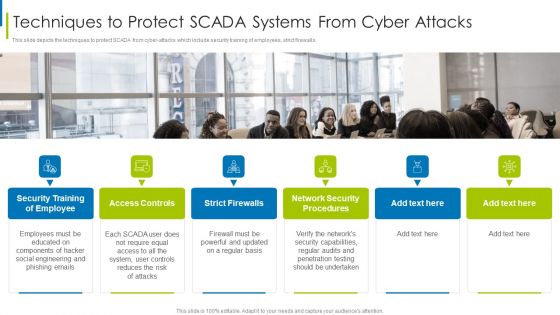
Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
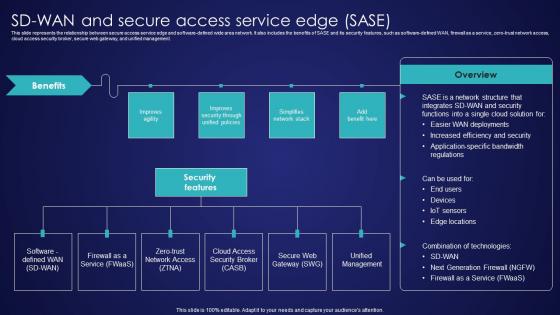
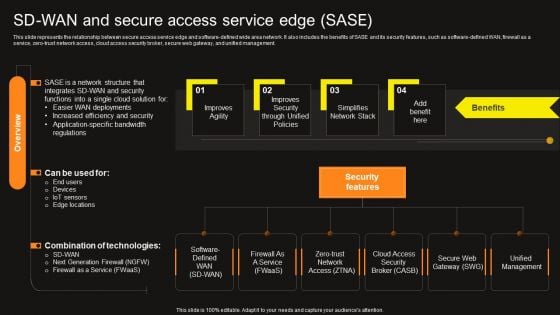
SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Welcome to our selection of the SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management.

Portable Home Safety Systems Company Profile Our Expertise Ppt Summary Graphics Example PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. This is a Portable Home Safety Systems Company Profile Our Expertise Ppt Summary Graphics Example PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Integrated Control, Voice Assistant, Internet Protocol, RFID Based. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Portable Home Safety Systems Company Profile Market Positioning With Technology Icons PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. This is a Portable Home Safety Systems Company Profile Market Positioning With Technology Icons PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Value Money, Transformative, Smart Home, Security Experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Web Access Control Solution Reasons Behind Need For Secure Web Gateway
Find a pre-designed and impeccable Web Access Control Solution Reasons Behind Need For Secure Web Gateway. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc.

Digitized Record Book Technology Is Digital Ledger Technology Secure Sample PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Presenting digitized record book technology is digital ledger technology secure sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like information, data, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
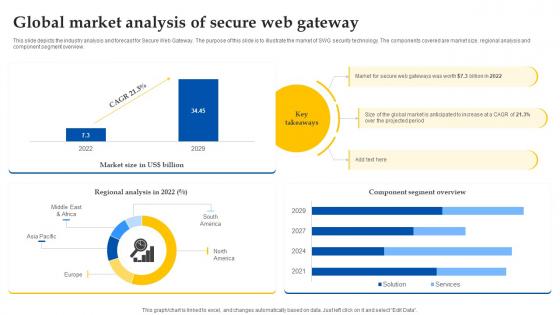
Web Access Control Solution Global Market Analysis Of Secure Web Gateway
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. This Web Access Control Solution Global Market Analysis Of Secure Web Gateway is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Web Access Control Solution Global Market Analysis Of Secure Web Gateway features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.
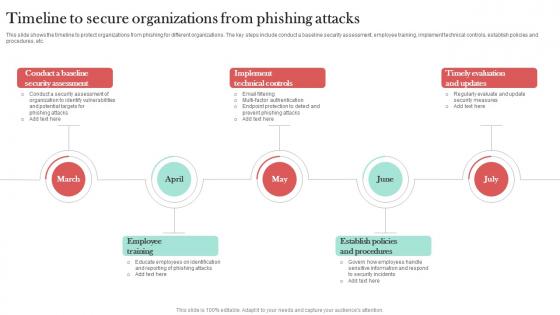
Timeline To Secure Organizations From Man In The Middle Phishing IT
This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. This Timeline To Secure Organizations From Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Timeline To Secure Organizations From Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Wireless Banking To Improve Checklist To Ensure Secure Mobile Banking Fin SS V
This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Wireless Banking To Improve Checklist To Ensure Secure Mobile Banking Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
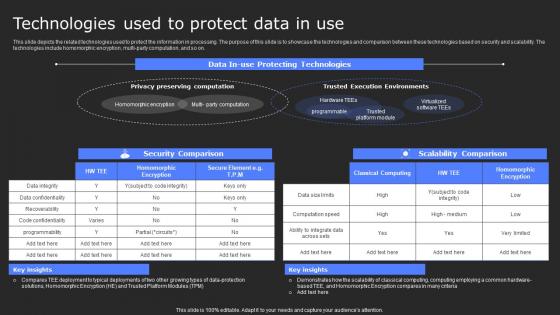
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
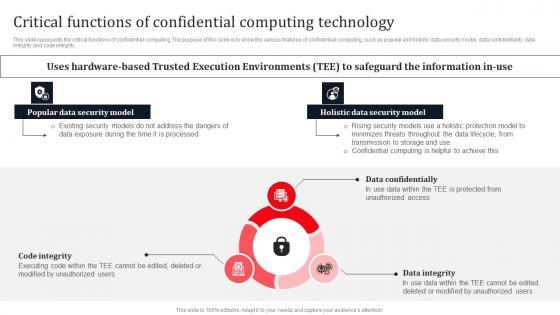
Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
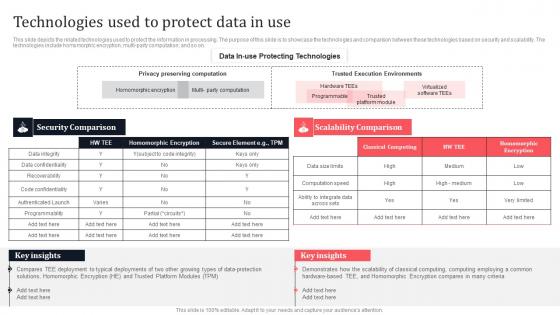
Technologies Used To Protect Data In Use Secure Multi Party Template Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Technologies Used To Protect Data In Use Secure Multi Party Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Technologies Used To Protect Data In Use Secure Multi Party Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

Web Access Control Solution Key Benefits Of Using Secure Web Gateway
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Slidegeeks has constructed Web Access Control Solution Key Benefits Of Using Secure Web Gateway after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc.

Comparison Between Secure Web Gateway And Firewalls Web Access Control Solution
This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Web Access Control Solution Comparison Between Secure Web Gateway And Firewalls and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Web Access Control Solution Comparison Between Secure Web Gateway And Firewalls and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
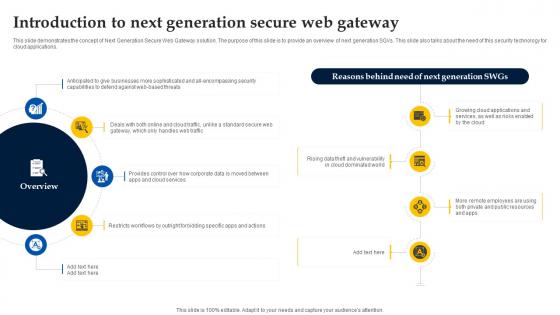
Web Access Control Solution Introduction To Next Generation Secure Web Gateway
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Are you searching for a Web Access Control Solution Introduction To Next Generation Secure Web Gateway that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Web Access Control Solution Introduction To Next Generation Secure Web Gateway from Slidegeeks today. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.
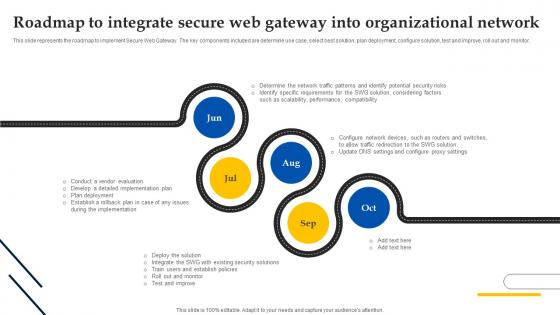
Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network
This slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Create an editable Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.
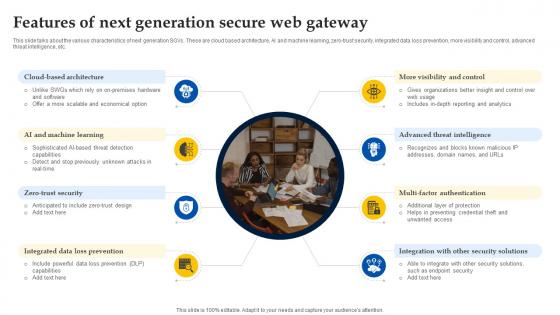
Web Access Control Solution Features Of Next Generation Secure Web Gateway
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Access Control Solution Features Of Next Generation Secure Web Gateway to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.
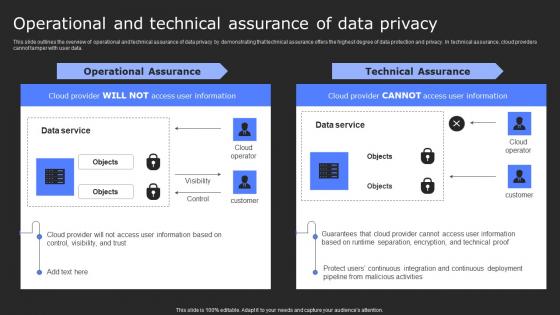
Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Get a simple yet stunning designed Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.

Web Access Control Solution Before Vs After Implementing Secure Web Gateway
This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Web Access Control Solution Before Vs After Implementing Secure Web Gateway. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Web Access Control Solution Before Vs After Implementing Secure Web Gateway today and make your presentation stand out from the rest This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc.

Our Strategies To Secure Network Load Balancer Ppt Outline Topics PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. Presenting our strategies to secure network load balancer ppt outline topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like our strategies to secure network load balancer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF today and make your presentation stand out from the rest.

Web Access Control Solution Applications Of Secure Web Gateway In Various Industries
This slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc. Present like a pro with Web Access Control Solution Applications Of Secure Web Gateway In Various Industries. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc.
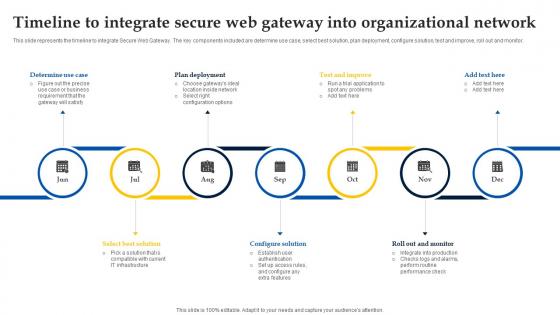
Web Access Control Solution Timeline To Integrate Secure Web Gateway Into Organizational Network
This slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Web Access Control Solution Timeline To Integrate Secure Web Gateway Into Organizational Network and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.
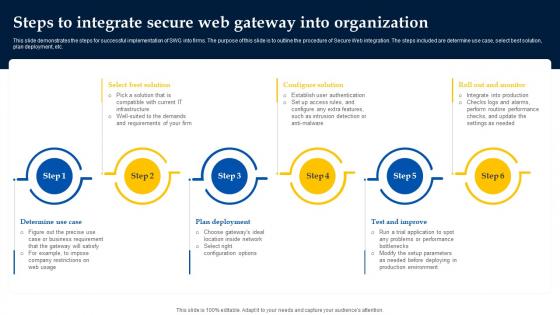
Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization today and make your presentation stand out from the rest This slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc.

Web Access Control Solution Different Types Of Secure Web Gateway Deployment
This slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Make sure to capture your audiences attention in your business displays with our gratis customizable Web Access Control Solution Different Types Of Secure Web Gateway Deployment. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment.

Web Access Control Solution Best Practices For Secure Web Gateway Implementation
This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Best Practices For Secure Web Gateway Implementation can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Best Practices For Secure Web Gateway Implementation and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc.
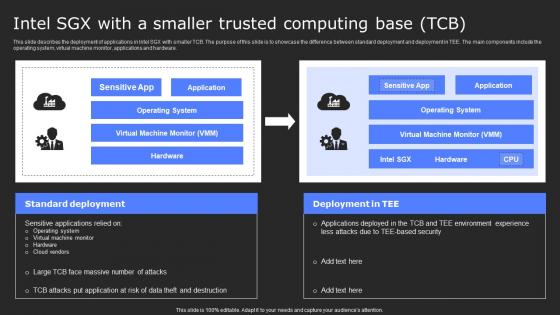
Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Find a pre-designed and impeccable Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
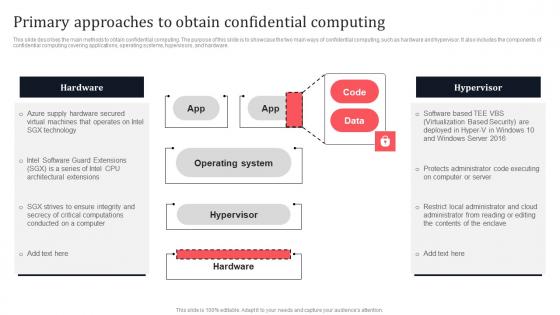
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.

Web Access Control Solution Secure Web Gateway Set Up Planning And Preparation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Present like a pro with Web Access Control Solution Secure Web Gateway Set Up Planning And Preparation. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc.
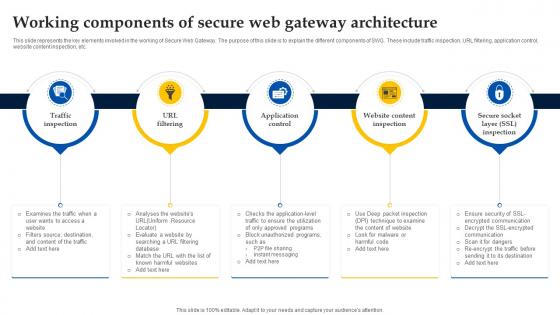
Web Access Control Solution Working Components Of Secure Web Gateway Architecture
This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Web Access Control Solution Working Components Of Secure Web Gateway Architecture and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc.
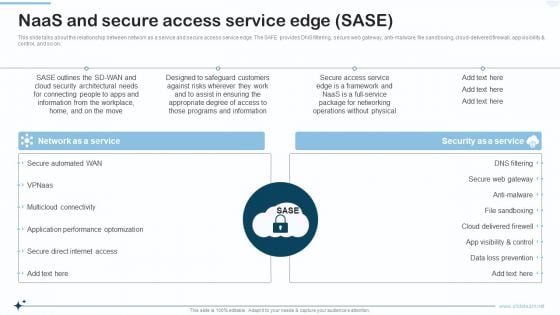
Naas Integrated Solution IT Naas And Secure Access Service Edge SASE Designs PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti malware, file sandboxing, cloud delivered firewall, app visibility and control, and so on. Presenting Naas Integrated Solution IT Naas And Secure Access Service Edge SASE Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Network As A Service, Security As A Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
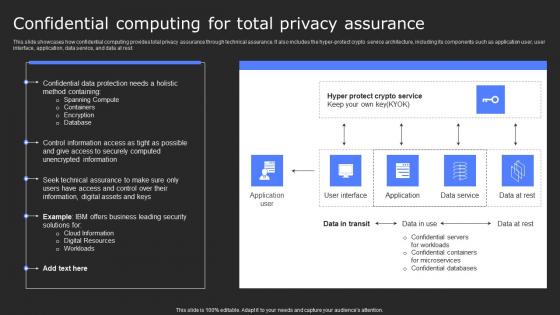
Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
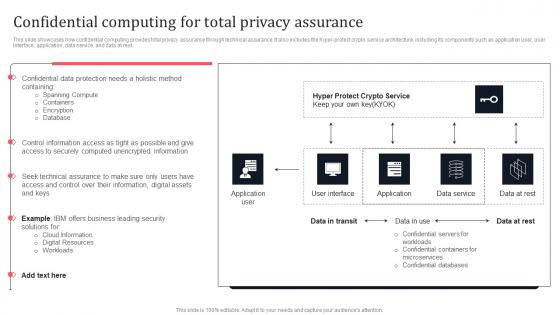
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
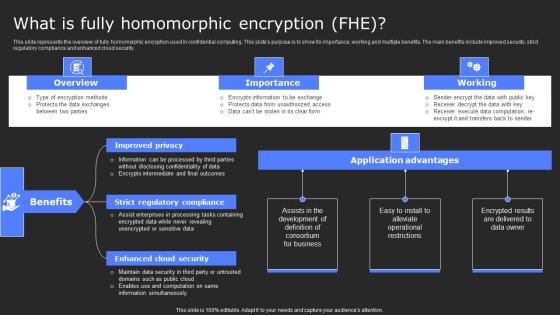
What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.
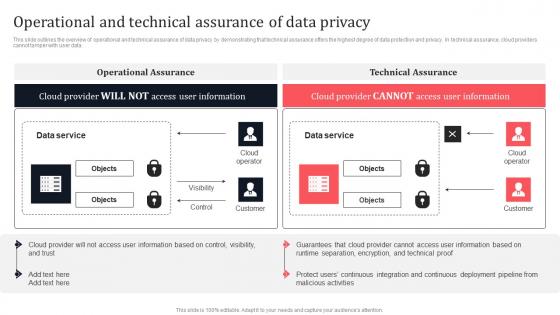
Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. There are so many reasons you need a Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.
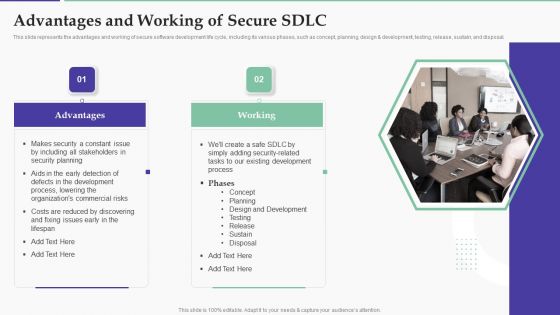
Solution Development Process Advantages And Working Of Secure SDLC Structure PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design development, testing, release, sustain, and disposal.Presenting Solution Development Process Advantages And Working Of Secure SDLC Structure PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Including Stakeholders, Security Planning, Process, Lowering Commercial. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solution Development Process Overview And Importance Of Secure SDLC Demonstration PDF
This slide depicts the overview and importance of a secure software development life cycle, including how it helps to reduce total software development time and cost.Presenting Solution Development Process Overview And Importance Of Secure SDLC Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Security Components, Software Development, Vulnerabilities Detected. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
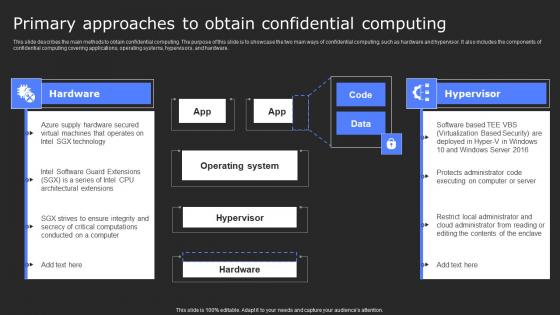
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
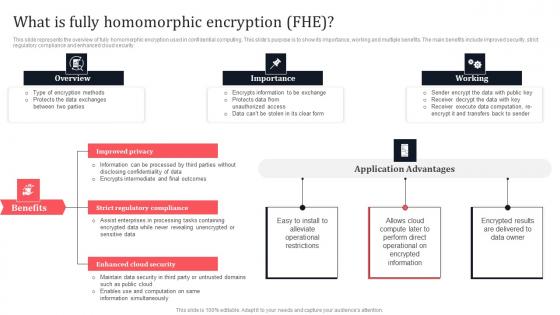
What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Make sure to capture your audiences attention in your business displays with our gratis customizable What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.
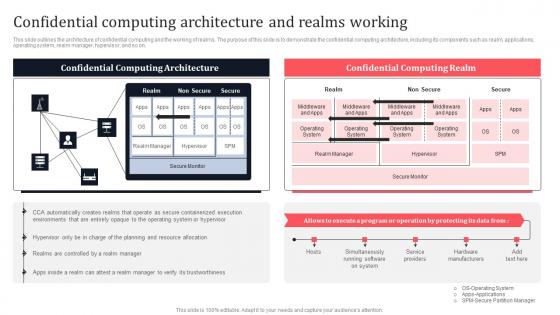
Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Slidegeeks is here to make your presentations a breeze with Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
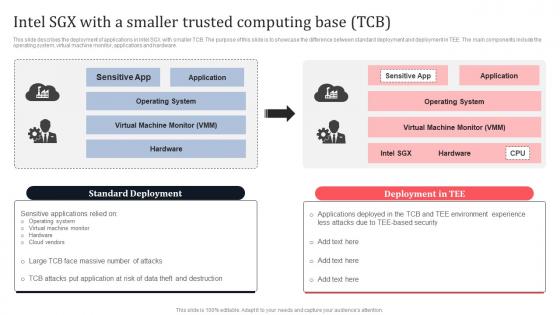
Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Take your projects to the next level with our ultimate collection of Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.

Web Access Control Solution Secure Web Gateway For Remote And Onsite Workers
This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. There are so many reasons you need a Web Access Control Solution Secure Web Gateway For Remote And Onsite Workers. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees.


 Continue with Email
Continue with Email

 Home
Home


































