System Security
Major Digital Transformation Digital Approaches To Increase Business Growth Formats Pdf
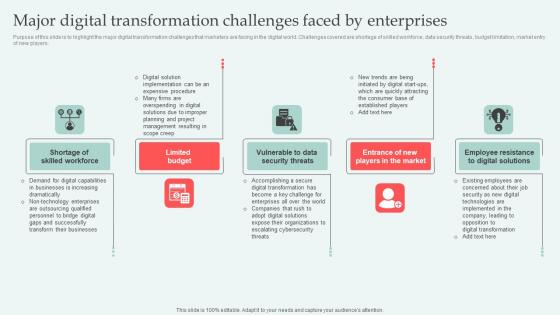
Purpose of this slide is to highlight the major digital transformation challenges that marketers are facing in the digital world. Challenges covered are shortage of skilled workforce, data security threats, budget limitation, market entry of new players. If you are looking for a format to display your unique thoughts, then the professionally designed Major Digital Transformation Digital Approaches To Increase Business Growth Formats Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Digital Transformation Digital Approaches To Increase Business Growth Formats Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Purpose of this slide is to highlight the major digital transformation challenges that marketers are facing in the digital world. Challenges covered are shortage of skilled workforce, data security threats, budget limitation, market entry of new players.
Deploying An Efficient Organizational Elderly Care Business Plan Go To Market Strategy Background Pdf
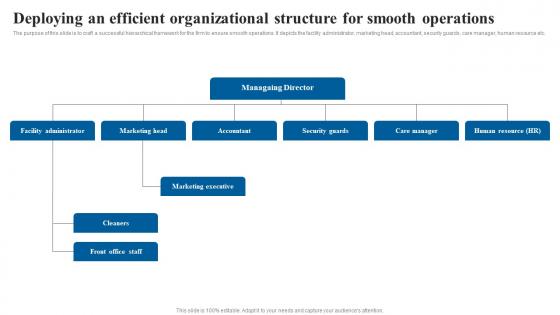
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying An Efficient Organizational Elderly Care Business Plan Go To Market Strategy Background Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying An Efficient Organizational Elderly Care Business Plan Go To Market Strategy Background Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc.

Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V
Following slide showcases issues faced by educational institutions during implementation of intent of things IoT technologies. It includes challenges such as high cost infrastructure, security challenges and complexity. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V. Following slide showcases issues faced by educational institutions during implementation of intent of things IoT technologies. It includes challenges such as high cost infrastructure, security challenges and complexity.

Major Focus Of White Box Testing Gray Box Testing Best Practices
This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Focus Of White Box Testing Gray Box Testing Best Practices and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on.
Various Inflation Indexing Instruments To Maintain Real Value Strategies For Inflation A Tactical Guide Fin SS V
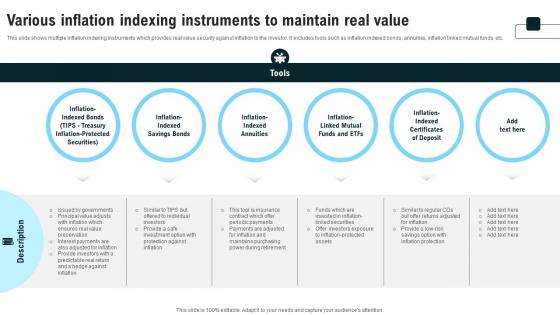
This slide shows multiple inflation indexing instruments which provides real value security against inflation to the investor. It includes tools such as inflation indexed bonds, annuities, inflation linked mutual funds, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Various Inflation Indexing Instruments To Maintain Real Value Strategies For Inflation A Tactical Guide Fin SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide shows multiple inflation indexing instruments which provides real value security against inflation to the investor. It includes tools such as inflation indexed bonds, annuities, inflation linked mutual funds, etc.
Mastering Blockchain Wallets Defining Software Wallets With Key Benefits BCT SS V
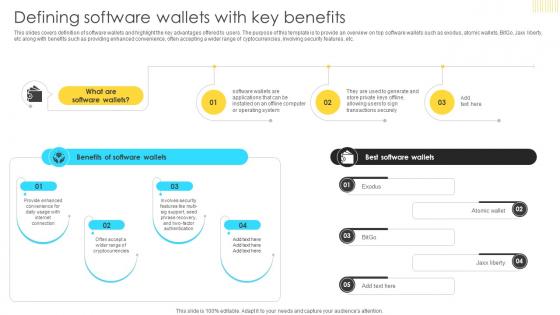
This slides covers definition of software wallets and highlight the key advantages offered to users. The purpose of this template is to provide an overview on top software wallets such as exodus, atomic wallets, BitGo, Jaxx liberty, etc along with benefits such as providing enhanced convenience, often accepting a wider range of cyptocurrencies, involving security features, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Mastering Blockchain Wallets Defining Software Wallets With Key Benefits BCT SS V from Slidegeeks and deliver a wonderful presentation. This slides covers definition of software wallets and highlight the key advantages offered to users. The purpose of this template is to provide an overview on top software wallets such as exodus, atomic wallets, BitGo, Jaxx liberty, etc along with benefits such as providing enhanced convenience, often accepting a wider range of cyptocurrencies, involving security features, etc.
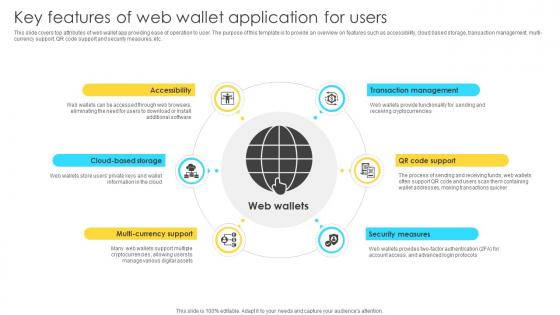
Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V
This slide covers top attributes of web wallet app providing ease of operation to user. The purpose of this template is to provide an overview on features such as accessibility, cloud based storage, transaction management, multi-currency support, QR code support and security measures, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers top attributes of web wallet app providing ease of operation to user. The purpose of this template is to provide an overview on features such as accessibility, cloud based storage, transaction management, multi-currency support, QR code support and security measures, etc.
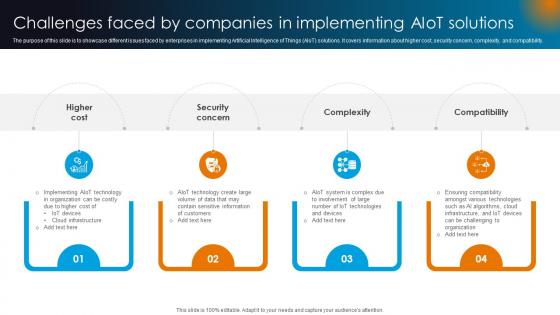
Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V
The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility.

Problems With Dark Data Accumulation Importance Of Unstructured Data Ppt Sample
This slide track the problems that are caused by dark data. The purpose of this slide is to explain how dark data can cause storage issues, hide valuable information, security issues, etc.Presenting this PowerPoint presentation, titled Problems With Dark Data Accumulation Importance Of Unstructured Data Ppt Sample, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Problems With Dark Data Accumulation Importance Of Unstructured Data Ppt Sample. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Problems With Dark Data Accumulation Importance Of Unstructured Data Ppt Sample that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide track the problems that are caused by dark data. The purpose of this slide is to explain how dark data can cause storage issues, hide valuable information, security issues, etc.
5g Transport Network Silicon Photonics SiPh It Ppt Example
This slide represents the relationship between 5g transport network architecture and the photonics system. The purpose of this slide is to showcase the transformation of transform network architecture through three stages such as traditional RBS, main remote system and centralized RAN.Find a pre-designed and impeccable 5g Transport Network Silicon Photonics SiPh It Ppt Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents the relationship between 5g transport network architecture and the photonics system. The purpose of this slide is to showcase the transformation of transform network architecture through three stages such as traditional RBS, main remote system and centralized RAN.
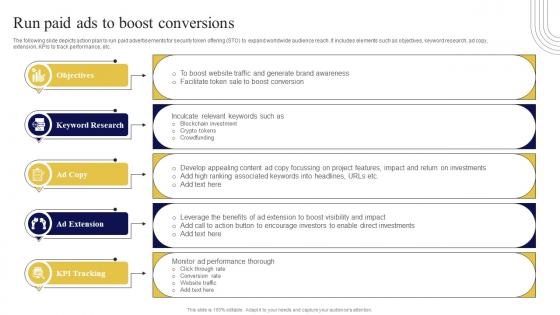
Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf
The following slide depicts action plan to run paid advertisements for security token offering STO to expand worldwide audience reach. It includes elements such as objectives, keyword research, ad copy, extension, KPIs to track performance, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts action plan to run paid advertisements for security token offering STO to expand worldwide audience reach. It includes elements such as objectives, keyword research, ad copy, extension, KPIs to track performance, etc.
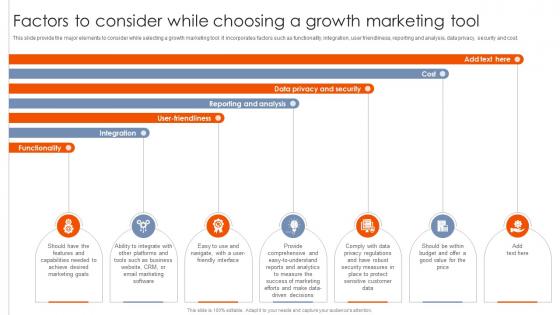
Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V
This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost.
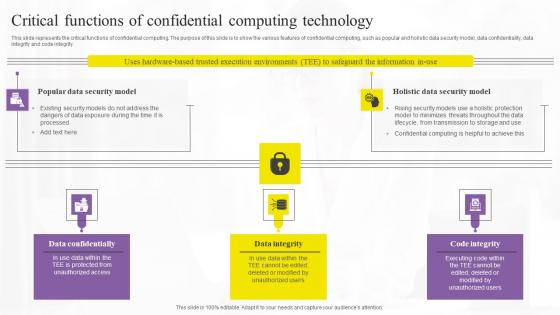
Critical Functions Of Confidential Computing Technology Demonstration Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Presenting this PowerPoint presentation, titled Critical Functions Of Confidential Computing Technology Demonstration Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Critical Functions Of Confidential Computing Technology Demonstration Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Critical Functions Of Confidential Computing Technology Demonstration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
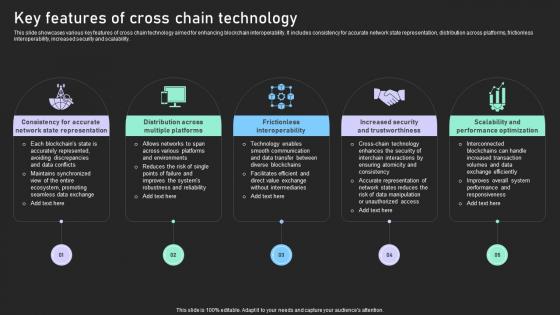
Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.

How Is Open Ran Important To 5G Revolutionizing Mobile Networks Graphics PDF
This slide depicts the importance of an open random access network to a 5G telecommunication system. It will help the 5G system widen the range and cut the CapEx of telecoms. Present like a pro with How Is Open Ran Important To 5G Revolutionizing Mobile Networks Graphics PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the importance of an open random access network to a 5G telecommunication system. It will help the 5G system widen the range and cut the CapEx of telecoms.
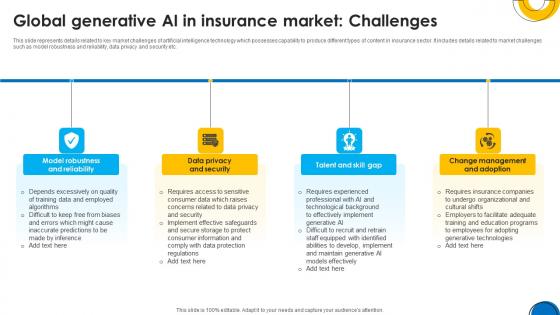
Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V
This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc.

Solutions Tackle Key Challenges Business Integration Tactics To Eliminate Competitors Elements Pdf
This slide showcases key challenges faced by organization during merger and acquisition process that are employee retention, security threats, unexpected costs and wrong valuation. It also highlights solutions to tackle these hindrances during implementing of strategy Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Solutions Tackle Key Challenges Business Integration Tactics To Eliminate Competitors Elements Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Solutions Tackle Key Challenges Business Integration Tactics To Eliminate Competitors Elements Pdf today and make your presentation stand out from the rest This slide showcases key challenges faced by organization during merger and acquisition process that are employee retention, security threats, unexpected costs and wrong valuation. It also highlights solutions to tackle these hindrances during implementing of strategy
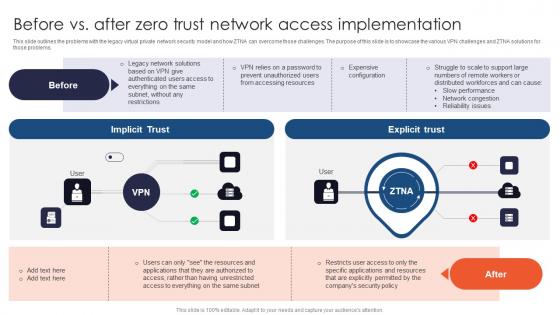
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
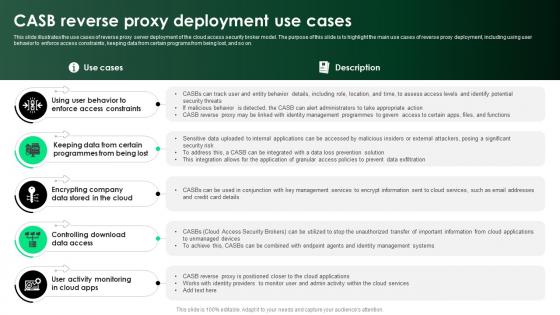
CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases
This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on.

Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Find highly impressive Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.

Mastering Blockchain Wallets Challenges With Solutions For Improving Efficiency BCT SS V
This slide covers issues highlighting common challenges associated with software wallets. The purpose of this template is to potential solutions to enhance their efficiency for risks such as security risks, user error and loss, compatibility issues along with description and solutions. Find highly impressive Mastering Blockchain Wallets Challenges With Solutions For Improving Efficiency BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Mastering Blockchain Wallets Challenges With Solutions For Improving Efficiency BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide covers issues highlighting common challenges associated with software wallets. The purpose of this template is to potential solutions to enhance their efficiency for risks such as security risks, user error and loss, compatibility issues along with description and solutions.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
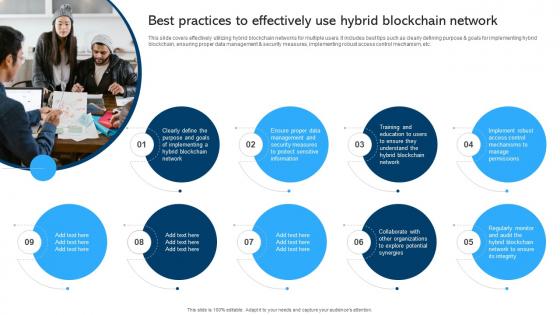
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc.

Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.
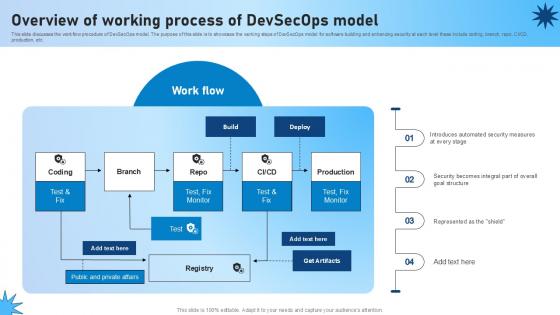
Overview Of Working Process Of Devsecops Model Role Of Devsecops Ppt Sample
This slide discusses the workflow procedure of DevSecOps model. The purpose of this slide is to showcase the working steps of DevSecOps model for software building and enhancing security at each level these include coding, branch, repo, CI CD, production, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Overview Of Working Process Of Devsecops Model Role Of Devsecops Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide discusses the workflow procedure of DevSecOps model. The purpose of this slide is to showcase the working steps of DevSecOps model for software building and enhancing security at each level these include coding, branch, repo, CI CD, production, etc.
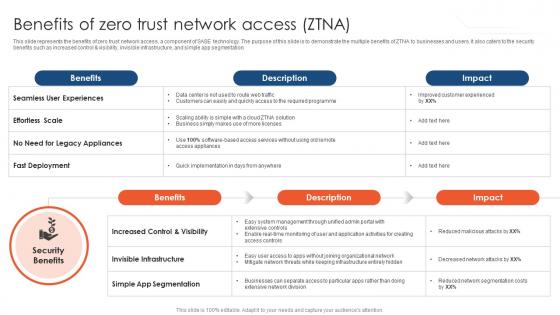
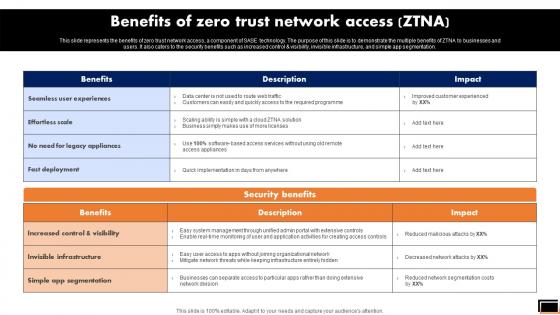
Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Zero Trust Model Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Steps To Implement Zero Trust Network Access Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc.

Zero Trust Model Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Get a simple yet stunning designed Zero Trust Model Step 3 Assess The Environment. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Step 3 Assess The Environment can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

IoT Device Management Fundamentals IoT Device Update Management Process IoT Ss V
This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback. Find highly impressive IoT Device Management Fundamentals IoT Device Update Management Process IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IoT Device Management Fundamentals IoT Device Update Management Process IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback.

Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V
This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc. Get a simple yet stunning designed Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc.
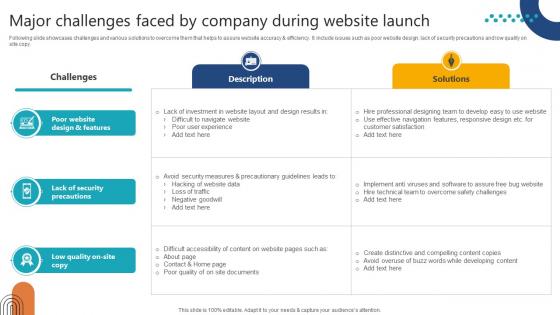
Complete Guide To Launch Major Challenges Faced By Company During Website
Following slide showcases challenges and various solutions to overcome them that helps to assure website accuracy and efficiency. It include issues such as poor website design, lack of security precautions and low quality on site copy. Explore a selection of the finest Complete Guide To Launch Major Challenges Faced By Company During Website here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Complete Guide To Launch Major Challenges Faced By Company During Website to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Following slide showcases challenges and various solutions to overcome them that helps to assure website accuracy and efficiency. It include issues such as poor website design, lack of security precautions and low quality on site copy.

CASB 2 0 IT CASB Deployment With Optional Components Pricing
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT CASB Deployment With Optional Components Pricing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT CASB Deployment With Optional Components Pricing today and make your presentation stand out from the rest This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on.
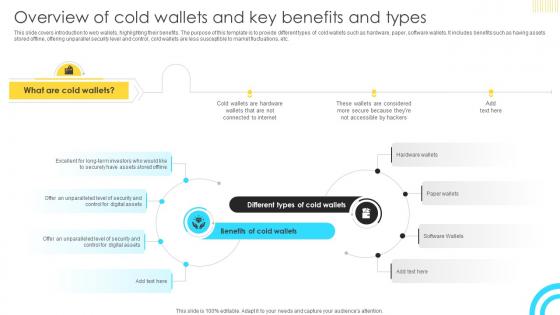
Mastering Blockchain Wallets Overview Of Cold Wallets And Key Benefits BCT SS V
This slide covers introduction to web wallets, highlighting their benefits. The purpose of this template is to provide different types of cold wallets such as hardware, paper, software wallets. It includes benefits such as having assets stored offline, offering unparallel security level and control, cold wallets are less susceptible to market fluctuations, etc. Slidegeeks is here to make your presentations a breeze with Mastering Blockchain Wallets Overview Of Cold Wallets And Key Benefits BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers introduction to web wallets, highlighting their benefits. The purpose of this template is to provide different types of cold wallets such as hardware, paper, software wallets. It includes benefits such as having assets stored offline, offering unparallel security level and control, cold wallets are less susceptible to market fluctuations, etc.
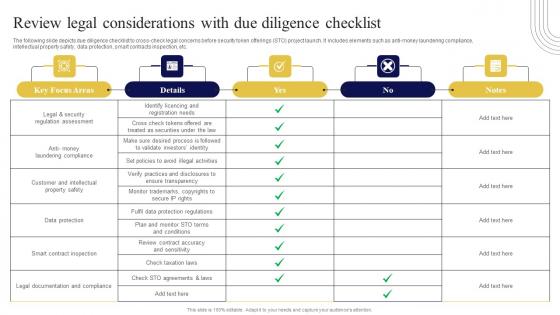
Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf
The following slide depicts due diligence checklist to cross-check legal concerns before security token offerings STO project launch. It includes elements such as anti-money laundering compliance, intellectual property safety, data protection, smart contracts inspection, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf today and make your presentation stand out from the rest The following slide depicts due diligence checklist to cross-check legal concerns before security token offerings STO project launch. It includes elements such as anti-money laundering compliance, intellectual property safety, data protection, smart contracts inspection, etc.
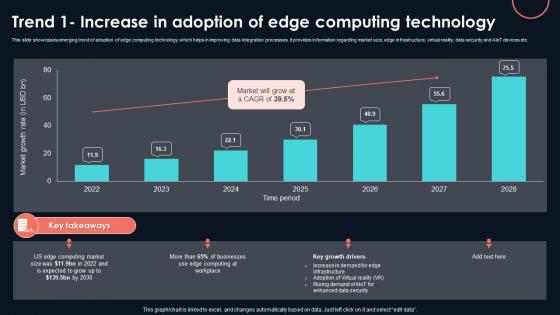
Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V. This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc.
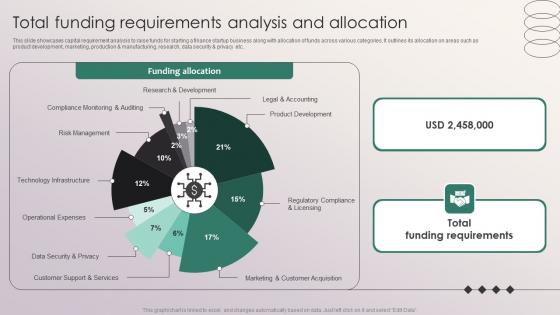
Total Funding Requirements Analysis And Allocation Penetrating Markets With Financial Strategy SS V
This slide showcases capital requirement analysis to raise funds for starting a finance startup business along with allocation of funds across various categories. It outlines its allocation on areas such as product development, marketing, production and manufacturing, research, data security and privacy etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Total Funding Requirements Analysis And Allocation Penetrating Markets With Financial Strategy SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases capital requirement analysis to raise funds for starting a finance startup business along with allocation of funds across various categories. It outlines its allocation on areas such as product development, marketing, production and manufacturing, research, data security and privacy etc.

Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
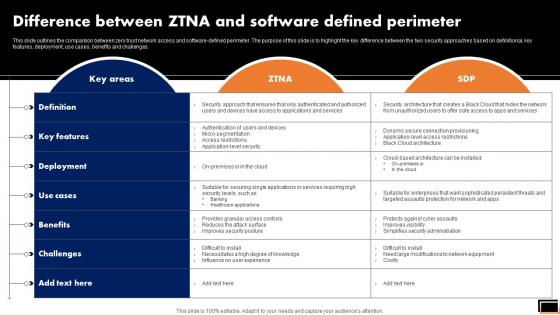
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
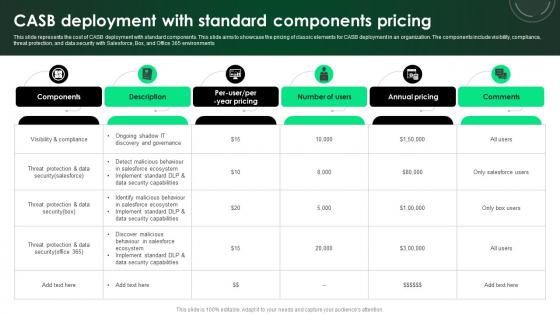
CASB 2 0 IT CASB Deployment With Standard Components Pricing
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT CASB Deployment With Standard Components Pricing can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT CASB Deployment With Standard Components Pricing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments
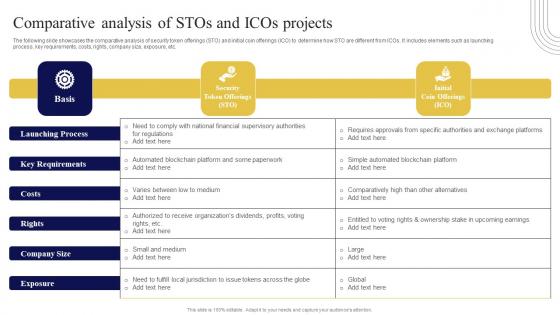
Comparative Analysis Of Stos And Icos Exploring Investment Opportunities Download Pdf
The following slide showcases the comparative analysis of security token offerings STO and initial coin offerings ICO to determine how STO are different from ICOs. It includes elements such as launching process, key requirements, costs, rights, company size, exposure, etc. Slidegeeks is here to make your presentations a breeze with Comparative Analysis Of Stos And Icos Exploring Investment Opportunities Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide showcases the comparative analysis of security token offerings STO and initial coin offerings ICO to determine how STO are different from ICOs. It includes elements such as launching process, key requirements, costs, rights, company size, exposure, etc.
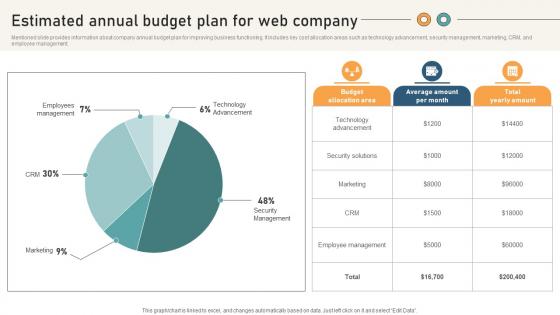
Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company. Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management.

Data Breach Awareness Training Program Data Breach Prevention Professional Pdf
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Find highly impressive Data Breach Awareness Training Program Data Breach Prevention Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Breach Prevention Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment
This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc.

Data Breach Awareness Training Program Data Fortification Strengthening Defenses
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.Find highly impressive Data Breach Awareness Training Program Data Fortification Strengthening Defenses on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Fortification Strengthening Defenses for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

IoT Device Management Fundamentals IoT Device Monitoring Dashboard To Analyse IoT Ss V
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. Slidegeeks is here to make your presentations a breeze with IoT Device Management Fundamentals IoT Device Monitoring Dashboard To Analyse IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc.
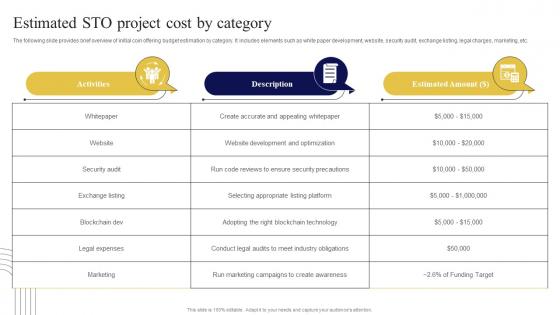
Estimated STO Project Cost By Category Exploring Investment Opportunities Designs Pdf
The following slide provides brief overview of initial coin offering budget estimation by category. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Estimated STO Project Cost By Category Exploring Investment Opportunities Designs Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Estimated Sto Project Cost By Category Exploring Investment Opportunities Designs Pdf The following slide provides brief overview of initial coin offering budget estimation by category. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc.
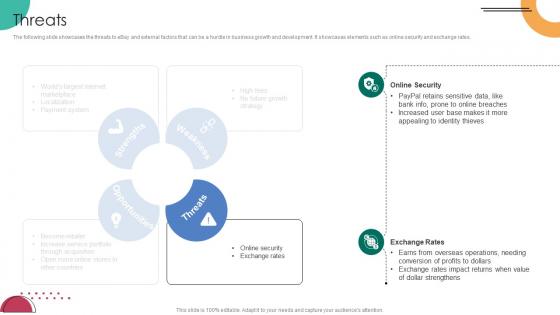
Threats C2C Ecommerce Platform Company Profile CP SS V
The following slide showcases the threats to eBay and external factors that can be a hurdle in business growth and development. It showcases elements such as online security and exchange rates.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Threats C2C Ecommerce Platform Company Profile CP SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Threats C2C Ecommerce Platform Company Profile CP SS V. The following slide showcases the threats to eBay and external factors that can be a hurdle in business growth and development. It showcases elements such as online security and exchange rates.

Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf today and make your presentation stand out from the rest. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.

Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V
This slide provides an overview of the blockchain technology used for remote monotiling. It also includes the benefits that are it allows device communication, enhance security and provides authorization access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V today and make your presentation stand out from the rest This slide provides an overview of the blockchain technology used for remote monotiling. It also includes the benefits that are it allows device communication, enhance security and provides authorization access.
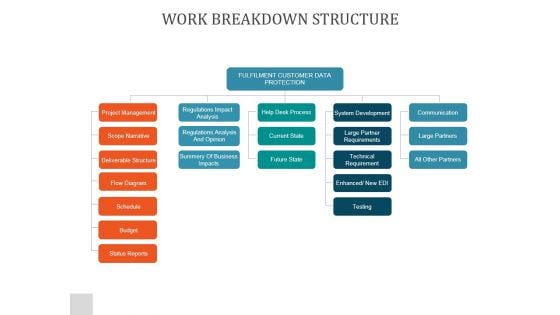
Work Breakdown Structure Ppt PowerPoint Presentation Infographics
This is a work breakdown structure ppt powerpoint presentation infographics. This is a five stage process. The stages in this process are fulfilment customer data protection, project management, regulations impact analysis, help desk process, system development, communication, scope narrative.

Facilitate Payments And Remittances Ppt Slides
This is a facilitate payments and remittances ppt slides. This is a five stage process. The stages in this process are governance and risk management, market structure and competition, legal and regulatory framework, payment system infrastructure, transparency and consumer protection.
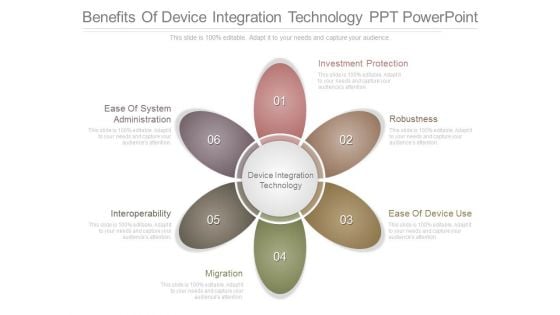
Benefits Of Device Integration Technology Ppt Powerpoint
This is a benefits of device integration technology ppt powerpoint. This is a six stage process. The stages in this process are investment protection, robustness, ease of device use, migration, interoperability, ease of system administration.

Structure And Services Framework Ppt Images
This is a structure and services framework ppt images. This is a five stage process. The stages in this process are structure and services framework, best service strategy, system lock in, total solution, increasing customer bonding.


 Continue with Email
Continue with Email

 Home
Home


































