Technology Security

Key Resources Security Service Provider Business Model BMC SS V
This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources. Slidegeeks is here to make your presentations a breeze with Key Resources Security Service Provider Business Model BMC SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources.
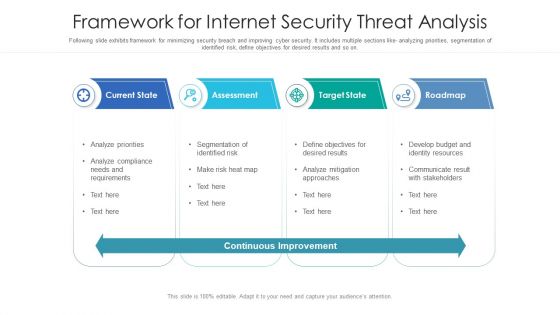
Framework For Internet Security Threat Analysis Structure PDF
Following slide exhibits framework for minimizing security breach and improving cyber security. It includes multiple sections like- analyzing priorities, segmentation of identified risk, define objectives for desired results and so on. Showcasing this set of slides titled framework for internet security threat analysis structure pdf. The topics addressed in these templates are current state, assessment, target state, roadmap. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Manpower Corporate Security Business Profile Swot Analysis Introduction PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Manpower Corporate Security Business Profile Swot Analysis Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weaknesses, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
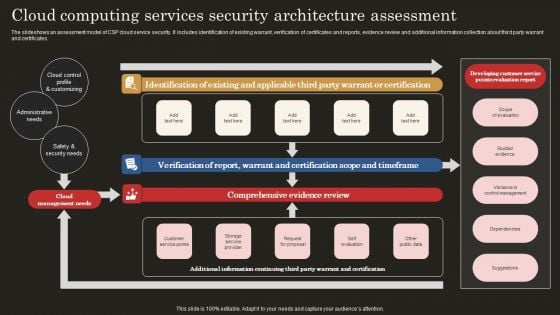
Cloud Computing Services Security Architecture Assessment Infographics PDF
The slideshows an assessment model of CSP cloud service security. It includes identification of existing warrant, verification of certificates and reports, evidence review and additional information collection about third party warrant and certificates. Showcasing this set of slides titled Cloud Computing Services Security Architecture Assessment Infographics PDF. The topics addressed in these templates are Cloud Control Profile, Administrative Need, Safety Security Needs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
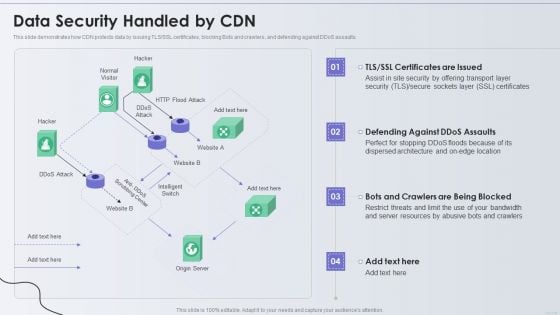
Distribution Network Data Security Handled By CDN Topics PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative Distribution Network Data Security Handled By CDN Topics PDF bundle. Topics like Security, Resources, Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Information And Event Management Services Mockup PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting security information and event management services mockup pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
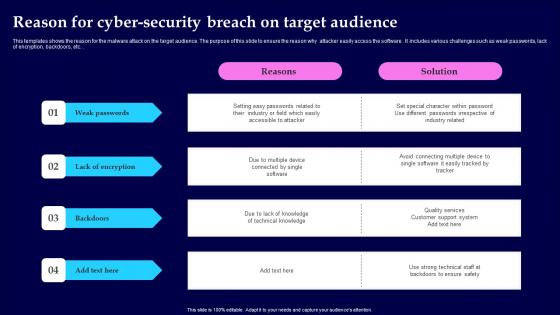
Reason For Cyber Security Breach On Target Audience Microsoft Pdf
This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc. Showcasing this set of slides titled Reason For Cyber Security Breach On Target Audience Microsoft Pdf The topics addressed in these templates are Weak Passwords, Lack Of Encryption, Backdoors All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc.
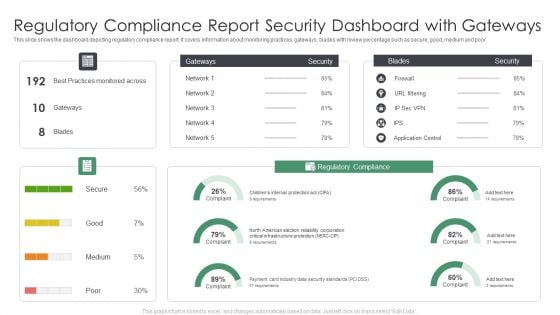
Regulatory Compliance Report Security Dashboard With Gateways Information PDF
This slide shows the dashboard depicting regulatory compliance report. It covers information about monitoring practices, gateways, blades with review percentage such as secure, good, medium and poor. Showcasing this set of slides titled Regulatory Compliance Report Security Dashboard With Gateways Information PDF. The topics addressed in these templates are Regulatory Compliance Report Security, Dashboard With Gateways. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
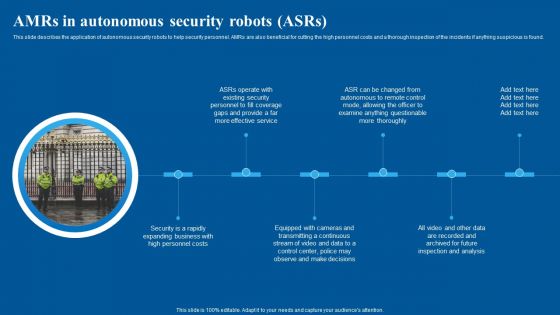
Amrs In Autonomous Security Robots Asrs Inspiration PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Boost your pitch with our creative Amrs In Autonomous Security Robots Asrs Inspiration PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF
This slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi-stage incidents, known campaign tracking, and high-volume incidents. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Comparative Assessment Of Hotel Protection And Security Solutions Mockup PDF
This slide covers comparative assessment of hotel safety and security solutions. It involves parameters of comparison such as anti slip solution, fire retarder, anti theft, test alarms and cost involved. Persuade your audience using this Comparative Assessment Of Hotel Protection And Security Solutions Mockup PDF This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Comparative Assessment, Hotel Protection, Security Solutions Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Key Consideration For Hotel Protection And Security Infographics PDF
This slide highlights five strategies to ensure safety and security in hotels. It involves strategies such as installation of proper lighting, CCTV security cameras, fire alarms, emergency power and manual.Presenting Five Key Consideration For Hotel Protection And Security Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Emergency Power, Emergency Manual, Proper Lighting This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF. Use them to share invaluable insights on Project Managers, Senior Executives, Security Introduction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
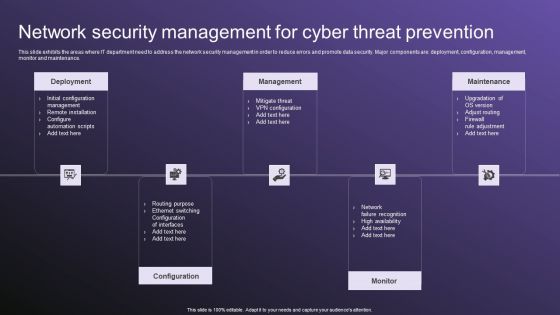
Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
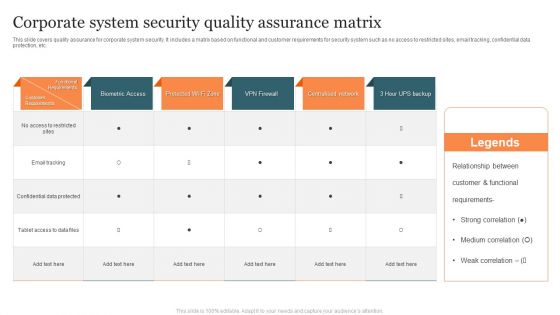
Corporate System Security Quality Assurance Matrix Demonstration PDF
This slide covers quality assurance for corporate system security. It includes a matrix based on functional and customer requirements for security system such as no access to restricted sites, email tracking, confidential data protection, etc. Showcasing this set of slides titled Corporate System Security Quality Assurance Matrix Demonstration PDF. The topics addressed in these templates are Customer Requirements, Functional Requirements, Centralised Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
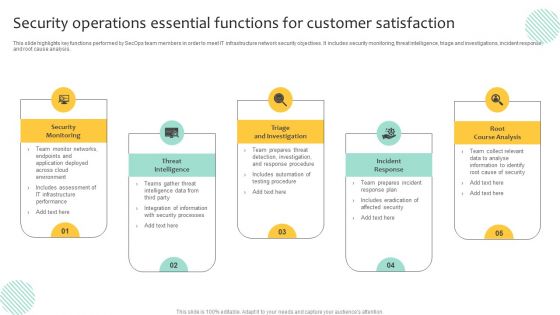
Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
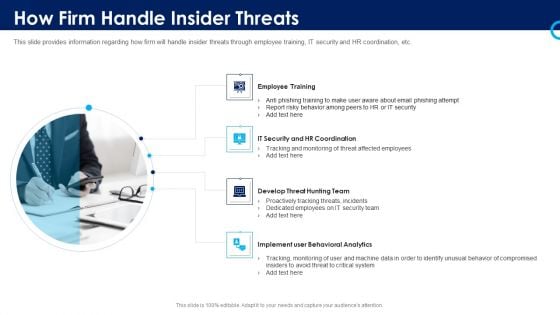
Organizational Security Solutions How Firm Handle Insider Threats Introduction PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a organizational security solutions how firm handle insider threats introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
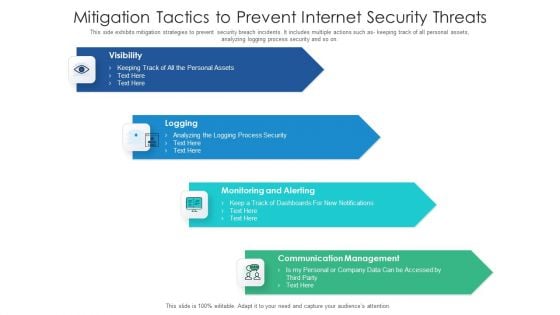
Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Problems Management And Action Plan Microsoft PDF
The following slide illustrates the cyber security risk management plan to outline business security threats and draft proposed strategies. It also includes elements such as objectives, issues, breach response actions, employee training etc. Persuade your audience using this Cyber Security Problems Management And Action Plan Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Breach Response Actions, Employee Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
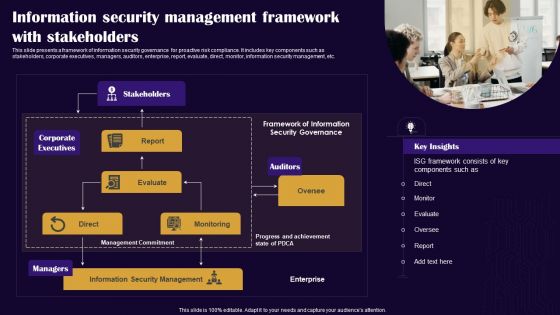
Information Security Management Framework With Stakeholders Diagrams PDF
This slide presents a framework of information security governance for proactive risk compliance. It includes key components such as stakeholders, corporate executives, managers, auditors, enterprise, report, evaluate, direct, monitor, information security management, etc. Persuade your audience using this Information Security Management Framework With Stakeholders Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Stakeholders, Auditors, Corporate Executives. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Agency Business Profile Employees Rules And Regulations Mockup PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. This is a Security Agency Business Profile Employees Rules And Regulations Mockup PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees, Security Officer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF. Use them to share invaluable insights on Factor Authentication, Phishing Malware, Accessing Organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
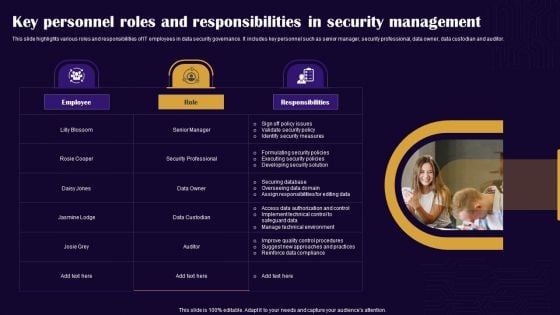
Key Personnel Roles And Responsibilities In Security Management Slides PDF
This slide highlights various roles and responsibilities of IT employees in data security governance. It includes key personnel such as senior manager, security professional, data owner, data custodian and auditor. Presenting Key Personnel Roles And Responsibilities In Security Management Slides PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employee, Role, Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
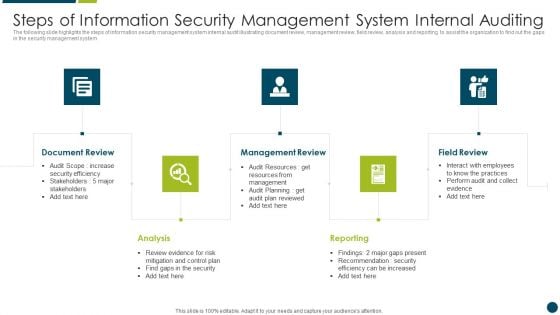
Steps Of Information Security Management System Internal Auditing Structure PDF
The following slide highlights the steps of information security management system internal audit illustrating document review, management review, field review, analysis and reporting to assist the organization to find out the gaps in the security management system Presenting Steps Of Information Security Management System Internal Auditing Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Management Review, Reporting, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

Security Measures To Prevent Phishing Attacks Ppt Gallery Deck PDF
This slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi factor authentication, and so on. This is a security measures to prevent phishing attacks ppt gallery deck pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, organization, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
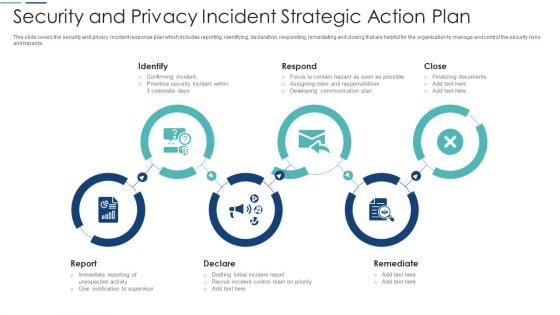
Security And Privacy Incident Strategic Action Plan Download PDF
This slide covers the security and privacy incident response plan which includes reporting, identifying, declaration, responding, remediating and closing that are helpful for the organization to manage and control the security risks and hazards. Presenting security and privacy incident strategic action plan download pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including confirming incident, assigning responsibilities, communication plan, supervisor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
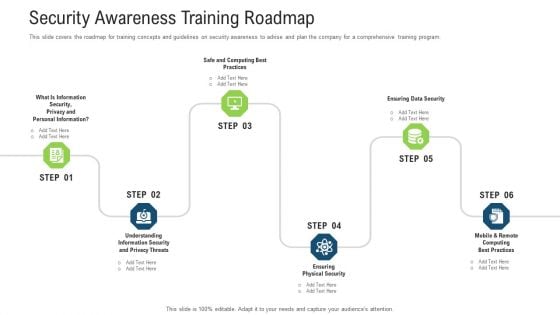
Security Awareness Training Roadmap Ppt Portfolio Demonstration PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a Security Awareness Training Roadmap Ppt Portfolio Demonstration Pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
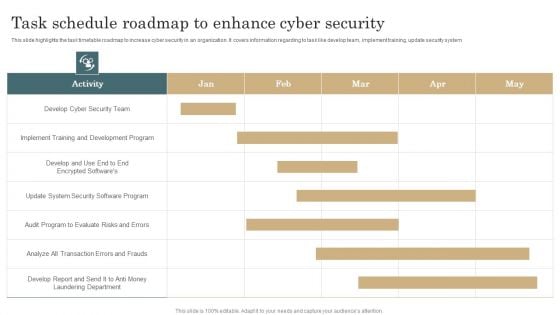
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
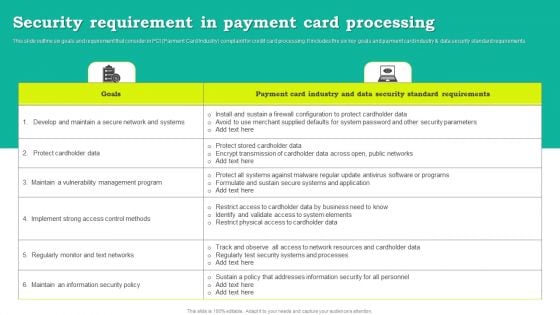
Security Requirement In Payment Card Processing Download PDF
This slide outline six goals and requirement that consider in PCI Payment Card Industry complaint for credit card processing. It includes the six key goals and payment card industry and data security standard requirements. Showcasing this set of slides titled Security Requirement In Payment Card Processing Download PDF. The topics addressed in these templates are Goals, Payment Card Industry, Data Security Standard Requirements. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Smart Home Security Solutions Company Profile Our Clients Inspiration PDF
This slide highlights the security company reputed clients which showcases client name, contract term and product or service including CCTV, wireless solution, CO2 monitor, door sensor, and fire fighting system. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Our Clients Inspiration PDF. Use them to share invaluable insights on Product Or Service, CCTV And Security, Wireless And Networking, Storage And Server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
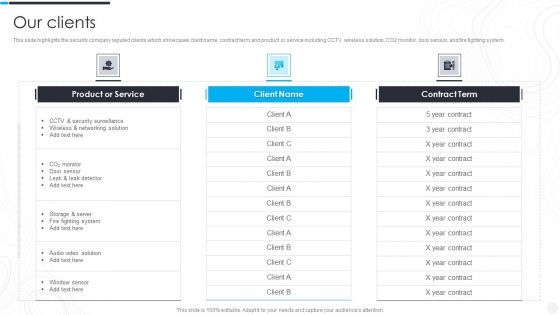
Security Camera System Company Profile Our Clients Rules PDF
This slide highlights the security company reputed clients which showcases client name, contract term and product or service including CCTV, wireless solution, CO2 monitor, door sensor, and fire fighting system. Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Our Clients Rules PDF. Use them to share invaluable insights on Product Or Service, Security Surveillance, Wireless Networking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
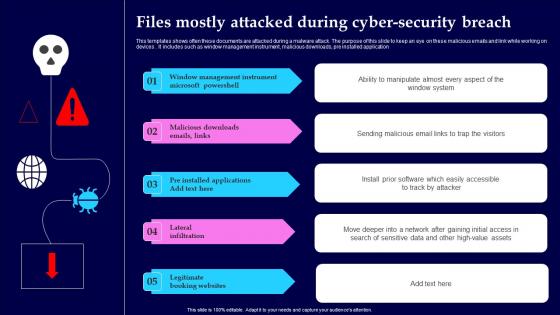
Files Mostly Attacked During Cyber Security Breach Structure Pdf
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application
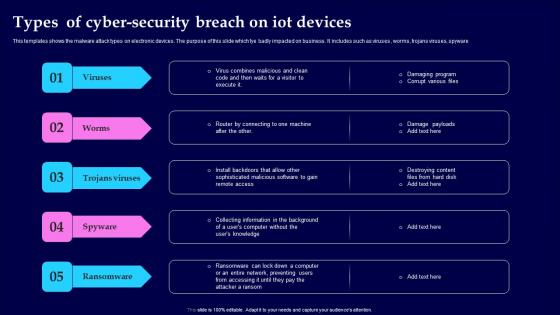
Types Of Cyber Security Breach On IOT Devices Themes Pdf
This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware Pitch your topic with ease and precision using this Types Of Cyber Security Breach On IOT Devices Themes Pdf This layout presents information on Viruses, Trojans Viruses, Spyware, Ransomware It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware
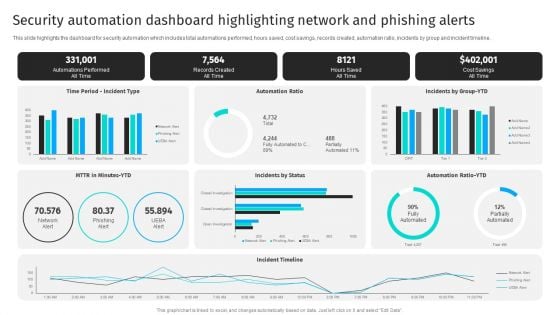
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

How Security Concerns Affect Firm In Present Times Pictures PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative how security concerns affect firm in present times pictures pdf bundle. Topics like reported financial losses due to increase security threats, data breaches and records exposed, security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
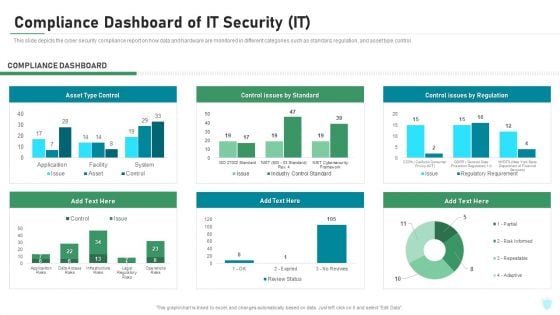
Compliance Dashboard Of IT Security IT Ppt Layouts Ideas PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative compliance dashboard of it security it ppt layouts ideas pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
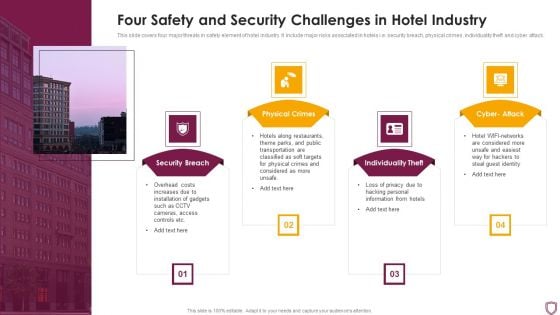
Four Safety And Security Challenges In Hotel Industry Topics PDF
This slide covers four major threats in safety element of hotel industry. It include major risks associated in hotels i.e. security breach, physical crimes, individuality theft and cyber attack. Persuade your audience using this Four Safety And Security Challenges In Hotel Industry Topics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Breach, Physical Crimes, Individuality Theft Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Flowchart For Security Orchestration And Automation System Icons PDF
The following slide highlights conceptual digitization of security systems flowchart. It includes components such as SOAR platform, orchestration process, unification, automation, detection, analysis, respond, security tool etc. Persuade your audience using this Flowchart For Security Orchestration And Automation System Icons PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Automation, Orchestration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
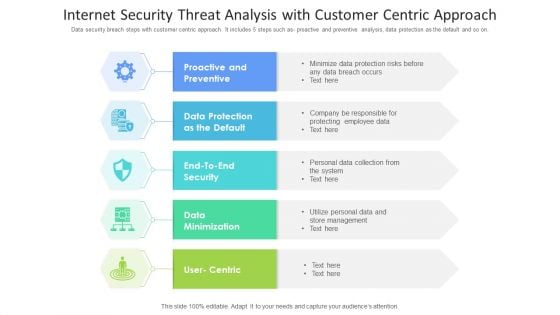
Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
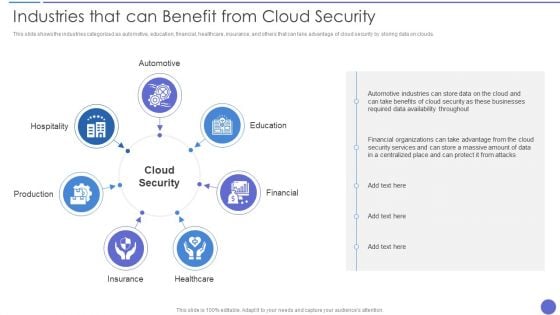
Industries That Can Benefit From Cloud Security Brochure PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds. Presenting Industries That Can Benefit From Cloud Security Brochure PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Cloud Security, Production, Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Data Security Protection Ppt PowerPoint Presentation Icon Graphics Download Cpb
Presenting this set of slides with name data security protection ppt powerpoint presentation icon graphics download cpb. This is an editable Powerpoint three stages graphic that deals with topics like data security protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Protection Security Controls Ppt PowerPoint Presentation Layouts Shapes Cpb
Presenting this set of slides with name data protection security controls ppt powerpoint presentation layouts shapes cpb. This is an editable Powerpoint four stages graphic that deals with topics like data protection security controls to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
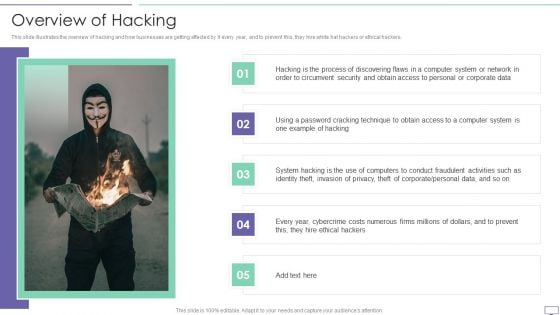
IT Security Hacker Overview Of Hacking Sample PDF
This slide illustrates the overview of hacking and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers.Deliver an awe inspiring pitch with this creative IT Security Hacker Overview Of Hacking Sample PDF bundle. Topics like Process Of Discovering, Circumvent Security, Example Of Hacking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
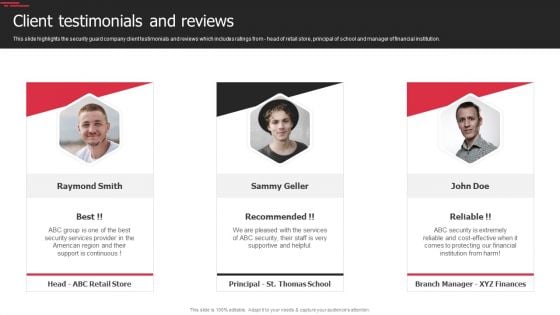
Security Agency Business Profile Client Testimonials And Reviews Inspiration PDF
This slide highlights the security guard company client testimonials and reviews which includes ratings from head of retail store, principal of school and manager of financial institution. This is a Security Agency Business Profile Client Testimonials And Reviews Inspiration PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Services, Financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Operational Outlook Of Security Awareness Training Software Icons PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Deliver an awe inspiring pitch with this creative Operational Outlook Of Security Awareness Training Software Icons PDF bundle. Topics like Educate Employees, Dynamic Training, Customized Content can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
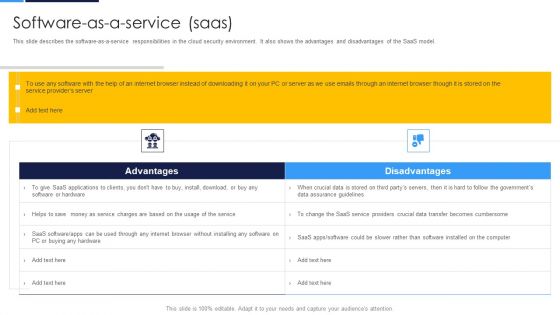
Cloud Security Assessment Software As A Service Saas Formats PDF
This slide describes the software as a service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Software As A Service Saas Formats PDF bundle. Topics like Disadvantages, Installing Any Software, Service Providers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Difference Between Authentication And Authorization Application Security Testing
This slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc. This modern and well-arranged Difference Between Authentication And Authorization Application Security Testing provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc.

Table Of Contents For Project Security Administration IT Pictures PDF
Presenting table of contents for project security administration it pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like project safety management, security centre implementation, budget assessment, dashboard analysis, project management team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
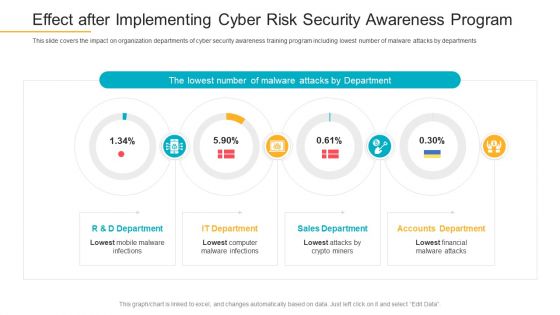
Effect After Implementing Cyber Risk Security Awareness Program Infographics PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Deliver an awe-inspiring pitch with this creative effect after implementing cyber risk security awareness program infographics pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Operations Training Department Program Icon Introduction PDF
Persuade your audience using this Information Security Operations Training Department Program Icon Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Operations Training, Department Program, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Data Security Privacy Ppt PowerPoint Presentation Icon Deck Cpb
Presenting this set of slides with name data security privacy ppt powerpoint presentation icon deck cpb. This is an editable Powerpoint six stages graphic that deals with topics like data security privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
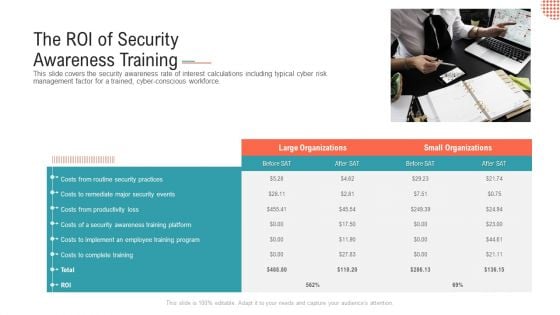
The ROI Of Security Awareness Training Ppt Slides Background PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyberconscious workforce.This is a the roi of security awareness training ppt slides background pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs from routine security practices, costs from productivity loss. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
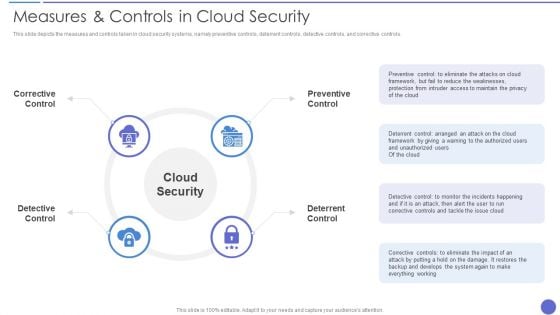
Measures And Controls In Cloud Security Ideas PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. This is a Measures And Controls In Cloud Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
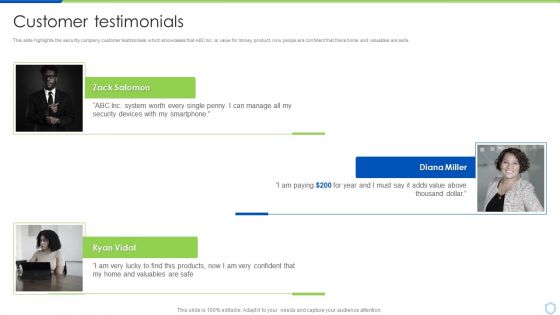
Security And Surveillance Company Profile Customer Testimonials Sample PDF
This slide highlights the security company customer testimonials which showcases that ABC Inc. is value for money product, now people are confident that there home and valuables are safe. This is a Security And Surveillance Company Profile Customer Testimonials Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Valuables Are Safe, Thousand Dollar, Security Devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
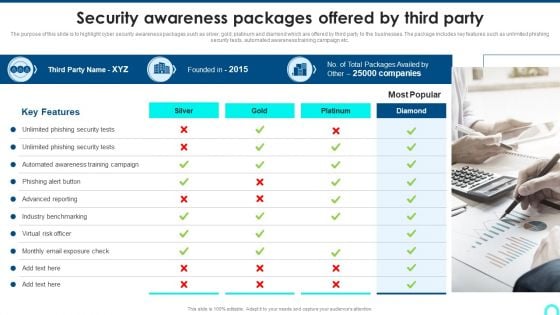
Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This is a Security Awareness Packages Offered By Third Party Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unlimited Phishing, Automated Awareness, Industry Benchmarking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
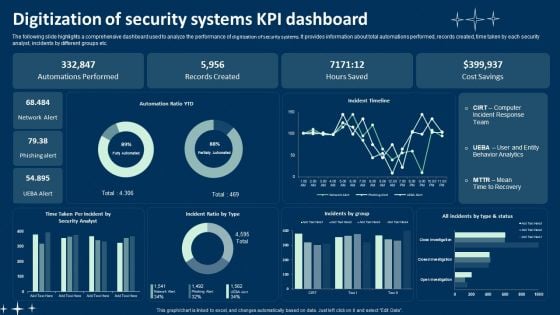
Digitization Of Security Systems KPI Dashboard Ppt Summary Portfolio PDF
The following slide highlights a comprehensive dashboard used to analyze the performance of digitization of security systems. It provides information about total automations performed, records created, time taken by each security analyst, incidents by different groups etc. Showcasing this set of slides titled Digitization Of Security Systems KPI Dashboard Ppt Summary Portfolio PDF. The topics addressed in these templates are Automations Performed, Records Created, Hours Saved. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
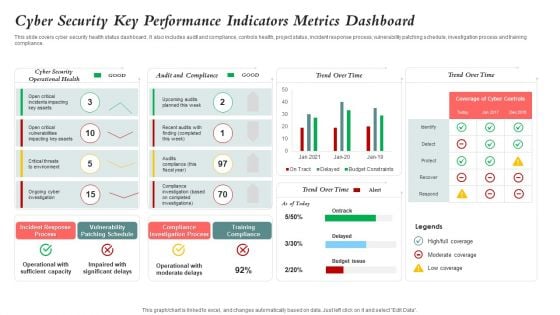
Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF
This slide covers cyber security health status dashboard . It also includes audit and compliance, controls health, project status, incident response process, vulnerability patching schedule, investigation process and training compliance. Pitch your topic with ease and precision using this Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF. This layout presents information on Cyber Security, Vulnerability Patching Schedule, Compliance Investigation Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cyber Security Threat Dashboard With KPI Metrics Icons PDF
This slide shows dashboard of cyber threats to organization and metrics and performance indicators for security officer. It covers operational health, audit and compliance, controls health and project status. Showcasing this set of slides titled Cyber Security Threat Dashboard With KPI Metrics Icons PDF. The topics addressed in these templates are Cyber Security Threat Dashboard, Kpi Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
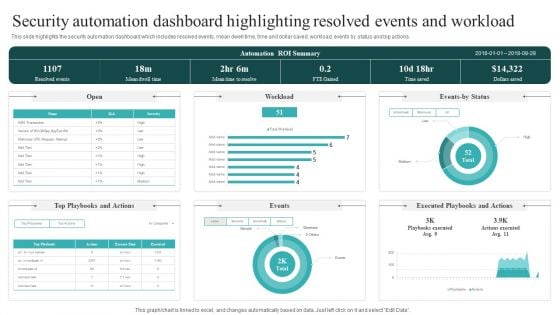
Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. This Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.


 Continue with Email
Continue with Email

 Home
Home


































