Technology Security
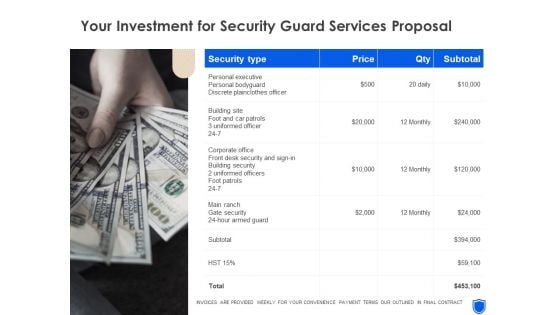
Your Investment For Security Guard Services Proposal Topics PDF
Deliver an awe-inspiring pitch with this creative your investment for security guard services proposal topics pdf bundle. Topics like your investment, security guard services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Services Proposal Example Document Report Doc Pdf Ppt
Heres a predesigned Security Services Proposal Example Document Report Doc Pdf Ppt for you. Built on extensive research and analysis, this one-complete deck has all the center pieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Security Services Proposal Example Document Report Doc Pdf Ppt A4 One-pager now.
Information Security Document Vector Icon Ppt Styles Mockup PDF
Presenting information security document vector icon ppt styles mockup pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including information security document vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
KPI Metrics Security Icon With Dashboard Template PDF
Persuade your audience using this KPI Metrics Security Icon With Dashboard Template PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Kpi Metrics, Security Icon, Dashboard. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
One Pager Safety And Security Sell PDF Document PPT Template
Heres a predesigned One Pager Safety And Security Sell PDF Document PPT Template for you. Built on extensive research and analysis, this one-pager template has all the centerpieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this One Pager Safety And Security Sell PDF Document PPT Template Download now.
Stakeholder Security Audit And Recognition Icon Demonstration PDF
Persuade your audience using this Stakeholder Security Audit And Recognition Icon Demonstration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Stakeholder Security Audit, Recognition Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
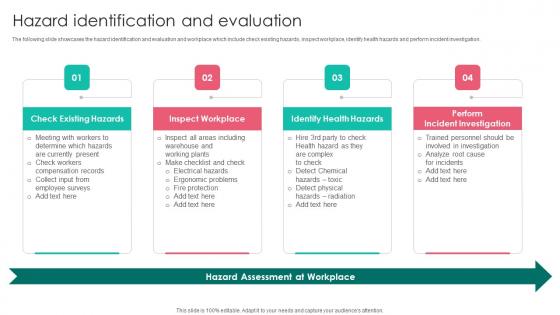
Hazard Identification Workplace Safety Protocol And Security Practices Background Pdf
The following slide showcases the hazard identification and evaluation and workplace which include check existing hazards, inspect workplace, identify health hazards and perform incident investigation. This modern and well arranged Hazard Identification Workplace Safety Protocol And Security Practices Background Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide showcases the hazard identification and evaluation and workplace which include check existing hazards, inspect workplace, identify health hazards and perform incident investigation.
Business Safety And Security Report Writing Icon Template PDF
Presenting Business Safety And Security Report Writing Icon Template PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Report, Business Safety. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Breach Prevention Recognition IT Infrastructure Security Budget Rules PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition it infrastructure security budget rules pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
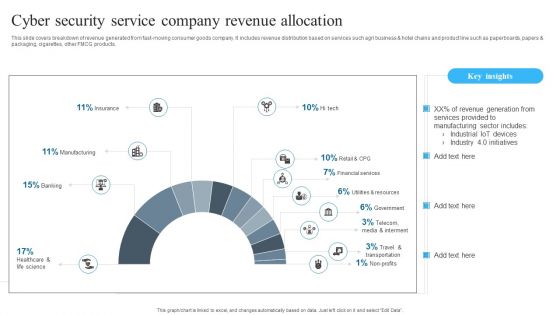
Cyber Security Service Company Revenue Allocation Background PDF
Showcasing this set of slides titled Cyber Security Service Company Revenue Allocation Background PDF. The topics addressed in these templates are Cyber Security, Service Company, Revenue Allocation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
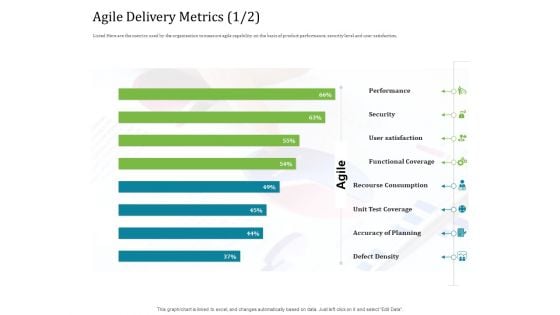
Agile Service Delivery Model Agile Delivery Metrics Security Professional PDF
Deliver an awe inspiring pitch with this creative agile service delivery model agile delivery metrics security professional pdf bundle. Topics like performance, security, user satisfaction, functional coverage, recourse consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
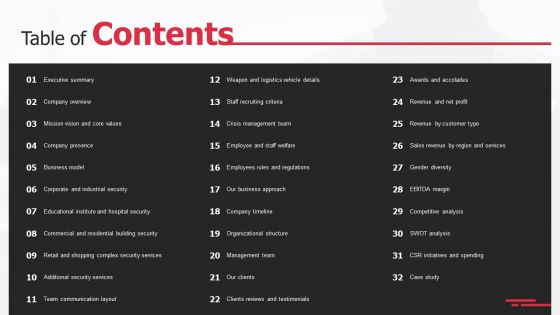
Security Agency Business Profile Table Of Contents Rules PDF
Deliver an awe inspiring pitch with this creative Security Agency Business Profile Table Of Contents Rules PDF bundle. Topics like Executive Summary, Business Model, Additional Security Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
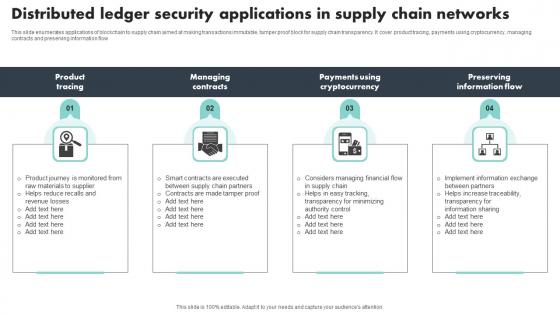
Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf
This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow Pitch your topic with ease and precision using this Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf This layout presents information on Product Tracing, Managing Contracts, Preserving Information Flow It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow
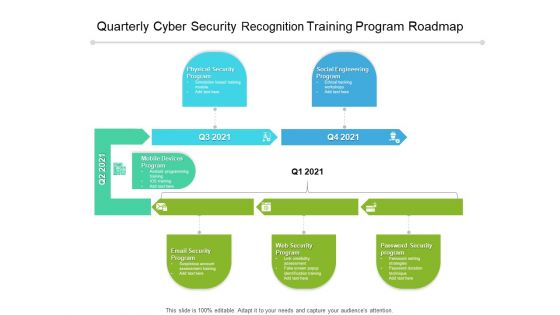
Quarterly Cyber Security Recognition Training Program Roadmap Elements
We present our quarterly cyber security recognition training program roadmap elements. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched quarterly cyber security recognition training program roadmap elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
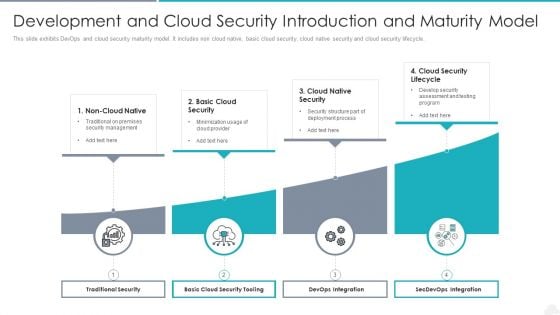
Development And Cloud Security Introduction And Maturity Model Graphics PDF
Presenting development and cloud security introduction and maturity model graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including traditional security, devops integration, secdevops integration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Transformation Of Security In Banking Icon Mockup PDF
Presenting digital transformation of security in banking icon mockup pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including digital transformation of security in banking icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Loss Prevention Icon With Security System Guidelines PDF
Persuade your audience using this Loss Prevention Icon With Security System Guidelines PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security System, Loss Prevention Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF
Presenting Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cybersecurity Training, Workshop On Security, Breach Trends Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Governance And Management Process Icon Introduction PDF
Persuade your audience using this Security Governance And Management Process Icon Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security, Governance, Management Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Computing Infra Cyber Security Icon Sample PDF
Presenting Cloud Computing Infra Cyber Security Icon Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Infra Cyber, Security Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
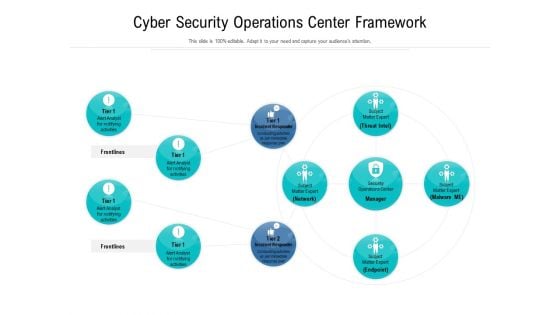
Cyber Security Operations Center Framework Ppt Styles Portfolio PDF
Showcasing this set of slides titled cyber security operations center framework ppt styles portfolio pdf. The topics addressed in these templates are cyber security operations center framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Differentiating 2 Items Graphic For Free Internet Security Guidelines PDF
Deliver an awe inspiring pitch with this creative differentiating 2 items graphic for free internet security guidelines pdf bundle. Topics like differentiating 2 items graphic for free internet security reviews can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
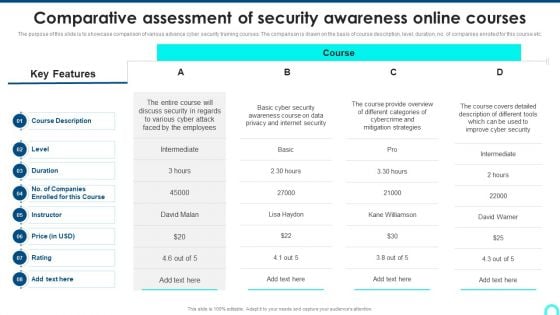
Comparative Assessment Of Security Awareness Online Courses Background PDF
Deliver an awe inspiring pitch with this creative Comparative Assessment Of Security Awareness Online Courses Background PDF bundle. Topics like Internet Security, Intermediate, Awareness Course can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icon Showcasing Online Security From Cyber Crime Clipart PDF
Showcasing this set of slides titled Icon Showcasing Online Security From Cyber Crime Clipart PDF. The topics addressed in these templates are Icon Showcasing Online, Security From Cyber Crime. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Critical Importance Of HR Security At Workplace Demonstration PDF
Showcasing this set of slides titled Critical Importance Of HR Security At Workplace Demonstration PDF. The topics addressed in these templates are Critical Importance, HR Security Workplace. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents Cyber Safety Incident Management Security Microsoft PDF
This is a table of contents cyber safety incident management security microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current scenario assessment, handling cyber threats to secure digital assets, ensuring physical security, securing firm from natural calamity threats . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
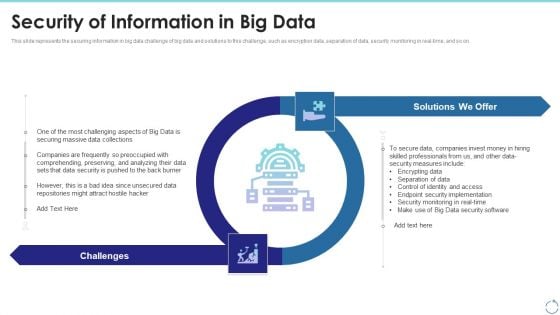
Security Of Information In Big Data Ppt Infographics Layout PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. This is a security of information in big data ppt infographics layout pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, implementation, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
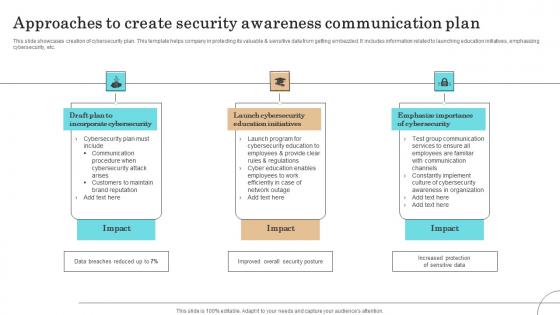
Approaches To Create Security Awareness Communication Plan Professional Pdf
This slide showcases creation of cybersecurity plan. This template helps company in protecting its valuable sensitive data from getting embezzled. It includes information related to launching education initiatives, emphasizing cybersecurity, etc.Showcasing this set of slides titled Approaches To Create Security Awareness Communication Plan Professional Pdf The topics addressed in these templates are Incorporate Cybersecurity, Launch Cybersecurity, Education Initiatives All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases creation of cybersecurity plan. This template helps company in protecting its valuable sensitive data from getting embezzled. It includes information related to launching education initiatives, emphasizing cybersecurity, etc.

IT Security Awareness Training Program Plan Ppt Show Tips PDF
This slide covers cybersecurity awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public wi-fi, phishing attacks, mobile device security and passwords and authentication. Showcasing this set of slides titled IT Security Awareness Training Program Plan Ppt Show Tips PDF. The topics addressed in these templates are Training Topic, Mode Of Training, Training Hours. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
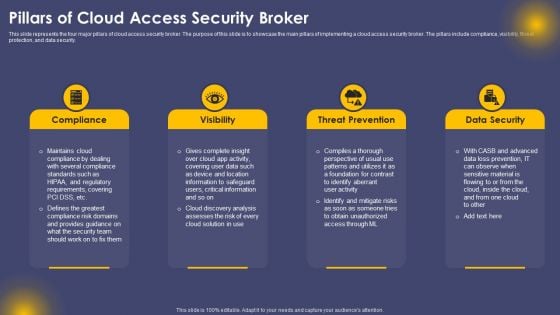
Pillars Of Cloud Access Security Broker Ppt Show Background PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Pillars Of Cloud Access Security Broker Ppt Show Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Pillars Of Cloud Access Security Broker Ppt Show Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
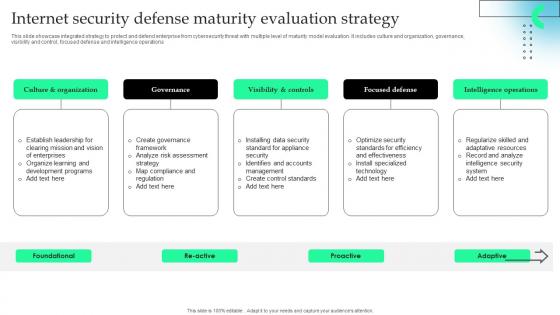
Internet Security Defense Maturity Evaluation Strategy Information Pdf
This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.Pitch your topic with ease and precision using this Internet Security Defense Maturity Evaluation Strategy Information Pdf This layout presents information on Visibility Controls, Focused Defense, Intelligence Operations It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.
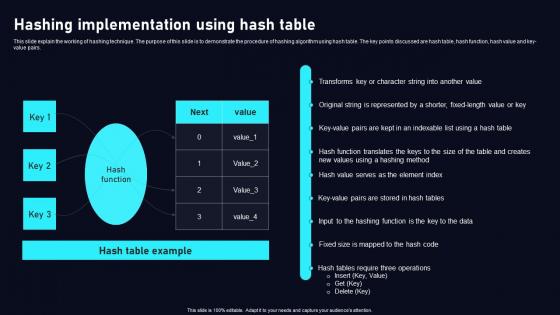
Hashing Implementation Using Cloud Data Security Using Cryptography Ideas Pdf
This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key value pairs. Find a pre designed and impeccable Hashing Implementation Using Cloud Data Security Using Cryptography Ideas Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key value pairs.
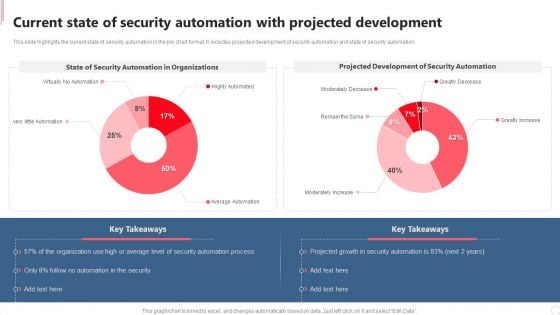
Current State Of Security Automation With Projected Development Rules PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed Current State Of Security Automation With Projected Development Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Current State Of Security Automation With Projected Development Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF
This slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
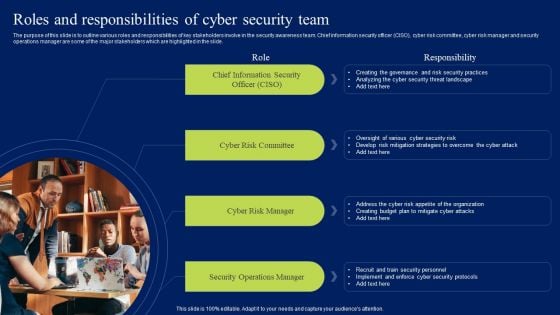
Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
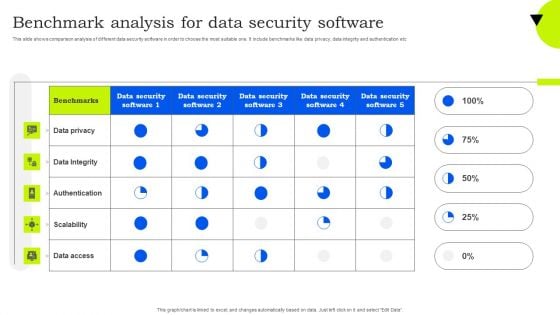
Benchmark Analysis For Data Security Software Mockup PDF
This slide shows comparison analysis of different data security software in order to choose the most suitable one. It include benchmarks like data privacy, data integrity and authentication etc. Showcasing this set of slides titled Benchmark Analysis For Data Security Software Mockup PDF. The topics addressed in these templates are Data Privacy, Data Integrity, Authentication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
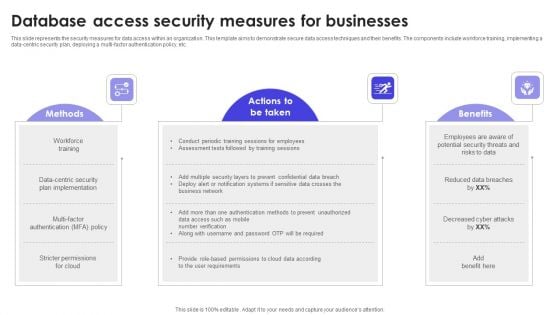
Database Access Security Measures For Businesses Portrait PDF
This slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data-centric security plan, deploying a multi-factor authentication policy, etc. Pitch your topic with ease and precision using this Database Access Security Measures For Businesses Portrait PDF. This layout presents information on Methods, Benefits, Actions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
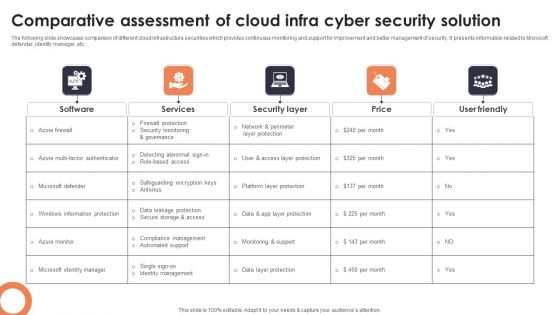
Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF
The following slide showcases comparison of different cloud infrastructure securities which provides continuous monitoring and support for improvement and better management of security. It presents information related to Microsoft defender, identity manager, etc. Showcasing this set of slides titled Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF. The topics addressed in these templates are Software, Services, Security Layer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
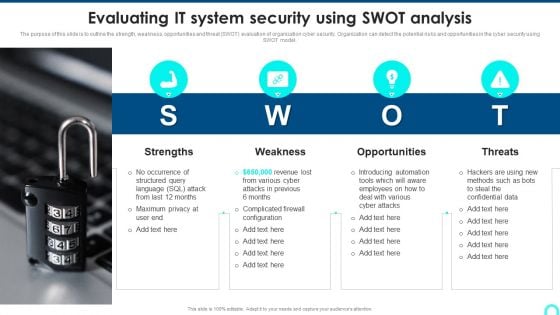
Evaluating IT System Security Using SWOT Analysis Portrait PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Presenting Evaluating IT System Security Using SWOT Analysis Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
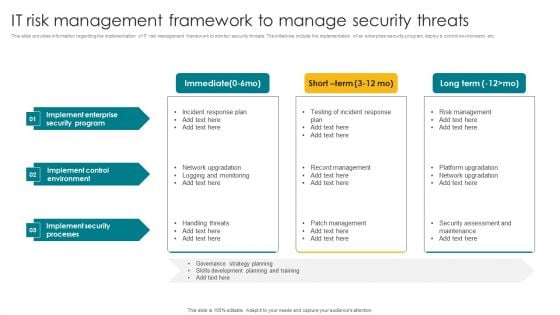
IT Risk Management Framework To Manage Security Threats Template PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. The IT Risk Management Framework To Manage Security Threats Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
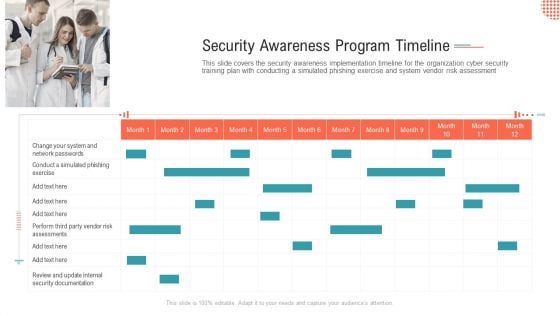
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
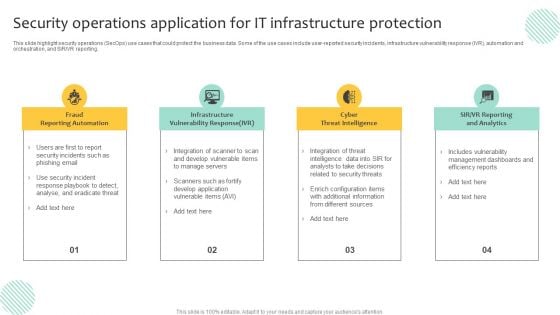
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
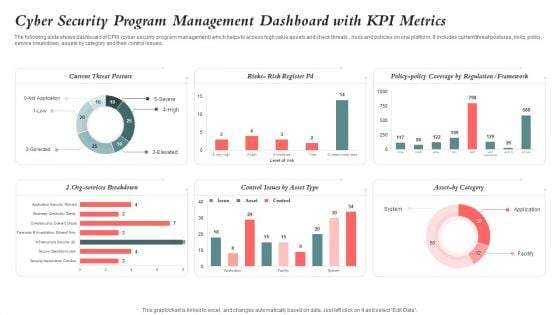
Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF
The following slide shows dashboard of CPM cyber security program management which helps to access high value assets and check threats , risks and policies on one platform. It includes current threat postures, risks, policy, service breakdown, assets by category and their control issues. Pitch your topic with ease and precision using this Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF. This layout presents information on Cyber Security, Program Management Dashboard, Kpi Metrics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
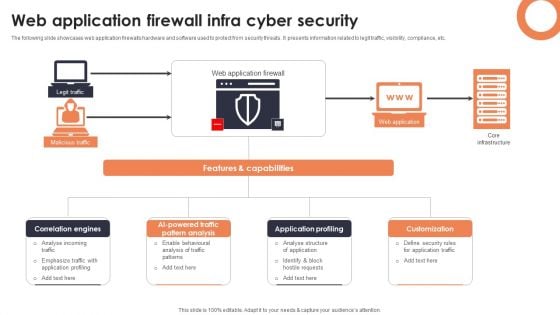
Web Application Firewall Infra Cyber Security Designs PDF
The following slide showcases web application firewalls hardware and software used to protect from security threats. It presents information related to legit traffic, visibility, compliance, etc. Showcasing this set of slides titled Web Application Firewall Infra Cyber Security Designs PDF. The topics addressed in these templates are Correlation Engines, AI Powered Traffic Pattern, Application Profiling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
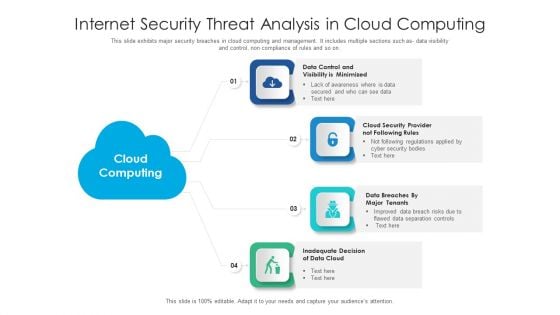
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
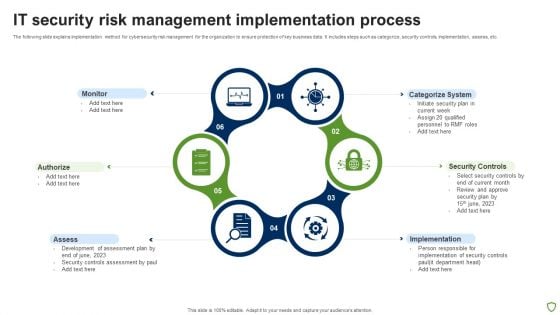
IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
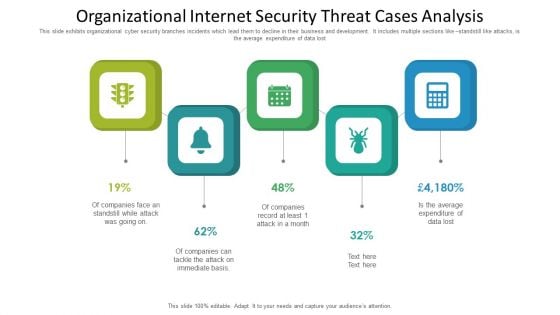
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
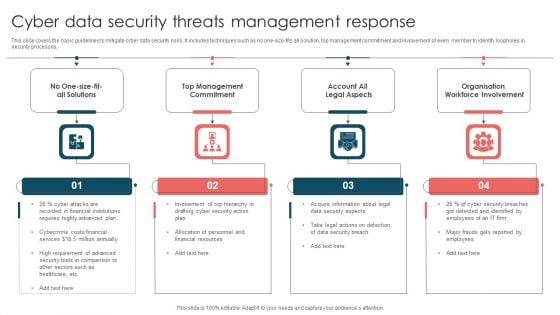
Cyber Data Security Threats Management Response Ppt Summary Skills PDF
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
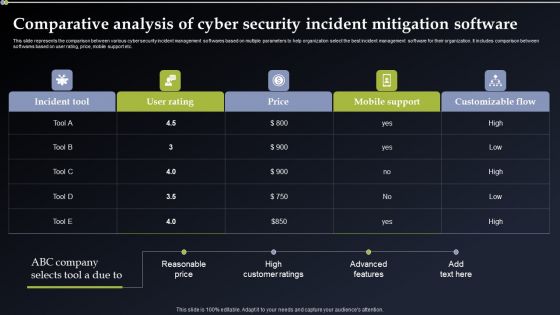
Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Presenting this PowerPoint presentation, titled Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Types Of IT Security Control Assessment Model Clipart PDF
This slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Persuade your audience using this Types Of IT Security Control Assessment Model Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Options, Framework, Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
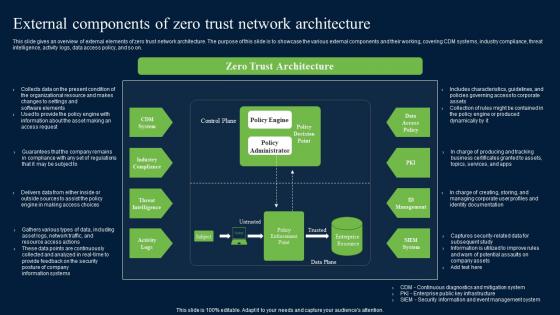
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
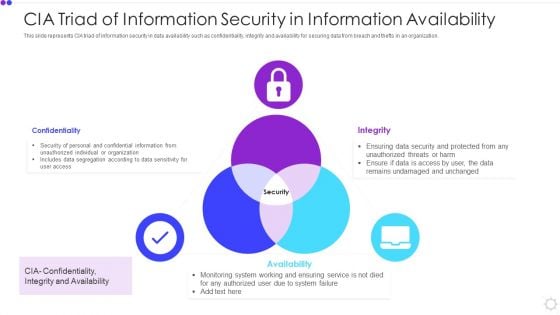
Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
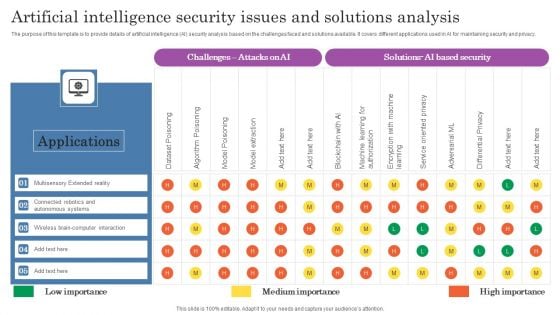
Artificial Intelligence Security Issues And Solutions Analysis Topics PDF
The purpose of this template is to provide details of artificial intelligence AI security analysis based on the challenges faced and solutions available. It covers different applications used in AI for maintaining security and privacy. Pitch your topic with ease and precision using this Artificial Intelligence Security Issues And Solutions Analysis Topics PDF. This layout presents information on Applications, Autonomous Systems, Wireless. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Agency Business Profile Swot Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes 30 years experience as strengths, attacks on security personnel as weakness, high industry growth as opportunity and high attrition rate as threats. This is a Security Agency Business Profile Swot Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities, Threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
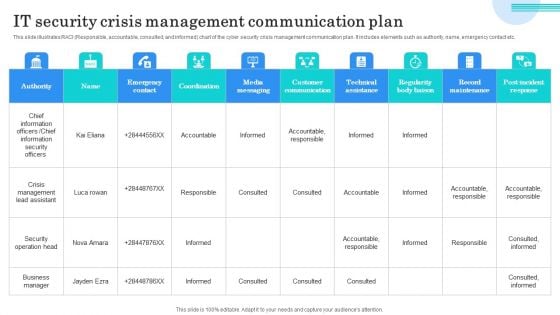
IT Security Crisis Management Communication Plan Microsoft PDF
This slide illustrates RACI Responsible, accountable, consulted, and informed chart of the cyber security crisis management communication plan. It includes elements such as authority, name, emergency contact etc. Showcasing this set of slides titled IT Security Crisis Management Communication Plan Microsoft PDF. The topics addressed in these templates are Chief Information Officers, Chief Information Security Officers, Crisis Management Lead Assistant. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Video Meeting Internet Security Threat Analysis Measures Brochure PDF
Following slide showcase video meeting security breach control tasks and actions. It includes multiple actions such as- run the recent version of application, utilizing corporate mails to send meeting links and so on. Persuade your audience using this video meeting internet security threat analysis measures brochure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including video meeting internet security threat analysis measures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































