Technology Security

Project Security Administration IT Roles And Responsibilities To Ensure Work Environment With Employee Safety Pictures PDF
This slide provides information regarding roles and responsibilities assigned to ensure minimum violence work environment. Presenting project security administration it roles and responsibilities to ensure work environment with employee safety pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like employee responsibilities, unit supervisor or manager responsibilities, internal investigations unit responsibilities, human resources responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Corporate Security And Risk Management Workplace Employee Assistance Program Icons PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. This is a corporate security and risk management workplace employee assistance program icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clinical services, work and life services, employer services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
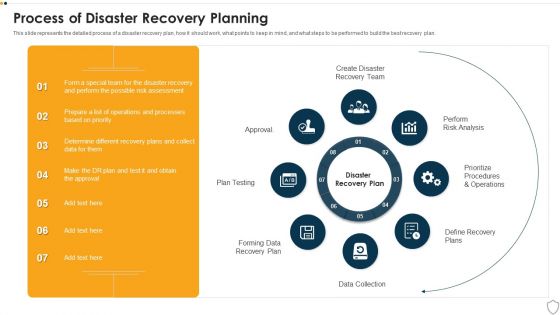
IT Security Process Of Disaster Recovery Planning Ppt Portfolio Microsoft PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting it security process of disaster recovery planning ppt portfolio microsoft pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like plan testing, perform risk analysis, data collection, prioritize procedures and operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Strategies To Manage Cyber Risks Ppt Icon Gallery PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting it security strategies to manage cyber risks ppt icon gallery pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like conduct awareness sessions, prioritize cyber risk as strategic issue, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
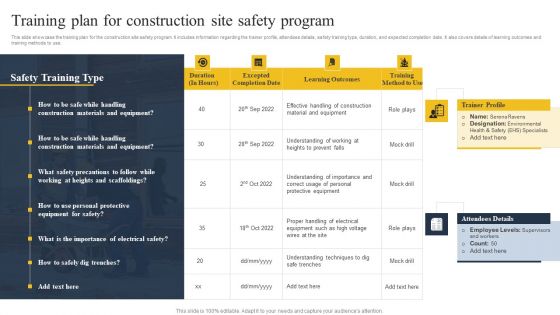
Security Control Techniques For Real Estate Project Training Plan For Construction Site Safety Program Structure PDF
Slidegeeks is here to make your presentations a breeze with Security Control Techniques For Real Estate Project Training Plan For Construction Site Safety Program Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youare sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Security Administration In Organization Workplace Employee Assistance Program Professional PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber security administration in organization workplace employee assistance program professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical, services, employer, management, consultations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
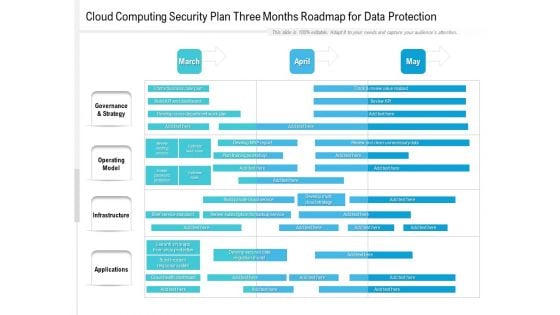
Cloud Computing Security Plan Three Months Roadmap For Data Protection Structure
Presenting the cloud computing security plan three months roadmap for data protection structure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
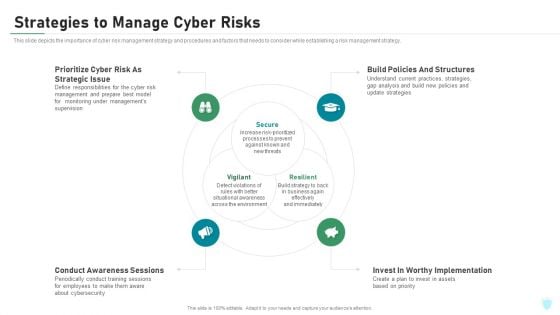
Strategies To Manage Cyber Risks IT Security IT Ppt Visual Aids Portfolio PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting strategies to manage cyber risks it security it ppt visual aids portfolio pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like prioritize cyber risk as strategic issue, conduct awareness sessions, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
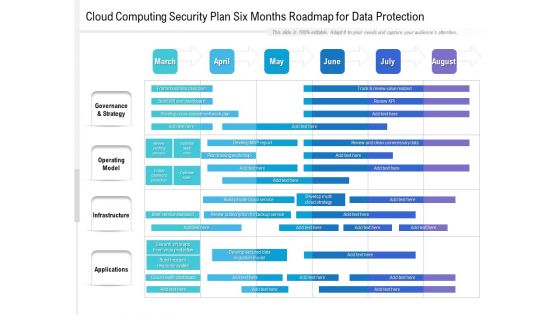
Cloud Computing Security Plan Six Months Roadmap For Data Protection Themes
Presenting our jaw dropping cloud computing security plan six months roadmap for data protection themes. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

How Is Automation Used In Cybersecurity IT Security IT Ppt Topics PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. This is a how is automation used in cybersecurity it security it ppt topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat detection, threat response, human augmentation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
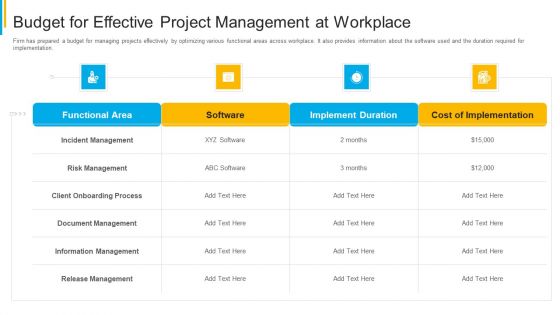
Project Security Administration IT Budget For Effective Project Management At Workplace Themes PDF
Firm has prepared a budget for managing projects effectively by optimizing various functional areas across workplace. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative project security administration it budget for effective project management at workplace themes pdf bundle. Topics like functional area, software, implement duration, cost of implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF
Welcome to our selection of the Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
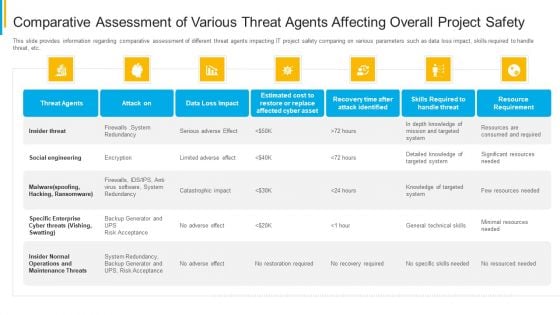
Project Security Administration IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Background PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this project security administration it comparative assessment of various threat agents affecting overall project safety background pdf. Use them to share invaluable insights on resource requirement, maintenance threats, cyber threats, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
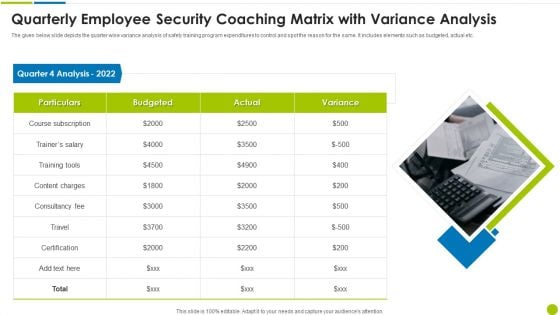
Quarterly Employee Security Coaching Matrix With Variance Analysis Ppt Styles Design Ideas PDF
The given below slide depicts the quarter wise variance analysis of safety training program expenditures to control and spot the reason for the same. It includes elements such as budgeted, actual etc. Presenting quarterly employee security coaching matrix with variance analysis ppt styles design ideas pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including particulars, quarter 4 analysis 2022, consultancy fee, content charges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
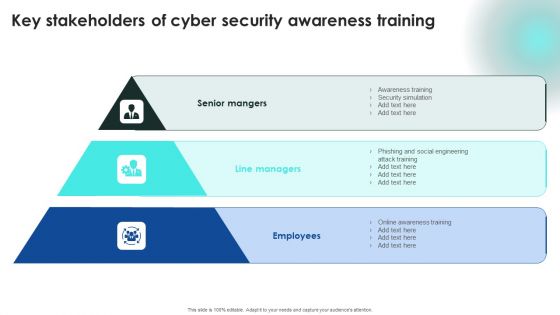
Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF bundle. Topics like Operating Breakdown, Session Duration, Goal Completions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
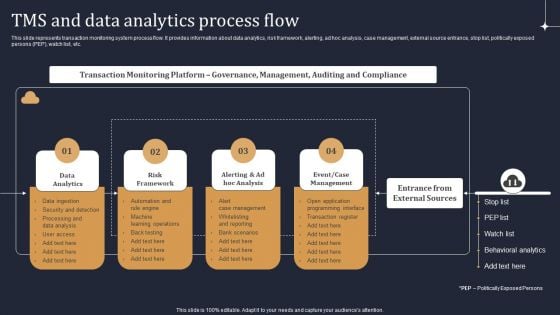
KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Global Cyber Terrorism Incidents On The Rise IT Roadmap To Implement Cyber Security Icons PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. This is a global cyber terrorism incidents on the rise it roadmap to implement cyber security icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like keep the hardware and software updated, awareness training for employees, creating personal accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
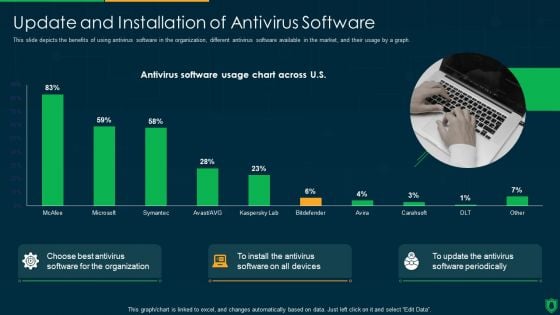
Info Security Update And Installation Of Antivirus Software Ppt PowerPoint Presentation File Designs PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this info security update and installation of antivirus software ppt powerpoint presentation file designs pdf. Use them to share invaluable insights on antivirus software usage chart across us, choose best antivirus, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
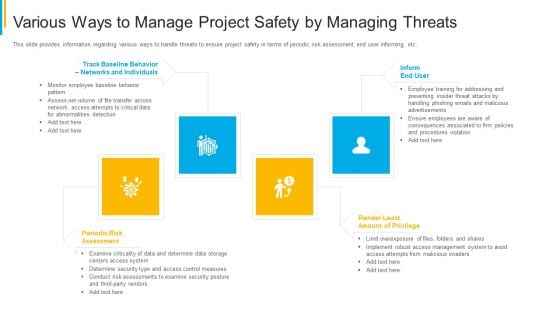
Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Software Company Investor Funding Pitch Deck Company Introduction Structure PDF
This slide represents the overview of IT company which offers an NTA solution to IT customers . It showcases industry, customer, headquarters, type, founded year, founders, website and legal name. Want to ace your presentation in front of a live audience Our Security Software Company Investor Funding Pitch Deck Company Introduction Structure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
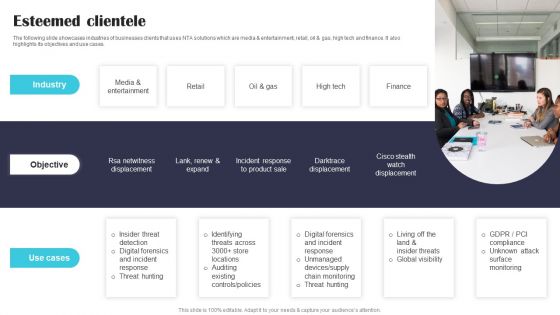
Security Software Company Investor Funding Pitch Deck Esteemed Clientele Themes PDF
The following slide showcases industries of businesses clients that uses NTA solutions which are media and entertainment, retail, oil and gas, high tech and finance. It also highlights its objectives and use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Security Software Company Investor Funding Pitch Deck Esteemed Clientele Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
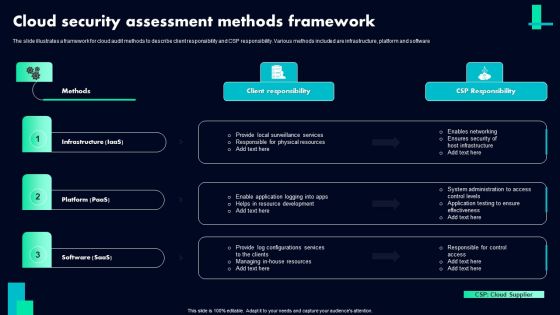
Cloud Security Assessment Methods Framework Ppt PowerPoint Presentation File Clipart PDF
The slide illustrates a framework for cloud audit methods to describe client responsibility and CSP responsibility. Various methods included are infrastructure, platform and software. Pitch your topic with ease and precision using this Cloud Security Assessment Methods Framework Ppt PowerPoint Presentation File Clipart PDF. This layout presents information on Methods, Infrastructure Iaas, Platform Paas, Client Responsibility. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF
The Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
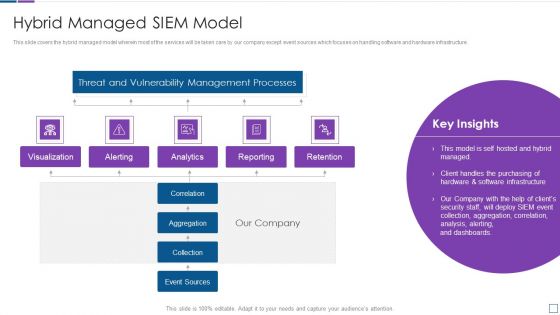
Real Time Assessment Of Security Threats Hybrid Managed SIEM Model Brochure PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative real time assessment of security threats hybrid managed siem model brochure pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
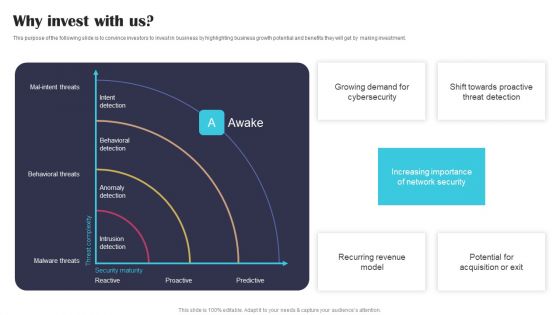
Security Software Company Investor Funding Pitch Deck Why Invest With Us Structure PDF
This purpose of the following slide is to convince investors to invest in business by highlighting business growth potential and benefits they will get by making investment. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Security Software Company Investor Funding Pitch Deck Why Invest With Us Structure PDF from Slidegeeks and deliver a wonderful presentation.

Hurdles In Business Data Security In Trade Secret Ppt PowerPoint Presentation Pictures Master Slide PDF
Showcasing this set of slides titled hurdles in business data security in trade secret ppt powerpoint presentation pictures master slide pdf. The topics addressed in these templates are once trade secret is made public, it can be accessed by anyone, difficult to enforce than patent, level of protection granted to trade is generally considered weak and is different from country country. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
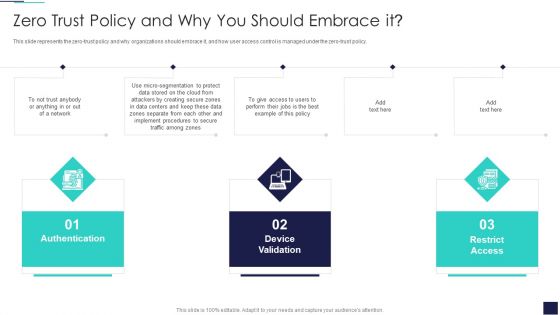
Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
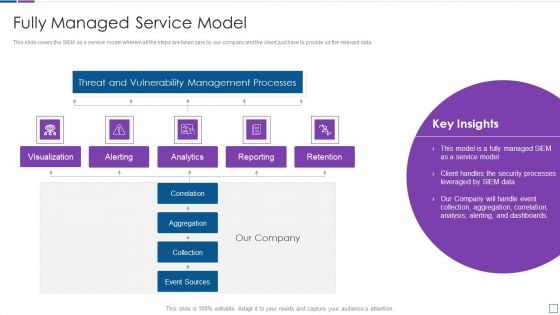
Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
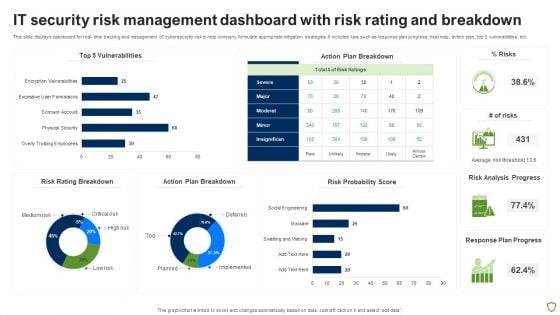
IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF
This slide displays dashboard for real- time tracking and management of cybersecurity risk to help company formulate appropriate mitigation strategies. It includes kpis such as response plan progress, heat map, action plan, top 5 vulnerabilities, etc. Pitch your topic with ease and precision using this IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF. This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Probability Score, Risk Analysis Progress. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Contd Sample PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a project security administration it various ways to manage project safety by managing threats contd sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deactivate orphaned user accounts, develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
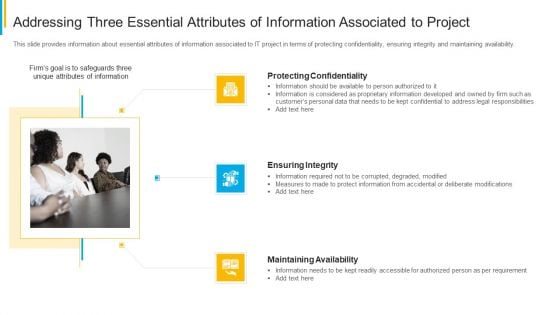
Project Security Administration IT Addressing Three Essential Attributes Of Information Associated To Project Topics PDF
This slide provides information about essential attributes of information associated to IT project in terms of protecting confidentiality, ensuring integrity and maintaining availability. This is a project security administration it addressing three essential attributes of information associated to project topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting confidentiality, ensuring integrity, maintaining availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
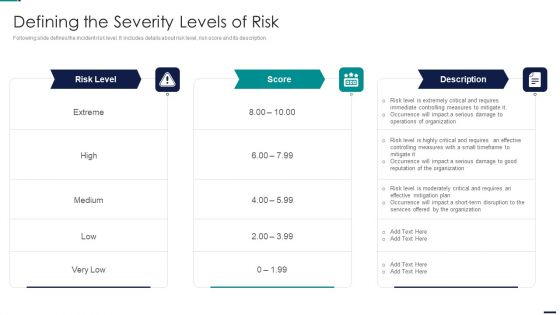
Risk Management Model For Data Security Defining The Severity Levels Of Risk Clipart PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. This is a Risk Management Model For Data Security Defining The Severity Levels Of Risk Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Level, Score, High, Low, Medium, Operations, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF. Use them to share invaluable insights on Threat Encountered, Risk Level, Mitigation Plan, Resources Required and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
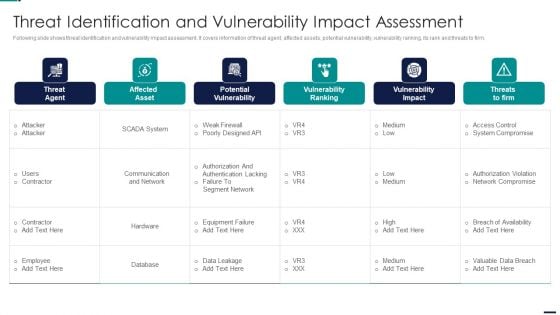
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
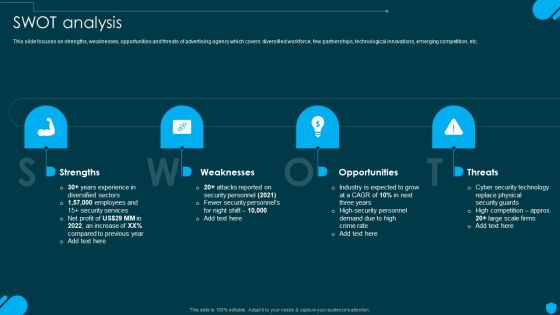
Security And Human Resource Services Business Profile SWOT Analysis Formats PDF
Retrieve professionally designed Security And Human Resource Services Business Profile SWOT Analysis Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
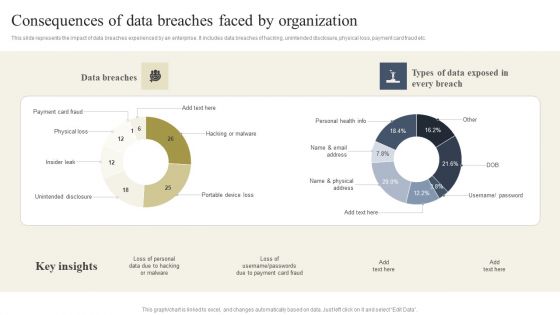
Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Risk Management Model For Data Security Asset Criticality Of Identified System Components Topics PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Asset Criticality Of Identified System Components Topics PDF. Use them to share invaluable insights on Impact Rating On Business, Criticality Rating, Failure Cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
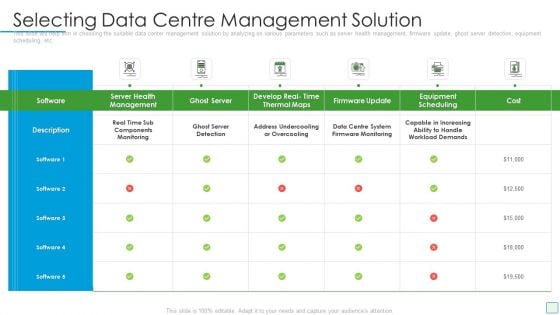
Developing Firm Security Strategy Plan Selecting Data Centre Management Solution Pictures PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan selecting data centre management solution pictures pdf. Use them to share invaluable insights on monitoring, management, develop, ghost server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
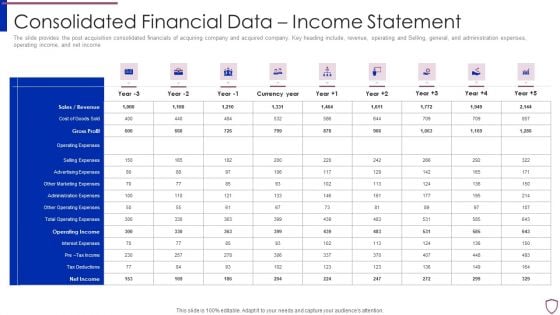
Financing Catalogue For Security Underwriting Agreement Consolidated Financial Data Income Statement Template PDF
The slide provides the post acquisition consolidated financials of acquiring company and acquired company. Key heading include, revenue, operating and Selling, general, and administration expenses, operating income, and net income. Deliver and pitch your topic in the best possible manner with this financing catalogue for security underwriting agreement consolidated financial data income statement template pdf. Use them to share invaluable insights on sales or revenue, cost of goods sold, gross profit, operating expenses, selling expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
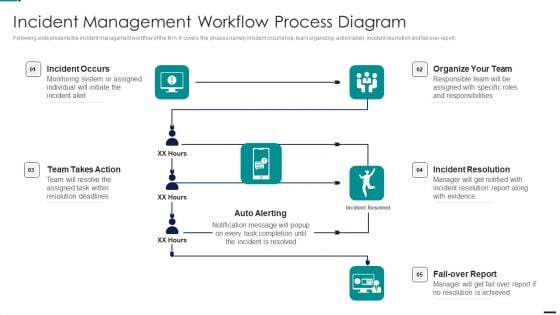
Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Incident Occurs, Organize Team, Incident Resolution, Fail Over Report, Auto Alerting, Team Takes Action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
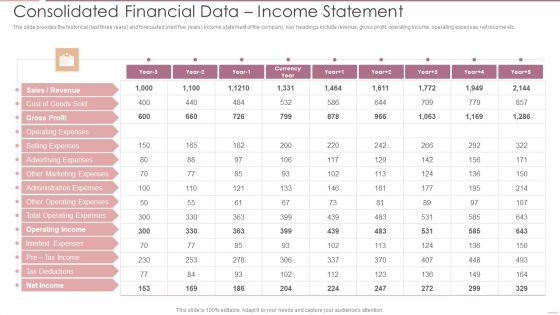
Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF
The slide provides the historical last three years and forecasted next five years income statement of the company. Key headings include revenue, gross profit, operating income, operating expenses, net income etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF Use them to share invaluable insights on Gross Profit, Operating Expenses, Advertising Expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
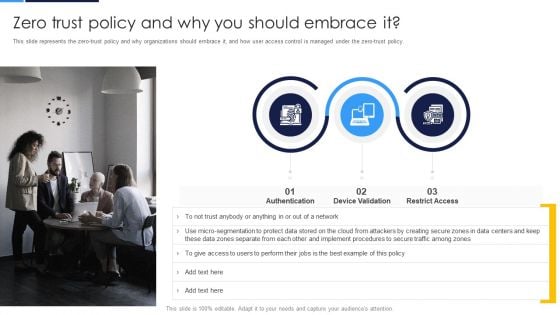
Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF
This slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy.This is a Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Best Example, Authentication, Implement Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Dispose Data And Equipment Properly Ppt Infographics Styles PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting information security dispose data and equipment properly ppt infographics styles pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
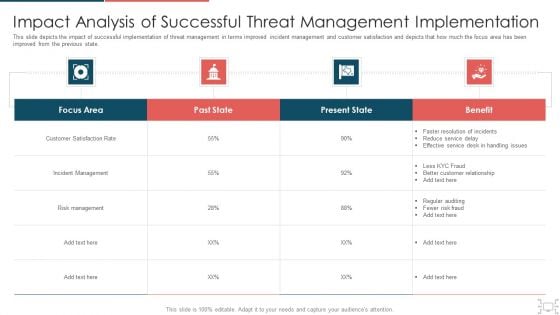
Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
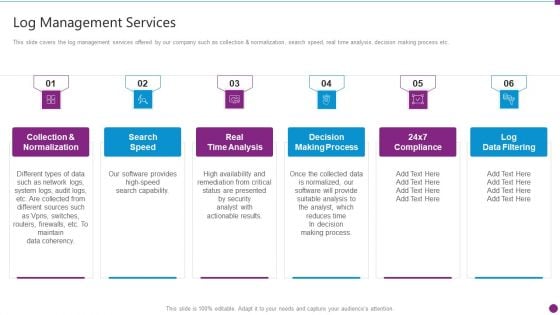
Security Information And Event Management Strategies For Financial Audit And Compliance Log Management Services Microsoft PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. This is a security information and event management strategies for financial audit and compliance log management services microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collection and normalization, search speed, real time analysis, decision making process, log data filtering. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Control Techniques For Real Estate Project Ppt PowerPoint Presentation Complete Deck With Slides
This Security Control Techniques For Real Estate Project Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This Fifty one slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence.
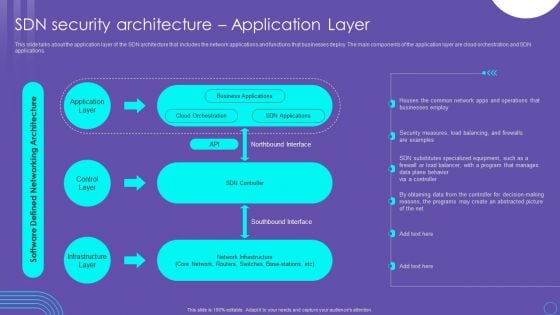
SDN Security Architecture Application Layer Ppt PowerPoint Presentation File Inspiration PDF
This slide talks about the application layer of the SDN architecture that includes the network applications and functions that businesses deploy. The main components of the application layer are cloud orchestration and SDN applications. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit SDN Security Architecture Application Layer Ppt PowerPoint Presentation File Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Major Components, Criticality Rating, Failure Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
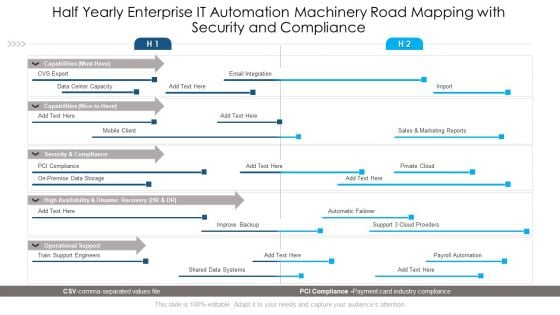
Half Yearly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Inspiration
Introducing our half yearly enterprise it automation machinery road mapping with security and compliance inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Project Security Administration IT Different Modes Of Coordination For Project Management Professional PDF
This slide provides information about different ways by which the firm can coordinate with its partners about project. The coordination can be of electronic mode like through email, etc. Deliver an awe inspiring pitch with this creative project security administration it different modes of coordination for project management professional pdf bundle. Topics like group mode of coordination, individual mode of coordination, electronic mode of coordination, impersonal mode of coordination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
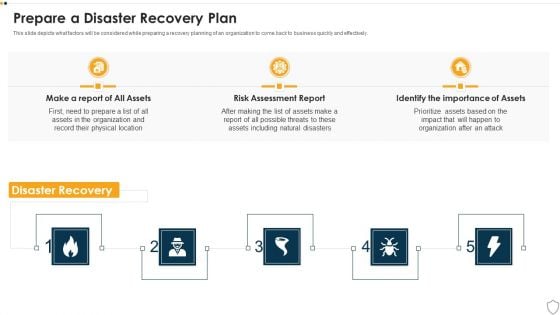
IT Security Prepare A Disaster Recovery Plan Ppt Show Templates PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a it security prepare a disaster recovery plan ppt show templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.This is a Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Categorization, Incident Resolution, Incident Prioritization You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
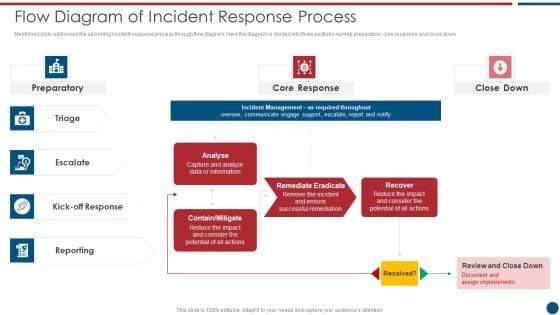
Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
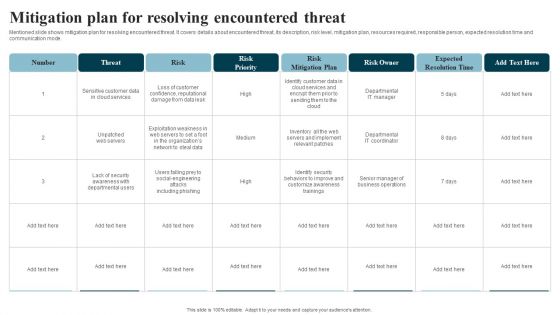
Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
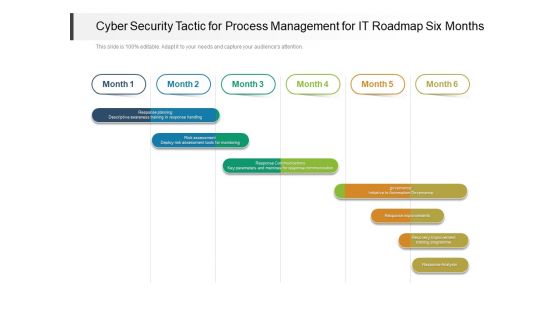
Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
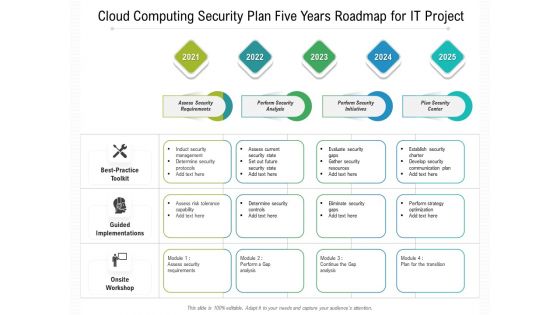
Cloud Computing Security Plan Five Years Roadmap For IT Project Slides
Presenting the cloud computing security plan five years roadmap for it project slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.


 Continue with Email
Continue with Email

 Home
Home


































