Technology Security
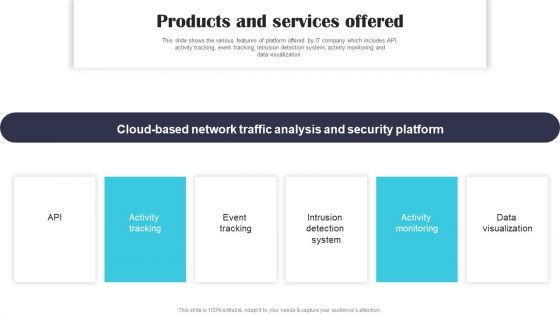
Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF
This slide shows the various features of platform offered by IT company which includes API, activity tracking, event tracking, intrusion detection system, activity monitoring and data visualization. This modern and well arranged Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
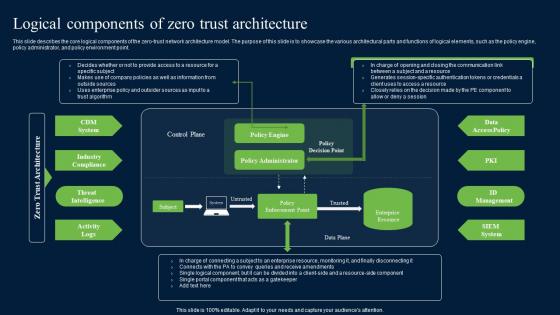
Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
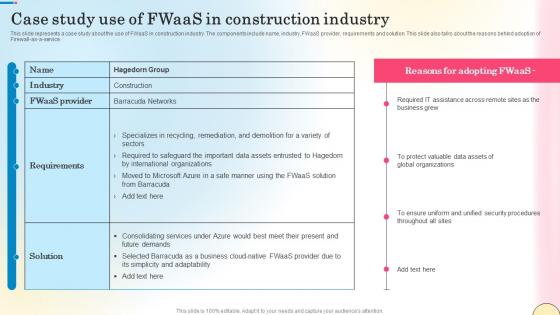
Case Study Use Of Fwaas In Construction Industry Network Security Guidelines Pdf
This slide represents a case study about the use of FWaaS in construction industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the reasons behind adoption of Firewall-as-a-service. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Case Study Use Of Fwaas In Construction Industry Network Security Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Case Study Use Of Fwaas In Construction Industry Network Security Guidelines Pdf today and make your presentation stand out from the rest This slide represents a case study about the use of FWaaS in construction industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the reasons behind adoption of Firewall-as-a-service.

Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf today and make your presentation stand out from the rest The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc.
Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black. Aim for the skies with our Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides. You will come out on top.
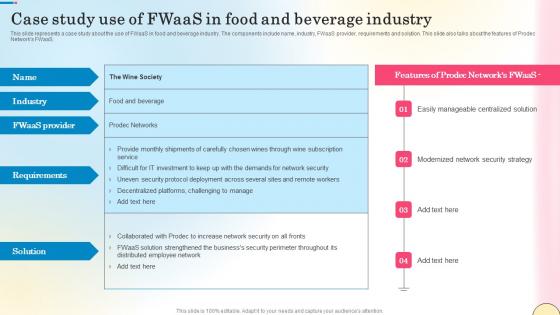
Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf
This slide represents a case study about the use of FWaaS in food and beverage industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the features of Prodec Networks FWaaS. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf can be your best option for delivering a presentation. Represent everything in detail using Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents a case study about the use of FWaaS in food and beverage industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the features of Prodec Networks FWaaS.

How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Get a simple yet stunning designed How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc.

House And Question Mark Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our House And Question Mark Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Network diagrams PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download our Communication PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune.Use these PowerPoint slides for presentations relating to Question mark with house,business, finance, success, signs, marketing . The prominent colors used in the PowerPoint template are Blue, Gray, Blue. Specify paths to success with our House And Question Mark Security PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.
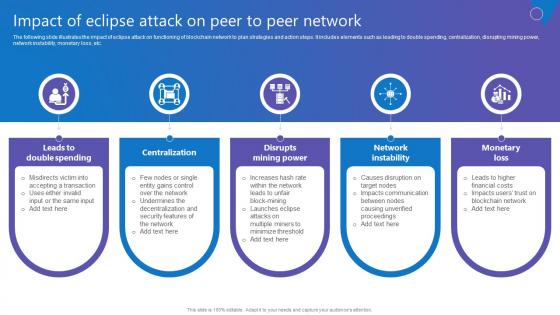
Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf today and make your presentation stand out from the rest The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc.
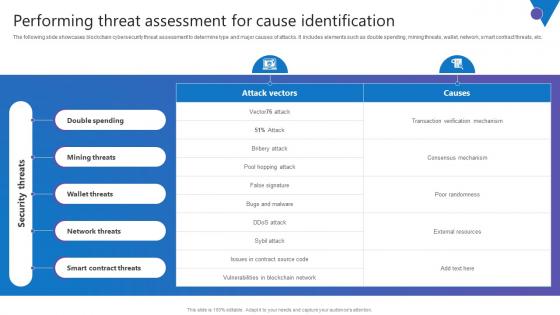
Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf
The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf. The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc.

Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112
We present our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because,You too have got the framework of your companys growth in place. Use our Success PowerPoint Templates because, You can Transmit this concern to your staff using our helpful slides. Use our Puzzles or jigsaws PowerPoint Templates because,We all know that alphabetical order is a time honoured concept. Use our Shapes PowerPoint Templates because,you can put it up there for all to see. Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Key chain tied with puzzle piece, business, success, puzzles or jigsaws, shapes, marketing. The prominent colors used in the PowerPoint template are Yellow, Black, Red Engineer growth with our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112. Download without worries with our money back guaranteee.

Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc.

Risk Procedure Security Threads Ppt PowerPoint Presentation Complete Deck With Slides
This risk procedure security threads ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing eleven slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this risk procedure security threads ppt powerpoint presentation complete deck with slides PPT slideshow.

IT Security Awareness Training Program Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this IT Security Awareness Training Program Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty four slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
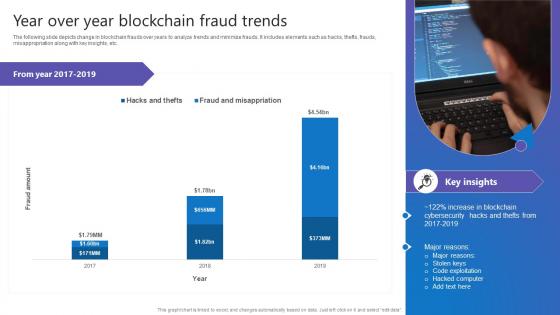
Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf
The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf can be your best option for delivering a presentation. Represent everything in detail using Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc.
Collection Of Interrelated Tasks 6 Stages Security Business Plan PowerPoint Slides
We present our collection of interrelated tasks 6 stages security business plan PowerPoint Slides.Download and present our Arrows PowerPoint Templates because You will get more than you ever bargained for. Download our Circle Charts PowerPoint Templates because It can Bubble and burst with your ideas. Present our Shapes PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Download and present our Business PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Download and present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team.Use these PowerPoint slides for presentations relating to arrow, circular, process, round, flow, business, vector, graphic, part, green, red, concept, yellow, presentation, symbol, circle, orange, repeat, cycle, illustration, icon, pink, six, purple, blue, repetitive. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Rule the roost with our Collection Of Interrelated Tasks 6 Stages Security Business Plan PowerPoint Slides. They will enthrone your thoughts.

Security Control Techniques For Real Estate Project Key Goals Of Construction Site Safety Program Professional PDF
This slide indicates the major focus areas for the construction site safety program. It also includes details of multiple program goals such as setting up safety department, identifying hazards and conduct impact, setting up control measures to prevent hazards, and impart safety training. Boost your pitch with our creative Security Control Techniques For Real Estate Project Key Goals Of Construction Site Safety Program Professional PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you donot have to invest time in any additional work. Just grab the template now and use them.

Core Elements And Recommended Workplace Safety Protocol And Security Practices Download Pdf
This slide highlights the recommended practices for safety management at organization level which includes management leadership, worker participation, hazard identification and prevention and education and training program. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Core Elements And Recommended Workplace Safety Protocol And Security Practices Download Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide highlights the recommended practices for safety management at organization level which includes management leadership, worker participation, hazard identification and prevention and education and training program.
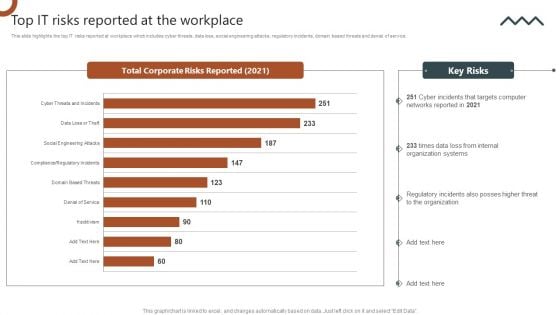
Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Comprehensive Guide For Website Development Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup This modern and well-arranged Comprehensive Guide For Website Development Best Practices For Web Security Management provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup
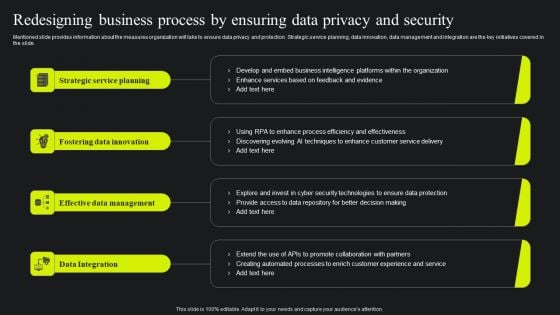
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Slidegeeks is here to make your presentations a breeze with Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Security Control Techniques For Real Estate Project Budget Plan For Construction Site Safety Program Microsoft PDF
The purpose of this slide is to highlight the budget plan for the construction site safety program. It includes details regarding the breakup of multiple costs, such as equipment and training costs along with the units required, cost per unit and total cost. This slide showcase the major barriers to successfully implement of construction site safety program such as limited awareness, limited employee participation, insufficient legislation, and behavioral rigidity. It also contains details of recommended solutions to overcome them. Make sure to capture your audiences attention in your business displays with our gratis customizable Security Control Techniques For Real Estate Project Budget Plan For Construction Site Safety Program Microsoft PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Pictograms To Specify Details Workplace Safety Protocol And Security Practices Download Pdf
This slide highlights the pictograms of chemical hazards which showcase health hazard, flame, exclamation mark, gas cylinder, exploding bomb, cross bones to alert the workers. This Pictograms To Specify Details Workplace Safety Protocol And Security Practices Download Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the pictograms of chemical hazards which showcase health hazard, flame, exclamation mark, gas cylinder, exploding bomb, cross bones to alert the workers.

Safety Guidelines To Control Fire At Workplace Safety Protocol And Security Practices Microsoft Pdf
This slide highlights the measures to control fire at workplace which includes steps such as raise the alarm, alert everyone, fight fire and evacuate from the worksite. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Safety Guidelines To Control Fire At Workplace Safety Protocol And Security Practices Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights the measures to control fire at workplace which includes steps such as raise the alarm, alert everyone, fight fire and evacuate from the worksite.

Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
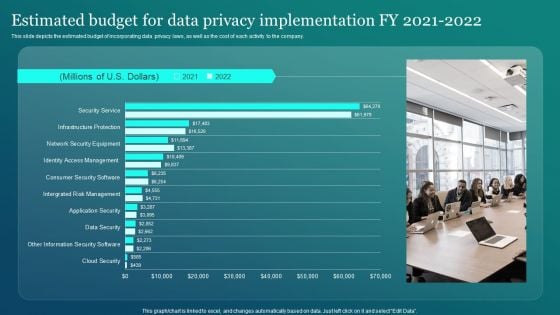
Information Security Estimated Budget For Data Privacy Implementation Fy 2021 2022 Graphics PDF
This slide depicts the estimated budget of incorporating data privacy laws, as well as the cost of each activity to the company. This Information Security Estimated Budget For Data Privacy Implementation Fy 2021 2022 Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
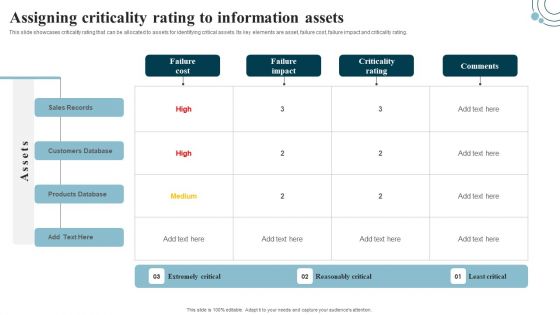
Developing IT Security Strategy Assigning Criticality Rating To Information Assets Ideas PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating. This modern and well-arranged Developing IT Security Strategy Assigning Criticality Rating To Information Assets Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
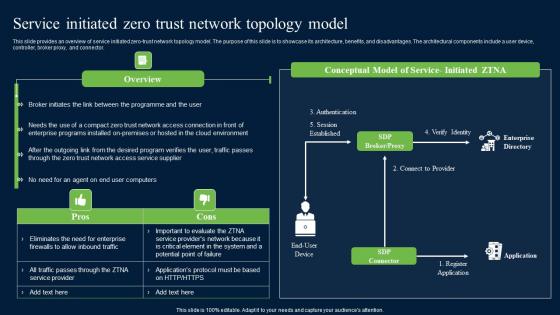
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
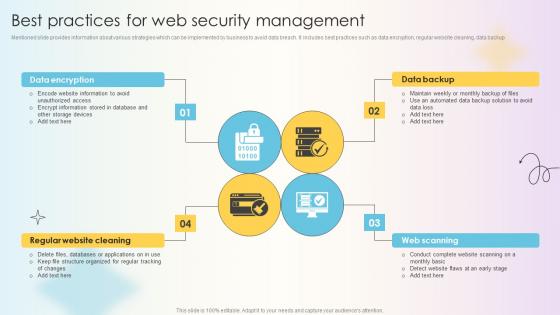
Managing Technical And Non Technical Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup Present like a pro with Managing Technical And Non Technical Best Practices For Web Security Management. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
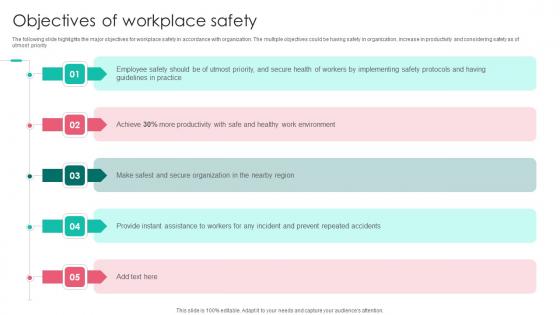
Objectives Of Workplace Safety Workplace Safety Protocol And Security Practices Ideas Pdf
The following slide highlights the major objectives for workplace safety in accordance with organization. The multiple objectives could be having safety in organization, increase in productivity and considering safety as of utmost priority. Slidegeeks has constructed Objectives Of Workplace Safety Workplace Safety Protocol And Security Practices Ideas Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. The following slide highlights the major objectives for workplace safety in accordance with organization. The multiple objectives could be having safety in organization, increase in productivity and considering safety as of utmost priority.
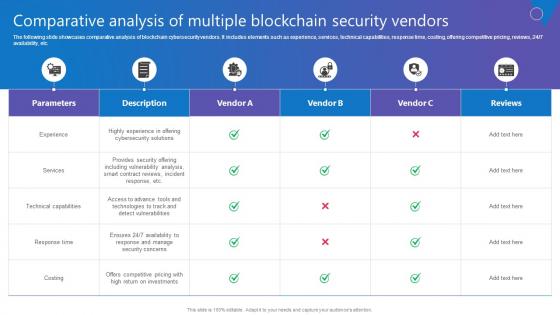
Comparative Analysis Multiple Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc. Do you know about Slidesgeeks Comparative Analysis Multiple Comprehensive Guide To Blockchain Digital Security Introduction Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc.
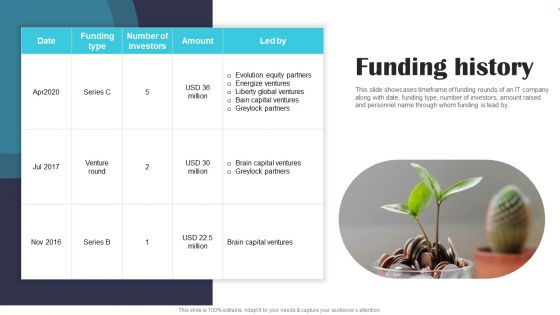
Security Software Company Investor Funding Pitch Deck Funding History Portrait PDF
This slide showcases timeframe of funding rounds of an IT company along with date, funding type, number of investors, amount raised and personnel name through whom funding is lead by. Slidegeeks is here to make your presentations a breeze with Security Software Company Investor Funding Pitch Deck Funding History Portrait PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
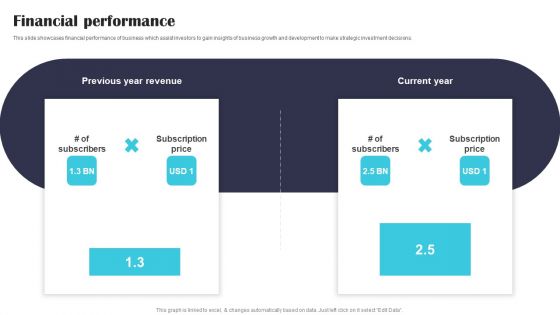
Security Software Company Investor Funding Pitch Deck Financial Performance Formats PDF
This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Software Company Investor Funding Pitch Deck Financial Performance Formats PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
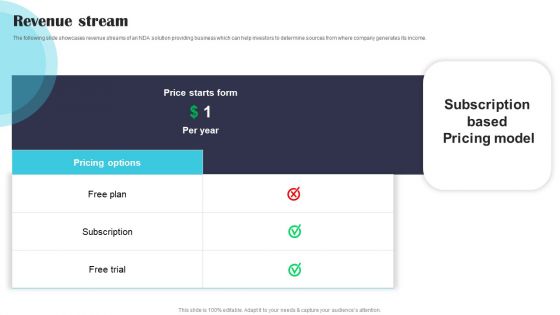
Security Software Company Investor Funding Pitch Deck Revenue Stream Demonstration PDF
The following slide showcases revenue streams of an NDA solution providing business which can help investors to determine sources from where company generates its income. Welcome to our selection of the Security Software Company Investor Funding Pitch Deck Revenue Stream Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Problem Related Drug Alcohol Abuse Workplace Safety Protocol And Security Practices Brochure Pdf
The following slide highlights the problems with excessive drug and alcohol at workplace which showcases the alcohol abuse leads to multiple problems and major drinking habits that creates issues for work. Take your projects to the next level with our ultimate collection of Problem Related Drug Alcohol Abuse Workplace Safety Protocol And Security Practices Brochure Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide highlights the problems with excessive drug and alcohol at workplace which showcases the alcohol abuse leads to multiple problems and major drinking habits that creates issues for work.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides
This presentation deck enables you to communicate the message, idea, and proposal to your audience in a clear and effective manner. The slides of this PowerPoint Bundle are professional and visually appealing, engaging your audience and gaining their heartful interest in your content. In addition to its spectacular design, this PPT deck is easy to use and altered to fit the specific needs of the user. All fifty one slides in this set are compatible with multiple data handling and presentation platforms like Google Slides, MS Excel, Tableau, etc., so you can present your information hassle free. Begin your journey to tremendous success using our Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides in many settings, including meetings, pitches, and conference presentations In fact, customer testimonials.

Safety Guidelines Detect Prevent Alcohol Workplace Safety Protocol And Security Practices Clipart Pdf
This slide highlights the preventive and detective measures for alcohol abuse which showcase multiple ways to deal the situation with training program, and experts assistance. Boost your pitch with our creative Safety Guidelines Detect Prevent Alcohol Workplace Safety Protocol And Security Practices Clipart Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the preventive and detective measures for alcohol abuse which showcase multiple ways to deal the situation with training program, and experts assistance.
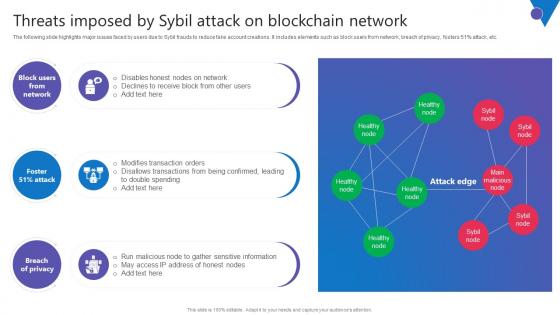
Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc.

Data Security Audit Questionnaire Ppt PowerPoint Presentation Complete Deck With Slides Survey
Boost your confidence and team morale with this well-structured Data Security Audit Questionnaire Ppt PowerPoint Presentation Complete Deck With Slides Survey. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of six slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
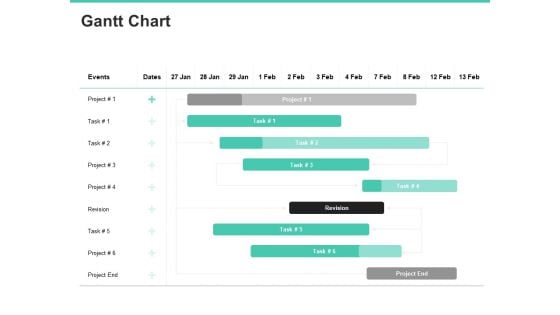
Email Security Encryption And Data Loss Prevention Gantt Chart Information PDF
Your complex projects can be managed and organized simultaneously using this detailed email security encryption and data loss prevention gantt chart information pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well-crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.
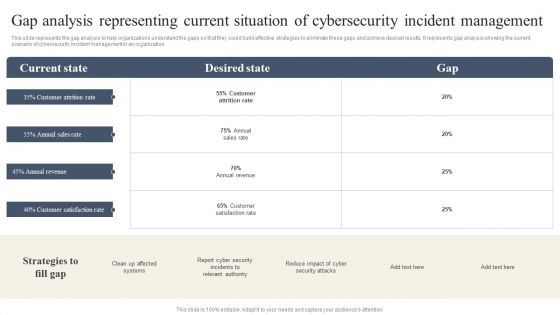
CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Slidegeeks has constructed CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
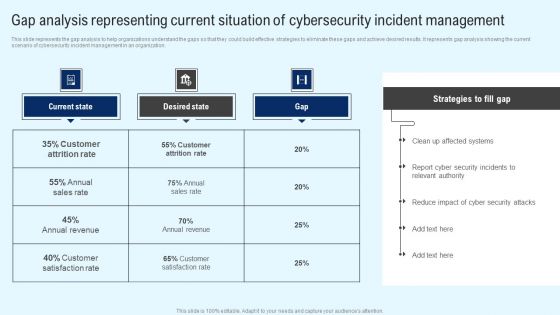
Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Retrieve professionally designed Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Overview And Workflow Process Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Overview And Workflow Process Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks and deliver a wonderful presentation. The following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc.
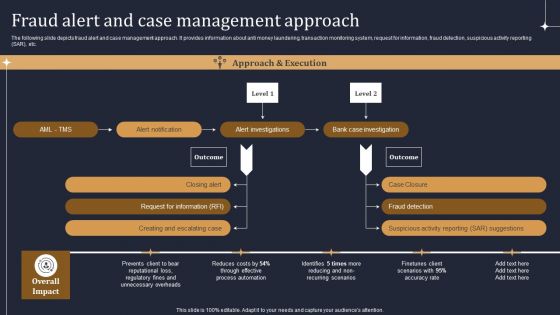
KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF
The following slide depicts fraud alert and case management approach. It provides information about anti money laundering, transaction monitoring system, request for information, fraud detection, suspicious activity reporting SAR, etc. The KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

IT Security Risk Management Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured IT Security Risk Management Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
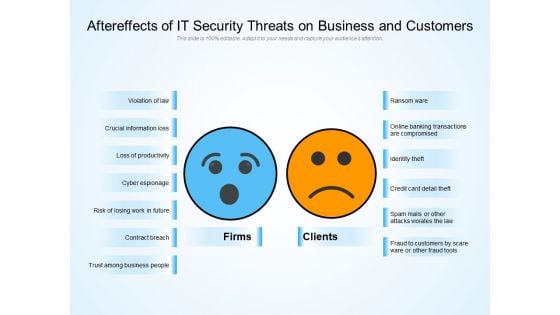
Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Communication Plan Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this IT Security Communication Plan Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the seventeen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
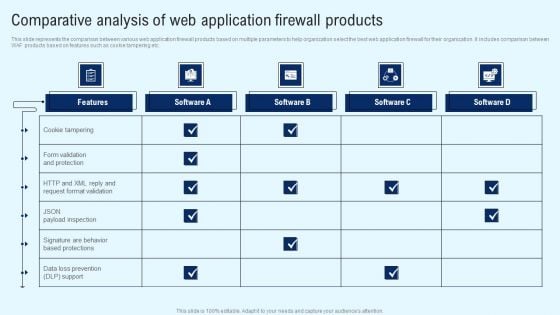
Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
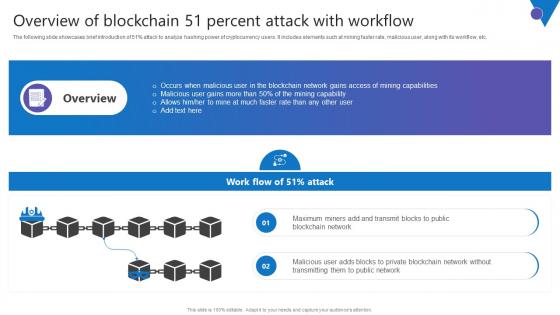
Overview Of Blockchain 51 Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Slidegeeks has constructed Overview Of Blockchain 51 Comprehensive Guide To Blockchain Digital Security Information Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. The following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc.
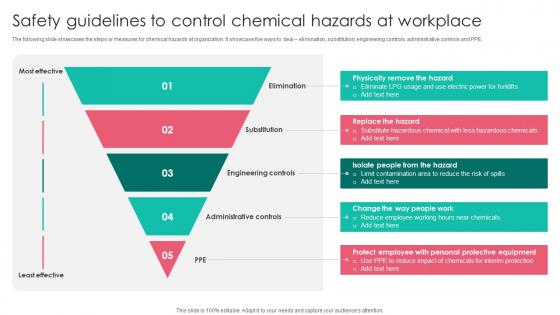
Safety Guidelines Control Chemical Workplace Safety Protocol And Security Practices Portrait Pdf
The following slide showcases the steps or measures for chemical hazards at organization. It showcase five ways to deal elimination, substitution, engineering controls, administrative controls and PPE.Find a pre designed and impeccable Safety Guidelines Control Chemical Workplace Safety Protocol And Security Practices Portrait Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide showcases the steps or measures for chemical hazards at organization. It showcase five ways to deal elimination, substitution, engineering controls, administrative controls and PPE.
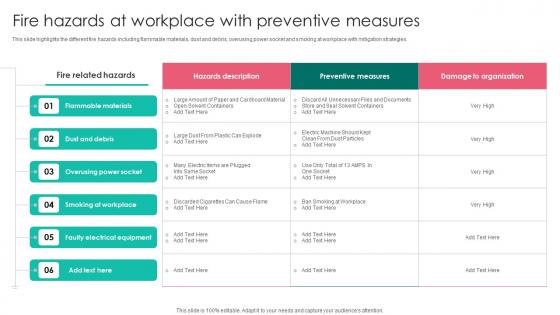
Fire Hazards At Workplace With Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide highlights the different fire hazards including flammable materials, dust and debris, overusing power socket and smoking at workplace with mitigation strategies. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fire Hazards At Workplace With Workplace Safety Protocol And Security Practices Demonstration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights the different fire hazards including flammable materials, dust and debris, overusing power socket and smoking at workplace with mitigation strategies.
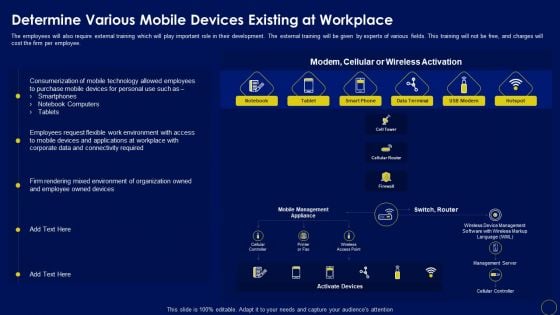
Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Do you know about Slidesgeeks Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Information Security Accountability Principle Of GDPR Law Ppt PowerPoint Presentation File Backgrounds PDF
This slide shows the accountability principle, which implies that the data controller or organization is responsible for adhering to all the standards of GDPR and showing compliance if required. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Information Security Accountability Principle Of GDPR Law Ppt PowerPoint Presentation File Backgrounds PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
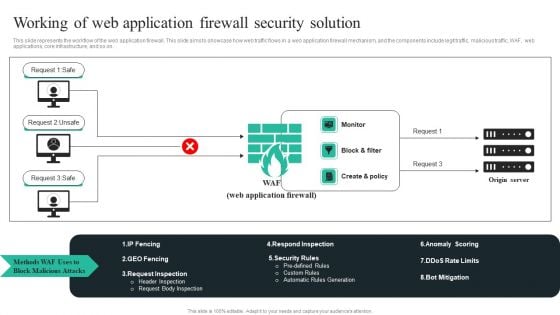
WAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF
This slide represents the workflow of the web application firewall. This slide aims to showcase how web traffic flows in a web application firewall mechanism, and the components include legit traffic, malicious traffic, WAF, web applications, core infrastructure, and so on. Take your projects to the next level with our ultimate collection ofWAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
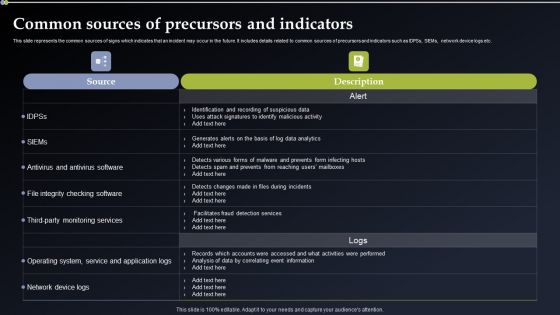
Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
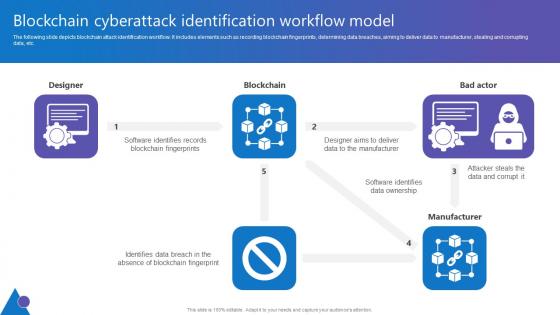
Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf
The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Take your projects to the next level with our ultimate collection of Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc.

Hotel Protection And Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Hotel Protection And Security Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of eleven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































