Theft

Key Considerations For Filing Steps By Step Guide For Claiming Car PPT Example
The slide carries various points to be considered while filing the car theft claims such as getting no-trace report, collecting duplicate RC book, checking the documents, etc. along with the reasons for cancellation of claims such as late communication to insurer, invalid supporting documents, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Considerations For Filing Steps By Step Guide For Claiming Car PPT Example template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Considerations For Filing Steps By Step Guide For Claiming Car PPT Example that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The slide carries various points to be considered while filing the car theft claims such as getting no-trace report, collecting duplicate RC book, checking the documents, etc. along with the reasons for cancellation of claims such as late communication to insurer, invalid supporting documents, etc.
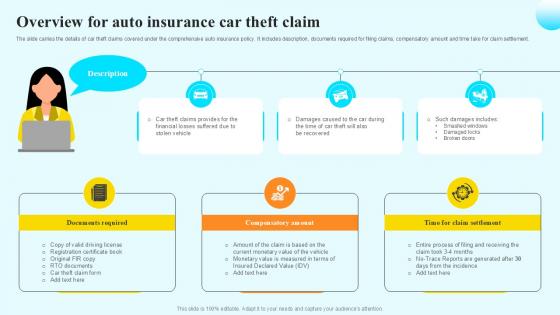
Overview For Auto Insurance Steps By Step Guide For Claiming Car PPT Presentation
The slide carries the details of car theft claims covered under the comprehensive auto insurance policy. It includes description, documents required for filing claims, compensatory amount and time take for claim settlement. Presenting this PowerPoint presentation, titled Overview For Auto Insurance Steps By Step Guide For Claiming Car PPT Presentation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Overview For Auto Insurance Steps By Step Guide For Claiming Car PPT Presentation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Overview For Auto Insurance Steps By Step Guide For Claiming Car PPT Presentation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The slide carries the details of car theft claims covered under the comprehensive auto insurance policy. It includes description, documents required for filing claims, compensatory amount and time take for claim settlement.
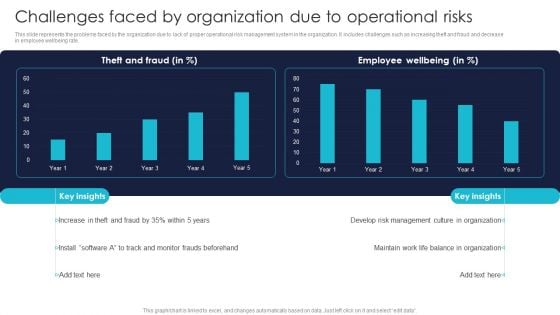
Challenges Faced By Organization Due To Operational Risks Professional PDF
This slide represents the problems faced by the organization due to lack of proper operational risk management system in the organization. It includes challenges such as increasing theft and fraud and decrease in employee wellbeing rate. Create an editable Challenges Faced By Organization Due To Operational Risks Professional PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Challenges Faced By Organization Due To Operational Risks Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
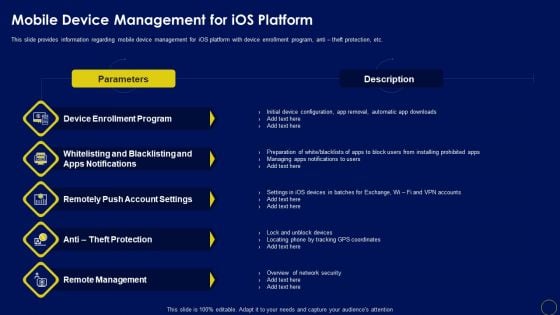
Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF today and make your presentation stand out from the rest.

Workplace Portable Device Monitoring And Administration Mobile Device Management For Ios Platform Elements PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Are you searching for a Workplace Portable Device Monitoring And Administration Mobile Device Management For Ios Platform Elements PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Workplace Portable Device Monitoring And Administration Mobile Device Management For Ios Platform Elements PDF from Slidegeeks today.
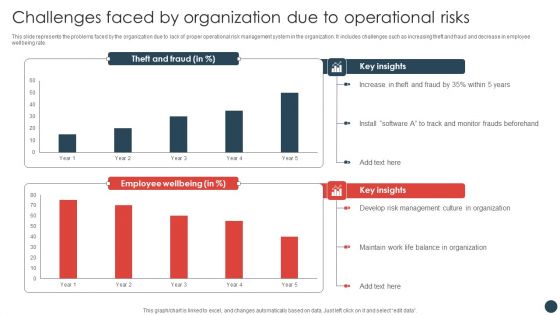
Strategic Risk Management Plan Challenges Faced By Organization Due To Operational Risks Elements PDF
This slide represents the problems faced by the organization due to lack of proper operational risk management system in the organization. It includes challenges such as increasing theft and fraud and decrease in employee wellbeing rate.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Strategic Risk Management Plan Challenges Faced By Organization Due To Operational Risks Elements PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
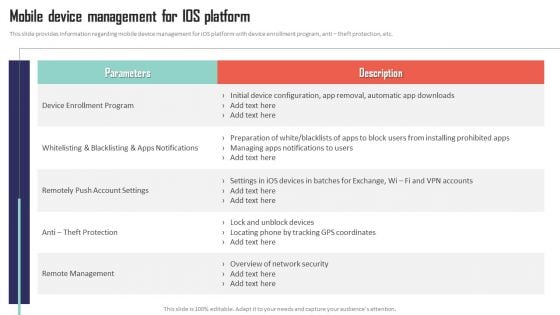
Mobile Device Management Mobile Device Management For Ios Platform Portrait PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Find highly impressive Mobile Device Management Mobile Device Management For Ios Platform Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Mobile Device Management Mobile Device Management For Ios Platform Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
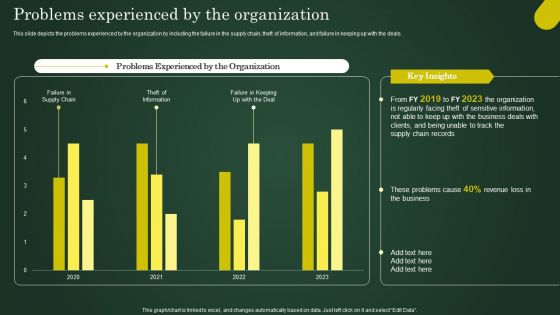
Problems Experienced By The Organization Involving Cryptographic Ledger To Enhance Introduction PDF
This slide depicts the problems experienced by the organization by including the failure in the supply chain, theft of information, and failure in keeping up with the deals. Retrieve professionally designed Problems Experienced By The Organization Involving Cryptographic Ledger To Enhance Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
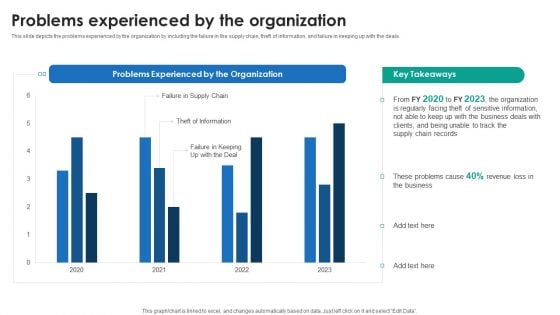
P2P Ledger Problems Experienced By The Organization Slides PDF
This slide depicts the problems experienced by the organization by including the failure in the supply chain, theft of information, and failure in keeping up with the deals. This P2P Ledger Problems Experienced By The Organization Slides PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
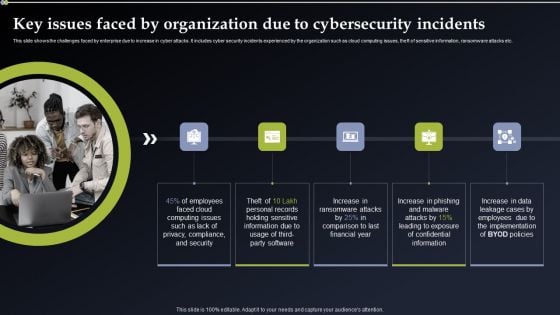
Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
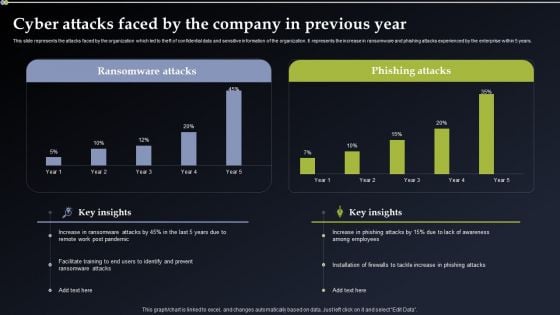
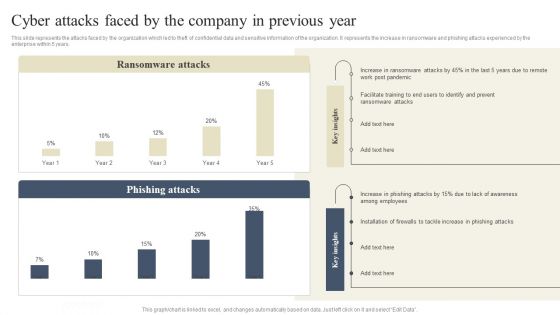
Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

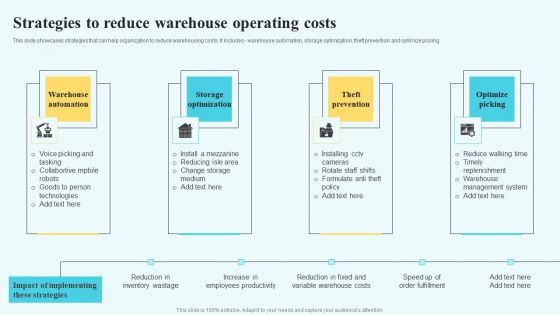
Strategic Guidelines To Administer Strategies To Reduce Warehouse Operating Costs Clipart PDF
This slide showcases strategies that can help organization to reduce warehousing costs. It includes - warehouse automation, storage optimization, theft prevention and optimize picking. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategic Guidelines To Administer Strategies To Reduce Warehouse Operating Costs Clipart PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategic Guidelines To Administer Strategies To Reduce Warehouse Operating Costs Clipart PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Mobile Device Management For Improving IT Operations Mobile Device Management For IOS Clipart PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Mobile Device Management For Improving IT Operations Mobile Device Management For IOS Clipart PDF can be your best option for delivering a presentation. Represent everything in detail using Mobile Device Management For Improving IT Operations Mobile Device Management For IOS Clipart PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

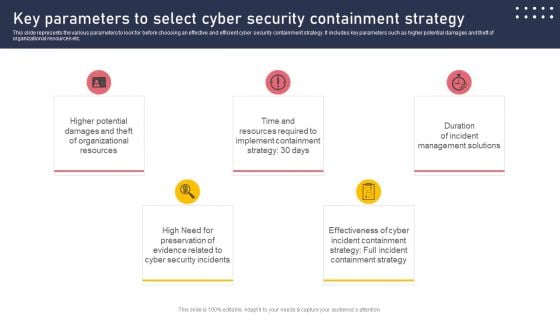
Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Present like a pro with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
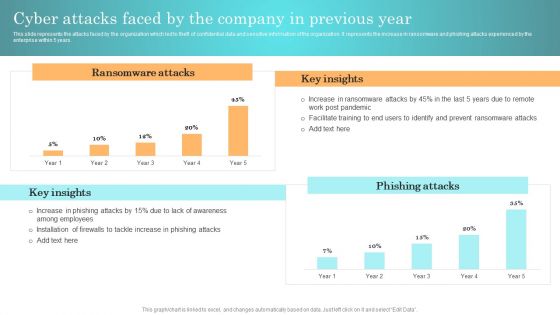
Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Adopting Multiple Tactics To Improve Inventory Optimization Strategies To Reduce Warehouse Operating Costs Portrait PDF
This slide showcases strategies that can help organization to reduce warehousing costs. It includes - warehouse automation, storage optimization, theft prevention and optimize picking Get a simple yet stunning designed Adopting Multiple Tactics To Improve Inventory Optimization Strategies To Reduce Warehouse Operating Costs Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Adopting Multiple Tactics To Improve Inventory Optimization Strategies To Reduce Warehouse Operating Costs Portrait PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

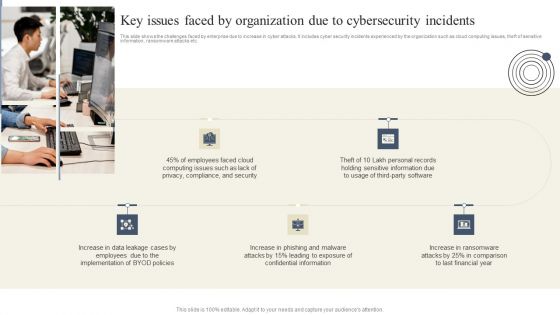
Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Slidegeeks is here to make your presentations a breeze with Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
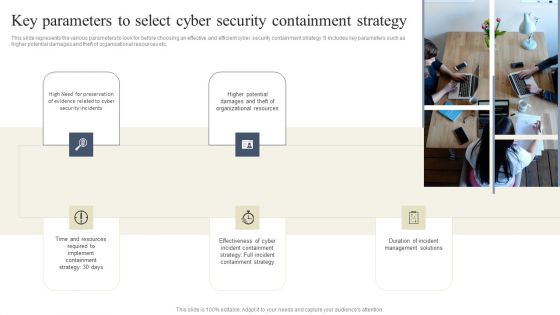
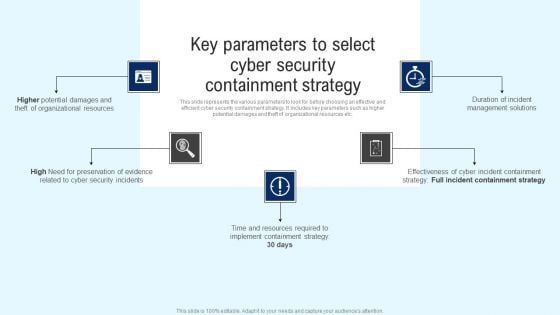
Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Create an editable Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
CYBER Security Breache Response Strategy Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Take your projects to the next level with our ultimate collection of CYBER Security Breache Response Strategy Key Parameters To Select Cyber Security Containment Strategy Information PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
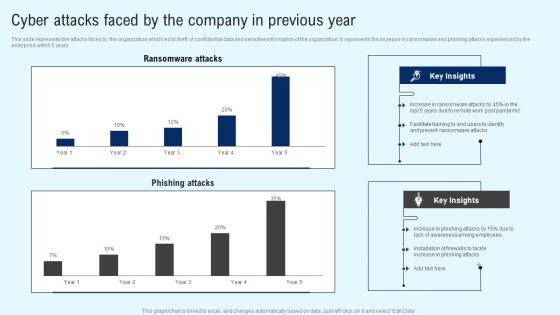
Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
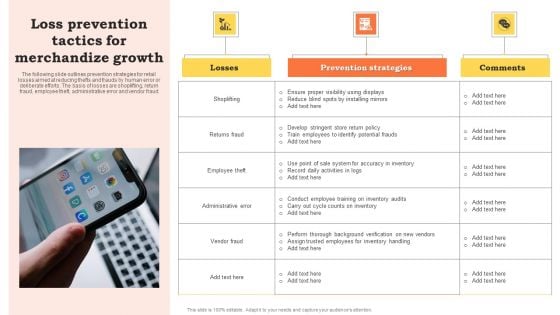
Loss Prevention Tactics For Merchandize Growth Introduction PDF
The following slide outlines prevention strategies for retail losses aimed at reducing thefts and frauds by human error or deliberate efforts. The basis of losses are shoplifting, return fraud, employee theft, administrative error and vendor fraud. Presenting Loss Prevention Tactics For Merchandize Growth Introduction PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Losses, Prevention Strategies, Comments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
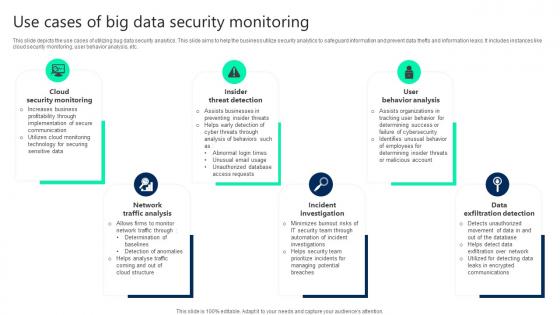
Use Cases Of Big Data Security Monitoring Clipart pdf
This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc. Pitch your topic with ease and precision using this Use Cases Of Big Data Security Monitoring Clipart pdf. This layout presents information on Cloud Security Monitoring, Insider Threat Detection, User Behavior Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc.
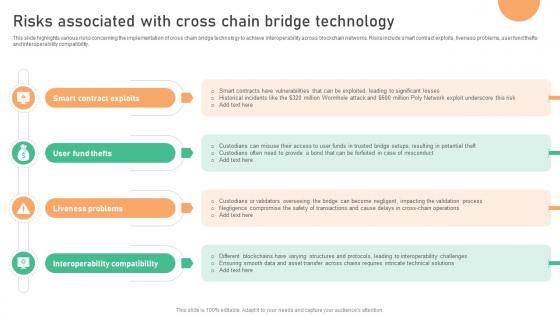
Seamless Integration The Power Risks Associated With Cross Chain Bridge Technology BCT SS V
This slide highlights various risks concerning the implementation of cross chain bridge technology to achieve interoperability across blockchain networks. Risks include smart contract exploits, liveness problems, user fund thefts and interoperability compatibility. Create an editable Seamless Integration The Power Risks Associated With Cross Chain Bridge Technology BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Seamless Integration The Power Risks Associated With Cross Chain Bridge Technology BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide highlights various risks concerning the implementation of cross chain bridge technology to achieve interoperability across blockchain networks. Risks include smart contract exploits, liveness problems, user fund thefts and interoperability compatibility.

Understanding Various Blockchain Risks Associated With Cross Chain Bridge Technology BCT SS V
This slide highlights various risks concerning the implementation of cross chain bridge technology to achieve interoperability across blockchain networks. Risks include smart contract exploits, liveness problems, user fund thefts and interoperability compatibility. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Understanding Various Blockchain Risks Associated With Cross Chain Bridge Technology BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights various risks concerning the implementation of cross chain bridge technology to achieve interoperability across blockchain networks. Risks include smart contract exploits, liveness problems, user fund thefts and interoperability compatibility.

Bridging Blockchains A Deep Risks Associated With Cross Chain Bridge Technology BCT SS V
This slide highlights various risks concerning the implementation of cross chain bridge technology to achieve interoperability across blockchain networks. Risks include smart contract exploits, liveness problems, user fund thefts and interoperability compatibility. Boost your pitch with our creative Bridging Blockchains A Deep Risks Associated With Cross Chain Bridge Technology BCT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights various risks concerning the implementation of cross chain bridge technology to achieve interoperability across blockchain networks. Risks include smart contract exploits, liveness problems, user fund thefts and interoperability compatibility.
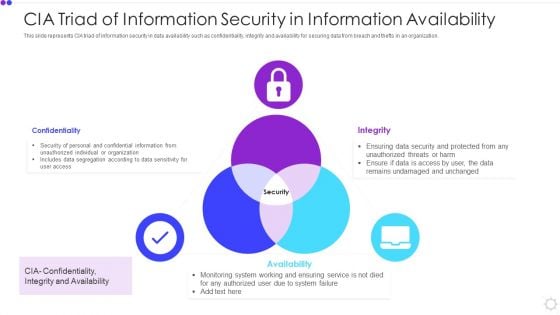
Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Solutions To Overcome Employee Management Challenges At Retail Store Retail Outlet Operations Clipart PDF
This slide illustrates the recommended solutions to overcome employee management challenges in retail store such as offer competitive salaries, conduct background checks, deploy HR software etc.Deliver an awe inspiring pitch with this creative Solutions To Overcome Employee Management Challenges At Retail Store Retail Outlet Operations Clipart PDF bundle. Topics like Turnover Rate, Employee Engagement, Employees Thefts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
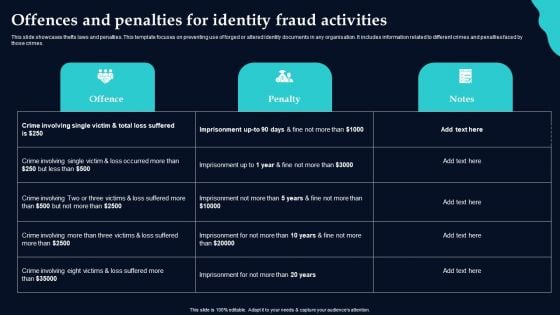
Offences And Penalties For Identity Fraud Activities Designs PDF
This slide showcases thefts laws and penalties. This template focuses on preventing use of forged or altered identity documents in any organisation. It includes information related to different crimes and penalties faced by those crimes. Showcasing this set of slides titled Offences And Penalties For Identity Fraud Activities Designs PDF. The topics addressed in these templates are Offence, Penalty, Notes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Statistical Data For Identity Fraud Reports Icons PDF
This slide showcases identity thefts and frauds complaints in various years. This template focuses on providing layers of protection to customers digital identities and reduce risk of financial loss. It includes information related to consumer complainants, etc. Showcasing this set of slides titled Statistical Data For Identity Fraud Reports Icons PDF. The topics addressed in these templates are Poor Management Information, Lack Of Transparency, Protected Accounts. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
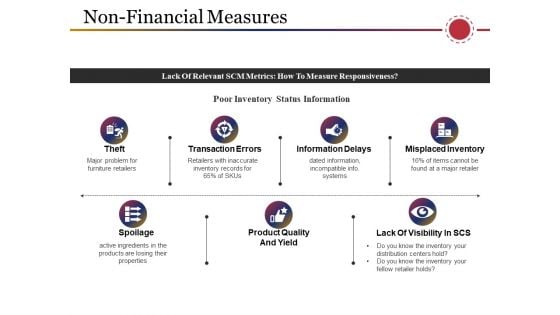
Non Financial Measures Template 4 Ppt PowerPoint Presentation Ideas Template
This is a non financial measures template 4 ppt powerpoint presentation ideas template. This is a seven stage process. The stages in this process are theft, spoilage, transaction errors, information delays, misplaced inventory.

Common Problems With Scm Template 1 Ppt PowerPoint Presentation Gallery Mockup
This is a common problems with scm template 1 ppt powerpoint presentation gallery mockup. This is a seven stage process. The stages in this process are theft, spoilage, transaction errors, information delays, misplaced inventory.
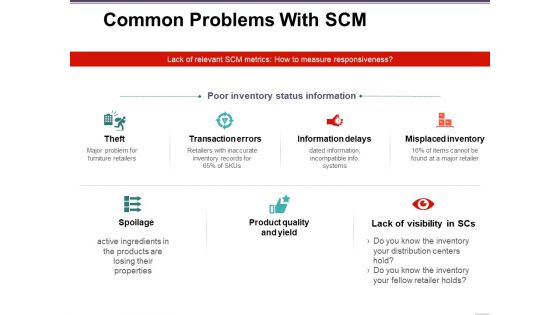
Common Problems With Scm Template 1 Ppt PowerPoint Presentation Gallery Background Images
This is a common problems with scm template 1 ppt powerpoint presentation gallery background images. This is a seven stage process. The stages in this process are theft, spoilage, transaction errors, information delays, misplaced inventory.
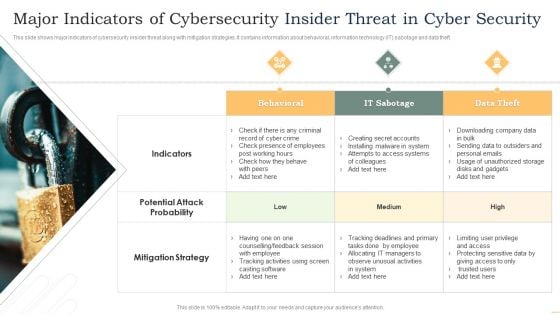
Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Processes Prior And Current Blockchain Technology Implementation Formats PDF
The slide highlights the improvements the blockchain integration brings in various processes. It includes cross-border payments, supply chain management, accountability issues and identity theft. Showcasing this set of slides titled Processes Prior And Current Blockchain Technology Implementation Formats PDF. The topics addressed in these templates are Accountability Issues, Supply Chain Management, Identity Theft. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
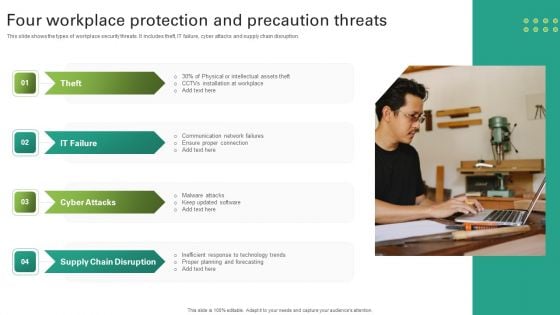
Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
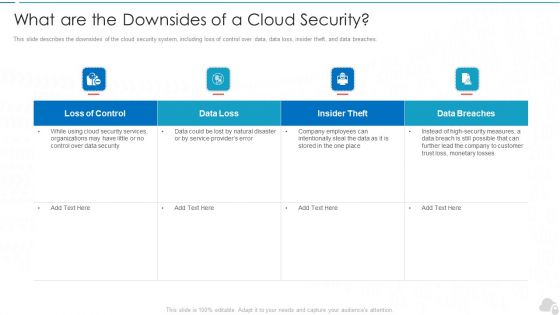
What Are The Downsides Of A Cloud Security Cloud Computing Security IT Ppt Summary Structure PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Deliver and pitch your topic in the best possible manner with this what are the downsides of a cloud security cloud computing security it ppt summary structure pdf. Use them to share invaluable insights on loss of control, data loss, insider theft, data breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Loss Control, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

What Are The Downsides Of A Cloud Security Download PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting What Are The Downsides Of A Cloud Security Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
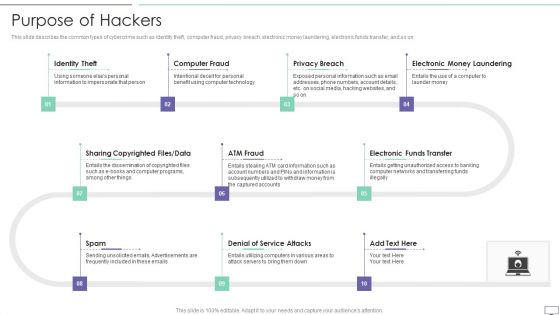
IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
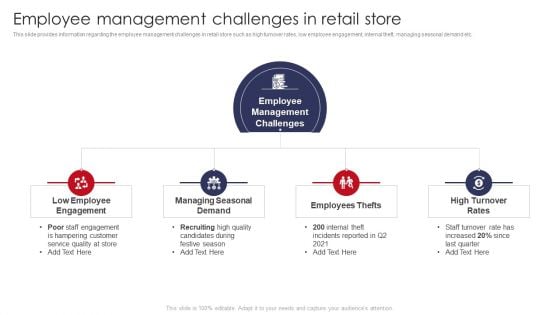
Employee Management Challenges In Retail Store Retail Outlet Operations Performance Evaluation Template PDF
This slide provides information regarding the employee management challenges in retail store such as high turnover rates, low employee engagement, internal theft, managing seasonal demand etc.Presenting Employee Management Challenges In Retail Store Retail Outlet Operations Performance Evaluation Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Employee Engagement, Managing Seasonal, Employees Thefts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
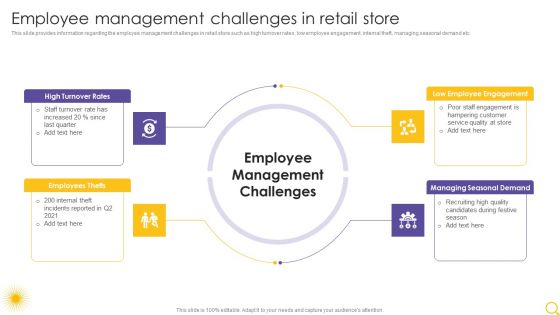
Retail Outlet Operational Efficiency Analytics Employee Management Challenges In Retail Store Template PDF
This slide provides information regarding the employee management challenges in retail store such as high turnover rates, low employee engagement, internal theft, managing seasonal demand etc. Presenting Retail Outlet Operational Efficiency Analytics Employee Management Challenges In Retail Store Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like High Turnover Rates, Employees Thefts, Low Employee Engagement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
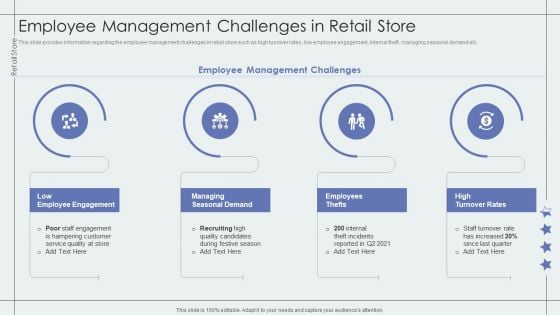
Employee Management Challenges In Retail Store Retail Outlet Performance Assessment Structure PDF
This slide provides information regarding the employee management challenges in retail store such as high turnover rates, low employee engagement, internal theft, managing seasonal demand etc.This is a Employee Management Challenges In Retail Store Retail Outlet Performance Assessment Structure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Engagement, Seasonal Demand, Employees Thefts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
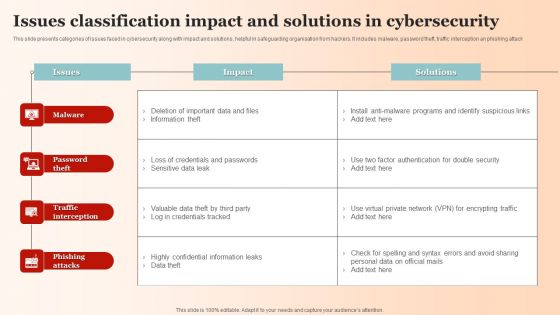
Issues Classification Impact And Solutions In Cybersecurity Pictures PDF
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack Pitch your topic with ease and precision using this Issues Classification Impact And Solutions In Cybersecurity Pictures PDF. This layout presents information on Malware, Password Theft, Traffic Interception. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
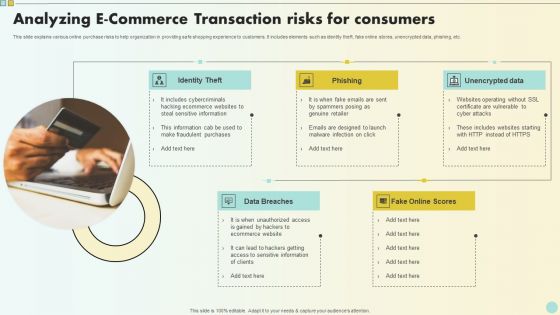
Analyzing E Commerce Transaction Risks For Consumers Clipart PDF
This slide explains various online purchase risks to help organization in providing safe shopping experience to customers. It includes elements such as identity theft, fake online stores, unencrypted data, phishing, etc. Presenting Analyzing E Commerce Transaction Risks For Consumers Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identity Theft, Phishing, Unencrypted Data . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
5G Network Security Technologies To Overcome Threats Icons Pdf
This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks. Showcasing this set of slides titled 5G Network Security Technologies To Overcome Threats Icons Pdf. The topics addressed in these templates are Security Threat, Impact, Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks.

Sales And Marketing Challenges Ppt PowerPoint Presentation Slides Demonstration
This is a sales and marketing challenges ppt powerpoint presentation slides demonstration. This is a six stage process. The stages in this process are salespeople reporting false, salespeople not reporting crucial information, sales reps short on sales skills, risk of duplication, no reliable automatic way to track sales, theft.

Ethical Framework Of Business With Leadership Commitment Ppt PowerPoint Presentation Outline Format PDF
Presenting this set of slides with name ethical framework of business with leadership commitment ppt powerpoint presentation outline format pdf. This is a four stage process. The stages in this process are bribery and theft, governance model, corrupt practises, leadership commitment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
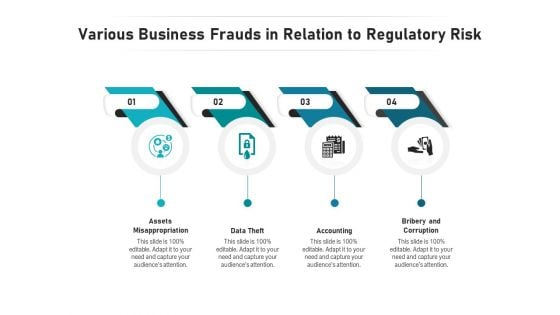
Various Business Frauds In Relation To Regulatory Risk Ppt PowerPoint Presentation Infographic Template Gridlines PDF
Presenting various business frauds in relation to regulatory risk ppt powerpoint presentation infographic template gridlines pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including assets misappropriation, data theft, accounting, bribery and corruption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Strategic Database Management Objectives To Attain Business Operational Objectives Topics PDF
Presenting Strategic Database Management Objectives To Attain Business Operational Objectives Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Integrity, Authenticity, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Store Workforce Assessment Retail Outlet Performance Assessment Infographics PDF
Deliver an awe inspiring pitch with this creative Store Workforce Assessment Retail Outlet Performance Assessment Infographics PDF bundle. Topics like Turnover Rate, Employee Thefts, Seasonal Workforce can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
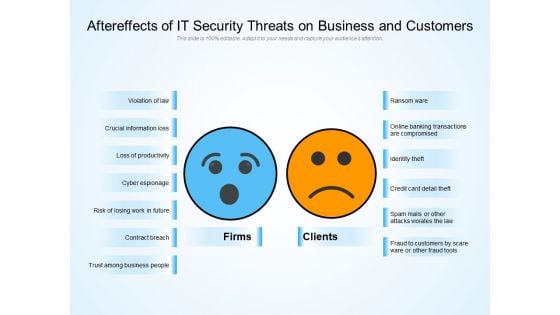
Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
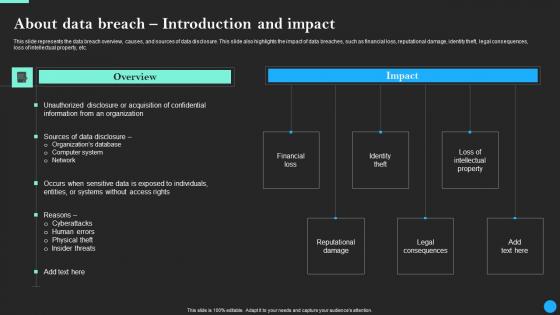
About Data Breach Introduction And Impact Data Breach Prevention Diagrams Pdf
This slide represents the data breach overview, causes, and sources of data disclosure. This slide also highlights the impact of data breaches, such as financial loss, reputational damage, identity theft, legal consequences, loss of intellectual property, etc. Boost your pitch with our creative About Data Breach Introduction And Impact Data Breach Prevention Diagrams Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the data breach overview, causes, and sources of data disclosure. This slide also highlights the impact of data breaches, such as financial loss, reputational damage, identity theft, legal consequences, loss of intellectual property, etc.
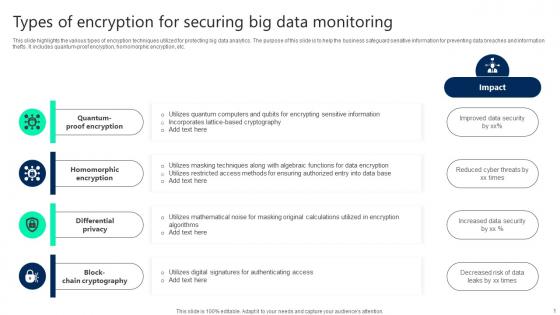
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.
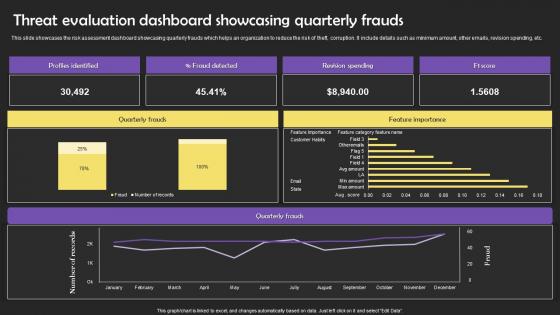
Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf
This slide showcases the risk assessment dashboard showcasing quarterly frauds which helps an organization to reduce the risk of theft, corruption. It include details such as minimum amount, other emails, revision spending, etc. Pitch your topic with ease and precision using this Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf This layout presents information on Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the risk assessment dashboard showcasing quarterly frauds which helps an organization to reduce the risk of theft, corruption. It include details such as minimum amount, other emails, revision spending, etc.

Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V
This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers. There are so many reasons you need a Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers.

Smart Home System Security Threats Utilizing Smart Appliances IoT SS V
This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Take your projects to the next level with our ultimate collection of Smart Home System Security Threats Utilizing Smart Appliances IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft.


 Continue with Email
Continue with Email

 Home
Home


































