Theft
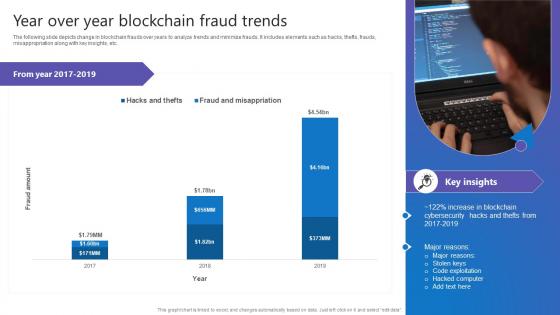
Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf
The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf can be your best option for delivering a presentation. Represent everything in detail using Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc.
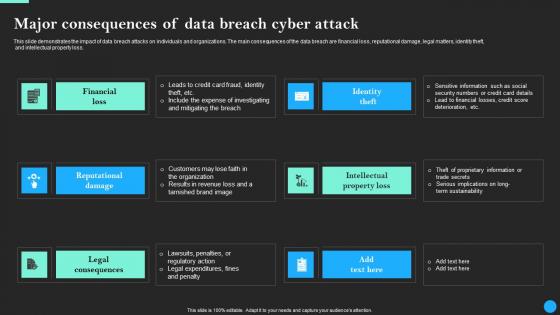
Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Presenting this PowerPoint presentation, titled Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss.
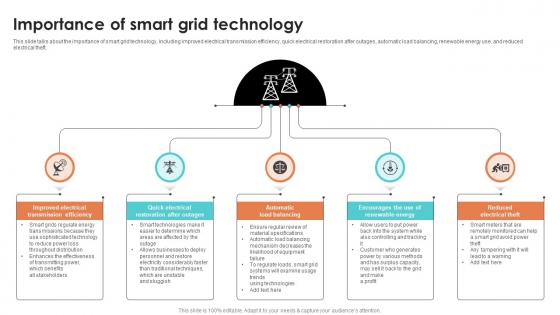
Importance Of Smart Grid Technology Smart Grid Working
This slide talks about the importance of smart grid technology, including improved electrical transmission efficiency, quick electrical restoration after outages, automatic load balancing, renewable energy use, and reduced electrical theft. If you are looking for a format to display your unique thoughts, then the professionally designed Importance Of Smart Grid Technology Smart Grid Working is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Importance Of Smart Grid Technology Smart Grid Working and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the importance of smart grid technology, including improved electrical transmission efficiency, quick electrical restoration after outages, automatic load balancing, renewable energy use, and reduced electrical theft.
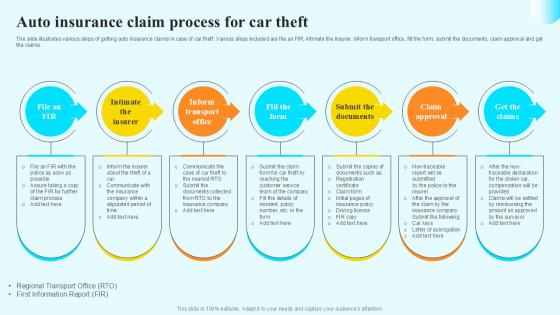
Auto Insurance Claim Process Steps By Step Guide For Claiming Car PPT PowerPoint
The slide illustrates various steps of getting auto insurance claims in case of car theft. Various steps included are file an FIR, intimate the insurer, inform transport office, fill the form, submit the documents, claim approval and get the claims. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Auto Insurance Claim Process Steps By Step Guide For Claiming Car PPT PowerPoint for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide illustrates various steps of getting auto insurance claims in case of car theft. Various steps included are file an FIR, intimate the insurer, inform transport office, fill the form, submit the documents, claim approval and get the claims.
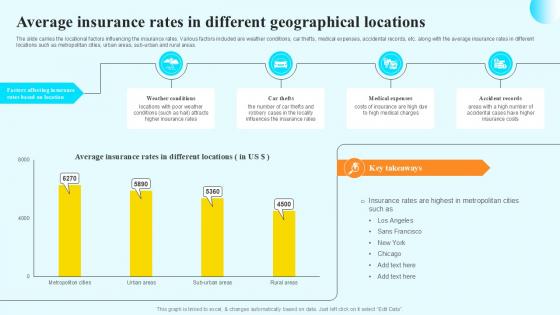
Average Insurance Rates In Different Steps By Step Guide For Claiming Car PPT Example
The slide carries the locational factors influencing the insurance rates. Various factors included are weather conditions, car thefts, medical expenses, accidental records, etc. along with the average insurance rates in different locations such as metropolitan cities, urban areas, sub-urban and rural areas. Get a simple yet stunning designed Average Insurance Rates In Different Steps By Step Guide For Claiming Car PPT Example. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Average Insurance Rates In Different Steps By Step Guide For Claiming Car PPT Example can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide carries the locational factors influencing the insurance rates. Various factors included are weather conditions, car thefts, medical expenses, accidental records, etc. along with the average insurance rates in different locations such as metropolitan cities, urban areas, sub-urban and rural areas.
Ppt 3d Constant Description To Prevent Business Losses Three Steps PowerPoint Templates
PPT 3d constant description to prevent business losses three steps PowerPoint Templates-The theme of this PowerPoint template is linear arrows. Use them to illustrate a stepwise process or a phase structure.-PPT 3d constant description to prevent business losses three steps PowerPoint Templates-Abstract, Background, Banking, Banknote, Business, Cash, Chain, Chained, Commerce, Commercial, Concept, Conceptual, Crime, Currency, Cutout, Dollar, Finance, Fraud, Guard, Insurance, Investment, Isolated, Law, Locked, Money, Note, Object, Padlock, Paper, Prevention, Protect, Protection, Risk, Rusty, Safe, Safeguard, Safety, Savings, Secure, Security, Theft, Trust, Us, Wealth, White Load up with our Ppt 3d Constant Description To Prevent Business Losses Three Steps PowerPoint Templates with our Ppt 3d Constant Description To Prevent Business Losses Three Steps PowerPoint Templates. You will be at the top of your game.
Ppt Continual Way To Prevent Manufacture Losses Seven Steps PowerPoint Templates
PPT continual way to prevent manufacture losses seven steps PowerPoint Templates-This PowerPoint Diagram shows you the continual way to prevent manufacture losses in any Business related Activities. It is shown by different shades of Brown color. -PPT continual way to prevent manufacture losses seven steps PowerPoint Templates-Anti-Virus, Caution, Computer, Computing, Concept, Crime, Danger, Encrypt, Encryption, Firewall, Fraud, Hazard, Hazardous, Internet, Lose, Loss, Network, Networking, Online, Password, Piracy, Precaution, Prevent, Prevention, Privacy, Private, Protect, Protection, Risk, Screen, Secure, Security, Site, Steal, Stealing, Text, Theft, Thievery, Viral, Virus, Warn, Web, Website, Words Review your plans with our Ppt Continual Way To Prevent Manufacture Losses Seven Steps PowerPoint Templates. Download without worries with our money back guaranteee.
Ppt Successive Representation Of 7 Stages An Arrow PowerPoint Templates
PPT successive representation of 7 stages an arrow PowerPoint Templates-This PowerPoint Diagram shows you the Successive Representation of five approaches on the Arrow. It shows the successive concepts used in a procedure. You can change color, size and orientation of any icon to your liking.-PPT successive representation of 7 stages an arrow PowerPoint Templates-Anti-Virus, Caution, Computer, Computing, Concept, Crime, Danger, Encrypt, Encryption, Firewall, Fraud, Hazard, Hazardous, Internet, Lose, Loss, Network, Networking, Online, Password, Piracy, Precaution, Prevent, Prevention, Privacy, Private, Protect, Protection, Risk, Screen, Secure, Security, Site, Steal, Stealing, Text, Theft, Thievery, Viral, Virus, Warn, Web, Website, Words Let the audience decide with our Ppt Successive Representation Of 7 Stages An Arrow PowerPoint Templates. Make sure your presentation gets the attention it deserves.
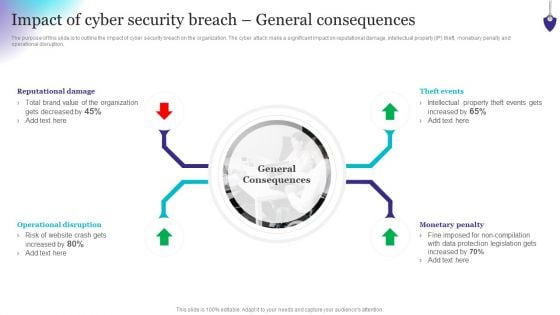
Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetxary penalty and operational disruption. If you are looking for a format to display your unique thoughts, then the professionally designed Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

IT Policies And Procedures BYOD Lost Stolen Hacked Or Damaged Equipment Elements PDF
This slide describes the scenarios of lost, stolen, hacked, or damaged personal equipment under BYOD policy. It also includes that remote wipe software should be installed on employees devices to remove the work data remotely in case of theft. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate IT Policies And Procedures BYOD Lost Stolen Hacked Or Damaged Equipment Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
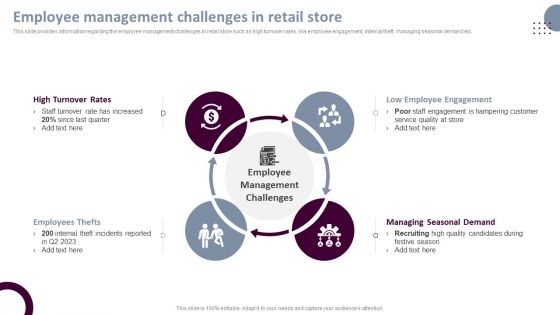
Retail Store Operations Employee Management Challenges In Retail Store Ideas PDF
This slide provides information regarding the employee management challenges in retail store such as high turnover rates, low employee engagement, internal theft, managing seasonal demand etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Retail Store Operations Employee Management Challenges In Retail Store Ideas PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
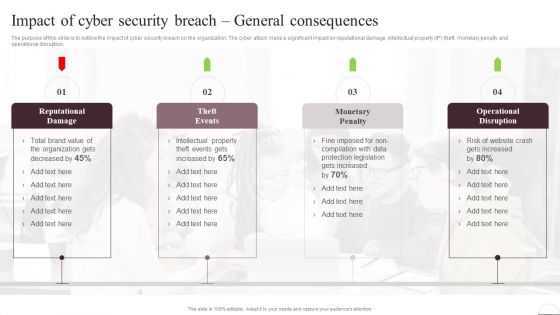
Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
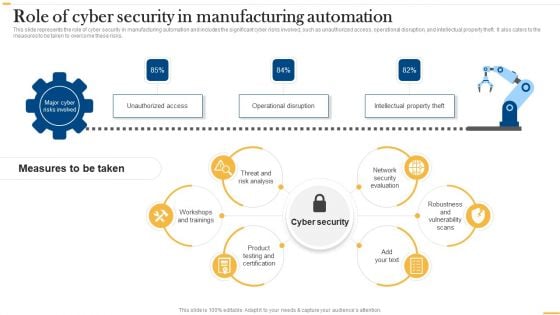
Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Are you searching for a Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF from Slidegeeks today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well arranged Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
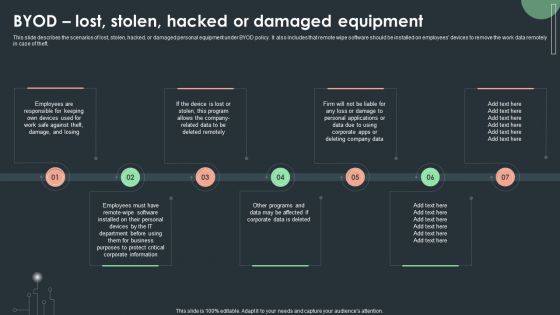
Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF
This slide describes the scenarios of lost, stolen, hacked, or damaged personal equipment under BYOD policy. It also includes that remote wipe software should be installed on employees devices to remove the work data remotely in case of theft. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Impact Of Cyber Security Breach General Consequences Ppt Styles Icon PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Present like a pro with Impact Of Cyber Security Breach General Consequences Ppt Styles Icon PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
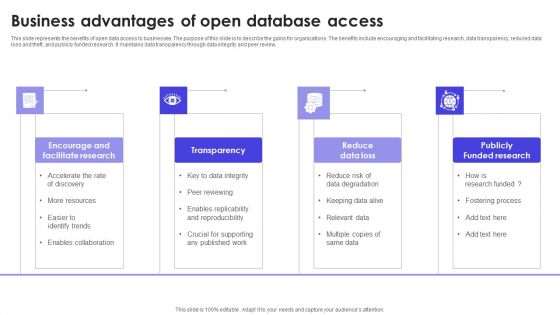
Business Advantages Of Open Database Access Structure PDF
This slide represents the benefits of open data access to businesses. The purpose of this slide is to describe the gains for organizations. The benefits include encouraging and facilitating research, data transparency, reduced data loss and theft, and publicly funded research. It maintains data transparency through data integrity and peer review. Persuade your audience using this Business Advantages Of Open Database Access Structure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Research, Transparency, Reduce Data Loss . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Policy And Processes BYOD Lost Stolen Hacked Or Damaged Equipment Portrait PDF
This slide describes the scenarios of lost, stolen, hacked, or damaged personal equipment under BYOD policy. It also includes that remote wipe software should be installed on employees devices to remove the work data remotely in case of theft. Want to ace your presentation in front of a live audience Our Information Technology Policy And Processes BYOD Lost Stolen Hacked Or Damaged Equipment Portrait PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
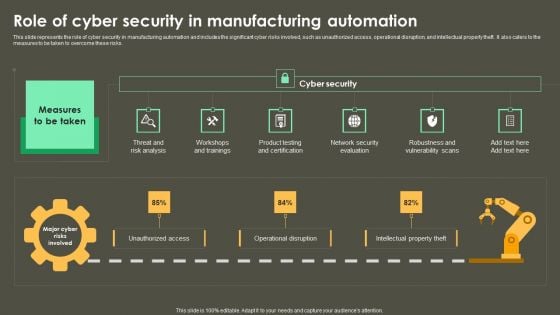
Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well-arranged Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
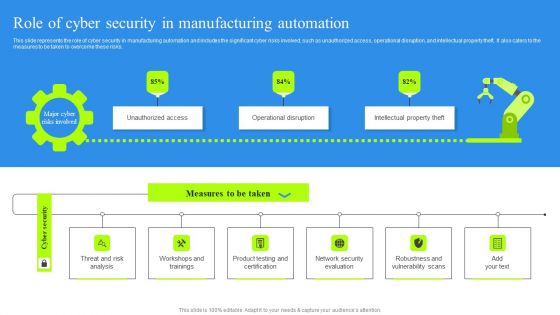
Role Of Cyber Security In Manufacturing Automation Portrait PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
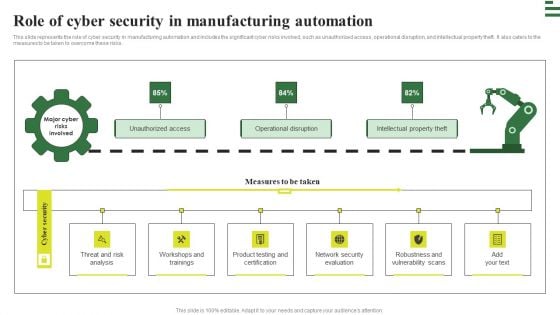
Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.


 Continue with Email
Continue with Email

 Home
Home


































