Web Security

Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
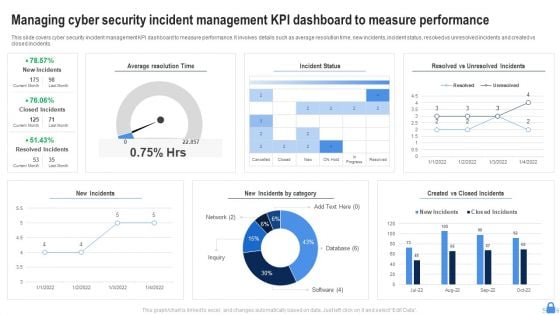
Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF
This slide covers cyber security incident management KPI dashboard to measure performance. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
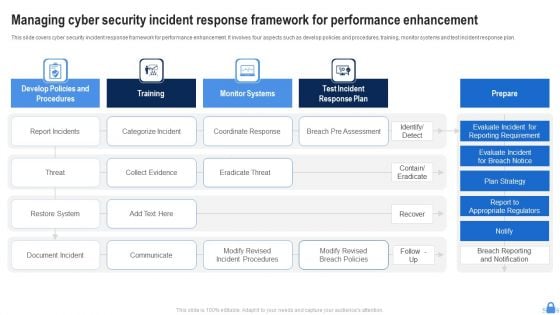
Managing Cyber Security Incident Response Framework For Performance Enhancement Formats PDF
This slide covers cyber security incident response framework for performance enhancement. It involves four aspects such as develop policies and procedures, training, monitor systems and test incident response plan. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response Framework For Performance Enhancement Formats PDF. This layout presents information on Report Incidents, Threat, Restore System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
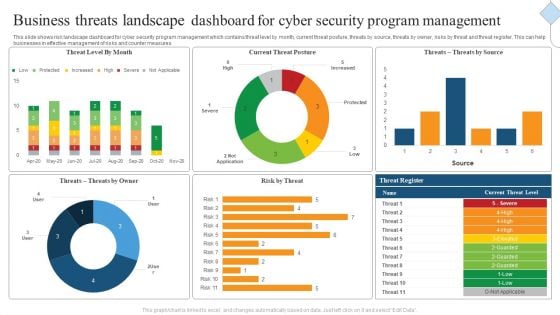
Business Threats Landscape Dashboard For Cyber Security Program Management Ppt Gallery Images PDF
This slide shows risk landscape dashboard for cyber security program management which contains threat level by month, current threat posture, threats by source, threats by owner, risks by threat and threat register. This can help businesses in effective management of risks and counter measures. Showcasing this set of slides titled Business Threats Landscape Dashboard For Cyber Security Program Management Ppt Gallery Images PDF. The topics addressed in these templates are Current Threat Posture, Threat Register, Source. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Welcome to our selection of the IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
6 Stage Yearly Business Planning Cycle For Cyber Security Project Icons PDF
This slide signifies the six step yearly planning life cycle for cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor.Persuade your audience using this 6 Stage Yearly Business Planning Cycle For Cyber Security Project Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Money Laundering, System Malfunction, Financial Transaction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Cyber Physical System To Enhance Security Topics PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Cyber Physical System To Enhance Security Topics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Cyber Physical System To Enhance Security Topics PDF today and make your presentation stand out from the rest.
Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF.

Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF
Find highly impressive Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF
Explore a selection of the finest Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Want to ace your presentation in front of a live audience Our Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
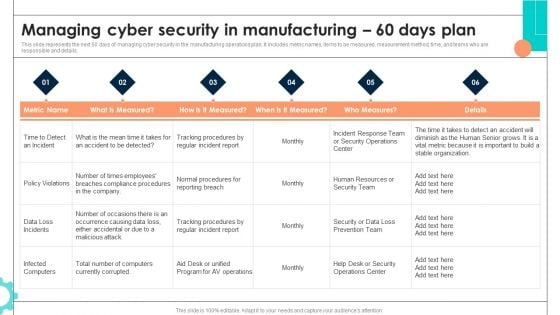
Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
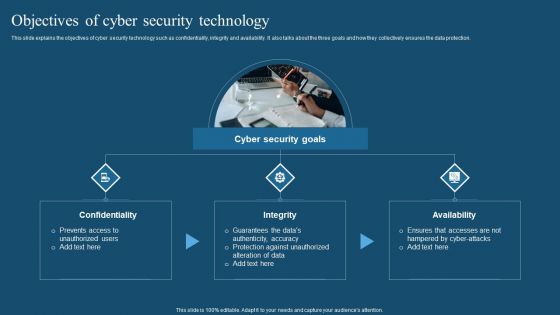
Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF
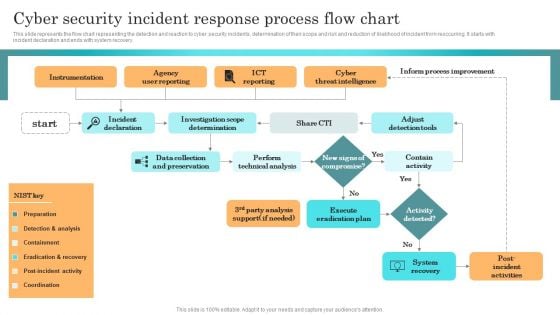
Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.
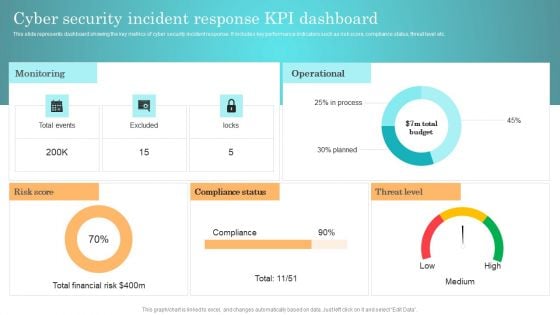
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF
The following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Want to ace your presentation in front of a live audience Our Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF
This slide signifies the strategic plan timeline to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor Persuade your audience using this Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Analyse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
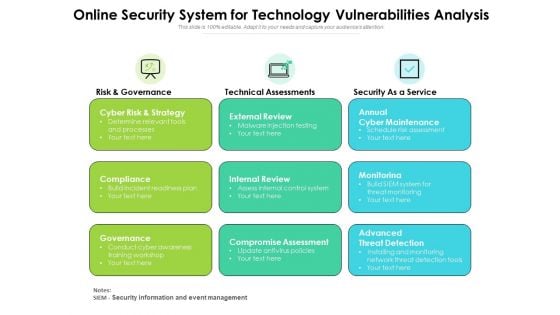
Online Security System For Technology Vulnerabilities Analysis Ppt PowerPoint Presentation Ideas Design Ideas PDF
Presenting this set of slides with name online security system for technology vulnerabilities analysis ppt powerpoint presentation ideas design ideas pdf. This is a three stage process. The stages in this process are cyber risk and strategy, compliance governance, external review, internal review, compromise assessment, annual cyber maintenance, monitorinag, advanced threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
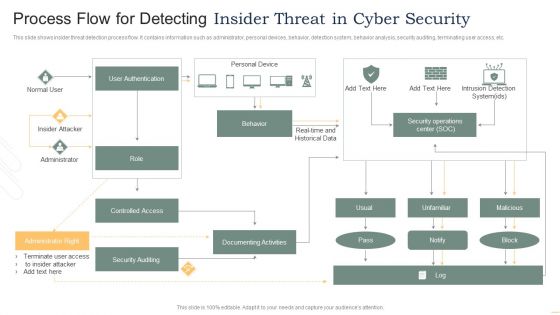
Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
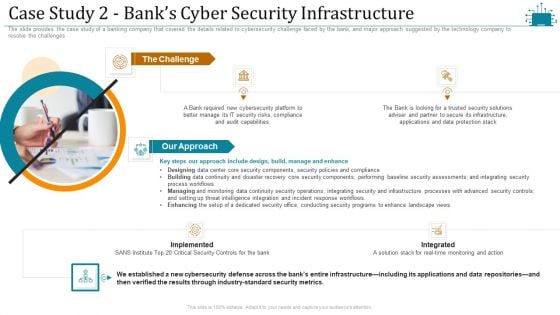
Cloud Intelligence Framework For Application Consumption Case Study 2 Banks Cyber Security Infrastructure Microsoft PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges. This is a cloud intelligence framework for application consumption case study 2 banks cyber security infrastructure microsoft pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process workflows, industry standard security metrics, implemented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
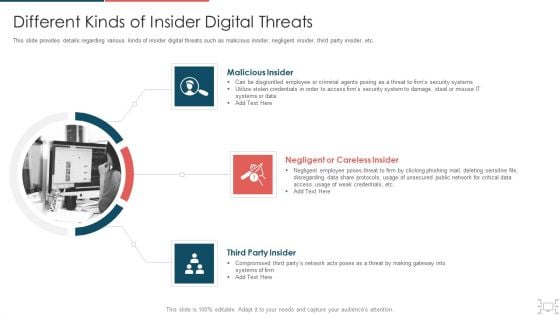
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
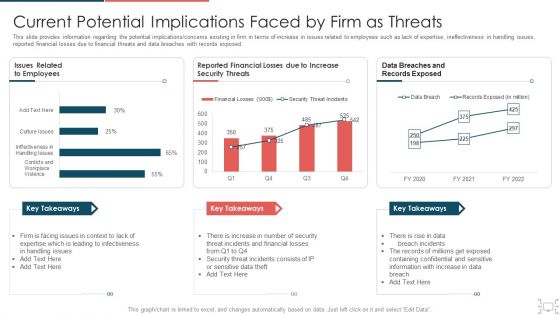
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
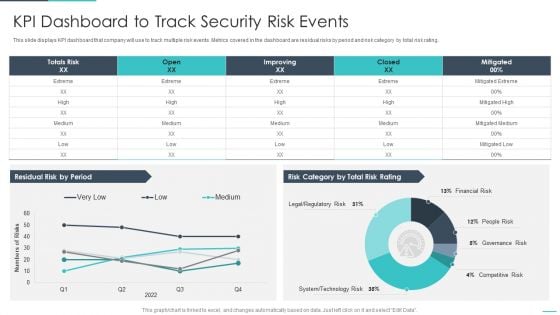
Handling Cyber Threats Digital Era KPI Dashboard To Track Security Risk Events Ppt Inspiration PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era kpi dashboard to track security risk events ppt inspiration pdf. Use them to share invaluable insights on kpi dashboard to track security risk events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
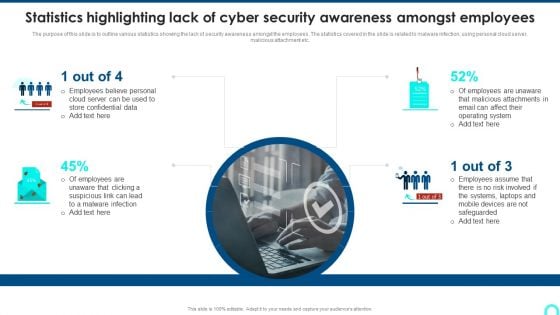
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
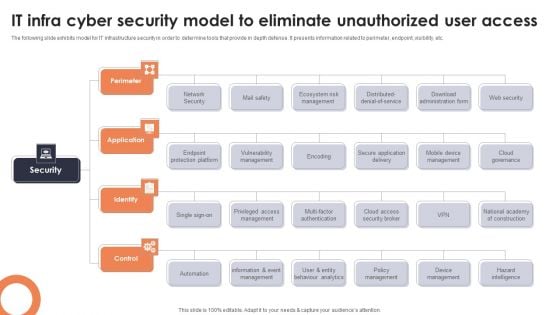
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
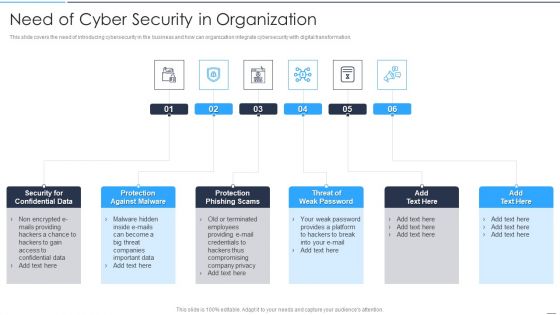
Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
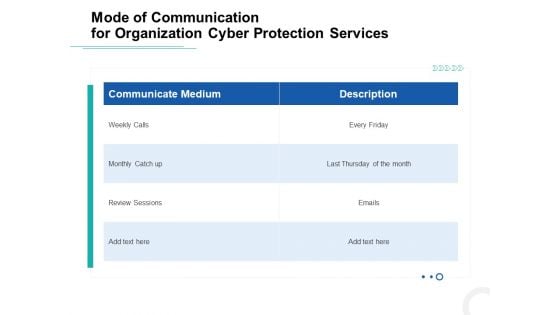
Develop Corporate Cyber Security Risk Mitigation Plan Mode Communication Organization Protection Services Introduction PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan mode communication organization protection services introduction pdf bundle. Topics like communicate medium, weekly calls, monthly catch up, review sessions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
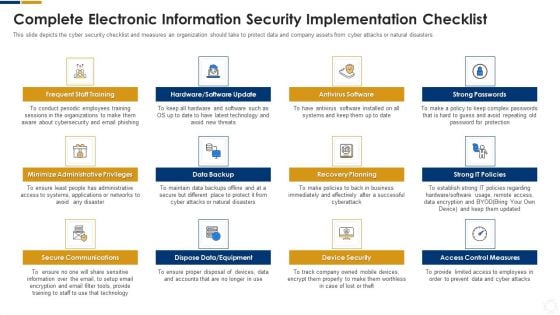
Cybersecurity Complete Electronic Information Security Implementation Checklist Ppt Inspiration Outline PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting cybersecurity complete electronic information security implementation checklist ppt inspiration outline pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, equipment, secure communications, data backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF
This slide provides information about enabling online brand protection by tracking incidents per seller, incident per platform and infringements per country. Presenting this PowerPoint presentation, titled Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Strategies To Mitigate Cyber Security Risks Determining Firm Current Capabilities Ppt Inspiration Smartart PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining firm current capabilities ppt inspiration smartart pdf. The topics discussed in these slides are identify, protect, detect, response, recovery, key enablers, minimum standard, evolving strength. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Determining Firm Current Capabilities Ppt Outline Shapes PDF
Presenting this set of slides with name cyber security implementation framework determining firm current capabilities ppt outline shapes pdf. The topics discussed in these slides are identify, protect, detect, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Process Steps With Icons Ppt PowerPoint Presentation Summary Slide
Presenting this set of slides with name cyber security process steps with icons ppt powerpoint presentation summary slide. This is a four stage process. The stages in this process are assess, evaluate, build, execute. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
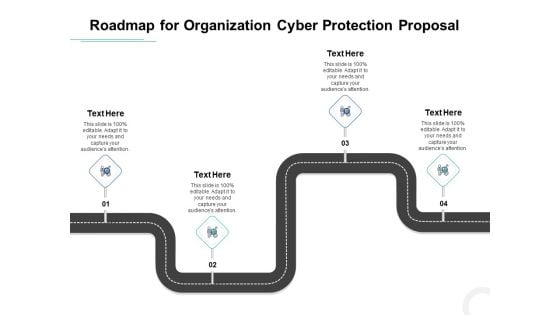
Develop Corporate Cyber Security Risk Mitigation Plan Roadmap For Organization Cyber Protection Proposal Summary PDF
Presenting develop corporate cyber security risk mitigation plan roadmap for organization cyber protection proposal summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap, organization cyber protection. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Five Stages Circular Process Business Cyber Security Ppt PowerPoint Presentation Icon Tips
Presenting this set of slides with name five stages circular process business cyber security ppt powerpoint presentation icon tips. This is a five stage process. The stages in this process are technology, strategy, steps approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Testing Process With Icons Ppt PowerPoint Presentation Infographic Template Demonstration
Presenting this set of slides with name cyber security testing process with icons ppt powerpoint presentation infographic template demonstration. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
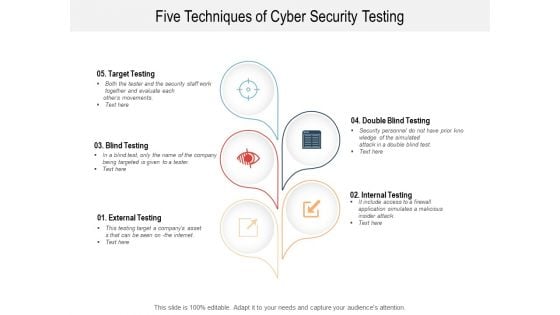
Five Techniques Of Cyber Security Testing Ppt PowerPoint Presentation Layouts Model
Presenting this set of slides with name five techniques of cyber security testing ppt powerpoint presentation layouts model. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name cyber security for your organization ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are risk management, business, analysis, goal, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Backup Maintenance Recovery Budget Planning Ppt Inspiration Slide Portrait PDF
Presenting this set of slides with name cyber security for your organization backup maintenance recovery budget planning ppt inspiration slide portrait pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, travel shipping costs, labor contractor costs, testing costs, supply costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Critical Business Functions Recovery Priorities Ppt Inspiration Slide PDF
Presenting this set of slides with name cyber security for your organization critical business functions recovery priorities ppt inspiration slide pdf. This is a one stage process. The stages in this process are priorities, maximum allowable downtime, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Essential Contingency Plan Strategies Ppt Layouts Vector PDF
Presenting this set of slides with name cyber security for your organization essential contingency plan strategies ppt layouts vector pdf. This is a one stage process. The stages in this process are contingency considerations, contingency solutions, server, vendor information, critical components, technologies integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Our Mission Ppt Infographics Model PDF
Presenting this set of slides with name cyber security for your organization our mission ppt infographics model pdf. This is a one stage process. The stages in this process are vision, mission, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Our Team Ppt Ideas Infographic Template PDF
Presenting this set of slides with name cyber security for your organization our team ppt ideas infographic template pdf. This is a four stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
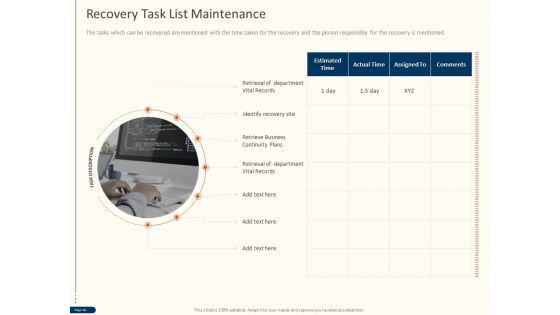
Cyber Security For Your Organization Recovery Task List Maintenance Ppt Layouts Designs Download PDF
Presenting this set of slides with name cyber security for your organization recovery task list maintenance ppt layouts designs download pdf. This is a one stage process. The stages in this process are estimated time, actual time, assigned, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Risk Assessment Matrix Ppt Ideas PDF
Presenting this set of slides with name cyber security for your organization risk assessment matrix ppt ideas pdf. This is a one stage process. The stages in this process are insignificant, minor, severity, risk, catastrophic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Staff Training Schedule With Cost Ppt Visual Aids Slides PDF
Presenting this set of slides with name cyber security for your organization staff training schedule with cost ppt visual aids slides pdf. This is a one stage process. The stages in this process are advanced software training, advanced skills train, training module. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Thank You Ppt Portfolio Clipart PDF
Presenting this set of slides with name cyber security for your organization thank you ppt portfolio clipart pdf. The topics discussed in these slide is thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security For Your Organization Timeframe For Incident Management Ppt Icon Graphics Design PDF
Presenting this set of slides with name cyber security for your organization timeframe for incident management ppt icon graphics design pdf. This is a one stage process. The stages in this process are incident logging, ticket creation, incident categorization, incident prioritization, incident resolution, incident closure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Weekly Timeline With Task Name Ppt Outline Ideas PDF
Presenting this set of slides with name cyber security for your organization weekly timeline with task name ppt outline ideas pdf. The topics discussed in these slide is organization weekly timeline. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
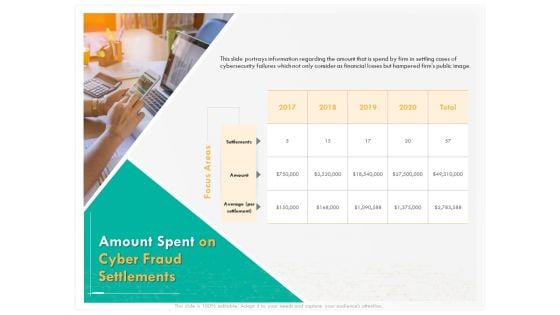
Computer Security Incident Handling Amount Spent On Cyber Fraud Settlements Portrait PDF
Presenting this set of slides with name computer security incident handling amount spent on cyber fraud settlements portrait pdf. The topics discussed in these slides are settlements, amount, average. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
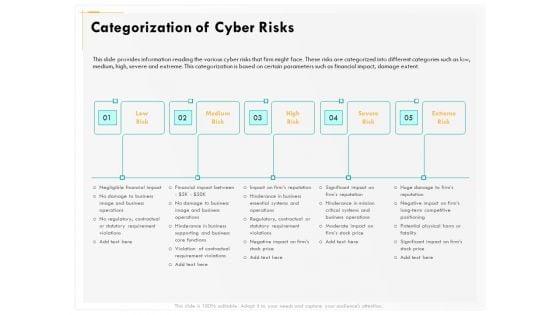
Computer Security Incident Handling Categorization Of Cyber Risks Ppt Gallery Template PDF
Presenting this set of slides with name computer security incident handling categorization of cyber risks ppt gallery template pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
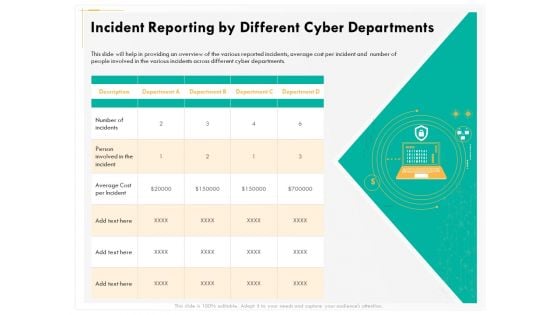
Computer Security Incident Handling Incident Reporting By Different Cyber Departments Brochure PDF
Presenting this set of slides with name computer security incident handling incident reporting by different cyber departments brochure pdf. The topics discussed in these slides are description, department a, department b, department c, department d. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For Strategies To Mitigate Cyber Security Risks Ppt Icon Themes PDF
Presenting this set of slides containing editable icons for topic icons slide for strategies to mitigate cyber security risks ppt icon themes pdf. All icons in this slide are 100 percent editable. You can replace icons in your deck with any of these icons. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































